| File name: | powershell payload.txt |
| Full analysis: | https://app.any.run/tasks/32d45102-1fe1-4846-95bd-77042ae94fa9 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | January 31, 2024, 17:29:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Little-endian UTF-16 Unicode text, with very long lines, with CRLF line terminators |
| MD5: | 4A6EAEBF9BBDA278AF047EA44C85373D |
| SHA1: | 03CDE01EE5FE0F1A0BE9886CD04B46CDFF367C35 |
| SHA256: | 54FB920C90A80446A0382C2109F9D3F28743FBDCC7A68F501CD8FC1B18E0DB38 |
| SSDEEP: | 12288:Z/rv57RCRYnBjWIdsFh0H2klKh4E/ESaFoz+wswIVkURjzq66/ByOYSRSCQYPiEk:ZzvVRMYBddTWuUzESYoz+MIVfFe6XSRm |
MALICIOUS
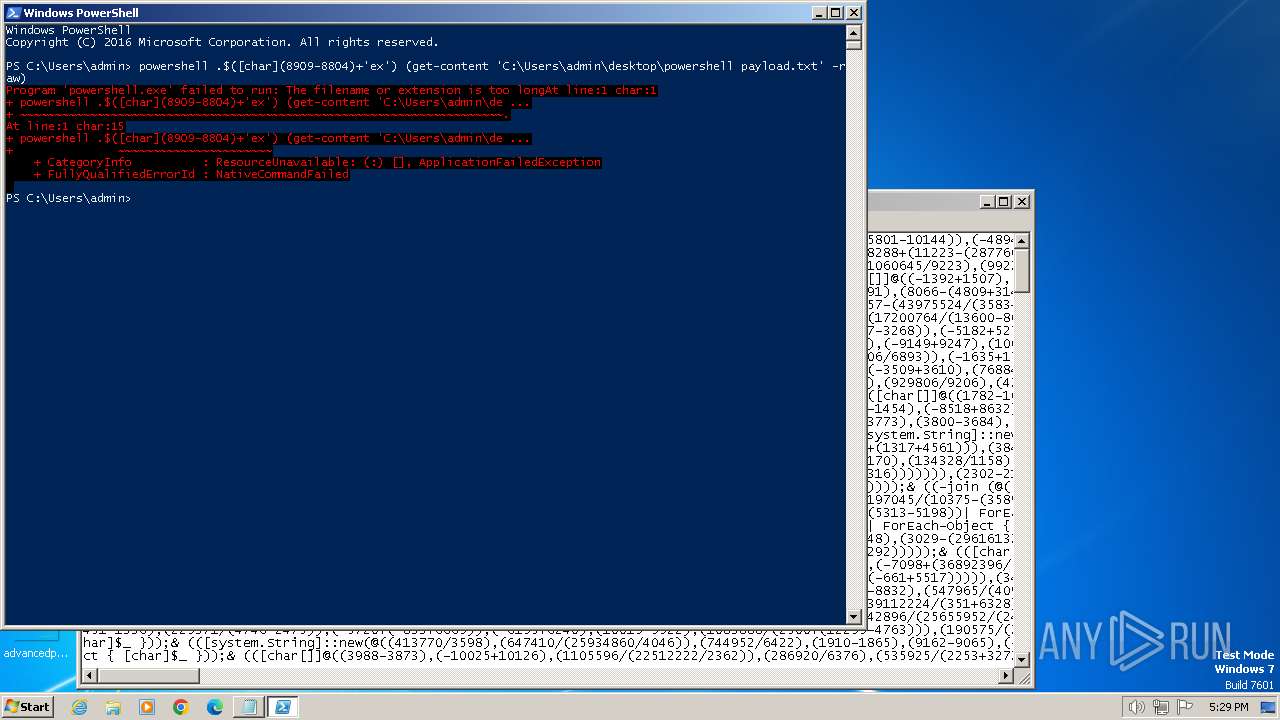
Starts Visual C# compiler
- powershell.exe (PID: 1028)
Drops the executable file immediately after the start
- csc.exe (PID: 3596)
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 1028)
SUSPICIOUS
Reads the Internet Settings
- notepad.exe (PID: 1044)
- powershell.exe (PID: 1028)
Uses .NET C# to load dll
- powershell.exe (PID: 1028)
Executable content was dropped or overwritten
- csc.exe (PID: 3596)
The Powershell connects to the Internet
- powershell.exe (PID: 1028)
Connects to unusual port
- powershell.exe (PID: 1028)
Unusual connection from system programs
- powershell.exe (PID: 1028)
INFO
Checks supported languages
- csc.exe (PID: 3596)
- cvtres.exe (PID: 3600)
Manual execution by a user
- powershell.exe (PID: 1028)
Reads the machine GUID from the registry
- cvtres.exe (PID: 3600)
- csc.exe (PID: 3596)
Create files in a temporary directory
- cvtres.exe (PID: 3600)
- csc.exe (PID: 3596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1028 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1044 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\powershell payload.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3596 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\q0fflboh.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 3600 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESC827.tmp" "c:\Users\admin\AppData\Local\Temp\CSCFBB2E916464744EB9B5596A5CD5C77E.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
Total events
8 018
Read events
7 888
Write events
128
Delete events
2
Modification events
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 010000000200000006000000000000000B000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000006000000000000000B000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (1044) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
Executable files
1
Suspicious files
12
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1028 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 1044 | notepad.exe | C:\Users\admin\Desktop\powershell payload.txt | text | |
MD5:4A6EAEBF9BBDA278AF047EA44C85373D | SHA256:54FB920C90A80446A0382C2109F9D3F28743FBDCC7A68F501CD8FC1B18E0DB38 | |||
| 1028 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF16862c.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 1028 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:67BC9011476C87B42100EDEB9660C156 | SHA256:1332A0F6F56E228FD1BF8D1756BBA448C457E74C26A8E2DDA9F0BA80BE65F1BC | |||
| 1028 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1FXLATJMY7BUV6ZZ2Z9S.temp | binary | |
MD5:67BC9011476C87B42100EDEB9660C156 | SHA256:1332A0F6F56E228FD1BF8D1756BBA448C457E74C26A8E2DDA9F0BA80BE65F1BC | |||
| 1028 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3596 | csc.exe | C:\Users\admin\AppData\Local\Temp\q0fflboh.dll | executable | |
MD5:2B96BD724E0C572B29101B3BDF27608A | SHA256:83388C4FD5CEBE33AE2E42701B6F82A983A8A6F8B5D7312D0AA420526E55C083 | |||
| 1028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\CabD91F.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3596 | csc.exe | C:\Users\admin\AppData\Local\Temp\q0fflboh.out | text | |
MD5:2D73017FFB26E5A83609189F1E2CCB10 | SHA256:502EAE6687A20D3CF6E98E57664139D8AAD789780C681A05AF95EB202D2C6C13 | |||
| 3596 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCFBB2E916464744EB9B5596A5CD5C77E.TMP | binary | |
MD5:00466CA899CCE5A05268D26914403E5B | SHA256:C4AC857227D230688853394AD1F8CB81E19797A51D8B0827CDE68BF4ABDCCC55 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
3
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1028 | powershell.exe | GET | 200 | 184.24.77.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?011afa2a3692420e | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1028 | powershell.exe | 5.161.113.150:25658 | w89tu45t8e7dqzo.top | Hetzner Online GmbH | US | unknown |
1028 | powershell.exe | 184.24.77.205:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1028 | powershell.exe | 104.237.62.212:443 | api.ipify.org | WEBNX | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
w89tu45t8e7dqzo.top |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1028 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |