| File name: | 5437af5e79914042729430bc9068c1d063222c075c0a440fbd601c13ffae30af.ps1 |
| Full analysis: | https://app.any.run/tasks/7e59d985-a039-4b50-9aaa-1ee2e54f048d |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 14, 2024, 03:57:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (65265), with CRLF line terminators |
| MD5: | 76B848945680EA0E25D8CFCAF90898F9 |
| SHA1: | 56E20893150808A0F83BA8942E0BB5BD42B8C810 |
| SHA256: | 5437AF5E79914042729430BC9068C1D063222C075C0A440FBD601C13FFAE30AF |
| SSDEEP: | 24576:DqKQMEfBqn2JyRLD1GqKttY6ILX4itwHzFk+nJTchZvFCkMJYucwADEJaO39:rCf+EyZoRfYHLgR5E/CRYtgRN |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6096)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- errorreporter.exe (PID: 3820)
Connects to the CnC server
- svchost.exe (PID: 2192)
LUMMA mutex has been found
- errorreporter.exe (PID: 3820)
Actions looks like stealing of personal data
- errorreporter.exe (PID: 3820)
Steals credentials from Web Browsers
- errorreporter.exe (PID: 3820)
SUSPICIOUS
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6096)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6096)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6096)
Executable content was dropped or overwritten
- powershell.exe (PID: 6096)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- errorreporter.exe (PID: 3820)
INFO
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6096)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6096)
The process uses the downloaded file
- powershell.exe (PID: 6096)
The executable file from the user directory is run by the Powershell process
- errorreporter.exe (PID: 3820)
Checks supported languages
- errorreporter.exe (PID: 3820)
Reads the computer name
- errorreporter.exe (PID: 3820)
Reads the machine GUID from the registry
- errorreporter.exe (PID: 3820)
Reads the software policy settings
- errorreporter.exe (PID: 3820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
120
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3820 | "C:\Users\admin\AppData\Roaming\URwUsdxX\errorreporter.exe" | C:\Users\admin\AppData\Roaming\URwUsdxX\errorreporter.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6096 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\5437af5e79914042729430bc9068c1d063222c075c0a440fbd601c13ffae30af.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 505
Read events
8 504
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6096) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | NetUtilityApp |
Value: C:\Users\admin\AppData\Roaming\URwUsdxX\errorreporter.exe | |||
Executable files
1
Suspicious files
5
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6096 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\55C6TUR5LSRCY9OXMY1Y.temp | binary | |
MD5:6DE3BAF06A5C9EDF722EF052E05FEB4E | SHA256:176FCB5588167B1C83AAA0B19CB625F451FAE0D925B1AC9AA661D014357E0B62 | |||
| 6096 | powershell.exe | C:\Users\admin\AppData\Roaming\URwUsdxX\errorreporter.exe | executable | |
MD5:4E041C46B85E78E232DAA1093220054F | SHA256:1B664F8A2B34EEA7D3B89AB477583D668DD7BCDE3B226306B84AE48D4AB884CC | |||
| 6096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_douppgac.5o2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
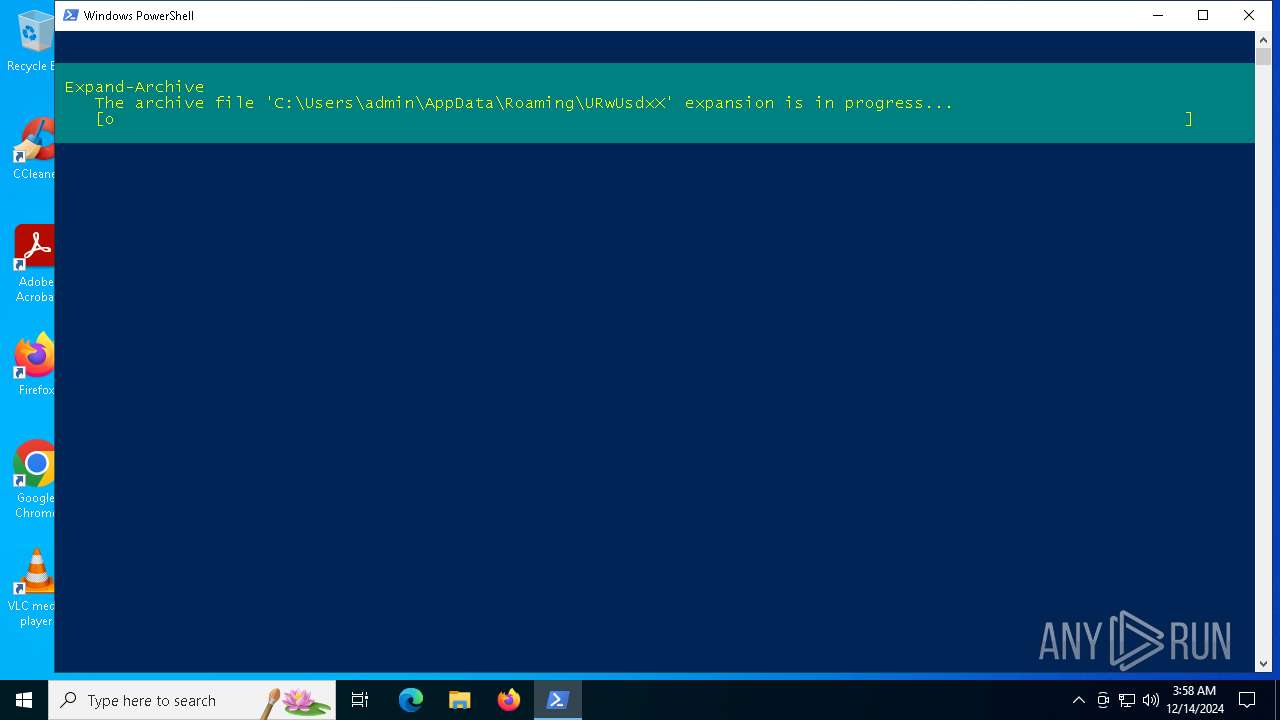
| 6096 | powershell.exe | C:\Users\admin\AppData\Roaming\fKSXNEKA.zip | compressed | |
MD5:FC52585CE16D85F5054ABA80F0CE0D3C | SHA256:99B59C7368F077793619DD93FC8501A8ED4A25107C15358EACF69911D5584408 | |||
| 6096 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:6DE3BAF06A5C9EDF722EF052E05FEB4E | SHA256:176FCB5588167B1C83AAA0B19CB625F451FAE0D925B1AC9AA661D014357E0B62 | |||
| 6096 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1362f3.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ig0bzxjr.gxi.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6096 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:FA533956829C832D87104FB467E08BC6 | SHA256:5D61134E2CB8F12A9AED01F614EFD2FA0851F3BAF4CDE6EC7BF66CFC28C70433 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
27
DNS requests
10
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 172.67.207.38:443 | https://immureprech.biz/api | unknown | text | 17 b | malicious |
— | — | POST | 200 | 104.21.22.222:443 | https://immureprech.biz/api | unknown | text | 18.2 Kb | malicious |
— | — | POST | 200 | 104.21.22.222:443 | https://immureprech.biz/api | unknown | text | 17 b | malicious |
— | — | POST | 200 | 172.67.207.38:443 | https://immureprech.biz/api | unknown | text | 2 b | malicious |
— | — | POST | 200 | 172.67.207.38:443 | https://immureprech.biz/api | unknown | text | 17 b | malicious |
— | — | POST | 200 | 104.21.22.222:443 | https://immureprech.biz/api | unknown | text | 48 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
6092 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6092 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6092 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
debonairnukk.xyz |
| malicious |
immureprech.biz |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (debonairnukk .xyz) |
3820 | errorreporter.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (immureprech .biz in TLS SNI) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (immureprech .biz) |
3820 | errorreporter.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (immureprech .biz in TLS SNI) |
3820 | errorreporter.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (immureprech .biz in TLS SNI) |
3820 | errorreporter.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (immureprech .biz in TLS SNI) |
3820 | errorreporter.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (immureprech .biz in TLS SNI) |
3820 | errorreporter.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (immureprech .biz in TLS SNI) |