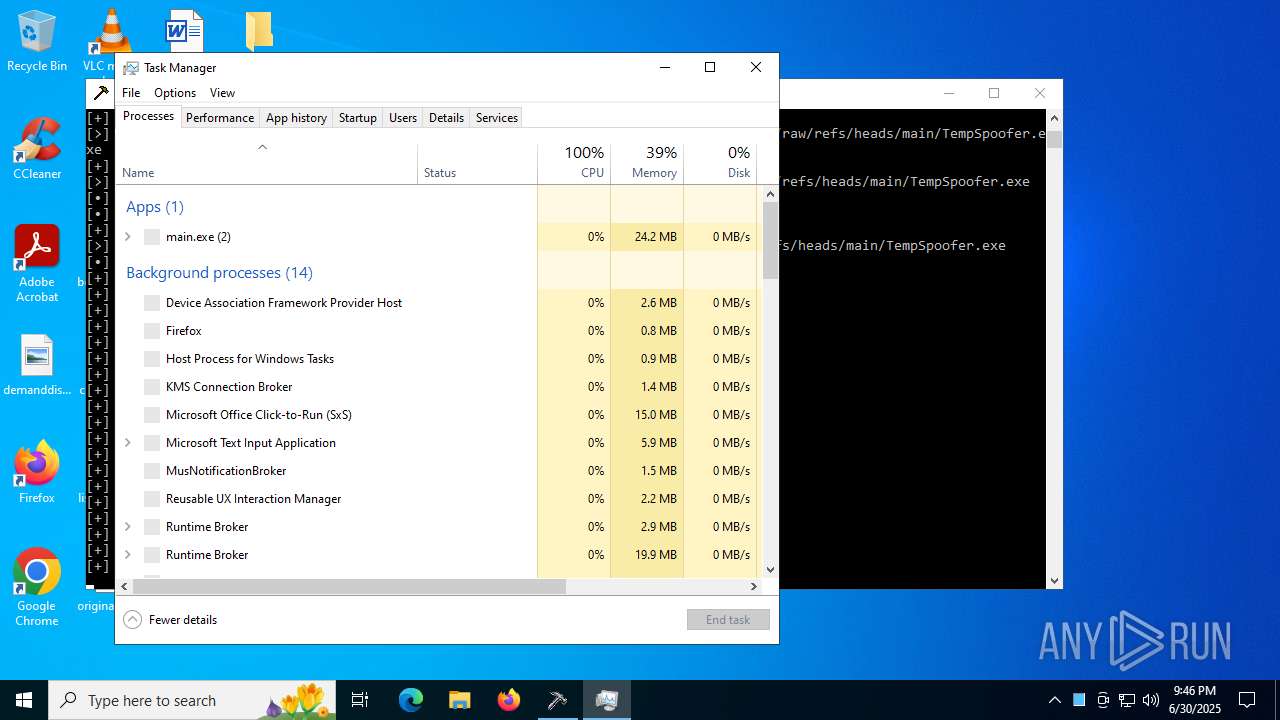
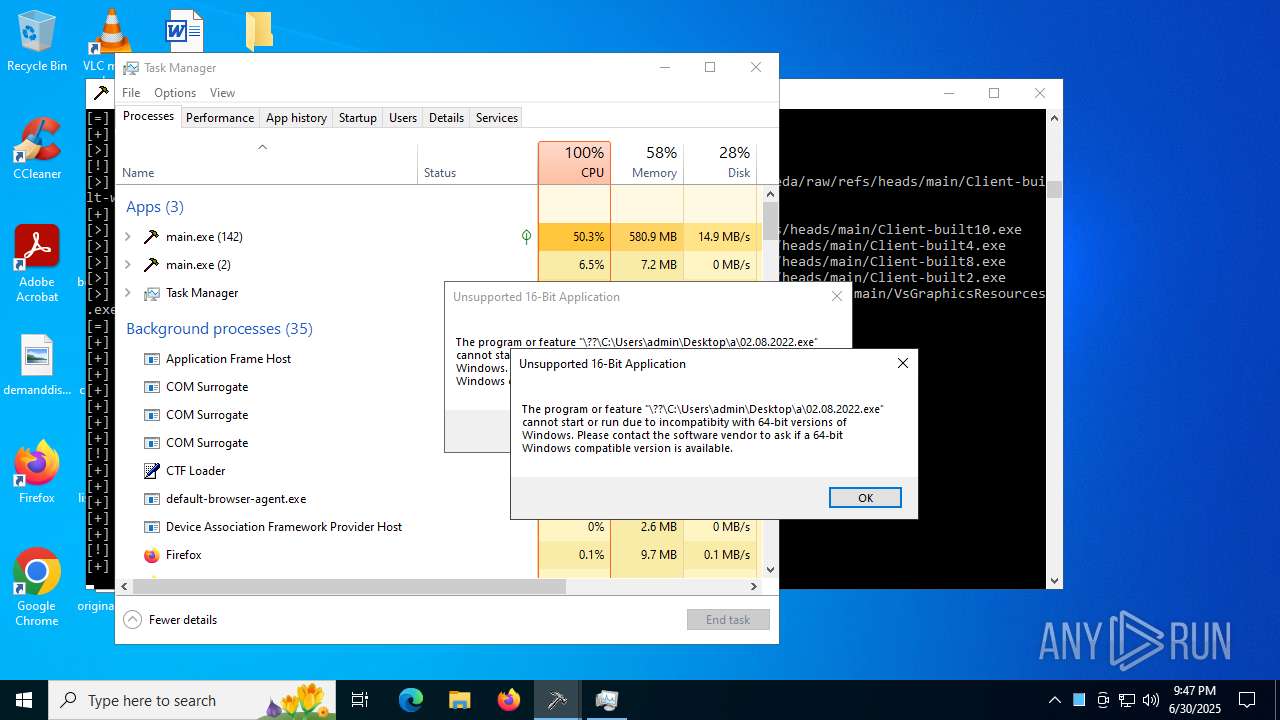
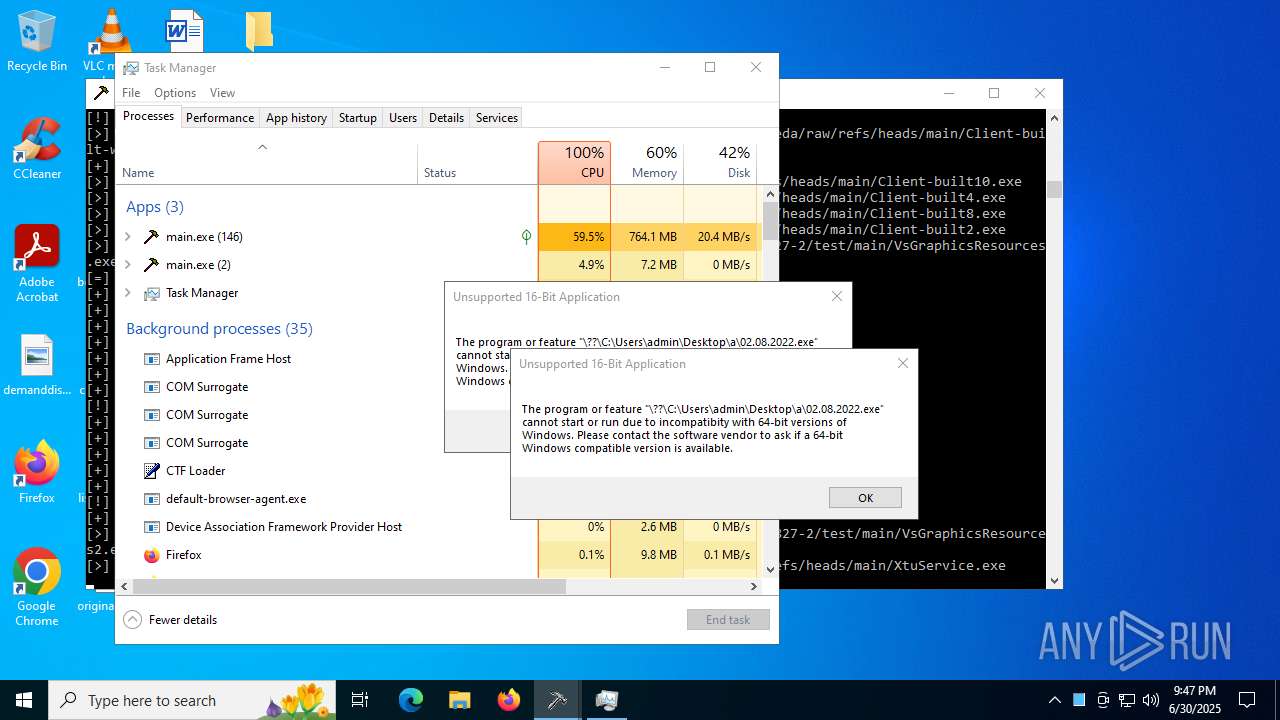
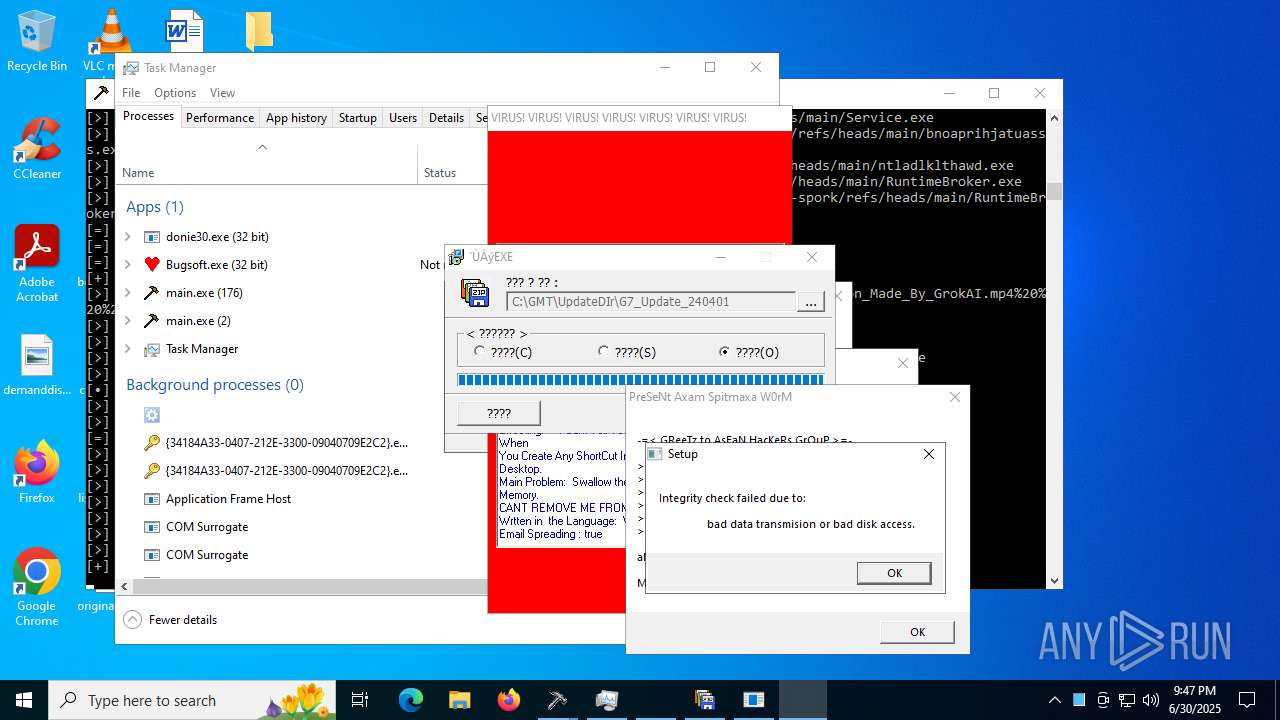
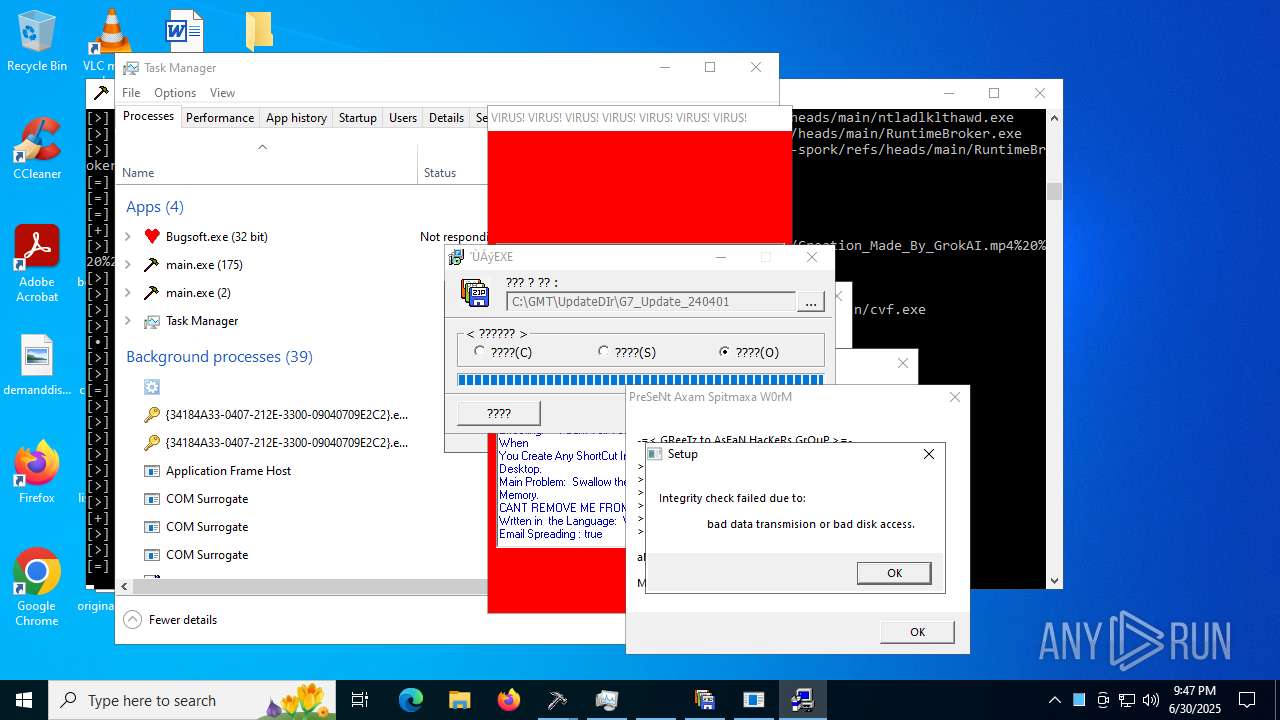
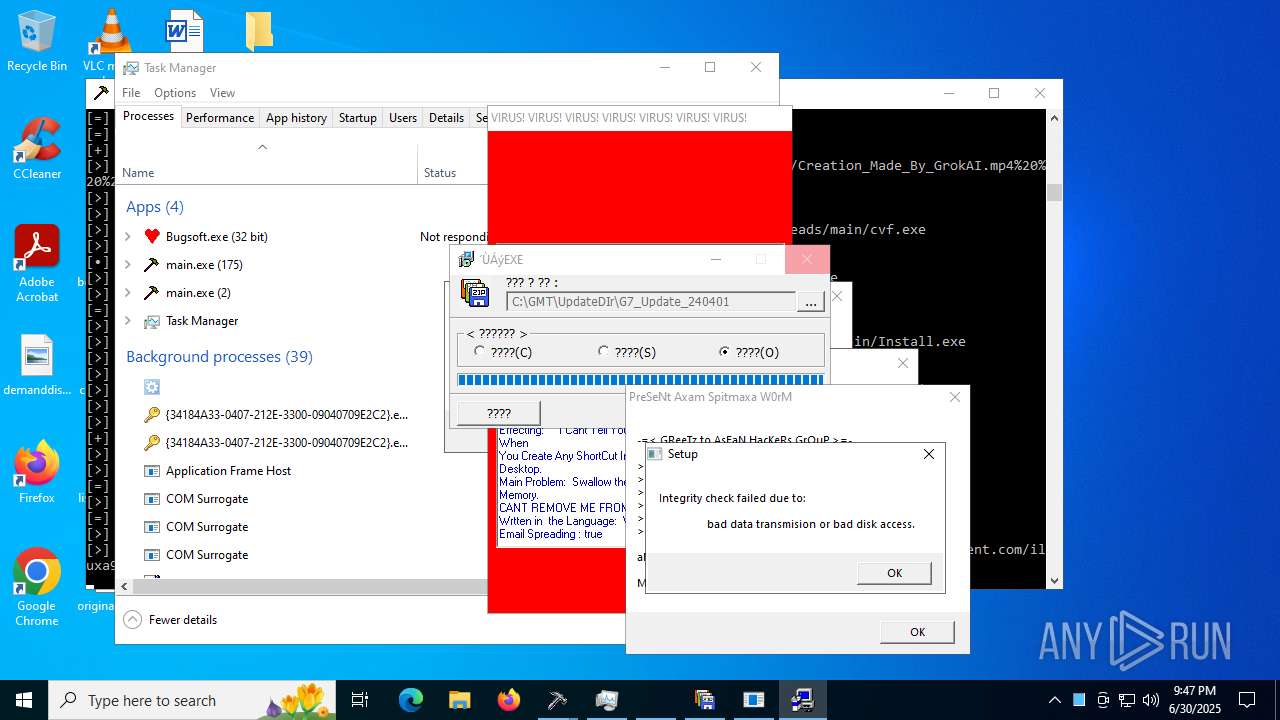
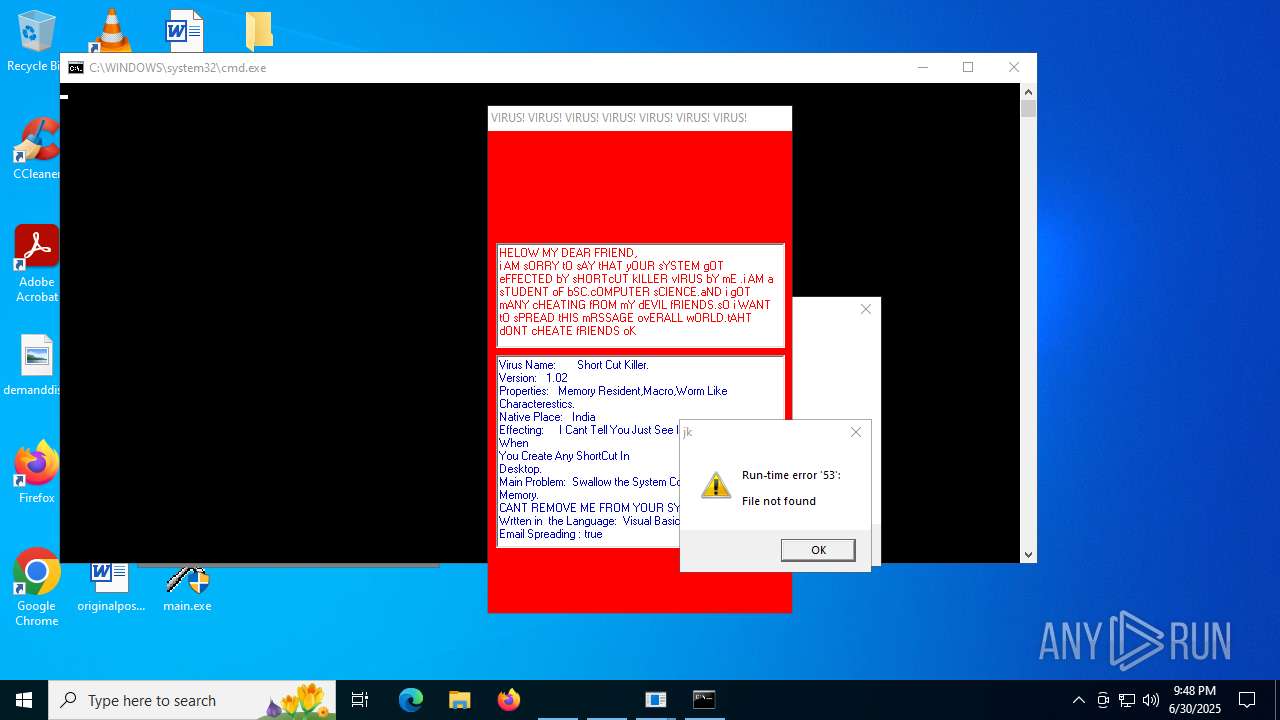
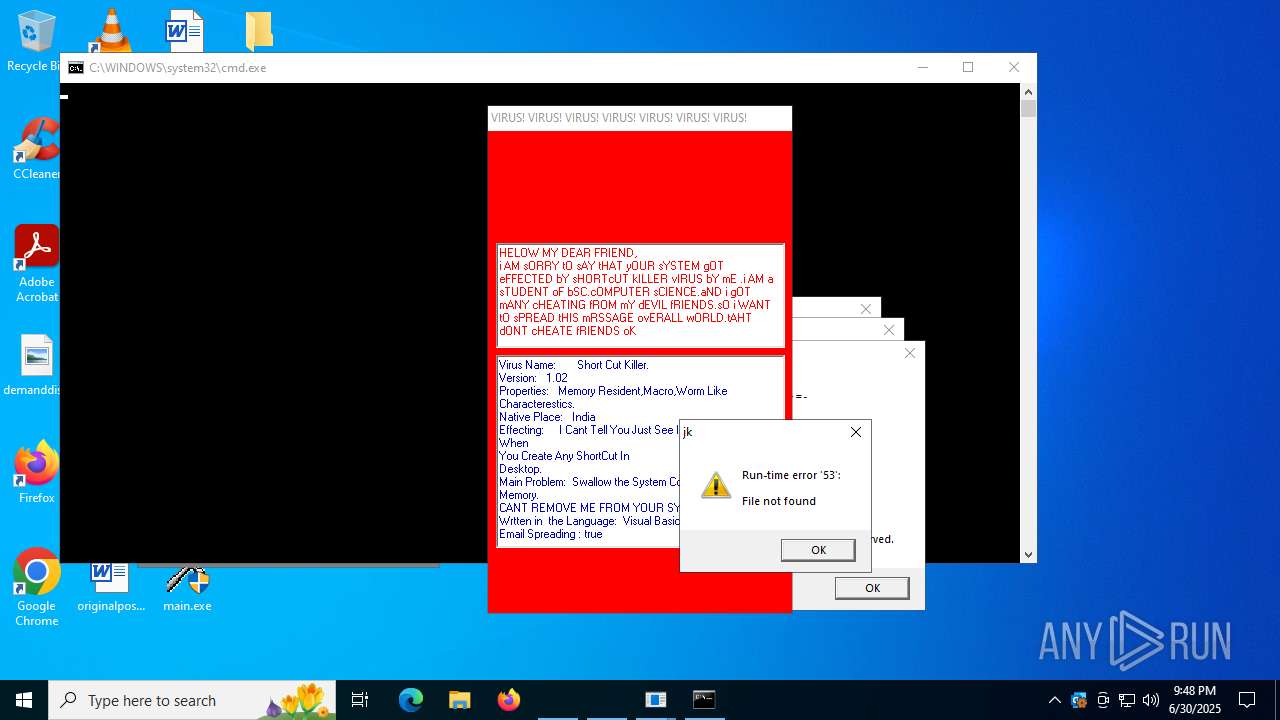
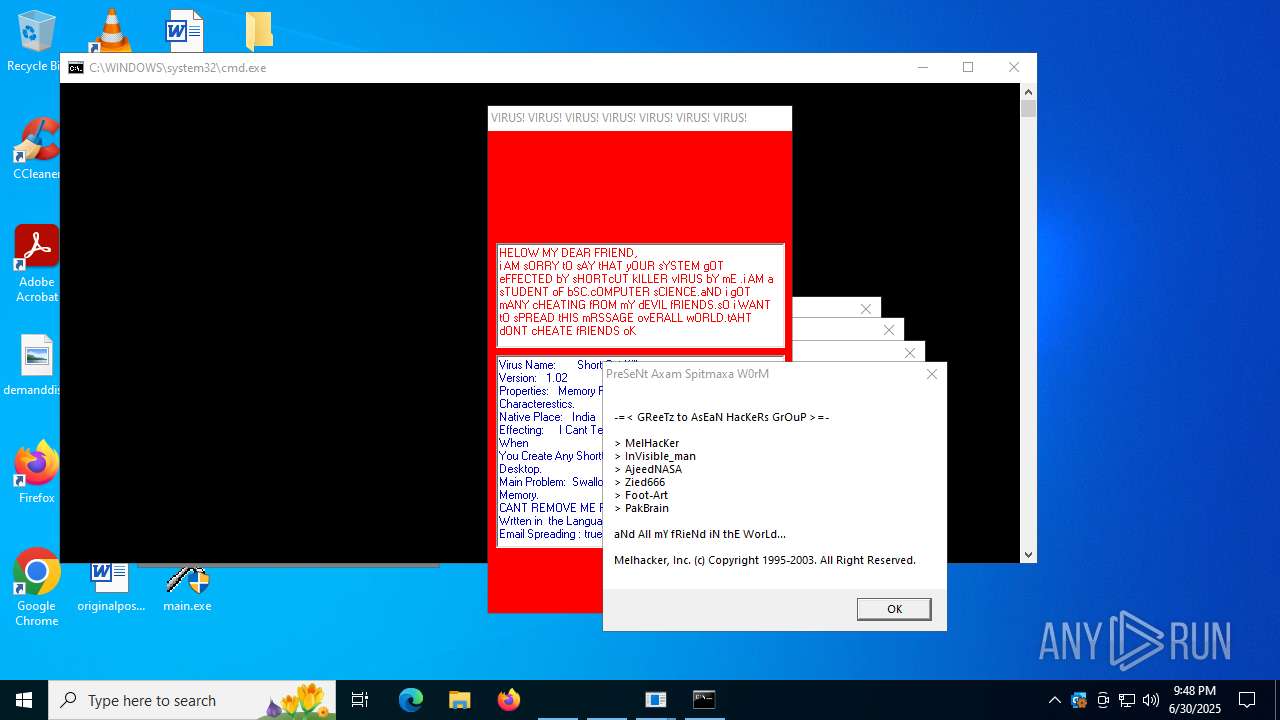
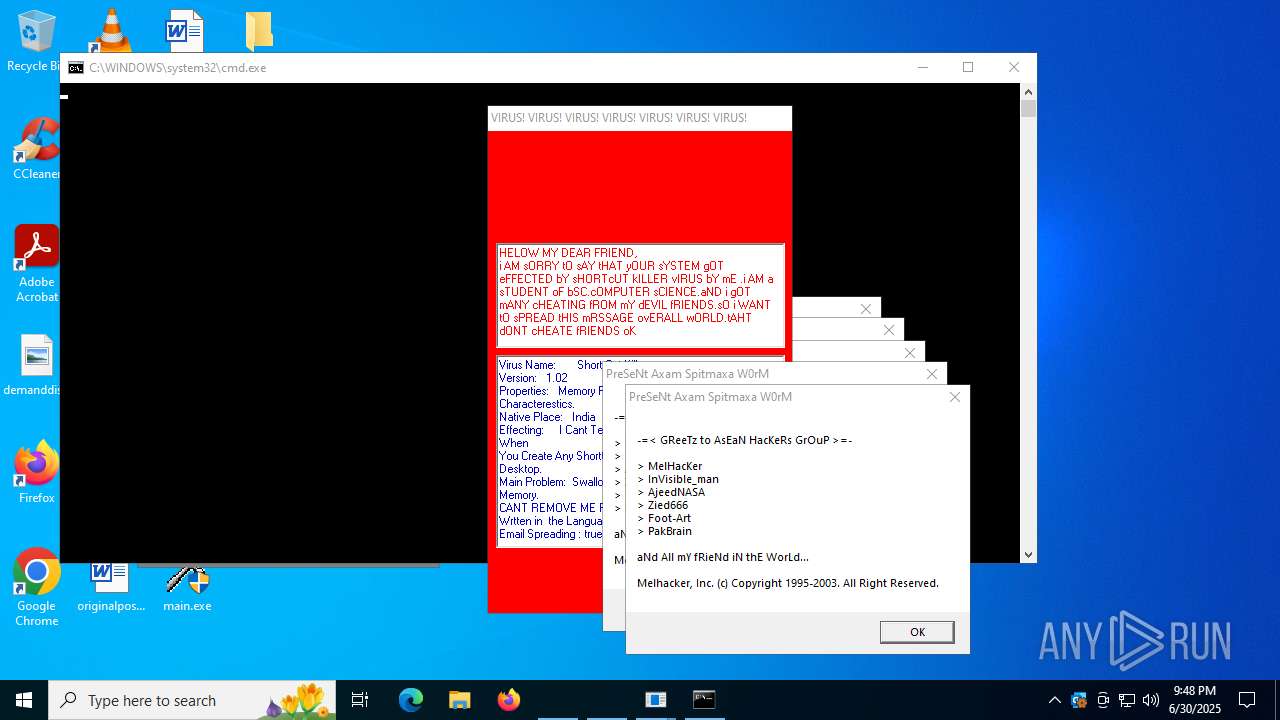
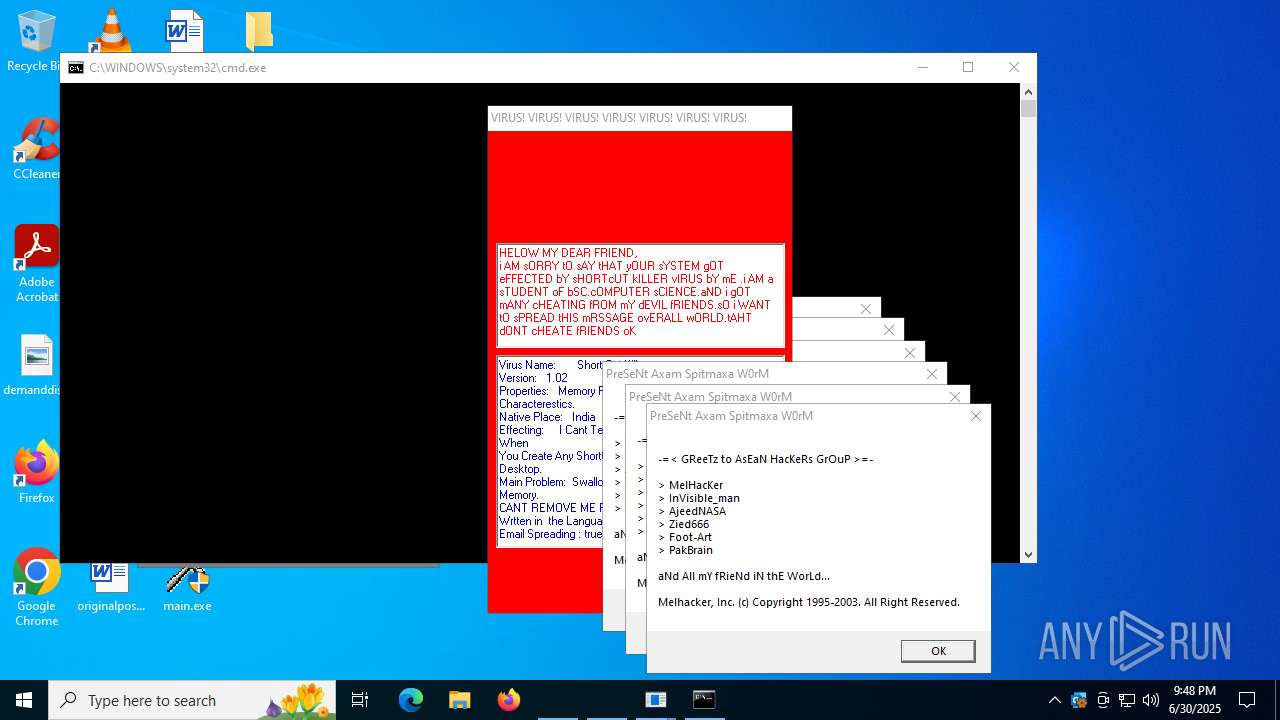
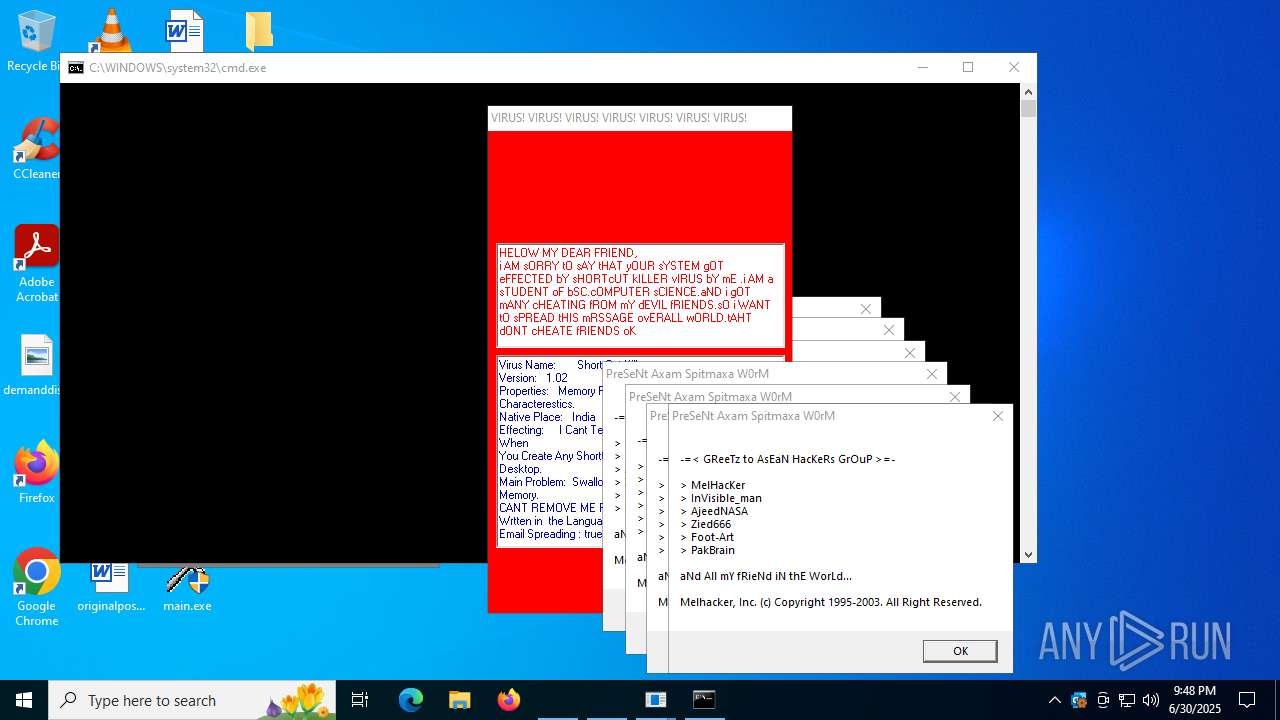
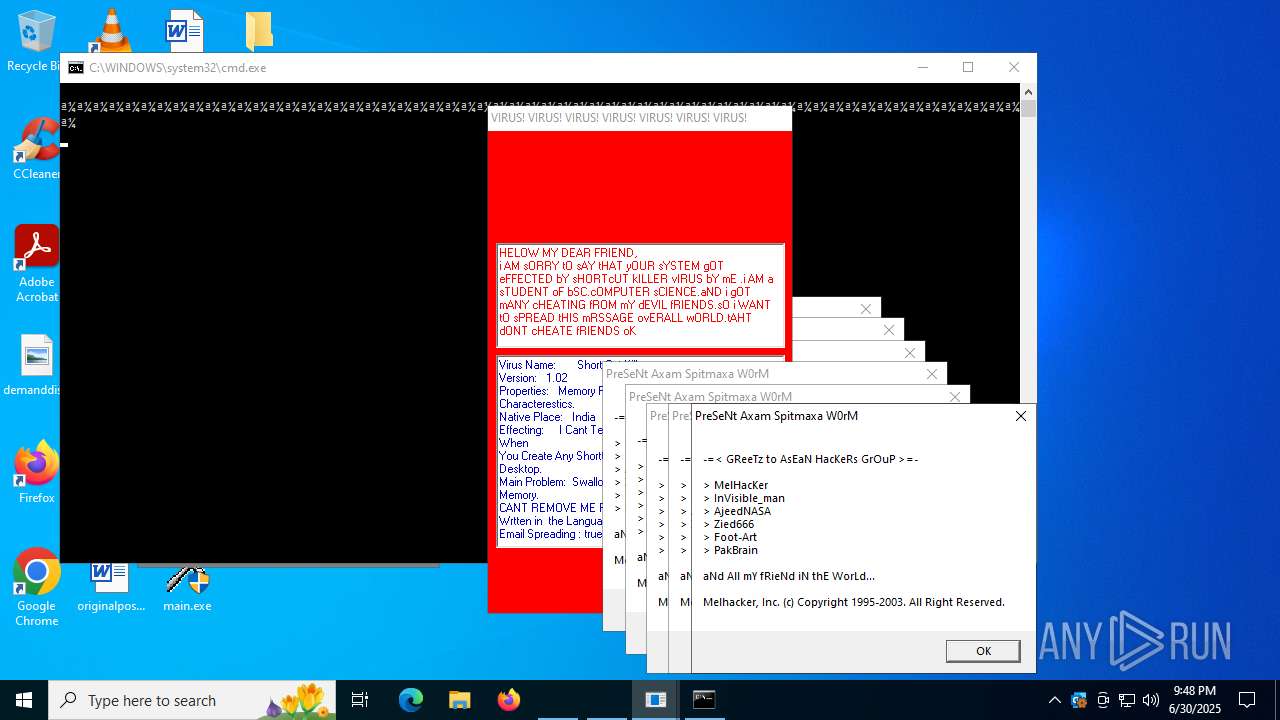
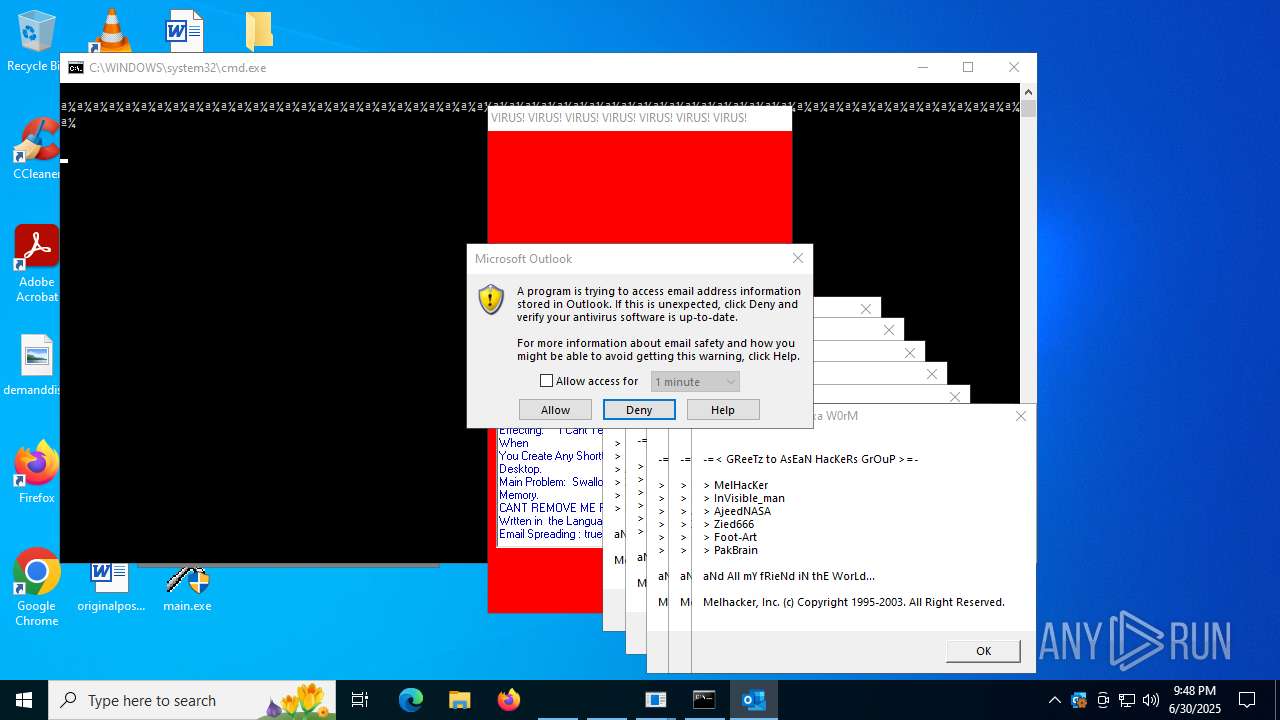
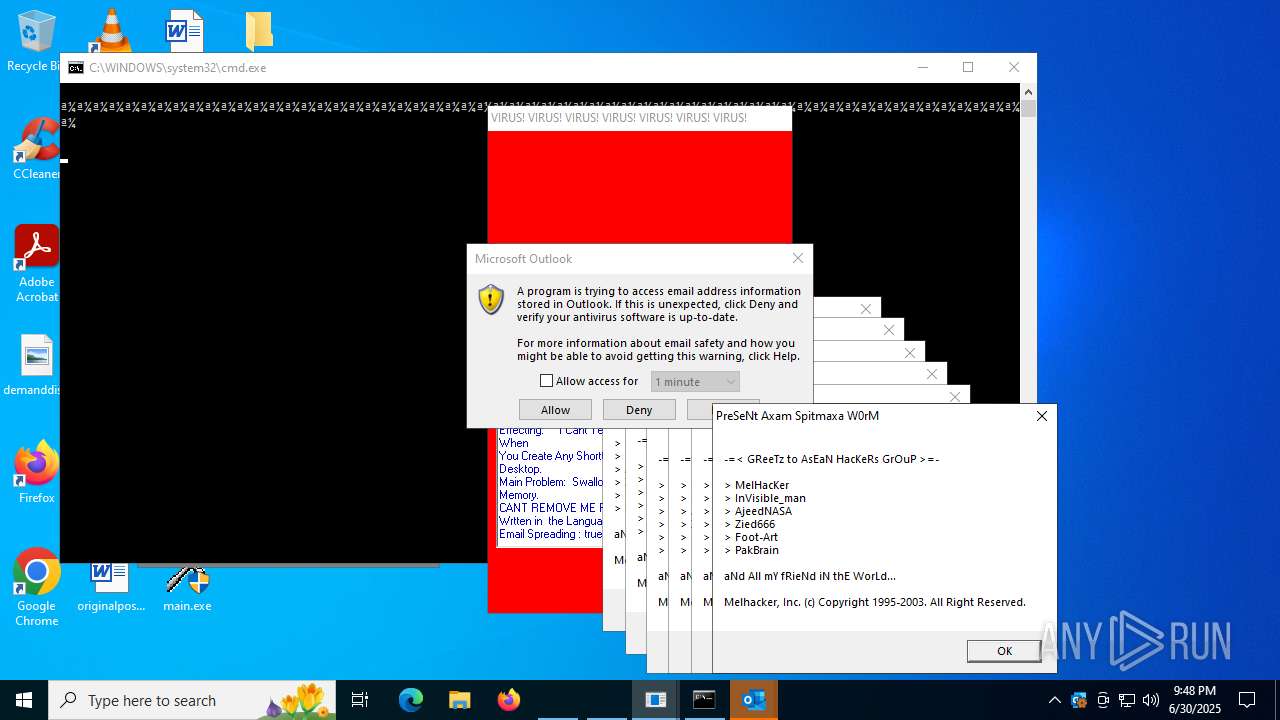
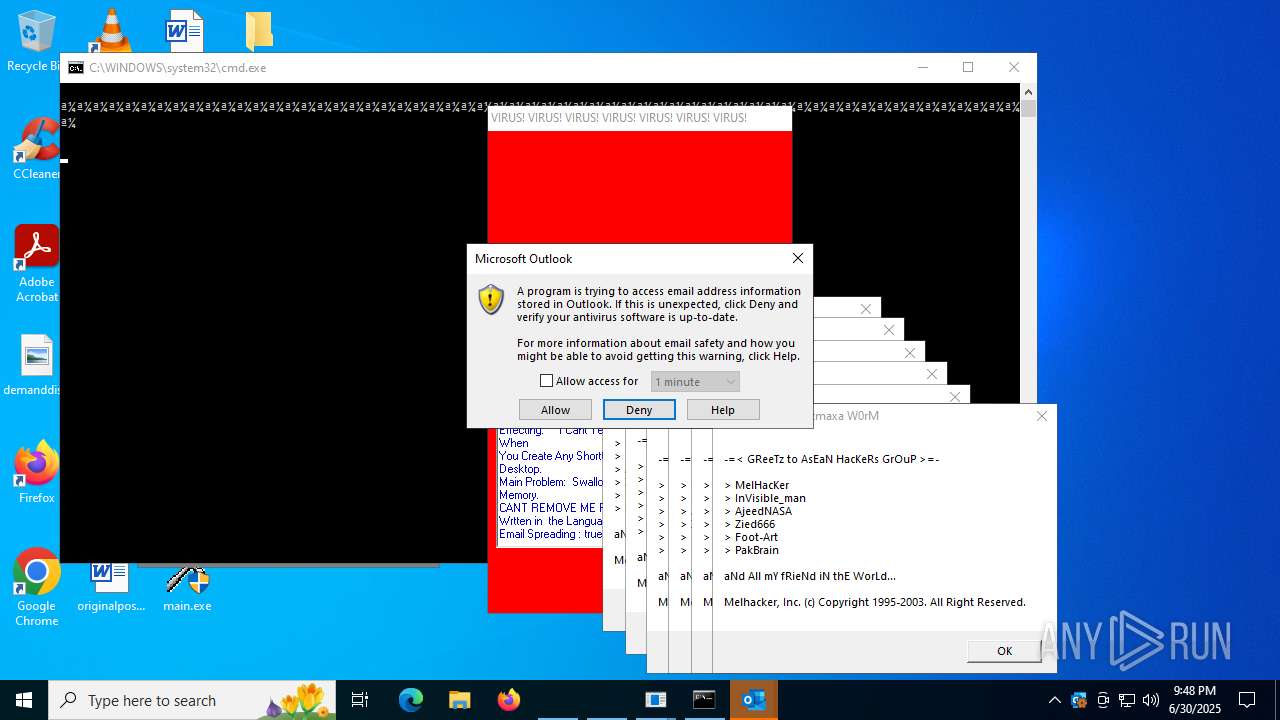
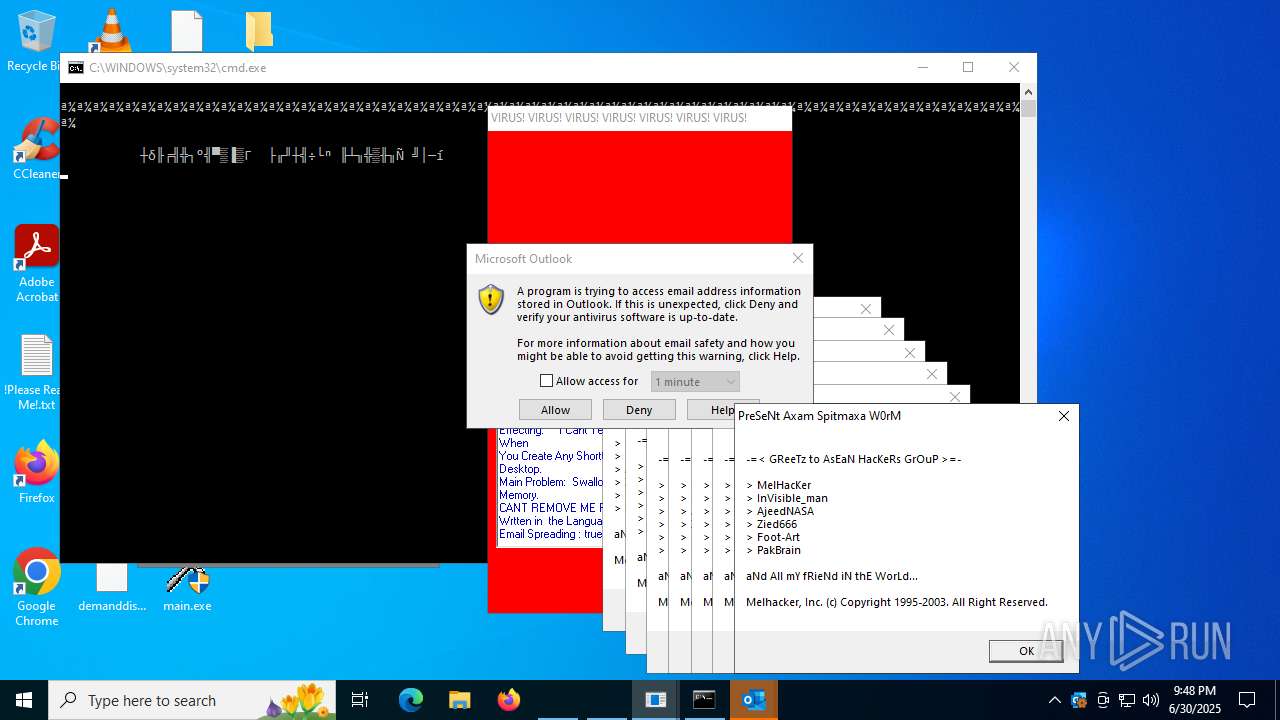
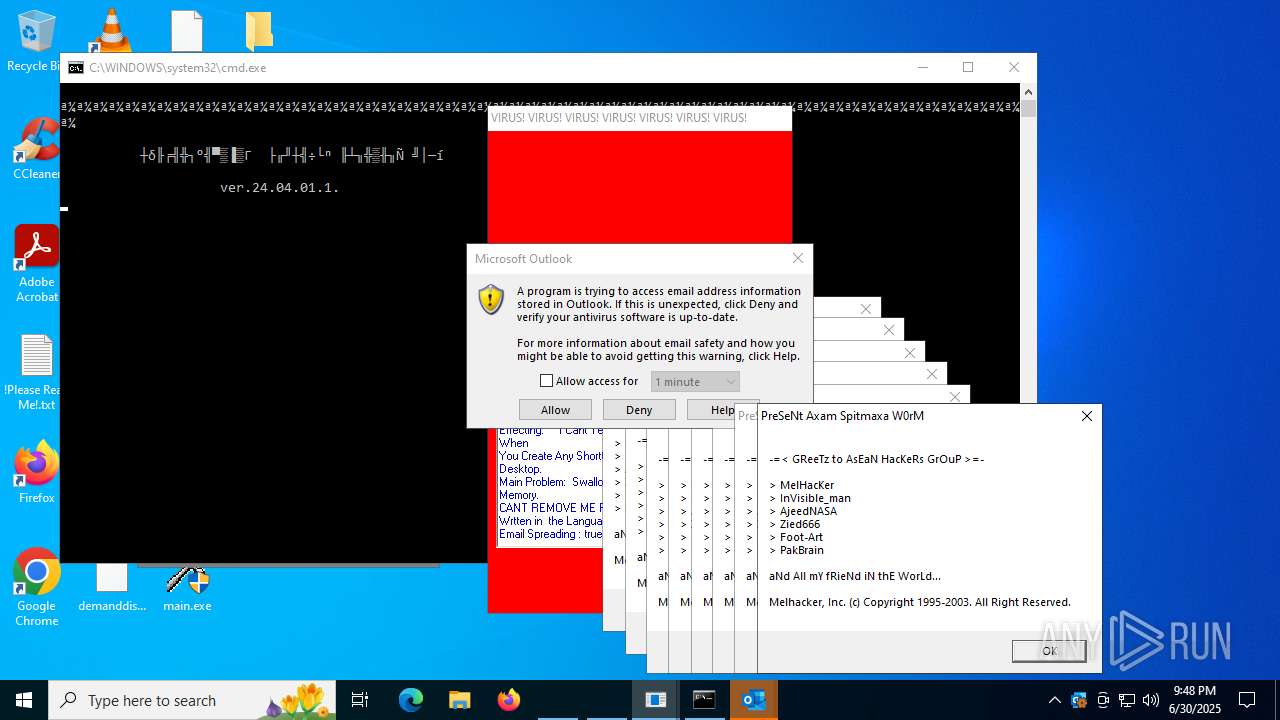
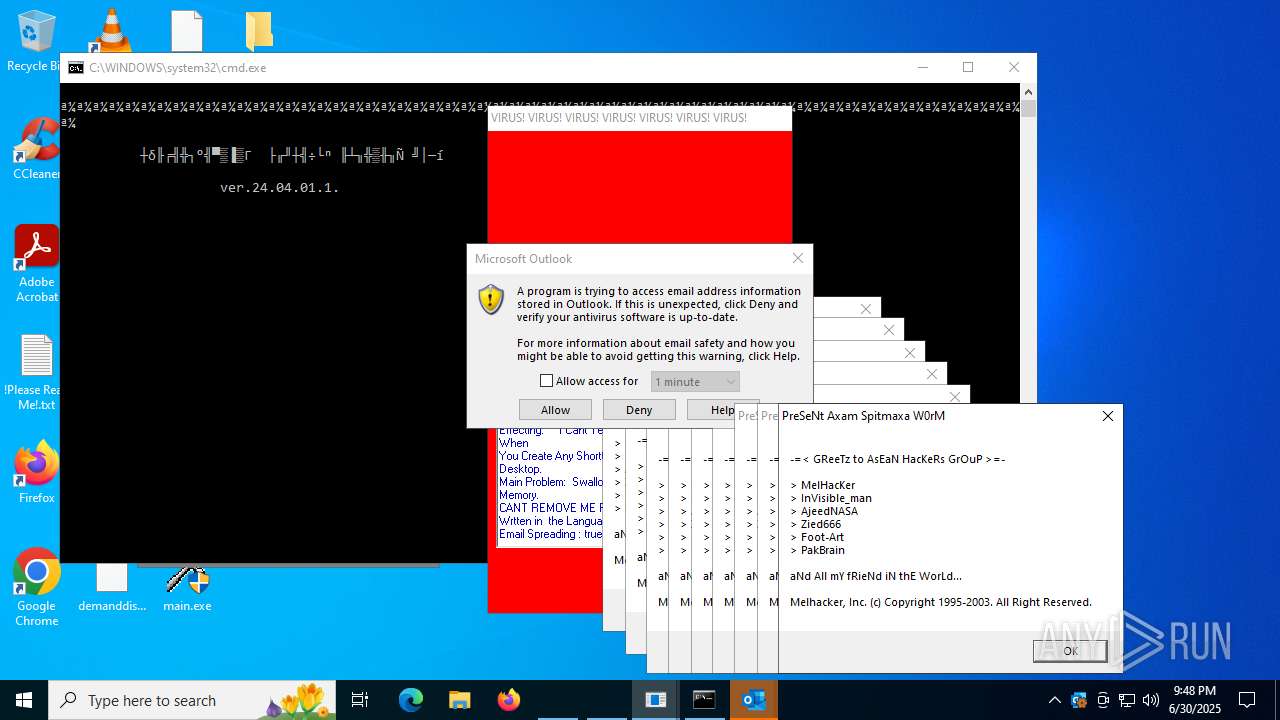
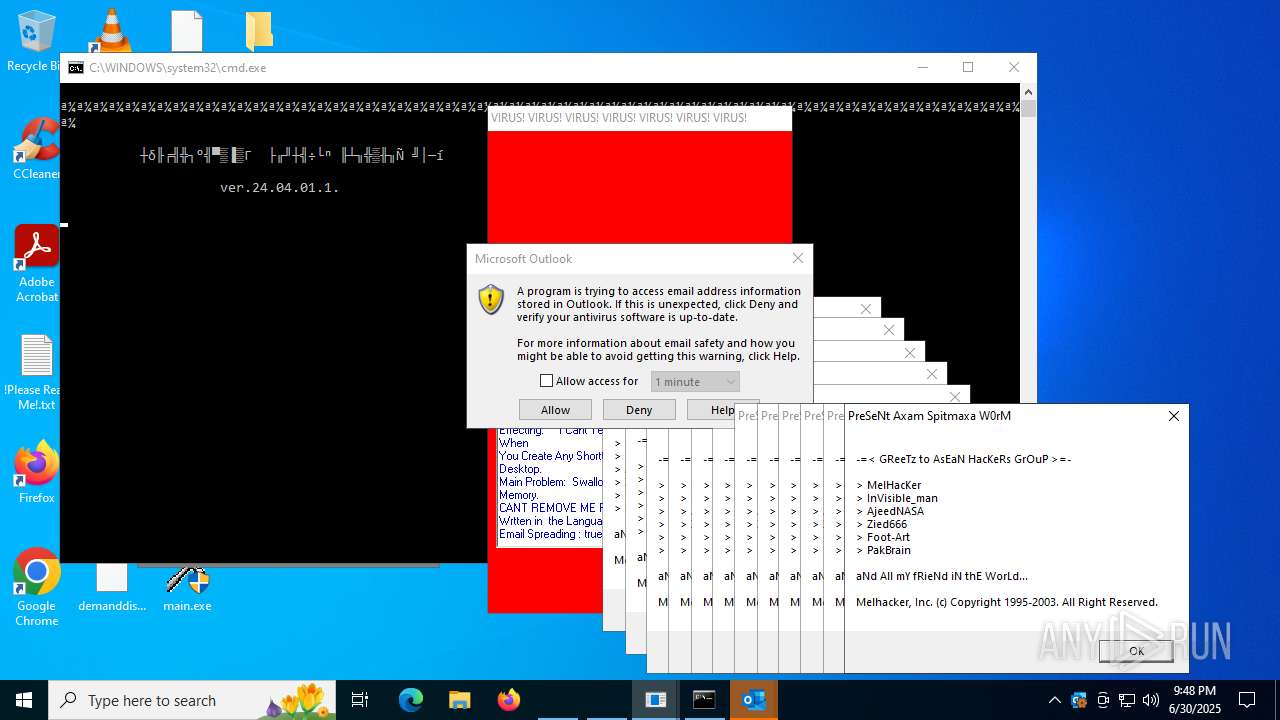
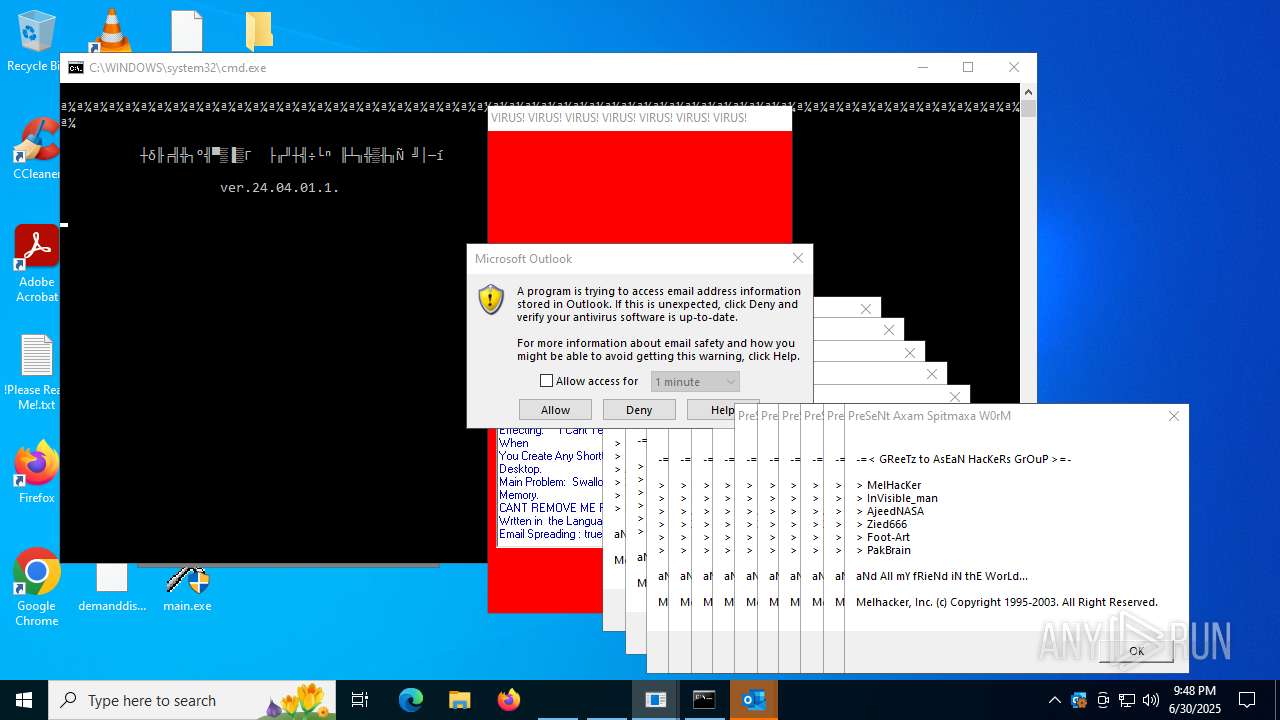
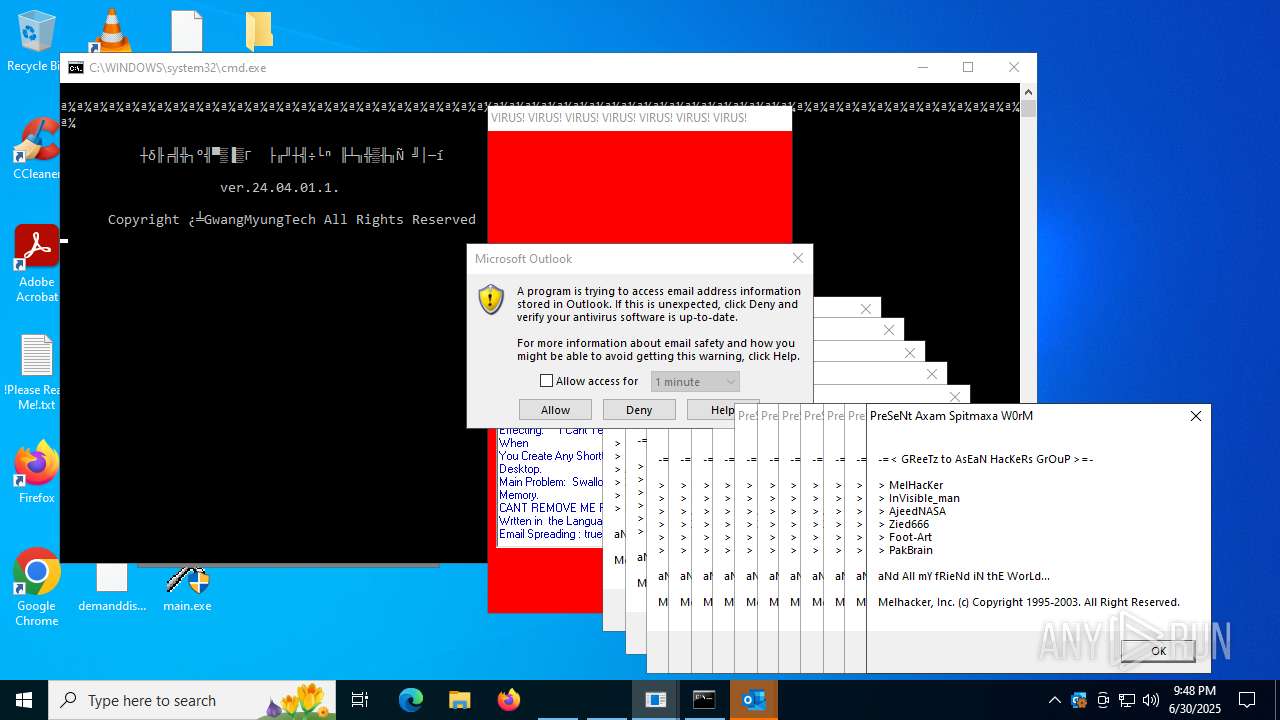
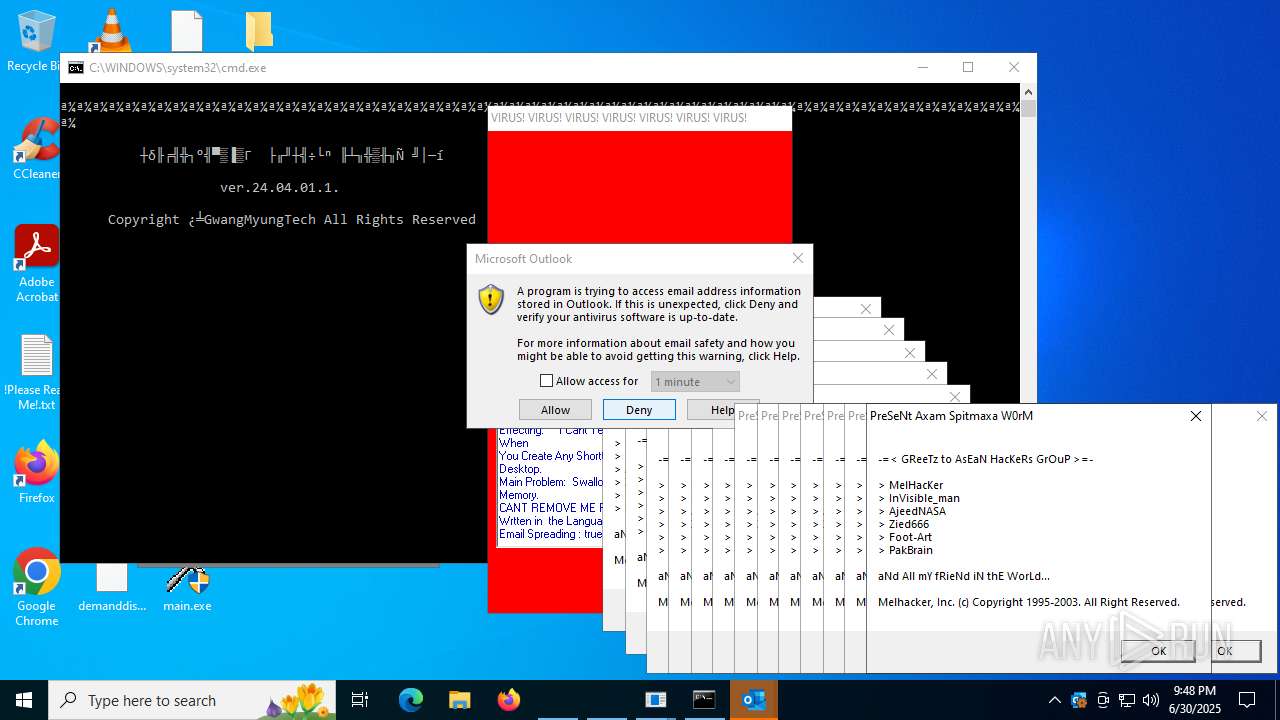
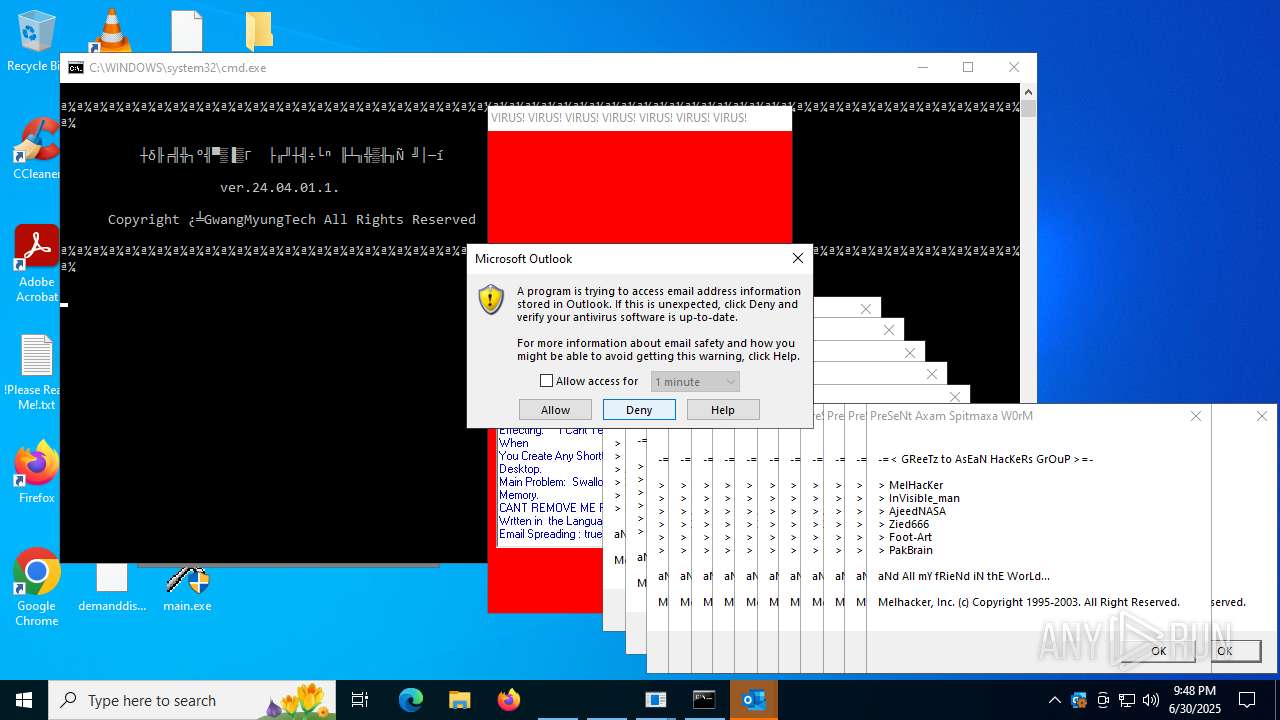
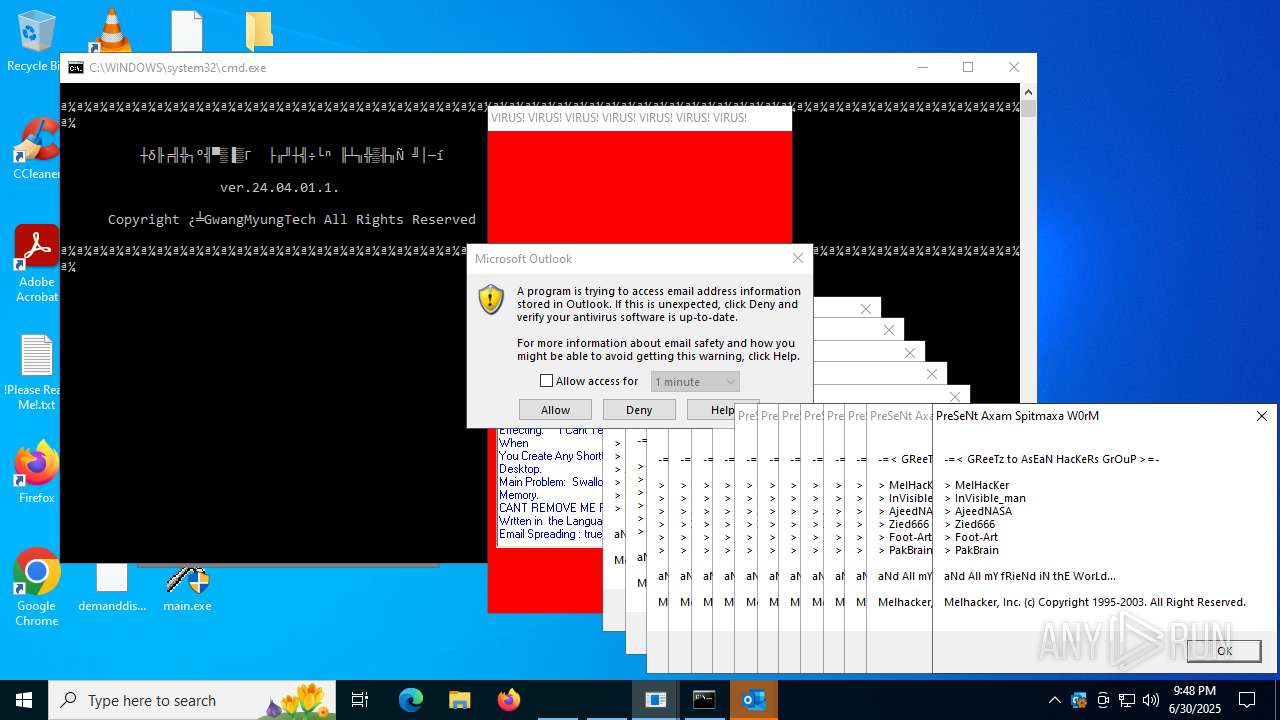
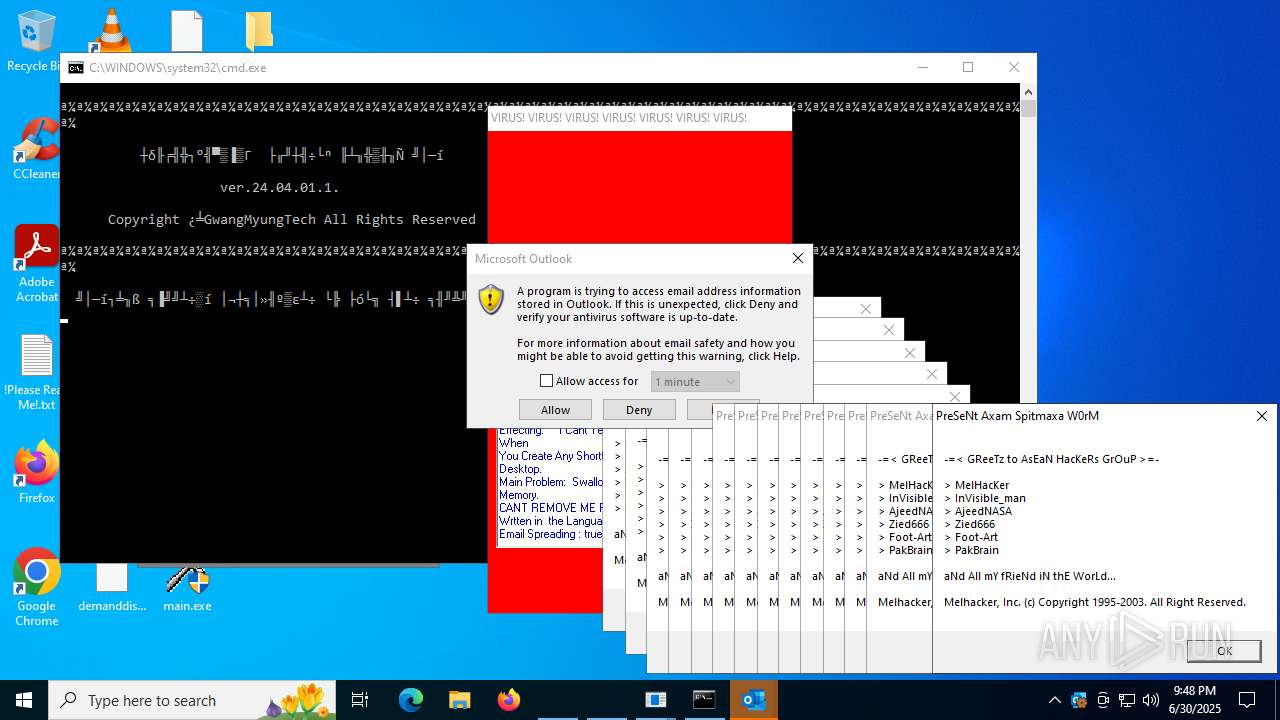
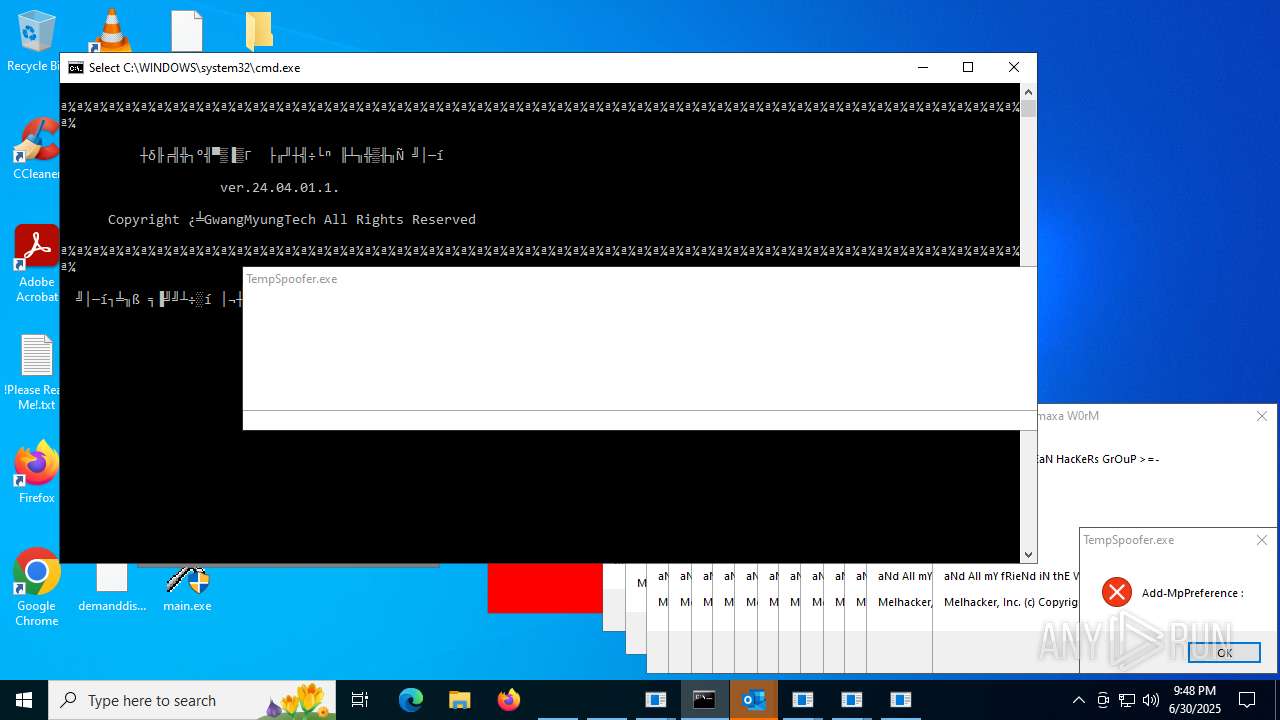
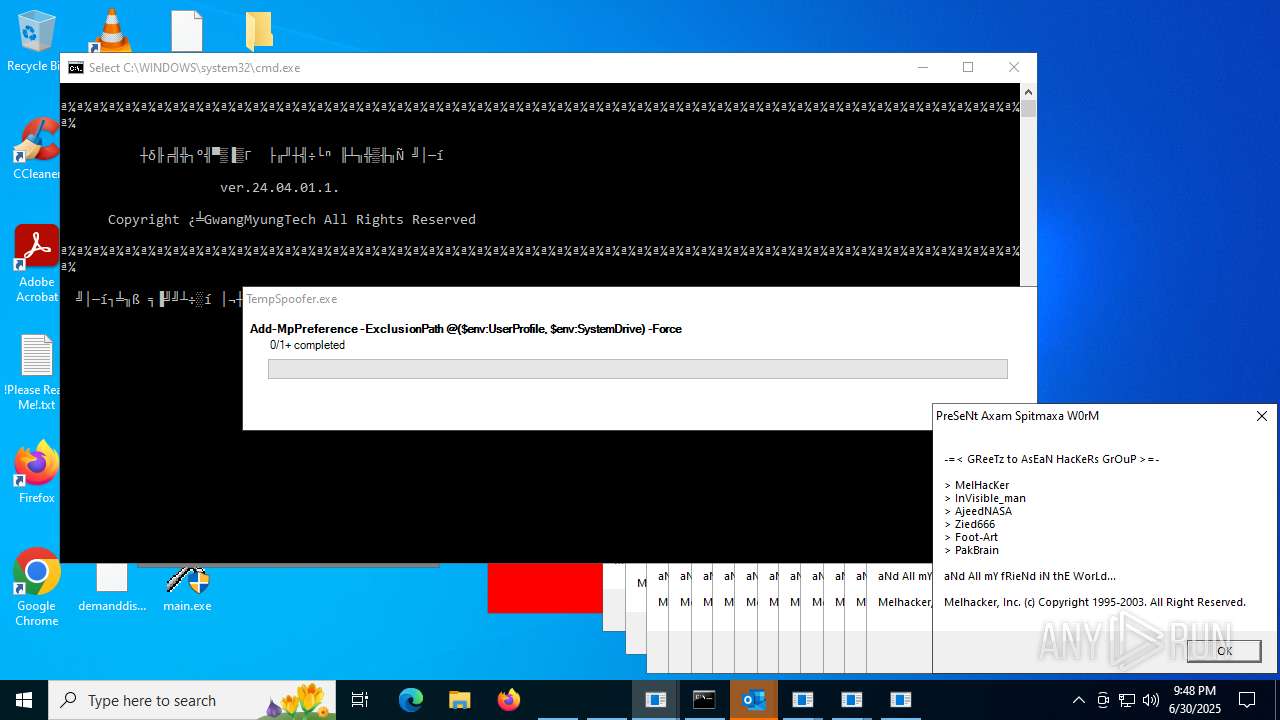
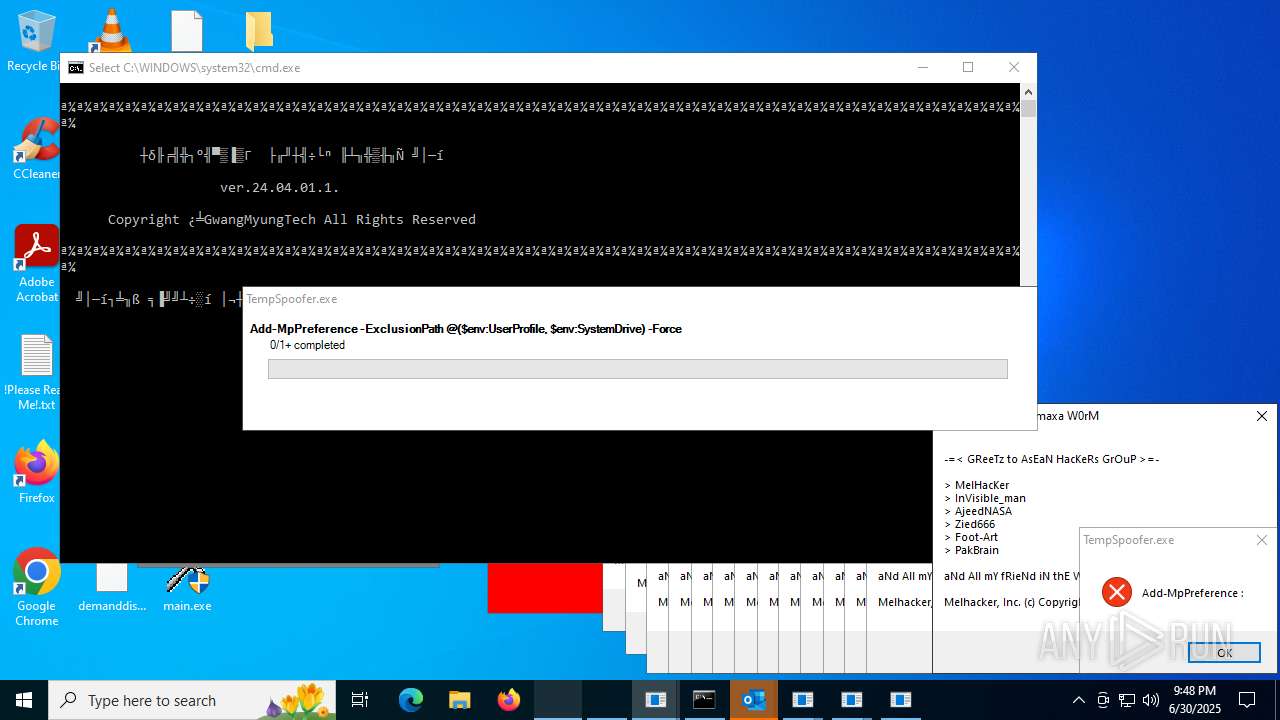
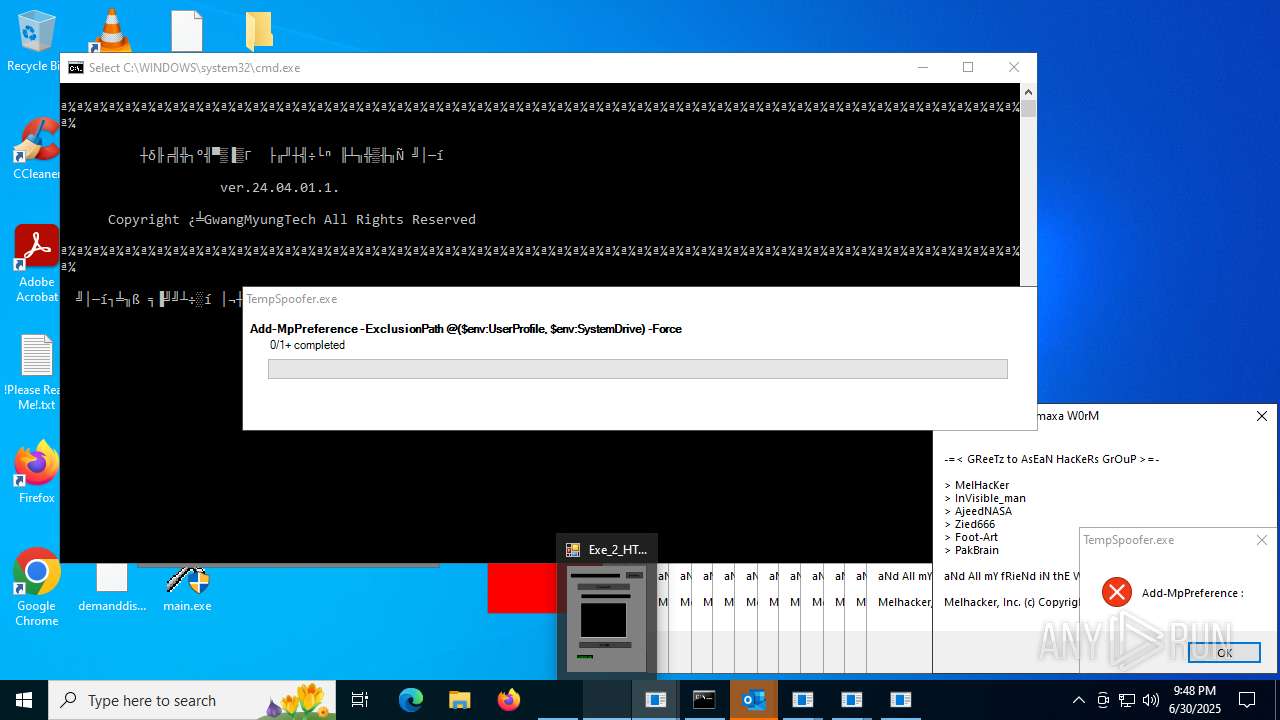
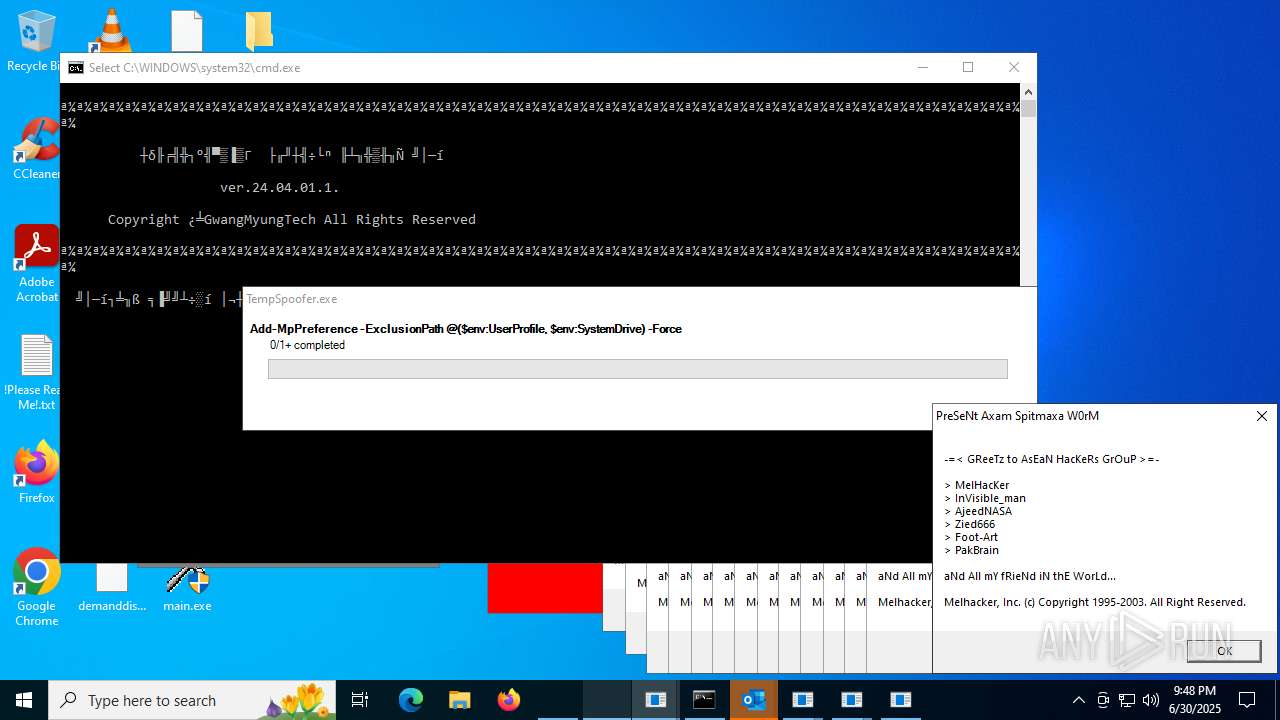
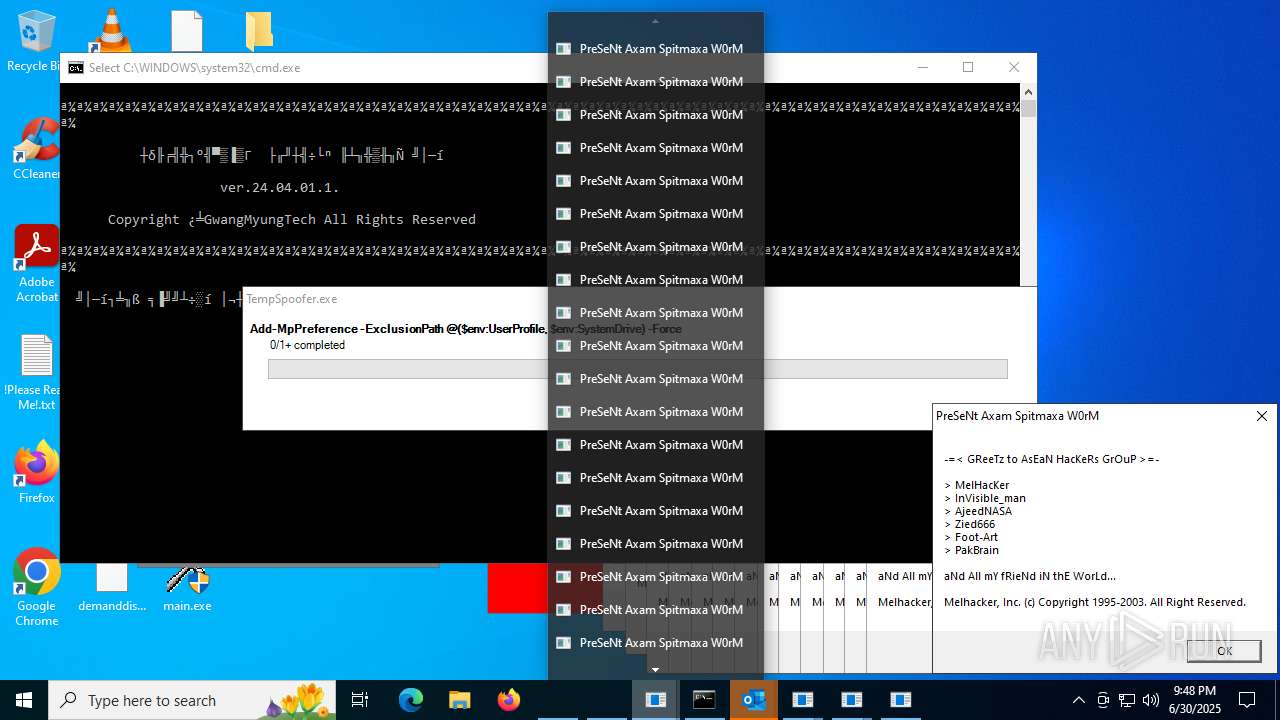
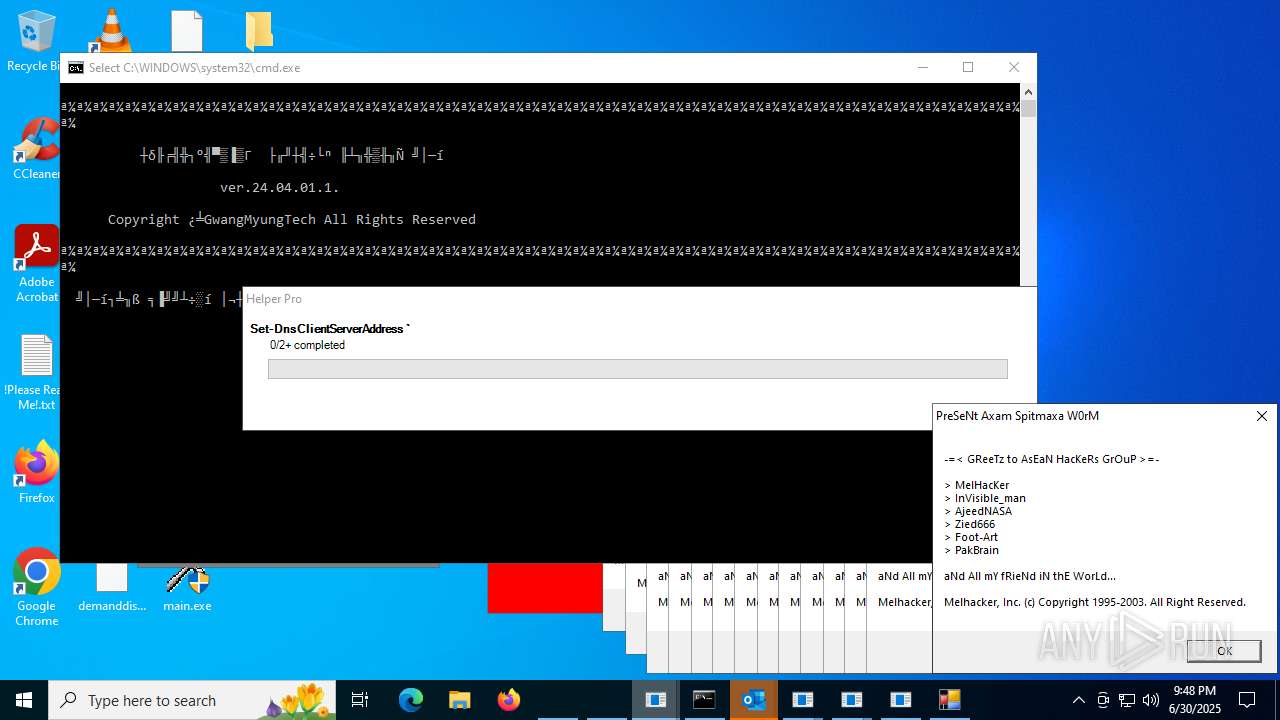
| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/51f85495-4490-4e35-9a22-d0f09eb3d539 |
| Verdict: | Malicious activity |
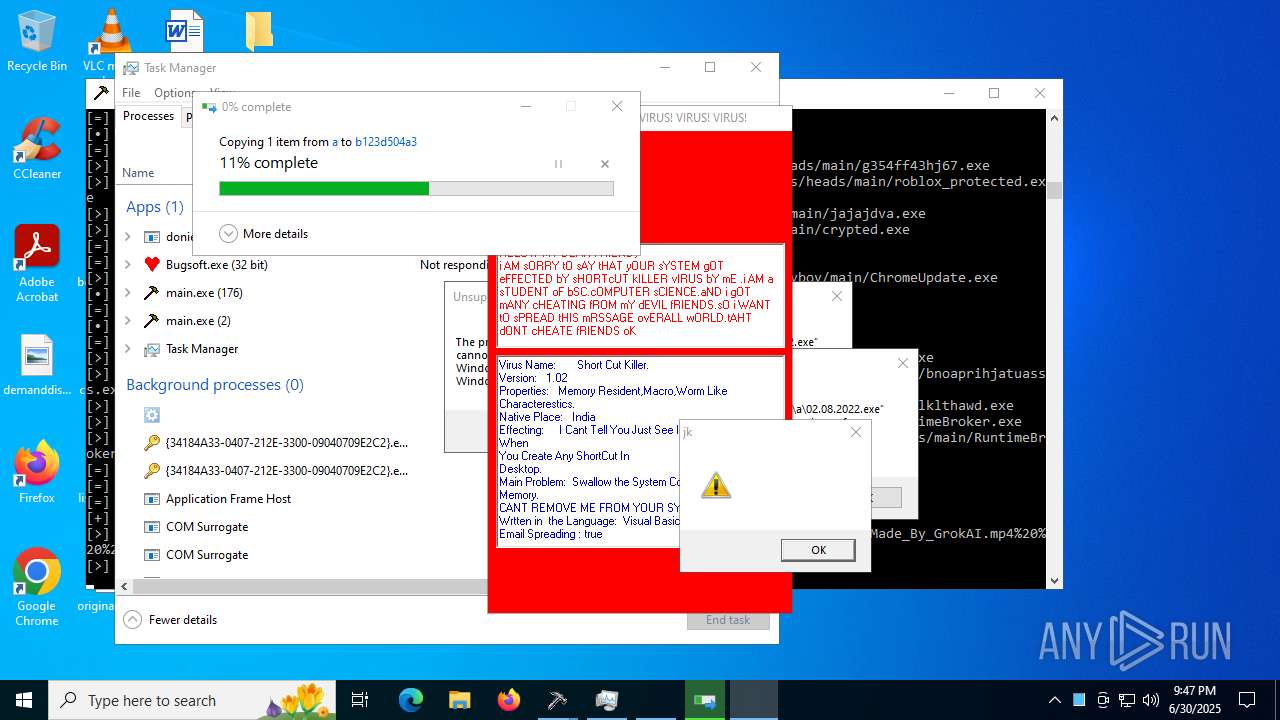
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 30, 2025, 21:46:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | C942A56638772644D847709D906FA23D |
| SHA1: | 12D6B77FEC2244CDC4050A083AA741185CC48010 |
| SHA256: | 56A28391D309102557FCF9BC34351A50B49054282F2007851DCBC4E825E7C37A |
| SSDEEP: | 98304:R/0Cg6brcfRkzKVfq7AnYRO4Y6ZhkDQet54netUjZUj0vNQLFZfQpyJoic3yjHFD:ivfkEwE1MUQ881mw02/ki+BIsG |
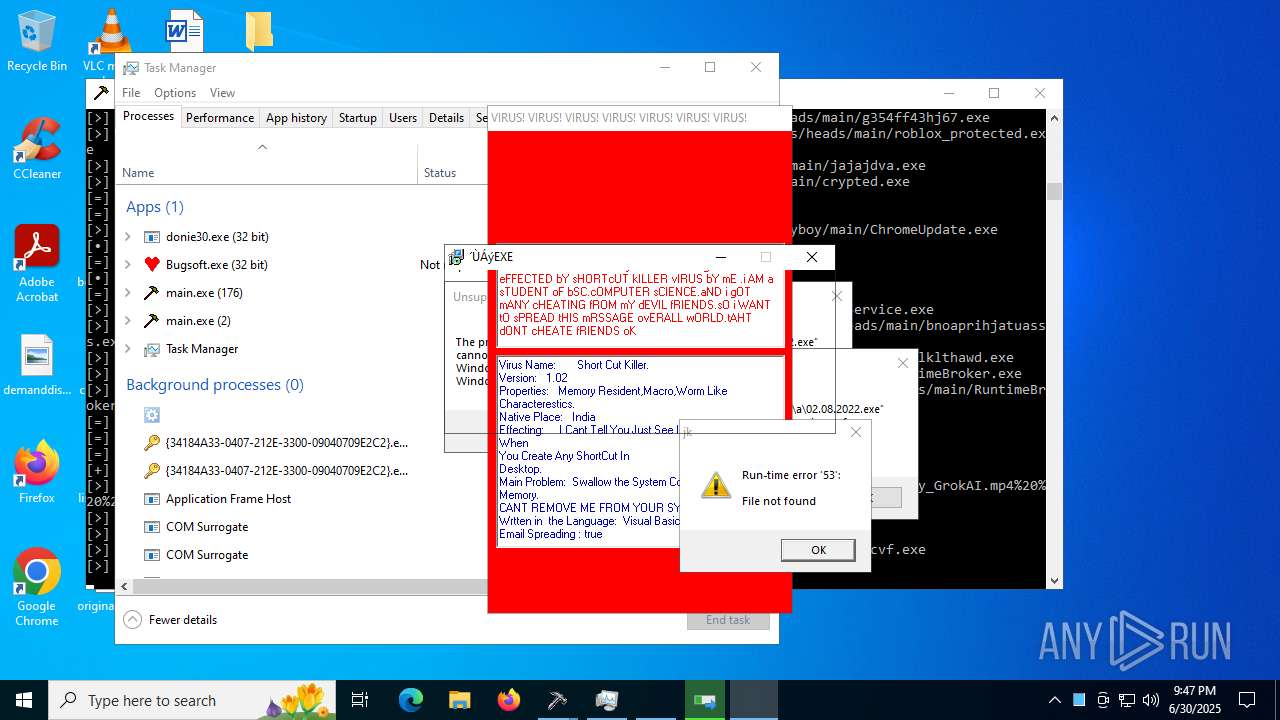
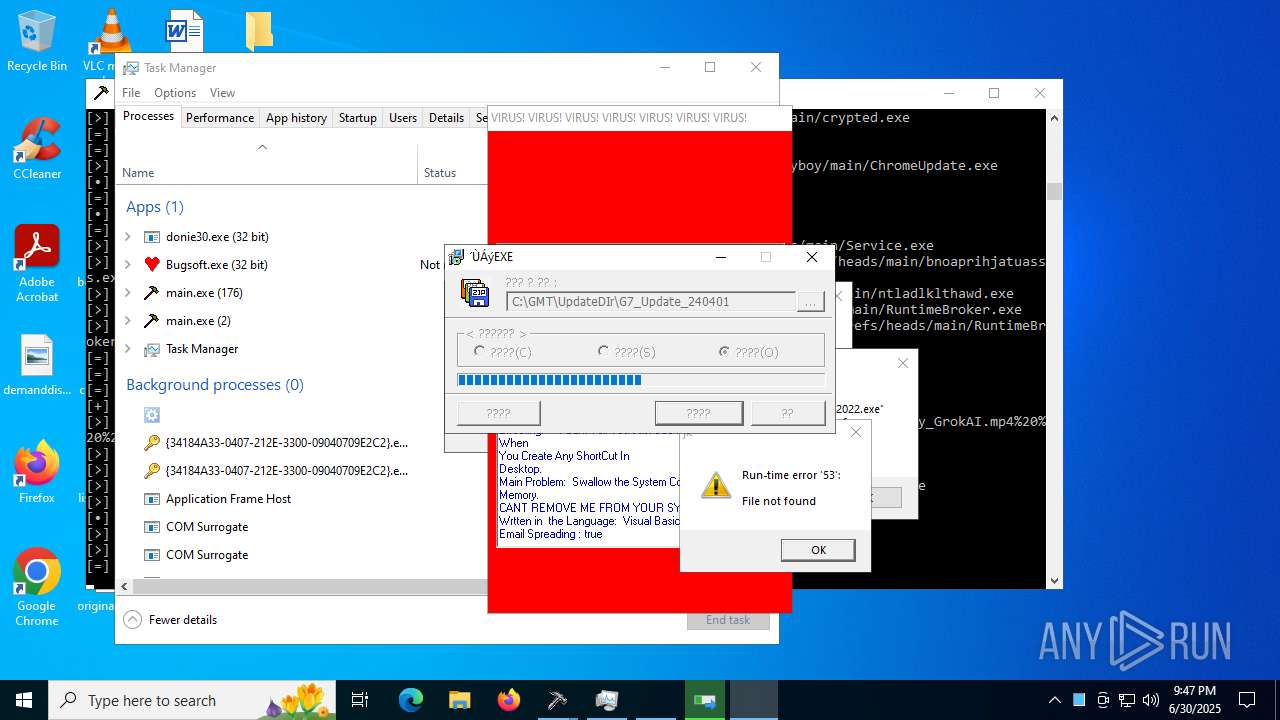
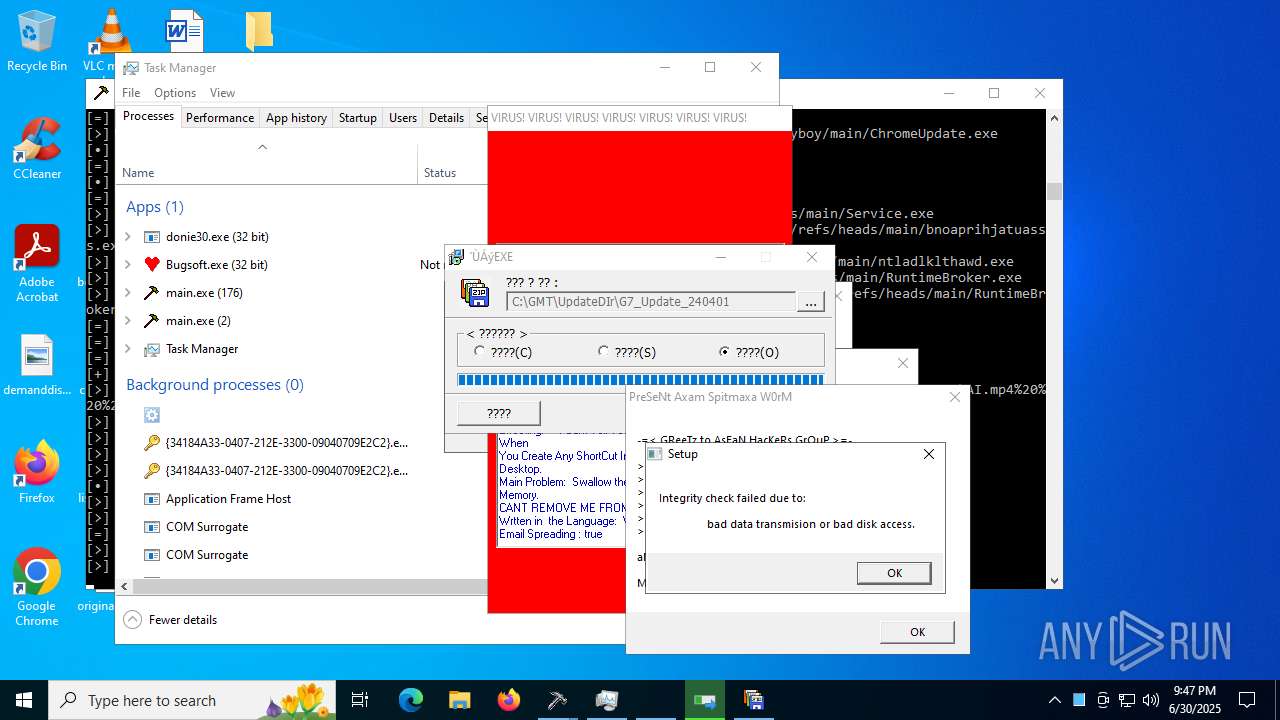
MALICIOUS
Changes powershell execution policy (Bypass)
- main.exe (PID: 3788)
- cmd.exe (PID: 5352)
- powershell.exe (PID: 8424)
- conhost.exe (PID: 15488)
Bypass execution policy to execute commands
- powershell.exe (PID: 6304)
- powershell.exe (PID: 8424)
- powershell.exe (PID: 9188)
- powershell.exe (PID: 9816)
- powershell.exe (PID: 9952)
- powershell.exe (PID: 10976)
- powershell.exe (PID: 11024)
- powershell.exe (PID: 11060)
- powershell.exe (PID: 11536)
- powershell.exe (PID: 11172)
- powershell.exe (PID: 10724)
- powershell.exe (PID: 12760)
- powershell.exe (PID: 12928)
- powershell.exe (PID: 13536)
- powershell.exe (PID: 14012)
- powershell.exe (PID: 14004)
- powershell.exe (PID: 14144)
- powershell.exe (PID: 14080)
- powershell.exe (PID: 14268)
- powershell.exe (PID: 14160)
- powershell.exe (PID: 14228)
- powershell.exe (PID: 14236)
- powershell.exe (PID: 9552)
- powershell.exe (PID: 16580)
- powershell.exe (PID: 6380)
- powershell.exe (PID: 7908)
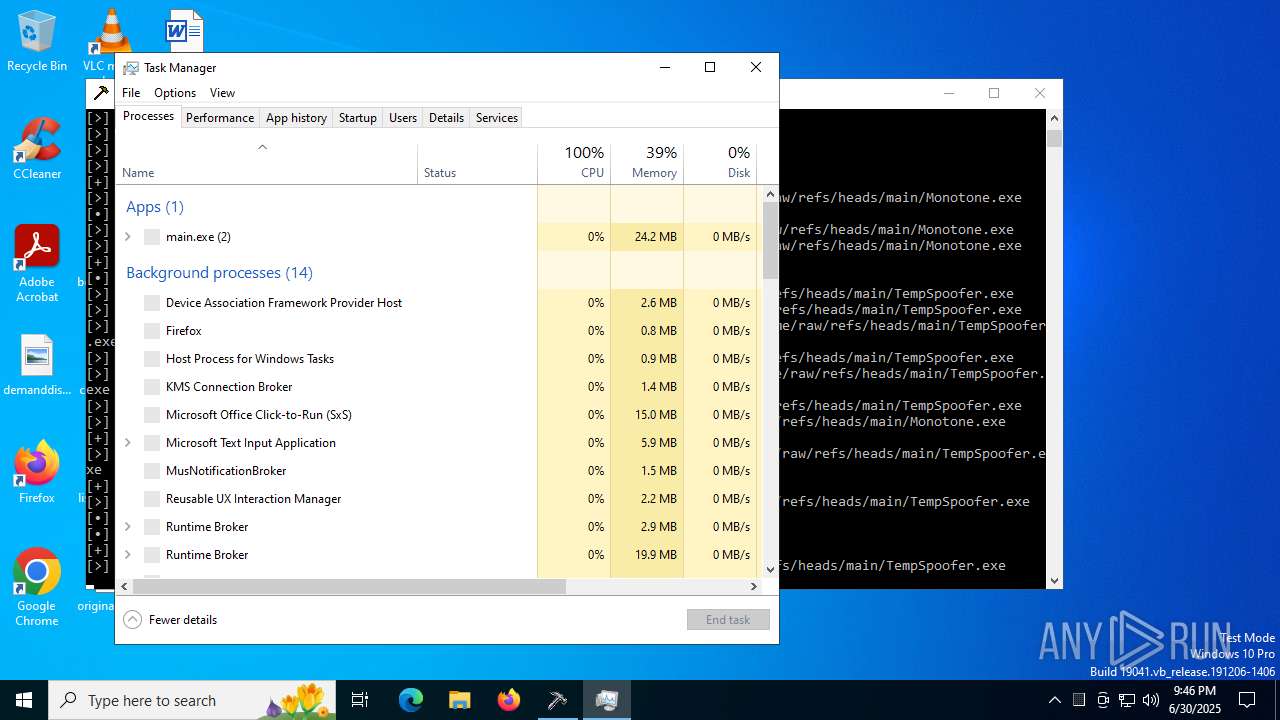
REMCOS has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- e.exe (PID: 7752)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
GENERIC has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- Amus.exe (PID: 13568)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
LUMMA has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- varen.exe (PID: 9920)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8632)
AMADEY has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- donie30.exe (PID: 7544)
- bravo29.exe (PID: 8292)
- amnew.exe (PID: 14136)
- dumer.exe (PID: 13432)
Application was injected by another process
- explorer.exe (PID: 4772)
Changes the autorun value in the registry
- 1.exe (PID: 7600)
- e.exe (PID: 7752)
- syspool.exe (PID: 9924)
- explorer.exe (PID: 11328)
- klass.exe (PID: 12148)
- ls.exe (PID: 3844)
- msconfig.exe (PID: 12024)
- loader.exe (PID: 14104)
- WannaCry.exe (PID: 14292)
- winsvchost.exe (PID: 14048)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 14604)
- Adobe.exe (PID: 11696)
- remcos.exe (PID: 13016)
- Axam.a.exe (PID: 13528)
- Amus.exe (PID: 13568)
- explorer.exe (PID: 4772)
- AdobeART.exe (PID: 17828)
- Bloxflip%20Predictor.exe (PID: 12624)
- Axam.exe (PID: 19048)
- AdobeART.exe (PID: 7620)
- Axam.exe (PID: 10744)
- Axam.exe (PID: 8088)
- Axam.exe (PID: 8496)
- Axam.exe (PID: 8008)
- Axam.exe (PID: 7968)
- Axam.exe (PID: 8580)
- quasarat.exe (PID: 14276)
- Axam.exe (PID: 9004)
- Axam.exe (PID: 8952)
- Axam.exe (PID: 10600)
- Axam.exe (PID: 10612)
- Axam.exe (PID: 3756)
- server.exe (PID: 11192)
- Axam.exe (PID: 5416)
- Axam.exe (PID: 17272)
- Axam.exe (PID: 17348)
- Axam.exe (PID: 14828)
- Axam.exe (PID: 5424)
- Axam.exe (PID: 14984)
- Axam.exe (PID: 16892)
- Axam.exe (PID: 13464)
- Axam.exe (PID: 13668)
- Axam.exe (PID: 3724)
- Axam.exe (PID: 16908)
- Axam.exe (PID: 12044)
- Axam.exe (PID: 17740)
- Axam.exe (PID: 18076)
- Axam.exe (PID: 12500)
- Axam.exe (PID: 9240)
- Axam.exe (PID: 13164)
- Axam.exe (PID: 15024)
- Axam.exe (PID: 4560)
- Axam.exe (PID: 16444)
- Axam.exe (PID: 9868)
- Axam.exe (PID: 10584)
- Axam.exe (PID: 18880)
- Axam.exe (PID: 4820)
- Axam.exe (PID: 7320)
- Axam.exe (PID: 17512)
- Axam.exe (PID: 11628)
- Axam.exe (PID: 1520)
- Axam.exe (PID: 17896)
- Axam.exe (PID: 4120)
- dumer.exe (PID: 13432)
- Axam.exe (PID: 18988)
- Axam.exe (PID: 12124)
- Axam.exe (PID: 18264)
- Axam.exe (PID: 17984)
- Axam.exe (PID: 16408)
- Axam.exe (PID: 1068)
- Axam.exe (PID: 17472)
- Axam.exe (PID: 12720)
- Axam.exe (PID: 11092)
- Axam.exe (PID: 16064)
- Axam.exe (PID: 13664)
- Axam.exe (PID: 7868)
- Axam.exe (PID: 11136)
- Axam.exe (PID: 6388)
- Axam.exe (PID: 8888)
Runs injected code in another process
- 1.exe (PID: 7600)
AMADEY mutex has been found
- donie30.exe (PID: 7544)
- amnew.exe (PID: 14136)
- dumer.exe (PID: 18156)
- varen.exe (PID: 9920)
- dumer.exe (PID: 13432)
REMCOS mutex has been found
- e.exe (PID: 7752)
- K.exe (PID: 7704)
- remcos.exe (PID: 13016)
REMCOS has been detected
- e.exe (PID: 7752)
- K.exe (PID: 7704)
- remcos.exe (PID: 13016)
- remcos.exe (PID: 13016)
RESOLVERRAT has been found (auto)
- main.exe (PID: 3788)
REDLINE has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
NJRAT has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
- your_app.exe (PID: 11208)
- Bloxflip%20Predictor.exe (PID: 12624)
FORMBOOK has been found (auto)
- main.exe (PID: 3788)
AGENTTESLA has been found (auto)
- main.exe (PID: 3788)
YOUNGLOTUS has been found (auto)
- main.exe (PID: 3788)
METASPLOIT has been found (auto)
- main.exe (PID: 3788)
REMCOS has been detected (SURICATA)
- K.exe (PID: 7704)
- remcos.exe (PID: 13016)
METASPLOIT has been detected (SURICATA)
- main.exe (PID: 3788)
METERPRETER has been detected (SURICATA)
- main.exe (PID: 3788)
Create files in the Startup directory
- explorer.exe (PID: 11328)
- trails.exe (PID: 7796)
- bot.exe (PID: 2216)
- Axam.a.exe (PID: 13528)
- Bloxflip%20Predictor.exe (PID: 12624)
- Setup.exe (PID: 10952)
SCREENCONNECT has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
Registers / Runs the DLL via REGSVR32.EXE
- loader.exe (PID: 14104)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2200)
CLICKFIX has been detected (SURICATA)
- svchost.exe (PID: 2200)
- main.exe (PID: 3788)
PHORPIEX has been found (auto)
- kajmak.exe (PID: 14064)
WANNACRY mutex has been found
- WannaCry.exe (PID: 14292)
NETWORM mutex has been found
- Amus.exe (PID: 13568)
ARECHCLIENT2 has been found (auto)
- main.exe (PID: 3788)
DCRAT mutex has been found
- startud.exe (PID: 9168)
ASYNCRAT has been detected (SURICATA)
- trails.exe (PID: 7796)
- foncar.exe (PID: 14216)
- aspnet_compiler.exe (PID: 14796)
Connects to the CnC server
- remcos.exe (PID: 13016)
- cc.exe (PID: 11080)
- svchost.exe (PID: 2200)
- powershell.exe (PID: 12928)
- varen.exe (PID: 9920)
- Crypt.exe (PID: 8480)
- dumer.exe (PID: 13432)
- explorer.exe (PID: 4772)
PURELOGS has been found (auto)
- main.exe (PID: 3788)
FORMBOOK has been detected
- cmmon32.exe (PID: 10680)
- explorer.exe (PID: 4772)
REDLINE has been detected (SURICATA)
- cc.exe (PID: 11080)
METASTEALER has been detected (SURICATA)
- cc.exe (PID: 11080)
DCRAT has been found (auto)
- main.exe (PID: 3788)
- main.exe (PID: 3788)
ASYNCRAT has been found (auto)
- main.exe (PID: 3788)
COINMINER has been found (auto)
- main.exe (PID: 3788)
- varen.exe (PID: 9920)
SNAKEKEYLOGGER has been detected (SURICATA)
- mexx.exe (PID: 7692)
- RegSvcs.exe (PID: 1164)
NJRAT mutex has been found
- Bloxflip%20Predictor.exe (PID: 12624)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 16660)
MODILOADER mutex has been found
- AdobeART.exe (PID: 17828)
- AdobeART.exe (PID: 7620)
NESHTA mutex has been found
- Setup.exe (PID: 10988)
- Setup.exe (PID: 10952)
- svchost.com (PID: 18808)
- quasarat.exe (PID: 10420)
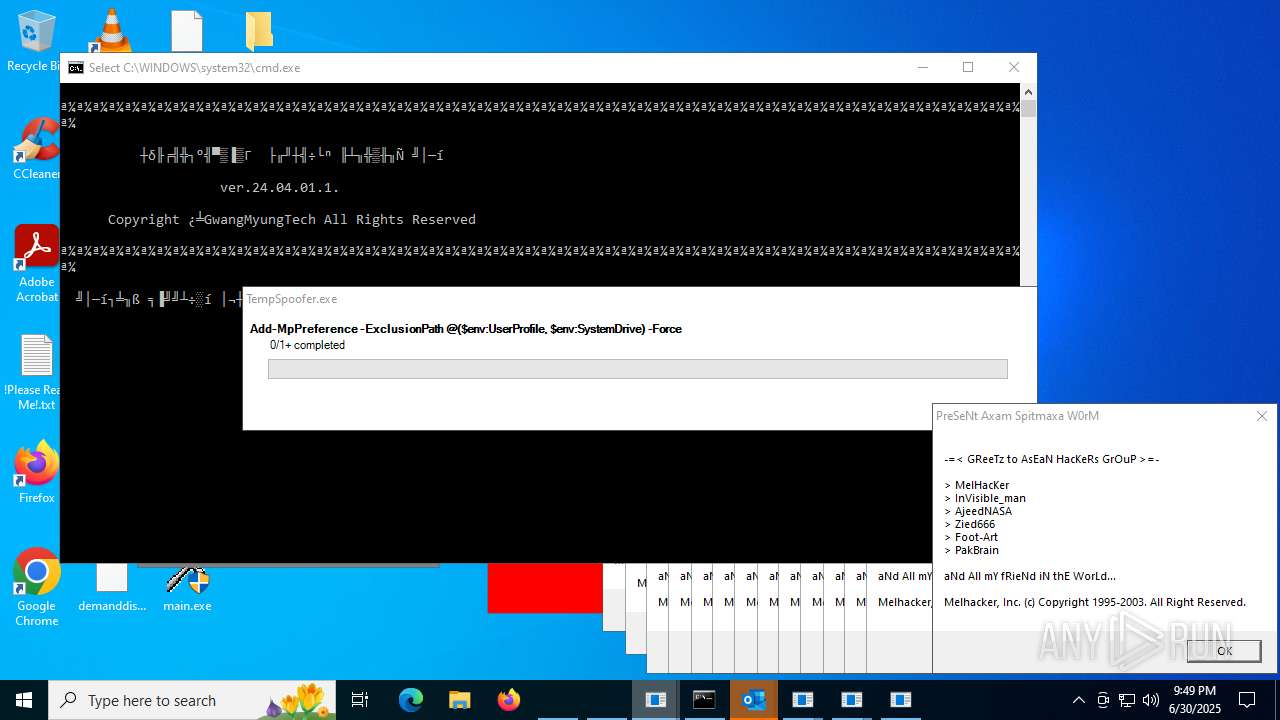
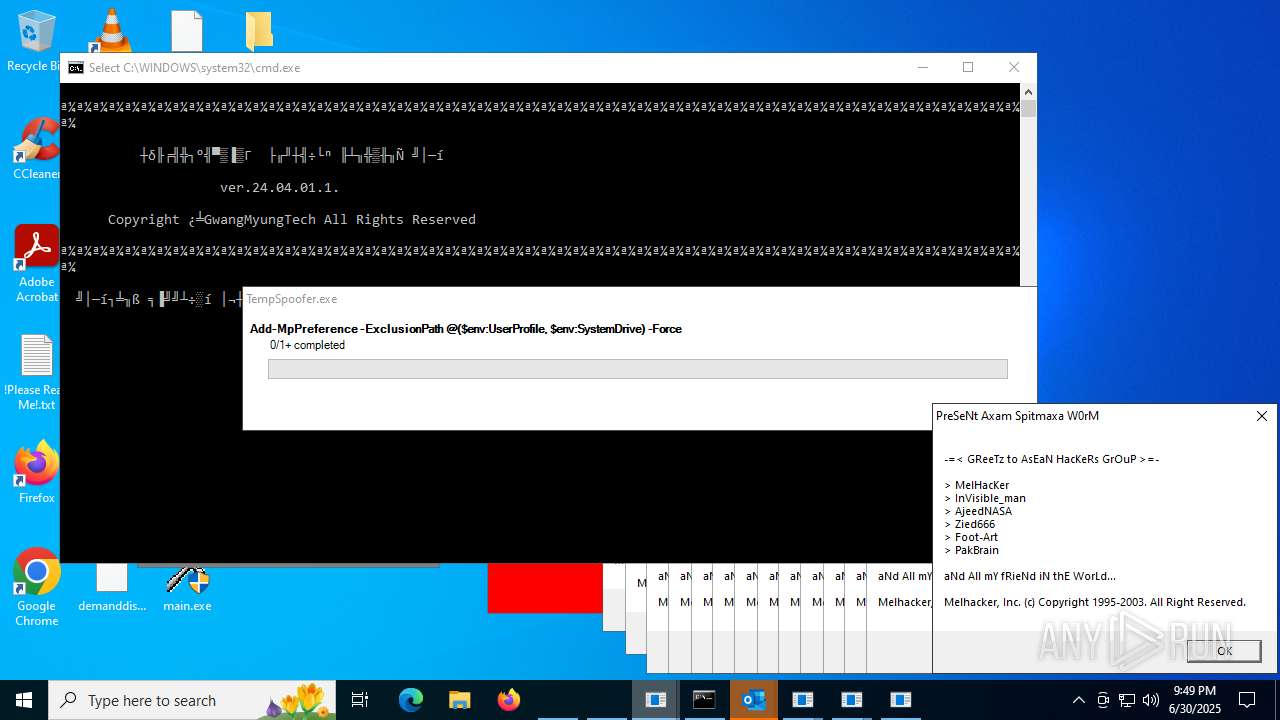
Adds path to the Windows Defender exclusion list
- Crypt.exe (PID: 8480)
- ap.exe (PID: 9344)
DIAMOTRIX has been detected (SURICATA)
- explorer.exe (PID: 4772)
Changes Windows Defender settings
- Crypt.exe (PID: 8480)
Actions looks like stealing of personal data
- mexx.exe (PID: 7692)
- cc.exe (PID: 11080)
- Jay.exe (PID: 13408)
- F.exe (PID: 12576)
- aspnet_compiler.exe (PID: 14796)
- RegSvcs.exe (PID: 1164)
- Vb5HUIU.exe (PID: 7612)
Steals credentials from Web Browsers
- mexx.exe (PID: 7692)
- cc.exe (PID: 11080)
- Jay.exe (PID: 13408)
- F.exe (PID: 12576)
- RegSvcs.exe (PID: 1164)
AUROTUN mutex has been found
- Crypt.exe (PID: 8480)
Run PowerShell with an invisible window
- powershell.exe (PID: 6380)
- powershell.exe (PID: 7908)
QUASAR mutex has been found
- Client-built.exe (PID: 13256)
- quasarat.exe (PID: 14276)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 6304)
- powershell.exe (PID: 10976)
- powershell.exe (PID: 12760)
- powershell.exe (PID: 14004)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 10724)
- powershell.exe (PID: 14004)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 9952)
- powershell.exe (PID: 12928)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 13536)
Uses Task Scheduler to autorun other applications
- quasarat.exe (PID: 14276)
LUMMA mutex has been found
- MSBuild.exe (PID: 12004)
- MSBuild.exe (PID: 16660)
AMADEY has been detected (SURICATA)
- gaved.exe (PID: 10776)
- dumer.exe (PID: 13432)
- varen.exe (PID: 9920)
KOI has been detected (SURICATA)
- powershell.exe (PID: 12928)
Execute application with conhost.exe as parent process
- powershell.exe (PID: 7908)
WannaCry Ransomware is detected
- WannaCry.exe (PID: 14292)
QUASAR has been detected (SURICATA)
- Client-built.exe (PID: 13256)
NjRAT is detected
- server.exe (PID: 11192)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 14228)
- powershell.exe (PID: 14144)
AGENTTESLA has been detected (SURICATA)
- Jay.exe (PID: 13408)
- F.exe (PID: 12576)
Writes a file to the Word startup folder
- WannaCry.exe (PID: 14292)
RANSOMWARE has been detected
- WannaCry.exe (PID: 14292)
Modifies files in the Chrome extension folder
- WannaCry.exe (PID: 14292)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 4772)
Uses Task Scheduler to run other applications
- powershell.exe (PID: 14228)
SUSPICIOUS
Application launched itself
- main.exe (PID: 2076)
- 90.exe (PID: 10888)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 14604)
- AdobeART.exe (PID: 17596)
- powershell.exe (PID: 8424)
- AdobeART.exe (PID: 19332)
Process drops python dynamic module
- main.exe (PID: 2076)
The process drops C-runtime libraries
- main.exe (PID: 2076)
- main.exe (PID: 3788)
Process drops legitimate windows executable
- main.exe (PID: 2076)
- main.exe (PID: 3788)
- WannaCry.exe (PID: 14292)
- varen.exe (PID: 9920)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8632)
Loads Python modules
- main.exe (PID: 3788)
Starts CMD.EXE for commands execution
- main.exe (PID: 3788)
- Bugsoft.exe (PID: 13584)
- WannaCry.exe (PID: 14292)
- winxclient.exe (PID: 12508)
- cmmon32.exe (PID: 10680)
- esp.exe (PID: 14192)
- G7_Update.exe (PID: 14300)
- quasarat.exe (PID: 14276)
- pe2shc.exe (PID: 13576)
Executable content was dropped or overwritten
- main.exe (PID: 2076)
- main.exe (PID: 3788)
- 1.exe (PID: 7600)
- e.exe (PID: 7752)
- syspool.exe (PID: 9924)
- test1.exe (PID: 9988)
- lol.exe (PID: 10664)
- Ganja90.exe (PID: 11184)
- Ganja180.exe (PID: 10744)
- explorer.exe (PID: 11328)
- Ganja39.exe (PID: 11160)
- Setup.exe (PID: 10988)
- Ganja199.exe (PID: 11916)
- Ganja195.exe (PID: 10916)
- Setup.exe (PID: 10952)
- Prolin.exe (PID: 10876)
- loader.exe (PID: 14104)
- WannaCry.exe (PID: 14292)
- porn.exe (PID: 10788)
- kajmak.exe (PID: 14064)
- CryptoLocker.exe (PID: 14088)
- swagggg.exe (PID: 7192)
- donie30.exe (PID: 7544)
- bot.exe (PID: 2216)
- your_app.exe (PID: 11208)
- bravo29.exe (PID: 8292)
- Axam.a.exe (PID: 13528)
- G7_Update.exe (PID: 14300)
- 123.exe (PID: 14096)
- 4De3.exe (PID: 17212)
- Amus.exe (PID: 13568)
- Bloxflip%20Predictor.exe (PID: 12624)
- Crypt.exe (PID: 8480)
- amnew.exe (PID: 14136)
- ap.exe (PID: 9344)
- Ganja128.exe (PID: 10760)
- powershell.exe (PID: 6304)
- Vb5HUIU.exe (PID: 7612)
- powershell.exe (PID: 10976)
- powershell.exe (PID: 12760)
- csc.exe (PID: 10632)
- csc.exe (PID: 10508)
- dumer.exe (PID: 13432)
- varen.exe (PID: 9920)
- svchost.com (PID: 18808)
- csc.exe (PID: 16960)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 8544)
- quasarat.exe (PID: 10420)
- powershell.exe (PID: 14228)
- csc.exe (PID: 6152)
- csc.exe (PID: 9784)
The process checks if it is being run in the virtual environment
- main.exe (PID: 3788)
- Vb5HUIU.exe (PID: 7612)
Reads security settings of Internet Explorer
- sFFG7Wg.exe (PID: 2388)
- build.exe (PID: 5348)
- TempSpoofer.exe (PID: 7224)
- Helper.exe (PID: 7176)
- Monotone.exe (PID: 7208)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7232)
- TempSpoofer.exe (PID: 7496)
- Monotone.exe (PID: 7184)
- TempSpoofer.exe (PID: 7396)
- TempSpoofer.exe (PID: 7296)
- TempSpoofer.exe (PID: 7664)
- TempSpoofer.exe (PID: 7636)
- game3.exe (PID: 7588)
- TempSpoofer.exe (PID: 7648)
- UniversalSpoofer.exe (PID: 8620)
- e.exe (PID: 7752)
- test1.exe (PID: 9988)
- LOIC.exe (PID: 9864)
- Amus.exe (PID: 13568)
- donie30.exe (PID: 7544)
- lol.exe (PID: 10664)
- bravo29.exe (PID: 8292)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 14604)
- cabal.exe (PID: 14200)
- Setup.exe (PID: 10988)
- Setup.exe (PID: 10952)
- 90.exe (PID: 12400)
- Bloxflip%20Predictor.exe (PID: 12624)
- L2.exe (PID: 14152)
- your_app.exe (PID: 11208)
- 123.exe (PID: 14096)
- G7_Update.exe (PID: 14300)
- amnew.exe (PID: 14136)
- 4De3.exe (PID: 17212)
- ap.exe (PID: 9344)
- Ganja128.exe (PID: 10760)
- Vb5HUIU.exe (PID: 7612)
- varen.exe (PID: 9920)
- quasarat.exe (PID: 14276)
- gaved.exe (PID: 10776)
- dumer.exe (PID: 13432)
- !WannaDecryptor!.exe (PID: 7000)
- quasarat.exe (PID: 10420)
- ShellExperienceHost.exe (PID: 15736)
Executing commands from ".cmd" file
- main.exe (PID: 3788)
Starts POWERSHELL.EXE for commands execution
- main.exe (PID: 3788)
- cmd.exe (PID: 5352)
- Crypt.exe (PID: 8480)
- powershell.exe (PID: 8424)
- UniversalSpoofer.exe (PID: 8620)
- TempSpoofer.exe (PID: 7648)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7496)
- TempSpoofer.exe (PID: 7396)
- Monotone.exe (PID: 7208)
- TempSpoofer.exe (PID: 7636)
- TempSpoofer.exe (PID: 7232)
- TempSpoofer.exe (PID: 7664)
- TempSpoofer.exe (PID: 7296)
- Monotone.exe (PID: 7184)
- TempSpoofer.exe (PID: 7224)
- conhost.exe (PID: 15488)
The process executes Powershell scripts
- main.exe (PID: 3788)
- cmd.exe (PID: 5352)
Suspicious files were dropped or overwritten
- main.exe (PID: 3788)
Connects to the server without a host name
- main.exe (PID: 3788)
- syspool.exe (PID: 9924)
- VXHDH.exe (PID: 4044)
- cabal.exe (PID: 14200)
- trip.exe (PID: 11032)
- explorer.exe (PID: 4772)
- powershell.exe (PID: 9952)
- varen.exe (PID: 9920)
- dumer.exe (PID: 13432)
- gaved.exe (PID: 10776)
- powershell.exe (PID: 12928)
- powershell.exe (PID: 14228)
- esp32.exe (PID: 13552)
Potential Corporate Privacy Violation
- main.exe (PID: 3788)
- dumer.exe (PID: 13432)
- varen.exe (PID: 9920)
- powershell.exe (PID: 14228)
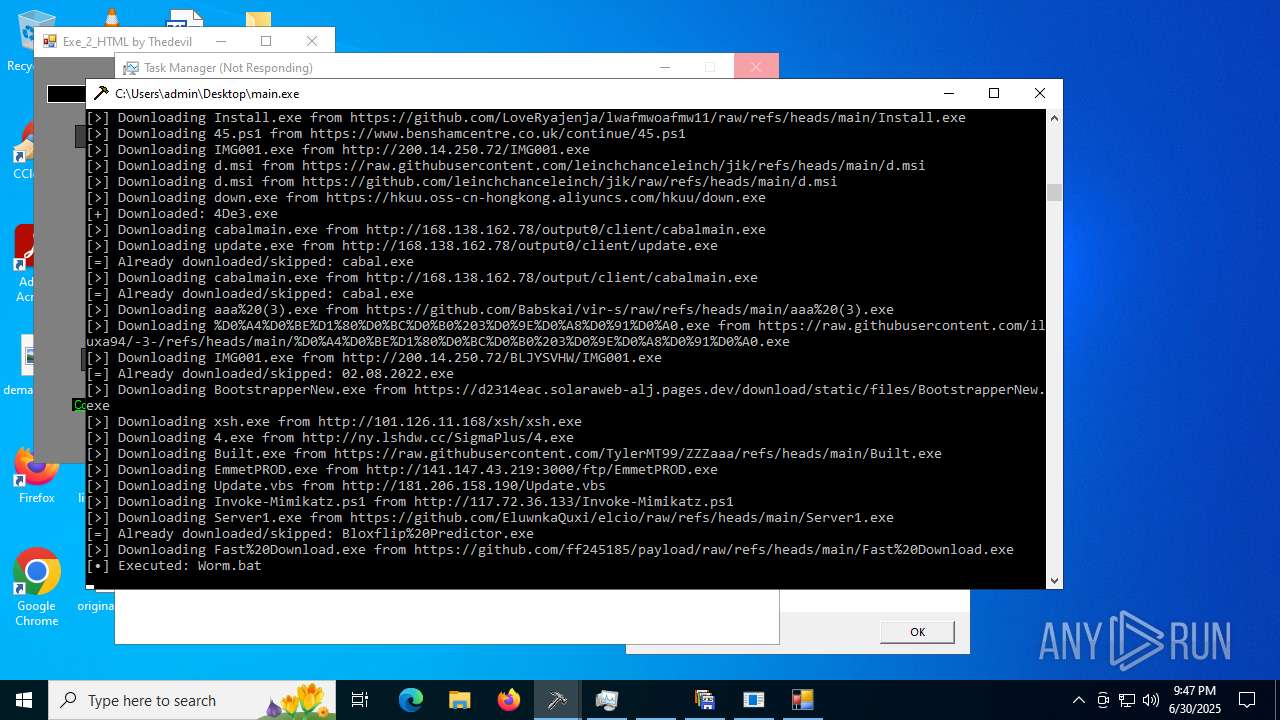
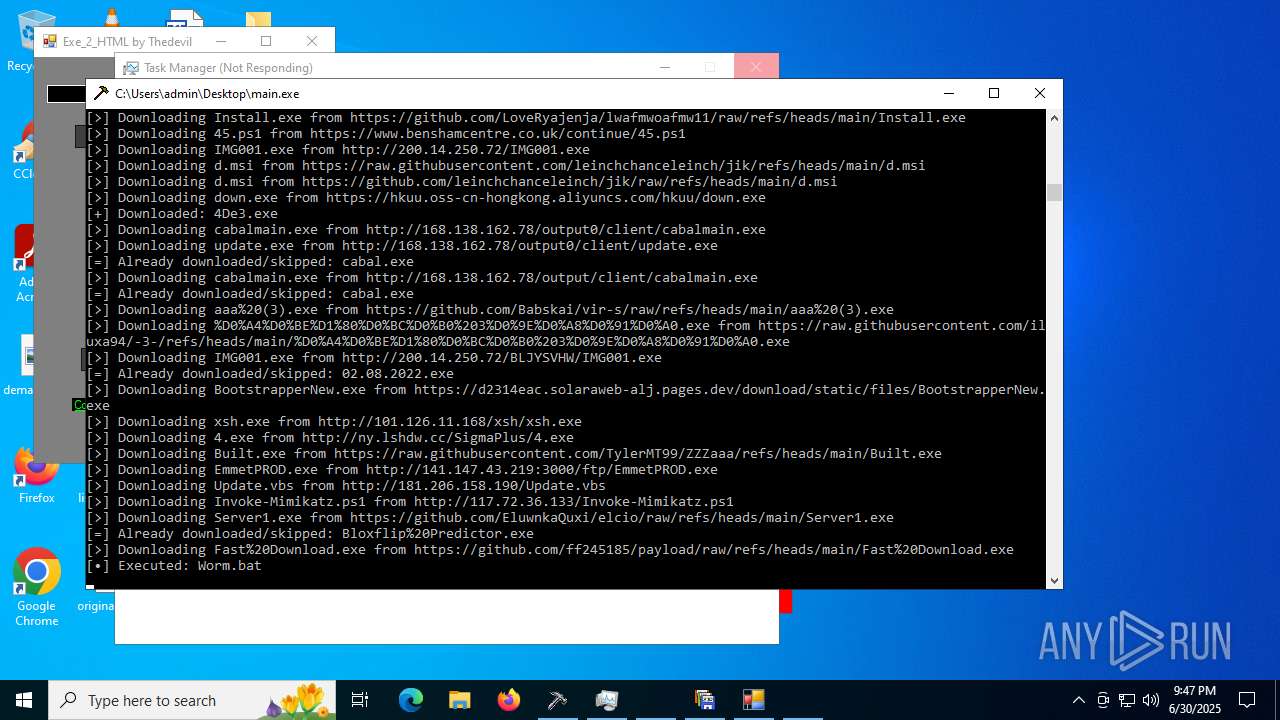
Process requests binary or script from the Internet
- main.exe (PID: 3788)
- varen.exe (PID: 9920)
- dumer.exe (PID: 13432)
- powershell.exe (PID: 14228)
Connects to unusual port
- main.exe (PID: 3788)
- K.exe (PID: 7704)
- tcp_windows_amd64.exe (PID: 9440)
- Worldofficee.exe (PID: 8132)
- Worldoffice.exe (PID: 10960)
- winxclient.exe (PID: 12508)
- winsvchost.exe (PID: 14048)
- my%20file.exe (PID: 7564)
- trails.exe (PID: 7796)
- XClient.exe (PID: 8568)
- remcos.exe (PID: 13016)
- march.exe (PID: 11052)
- demon.exe (PID: 11072)
- https.exe (PID: 11124)
- esp.exe (PID: 14192)
- Adobe.exe (PID: 11696)
- cc.exe (PID: 11080)
- Clien123.exe (PID: 14252)
- startud.exe (PID: 9168)
- svchost.exe (PID: 13124)
- foncar.exe (PID: 14216)
- c2_payload_aes.exe (PID: 13196)
- esp32.exe (PID: 13552)
- AdobeART.exe (PID: 17828)
- Crypt.exe (PID: 8480)
- Client-built.exe (PID: 13256)
- build.exe (PID: 5348)
- Jay.exe (PID: 13408)
- F.exe (PID: 12576)
- installs.exe (PID: 8560)
- aspnet_compiler.exe (PID: 14796)
- svchost.exe (PID: 13844)
Executing commands from a ".bat" file
- main.exe (PID: 3788)
- Bugsoft.exe (PID: 13584)
- WannaCry.exe (PID: 14292)
- G7_Update.exe (PID: 14300)
- quasarat.exe (PID: 14276)
Reads the date of Windows installation
- 1.exe (PID: 7600)
- 123.exe (PID: 14096)
- Ganja128.exe (PID: 10760)
- Helper.exe (PID: 7176)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- porn.exe (PID: 10788)
Contacting a server suspected of hosting an Exploit Kit
- main.exe (PID: 3788)
Contacting a server suspected of hosting an CnC
- K.exe (PID: 7704)
- trails.exe (PID: 7796)
- remcos.exe (PID: 13016)
- foncar.exe (PID: 14216)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 16660)
- gaved.exe (PID: 10776)
- dumer.exe (PID: 13432)
- varen.exe (PID: 9920)
- Client-built.exe (PID: 13256)
- aspnet_compiler.exe (PID: 14796)
- explorer.exe (PID: 4772)
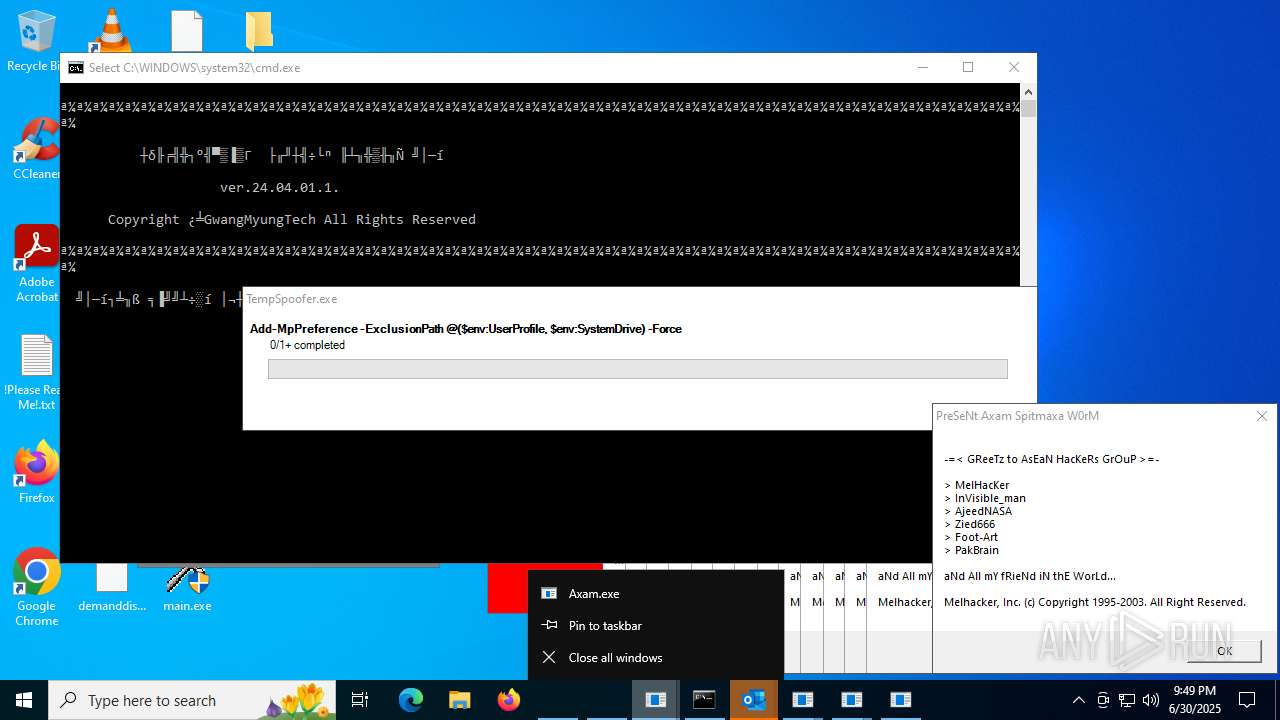
Starts itself from another location
- Ganja90.exe (PID: 11184)
- Ganja180.exe (PID: 10744)
- Ganja39.exe (PID: 11160)
- Ganja199.exe (PID: 11916)
- Ganja195.exe (PID: 10916)
- kajmak.exe (PID: 14064)
- CryptoLocker.exe (PID: 14088)
- test1.exe (PID: 9988)
- e.exe (PID: 7752)
- donie30.exe (PID: 7544)
- 90.exe (PID: 12400)
The process creates files with name similar to system file names
- main.exe (PID: 3788)
- kajmak.exe (PID: 14064)
- loader.exe (PID: 14104)
- 4De3.exe (PID: 17212)
- WerFault.exe (PID: 15416)
- WannaCry.exe (PID: 14292)
Crypto Currency Mining Activity Detected
- main.exe (PID: 3788)
- powershell.exe (PID: 14228)
Creates file in the systems drive root
- Prolin.exe (PID: 10876)
- Axam.a.exe (PID: 13528)
- Amus.exe (PID: 13568)
- 4De3.exe (PID: 17212)
- Setup.exe (PID: 10988)
- Setup.exe (PID: 10952)
- Axam.exe (PID: 19048)
- Axam.exe (PID: 10744)
- Axam.exe (PID: 8088)
- Axam.exe (PID: 8008)
- Axam.exe (PID: 7968)
- Axam.exe (PID: 8496)
- Axam.exe (PID: 8580)
- Axam.exe (PID: 9004)
- Axam.exe (PID: 8952)
- attrib.exe (PID: 9376)
- Axam.exe (PID: 10600)
- cmd.exe (PID: 12880)
- explorer.exe (PID: 4772)
- Axam.exe (PID: 10612)
- svchost.com (PID: 18808)
- Axam.exe (PID: 3756)
- attrib.exe (PID: 16512)
- Axam.exe (PID: 17272)
- Axam.exe (PID: 5416)
- Axam.exe (PID: 17348)
- Axam.exe (PID: 5424)
- Axam.exe (PID: 14828)
- Axam.exe (PID: 14984)
- Axam.exe (PID: 16892)
- Axam.exe (PID: 12044)
- Axam.exe (PID: 13668)
- Axam.exe (PID: 13464)
- Axam.exe (PID: 16908)
- Axam.exe (PID: 17740)
- Axam.exe (PID: 18076)
- Axam.exe (PID: 3724)
- Axam.exe (PID: 12500)
- Axam.exe (PID: 15024)
- Axam.exe (PID: 9240)
- Axam.exe (PID: 13164)
- Axam.exe (PID: 4560)
- Axam.exe (PID: 9868)
- Axam.exe (PID: 16444)
- Axam.exe (PID: 4820)
- Axam.exe (PID: 18880)
- Axam.exe (PID: 1520)
- Axam.exe (PID: 10584)
- Axam.exe (PID: 7320)
- Axam.exe (PID: 11628)
- Axam.exe (PID: 17512)
- Axam.exe (PID: 17896)
- Axam.exe (PID: 18988)
- Axam.exe (PID: 4120)
- Axam.exe (PID: 12124)
- Axam.exe (PID: 18264)
- Axam.exe (PID: 17984)
- Axam.exe (PID: 16408)
- Axam.exe (PID: 1068)
- Axam.exe (PID: 17472)
- WannaCry.exe (PID: 14292)
- Axam.exe (PID: 7868)
- Axam.exe (PID: 6388)
- Axam.exe (PID: 8888)
Starts a Microsoft application from unusual location
- WannaCry.exe (PID: 14292)
- cron123123213.exe (PID: 13316)
- !WannaDecryptor!.exe (PID: 7000)
Possible Social Engineering Attempted
- svchost.exe (PID: 2200)
Block-list domains
- main.exe (PID: 3788)
Executes application which crashes
- PluGman23333%20233.exe (PID: 7628)
- kj.exe (PID: 6836)
- cabal.exe (PID: 14200)
- powershell.exe (PID: 14268)
Checks for external IP
- svchost.exe (PID: 2200)
- mexx.exe (PID: 7692)
- Vb5HUIU.exe (PID: 7612)
- svchost.exe (PID: 13844)
- Client-built.exe (PID: 13256)
- quasarat.exe (PID: 14276)
- Crypt.exe (PID: 8480)
- Jay.exe (PID: 13408)
- F.exe (PID: 12576)
- build.exe (PID: 5348)
- installs.exe (PID: 8560)
- RegSvcs.exe (PID: 1164)
- powershell.exe (PID: 10724)
Mutex name with non-standard characters
- Setup.exe (PID: 10988)
- Setup.exe (PID: 10952)
- svchost.com (PID: 18808)
- quasarat.exe (PID: 10420)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- mexx.exe (PID: 7692)
- build.exe (PID: 5348)
- RegSvcs.exe (PID: 1164)
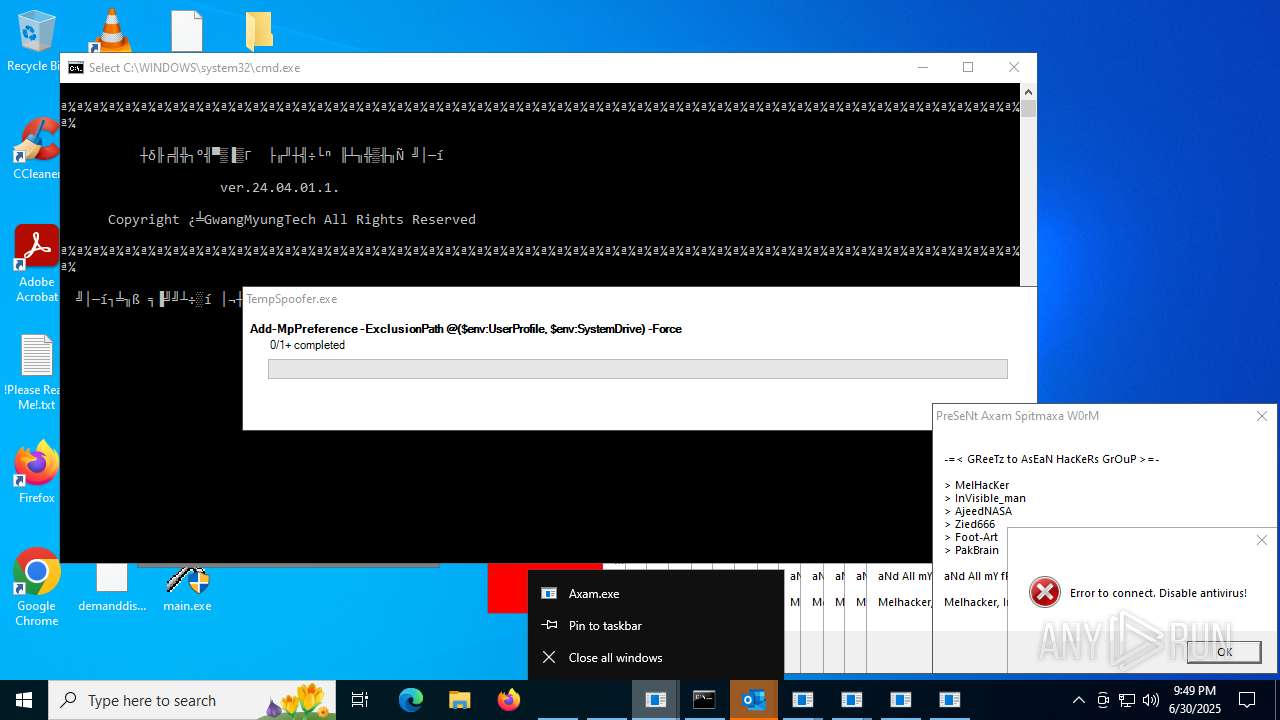
The process verifies whether the antivirus software is installed
- cmd.exe (PID: 10012)
- mexx.exe (PID: 7692)
- RegSvcs.exe (PID: 1164)
- Vb5HUIU.exe (PID: 7612)
Script adds exclusion path to Windows Defender
- Crypt.exe (PID: 8480)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6304)
- Helper.exe (PID: 7176)
- powershell.exe (PID: 9188)
- powershell.exe (PID: 10976)
- powershell.exe (PID: 10724)
- powershell.exe (PID: 12760)
- powershell.exe (PID: 14004)
Starts application with an unusual extension
- your_app.exe (PID: 11208)
- cmd.exe (PID: 11344)
Uses ATTRIB.EXE to modify file attributes
- Bloxflip%20Predictor.exe (PID: 12624)
- cmd.exe (PID: 12880)
The process executes VB scripts
- cmd.exe (PID: 12144)
Executes script without checking the security policy
- powershell.exe (PID: 6380)
Potential TCP-based PowerShell reverse shell connection
- powershell.exe (PID: 8424)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 8424)
Possibly malicious use of IEX has been detected
- powershell.exe (PID: 8424)
Found IP address in command line
- powershell.exe (PID: 6380)
The process hide an interactive prompt from the user
- powershell.exe (PID: 8424)
BASE64 encoded PowerShell command has been detected
- UniversalSpoofer.exe (PID: 8620)
- TempSpoofer.exe (PID: 7648)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7496)
- Monotone.exe (PID: 7208)
- TempSpoofer.exe (PID: 7636)
- TempSpoofer.exe (PID: 7396)
- TempSpoofer.exe (PID: 7232)
- TempSpoofer.exe (PID: 7296)
- Monotone.exe (PID: 7184)
- TempSpoofer.exe (PID: 7664)
- TempSpoofer.exe (PID: 7224)
Uses sleep to delay execution (POWERSHELL)
- Helper.exe (PID: 7176)
Starts a new process with hidden mode (POWERSHELL)
- Helper.exe (PID: 7176)
Base64-obfuscated command line is found
- UniversalSpoofer.exe (PID: 8620)
- TempSpoofer.exe (PID: 7648)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7496)
- Monotone.exe (PID: 7208)
- TempSpoofer.exe (PID: 7636)
- TempSpoofer.exe (PID: 7232)
- TempSpoofer.exe (PID: 7664)
- TempSpoofer.exe (PID: 7296)
- Monotone.exe (PID: 7184)
- TempSpoofer.exe (PID: 7396)
- TempSpoofer.exe (PID: 7224)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 10724)
Checks a user's role membership (POWERSHELL)
- Helper.exe (PID: 7176)
- powershell.exe (PID: 10724)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 14080)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 14080)
- powershell.exe (PID: 10724)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6304)
- powershell.exe (PID: 10976)
- powershell.exe (PID: 12760)
Changes AMSI initialization state that disables detection systems (POWERSHELL)
- powershell.exe (PID: 10724)
The process executes via Task Scheduler
- gaved.exe (PID: 10776)
- varen.exe (PID: 9920)
- dumer.exe (PID: 13432)
Adds/modifies Windows certificates
- certutil.exe (PID: 5368)
Uses WMIC.EXE to obtain computer system information
- trails.exe (PID: 7796)
CSC.EXE is used to compile C# code
- csc.exe (PID: 10632)
- csc.exe (PID: 10508)
- csc.exe (PID: 16960)
- csc.exe (PID: 6152)
- csc.exe (PID: 9784)
Searches for installed software
- MSBuild.exe (PID: 12004)
- MSBuild.exe (PID: 16660)
- Vb5HUIU.exe (PID: 7612)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 11192)
Modifies hosts file to alter network resolution
- Vb5HUIU.exe (PID: 7612)
Process uses IPCONFIG to clear DNS cache
- Vb5HUIU.exe (PID: 7612)
- Helper.exe (PID: 7176)
Uses TASKKILL.EXE to kill process
- WannaCry.exe (PID: 14292)
- cmd.exe (PID: 11156)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 14080)
Accesses domain name via WMI (SCRIPT)
- WMIC.exe (PID: 13744)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 11344)
Connects to FTP
- F.exe (PID: 12576)
- Jay.exe (PID: 13408)
Deletes system .NET executable
- Client-built.exe (PID: 13256)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 14004)
Executes as Windows Service
- WmiApSrv.exe (PID: 14668)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 14004)
Process copies executable file
- powershell.exe (PID: 14228)
Loads DLL from Mozilla Firefox
- Vb5HUIU.exe (PID: 7612)
INFO
Create files in a temporary directory
- main.exe (PID: 2076)
- build.exe (PID: 5348)
- catqw.exe (PID: 7216)
- TempSpoofer.exe (PID: 7224)
- Monotone.exe (PID: 7208)
- Helper.exe (PID: 7176)
- TempSpoofer.exe (PID: 7496)
- TempSpoofer.exe (PID: 7296)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7396)
- TempSpoofer.exe (PID: 7232)
- Monotone.exe (PID: 7184)
- kj.exe (PID: 6836)
- TempSpoofer.exe (PID: 7664)
- TempSpoofer.exe (PID: 7636)
- TempSpoofer.exe (PID: 7648)
- UniversalSpoofer.exe (PID: 8620)
- Setup.exe (PID: 10988)
- Setup.exe (PID: 10952)
- Prolin.exe (PID: 10876)
- Bugsoft.exe (PID: 13584)
- Amus.exe (PID: 13568)
- Axam.a.exe (PID: 13528)
- PluGman23333%20233.exe (PID: 7628)
- donie30.exe (PID: 7544)
- msconfig.exe (PID: 12024)
- your_app.exe (PID: 11208)
- bravo29.exe (PID: 8292)
- cabal.exe (PID: 14200)
- 4De3.exe (PID: 17212)
- Axam.exe (PID: 19048)
- amnew.exe (PID: 14136)
- Axam.exe (PID: 10744)
- Axam.exe (PID: 8496)
- Axam.exe (PID: 8008)
- Axam.exe (PID: 7968)
- Axam.exe (PID: 8088)
- ap.exe (PID: 9344)
- Axam.exe (PID: 9004)
- Axam.exe (PID: 8580)
- Axam.exe (PID: 8952)
- Vb5HUIU.exe (PID: 7612)
- Axam.exe (PID: 10600)
- quasarat.exe (PID: 14276)
- Axam.exe (PID: 10612)
- cvtres.exe (PID: 16968)
- csc.exe (PID: 10632)
- cvtres.exe (PID: 12824)
- csc.exe (PID: 10508)
- Axam.exe (PID: 3756)
- dumer.exe (PID: 13432)
- varen.exe (PID: 9920)
- Axam.exe (PID: 17348)
- Axam.exe (PID: 5416)
- Axam.exe (PID: 17272)
- Axam.exe (PID: 5424)
- Axam.exe (PID: 14828)
- Axam.exe (PID: 16892)
- Axam.exe (PID: 14984)
- Axam.exe (PID: 13464)
- Axam.exe (PID: 16908)
- Axam.exe (PID: 12044)
- Axam.exe (PID: 17740)
- Axam.exe (PID: 3724)
- Axam.exe (PID: 13668)
- Axam.exe (PID: 13164)
- Axam.exe (PID: 18076)
- csc.exe (PID: 16960)
- Axam.exe (PID: 12500)
- cvtres.exe (PID: 8084)
- Axam.exe (PID: 15024)
- Axam.exe (PID: 9240)
- WannaCry.exe (PID: 14292)
- Axam.exe (PID: 4560)
- Axam.exe (PID: 16444)
- Axam.exe (PID: 4820)
- Axam.exe (PID: 10584)
- Axam.exe (PID: 17512)
- Axam.exe (PID: 1520)
- Axam.exe (PID: 17896)
- Axam.exe (PID: 4120)
- Axam.exe (PID: 9868)
- Axam.exe (PID: 18880)
- Axam.exe (PID: 7320)
- Axam.exe (PID: 11628)
- Axam.exe (PID: 18988)
- Axam.exe (PID: 12124)
- Axam.exe (PID: 18264)
- Axam.exe (PID: 17984)
- Axam.exe (PID: 16408)
- quasarat.exe (PID: 10420)
- Axam.exe (PID: 1068)
- Axam.exe (PID: 17472)
- Axam.exe (PID: 11092)
- Axam.exe (PID: 12720)
- Axam.exe (PID: 16064)
- Axam.exe (PID: 7868)
Reads the computer name
- main.exe (PID: 2076)
- main.exe (PID: 3788)
- build.exe (PID: 5348)
- sFFG7Wg.exe (PID: 2388)
- swagggg.exe (PID: 7192)
- Helper.exe (PID: 7176)
- Monotone.exe (PID: 7208)
- TempSpoofer.exe (PID: 7224)
- Monotone.exe (PID: 2708)
- VXHDH.exe (PID: 4044)
- Monotone.exe (PID: 7184)
- TempSpoofer.exe (PID: 7232)
- TempSpoofer.exe (PID: 7296)
- TempSpoofer.exe (PID: 7396)
- TempSpoofer.exe (PID: 7496)
- 1.exe (PID: 7600)
- Vb5HUIU.exe (PID: 7612)
- donie30.exe (PID: 7544)
- trails.exe (PID: 7796)
- K.exe (PID: 7704)
- TempSpoofer.exe (PID: 7664)
- TempSpoofer.exe (PID: 7648)
- TempSpoofer.exe (PID: 7636)
- installs.exe (PID: 8560)
- bravo29.exe (PID: 8292)
- tcp_windows_amd64.exe (PID: 9440)
- e.exe (PID: 7752)
- UniversalSpoofer.exe (PID: 8620)
- Crypt.exe (PID: 8480)
- startud.exe (PID: 9168)
- game3.exe (PID: 7588)
- LOIC.exe (PID: 9864)
- T.exe (PID: 8248)
- syspool.exe (PID: 9924)
- mexx.exe (PID: 7692)
- demonx64.exe (PID: 11140)
- demon.exe (PID: 11072)
- march.exe (PID: 11052)
- porn.exe (PID: 10788)
- ap.exe (PID: 9344)
- 90.exe (PID: 10888)
- test1.exe (PID: 9988)
- Ganja39.exe (PID: 11160)
- XClient.exe (PID: 8568)
- Ganja195.exe (PID: 10916)
- Ganja90.exe (PID: 11184)
- Ganja199.exe (PID: 11916)
- baboon.exe (PID: 11112)
- https.exe (PID: 11124)
- trip.exe (PID: 11032)
- klass.exe (PID: 12148)
- ls.exe (PID: 3844)
- WxWorkMultiOpen.exe (PID: 9900)
- WxWorkMultiOpen.exe (PID: 10008)
- Prolin.exe (PID: 10876)
- WxWorkMultiOpen.exe (PID: 9936)
- klass.exe (PID: 12528)
- Ganja128.exe (PID: 10760)
- cc.exe (PID: 11080)
- msconfig.exe (PID: 12024)
- ls.exe (PID: 12592)
- lol.exe (PID: 10664)
- Ganja165.exe (PID: 12676)
- Ganja99.exe (PID: 12688)
- Setup.exe (PID: 10988)
- WxWorkMultiOpen.exe (PID: 9964)
- WxWorkMultiOpen.exe (PID: 10340)
- WxWorkMultiOpen.exe (PID: 9880)
- WxWorkMultiOpen.exe (PID: 9996)
- WxWorkMultiOpen.exe (PID: 10020)
- WxWorkMultiOpen.exe (PID: 9892)
- WxWorkMultiOpen.exe (PID: 9912)
- WxWorkMultiOpen.exe (PID: 10672)
- WxWorkMultiOpen.exe (PID: 10680)
- WxWorkMultiOpen.exe (PID: 10308)
- WxWorkMultiOpen.exe (PID: 10032)
- svchost.exe (PID: 13124)
- Ganja35.exe (PID: 13156)
- Ganja174.exe (PID: 13248)
- ganja5.exe (PID: 10712)
- WxWorkMultiOpen.exe (PID: 10056)
- WxWorkMultiOpen.exe (PID: 10656)
- WxWorkMultiOpen.exe (PID: 10048)
- WxWorkMultiOpen.exe (PID: 9976)
- WxWorkMultiOpen.exe (PID: 10688)
- Ganja190.exe (PID: 13176)
- Ganja20.exe (PID: 13264)
- Client-built.exe (PID: 13256)
- Doppelganger.exe (PID: 10924)
- my%20file.exe (PID: 7564)
- Ganja36.exe (PID: 14208)
- 2.exe (PID: 14284)
- Ganja45.exe (PID: 12352)
- javaw.exe (PID: 13100)
- Ganja176.exe (PID: 14056)
- Ganja3.exe (PID: 14072)
- Ganja153.exe (PID: 14112)
- Ganja85.exe (PID: 14176)
- Ganja49.exe (PID: 14260)
- DumpAADUserPRT.exe (PID: 10704)
- Ganja13.exe (PID: 11252)
- quasarat.exe (PID: 14276)
- amnew.exe (PID: 14136)
- Ganja66.exe (PID: 14168)
- Bloxflip%20Predictor.exe (PID: 12624)
- Ganja172.exe (PID: 11436)
- foncar.exe (PID: 14216)
- cabal.exe (PID: 14200)
- Whisker.exe (PID: 10996)
- CryptoLocker.exe (PID: 14088)
- Bugsoft.exe (PID: 13584)
- F.exe (PID: 12576)
- Clien123.exe (PID: 14252)
- WannaCry.exe (PID: 14292)
- Setup.exe (PID: 10952)
- Ganja151.exe (PID: 13544)
- Amus.exe (PID: 13568)
- Jay.exe (PID: 13408)
- winsvchost.exe (PID: 14048)
- nbin22.exe (PID: 14128)
- Ganja61.exe (PID: 14120)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 14604)
- MSBuild.exe (PID: 12004)
- WxWorkMultiOpen.exe (PID: 10696)
- kajmak.exe (PID: 14064)
- 123.exe (PID: 14096)
- 90.exe (PID: 12400)
- Adobe.exe (PID: 11696)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 15216)
- crimkm.exe (PID: 7200)
- remcos.exe (PID: 13016)
- bot.exe (PID: 2216)
- your_app.exe (PID: 11208)
- c2_payload_aes.exe (PID: 13196)
- G7_Update.exe (PID: 14300)
- Axam.a.exe (PID: 13528)
- MSBuild.exe (PID: 6256)
- Anap.a.exe (PID: 9272)
- RegAsm.exe (PID: 16616)
- MSBuild.exe (PID: 16660)
- 4De3.exe (PID: 17212)
- AdobeART.exe (PID: 17596)
- AdobeART.exe (PID: 17828)
- AdobeART.exe (PID: 19332)
- Axam.exe (PID: 19048)
- Axam.exe (PID: 10744)
- Axam.exe (PID: 8008)
- Axam.exe (PID: 8088)
- Axam.exe (PID: 7968)
- Axam.exe (PID: 8496)
- varen.exe (PID: 9920)
- Axam.exe (PID: 8580)
- dumer.exe (PID: 13432)
- gaved.exe (PID: 10776)
- Axam.exe (PID: 9004)
- Axam.exe (PID: 8952)
- Axam.exe (PID: 10600)
- Axam.exe (PID: 10612)
- !WannaDecryptor!.exe (PID: 7000)
- Axam.exe (PID: 3756)
- server.exe (PID: 11192)
- Axam.exe (PID: 17348)
- Axam.exe (PID: 17272)
- Axam.exe (PID: 5416)
- Axam.exe (PID: 14828)
- Axam.exe (PID: 5424)
- Axam.exe (PID: 14984)
- Axam.exe (PID: 16908)
- Axam.exe (PID: 16892)
- Axam.exe (PID: 12044)
- Axam.exe (PID: 13668)
- Axam.exe (PID: 13464)
- Axam.exe (PID: 18076)
- Axam.exe (PID: 13164)
- Axam.exe (PID: 3724)
- Axam.exe (PID: 17740)
- Axam.exe (PID: 12500)
- Axam.exe (PID: 15024)
- Axam.exe (PID: 9240)
- aspnet_compiler.exe (PID: 14796)
- RegSvcs.exe (PID: 1164)
- Axam.exe (PID: 4560)
- Axam.exe (PID: 16444)
- Axam.exe (PID: 11628)
- Axam.exe (PID: 4820)
- Axam.exe (PID: 17512)
- Axam.exe (PID: 17896)
- Axam.exe (PID: 1520)
- Axam.exe (PID: 10584)
- Axam.exe (PID: 18880)
- Axam.exe (PID: 9868)
- Axam.exe (PID: 7320)
- Axam.exe (PID: 18988)
- Axam.exe (PID: 18264)
- Axam.exe (PID: 4120)
- Axam.exe (PID: 12124)
- quasarat.exe (PID: 10420)
- Axam.exe (PID: 17984)
- Axam.exe (PID: 16408)
- Axam.exe (PID: 1068)
- ShellExperienceHost.exe (PID: 15736)
- Axam.exe (PID: 17472)
- Axam.exe (PID: 12720)
- Axam.exe (PID: 11092)
- Axam.exe (PID: 16064)
- Axam.exe (PID: 13664)
- Axam.exe (PID: 7868)
- Axam.exe (PID: 11136)
- Axam.exe (PID: 6388)
- Axam.exe (PID: 8888)
Checks supported languages
- main.exe (PID: 2076)
- sFFG7Wg.exe (PID: 2388)
- VXHDH.exe (PID: 4044)
- TempSpoofer.exe (PID: 7224)
- catqw.exe (PID: 7216)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7232)
- swagggg.exe (PID: 7192)
- Helper.exe (PID: 7176)
- Monotone.exe (PID: 7208)
- kj.exe (PID: 6836)
- TempSpoofer.exe (PID: 7396)
- crimkm.exe (PID: 7200)
- TempSpoofer.exe (PID: 7296)
- TempSpoofer.exe (PID: 7496)
- build.exe (PID: 5348)
- Monotone.exe (PID: 7184)
- main.exe (PID: 3788)
- my%20file.exe (PID: 7564)
- 1.exe (PID: 7600)
- donie30.exe (PID: 7544)
- Vb5HUIU.exe (PID: 7612)
- mexx.exe (PID: 7692)
- trails.exe (PID: 7796)
- TempSpoofer.exe (PID: 7636)
- TempSpoofer.exe (PID: 7648)
- PluGman23333%20233.exe (PID: 7628)
- TempSpoofer.exe (PID: 7664)
- e.exe (PID: 7752)
- T.exe (PID: 8248)
- K.exe (PID: 7704)
- bravo29.exe (PID: 8292)
- XClient.exe (PID: 8568)
- Crypt.exe (PID: 8480)
- installs.exe (PID: 8560)
- game3.exe (PID: 7588)
- UniversalSpoofer.exe (PID: 8620)
- lollo.exe (PID: 9060)
- startud.exe (PID: 9168)
- ap.exe (PID: 9344)
- tcp_windows_amd64.exe (PID: 9440)
- Worldofficee.exe (PID: 8132)
- LOIC.exe (PID: 9864)
- syspool.exe (PID: 9924)
- CryptoWall.exe (PID: 10264)
- ganja5.exe (PID: 10712)
- Ganja128.exe (PID: 10760)
- Ganja180.exe (PID: 10744)
- porn.exe (PID: 10788)
- lol.exe (PID: 10664)
- demonx64.exe (PID: 11140)
- demon.exe (PID: 11072)
- march.exe (PID: 11052)
- 90.exe (PID: 10888)
- Prolin.exe (PID: 10876)
- cc.exe (PID: 11080)
- Ganja39.exe (PID: 11160)
- Ganja90.exe (PID: 11184)
- baboon.exe (PID: 11112)
- https.exe (PID: 11124)
- Setup.exe (PID: 10988)
- Ganja195.exe (PID: 10916)
- trip.exe (PID: 11032)
- Ganja199.exe (PID: 11916)
- msconfig.exe (PID: 12024)
- Worldoffice.exe (PID: 10960)
- test1.exe (PID: 9988)
- Setup.exe (PID: 10952)
- ls.exe (PID: 3844)
- klass.exe (PID: 12148)
- WxWorkMultiOpen.exe (PID: 9900)
- WxWorkMultiOpen.exe (PID: 10008)
- WxWorkMultiOpen.exe (PID: 9936)
- klass.exe (PID: 12528)
- ls.exe (PID: 12592)
- Ganja99.exe (PID: 12688)
- Bloxflip%20Predictor.exe (PID: 12624)
- Ganja165.exe (PID: 12676)
- WxWorkMultiOpen.exe (PID: 10020)
- WxWorkMultiOpen.exe (PID: 9880)
- WxWorkMultiOpen.exe (PID: 10672)
- WxWorkMultiOpen.exe (PID: 9964)
- WxWorkMultiOpen.exe (PID: 9892)
- WxWorkMultiOpen.exe (PID: 9912)
- WxWorkMultiOpen.exe (PID: 10688)
- WxWorkMultiOpen.exe (PID: 9996)
- Whisker.exe (PID: 10996)
- WxWorkMultiOpen.exe (PID: 10308)
- WxWorkMultiOpen.exe (PID: 10680)
- javaw.exe (PID: 13100)
- WxWorkMultiOpen.exe (PID: 10340)
- WxWorkMultiOpen.exe (PID: 10032)
- svchost.exe (PID: 13124)
- Ganja35.exe (PID: 13156)
- DumpAADUserPRT.exe (PID: 10704)
- Client-built.exe (PID: 13256)
- Ganja174.exe (PID: 13248)
- WxWorkMultiOpen.exe (PID: 10048)
- WxWorkMultiOpen.exe (PID: 10656)
- WxWorkMultiOpen.exe (PID: 9976)
- WxWorkMultiOpen.exe (PID: 10056)
- Jay.exe (PID: 13408)
- Ganja190.exe (PID: 13176)
- Ganja20.exe (PID: 13264)
- Ganja151.exe (PID: 13544)
- Amus.exe (PID: 13568)
- Bugsoft.exe (PID: 13584)
- Doppelganger.exe (PID: 10924)
- Ganja176.exe (PID: 14056)
- Ganja61.exe (PID: 14120)
- CryptoLocker.exe (PID: 14088)
- kajmak.exe (PID: 14064)
- amnew.exe (PID: 14136)
- Ganja121.exe (PID: 14184)
- Ganja36.exe (PID: 14208)
- L2.exe (PID: 14152)
- 2.exe (PID: 14284)
- bot.exe (PID: 2216)
- winxclient.exe (PID: 12508)
- F.exe (PID: 12576)
- quasarat.exe (PID: 14276)
- Ganja132.exe (PID: 14308)
- Ganja45.exe (PID: 12352)
- Ganja54.exe (PID: 12996)
- WxWorkMultiOpen.exe (PID: 10696)
- Ganja153.exe (PID: 14112)
- Ganja3.exe (PID: 14072)
- Ganja85.exe (PID: 14176)
- loader.exe (PID: 14104)
- cabal.exe (PID: 14200)
- foncar.exe (PID: 14216)
- G7_Update.exe (PID: 14300)
- WannaCry.exe (PID: 14292)
- Anap.a.exe (PID: 9272)
- your_app.exe (PID: 11208)
- Ganja13.exe (PID: 11252)
- Ganja172.exe (PID: 11436)
- Axam.a.exe (PID: 13528)
- Ganja49.exe (PID: 14260)
- ganja2.exe (PID: 11892)
- 123.exe (PID: 14096)
- Clien123.exe (PID: 14252)
- Ganja66.exe (PID: 14168)
- winsvchost.exe (PID: 14048)
- nbin22.exe (PID: 14128)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 14604)
- 90.exe (PID: 12400)
- pe2shc.exe (PID: 13576)
- MSBuild.exe (PID: 12004)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 15216)
- esp32.exe (PID: 13552)
- cron1.exe (PID: 14244)
- remcos.exe (PID: 13016)
- rickroll.exe (PID: 13560)
- c2_payload_aes.exe (PID: 13196)
- cron123123213.exe (PID: 13316)
- agent.exe (PID: 14332)
- esp.exe (PID: 14192)
- test.exe (PID: 16452)
- MSBuild.exe (PID: 6256)
- RegAsm.exe (PID: 16616)
- 4De3.exe (PID: 17212)
- MSBuild.exe (PID: 16660)
- AdobeART.exe (PID: 17596)
- dumer.exe (PID: 18156)
- AdobeART.exe (PID: 17828)
- Setup.exe (PID: 18148)
- Adobe.exe (PID: 11696)
- Axam.exe (PID: 19048)
- Setup.exe (PID: 18932)
- AdobeART.exe (PID: 19332)
- Axam.exe (PID: 10744)
- svchost.com (PID: 18808)
- server.exe (PID: 11192)
- Axam.exe (PID: 8496)
- Axam.exe (PID: 8008)
- AdobeART.exe (PID: 7620)
- Axam.exe (PID: 7968)
- Axam.exe (PID: 8088)
- Axam.exe (PID: 8580)
- Axam.exe (PID: 9004)
- Axam.exe (PID: 8952)
- gaved.exe (PID: 10776)
- varen.exe (PID: 9920)
- dumer.exe (PID: 13432)
- Axam.exe (PID: 10600)
- Axam.exe (PID: 10612)
- csc.exe (PID: 10632)
- csc.exe (PID: 10508)
- cvtres.exe (PID: 16968)
- cvtres.exe (PID: 12824)
- Axam.exe (PID: 3756)
- !WannaDecryptor!.exe (PID: 7000)
- Axam.exe (PID: 17348)
- Axam.exe (PID: 17272)
- Axam.exe (PID: 5416)
- Axam.exe (PID: 14828)
- csc.exe (PID: 16960)
- chcp.com (PID: 14124)
- Axam.exe (PID: 5424)
- Axam.exe (PID: 16892)
- Axam.exe (PID: 14984)
- Axam.exe (PID: 17740)
- Axam.exe (PID: 12044)
- Axam.exe (PID: 3724)
- Axam.exe (PID: 13464)
- Axam.exe (PID: 16908)
- Axam.exe (PID: 13668)
- Axam.exe (PID: 18076)
- Axam.exe (PID: 12500)
- Axam.exe (PID: 13164)
- cvtres.exe (PID: 8084)
- Axam.exe (PID: 15024)
- Axam.exe (PID: 9240)
- aspnet_compiler.exe (PID: 14796)
- Axam.exe (PID: 4560)
- RegSvcs.exe (PID: 1164)
- Axam.exe (PID: 17512)
- Axam.exe (PID: 16444)
- Axam.exe (PID: 9868)
- Axam.exe (PID: 10584)
- Axam.exe (PID: 1520)
- Axam.exe (PID: 4820)
- Axam.exe (PID: 18880)
- Axam.exe (PID: 7320)
- Axam.exe (PID: 11628)
- Axam.exe (PID: 18988)
- Axam.exe (PID: 4120)
- Axam.exe (PID: 17896)
- Axam.exe (PID: 18264)
- Axam.exe (PID: 12124)
- quasarat.exe (PID: 10420)
- Axam.exe (PID: 17984)
- Axam.exe (PID: 16408)
- Axam.exe (PID: 1068)
- Axam.exe (PID: 17472)
- ShellExperienceHost.exe (PID: 15736)
- Axam.exe (PID: 16064)
- Axam.exe (PID: 11092)
- Axam.exe (PID: 12720)
- Axam.exe (PID: 13664)
- csc.exe (PID: 6152)
- cvtres.exe (PID: 9312)
- Axam.exe (PID: 11136)
- Axam.exe (PID: 7868)
- csc.exe (PID: 9784)
- cvtres.exe (PID: 17608)
- Axam.exe (PID: 6388)
- Axam.exe (PID: 8888)
The sample compiled with english language support
- main.exe (PID: 2076)
- main.exe (PID: 3788)
- Setup.exe (PID: 10952)
- Setup.exe (PID: 10988)
- Prolin.exe (PID: 10876)
- WannaCry.exe (PID: 14292)
- Axam.a.exe (PID: 13528)
- 123.exe (PID: 14096)
- Amus.exe (PID: 13568)
- varen.exe (PID: 9920)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 8632)
- dumer.exe (PID: 13432)
- powershell.exe (PID: 14144)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- cmd.exe (PID: 6936)
- swagggg.exe (PID: 7192)
Checks proxy server information
- main.exe (PID: 3788)
- sFFG7Wg.exe (PID: 2388)
- demonx64.exe (PID: 11140)
- demon.exe (PID: 11072)
- march.exe (PID: 11052)
- baboon.exe (PID: 11112)
- mexx.exe (PID: 7692)
- https.exe (PID: 11124)
- Vb5HUIU.exe (PID: 7612)
- svchost.exe (PID: 13124)
- VXHDH.exe (PID: 4044)
- trip.exe (PID: 11032)
- c2_payload_aes.exe (PID: 13196)
- cabal.exe (PID: 14200)
- L2.exe (PID: 14152)
- explorer.exe (PID: 4772)
- svchost.exe (PID: 13844)
- Ganja128.exe (PID: 10760)
- bot.exe (PID: 2216)
- Ganja61.exe (PID: 14120)
- ganja5.exe (PID: 10712)
- LOIC.exe (PID: 9864)
- Ganja151.exe (PID: 13544)
- Client-built.exe (PID: 13256)
- powershell.exe (PID: 9816)
- quasarat.exe (PID: 14276)
- powershell.exe (PID: 9952)
- varen.exe (PID: 9920)
- Jay.exe (PID: 13408)
- dumer.exe (PID: 13432)
- gaved.exe (PID: 10776)
- powershell.exe (PID: 13536)
- powershell.exe (PID: 12928)
- F.exe (PID: 12576)
- build.exe (PID: 5348)
- WerFault.exe (PID: 15500)
- WerFault.exe (PID: 14440)
- WerFault.exe (PID: 17748)
- WerFault.exe (PID: 15416)
- powershell.exe (PID: 8020)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8552)
- installs.exe (PID: 8560)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 13608)
- RegSvcs.exe (PID: 1164)
- powershell.exe (PID: 10724)
- slui.exe (PID: 3388)
- powershell.exe (PID: 14228)
- powershell.exe (PID: 14144)
Reads Internet Explorer settings
- mshta.exe (PID: 4044)
- mshta.exe (PID: 3844)
- mshta.exe (PID: 1052)
- mshta.exe (PID: 1180)
- mshta.exe (PID: 5496)
- mshta.exe (PID: 1468)
- mshta.exe (PID: 9272)
- mshta.exe (PID: 9632)
- mshta.exe (PID: 9788)
- mshta.exe (PID: 9796)
Reads the machine GUID from the registry
- build.exe (PID: 5348)
- sFFG7Wg.exe (PID: 2388)
- TempSpoofer.exe (PID: 7224)
- Helper.exe (PID: 7176)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7232)
- TempSpoofer.exe (PID: 7296)
- swagggg.exe (PID: 7192)
- Monotone.exe (PID: 7208)
- 1.exe (PID: 7600)
- TempSpoofer.exe (PID: 7496)
- TempSpoofer.exe (PID: 7396)
- Monotone.exe (PID: 7184)
- TempSpoofer.exe (PID: 7664)
- K.exe (PID: 7704)
- TempSpoofer.exe (PID: 7636)
- trails.exe (PID: 7796)
- TempSpoofer.exe (PID: 7648)
- Vb5HUIU.exe (PID: 7612)
- game3.exe (PID: 7588)
- CryptoWall.exe (PID: 10264)
- T.exe (PID: 8248)
- VXHDH.exe (PID: 4044)
- startud.exe (PID: 9168)
- UniversalSpoofer.exe (PID: 8620)
- LOIC.exe (PID: 9864)
- ap.exe (PID: 9344)
- my%20file.exe (PID: 7564)
- mexx.exe (PID: 7692)
- trip.exe (PID: 11032)
- installs.exe (PID: 8560)
- cc.exe (PID: 11080)
- XClient.exe (PID: 8568)
- WannaCry.exe (PID: 14292)
- ganja5.exe (PID: 10712)
- Client-built.exe (PID: 13256)
- Ganja128.exe (PID: 10760)
- javaw.exe (PID: 13100)
- quasarat.exe (PID: 14276)
- Jay.exe (PID: 13408)
- cabal.exe (PID: 14200)
- 90.exe (PID: 10888)
- Ganja61.exe (PID: 14120)
- Ganja151.exe (PID: 13544)
- F.exe (PID: 12576)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 14604)
- Amus.exe (PID: 13568)
- Clien123.exe (PID: 14252)
- foncar.exe (PID: 14216)
- bot.exe (PID: 2216)
- c2_payload_aes.exe (PID: 13196)
- RegAsm.exe (PID: 16616)
- MSBuild.exe (PID: 12004)
- AdobeART.exe (PID: 17596)
- MSBuild.exe (PID: 16660)
- Crypt.exe (PID: 8480)
- AdobeART.exe (PID: 19332)
- csc.exe (PID: 10632)
- csc.exe (PID: 10508)
- server.exe (PID: 11192)
- csc.exe (PID: 16960)
- aspnet_compiler.exe (PID: 14796)
- RegSvcs.exe (PID: 1164)
- varen.exe (PID: 9920)
- csc.exe (PID: 6152)
- csc.exe (PID: 9784)
Creates files or folders in the user directory
- Taskmgr.exe (PID: 3820)
- syspool.exe (PID: 9924)
- test1.exe (PID: 9988)
- lol.exe (PID: 10664)
- explorer.exe (PID: 11328)
- my%20file.exe (PID: 7564)
- Ganja180.exe (PID: 10744)
- sFFG7Wg.exe (PID: 2388)
- loader.exe (PID: 14104)
- CryptoLocker.exe (PID: 14088)
- swagggg.exe (PID: 7192)
- trails.exe (PID: 7796)
- Amus.exe (PID: 13568)
- 123.exe (PID: 14096)
- Axam.a.exe (PID: 13528)
- Bloxflip%20Predictor.exe (PID: 12624)
- explorer.exe (PID: 4772)
- ap.exe (PID: 9344)
- Client-built.exe (PID: 13256)
- Vb5HUIU.exe (PID: 7612)
- dumer.exe (PID: 13432)
- varen.exe (PID: 9920)
- WerFault.exe (PID: 14440)
- WerFault.exe (PID: 15500)
- WannaCry.exe (PID: 14292)
- WerFault.exe (PID: 17748)
- WerFault.exe (PID: 15416)
Reads the software policy settings
- sFFG7Wg.exe (PID: 2388)
- trails.exe (PID: 7796)
- foncar.exe (PID: 14216)
- MSBuild.exe (PID: 12004)
- mexx.exe (PID: 7692)
- MSBuild.exe (PID: 16660)
- MSBuild.exe (PID: 6256)
- Helper.exe (PID: 7176)
- Vb5HUIU.exe (PID: 7612)
- WerFault.exe (PID: 15500)
- WerFault.exe (PID: 14440)
- WerFault.exe (PID: 17748)
- build.exe (PID: 5348)
- WerFault.exe (PID: 15416)
- aspnet_compiler.exe (PID: 14796)
- RegSvcs.exe (PID: 1164)
- slui.exe (PID: 3388)
- varen.exe (PID: 9920)
Reads mouse settings
- kj.exe (PID: 6836)
- catqw.exe (PID: 7216)
- PluGman23333%20233.exe (PID: 7628)
Reads Environment values
- swagggg.exe (PID: 7192)
- Vb5HUIU.exe (PID: 7612)
- ganja5.exe (PID: 10712)
- Ganja128.exe (PID: 10760)
- Ganja61.exe (PID: 14120)
- Ganja151.exe (PID: 13544)
- trails.exe (PID: 7796)
- TempSpoofer.exe (PID: 7296)
- TempSpoofer.exe (PID: 7396)
- Helper.exe (PID: 7176)
- TempSpoofer.exe (PID: 7496)
- TempSpoofer.exe (PID: 7664)
- TempSpoofer.exe (PID: 7648)
- TempSpoofer.exe (PID: 7636)
- Monotone.exe (PID: 7184)
- TempSpoofer.exe (PID: 7232)
- Monotone.exe (PID: 2708)
- TempSpoofer.exe (PID: 7224)
- UniversalSpoofer.exe (PID: 8620)
- build.exe (PID: 5348)
- Monotone.exe (PID: 7208)
- bot.exe (PID: 2216)
- javaw.exe (PID: 13100)
- startud.exe (PID: 9168)
- installs.exe (PID: 8560)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 3820)
- svchost.exe (PID: 13844)
- cscript.exe (PID: 18820)
- WMIC.exe (PID: 13744)
- explorer.exe (PID: 4772)
Launching a file from a Registry key
- 1.exe (PID: 7600)
- e.exe (PID: 7752)
- syspool.exe (PID: 9924)
- explorer.exe (PID: 11328)
- klass.exe (PID: 12148)
- ls.exe (PID: 3844)
- msconfig.exe (PID: 12024)
- loader.exe (PID: 14104)
- WannaCry.exe (PID: 14292)
- winsvchost.exe (PID: 14048)
- {34184A33-0407-212E-3300-09040709E2C2}.exe (PID: 14604)
- Adobe.exe (PID: 11696)
- remcos.exe (PID: 13016)
- Axam.a.exe (PID: 13528)
- Amus.exe (PID: 13568)
- explorer.exe (PID: 4772)
- AdobeART.exe (PID: 17828)
- Bloxflip%20Predictor.exe (PID: 12624)
- Axam.exe (PID: 19048)
- Axam.exe (PID: 10744)
- AdobeART.exe (PID: 7620)
- Axam.exe (PID: 8008)
- Axam.exe (PID: 8088)
- Axam.exe (PID: 8496)
- Axam.exe (PID: 8580)
- Axam.exe (PID: 7968)
- Axam.exe (PID: 9004)
- Axam.exe (PID: 8952)
- quasarat.exe (PID: 14276)
- Axam.exe (PID: 10600)
- Axam.exe (PID: 10612)
- Axam.exe (PID: 3756)
- server.exe (PID: 11192)
- Axam.exe (PID: 5416)
- Axam.exe (PID: 17272)
- Axam.exe (PID: 17348)
- Axam.exe (PID: 14828)
- Axam.exe (PID: 5424)
- Axam.exe (PID: 14984)
- Axam.exe (PID: 16892)
- Axam.exe (PID: 16908)
- Axam.exe (PID: 12044)
- Axam.exe (PID: 13668)
- Axam.exe (PID: 13464)
- Axam.exe (PID: 3724)
- Axam.exe (PID: 17740)
- Axam.exe (PID: 18076)
- Axam.exe (PID: 12500)
- Axam.exe (PID: 15024)
- Axam.exe (PID: 9240)
- Axam.exe (PID: 13164)
- Axam.exe (PID: 4560)
- Axam.exe (PID: 16444)
- Axam.exe (PID: 9868)
- Axam.exe (PID: 18880)
- Axam.exe (PID: 10584)
- Axam.exe (PID: 4820)
- Axam.exe (PID: 7320)
- Axam.exe (PID: 17512)
- Axam.exe (PID: 11628)
- Axam.exe (PID: 1520)
- Axam.exe (PID: 17896)
- Axam.exe (PID: 4120)
- dumer.exe (PID: 13432)
- Axam.exe (PID: 18988)
- Axam.exe (PID: 12124)
- Axam.exe (PID: 18264)
- Axam.exe (PID: 17984)
- Axam.exe (PID: 16408)
- Axam.exe (PID: 1068)
- Axam.exe (PID: 17472)
- Axam.exe (PID: 11092)
- Axam.exe (PID: 12720)
- Axam.exe (PID: 16064)
- Axam.exe (PID: 13664)
- Axam.exe (PID: 7868)
- Axam.exe (PID: 11136)
- Axam.exe (PID: 8888)
- Axam.exe (PID: 6388)
Creates files in the program directory
- 1.exe (PID: 7600)
- e.exe (PID: 7752)
- Ganja39.exe (PID: 11160)
- Ganja90.exe (PID: 11184)
- kajmak.exe (PID: 14064)
- bot.exe (PID: 2216)
- remcos.exe (PID: 13016)
- Ganja128.exe (PID: 10760)
- WannaCry.exe (PID: 14292)
Disables trace logs
- mexx.exe (PID: 7692)
- Vb5HUIU.exe (PID: 7612)
- Ganja128.exe (PID: 10760)
- ganja5.exe (PID: 10712)
- Ganja151.exe (PID: 13544)
- Ganja61.exe (PID: 14120)
- VXHDH.exe (PID: 4044)
- bot.exe (PID: 2216)
- trip.exe (PID: 11032)
- cabal.exe (PID: 14200)
- Client-built.exe (PID: 13256)
- powershell.exe (PID: 9816)
- powershell.exe (PID: 9952)
- quasarat.exe (PID: 14276)
- Jay.exe (PID: 13408)
- powershell.exe (PID: 13536)
- powershell.exe (PID: 12928)
- F.exe (PID: 12576)
- build.exe (PID: 5348)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8020)
- installs.exe (PID: 8560)
- RegSvcs.exe (PID: 1164)
- powershell.exe (PID: 10724)
- powershell.exe (PID: 14228)
- powershell.exe (PID: 14144)
Launching a file from the Startup directory
- explorer.exe (PID: 11328)
- trails.exe (PID: 7796)
- bot.exe (PID: 2216)
- Axam.a.exe (PID: 13528)
- Bloxflip%20Predictor.exe (PID: 12624)
- Setup.exe (PID: 10952)
Process checks whether UAC notifications are on
- my%20file.exe (PID: 7564)
Process checks computer location settings
- e.exe (PID: 7752)
- test1.exe (PID: 9988)
- lol.exe (PID: 10664)
- donie30.exe (PID: 7544)
- Setup.exe (PID: 10988)
- bravo29.exe (PID: 8292)
- 90.exe (PID: 12400)
- Setup.exe (PID: 10952)
- Bloxflip%20Predictor.exe (PID: 12624)
- your_app.exe (PID: 11208)
- G7_Update.exe (PID: 14300)
- 123.exe (PID: 14096)
- Crypt.exe (PID: 8480)
- amnew.exe (PID: 14136)
- 4De3.exe (PID: 17212)
- ap.exe (PID: 9344)
- Ganja128.exe (PID: 10760)
- quasarat.exe (PID: 14276)
- varen.exe (PID: 9920)
- dumer.exe (PID: 13432)
- quasarat.exe (PID: 10420)
- Helper.exe (PID: 7176)
PyInstaller has been detected (YARA)
- main.exe (PID: 2076)
The sample compiled with chinese language support
- main.exe (PID: 3788)
Manual execution by a user
- cmmon32.exe (PID: 10680)
The sample compiled with Italian language support
- main.exe (PID: 3788)
The sample compiled with korean language support
- G7_Update.exe (PID: 14300)
- main.exe (PID: 3788)
The sample compiled with turkish language support
- main.exe (PID: 3788)
The sample compiled with polish language support
- main.exe (PID: 3788)
Attempting to use instant messaging service
- svchost.exe (PID: 2200)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6304)
- powershell.exe (PID: 10976)
- powershell.exe (PID: 12760)
- powershell.exe (PID: 12928)
- powershell.exe (PID: 14268)
- build.exe (PID: 5348)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 14144)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 14004)
- powershell.exe (PID: 9952)
Checks whether the specified file exists (POWERSHELL)
- Helper.exe (PID: 7176)
- powershell.exe (PID: 14080)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 11172)
- powershell.exe (PID: 9816)
- powershell.exe (PID: 14228)
- powershell.exe (PID: 13536)
- powershell.exe (PID: 12928)
- powershell.exe (PID: 18472)
- powershell.exe (PID: 6380)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 8020)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 9188)
- powershell.exe (PID: 14144)
- powershell.exe (PID: 14004)
- powershell.exe (PID: 9952)
Reads CPU info
- Ganja128.exe (PID: 10760)
- ganja5.exe (PID: 10712)
- Ganja61.exe (PID: 14120)
- Ganja151.exe (PID: 13544)
- Vb5HUIU.exe (PID: 7612)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 10724)
The executable file from the user directory is run by the Powershell process
- Axam.exe (PID: 10600)
- Axam.exe (PID: 10612)
- Axam.exe (PID: 3756)
- Axam.exe (PID: 14984)
- Axam.exe (PID: 14828)
- Axam.exe (PID: 5416)
- Axam.exe (PID: 12044)
- Axam.exe (PID: 13464)
- Axam.exe (PID: 16908)
- Axam.exe (PID: 17740)
- Axam.exe (PID: 13668)
- Axam.exe (PID: 3724)
- Axam.exe (PID: 13164)
- Axam.exe (PID: 12500)
- Axam.exe (PID: 18076)
- Axam.exe (PID: 17512)
- Axam.exe (PID: 18988)
- Axam.exe (PID: 10584)
- Axam.exe (PID: 9868)
- Axam.exe (PID: 1520)
- Axam.exe (PID: 4820)
- Axam.exe (PID: 17896)
- Axam.exe (PID: 11628)
- Axam.exe (PID: 18880)
- Axam.exe (PID: 7320)
- Axam.exe (PID: 4120)
- Axam.exe (PID: 8888)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 10724)
- powershell.exe (PID: 9188)
- Helper.exe (PID: 7176)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8308)
- powershell.exe (PID: 13608)
- powershell.exe (PID: 7836)
- powershell.exe (PID: 8544)
- powershell.exe (PID: 14080)
- powershell.exe (PID: 8380)
- powershell.exe (PID: 8020)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 8488)
- powershell.exe (PID: 8552)
- powershell.exe (PID: 8516)
- powershell.exe (PID: 8320)
- powershell.exe (PID: 7908)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 12928)
- powershell.exe (PID: 9816)
Changes the display of characters in the console
- cmd.exe (PID: 11344)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 8020)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 9816)
Reads Windows Product ID
- powershell.exe (PID: 10724)
Reads the time zone
- Vb5HUIU.exe (PID: 7612)
Launching a file from Task Scheduler
- powershell.exe (PID: 14228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:19 18:59:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 154624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
591
Monitored processes
450
Malicious processes
97
Suspicious processes
87
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | mshta.exe bestdreamchaningwithbetterpower.hta | C:\Windows\System32\mshta.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\AppData\Roaming\Axam.exe" "C:\Users\admin\AppData\Local\Temp\3582-490\quasarat.exe" | C:\Users\admin\AppData\Roaming\Axam.exe | quasarat.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 1100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | catqw.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | catqw.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Services Installation Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1180 | mshta.exe weneedgreatattitudewithbestthinkingsforme.hta | C:\Windows\System32\mshta.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | mshta.exe supergoodthingswithbestfriendthingsbetterforme.hta | C:\Windows\System32\mshta.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | "C:\Users\admin\AppData\Roaming\Axam.exe" "C:\Users\admin\AppData\Roaming\4rpscvg5.ler0.exe" | C:\Users\admin\AppData\Roaming\Axam.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 1612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1636 | "ipconfig" /flushdns | C:\Windows\System32\ipconfig.exe | — | Vb5HUIU.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
406 319
Read events
404 661
Write events
1 571
Delete events
87
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000090230 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (3820) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000001102BA |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (2388) sFFG7Wg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2388) sFFG7Wg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2388) sFFG7Wg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010013000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000001A00000000000000640065006D0061006E00640064006900730074007200690062007500740069006F006E002E0070006E0067003E002000200000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000001100000000000000620065006C006F00770072006F00610064002E006A00700067003E002000200000001300000000000000630061006D006500720061006E0061006B00650064002E007200740066003E0020002000000014000000000000006C0069007300740069006E006700610072006500610073002E007200740066003E0020002000000018000000000000006F0072006900670069006E0061006C0070006F0073006900740069006F006E002E007200740066003E002000200000001600000000000000700072006500730065006E0074006100620069006C006900740079002E007200740066003E0020002000000016000000000000007000720069006E0074006500720066006F00720077006100720064002E007200740066003E0020002000000018000000000000007200650063006F006D006D0065006E00640065006400700061007000650072002E007200740066003E002000200000001B00000000000000720065006C006100740069006F006E00730068006900700070006C00610079006500720073002E007200740066003E002000200000001700000000000000720065006D006F007400650069006E0074006500720066006100630065002E0070006E0067003E002000200000000C000000000000006D00610069006E002E006500780065003E00200020000000050000000000000061003E005C002000000001000000000000000200010000000000000000000100000000000000020001000000000000000000110000000600000001000000130000000000000000004040000000001200000000000000000000000000803F0000004008000000803F000040400900000000000000404003000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F01000000000000000040020000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000000400000A0401100 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000801F4 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000801F4 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
813
Suspicious files
561
Text files
378
Unknown types
97
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_asyncio.pyd | executable | |
MD5:56F958EEBBC62305B4BF690D61C78E28 | SHA256:50631361EF074BE42D788818AF91D0301D22FA24A970F41F496D8272B92CFE31 | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_hashlib.pyd | executable | |
MD5:3E540EF568215561590DF215801B0F59 | SHA256:0ED7A6ED080499BC6C29D7113485A8A61BDBA93087B010FCA67D9B8289CBE6FA | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_socket.pyd | executable | |
MD5:566CB4D39B700C19DBD7175BD4F2B649 | SHA256:77EBA293FE03253396D7BB6E575187CD026C80766D7A345EB72AD92F0BBBC3AA | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_multiprocessing.pyd | executable | |
MD5:807DD90BE59EA971DAC06F3AAB4F2A7E | SHA256:B20DD6F5FAB31476D3D8D7F40CB5AB098117FA5612168C0FF4044945B6156D47 | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_ssl.pyd | executable | |
MD5:689F1ABAC772C9E4C2D3BAD3758CB398 | SHA256:D3A89AA7E4A1DF1151632A8A5CAF338C4DDDB674EC093BFDBC122ADC9DB28A97 | |||
| 2076 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI20762\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
573
TCP/UDP connections
8 493
DNS requests
330
Threats
2 398
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3788 | main.exe | GET | 200 | 172.245.95.29:80 | http://172.245.95.29/86/weseethebestthingswithbetterfuturegoodfor.hta | unknown | — | — | malicious |
3788 | main.exe | GET | 200 | 107.173.9.87:80 | http://107.173.9.87/90/weneedgreatattitudewithbestthinkingsforme.hta | unknown | — | — | malicious |
3788 | main.exe | GET | — | 185.156.72.61:80 | http://185.156.72.61/inc/miromangos.exe | unknown | — | — | malicious |
3788 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/files/978980897/Vb5HUIU.exe | unknown | — | — | unknown |
3788 | main.exe | GET | 200 | 8.137.98.198:8082 | http://8.137.98.198:8082/02.08.2022.exe | unknown | — | — | unknown |
3788 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/files/6053747383/O1sOUoo.exe | unknown | — | — | unknown |
3788 | main.exe | GET | 200 | 47.122.1.243:8000 | http://47.122.1.243:8000/02.08.2022.exe | unknown | — | — | unknown |
3788 | main.exe | GET | 200 | 109.120.137.172:80 | http://109.120.137.172/Crypt.exe | unknown | — | — | unknown |
3788 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/files/8052963817/ku56mNL.exe | unknown | — | — | unknown |
3788 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/files/6299414420/sFFG7Wg.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3688 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3788 | main.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
3788 | main.exe | 66.63.187.170:80 | — | QUADRANET-INTERNET-SERVICES | US | unknown |
3788 | main.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | unknown |
3788 | main.exe | 77.90.153.74:80 | — | K&K Kommunikationssysteme GmbH | GB | unknown |
3788 | main.exe | 107.173.9.87:80 | — | AS-COLOCROSSING | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
pub-75d9e09aa5304a0f9b7cd6c04c01b53e.r2.dev |
| unknown |
hbws.cc |
| unknown |
file.tuff.cat |
| unknown |
cptchvrf.com |
| unknown |
github.com |
| whitelisted |
bitbucket.org |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3788 | main.exe | Misc activity | ET INFO Observed Cloudflare R2 Public Bucket (r2 .dev) Domain in TLS SNI |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] CloudFlare Public R2.dev Bucket |
3788 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
3788 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3788 | main.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 60 |
2200 | svchost.exe | A Network Trojan was detected | ET INFO Observed DNS Query to Cloudflare R2 Public Bucket (r2 .dev) Domain |
3788 | main.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 36 |
3788 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3788 | main.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |