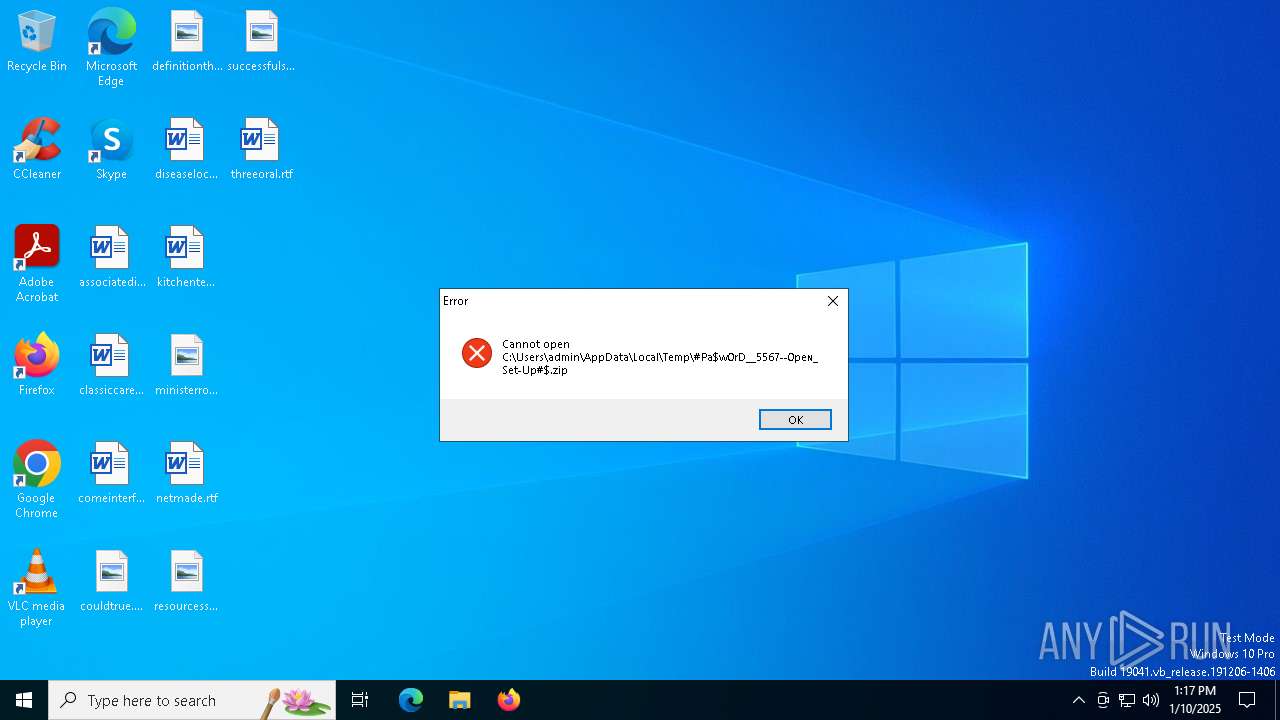
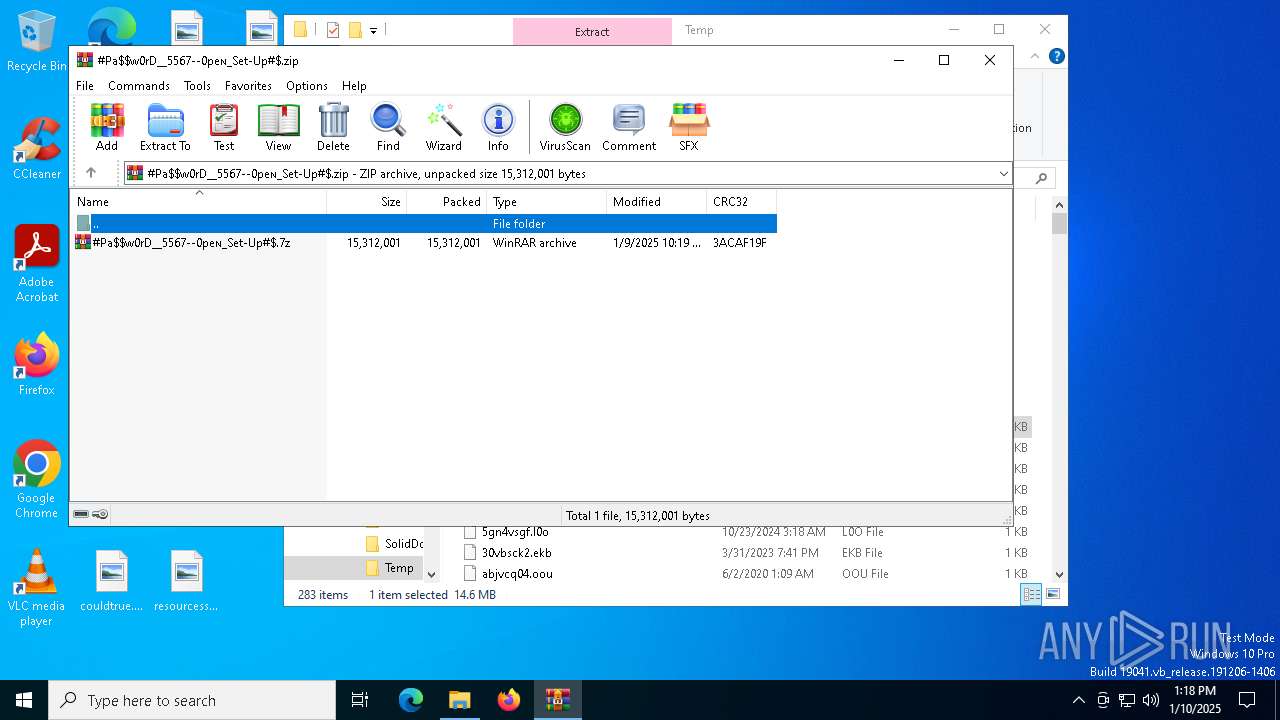
| File name: | #Pa$w0rD__5567--0peɴ_Set-Up#$.zip |
| Full analysis: | https://app.any.run/tasks/00c5c187-df90-4140-981f-f7aba6adda50 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 10, 2025, 13:17:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 031FC50C4F76B9BCDCEB31D7A34E7D89 |
| SHA1: | D985D8F056BD28069B43F27E88472ACE1D7F2867 |
| SHA256: | 56704F7CC295F766F2C8021540FE950D745C270E36A39ED630F1D5B17F514836 |
| SSDEEP: | 196608:y4Y9ABVS+shjJVvDcF8wm4qkSGrZ1sWsMlGz4v:y4lBVSVNJcKwLLthsMlGz4v |
MALICIOUS
Executing a file with an untrusted certificate
- Set-up.exe (PID: 4824)
AutoIt loader has been detected (YARA)
- Translator.com (PID: 880)
LUMMA mutex has been found
- Translator.com (PID: 880)
Actions looks like stealing of personal data
- Translator.com (PID: 880)
Steals credentials from Web Browsers
- Translator.com (PID: 880)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6248)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4512)
- WinRAR.exe (PID: 1904)
- Set-up.exe (PID: 4824)
Process drops legitimate windows executable
- WinRAR.exe (PID: 1904)
Application launched itself
- WinRAR.exe (PID: 4512)
- cmd.exe (PID: 2324)
Executing commands from ".cmd" file
- Set-up.exe (PID: 4824)
Starts CMD.EXE for commands execution
- Set-up.exe (PID: 4824)
- cmd.exe (PID: 2324)
Get information on the list of running processes
- cmd.exe (PID: 2324)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2324)
Starts application with an unusual extension
- cmd.exe (PID: 2324)
Starts the AutoIt3 executable file
- cmd.exe (PID: 2324)
The executable file from the user directory is run by the CMD process
- Translator.com (PID: 880)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1904)
Checks supported languages
- Set-up.exe (PID: 4824)
- extrac32.exe (PID: 6536)
- Translator.com (PID: 880)
Manual execution by a user
- WinRAR.exe (PID: 4512)
The sample compiled with english language support
- WinRAR.exe (PID: 1904)
The process uses the downloaded file
- WinRAR.exe (PID: 1904)
- Set-up.exe (PID: 4824)
- WinRAR.exe (PID: 4512)
Reads the computer name
- Set-up.exe (PID: 4824)
- extrac32.exe (PID: 6536)
- Translator.com (PID: 880)
Creates files or folders in the user directory
- Set-up.exe (PID: 4824)
- extrac32.exe (PID: 6536)
Process checks computer location settings
- Set-up.exe (PID: 4824)
Creates a new folder
- cmd.exe (PID: 6484)
Reads mouse settings
- Translator.com (PID: 880)
Reads the software policy settings
- Translator.com (PID: 880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:10 03:19:24 |
| ZipCRC: | 0x3acaf19f |
| ZipCompressedSize: | 15312001 |
| ZipUncompressedSize: | 15312001 |
| ZipFileName: | #Pa$w0rD__5567--0peɴ_Set-Up#$.7z |
Total processes
147
Monitored processes
18
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 880 | Translator.com E | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\404509\Translator.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa4512.41882\#Pa$w0rD__5567--0peɴ_Set-Up#$.7z | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2324 | "C:\Windows\System32\cmd.exe" /c move Brian Brian.cmd & Brian.cmd | C:\Windows\SysWOW64\cmd.exe | — | Set-up.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4320 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4512 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__5567--0peɴ_Set-Up#$.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4824 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Set-up.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Set-up.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6156 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__5567--0peɴ_Set-Up#$.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 239
Read events
6 215
Write events
24
Delete events
0
Modification events
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F0000000000000000000000000000000000000000000E001070000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F0000000000000000000000000000000000000000000980207000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000F40204000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (4512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
11
Suspicious files
20
Text files
64
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4512.41882\#Pa$w0rD__5567--0peɴ_Set-Up#$.7z | — | |
MD5:— | SHA256:— | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\bug73630.phpt | text | |
MD5:6F03CE9D564B2028FA84B7BBE2CCE694 | SHA256:E19540009179F8F6E4124DE072B9CC96E905BFE915A49E01B552C16A266A6501 | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\basic.txt | text | |
MD5:CD8731E6E98972FFC451EB0E69A6FD84 | SHA256:1324E0EC19AB2363D01FC8362C2A4F60F0C7695A827A7C198B4C8CC509AB8F9F | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\bug30519.phpt | text | |
MD5:AFA0449E3BA26766DEF9C408698CCF67 | SHA256:C7E6325DFC8C6C2F441835EB8D2ED201067AB43ABB3AFCAFD764D95A34DB7341 | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\DateTime_sub-spring-type2-type3.phpt | text | |
MD5:F4C4D3ABA4864D1410DD3F5555172D65 | SHA256:85EF989C19C86EFFB6D729246B3851EB05F5B9E7D113C787DAE6054D1D980E6E | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\019.phpt | text | |
MD5:6AC0B40208B70DAAA834C77FAF40BA4B | SHA256:347FA98F28A212F091BFAB3A1B57C2F9E70529F16A0EFC829B0DD5C382DD48AE | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\gh11244-005.phpt | text | |
MD5:2BEFE0EDF0D1F43AEEFEB1648259E31C | SHA256:9976A4D6DBFB50A3DAC688EEEE30B85DD56A7D473E766576D63EB417D1DE90B4 | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\openssl_get_md_methods.phpt | text | |
MD5:BA074AD271839C9E9537FE9688F4C024 | SHA256:C31486FA440DBC7BDD9684C63B18B099808B3102E36D76390BE7CD4BE39482CB | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\iterable_alias_redundancy_object_5.phpt | text | |
MD5:40CA3D3D061B52EAD7321800F95118F0 | SHA256:A2EE39C503457E705AA1562E2D6757F9B584C9C354CCFF276F87A75E6D0E6169 | |||
| 1904 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1904.44119\Resources\Data\match_flags3.phpt | text | |
MD5:27303F2F385FC5958922858A96BB5267 | SHA256:FB97804F00010745456C8A58775F0779877E2255A9CF61D7C523154A77A6BFD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
40
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2800 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2800 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7152 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7152 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2800 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5652 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
2800 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2800 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2800 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5064 | SearchApp.exe | 104.126.37.162:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
www.bing.com |
| unknown |
google.com |
| unknown |
crl.microsoft.com |
| unknown |
www.microsoft.com |
| unknown |
login.live.com |
| unknown |
ocsp.digicert.com |
| unknown |
go.microsoft.com |
| unknown |
slscr.update.microsoft.com |
| unknown |
fe3cr.delivery.mp.microsoft.com |
| unknown |