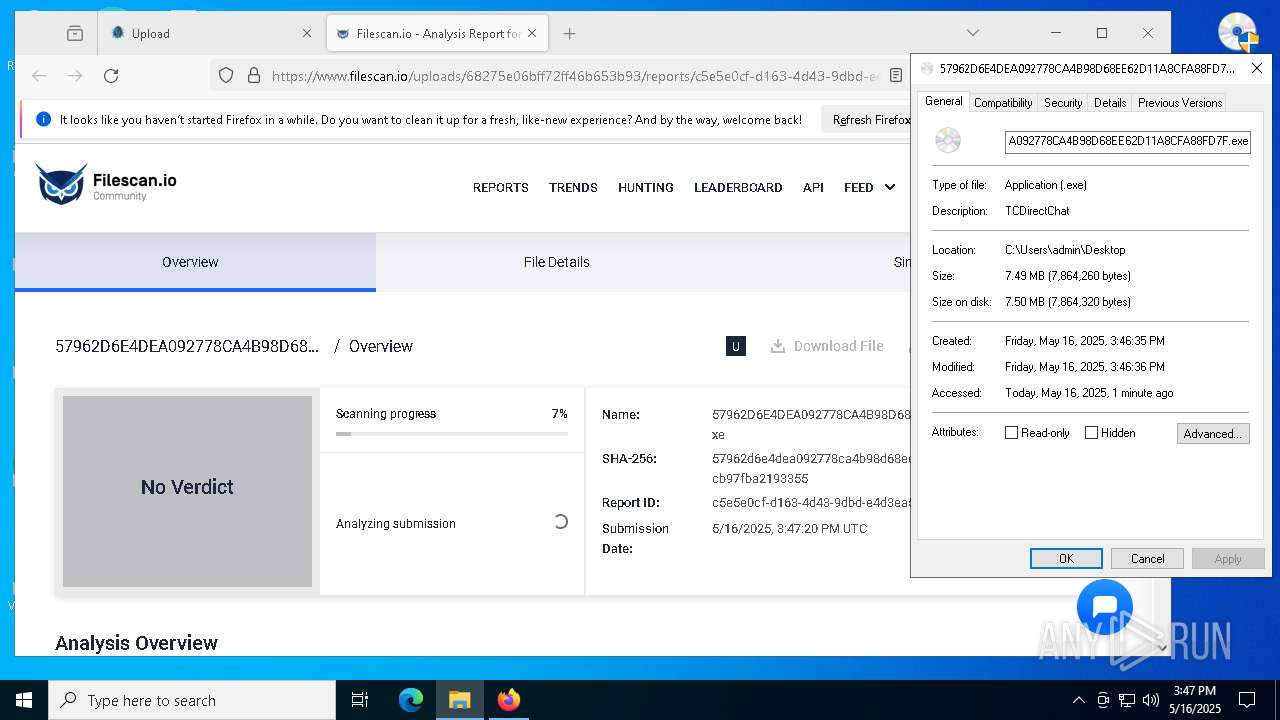
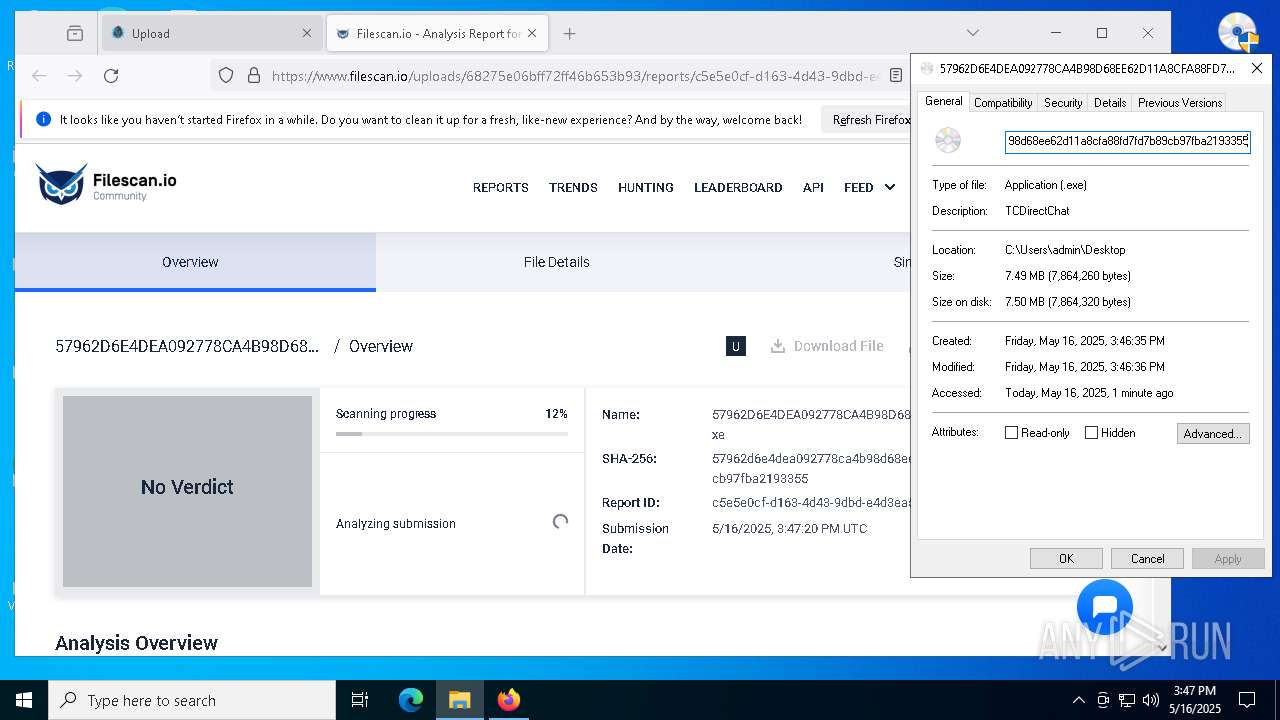
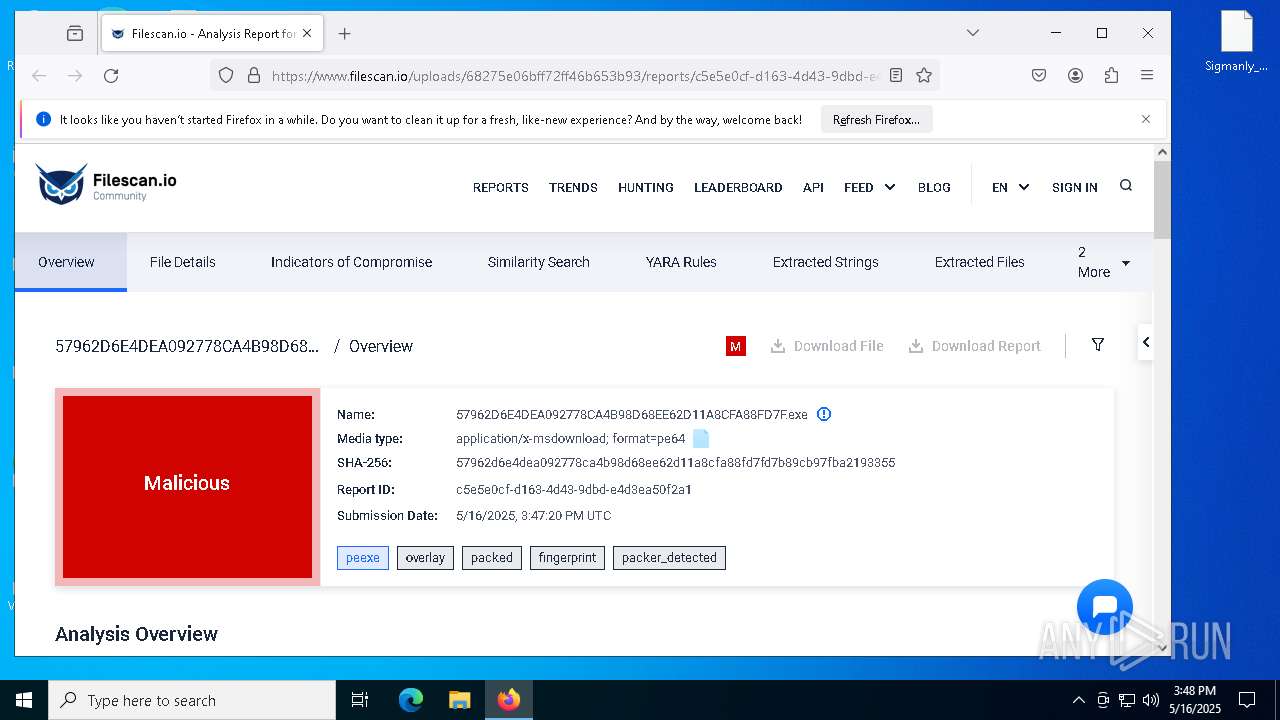
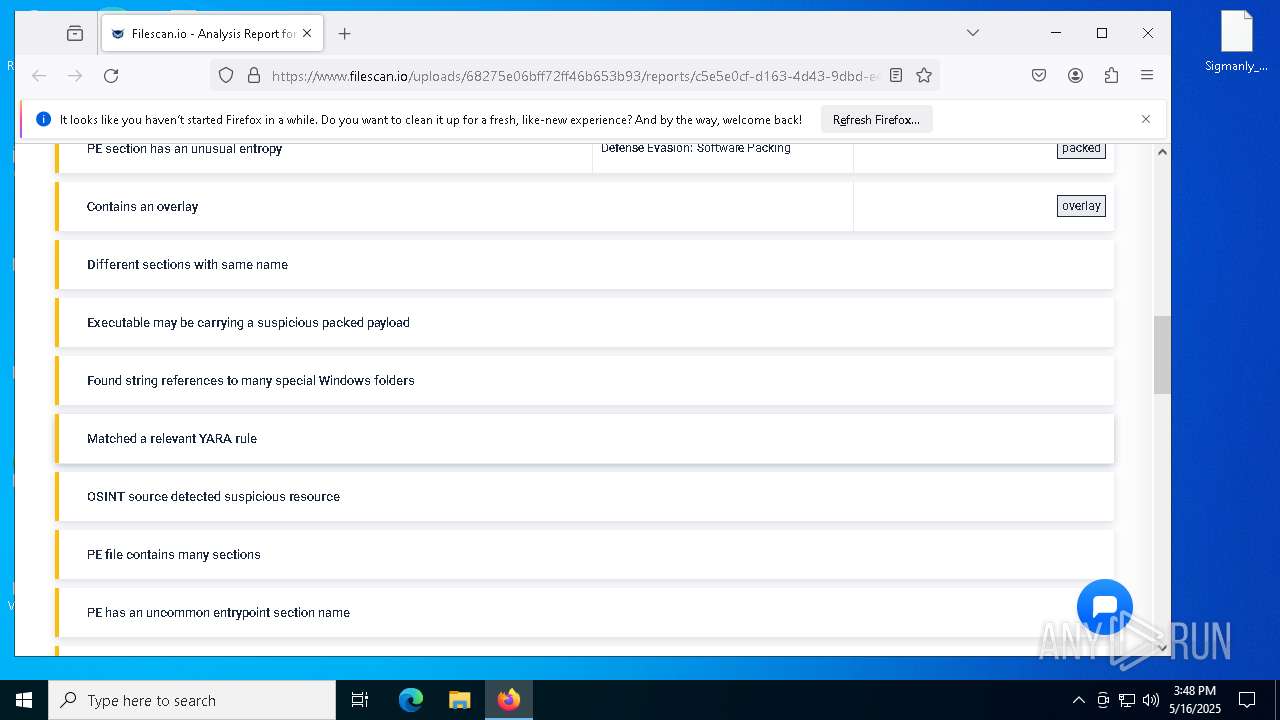
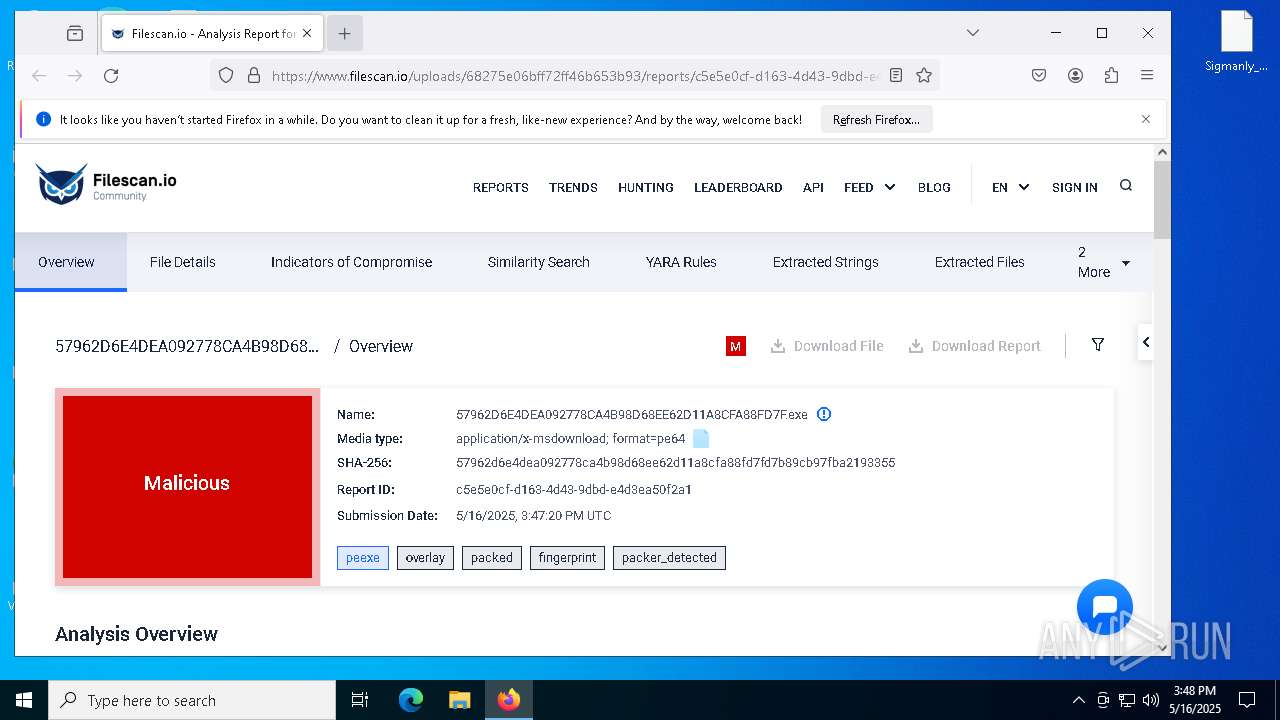
| File name: | 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe |
| Full analysis: | https://app.any.run/tasks/13b47a27-52e1-470d-95a5-d89200606759 |
| Verdict: | Malicious activity |
| Threats: | PrivateLoader is a malware family that is specifically created to infect computer systems and drop additional malicious programs. It operates using a pay-per-install business model, which means that the individuals behind it are paid for each instance of successful deployment of different types of harmful programs, including trojans, stealers, and other ransomware. |
| Analysis date: | May 16, 2025, 15:46:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 10 sections |
| MD5: | FDE4EC171A6E988C9640D8F8DCF35AEA |
| SHA1: | 47D357A4E617B46E47DDC8AA9869F33A3C9FFFB8 |
| SHA256: | 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7FD7B89CB97FBA2193355 |
| SSDEEP: | 98304:9bRwXuv0bjY0mqBvzKczYA3IycQ6XpyWzI/vjhugtsoQYWb7lFGo3:MeMVvaAPHzhug4pUy |
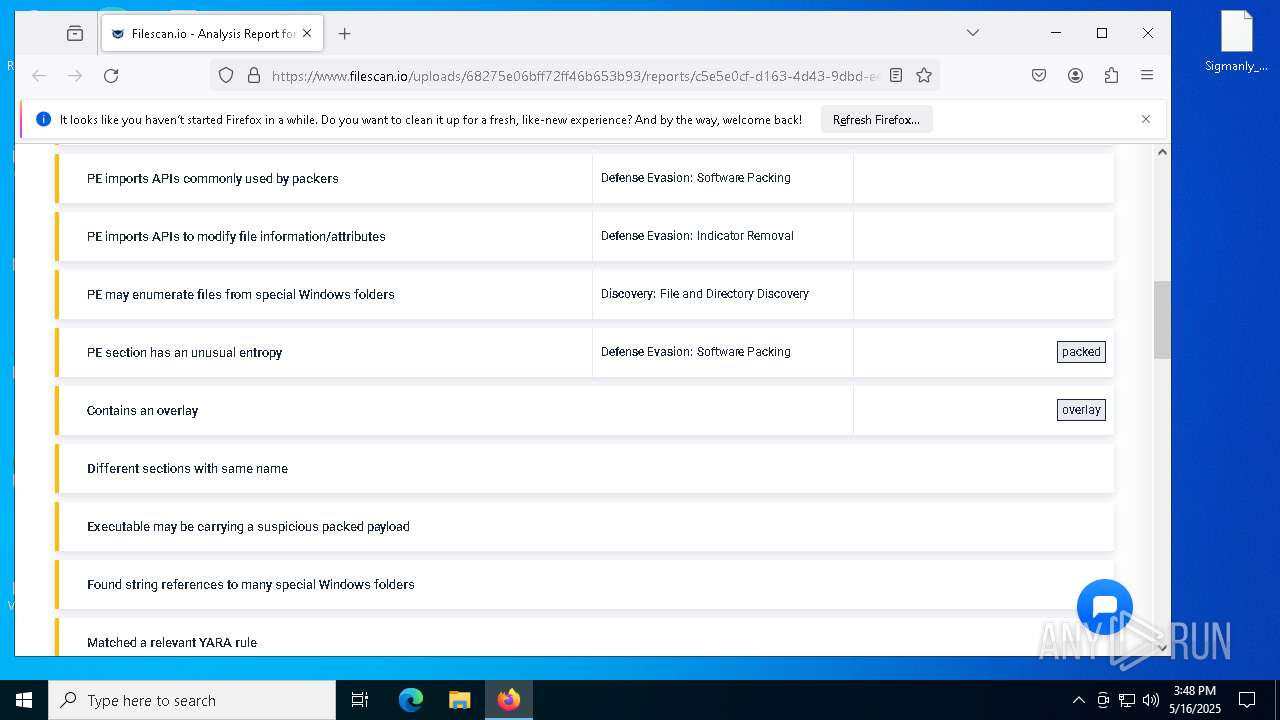
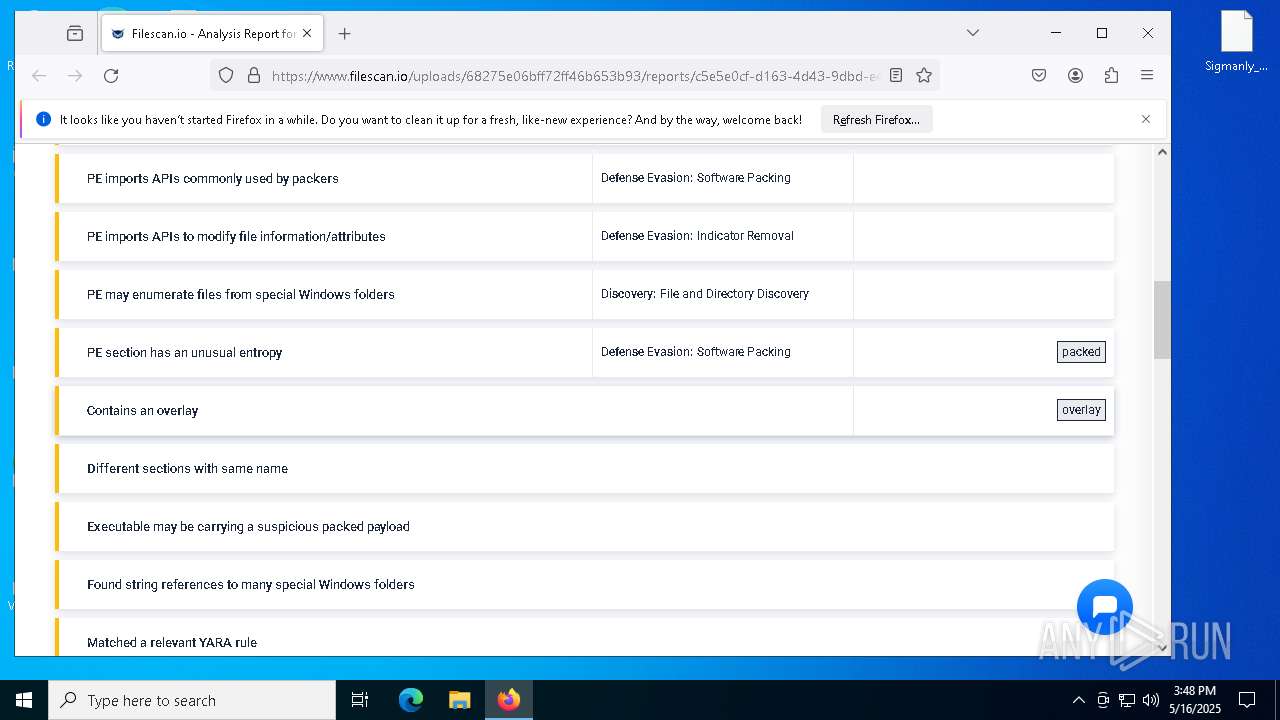
MALICIOUS
Changes the Windows auto-update feature
- 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe (PID: 1660)
PRIVATELOADER has been detected (YARA)
- 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe (PID: 1660)
- Botnet.exe (PID: 4736)
SUSPICIOUS
Executes application which crashes
- 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe (PID: 1660)
- Botnet.exe (PID: 4736)
- Botnet.exe (PID: 6668)
- Botnet.exe (PID: 2852)
- Botnet.exe (PID: 6184)
- Botnet.exe (PID: 2236)
- Botnet.exe (PID: 4188)
- Botnet.exe (PID: 720)
- Botnet.exe (PID: 3396)
- Botnet.exe (PID: 6264)
- Botnet.exe (PID: 2268)
- Botnet.exe (PID: 6072)
- Botnet.exe (PID: 8000)
- Botnet.exe (PID: 5232)
- Botnet.exe (PID: 2664)
- Botnet.exe (PID: 632)
- Botnet.exe (PID: 7420)
- Botnet.exe (PID: 4728)
- Botnet.exe (PID: 7212)
- Botnet.exe (PID: 7576)
- Botnet.exe (PID: 7820)
- Botnet.exe (PID: 7600)
- Botnet.exe (PID: 2560)
- Botnet.exe (PID: 7992)
- Botnet.exe (PID: 1852)
- Botnet.exe (PID: 660)
INFO
Checks supported languages
- 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe (PID: 1660)
The sample compiled with english language support
- 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe (PID: 1660)
Manual execution by a user
- Botnet.exe (PID: 7480)
- Botnet.exe (PID: 7864)
- Botnet.exe (PID: 4528)
- firefox.exe (PID: 4892)
- Botnet.exe (PID: 4736)
- Botnet.exe (PID: 3396)
- Botnet.exe (PID: 4268)
- Botnet.exe (PID: 4188)
- Botnet.exe (PID: 2236)
- Botnet.exe (PID: 7264)
- Botnet.exe (PID: 7460)
- Botnet.exe (PID: 5984)
- Botnet.exe (PID: 6264)
- Botnet.exe (PID: 2268)
- Botnet.exe (PID: 720)
- Botnet.exe (PID: 7412)
- Botnet.exe (PID: 8000)
- Botnet.exe (PID: 7372)
- Botnet.exe (PID: 6072)
- Botnet.exe (PID: 6828)
- Botnet.exe (PID: 1852)
- Botnet.exe (PID: 2664)
- Botnet.exe (PID: 3804)
- Botnet.exe (PID: 5232)
- Botnet.exe (PID: 2772)
- Botnet.exe (PID: 2432)
- Botnet.exe (PID: 632)
- Botnet.exe (PID: 7452)
- Botnet.exe (PID: 4728)
- Botnet.exe (PID: 7420)
- Botnet.exe (PID: 7636)
- Botnet.exe (PID: 7576)
- Botnet.exe (PID: 7264)
- Botnet.exe (PID: 7212)
- Botnet.exe (PID: 644)
- Botnet.exe (PID: 660)
- Botnet.exe (PID: 900)
- Botnet.exe (PID: 8068)
- Botnet.exe (PID: 2560)
- Botnet.exe (PID: 7992)
- Botnet.exe (PID: 7820)
- Botnet.exe (PID: 8060)
- Botnet.exe (PID: 7516)
- Botnet.exe (PID: 8168)
- Botnet.exe (PID: 7988)
- Botnet.exe (PID: 2852)
- Botnet.exe (PID: 6184)
- Botnet.exe (PID: 6668)
- Botnet.exe (PID: 7600)
- Botnet.exe (PID: 6540)
Creates files or folders in the user directory
- WerFault.exe (PID: 6712)
Reads the computer name
- 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe (PID: 1660)
Application launched itself
- firefox.exe (PID: 4892)
- firefox.exe (PID: 6480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:05:25 12:13:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 3105280 |
| InitializedDataSize: | 709120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8844a9 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.45.1145 |
| ProductVersionNumber: | 7.0.45.1145 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | N-able Take Control |
| FileDescription: | TCDirectChat |
| FileVersion: | 7.0.45.1145 |
| InternalName: | N-able Take Control |
| ProgramID: | com.embarcadero.TCDirectChat |
| ProductName: | TCDirectChat |
| ProductVersion: | 7.0.45.1145 |
Total processes
358
Monitored processes
96
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\WINDOWS\system32\WerFault.exe -u -p 7212 -s 896 | C:\Windows\System32\WerFault.exe | — | Botnet.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Users\admin\Desktop\Botnet.exe" | C:\Users\admin\Desktop\Botnet.exe | explorer.exe | ||||||||||||
User: admin Company: N-able Take Control Integrity Level: HIGH Description: TCDirectChat Exit code: 3221225620 Version: 7.0.45.1145 Modules
| |||||||||||||||
| 644 | "C:\Users\admin\Desktop\Botnet.exe" | C:\Users\admin\Desktop\Botnet.exe | — | explorer.exe | |||||||||||
User: admin Company: N-able Take Control Integrity Level: MEDIUM Description: TCDirectChat Exit code: 3221226540 Version: 7.0.45.1145 Modules
| |||||||||||||||
| 644 | C:\WINDOWS\system32\WerFault.exe -u -p 8000 -s 788 | C:\Windows\System32\WerFault.exe | — | Botnet.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\Users\admin\Desktop\Botnet.exe" | C:\Users\admin\Desktop\Botnet.exe | explorer.exe | ||||||||||||
User: admin Company: N-able Take Control Integrity Level: HIGH Description: TCDirectChat Exit code: 3221225620 Version: 7.0.45.1145 Modules
| |||||||||||||||
| 720 | "C:\Users\admin\Desktop\Botnet.exe" | C:\Users\admin\Desktop\Botnet.exe | explorer.exe | ||||||||||||
User: admin Company: N-able Take Control Integrity Level: HIGH Description: TCDirectChat Exit code: 3221225620 Version: 7.0.45.1145 Modules
| |||||||||||||||
| 900 | "C:\Users\admin\Desktop\Botnet.exe" | C:\Users\admin\Desktop\Botnet.exe | — | explorer.exe | |||||||||||
User: admin Company: N-able Take Control Integrity Level: MEDIUM Description: TCDirectChat Exit code: 3221226540 Version: 7.0.45.1145 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6216 -parentBuildID 20240213221259 -sandboxingKind 1 -prefsHandle 5668 -prefMapHandle 4768 -prefsLen 38523 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {50abeba3-cd59-4f32-89eb-3eba49b38f91} 6480 "\\.\pipe\gecko-crash-server-pipe.6480" 16a0cfc6310 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 1328 | C:\WINDOWS\system32\WerFault.exe -u -p 6184 -s 852 | C:\Windows\System32\WerFault.exe | — | Botnet.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe" | C:\Users\admin\Desktop\57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | explorer.exe | ||||||||||||
User: admin Company: N-able Take Control Integrity Level: HIGH Description: TCDirectChat Exit code: 3221225620 Version: 7.0.45.1145 Modules
| |||||||||||||||
Total events
84 995
Read events
83 066
Write events
1 174
Delete events
755
Modification events
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\AppHVSI |
| Operation: | write | Name: | AllowAppHVSI_ProviderSet |
Value: 0 | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UpdateDefault |
Value: 0 | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\Network Connections |
| Operation: | write | Name: | NC_DoNotShowLocalOnlyIcon |
Value: 1 | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\Windows Feeds |
| Operation: | write | Name: | EnableFeeds |
Value: 0 | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUStatusServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | UpdateServiceUrlAlternate |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | **del.FillEmptyContentUrls |
Value: | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | UseWUServer |
Value: 1 | |||
| (PID) Process: | (1660) 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4D39817A-A3B0-48BA-835C-A6FCE794EA2C}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | NoAutoUpdate |
Value: 0 | |||
Executable files
0
Suspicious files
284
Text files
45
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6712 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_57962D6E4DEA0927_9cce309a4e5bae7d751c69bc86cfd5159a8098_a4e47463_bcb35c48-e922-409b-8f09-51812202d59e\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6480 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6712 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF8AB.tmp.WERInternalMetadata.xml | binary | |
MD5:CBDC780329E6930183496CB4771D2C15 | SHA256:12507066677B911DB41926DD2EEA4A98E4898ED357BE190FFC58739FBB825F0F | |||
| 6712 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:A12D39C78F2F58EF30E04C11508469EF | SHA256:DBA7226E7B2C6F31620D4306488944D04F464A642762D96F9D6FF53D5B7C4130 | |||
| 6480 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 6480 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1660 | 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:3D89F23265C9E30A0CF055C3EB4D637C | SHA256:806582F6221C79BD4C7EACDC4B63E937CE247EEE2BA159F55C545CDFB2B1C25B | |||
| 6480 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1660 | 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:551F2716A3AF0148E9A55792A5708892 | SHA256:B4E6B3EB7656C4D44F67FBCC6803525C17DCA34BD65AF9F146D8FCA3441AB565 | |||
| 6712 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERF7C0.tmp.dmp | binary | |
MD5:E421924C5273268B40F28E2F4F99E1F1 | SHA256:97F094648CFCB098F9113ACA9285BC5049BFE2DC16B1A50B92B831956551B319 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
594
DNS requests
216
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | — | 142.250.185.195:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
6480 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1660 | 57962D6E4DEA092778CA4B98D68EE62D11A8CFA88FD7F.exe | 85.208.136.10:80 | — | AS-DC | US | malicious |
2196 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2196 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud-Hosted Matomo Analytics (matomo .cloud) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud-Hosted Matomo Analytics (matomo .cloud) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud-Hosted Matomo Analytics (matomo .cloud) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud-Hosted Matomo Analytics (matomo .cloud) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud-Hosted Matomo Analytics (matomo .cloud) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud-Hosted Matomo Analytics (matomo .cloud) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud-Hosted Matomo Analytics (matomo .cloud) |