| File name: | resource-hacker_5ND-At1.exe |
| Full analysis: | https://app.any.run/tasks/e02c2c7c-c0f9-4fe3-b5c3-a4654bd6e76f |
| Verdict: | Malicious activity |
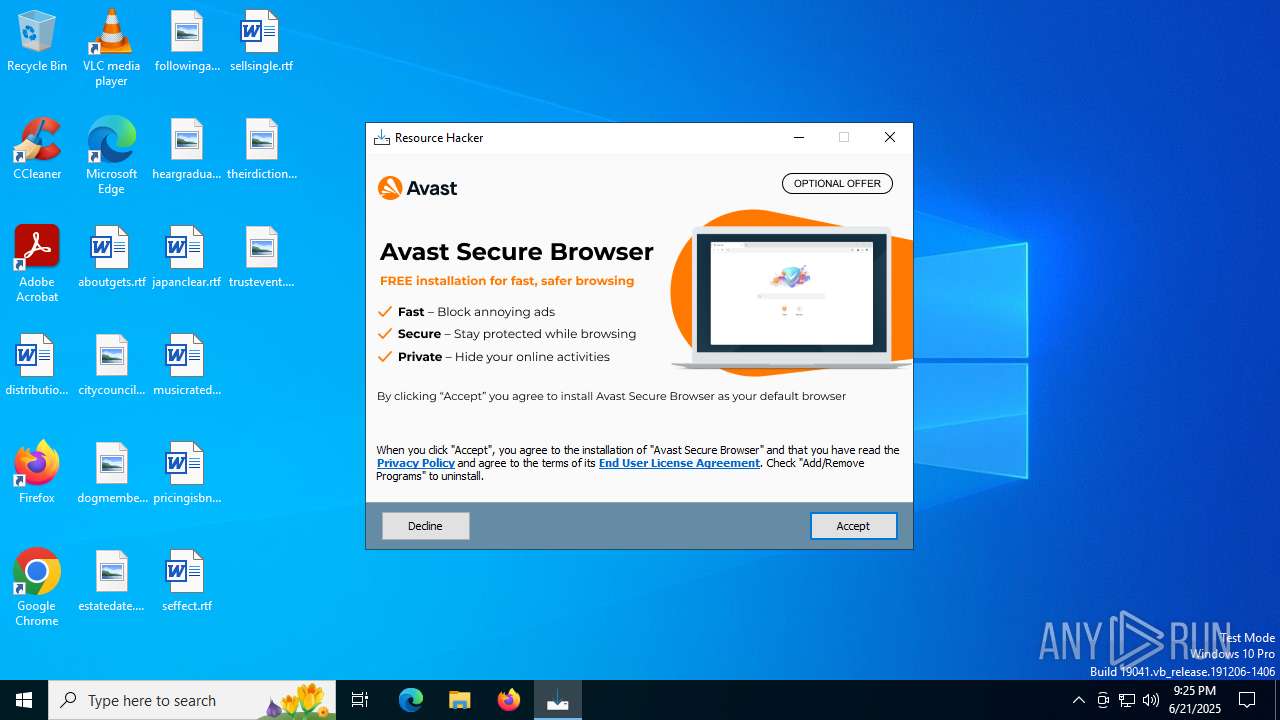
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | June 21, 2025, 21:24:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 4CEF35CB56164E4427C8890CF5CDFD85 |
| SHA1: | 242815E66819F32D46C37A57ED707030F57CA2C2 |
| SHA256: | 564B8E327A13C948CEA21587245B7B0005F786EA57F62BD602EF4ECEC66171C6 |
| SSDEEP: | 98304:b+cD4dno/Kiy69v/P4IzQ0eHJIsm/SK2gyGGnWfA/3nWAs1XnY/QI5QHpsisd:Uz |
MALICIOUS
Bundleinstaller mutex has been found
- resource-hacker_5ND-At1.tmp (PID: 2716)
INNOSETUP mutex has been found
- resource-hacker_5ND-At1.tmp (PID: 2716)
INNOSETUP has been detected (SURICATA)
- resource-hacker_5ND-At1.tmp (PID: 2716)
SUSPICIOUS
Executable content was dropped or overwritten
- resource-hacker_5ND-At1.exe (PID: 1944)
- resource-hacker_5ND-At1.exe (PID: 4380)
- resource-hacker_5ND-At1.tmp (PID: 2716)
Reads the Windows owner or organization settings
- resource-hacker_5ND-At1.tmp (PID: 2716)
Reads security settings of Internet Explorer
- resource-hacker_5ND-At1.tmp (PID: 2580)
- resource-hacker_5ND-At1.tmp (PID: 2716)
Access to an unwanted program domain was detected
- resource-hacker_5ND-At1.tmp (PID: 2716)
There is functionality for taking screenshot (YARA)
- resource-hacker_5ND-At1.tmp (PID: 2716)
The process executes via Task Scheduler
- updater.exe (PID: 6268)
Application launched itself
- updater.exe (PID: 6268)
INFO
Reads the computer name
- resource-hacker_5ND-At1.tmp (PID: 2580)
- resource-hacker_5ND-At1.tmp (PID: 2716)
- identity_helper.exe (PID: 2532)
- ResourceHacker.exe (PID: 6520)
- updater.exe (PID: 6268)
- ResourceHacker.exe (PID: 1512)
Checks supported languages
- resource-hacker_5ND-At1.exe (PID: 1944)
- resource-hacker_5ND-At1.exe (PID: 4380)
- resource-hacker_5ND-At1.tmp (PID: 2580)
- resource-hacker_5ND-At1.tmp (PID: 2716)
- ResourceHacker.exe (PID: 6520)
- updater.exe (PID: 6268)
- updater.exe (PID: 6704)
- ResourceHacker.exe (PID: 1512)
- identity_helper.exe (PID: 2532)
Create files in a temporary directory
- resource-hacker_5ND-At1.tmp (PID: 2716)
- resource-hacker_5ND-At1.exe (PID: 1944)
- resource-hacker_5ND-At1.exe (PID: 4380)
Reads the software policy settings
- resource-hacker_5ND-At1.tmp (PID: 2716)
- slui.exe (PID: 3980)
The sample compiled with english language support
- resource-hacker_5ND-At1.tmp (PID: 2716)
- WinRAR.exe (PID: 6380)
Reads the machine GUID from the registry
- resource-hacker_5ND-At1.tmp (PID: 2716)
Checks proxy server information
- resource-hacker_5ND-At1.tmp (PID: 2716)
- slui.exe (PID: 3980)
Detects InnoSetup installer (YARA)
- resource-hacker_5ND-At1.exe (PID: 1944)
- resource-hacker_5ND-At1.exe (PID: 4380)
- resource-hacker_5ND-At1.tmp (PID: 2716)
- resource-hacker_5ND-At1.tmp (PID: 2580)
Compiled with Borland Delphi (YARA)
- resource-hacker_5ND-At1.exe (PID: 1944)
- resource-hacker_5ND-At1.exe (PID: 4380)
- resource-hacker_5ND-At1.tmp (PID: 2716)
- resource-hacker_5ND-At1.tmp (PID: 2580)
- ResourceHacker.exe (PID: 6520)
Process checks computer location settings
- resource-hacker_5ND-At1.tmp (PID: 2716)
- resource-hacker_5ND-At1.tmp (PID: 2580)
Application launched itself
- msedge.exe (PID: 728)
- msedge.exe (PID: 436)
- msedge.exe (PID: 6688)
- msedge.exe (PID: 4192)
Reads Environment values
- identity_helper.exe (PID: 2532)
Manual execution by a user
- msedge.exe (PID: 6688)
- ResourceHacker.exe (PID: 6520)
- ResourceHacker.exe (PID: 1512)
RESOURCEHACKER mutex has been found
- ResourceHacker.exe (PID: 6520)
- ResourceHacker.exe (PID: 1512)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6380)
Process checks whether UAC notifications are on
- updater.exe (PID: 6268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.174.2916 |
| ProductVersionNumber: | 2.2.174.2916 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | |
| FileVersion: | 2.2.174.2916 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | |
| ProductVersion: | 2.2.174.2916 |
Total processes
183
Monitored processes
45
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2736,i,8964555744162941047,4380924504795287295,262144 --variations-seed-version --mojo-platform-channel-handle=2764 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 728 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --edge-skip-compat-layer-relaunch --single-argument https://en.download.it/typ | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4060,i,8964555744162941047,4380924504795287295,262144 --variations-seed-version --mojo-platform-channel-handle=3516 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4112,i,8964555744162941047,4380924504795287295,262144 --variations-seed-version --mojo-platform-channel-handle=4104 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\Desktop\ResourceHacker.exe" | C:\Users\admin\Desktop\ResourceHacker.exe | — | explorer.exe | |||||||||||
User: admin Company: Angus Johnson Integrity Level: MEDIUM Description: Resource viewer, decompiler & recompiler Exit code: 0 Version: 5.2.7.427 Modules
| |||||||||||||||
| 1944 | "C:\Users\admin\AppData\Local\Temp\resource-hacker_5ND-At1.exe" | C:\Users\admin\AppData\Local\Temp\resource-hacker_5ND-At1.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Exit code: 0 Version: 2.2.174.2916 Modules
| |||||||||||||||
| 2532 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4328,i,8964555744162941047,4380924504795287295,262144 --variations-seed-version --mojo-platform-channel-handle=4804 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Local\Temp\is-RLVD8.tmp\resource-hacker_5ND-At1.tmp" /SL5="$70374,1583588,832512,C:\Users\admin\AppData\Local\Temp\resource-hacker_5ND-At1.exe" | C:\Users\admin\AppData\Local\Temp\is-RLVD8.tmp\resource-hacker_5ND-At1.tmp | — | resource-hacker_5ND-At1.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2716 | "C:\Users\admin\AppData\Local\Temp\is-025PE.tmp\resource-hacker_5ND-At1.tmp" /SL5="$702BE,1583588,832512,C:\Users\admin\AppData\Local\Temp\resource-hacker_5ND-At1.exe" /SPAWNWND=$1102BA /NOTIFYWND=$70374 | C:\Users\admin\AppData\Local\Temp\is-025PE.tmp\resource-hacker_5ND-At1.tmp | resource-hacker_5ND-At1.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
10 154
Read events
10 106
Write events
48
Delete events
0
Modification events
| (PID) Process: | (2716) resource-hacker_5ND-At1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2716) resource-hacker_5ND-At1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2716) resource-hacker_5ND-At1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2716) resource-hacker_5ND-At1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4192) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4192) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (728) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 1 | |||
| (PID) Process: | (728) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2716) resource-hacker_5ND-At1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (6380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
Executable files
21
Suspicious files
147
Text files
67
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2716 | resource-hacker_5ND-At1.tmp | C:\Users\admin\AppData\Local\Temp\is-KRFC8.tmp\Helper.dll | executable | |
MD5:4EB0347E66FA465F602E52C03E5C0B4B | SHA256:C73E53CBB7B98FEAFE27CC7DE8FDAD51DF438E2235E91891461C5123888F73CC | |||
| 4380 | resource-hacker_5ND-At1.exe | C:\Users\admin\AppData\Local\Temp\is-025PE.tmp\resource-hacker_5ND-At1.tmp | executable | |
MD5:02B1D8FF84BCD4EBCB01156636269B99 | SHA256:A6497DDDDD577CAEFE5A39958A604F9EE4BFE93E9DA285B147BA6FC6788E75CA | |||
| 728 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:BAC9FEB21F102B8ED4CD3E469213E59B | SHA256:84ACD485899333CBDF5AD1F68D8C31658D5ECC9EE8DDDF62098A2218687D7E77 | |||
| 2716 | resource-hacker_5ND-At1.tmp | C:\Users\admin\AppData\Local\Temp\is-KRFC8.tmp\loader.gif | image | |
MD5:12D7FD91A06CEE2D0E76ABE0485036EE | SHA256:A6192B9A3FA5DB9917AEF72D651B7AD8FD8CCB9B53F3AD99D7C46701D00C78CB | |||
| 2716 | resource-hacker_5ND-At1.tmp | C:\Users\admin\Downloads\resource-hacker.zip | compressed | |
MD5:B1F79F26558459D1B401BA9ECE2E8D66 | SHA256:F958DB1D239E69051145777DE9943B267A3230CC3D140599B48CF024E2C8B3A2 | |||
| 2716 | resource-hacker_5ND-At1.tmp | C:\Users\admin\AppData\Local\Temp\is-KRFC8.tmp\is-HPDOJ.tmp | image | |
MD5:378F74A0CBDD582D8B434B7B978FF375 | SHA256:1225AFDA135B0BF3B5633595AF4096F8C6620EBB34AA5DF7C64253F03668B33D | |||
| 728 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\e6616d83-0338-40ed-a1f4-828d4985055e.tmp | binary | |
MD5:CAE702B1FF4DB5BC74283E7F274A34B7 | SHA256:165B2A9D3A50E9785E091A609054633981C963F7D7090699F1B3BBD6E2E50A5E | |||
| 2716 | resource-hacker_5ND-At1.tmp | C:\Users\admin\AppData\Local\Temp\is-KRFC8.tmp\resource-hacker.zip | compressed | |
MD5:B1F79F26558459D1B401BA9ECE2E8D66 | SHA256:F958DB1D239E69051145777DE9943B267A3230CC3D140599B48CF024E2C8B3A2 | |||
| 2716 | resource-hacker_5ND-At1.tmp | C:\Users\admin\AppData\Local\Temp\is-KRFC8.tmp\Avast_BRW.png | image | |
MD5:02B8B0EC0A909007904AF9FFD0BEB454 | SHA256:67CE7C9D63241A5F1AEBF9171E3AD640D254B70592C0407B2DC24F885E0576D9 | |||
| 2716 | resource-hacker_5ND-At1.tmp | C:\Users\admin\AppData\Local\Temp\is-KRFC8.tmp\mainlogo.png | image | |
MD5:B9BD51049A90621F498CA5D25F3D8C27 | SHA256:2D216E988CECB4867CC8E13F567514A8A80DAE87E8D1CE2B483CF2E9CED610CD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
74
DNS requests
89
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.18.121.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2716 | resource-hacker_5ND-At1.tmp | GET | 200 | 95.168.168.24:80 | http://dl.jalecdn.com/US/resource-hacker.zip | unknown | — | — | unknown |
5692 | svchost.exe | GET | 200 | 104.78.173.167:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1484 | SIHClient.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6176 | svchost.exe | HEAD | 200 | 2.18.244.211:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750784665&P2=404&P3=2&P4=U%2f91zsxVUpVOU4a6lEZyDWhlzxanTeWtIKgzq0W%2bR2xwSLhDnIcrQ82CS9gzvyDtg4Wf4l8x%2bmNnSfp9IxoTPw%3d%3d | unknown | — | — | whitelisted |
1484 | SIHClient.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.220.113.51:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6176 | svchost.exe | GET | 200 | 2.18.244.211:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9244b52a-55cc-41a2-b7c4-7f4983d8753c?P1=1750784666&P2=404&P3=2&P4=YVEOm2hYHlNlgpBHKoHevZ6annl7ANkmigpu%2bJXm05V1qw3WC%2bSPdh%2bPBXXaQ6NuCtoSNxncZsTmgLfc%2fv3TIg%3d%3d | unknown | — | — | whitelisted |
6176 | svchost.exe | GET | 206 | 2.18.244.211:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750784665&P2=404&P3=2&P4=U%2f91zsxVUpVOU4a6lEZyDWhlzxanTeWtIKgzq0W%2bR2xwSLhDnIcrQ82CS9gzvyDtg4Wf4l8x%2bmNnSfp9IxoTPw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
472 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2716 | resource-hacker_5ND-At1.tmp | 18.65.40.121:443 | d1e9165hyidvf5.cloudfront.net | AMAZON-02 | US | whitelisted |
2716 | resource-hacker_5ND-At1.tmp | 104.22.56.224:443 | static.download.it | CLOUDFLARENET | — | suspicious |
5692 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5692 | svchost.exe | 104.78.173.167:80 | ocsp.digicert.com | AKAMAI-AS | GB | whitelisted |
2716 | resource-hacker_5ND-At1.tmp | 95.168.168.24:80 | dl.jalecdn.com | LeaseWeb Netherlands B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
d1e9165hyidvf5.cloudfront.net |
| whitelisted |
static.download.it |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
dl.jalecdn.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2716 | resource-hacker_5ND-At1.tmp | Possibly Unwanted Program Detected | ADWARE [ANY.RUN] InnoSetup Installer |
4216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
4216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
4216 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |