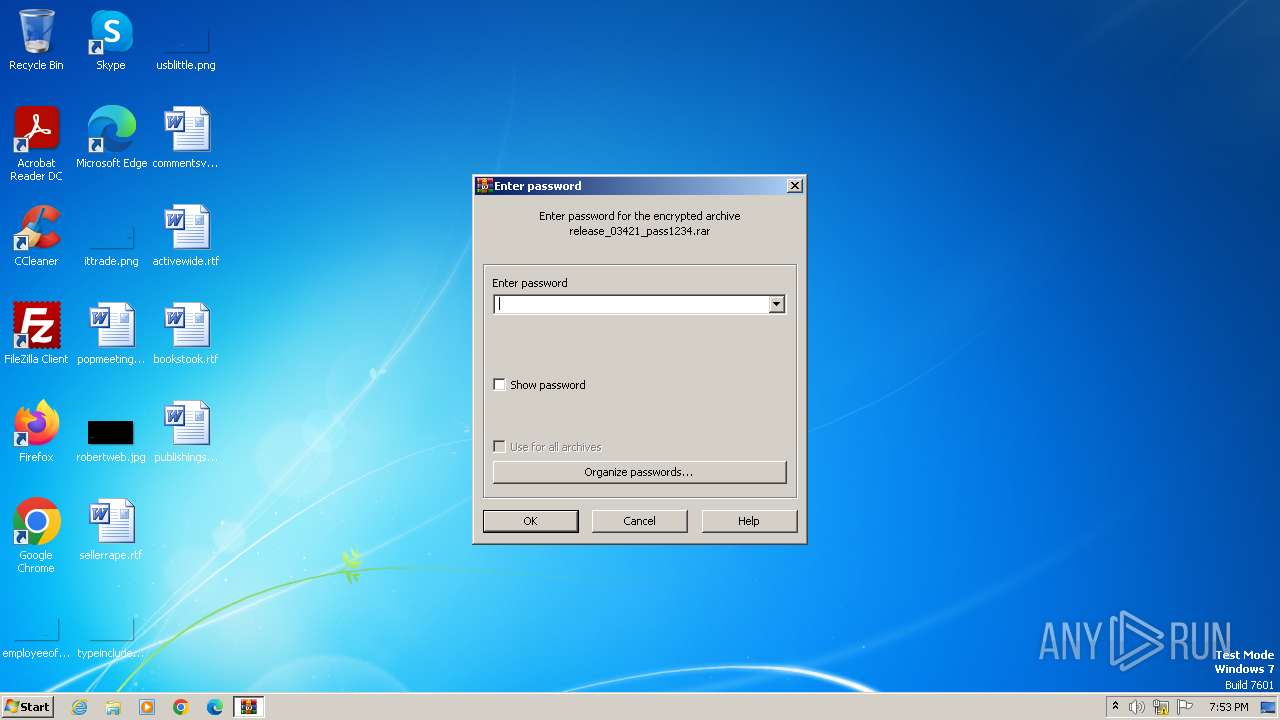
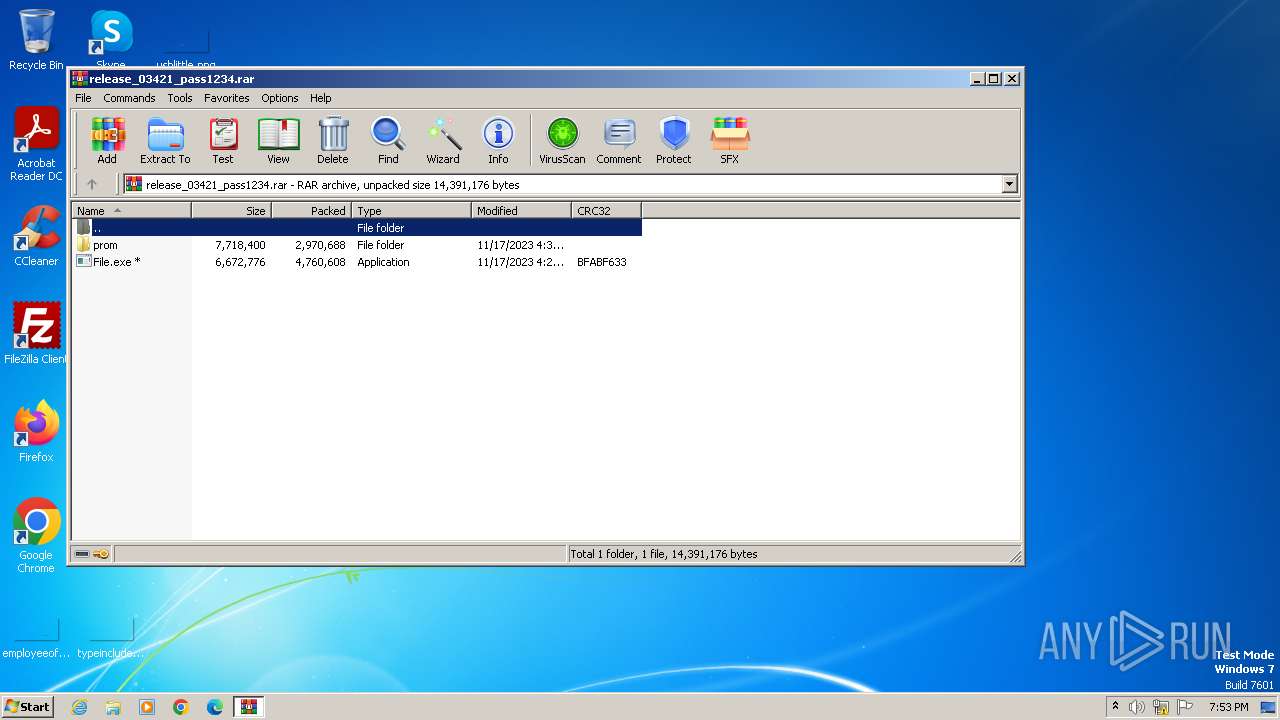
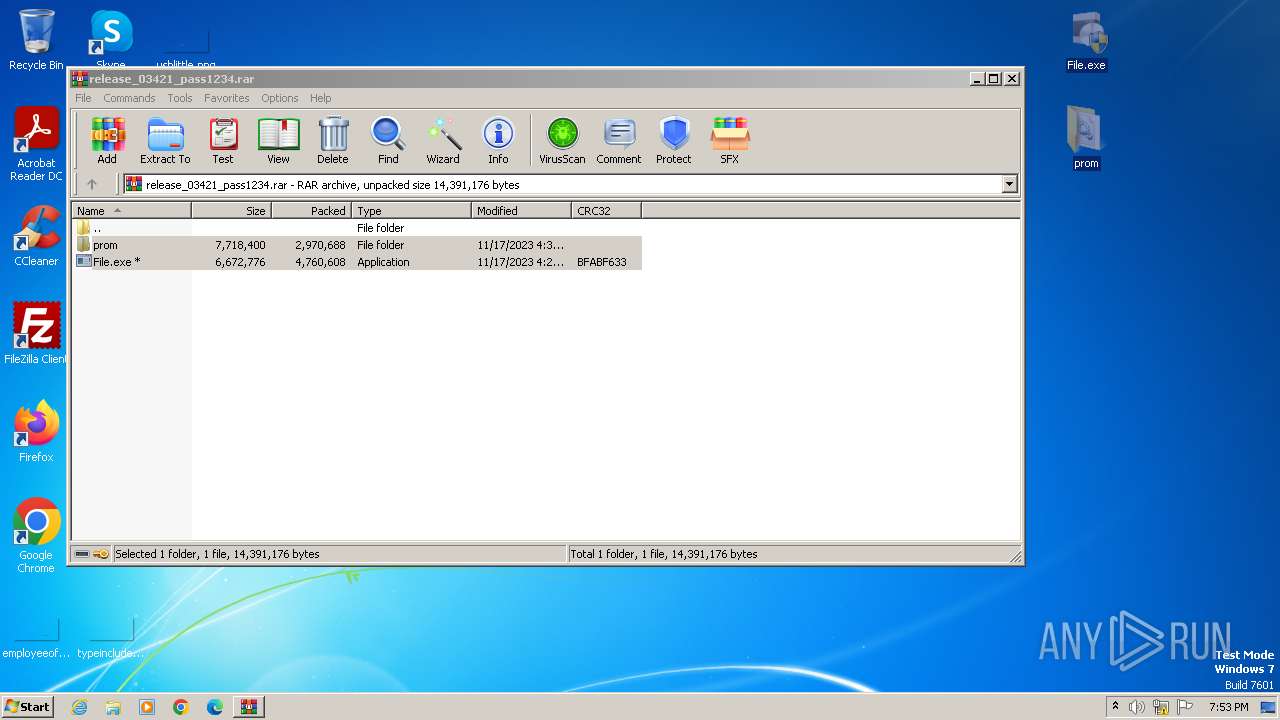
| File name: | release_03421_pass1234.rar |
| Full analysis: | https://app.any.run/tasks/4a967e2a-7274-46e6-9a9a-3fc87c6906f9 |
| Verdict: | Malicious activity |
| Threats: | PrivateLoader is a malware family that is specifically created to infect computer systems and drop additional malicious programs. It operates using a pay-per-install business model, which means that the individuals behind it are paid for each instance of successful deployment of different types of harmful programs, including trojans, stealers, and other ransomware. |
| Analysis date: | November 17, 2023, 19:53:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 09DB8E1C2749209D74D96136307CA3CF |
| SHA1: | 478ABD736659B2869564417CB4C22BFAA2A5D2C9 |
| SHA256: | 54758F87D4882B7D6DC4DEAA14306C5C3CF3E0737F739273291458944A4E7B31 |
| SSDEEP: | 98304:dZeu9Lpa6vJm0u8I/oHtPlO3AnTPfFvIuUFz+B11Hc/OUjncl9ZPlIevon+nq9eE:3KBNM2pGK7D |
MALICIOUS
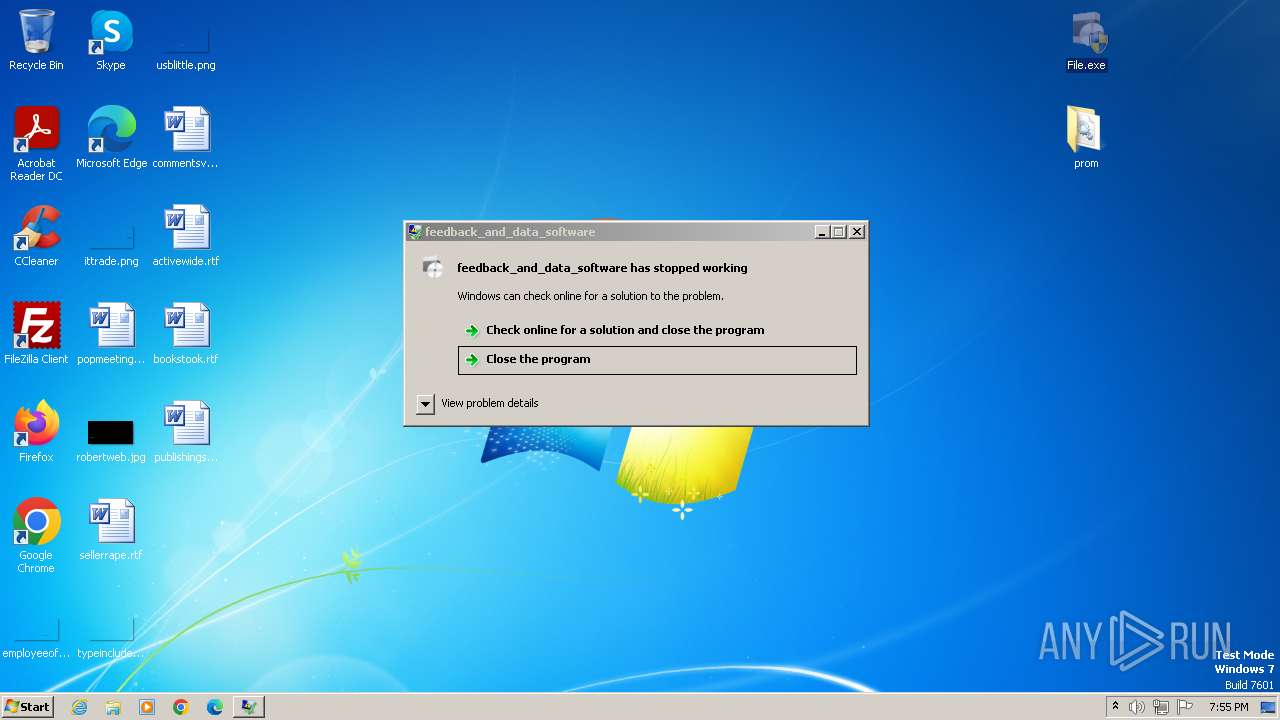
Drops the executable file immediately after the start
- File.exe (PID: 3528)
- AppLaunch.exe (PID: 3816)
Connects to the CnC server
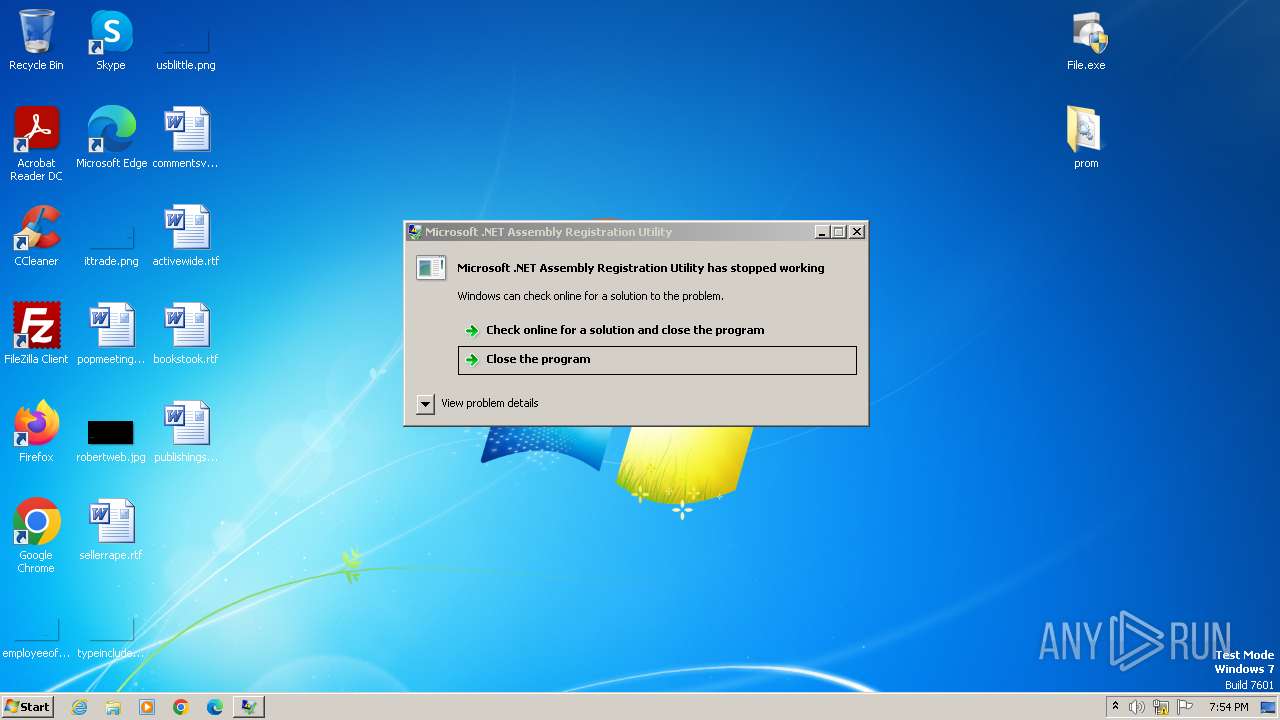
- RegAsm.exe (PID: 3876)
- RegAsm.exe (PID: 300)
- AppLaunch.exe (PID: 3816)
PRIVATELOADER has been detected (SURICATA)
- RegAsm.exe (PID: 3876)
- RegAsm.exe (PID: 300)
REDLINE has been detected (SURICATA)
- AppLaunch.exe (PID: 3816)
REDLINE has been detected (YARA)
- AppLaunch.exe (PID: 3816)
Steals credentials from Web Browsers
- AppLaunch.exe (PID: 3816)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 300)
- AppLaunch.exe (PID: 3816)
SUSPICIOUS
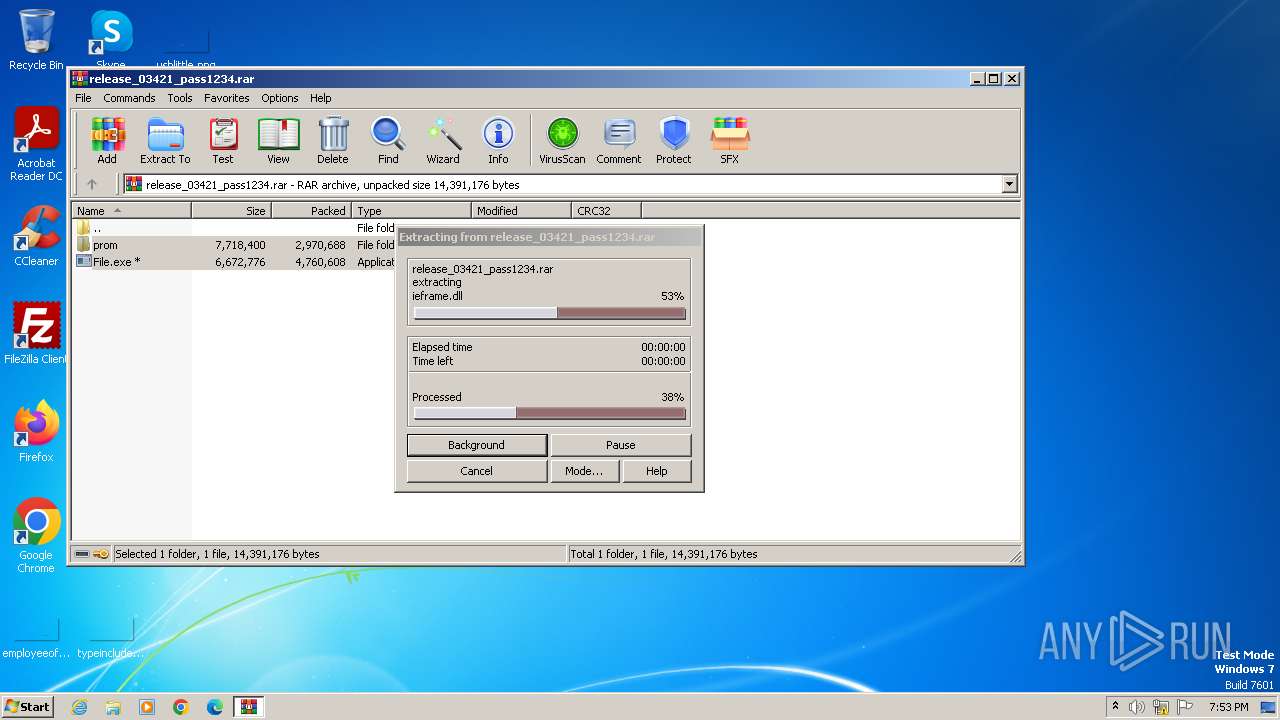
Process drops legitimate windows executable
- WinRAR.exe (PID: 3128)
Reads settings of System Certificates
- RegAsm.exe (PID: 3876)
- RegAsm.exe (PID: 300)
- AppLaunch.exe (PID: 3816)
Connects to the server without a host name
- RegAsm.exe (PID: 3876)
- RegAsm.exe (PID: 300)
Checks for external IP
- RegAsm.exe (PID: 3876)
- RegAsm.exe (PID: 300)
Checks Windows Trust Settings
- RegAsm.exe (PID: 300)
Reads security settings of Internet Explorer
- RegAsm.exe (PID: 300)
Reads the Internet Settings
- RegAsm.exe (PID: 300)
- AppLaunch.exe (PID: 3816)
Connects to unusual port
- AppLaunch.exe (PID: 3816)
Searches for installed software
- AppLaunch.exe (PID: 3816)
Reads browser cookies
- AppLaunch.exe (PID: 3816)
Adds/modifies Windows certificates
- File.exe (PID: 1576)
INFO
Checks supported languages
- RegAsm.exe (PID: 3876)
- File.exe (PID: 3528)
- wmpnscfg.exe (PID: 3968)
- File.exe (PID: 1576)
- RegAsm.exe (PID: 300)
- RegAsm.exe (PID: 2620)
- File.exe (PID: 2388)
- pg5hkbPnZegCO39fuJuYnM5h.exe (PID: 1828)
- AppLaunch.exe (PID: 3816)
- File.exe (PID: 2884)
- RegAsm.exe (PID: 2480)
Reads the computer name
- RegAsm.exe (PID: 3876)
- File.exe (PID: 3528)
- wmpnscfg.exe (PID: 3968)
- RegAsm.exe (PID: 300)
- File.exe (PID: 1576)
- File.exe (PID: 2388)
- AppLaunch.exe (PID: 3816)
- File.exe (PID: 2884)
Create files in a temporary directory
- File.exe (PID: 3528)
- AppLaunch.exe (PID: 3816)
- RegAsm.exe (PID: 300)
Manual execution by a user
- File.exe (PID: 3528)
- File.exe (PID: 3524)
- wmpnscfg.exe (PID: 3968)
- File.exe (PID: 3532)
- File.exe (PID: 1576)
- rundll32.exe (PID: 556)
- File.exe (PID: 2388)
- File.exe (PID: 2000)
- File.exe (PID: 2252)
- File.exe (PID: 2884)
Reads the machine GUID from the registry
- File.exe (PID: 3528)
- RegAsm.exe (PID: 3876)
- wmpnscfg.exe (PID: 3968)
- File.exe (PID: 1576)
- File.exe (PID: 2388)
- AppLaunch.exe (PID: 3816)
- RegAsm.exe (PID: 300)
- File.exe (PID: 2884)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3128)
Creates files or folders in the user directory
- RegAsm.exe (PID: 300)
Process checks computer location settings
- RegAsm.exe (PID: 300)
Checks proxy server information
- RegAsm.exe (PID: 300)
Reads product name
- AppLaunch.exe (PID: 3816)
Reads Environment values
- AppLaunch.exe (PID: 3816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3816) AppLaunch.exe
C2 (1)194.49.94.142:41292
Botnet123
Err_msg
Auth_value208cea6922f6803b969d28c5c259d920
US (12)
net.tcp://
/
localhost
208cea6922f6803b969d28c5c259d920
Authorization
ns1
HiQeQiIDP1I/ORtFPgQsXioZPEA4JidcIwBObg==
HiQ8CA==
Spurnings
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
73
Monitored processes
17
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | File.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
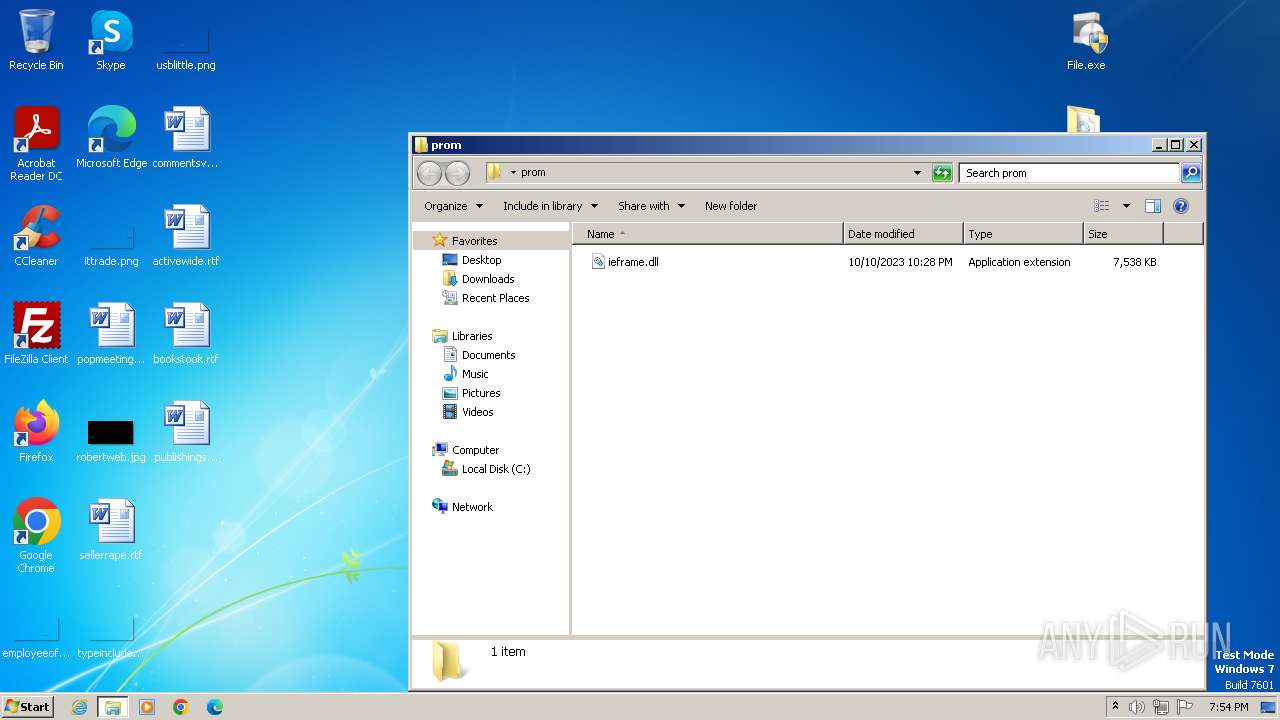
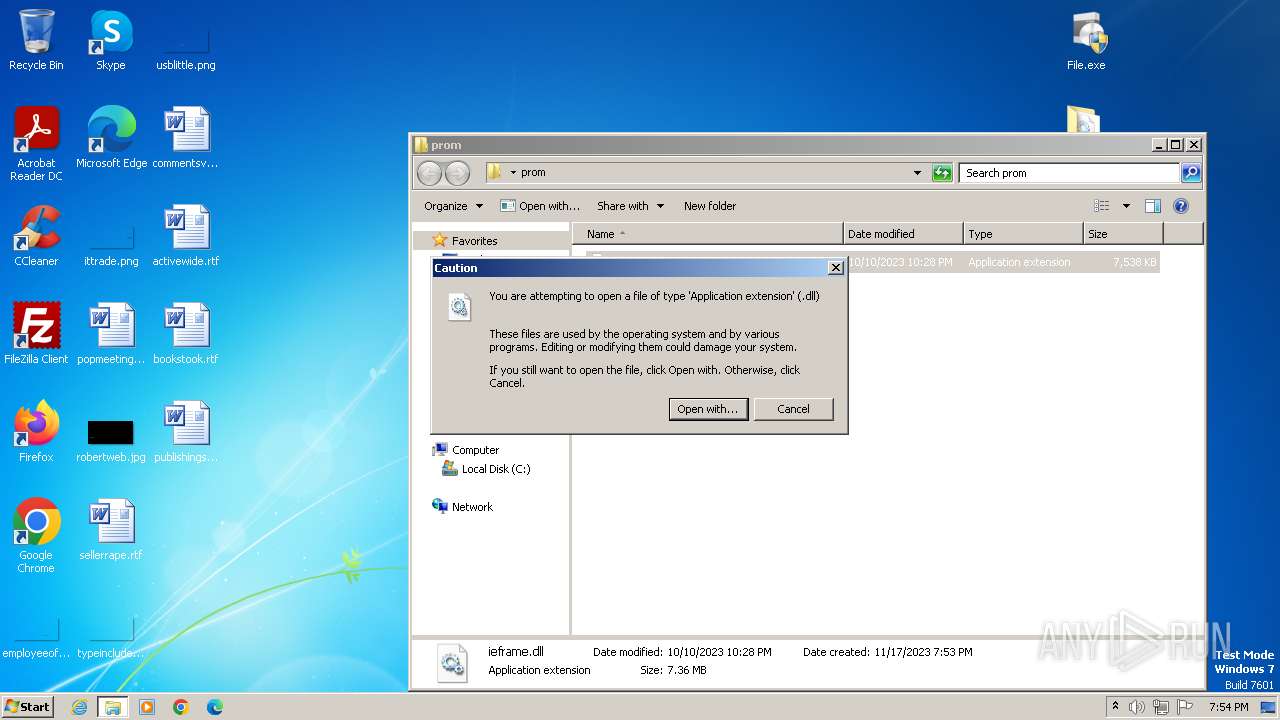
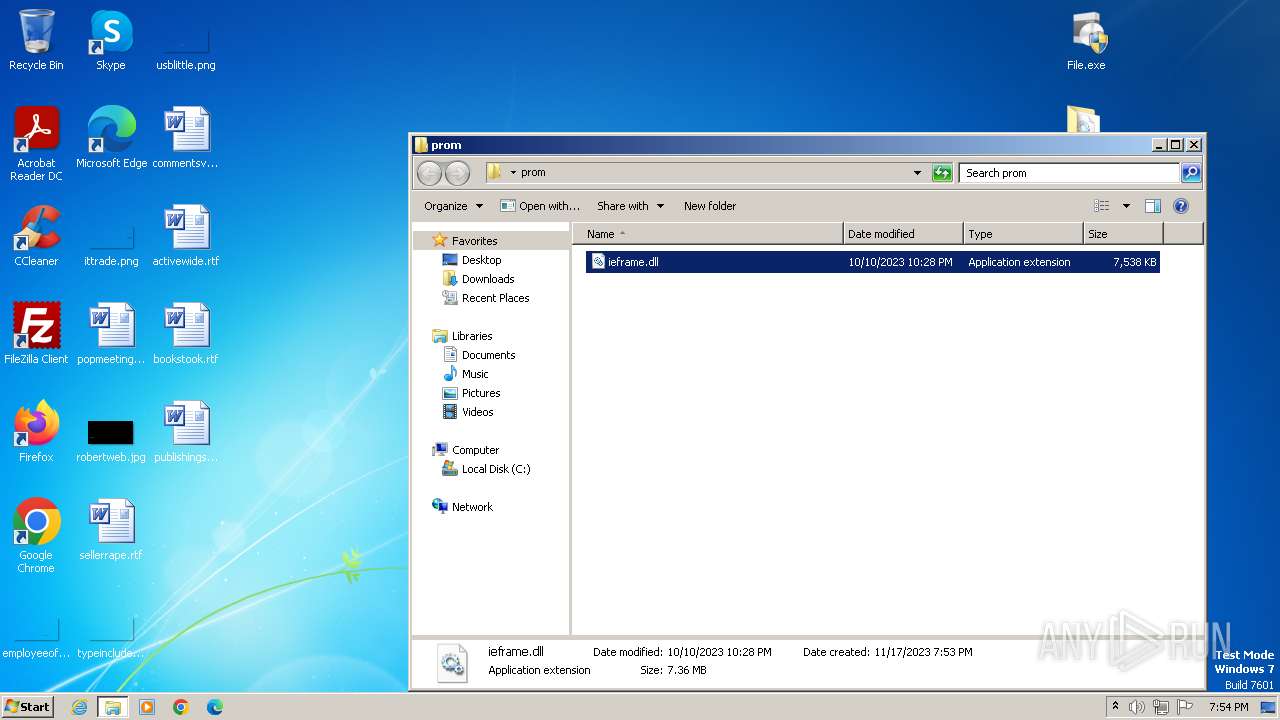
| 556 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\prom\ieframe.dll | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
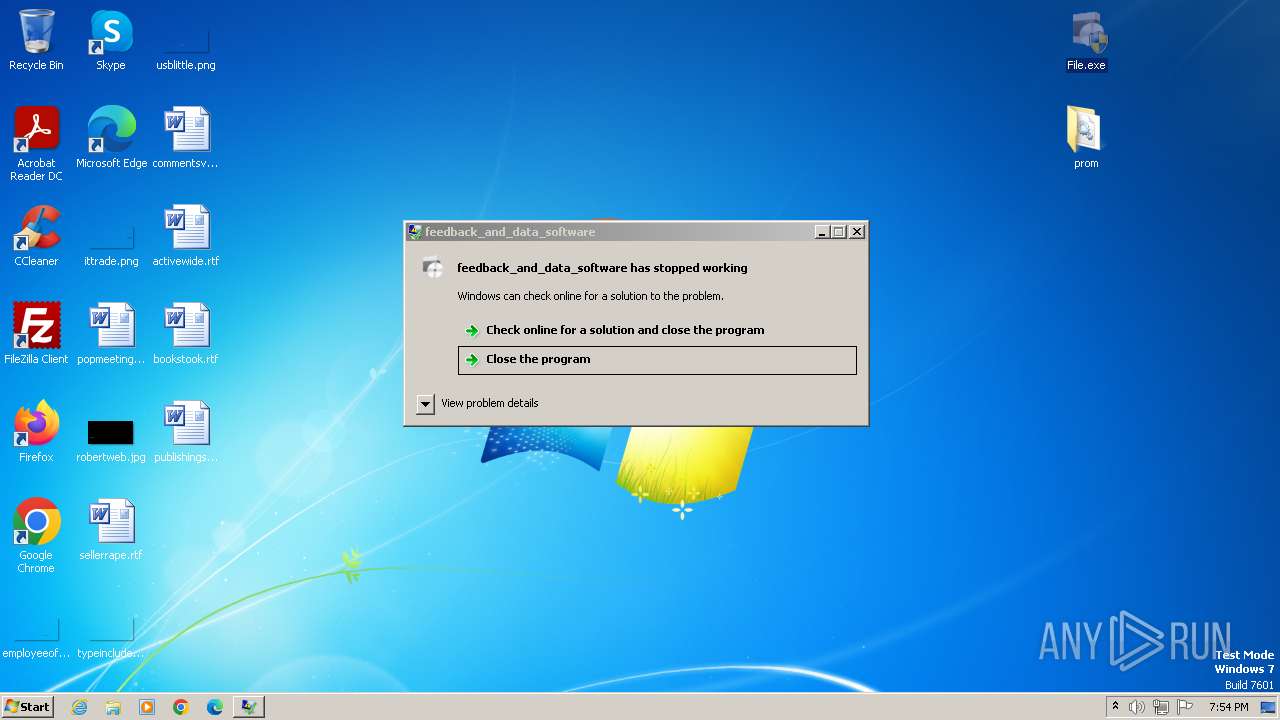
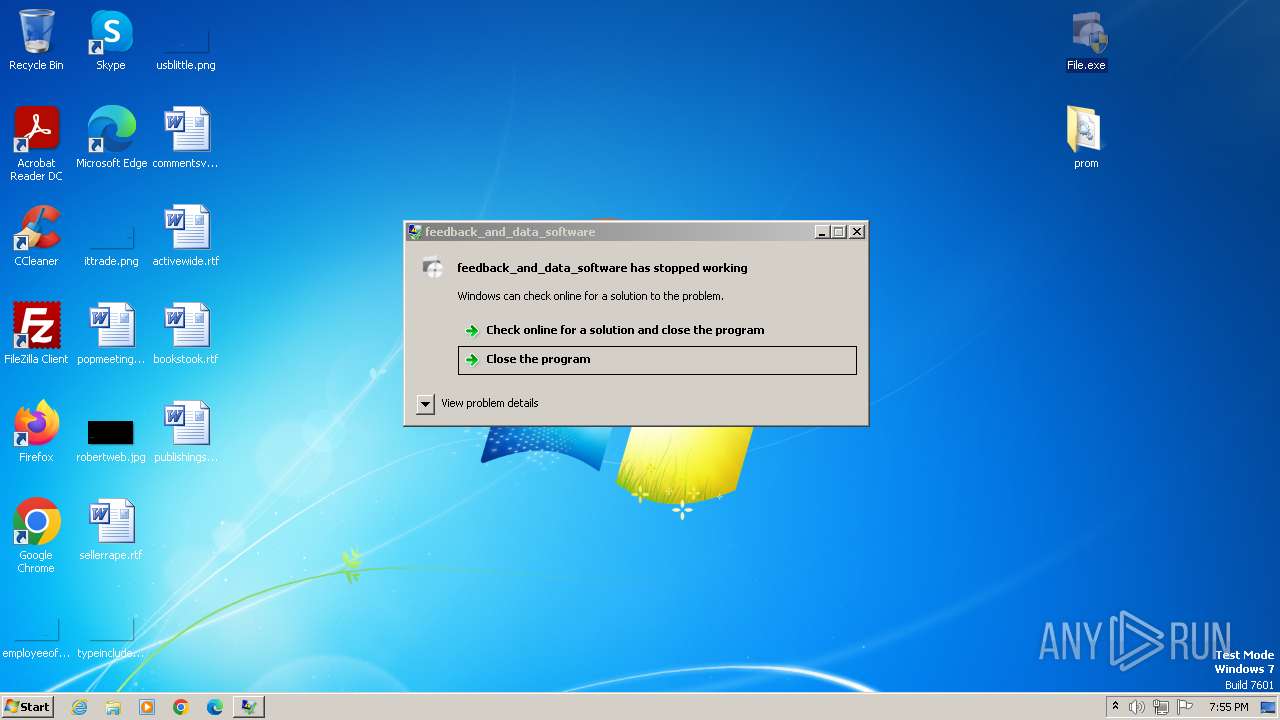
| 1576 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: feedback_and_data_software Exit code: 3221225477 Version: 1.2.0.0 Modules
| |||||||||||||||
| 1828 | "C:\Users\admin\Pictures\Minor Policy\pg5hkbPnZegCO39fuJuYnM5h.exe" | C:\Users\admin\Pictures\Minor Policy\pg5hkbPnZegCO39fuJuYnM5h.exe | — | RegAsm.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2000 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: feedback_and_data_software Exit code: 3221226540 Version: 1.2.0.0 Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: feedback_and_data_software Exit code: 3221226540 Version: 1.2.0.0 Modules
| |||||||||||||||
| 2388 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: feedback_and_data_software Exit code: 3221225477 Version: 1.2.0.0 Modules
| |||||||||||||||
| 2480 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | File.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 203 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 2620 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | File.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 205 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 2884 | "C:\Users\admin\Desktop\File.exe" | C:\Users\admin\Desktop\File.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: feedback_and_data_software Exit code: 0 Version: 1.2.0.0 Modules
| |||||||||||||||
Total events
16 936
Read events
16 727
Write events
144
Delete events
65
Modification events
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
4
Suspicious files
15
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 300 | RegAsm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3128.31415\prom\ieframe.dll | executable | |
MD5:E83B0AB78E74C9C70647DB94D88669DB | SHA256:84AFB3A5F5AB695E6467795E57E606655DE1029B96B57E05AC4DC1E5E9D2A77F | |||
| 3876 | RegAsm.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:CB74C9519D11B70696475FC269EC1815 | SHA256:0192DC85F901F57C4A346C1F77CE2D5E5193A0B4BBCB6CA51F9F676E95CD87A4 | |||
| 3528 | File.exe | C:\Users\admin\AppData\Local\Temp\Protect544cd51a.dll | executable | |
MD5:544CD51A596619B78E9B54B70088307D | SHA256:DFCE2D4D06DE6452998B3C5B2DC33EAA6DB2BD37810D04E3D02DC931887CFDDD | |||
| 300 | RegAsm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A65DBECD82A40019E873CE4ED0A79570 | binary | |
MD5:16CF4C163BAAF270DE654E6C095EBDF7 | SHA256:88251D280C626312FCC579DA0D1FFE0F914BA7B4690824B071BCEC7810B397E2 | |||
| 300 | RegAsm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\ACF244F1A10D4DBED0D88EBA0C43A9B5_16756CC7371BB76A269719AA1471E96C | binary | |
MD5:D64A3DB970C477F0E9A6BC1723453E43 | SHA256:14495A98E5B9D248D76F2B91405811F6AC8626952EC59D801F1B9DE8EA383FFE | |||
| 300 | RegAsm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:58597D66F34765AE53B69FE5F538B34E | SHA256:C8B117BDC2E7EC2410726D5183EB311D86599626CB51CCF06AB2F364395A2030 | |||
| 300 | RegAsm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A65DBECD82A40019E873CE4ED0A79570 | binary | |
MD5:A25558BF6D9285D5C072EF37A6164B05 | SHA256:5403E78560F5D3A80D153A96FE197EA5CF00FB51786E61E6F14022E40D7491D0 | |||
| 300 | RegAsm.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\BFUZ828R.txt | text | |
MD5:336464B701E7498F133284ADB04C4257 | SHA256:296C0A1195BC4B0DD08D584FC7513C4E76AF7822E54B0E98CB5BDC2364CD16CC | |||
| 3876 | RegAsm.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:FED929AE34422010496B5B4A1827A501 | SHA256:2DDA40A266ECA9DDD736701EFA24C6FE186EDD6737DB7BF52BFFE32D614667ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
34
DNS requests
15
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3876 | RegAsm.exe | GET | 200 | 194.49.94.113:80 | http://194.49.94.113/api/tracemap.php | unknown | text | 15 b | unknown |
300 | RegAsm.exe | GET | 200 | 185.216.70.235:80 | http://185.216.70.235/api/tracemap.php | unknown | text | 15 b | unknown |
300 | RegAsm.exe | POST | 200 | 185.216.70.235:80 | http://185.216.70.235/api/firegate.php | unknown | text | 108 b | unknown |
300 | RegAsm.exe | GET | 200 | 8.60.132.114:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ed283618bfcda275 | unknown | compressed | 4.66 Kb | unknown |
300 | RegAsm.exe | POST | 200 | 185.216.70.235:80 | http://185.216.70.235/api/firegate.php | unknown | text | 108 b | unknown |
300 | RegAsm.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8EJH | unknown | binary | 1.41 Kb | unknown |
300 | RegAsm.exe | GET | 200 | 151.101.2.133:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQMnk2cPe3vhNiR6XLHz4QGvBl7BwQUlt5h8b0cFilTHMDMfTuDAEDmGnwCDFAISJ5g2%2FpXsWindw%3D%3D | unknown | binary | 1.42 Kb | unknown |
300 | RegAsm.exe | GET | 200 | 151.101.2.133:80 | http://ocsp2.globalsign.com/gsorganizationvalsha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQMnk2cPe3vhNiR6XLHz4QGvBl7BwQUlt5h8b0cFilTHMDMfTuDAEDmGnwCDBp4iA5pDYaog9yj8g%3D%3D | unknown | binary | 1.42 Kb | unknown |
300 | RegAsm.exe | POST | 200 | 185.216.70.235:80 | http://185.216.70.235/api/firegate.php | unknown | text | 384 b | unknown |
300 | RegAsm.exe | GET | 200 | 8.60.132.114:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?8cb9185a6b7018b9 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3876 | RegAsm.exe | 194.49.94.113:80 | — | Enes Koken | DE | malicious |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3876 | RegAsm.exe | 104.26.9.59:443 | api.myip.com | CLOUDFLARENET | US | unknown |
3876 | RegAsm.exe | 34.117.59.81:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
300 | RegAsm.exe | 185.216.70.235:80 | — | Enes Koken | US | malicious |
300 | RegAsm.exe | 104.26.8.59:443 | api.myip.com | CLOUDFLARENET | US | unknown |
300 | RegAsm.exe | 104.237.62.213:443 | api64.ipify.org | WEBNX | US | unknown |
300 | RegAsm.exe | 34.117.59.81:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.myip.com |
| malicious |
ipinfo.io |
| shared |
api64.ipify.org |
| unknown |
db-ip.com |
| whitelisted |
www.maxmind.com |
| whitelisted |
vk.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
psv4.userapi.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3876 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
3876 | RegAsm.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET) |
3876 | RegAsm.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
300 | RegAsm.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET) |
300 | RegAsm.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
300 | RegAsm.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
300 | RegAsm.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Check (maxmind.com/geoip) |
3816 | AppLaunch.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
3816 | AppLaunch.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
5 ETPRO signatures available at the full report