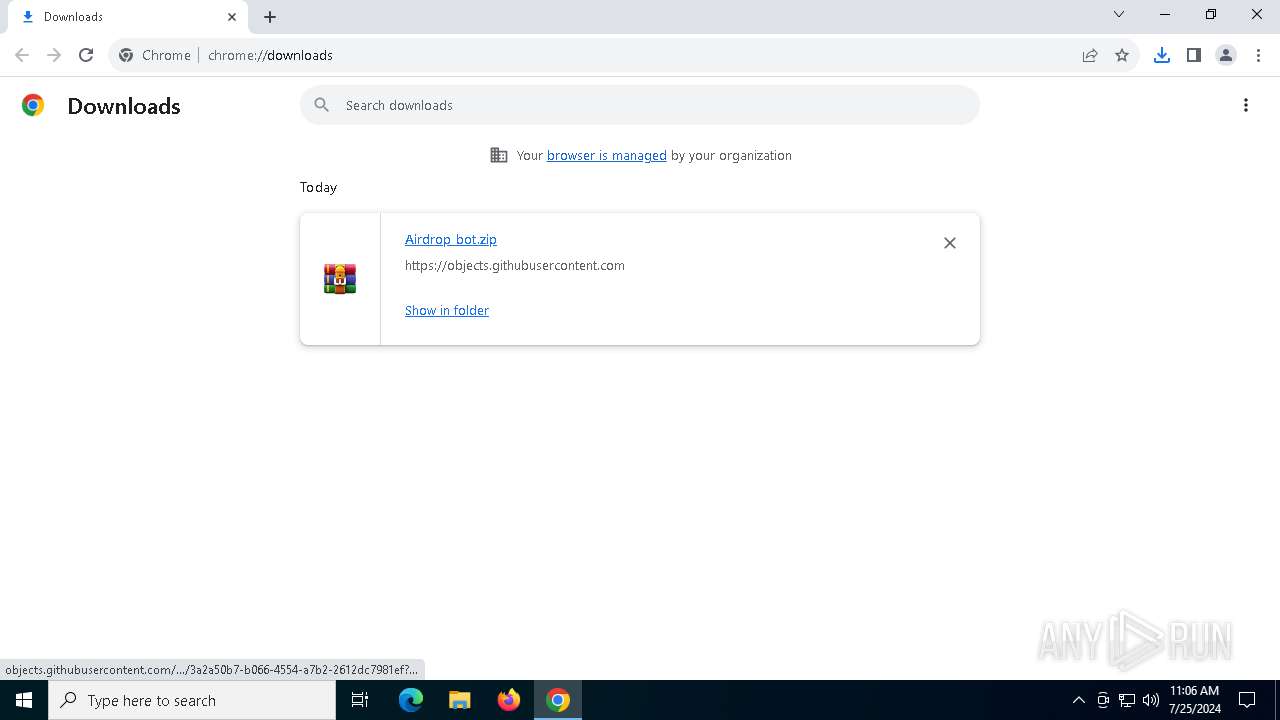
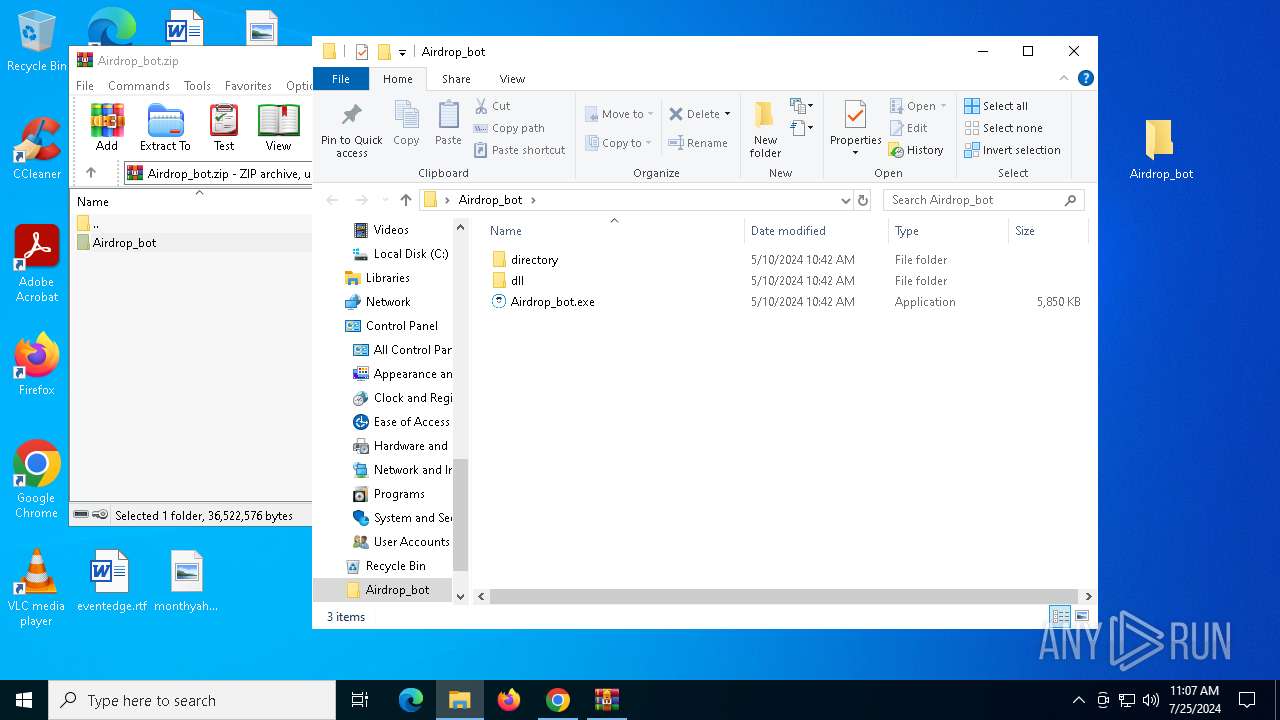
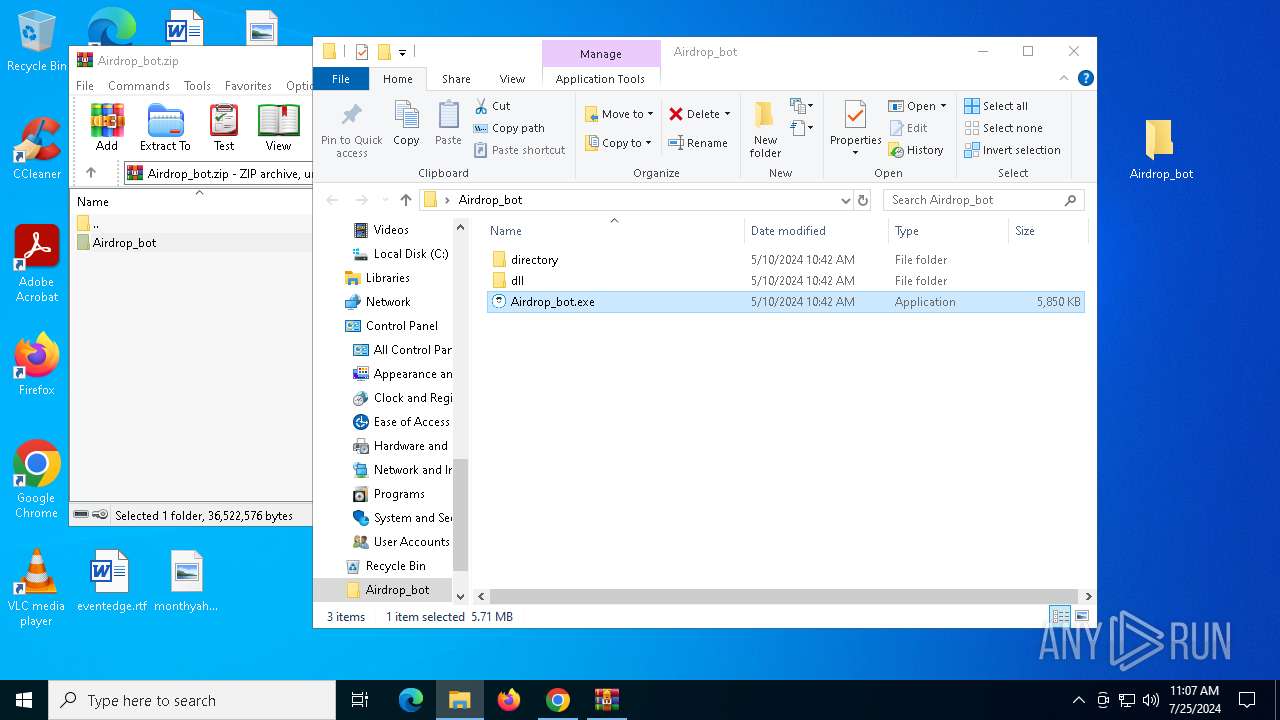
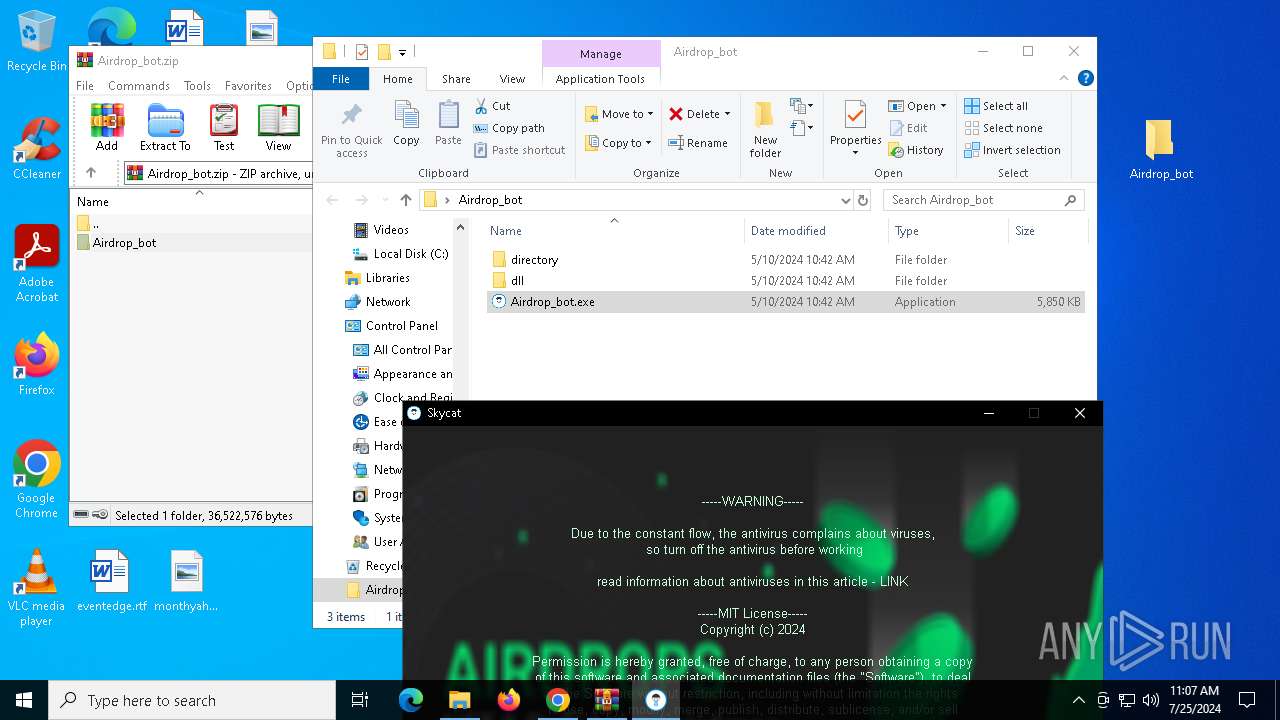
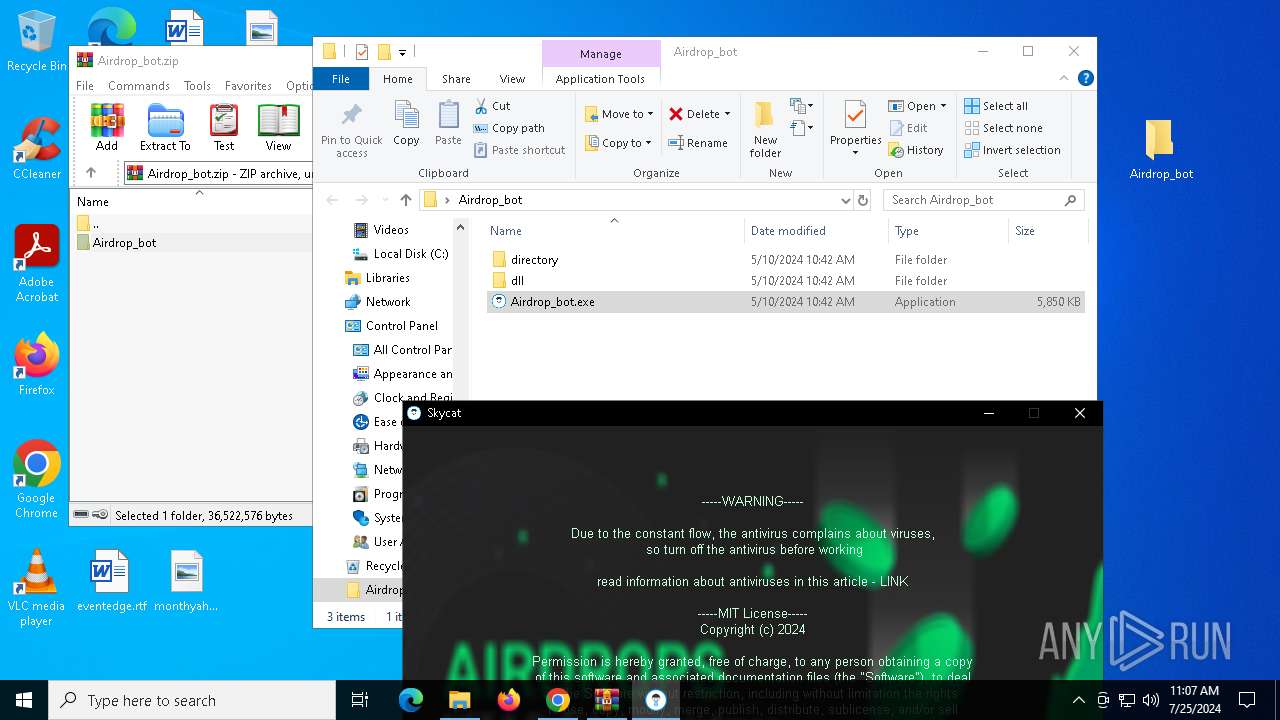
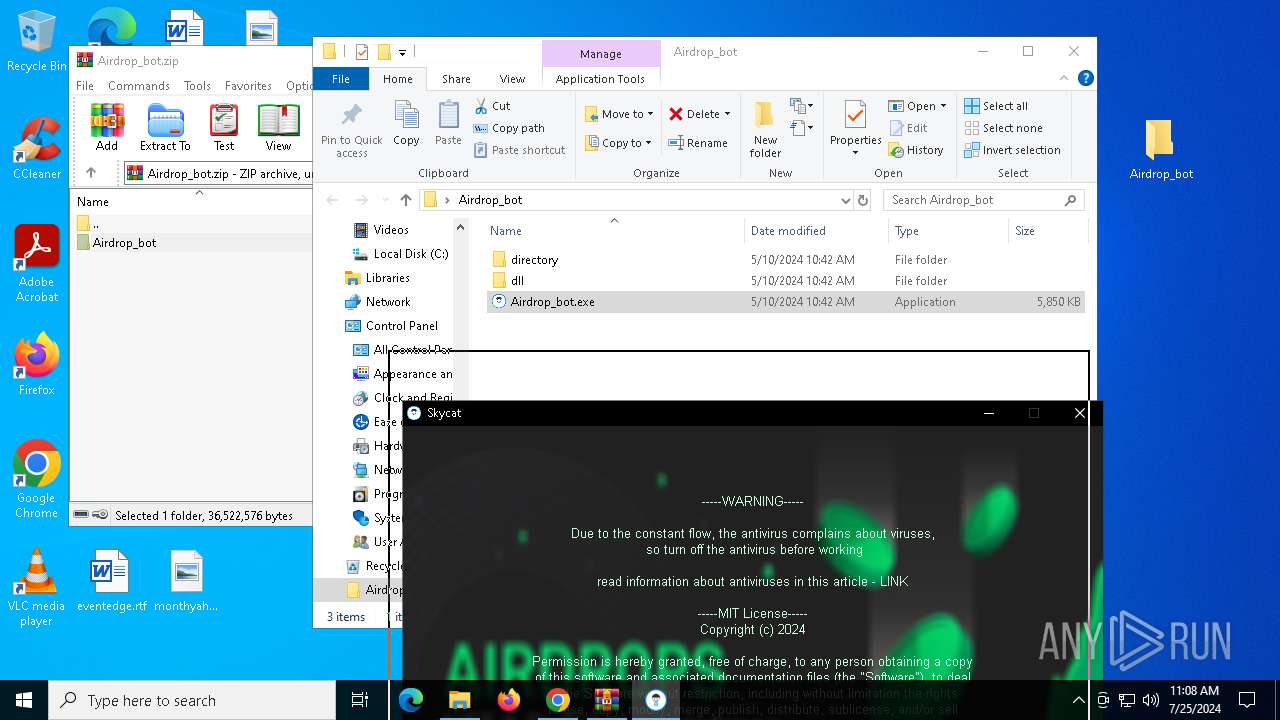
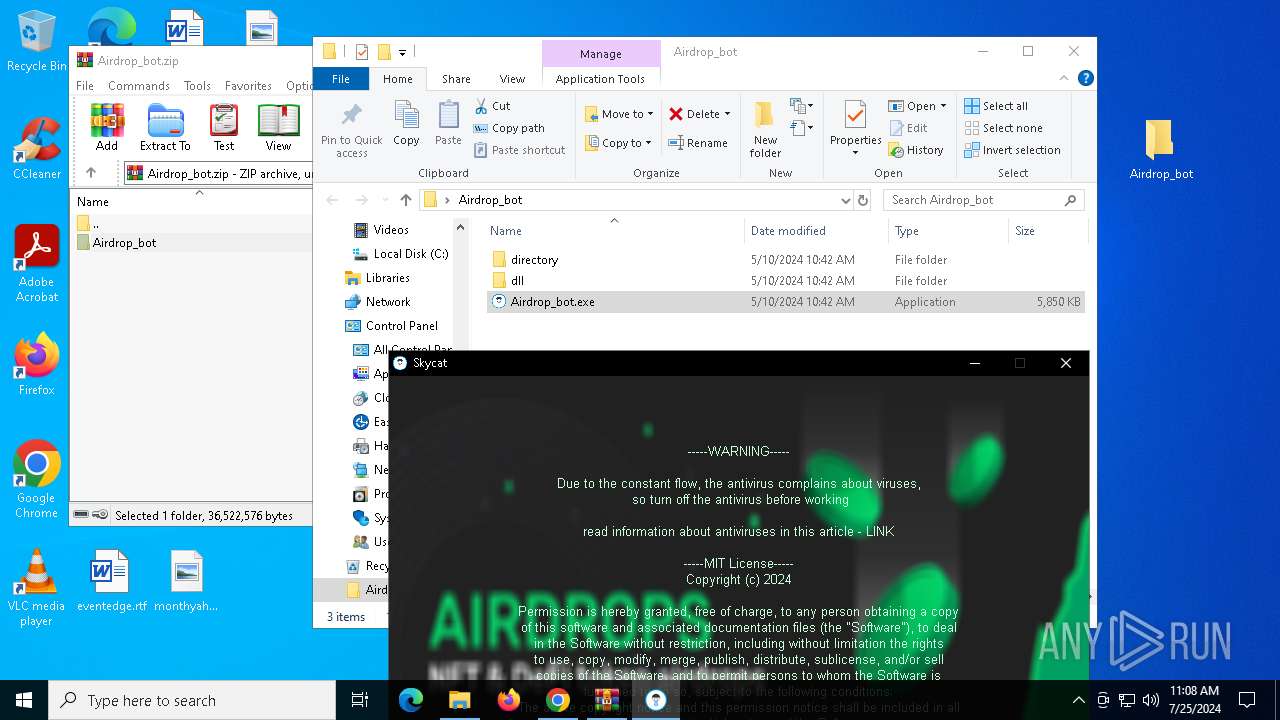
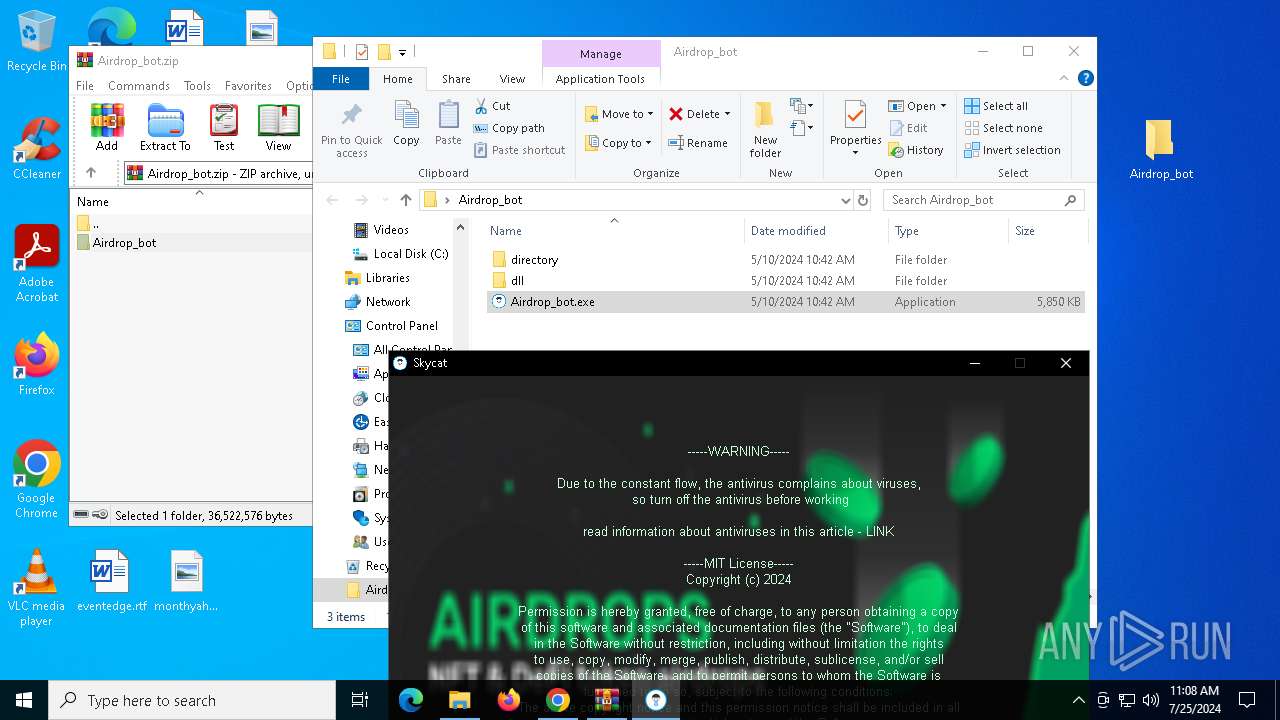
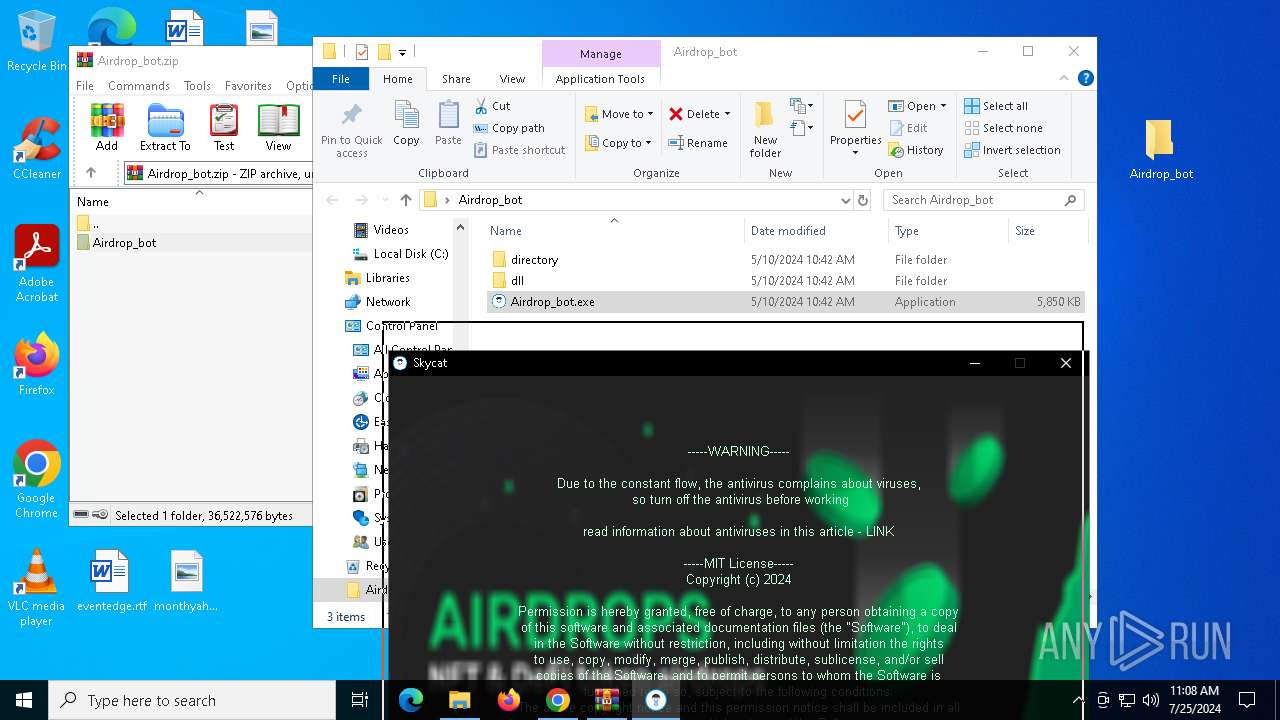
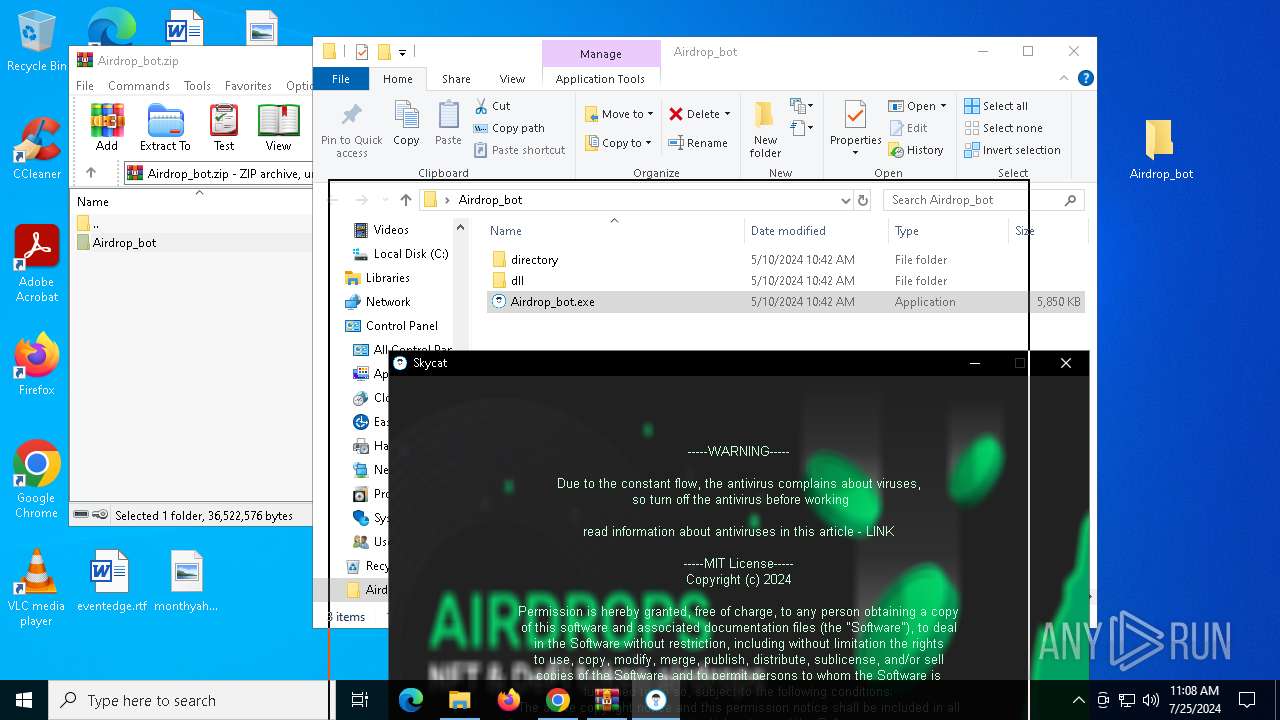
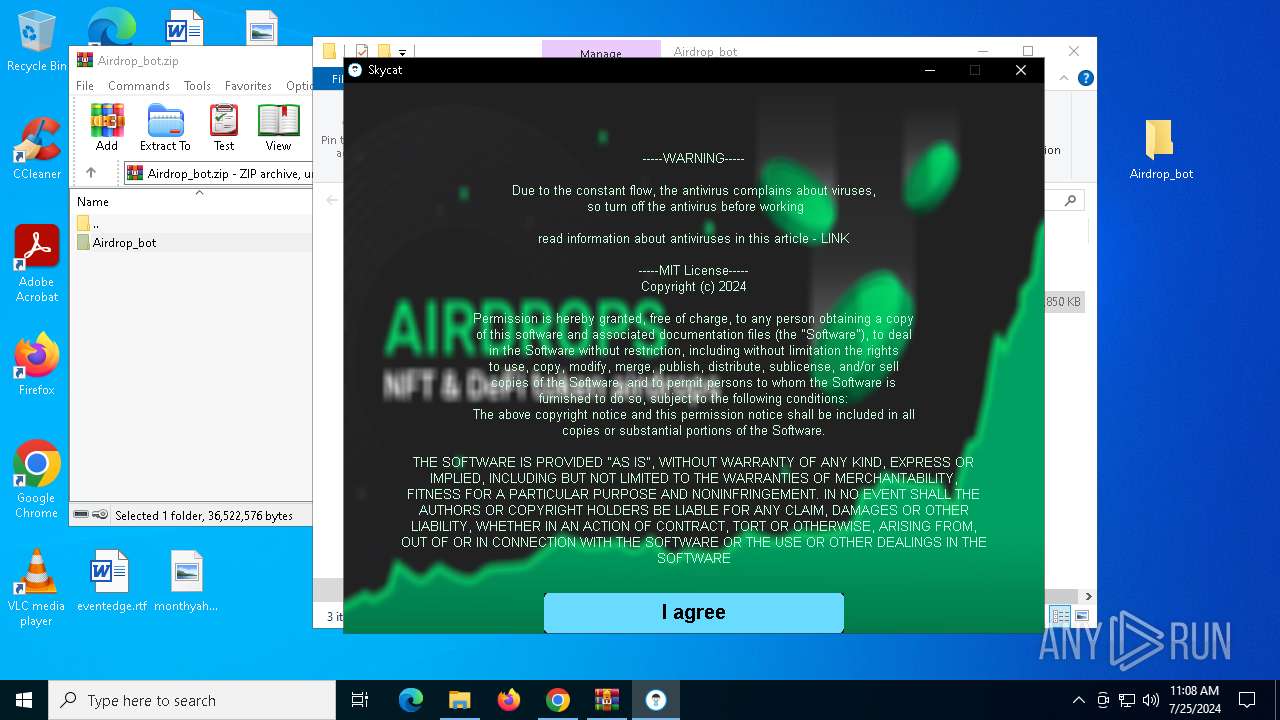
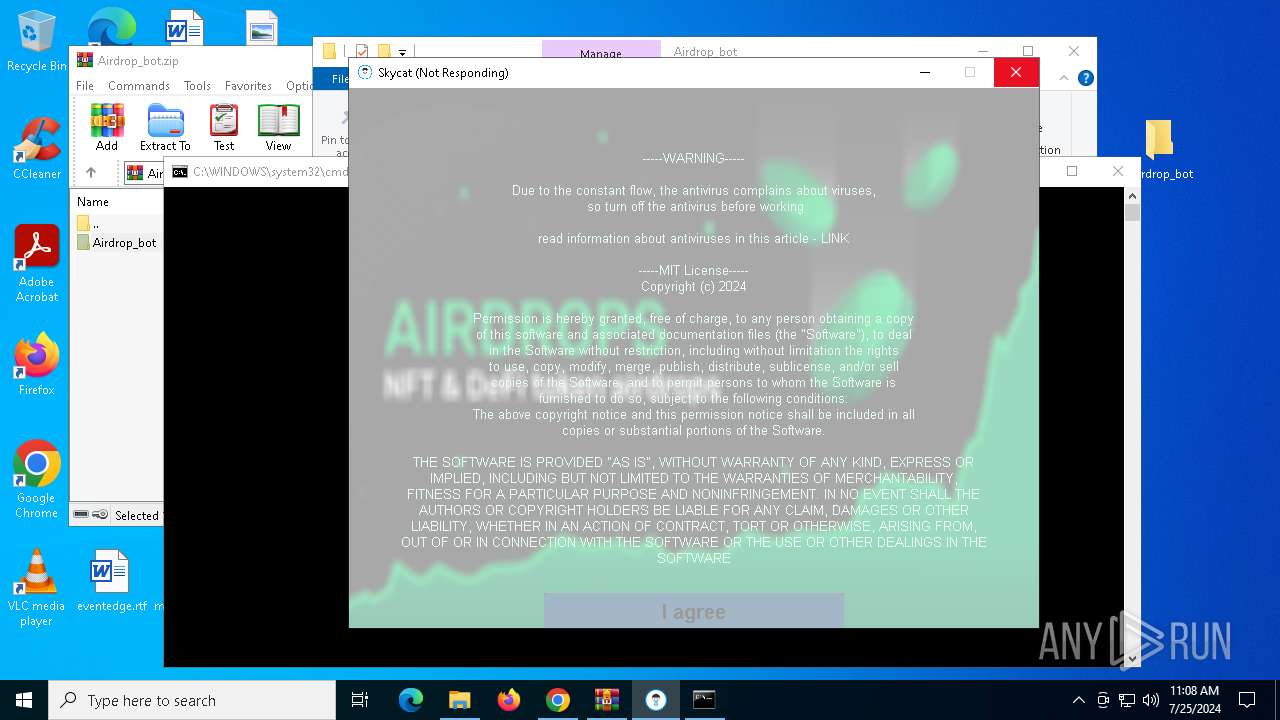
| URL: | https://github.com/Airdrop-hash/Airdrop_bot/releases/download/Download_last_version/Airdrop_bot.zip |
| Full analysis: | https://app.any.run/tasks/5aa44f12-a7ed-43c9-9f5e-786c7df1c541 |
| Verdict: | Malicious activity |
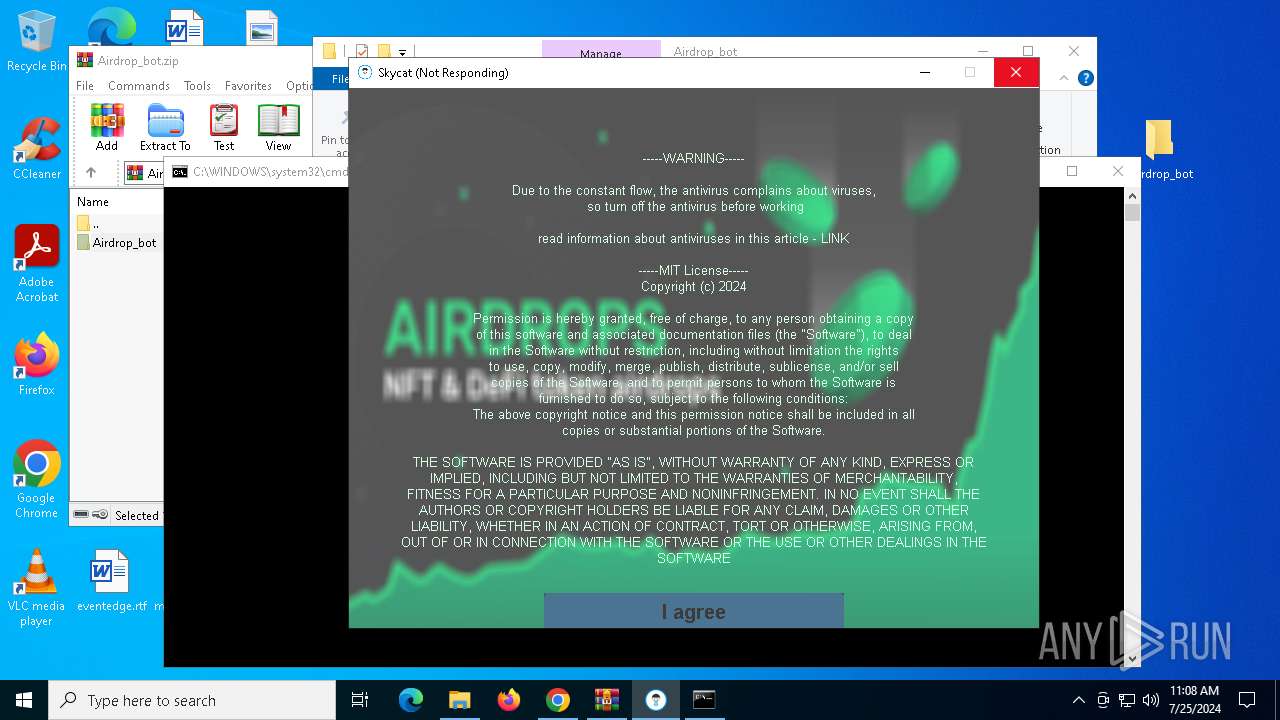
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 25, 2024, 11:05:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 692C01E52DEDFF35298D56CEB66E23E2 |
| SHA1: | FA4B5A9527AF99C366DC464AC53B4733119F3103 |
| SHA256: | 5435F159B9442FD40699EABCA65DD8C96B58EC5B70F5522533ADE2F2DC48FDF0 |
| SSDEEP: | 3:N8tEd97E1AKkCcSLJfMJXzthfn:2uvA1AK9tiRh |
MALICIOUS
LUMMA has been detected (YARA)
- update.exe (PID: 3164)
Drops the executable file immediately after the start
- Airdrop_bot.exe (PID: 3476)
SUSPICIOUS
Reads security settings of Internet Explorer
- Airdrop_bot.exe (PID: 3476)
Loads Python modules
- Airdrop_bot.exe (PID: 3476)
Process drops python dynamic module
- WinRAR.exe (PID: 7840)
Process drops legitimate windows executable
- WinRAR.exe (PID: 7840)
There is functionality for taking screenshot (YARA)
- Airdrop_bot.exe (PID: 3476)
Connects to unusual port
- Airdrop_bot.exe (PID: 3476)
Executes application which crashes
- update.exe (PID: 3164)
Connects to FTP
- Airdrop_bot.exe (PID: 3476)
Executable content was dropped or overwritten
- Airdrop_bot.exe (PID: 3476)
Starts CMD.EXE for commands execution
- Airdrop_bot.exe (PID: 3476)
INFO
Checks proxy server information
- slui.exe (PID: 6056)
- WerFault.exe (PID: 6756)
Manual execution by a user
- Airdrop_bot.exe (PID: 3476)
The process uses the downloaded file
- WinRAR.exe (PID: 7840)
- chrome.exe (PID: 7740)
- chrome.exe (PID: 540)
Reads the software policy settings
- slui.exe (PID: 6056)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7840)
Reads the computer name
- TextInputHost.exe (PID: 116)
- Airdrop_bot.exe (PID: 3476)
- identity_helper.exe (PID: 7984)
- identity_helper.exe (PID: 7304)
- RegAsm.exe (PID: 7688)
Checks supported languages
- TextInputHost.exe (PID: 116)
- Airdrop_bot.exe (PID: 3476)
- identity_helper.exe (PID: 7304)
- identity_helper.exe (PID: 7984)
- update.exe (PID: 3164)
- RegAsm.exe (PID: 7688)
Drops the executable file immediately after the start
- chrome.exe (PID: 540)
- WinRAR.exe (PID: 7840)
Reads Microsoft Office registry keys
- chrome.exe (PID: 540)
- msedge.exe (PID: 2588)
- msedge.exe (PID: 2380)
- Airdrop_bot.exe (PID: 3476)
- msedge.exe (PID: 7412)
Application launched itself
- chrome.exe (PID: 540)
- msedge.exe (PID: 2380)
- msedge.exe (PID: 7412)
- msedge.exe (PID: 2588)
Create files in a temporary directory
- Airdrop_bot.exe (PID: 3476)
Reads Environment values
- identity_helper.exe (PID: 7984)
- identity_helper.exe (PID: 7304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(3164) update.exe
C2 (9)relaxtionflouwerwi.shop
patternapplauderw.shop
detailbaconroollyws.shop
considerrycurrentyws.shop
messtimetabledkolvk.shop
understanndtytonyguw.shop
deprivedrinkyfaiir.shop
varianntyfeecterd.shop
horsedwollfedrwos.shop
Total processes
236
Monitored processes
93
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://github.com/Airdrop-hash/Airdrop_bot/releases/download/Download_last_version/Airdrop_bot.zip" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2260 --field-trial-handle=2428,i,11454591353468660916,17403337071982301851,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1252 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4804 --field-trial-handle=2344,i,6061864613682874117,1849071978687362934,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4264 --field-trial-handle=1908,i,7138431281421226730,5877709344658017146,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3164 --field-trial-handle=1908,i,7138431281421226730,5877709344658017146,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1996 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3924 --field-trial-handle=2344,i,6061864613682874117,1849071978687362934,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2376 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1648 --field-trial-handle=2344,i,6061864613682874117,1849071978687362934,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2380 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2588 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://answers.microsoft.com/en-us/windows/forum/all/why-is-my-python-exe-always-get-detected-as/6822a41e-0208-47ec-8c45-f9f9e5401d9b | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | Airdrop_bot.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
39 004
Read events
38 832
Write events
160
Delete events
12
Modification events
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (540) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
78
Suspicious files
600
Text files
1 106
Unknown types
96
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe242d.TMP | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe243d.TMP | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2044f396-e4e2-462d-ba15-59de64d697ce.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
155
DNS requests
190
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8120 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dvn6tjyuqqxdoyobslkdwn7pvi_2024.4.15.1148/ggkkehgbnfjpeggfpleeakpidbkibbmn_2024.4.15.1148_all_ad7h2np2zton5orbcmedhdzcqjqa.crx3 | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8120 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dvn6tjyuqqxdoyobslkdwn7pvi_2024.4.15.1148/ggkkehgbnfjpeggfpleeakpidbkibbmn_2024.4.15.1148_all_ad7h2np2zton5orbcmedhdzcqjqa.crx3 | unknown | — | — | whitelisted |
8120 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dvn6tjyuqqxdoyobslkdwn7pvi_2024.4.15.1148/ggkkehgbnfjpeggfpleeakpidbkibbmn_2024.4.15.1148_all_ad7h2np2zton5orbcmedhdzcqjqa.crx3 | unknown | — | — | whitelisted |
8120 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/admyr2veie7qjmxqbbcrx5bzw25a_3036/jflookgnkcckhobaglndicnbbgbonegd_3036_all_dps2mhamenj2ey2s4kt5h3wjgq.crx3 | unknown | — | — | whitelisted |
8120 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
7016 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2256 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8120 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2612 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.20.142.186:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6200 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4204 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6884 | chrome.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
540 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3044 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3044 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3044 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msftauth .net) |
3044 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
3476 | Airdrop_bot.exe | Misc activity | ET HUNTING ZIP file download over raw TCP |
2284 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (varianntyfeecterd .shop) |
2284 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup |
2284 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup |
2284 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup |
2284 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup |