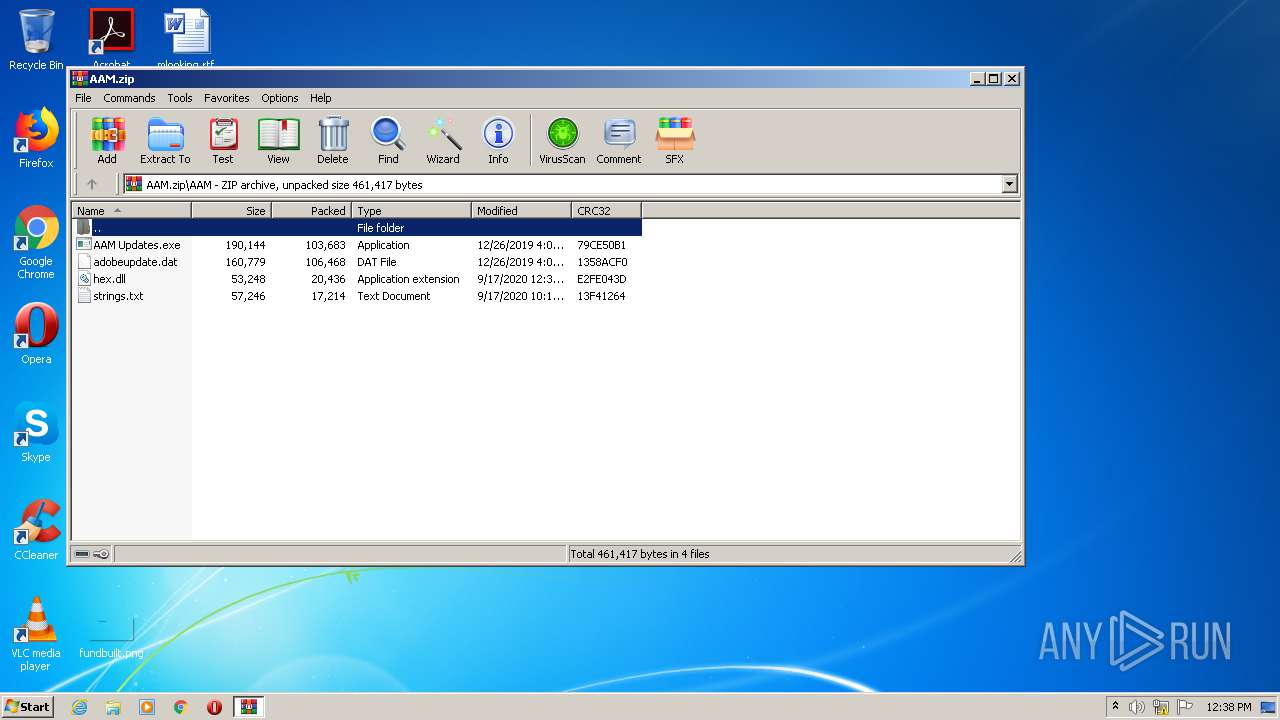
| File name: | AAM.zip |
| Full analysis: | https://app.any.run/tasks/95feca5e-48b0-4bff-a840-635de05b1744 |
| Verdict: | Malicious activity |
| Threats: | PlugX is a remote access trojan that is used extensively by Chinese APTs. The malware is primarily employed for spying on victims and can perform a variety of malicious activities, such as logging users’ keystrokes and exfiltrating information from browsers. |
| Analysis date: | September 17, 2020, 11:37:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8B940EF1616C553B59F360EA8F4E6E01 |
| SHA1: | A1F070917C4339577383425FF120E57DAE64A762 |
| SHA256: | 55FBC39D8C3AC28BA9FFAC1B773EFEC049E497719F49D44A73D1B553A5920162 |
| SSDEEP: | 6144:ztJX05exoj5L0bdCptv/IXsmygXIUIL+5UBYKGOwt:QPN0bdCbv3mFIL+6NGOG |
MALICIOUS
Application was dropped or rewritten from another process
- AAM Updates.exe (PID: 2196)
- AAM Updates.exe (PID: 2256)
- AAM Updates.exe (PID: 1848)
- AAM Updates.exe (PID: 2076)
Changes the autorun value in the registry
- AAM Updates.exe (PID: 2256)
- AAM Updates.exe (PID: 1848)
Loads dropped or rewritten executable
- AAM Updates.exe (PID: 2256)
- AAM Updates.exe (PID: 2196)
- explorer.exe (PID: 496)
- AAM Updates.exe (PID: 1848)
- SearchProtocolHost.exe (PID: 4020)
- AAM Updates.exe (PID: 2076)
PLUGX was detected
- AAM Updates.exe (PID: 2196)
Connects to CnC server
- AAM Updates.exe (PID: 2196)
SUSPICIOUS
Starts itself from another location
- AAM Updates.exe (PID: 2256)
- AAM Updates.exe (PID: 1848)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2528)
- AAM Updates.exe (PID: 2256)
- AAM Updates.exe (PID: 1848)
Creates files in the program directory
- AAM Updates.exe (PID: 2256)
Creates files in the user directory
- explorer.exe (PID: 496)
Reads Internet Cache Settings
- AAM Updates.exe (PID: 2196)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:09:17 18:37:13 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | AAM/ |
Total processes
39
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | "C:\Users\admin\Desktop\AAM Updates.exe" | C:\Users\admin\Desktop\AAM Updates.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe CEF Helper Exit code: 0 Version: 3.9.0.327 Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\AAM UpdateskUK\AAM Updates.exe" 903 | C:\Users\admin\AAM UpdateskUK\AAM Updates.exe | — | AAM Updates.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe CEF Helper Exit code: 0 Version: 3.9.0.327 Modules
| |||||||||||||||
| 2196 | "C:\ProgramData\AAM UpdateskUK\AAM Updates.exe" 651 | C:\ProgramData\AAM UpdateskUK\AAM Updates.exe | AAM Updates.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe CEF Helper Exit code: 0 Version: 3.9.0.327 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2528.2267\AAM\AAM Updates.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2528.2267\AAM\AAM Updates.exe | WinRAR.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe CEF Helper Exit code: 0 Version: 3.9.0.327 Modules
| |||||||||||||||
| 2528 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\AAM.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 4020 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 577
Read events
2 512
Write events
65
Delete events
0
Modification events
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AAM.zip | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2528) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (496) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (496) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
8
Suspicious files
4
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 496 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 496 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 496 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AAM.zip.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2528.2267\AAM\adobeupdate.dat | binary | |
MD5:25393CA6AD6B41D1B06FFB3FD22D768C | SHA256:635508330CF1A8359737F46F9C382694783A84640BEB88E3DCF1C537874E77B7 | |||
| 2256 | AAM Updates.exe | C:\ProgramData\AAM UpdateskUK\hex.dll | executable | |
MD5:6CA3439153577503FD71F7039A0045AB | SHA256:5928048ED1D76DF1AE4F3EDE0E3DA0B0006734F712A78036E6F4B6A78C05F0C6 | |||
| 2256 | AAM Updates.exe | C:\ProgramData\AAM UpdateskUK\adobeupdate.dat | binary | |
MD5:25393CA6AD6B41D1B06FFB3FD22D768C | SHA256:635508330CF1A8359737F46F9C382694783A84640BEB88E3DCF1C537874E77B7 | |||
| 2528 | WinRAR.exe | C:\Users\admin\Desktop\adobeupdate.dat | binary | |
MD5:25393CA6AD6B41D1B06FFB3FD22D768C | SHA256:635508330CF1A8359737F46F9C382694783A84640BEB88E3DCF1C537874E77B7 | |||
| 1848 | AAM Updates.exe | C:\Users\admin\AAM UpdateskUK\adobeupdate.dat | binary | |
MD5:25393CA6AD6B41D1B06FFB3FD22D768C | SHA256:635508330CF1A8359737F46F9C382694783A84640BEB88E3DCF1C537874E77B7 | |||
| 1848 | AAM Updates.exe | C:\Users\admin\AAM UpdateskUK\AAM Updates.exe | executable | |
MD5:C70D8DCE46B4551133ECC58AED84BF0E | SHA256:0459E62C5444896D5BE404C559C834BA455FA5CAE1689C70FC8C61BC15468681 | |||
| 2528 | WinRAR.exe | C:\Users\admin\Desktop\strings.txt | text | |
MD5:09E3256DAD2ACA9B633EDBD80C4E121C | SHA256:47454BD984E41A8816AAD2E9137FC0FD7EBBCE4BED634D2056327037C9B9452E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
0
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2196 | AAM Updates.exe | POST | — | 185.239.226.65:80 | http://185.239.226.65/update?wd=8f0f7b6f | unknown | — | — | malicious |
2196 | AAM Updates.exe | POST | — | 185.239.226.65:80 | http://185.239.226.65/update?wd=720fc3a0 | unknown | — | — | malicious |
2196 | AAM Updates.exe | POST | — | 185.239.226.65:80 | http://185.239.226.65/update?wd=8426f37e | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2196 | AAM Updates.exe | 185.239.226.65:80 | — | — | — | malicious |
— | — | 185.239.226.65:443 | — | — | — | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | AAM Updates.exe | A Network Trojan was detected | ET TROJAN Possible PlugX Common Header Struct |
2196 | AAM Updates.exe | A Network Trojan was detected | ET TROJAN APT Mustang Panda Payload - CnC Checkin |
2196 | AAM Updates.exe | A Network Trojan was detected | ET TROJAN Possible PlugX Common Header Struct |
2196 | AAM Updates.exe | A Network Trojan was detected | ET TROJAN APT Mustang Panda Payload - CnC Checkin |
2196 | AAM Updates.exe | A Network Trojan was detected | ET TROJAN Possible PlugX Common Header Struct |
2196 | AAM Updates.exe | A Network Trojan was detected | ET TROJAN APT Mustang Panda Payload - CnC Checkin |