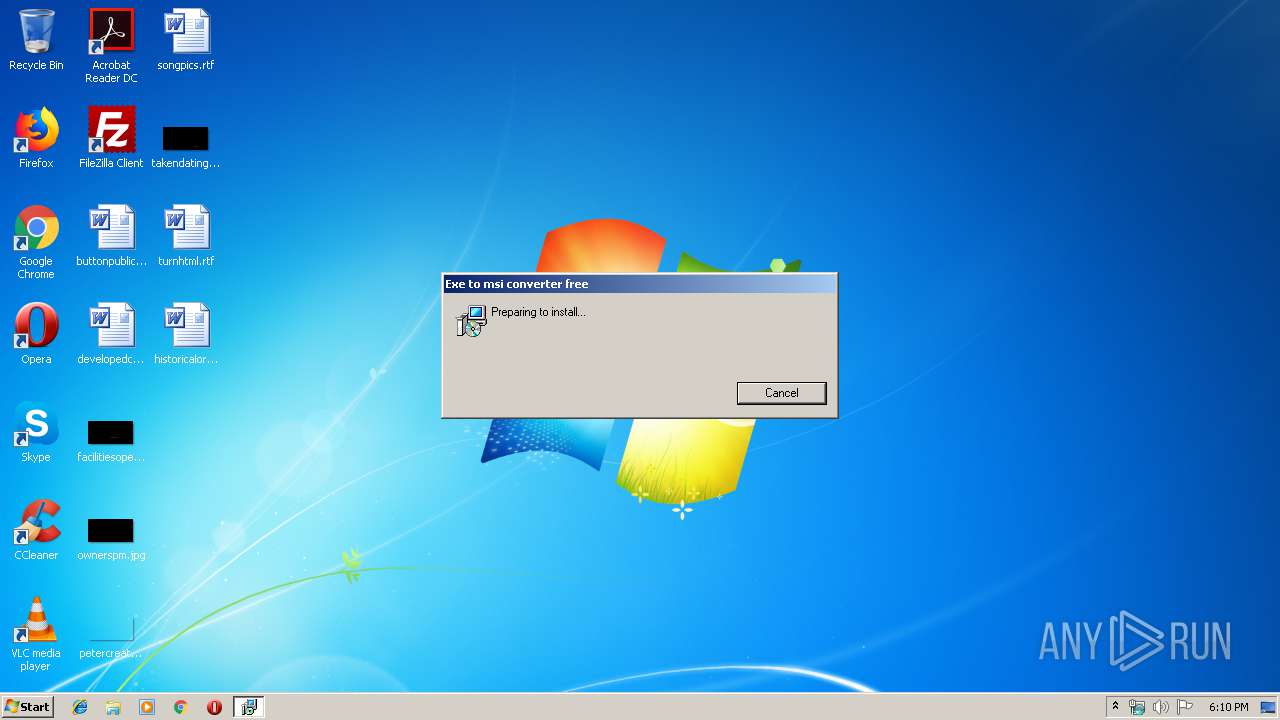
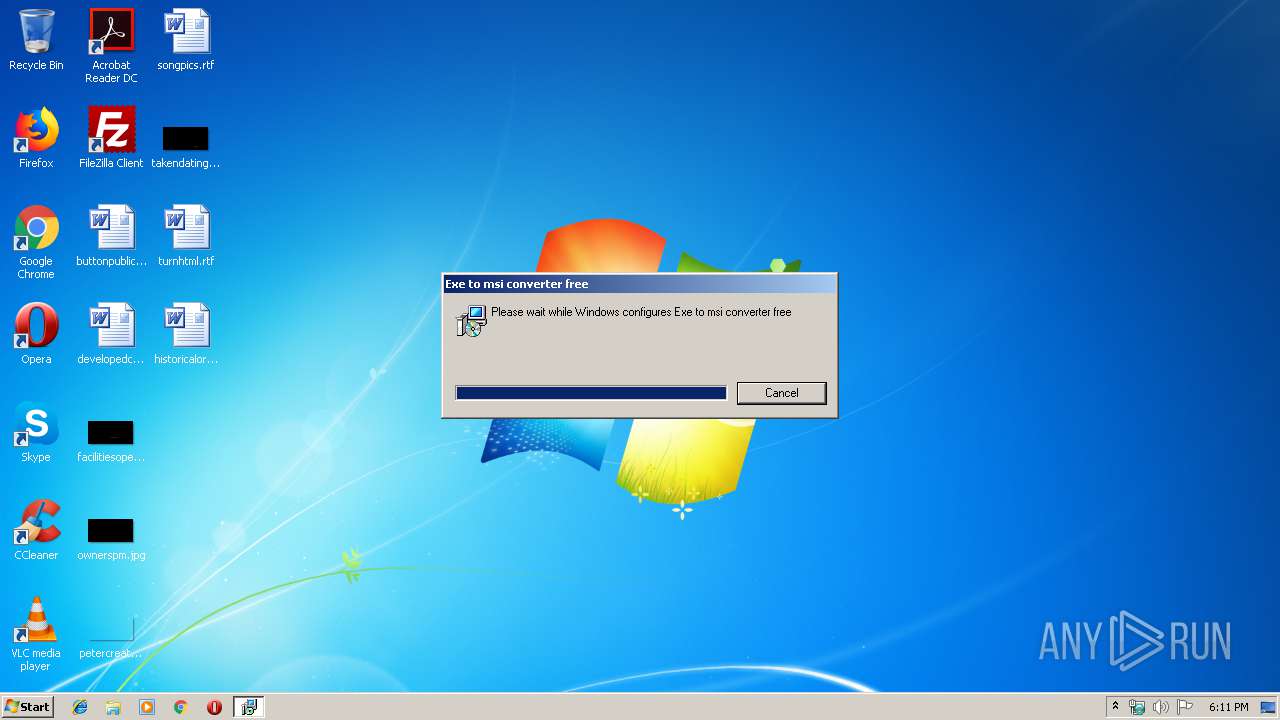
| File name: | fb.msi |
| Full analysis: | https://app.any.run/tasks/5ee1ab4a-ad1d-412b-84ef-e5b484da399e |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | August 25, 2019, 17:10:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Code page: 1252, Last Printed: Fri Sep 21 10:56:09 2012, Create Time/Date: Fri Sep 21 10:56:09 2012, Name of Creating Application: Windows Installer, Title: Exe to msi converter free, Author: www.exetomsi.com, Template: ;0, Last Saved By: devuser, Revision Number: {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E}, Last Saved Time/Date: Tue May 21 12:56:44 2013, Number of Pages: 100, Number of Words: 0, Security: 0 |
| MD5: | EE9F001F43232D7A4CDDD81028198A0F |
| SHA1: | 0577D413C9C38D999204A19F560AF179275B710A |
| SHA256: | 57792660079BC7EF67D5F4F1C72AADC575FB3F262D905214309598929B38EBB4 |
| SSDEEP: | 6144:UEPHzYVe1B9hYHT9X3AJTMZVyVVrLfHwBOBVdijv4DGMnggwIG2lCCxAO54DLQS:UEPMe9hqRmMZIVVnQ8Byjv7Mnf22lC7K |
MALICIOUS
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2936)
Uses Task Scheduler to run other applications
- MSID6DE.tmp (PID: 3868)
FORMBOOK was detected
- explorer.exe (PID: 276)
Connects to CnC server
- explorer.exe (PID: 276)
Actions looks like stealing of personal data
- dwm.exe (PID: 2880)
Stealing of credential data
- dwm.exe (PID: 2880)
Formbook was detected
- dwm.exe (PID: 2880)
- Firefox.exe (PID: 2488)
Changes the autorun value in the registry
- dwm.exe (PID: 2880)
SUSPICIOUS
Starts Microsoft Installer
- explorer.exe (PID: 276)
Executed as Windows Service
- vssvc.exe (PID: 2884)
Drop ExeToMSI Application
- msiexec.exe (PID: 3016)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3016)
- MSID6DE.tmp (PID: 3868)
Creates files in the user directory
- MSID6DE.tmp (PID: 3868)
- dwm.exe (PID: 2880)
Executed via COM
- DrvInst.exe (PID: 4000)
Starts CMD.EXE for commands execution
- dwm.exe (PID: 2880)
Loads DLL from Mozilla Firefox
- dwm.exe (PID: 2880)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 2884)
Searches for installed software
- msiexec.exe (PID: 3016)
Application was dropped or rewritten from another process
- MSID6DE.tmp (PID: 3868)
- MSID6DE.tmp (PID: 3828)
Application launched itself
- MSID6DE.tmp (PID: 3868)
Starts application with an unusual extension
- msiexec.exe (PID: 3016)
- MSID6DE.tmp (PID: 3868)
Manual execution by user
- dwm.exe (PID: 2880)
Creates files in the user directory
- Firefox.exe (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| LastPrinted: | 2012:09:21 09:56:09 |
| CreateDate: | 2012:09:21 09:56:09 |
| Software: | Windows Installer |
| Title: | Exe to msi converter free |
| Subject: | - |
| Author: | www.exetomsi.com |
| Keywords: | - |
| Comments: | - |
| Template: | ;0 |
| LastModifiedBy: | devuser |
| RevisionNumber: | {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E} |
| ModifyDate: | 2013:05:21 11:56:44 |
| Pages: | 100 |
| Words: | - |
| Security: | None |
Total processes
47
Monitored processes
11
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2072 | /c del "C:\Windows\Installer\MSID6DE.tmp" | C:\Windows\System32\cmd.exe | — | dwm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | dwm.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2880 | "C:\Windows\System32\dwm.exe" | C:\Windows\System32\dwm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\LYstYCepRBfmlj" /XML "C:\Users\admin\AppData\Local\Temp\tmpACF9.tmp" | C:\Windows\System32\schtasks.exe | MSID6DE.tmp | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3016 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\fb.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3828 | "C:\Windows\Installer\MSID6DE.tmp" | C:\Windows\Installer\MSID6DE.tmp | MSID6DE.tmp | ||||||||||||
User: SYSTEM Company: AntGames Integrity Level: SYSTEM Description: GameEnumerations Exit code: 0 Version: 1.4.9.9 Modules
| |||||||||||||||
| 3868 | "C:\Windows\Installer\MSID6DE.tmp" | C:\Windows\Installer\MSID6DE.tmp | msiexec.exe | ||||||||||||
User: admin Company: AntGames Integrity Level: MEDIUM Description: GameEnumerations Exit code: 0 Version: 1.4.9.9 Modules
| |||||||||||||||
Total events
552
Read events
371
Write events
169
Delete events
12
Modification events
| (PID) Process: | (3016) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000002A158609685BD501C80B0000780A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3016) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000002A158609685BD501C80B0000780A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3016) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 24 | |||
| (PID) Process: | (3016) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 400000000000000086AEE009685BD501C80B0000780A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3016) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000094D5E709685BD501C80B00003C090000E8030000010000000000000000000000B3B5EFEDF8E67941A5FD9C11FDDC7A5C0000000000000000 | |||
| (PID) Process: | (2884) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000FC5EF109685BD501440B0000A8090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2884) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000FC5EF109685BD501440B0000980D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2884) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000FC5EF109685BD501440B0000A0090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2884) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000FC5EF109685BD501440B0000900D0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2884) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000000A86F809685BD501440B0000900D0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
3
Suspicious files
79
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3016 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3016 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFE2AE87C39E87538F.TMP | — | |
MD5:— | SHA256:— | |||
| 2884 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 3016 | msiexec.exe | C:\Config.Msi\16d103.rbs | — | |
MD5:— | SHA256:— | |||
| 3016 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF741A419413B3C1AE.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | dwm.exe | C:\Users\admin\AppData\Roaming\3LL-T4ST\3LLlogrc.ini | binary | |
MD5:— | SHA256:— | |||
| 3016 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 4000 | DrvInst.exe | C:\Windows\INF\setupapi.ev3 | binary | |
MD5:— | SHA256:— | |||
| 3016 | msiexec.exe | C:\Windows\Installer\MSID5B4.tmp | binary | |
MD5:— | SHA256:— | |||
| 3868 | MSID6DE.tmp | C:\Users\admin\AppData\Local\Temp\tmpACF9.tmp | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
21
DNS requests
17
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
276 | explorer.exe | GET | — | 162.241.244.43:80 | http://www.nerdyheat.com/h313/?GV=rhl562GZV4GYctQL/y/UQ4lav8+/khNaOuGyneIg+ssPiDBZOrk4Z84kH0O1MwE9BZWBXw==&uzsD=jjmPcTbp1&sql=1 | US | — | — | malicious |
276 | explorer.exe | GET | 301 | 185.230.62.177:80 | http://www.sweetreflectionsbynora.com/h313/?GV=5lsZrOhRs/lGJP7gwryuzMlKPU9myIA4i+dF9Mpk2b6PkYez4g5qSOnMuBV72JEeQ8fe0g==&uzsD=jjmPcTbp1&sql=1 | unknown | — | — | malicious |
276 | explorer.exe | GET | — | 198.54.117.211:80 | http://www.maileast.com/h313/?GV=iHDzGS4vsiXCeJ1hUwmGv8VBt6qEVu027jsQpD94RY3bqdkDfxX/6Z/yzYHVRc5RojlR2A==&uzsD=jjmPcTbp1 | US | — | — | malicious |
276 | explorer.exe | POST | — | 162.241.244.43:80 | http://www.nerdyheat.com/h313/ | US | — | — | malicious |
276 | explorer.exe | POST | — | 185.230.62.177:80 | http://www.sweetreflectionsbynora.com/h313/ | unknown | — | — | malicious |
276 | explorer.exe | POST | — | 185.230.62.177:80 | http://www.sweetreflectionsbynora.com/h313/ | unknown | — | — | malicious |
276 | explorer.exe | POST | — | 185.230.62.177:80 | http://www.sweetreflectionsbynora.com/h313/ | unknown | — | — | malicious |
276 | explorer.exe | GET | 404 | 192.64.115.228:80 | http://www.menflax.com/h313/?GV=nx2oDViZMR/DbYxC9/2C5wSTEmkZKq9epMgAiP4sotqWRUm3hmi2dLU6MELqOqgvknDAuw==&uzsD=jjmPcTbp1 | US | html | 328 b | malicious |
276 | explorer.exe | POST | — | 192.64.115.228:80 | http://www.menflax.com/h313/ | US | — | — | malicious |
276 | explorer.exe | POST | — | 198.54.117.211:80 | http://www.maileast.com/h313/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
276 | explorer.exe | 162.241.244.43:80 | www.nerdyheat.com | CyrusOne LLC | US | malicious |
276 | explorer.exe | 192.64.115.228:80 | www.menflax.com | Namecheap, Inc. | US | malicious |
276 | explorer.exe | 198.54.117.211:80 | www.maileast.com | Namecheap, Inc. | US | malicious |
276 | explorer.exe | 69.172.201.153:80 | www.helloflat.com | Dosarrest Internet Security LTD | US | malicious |
276 | explorer.exe | 13.84.162.221:80 | www.artemisirt.com | Microsoft Corporation | US | malicious |
276 | explorer.exe | 185.230.62.177:80 | www.sweetreflectionsbynora.com | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.www464567.com |
| unknown |
www.helloflat.com |
| malicious |
www.nerdyheat.com |
| malicious |
www.artemisirt.com |
| malicious |
www.sweetreflectionsbynora.com |
| malicious |
www.menflax.com |
| malicious |
www.sistema-icarai-de-radio-tv.com |
| unknown |
www.maileast.com |
| malicious |
www.llqd-stories.review |
| unknown |
www.weiduicha.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
276 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
14 ETPRO signatures available at the full report