| File name: | hanBot Crack.rar |
| Full analysis: | https://app.any.run/tasks/fca54512-3b21-4470-881f-52cbb45ef4c2 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | April 15, 2019, 08:30:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 19F587D342C9C9907206BE589CCD3066 |
| SHA1: | 730CA23ADACF30B7C25DECEC3CBE169A4BE0CE17 |
| SHA256: | 546452AFAB27DB77502978C8A0706B3F3D3C04AA700F31E95818A54F119DCC74 |
| SSDEEP: | 24576:lwCi+HGxfZXfhcJzgZU2726We63v/IqdWJQMvOMzOvVmYfkgQjh2:SCTc0zga7L3v3dwQMjCvYAkg2h2 |
MALICIOUS
Application was dropped or rewritten from another process
- hanBot.Crack.exe (PID: 4028)
- scthosts.exe (PID: 3356)
- scthosts.exe (PID: 2732)
- scthosts.exe (PID: 2196)
- scthosts.exe (PID: 2808)
- tcpstreaming.exe (PID: 2796)
- tcpstreaming.exe (PID: 2968)
- hanBot.Crack.exe (PID: 3376)
Orcus was detected
- hanBot.Crack.exe (PID: 3376)
- scthosts.exe (PID: 2732)
- scthosts.exe (PID: 2808)
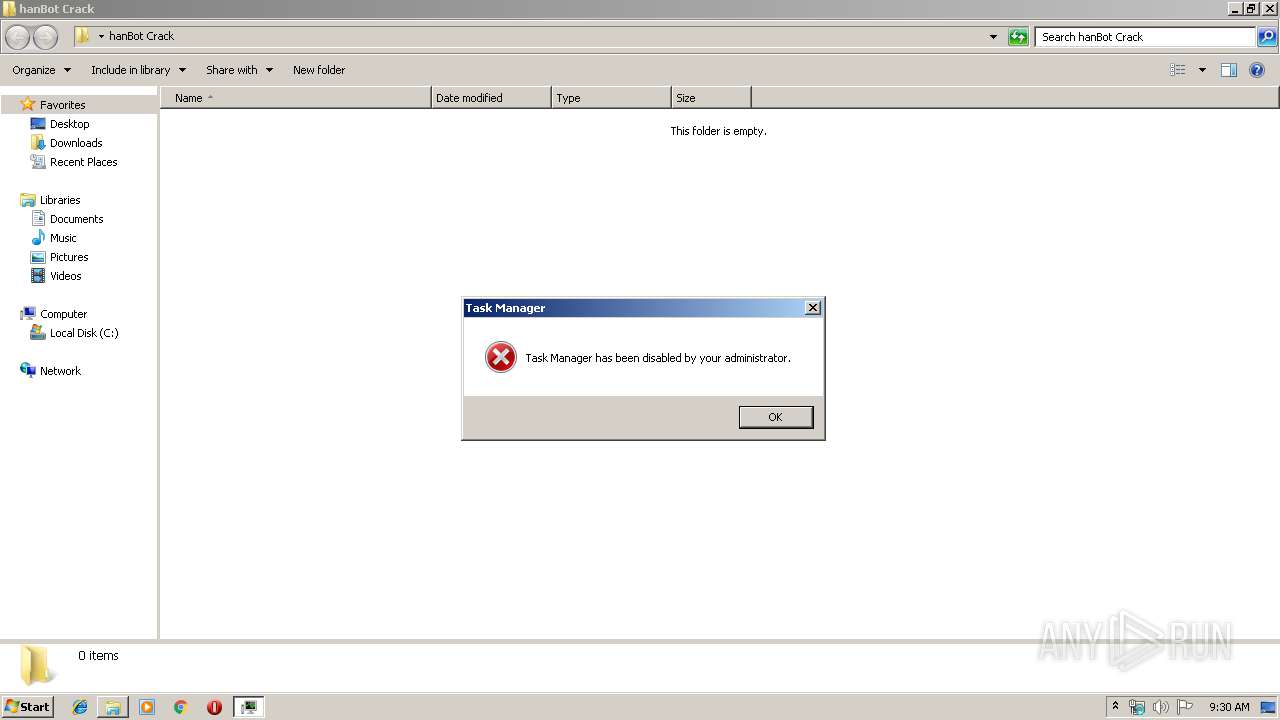
Task Manager has been disabled (taskmgr)
- hanBot.Crack.exe (PID: 4028)
- scthosts.exe (PID: 3356)
- scthosts.exe (PID: 2196)
Changes the autorun value in the registry
- scthosts.exe (PID: 2732)
Loads the Task Scheduler COM API
- scthosts.exe (PID: 2732)
Orcus RAT was detected
- tcpstreaming.exe (PID: 2796)
SUSPICIOUS
Creates files in the program directory
- hanBot.Crack.exe (PID: 3376)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2920)
- hanBot.Crack.exe (PID: 3376)
- scthosts.exe (PID: 2732)
Starts itself from another location
- hanBot.Crack.exe (PID: 3376)
Application launched itself
- scthosts.exe (PID: 3356)
Creates files in the user directory
- scthosts.exe (PID: 2732)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
10
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | "C:\Program Files\Orcus\scthosts.exe" | C:\Program Files\Orcus\scthosts.exe | — | taskeng.exe | |||||||||||
User: admin Company: hanBot Company Integrity Level: HIGH Description: hanBot Scripting Crack Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\Orcus\scthosts.exe" | C:\Program Files\Orcus\scthosts.exe | scthosts.exe | ||||||||||||
User: admin Company: hanBot Company Integrity Level: HIGH Description: hanBot Scripting Crack Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2796 | "C:\Users\admin\AppData\Roaming\tcpstreaming.exe" /launchSelfAndExit "C:\Program Files\Orcus\scthosts.exe" 2732 /protectFile | C:\Users\admin\AppData\Roaming\tcpstreaming.exe | scthosts.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2968 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2808 | "C:\Program Files\Orcus\scthosts.exe" | C:\Program Files\Orcus\scthosts.exe | scthosts.exe | ||||||||||||
User: admin Company: hanBot Company Integrity Level: HIGH Description: hanBot Scripting Crack Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2920 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\hanBot Crack.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2968 | "C:\Users\admin\AppData\Roaming\tcpstreaming.exe" /watchProcess "C:\Program Files\Orcus\scthosts.exe" 2732 "/protectFile" | C:\Users\admin\AppData\Roaming\tcpstreaming.exe | — | tcpstreaming.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3356 | "C:\Program Files\Orcus\scthosts.exe" | C:\Program Files\Orcus\scthosts.exe | — | hanBot.Crack.exe | |||||||||||
User: admin Company: hanBot Company Integrity Level: HIGH Description: hanBot Scripting Crack Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3376 | "C:\Users\admin\Desktop\hanBot Crack\hanBot.Crack.exe" | C:\Users\admin\Desktop\hanBot Crack\hanBot.Crack.exe | hanBot.Crack.exe | ||||||||||||
User: admin Company: hanBot Company Integrity Level: HIGH Description: hanBot Scripting Crack Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3596 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4028 | "C:\Users\admin\Desktop\hanBot Crack\hanBot.Crack.exe" | C:\Users\admin\Desktop\hanBot Crack\hanBot.Crack.exe | explorer.exe | ||||||||||||
User: admin Company: hanBot Company Integrity Level: HIGH Description: hanBot Scripting Crack Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 217
Read events
1 182
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\hanBot Crack.rar | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
3
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2920 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2920.3892\hanBot Crack\hanBot.Crack.exe | executable | |
MD5:— | SHA256:— | |||
| 3376 | hanBot.Crack.exe | C:\Program Files\Orcus\scthosts.exe | executable | |
MD5:— | SHA256:— | |||
| 2732 | scthosts.exe | C:\Users\admin\AppData\Roaming\tcpstreaming.exe.config | xml | |
MD5:A2B76CEA3A59FA9AF5EA21FF68139C98 | SHA256:F99EF5BF79A7C43701877F0BB0B890591885BB0A3D605762647CC8FFBF10C839 | |||
| 3376 | hanBot.Crack.exe | C:\Program Files\Orcus\scthosts.exe.config | xml | |
MD5:A2B76CEA3A59FA9AF5EA21FF68139C98 | SHA256:F99EF5BF79A7C43701877F0BB0B890591885BB0A3D605762647CC8FFBF10C839 | |||
| 2732 | scthosts.exe | C:\Users\admin\AppData\Roaming\tcpstreaming.exe | executable | |
MD5:913967B216326E36A08010FB70F9DBA3 | SHA256:8D880758549220154D2FF4EE578F2B49527C5FB76A07D55237B61E30BCC09E3A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
uyrtyrtyrtyhr.ddns.net |
| malicious |