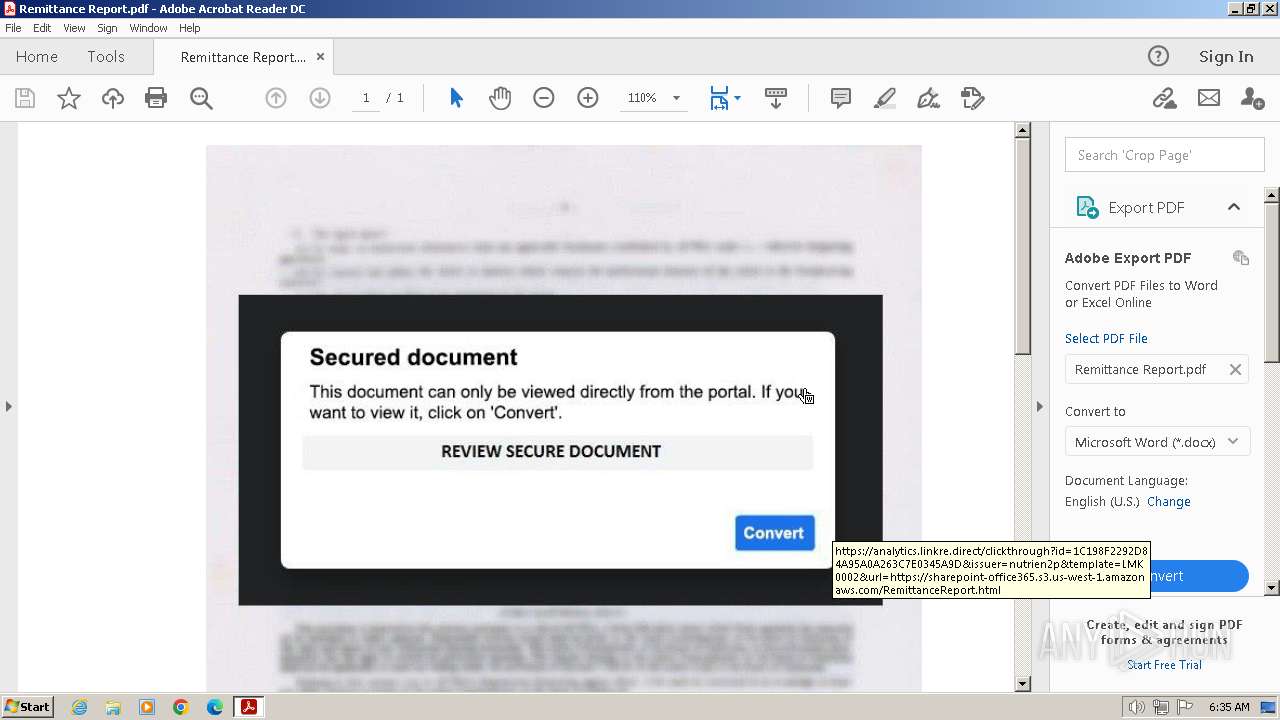
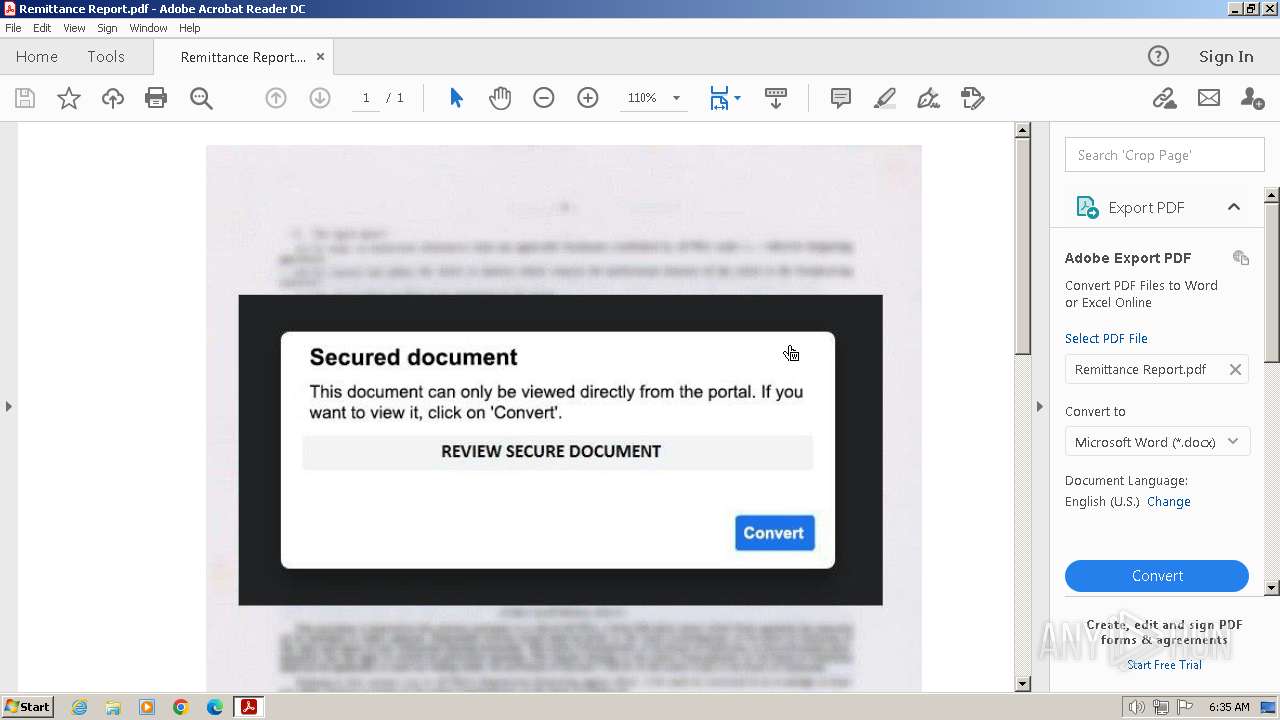
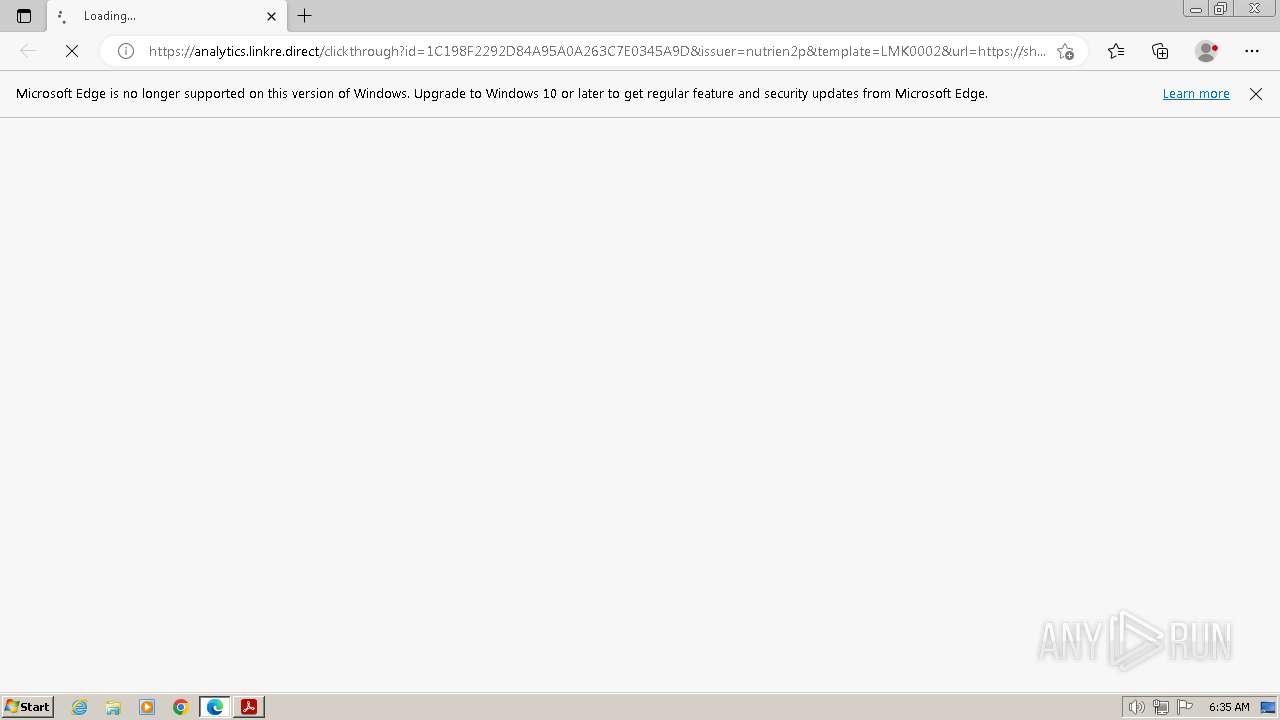
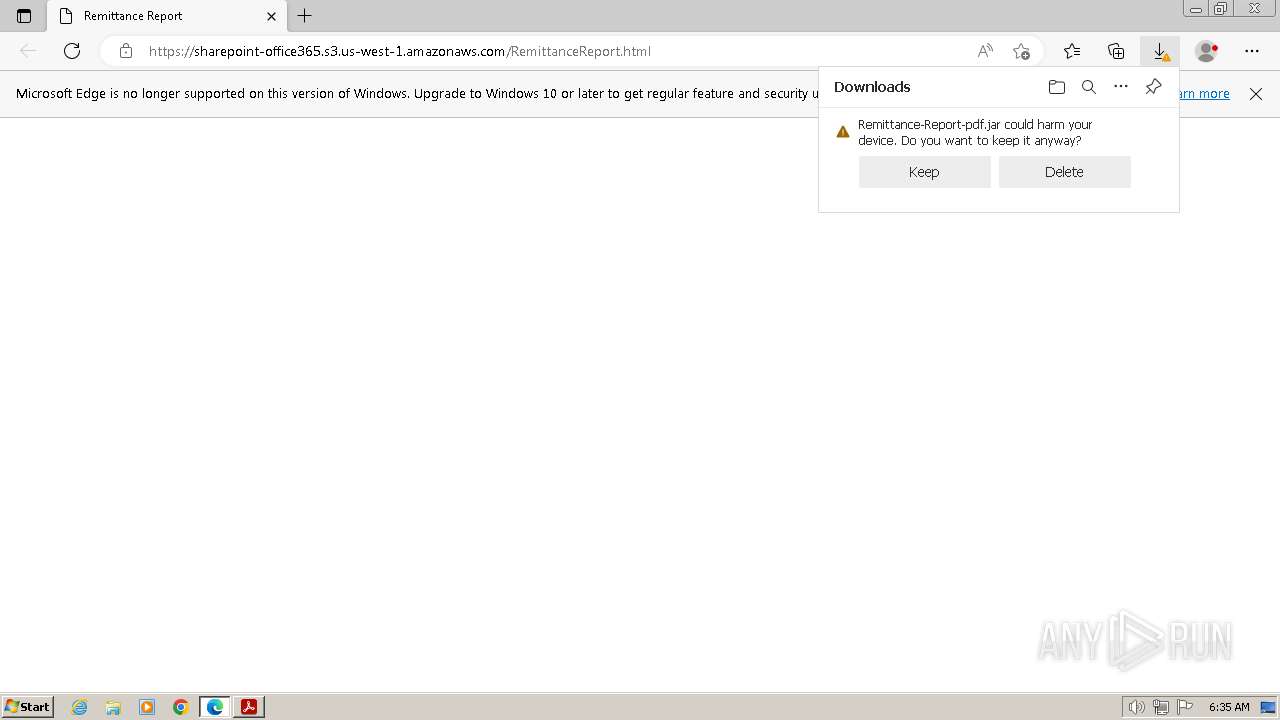
| File name: | Remittance Report.pdf |
| Full analysis: | https://app.any.run/tasks/950c4a5a-077c-439d-ae92-0e0b1c45e267 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | February 16, 2024, 06:34:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.7, 1 pages |
| MD5: | B3A5B0076BDF6A50E460DC477BDF2E4E |
| SHA1: | EF0A2B02AA98F79E4960BFF6E52E7F9BFBA14E92 |
| SHA256: | 53AAA536CB192034717C9307709AF793D5192869A2093C1343F09CCFF6E7126F |
| SSDEEP: | 768:6/IlwYVQVp0vlYWuZUmjglpcCglYYVS9a+SqS9Msq2EKLBxYM1SzBhnuvOuEIRue:dwwm8lpc/YYo9aXV9BsKLBxX1SzBja |
MALICIOUS
StrRat is detected
- javaw.exe (PID: 2504)
- javaw.exe (PID: 3568)
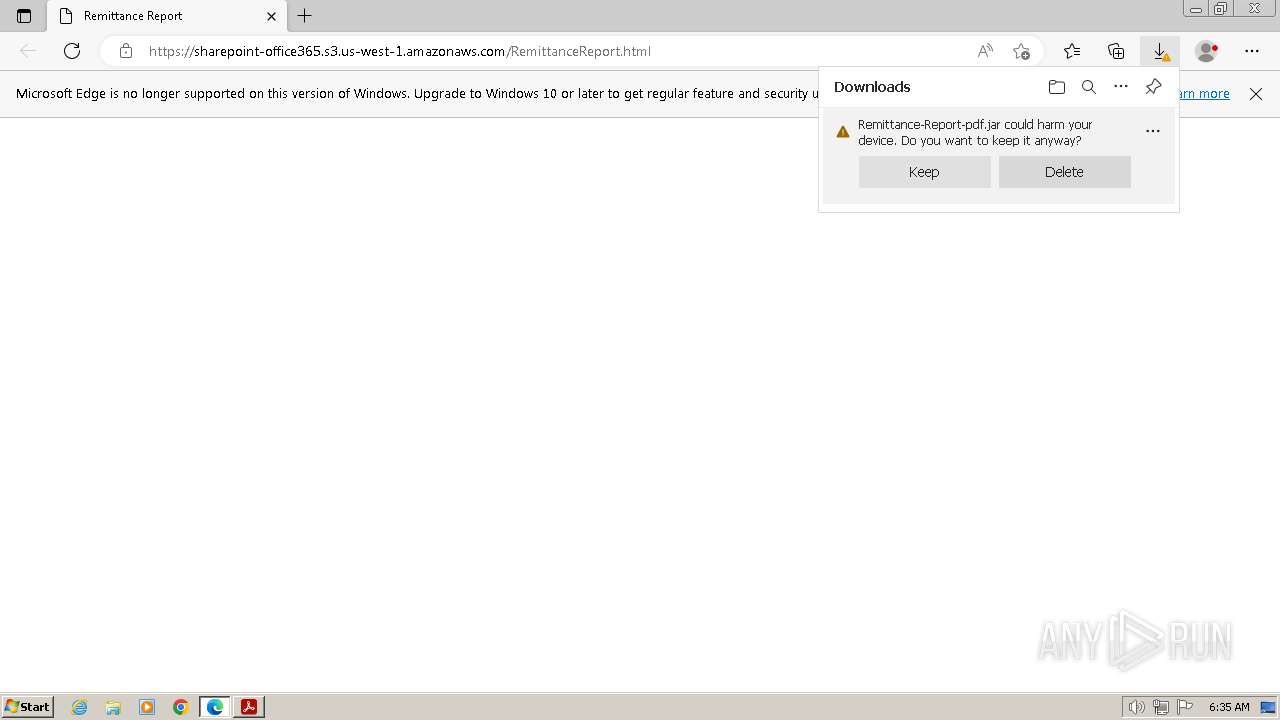
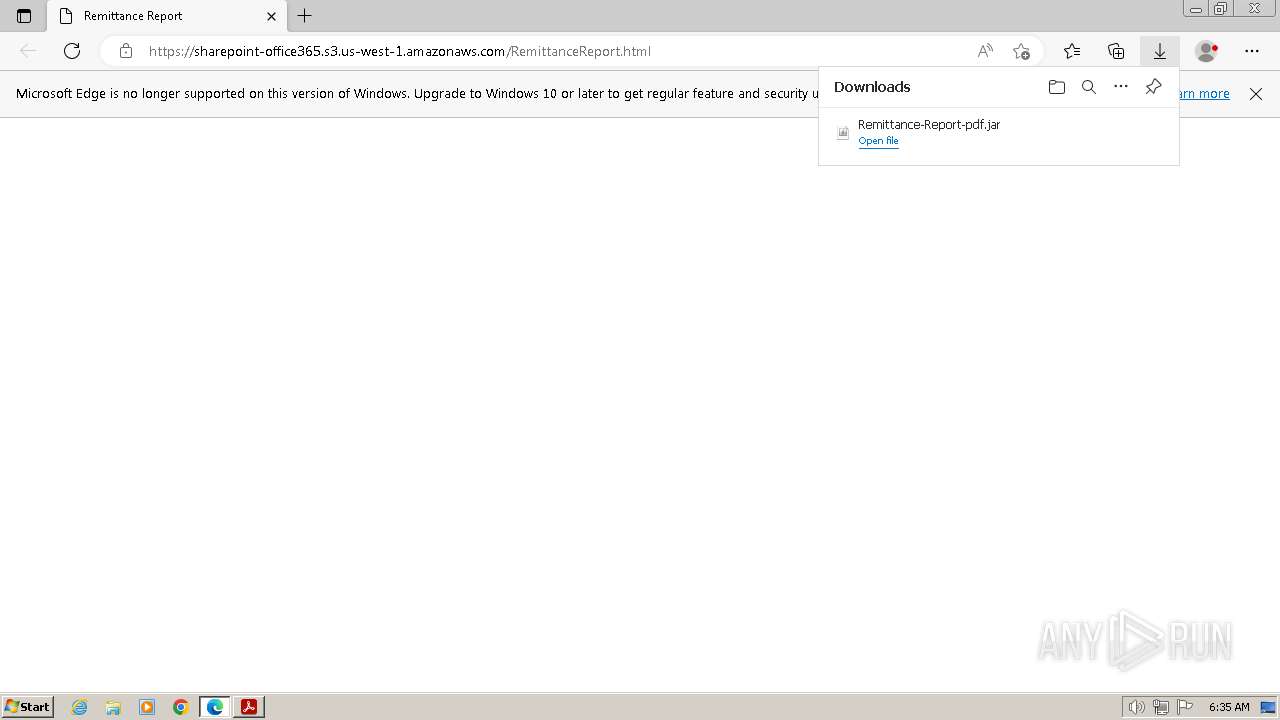
Drops the executable file immediately after the start
- java.exe (PID: 2424)
- java.exe (PID: 4064)
- java.exe (PID: 3060)
Create files in the Startup directory
- java.exe (PID: 2424)
STRRAT has been detected (SURICATA)
- java.exe (PID: 3060)
STRRAT has been detected (YARA)
- java.exe (PID: 3060)
- java.exe (PID: 2980)
- javaw.exe (PID: 3568)
Changes the autorun value in the registry
- java.exe (PID: 3060)
Connects to the CnC server
- java.exe (PID: 3060)
SUSPICIOUS
Application launched itself
- java.exe (PID: 2424)
- java.exe (PID: 4064)
Starts CMD.EXE for commands execution
- java.exe (PID: 2424)
- java.exe (PID: 4064)
- java.exe (PID: 3060)
Executable content was dropped or overwritten
- java.exe (PID: 4064)
- java.exe (PID: 2424)
- java.exe (PID: 3060)
Reads the Internet Settings
- WMIC.exe (PID: 3040)
- WMIC.exe (PID: 2572)
- WMIC.exe (PID: 2756)
- WMIC.exe (PID: 3496)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2324)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2976)
- cmd.exe (PID: 956)
Uses WMIC.EXE to obtain volume information
- cmd.exe (PID: 2316)
Connects to unusual port
- java.exe (PID: 3060)
Checks for external IP
- java.exe (PID: 3060)
INFO
Creates files in the program directory
- javaw.exe (PID: 3200)
Checks supported languages
- javaw.exe (PID: 3200)
- javaw.exe (PID: 2504)
- java.exe (PID: 2424)
- java.exe (PID: 4064)
- java.exe (PID: 3060)
- java.exe (PID: 2980)
- javaw.exe (PID: 3568)
Application launched itself
- msedge.exe (PID: 2384)
- AcroRd32.exe (PID: 2472)
- RdrCEF.exe (PID: 1492)
Reads Microsoft Office registry keys
- AcroRd32.exe (PID: 3916)
The process uses the downloaded file
- msedge.exe (PID: 3104)
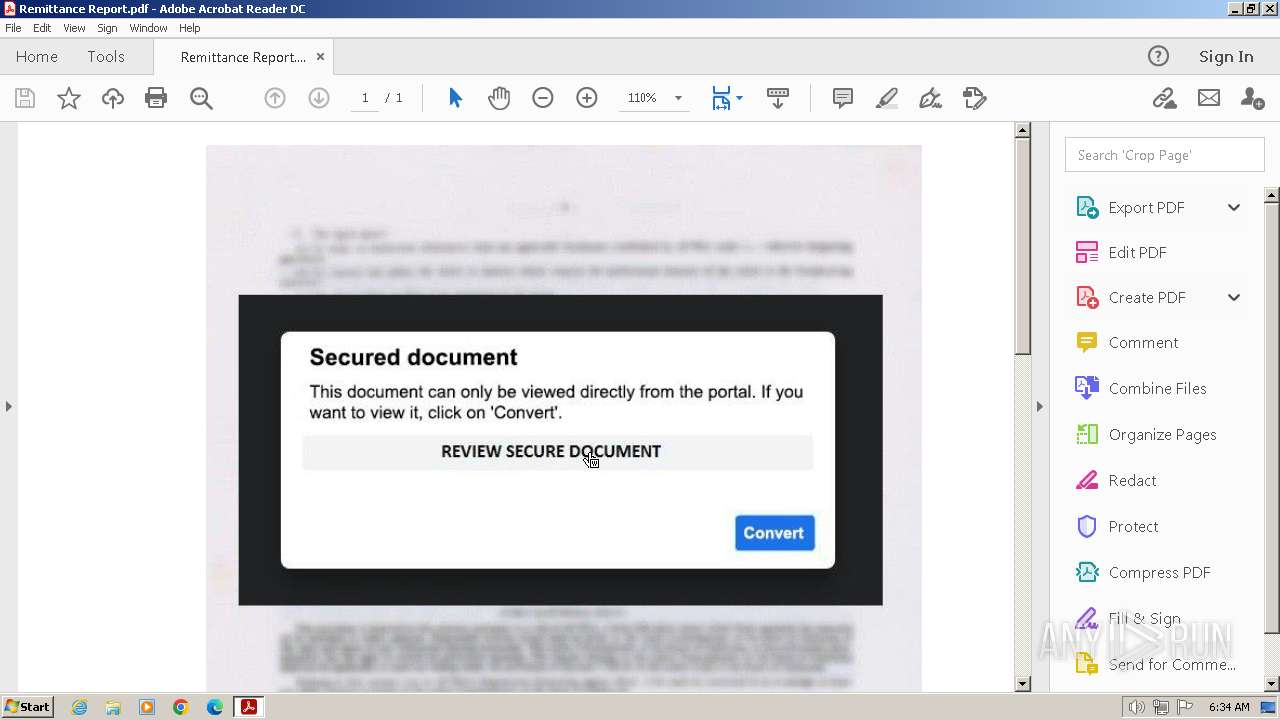
An automatically generated document
- AcroRd32.exe (PID: 2472)
Reads the machine GUID from the registry
- javaw.exe (PID: 3200)
- java.exe (PID: 2424)
- java.exe (PID: 4064)
- java.exe (PID: 3060)
Reads the computer name
- javaw.exe (PID: 3200)
- javaw.exe (PID: 2504)
- java.exe (PID: 2424)
- java.exe (PID: 4064)
- java.exe (PID: 3060)
- java.exe (PID: 2980)
- javaw.exe (PID: 3568)
Create files in a temporary directory
- javaw.exe (PID: 3200)
- javaw.exe (PID: 2504)
- java.exe (PID: 2424)
- java.exe (PID: 4064)
- java.exe (PID: 3060)
- java.exe (PID: 2980)
- javaw.exe (PID: 3568)
Manual execution by a user
- javaw.exe (PID: 2504)
- javaw.exe (PID: 3568)
Drops the executable file immediately after the start
- RdrCEF.exe (PID: 1492)
Creates files or folders in the user directory
- java.exe (PID: 2424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
STRRAT
(PID) Process(3060) java.exe
C2ofornta.ddns.net
Port2033
URLhttp://jbfrost.live/strigoi/server/?hwid=1&lid=m&ht=5
Options
Startup Folder Persistencefalse
Secondary Startup Folder Persistencetrue
Skype Scheduled Task Persistencetrue
Proxybackinghof.ddns.net
LIDkhonsa
(PID) Process(2980) java.exe
C2ofornta.ddns.net
Port2033
URLhttp://jbfrost.live/strigoi/server/?hwid=1&lid=m&ht=5
Options
Startup Folder Persistencefalse
Secondary Startup Folder Persistencetrue
Skype Scheduled Task Persistencetrue
Proxybackinghof.ddns.net
LIDkhonsa
(PID) Process(3568) javaw.exe
C2ofornta.ddns.net
Port2033
URLhttp://jbfrost.live/strigoi/server/?hwid=1&lid=m&ht=5
Options
Startup Folder Persistencefalse
Secondary Startup Folder Persistencetrue
Skype Scheduled Task Persistencetrue
Proxybackinghof.ddns.net
LIDkhonsa
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.7 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Language: | en-US |
| TaggedPDF: | Yes |
| Author: | user |
| Creator: | Microsoft® Word 2016 |
| CreateDate: | 2024:02:15 20:25:51-08:00 |
| ModifyDate: | 2024:02:15 20:25:51-08:00 |
| Producer: | Microsoft® Word 2016 |
XMP
| XMPToolkit: | 3.1-701 |
|---|---|
| Producer: | Microsoft® Word 2016 |
| Creator: | user |
| CreatorTool: | Microsoft® Word 2016 |
| CreateDate: | 2024:02:15 20:25:51-08:00 |
| ModifyDate: | 2024:02:15 20:25:51-08:00 |
| DocumentID: | uuid:2B47444A-BDD3-4D38-8084-00983BF73F8E |
| InstanceID: | uuid:2B47444A-BDD3-4D38-8084-00983BF73F8E |
Total processes
101
Monitored processes
51
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3600 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 532 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1336 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1608 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1172,2889408981078608500,9684078695080420971,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17099279243518368147 --renderer-client-id=7 --mojo-platform-channel-handle=1556 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2200 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 956 | cmd.exe /c "wmic /node:. /namespace:'\\root\cimv2' path win32_operatingsystem get caption,OSArchitecture /format:list" | C:\Windows\System32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 992 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1540 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3876 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2232 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1408 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --mojo-platform-channel-handle=3496 --field-trial-handle=1216,i,10418442031172271811,5809728184186559873,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
34 013
Read events
33 896
Write events
98
Delete events
19
Modification events
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | aDefaultRHPViewModeL |
Value: Expanded | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | iNumReaderLaunches |
Value: 6 | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FillSign |
| Operation: | write | Name: | uFillSignVariantTrackingTime |
Value: | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ToolsSearch |
| Operation: | write | Name: | iSearchHintIndex |
Value: 0 | |||
| (PID) Process: | (2472) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3916) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement |
| Operation: | write | Name: | bNormalExit |
Value: 0 | |||
Executable files
13
Suspicious files
123
Text files
49
Unknown types
116
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1492 | RdrCEF.exe | — | ||
MD5:— | SHA256:— | |||
| 1492 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\560e9c8bff5008d8_0 | binary | |
MD5:CBF50A64D743757D461CA2760FE017F4 | SHA256:F69AE8423AD4E2992722166E7E0E28B301EA582B4FC19C801EA82B3058435D68 | |||
| 1492 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:334CE16E76B6B13D75AE60C60024E534 | SHA256:D9129FF1A9584A0AD461BB017B76F74FA90E11D53D84F847A0F4F728D36CDEF8 | |||
| 1492 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\86b8040b7132b608_0 | binary | |
MD5:0B3DBA3F98BE4DF6667DC60C952074F8 | SHA256:63E46BD0A40B1031B039CF872737F3B9E1082973B931A7E6C8D0C716B99EA7DF | |||
| 1492 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:1689F62A2AB2742E51DA7EBA01688689 | SHA256:E5A0B36F1C000A3DB95CD46FD225D029ACE026E05AE6A9EFD1DCE9879A50611B | |||
| 3916 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 1492 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:45AD93945F396015DD3914036F198E6D | SHA256:E67201A55B7745A7192E890E9EDF7E5432877BE43EF33DDA9D8ACC9DF2E84AC4 | |||
| 3916 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\SOPHIA.json | binary | |
MD5:01F233C92A89C705229A0D63D09F846A | SHA256:62137C4381ACC2DE8BCA158AD9D9CE730BD7A96A39A2FB64CE7CFA5C861CF7B4 | |||
| 1492 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:D70E24A8941171BA6B1BCD6383625CA5 | SHA256:910B76234D720970F761A3E6523265A0649AC4A7FC5C5EF07C3729F2A5314CAC | |||
| 1492 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\d449e58cb15daaf1_0 | binary | |
MD5:8FB5296799028C0D1740CDC6E5487D3B | SHA256:D24BAAEB49C53C80FE36E9E405095C44A8E80D249E9AE5640F2F102F742C5377 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
42
DNS requests
34
Threats
35
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2472 | AcroRd32.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?93d47f0314f78b56 | unknown | — | — | unknown |
2472 | AcroRd32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3060 | java.exe | GET | 200 | 170.64.194.9:80 | http://str-master.pw/strigoi/server/ping.php?lid=khonsari | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1dd404ff67a3d8ee | unknown | compressed | 65.2 Kb | unknown |
3060 | java.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 312 b | unknown |
1080 | svchost.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6776476d79efed94 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1492 | RdrCEF.exe | 23.32.184.135:443 | geo2.adobe.com | AKAMAI-AS | BR | unknown |
1492 | RdrCEF.exe | 107.22.247.231:443 | p13n.adobe.io | AMAZON-AES | US | unknown |
1492 | RdrCEF.exe | 2.18.96.131:443 | armmf.adobe.com | Akamai International B.V. | FR | unknown |
2472 | AcroRd32.exe | 88.221.110.59:443 | acroipm2.adobe.com | Akamai International B.V. | DE | unknown |
2472 | AcroRd32.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2472 | AcroRd32.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2384 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
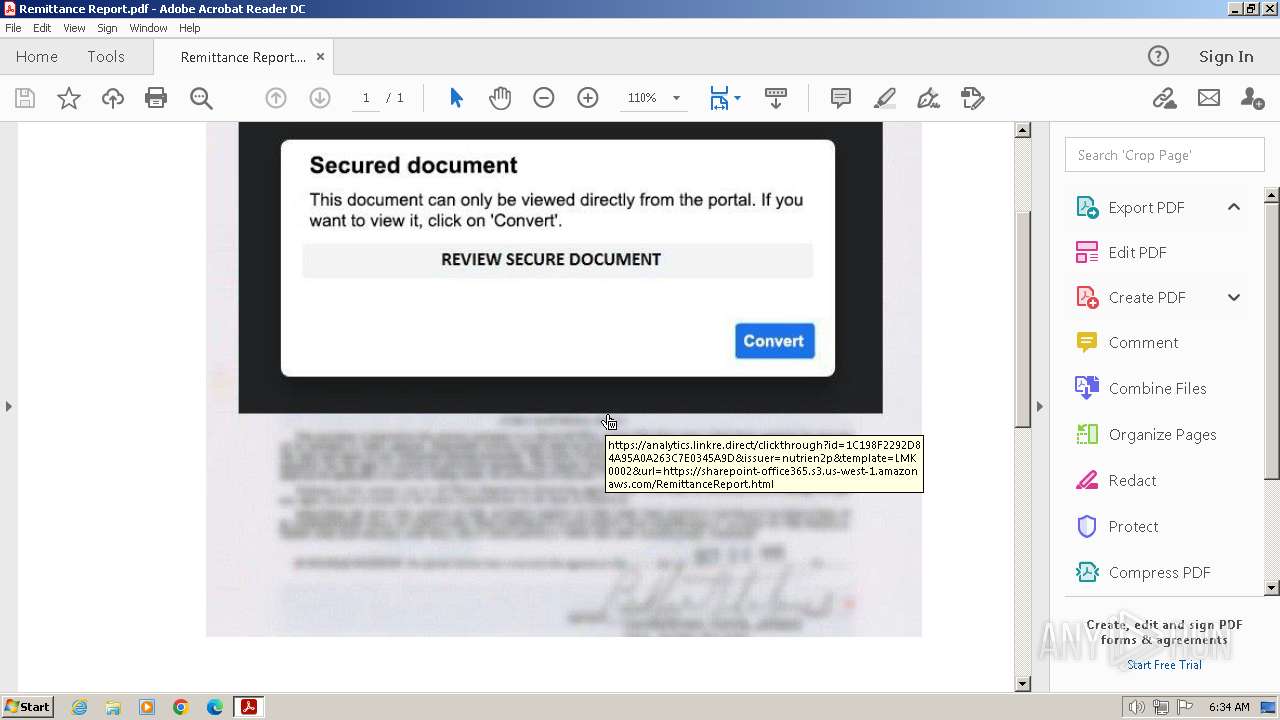
analytics.linkre.direct |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
sharepoint-office365.s3.us-west-1.amazonaws.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
3060 | java.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3060 | java.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
3060 | java.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3060 | java.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3060 | java.exe | Malware Command and Control Activity Detected | ET MALWARE STRRAT CnC Checkin |
3060 | java.exe | Malware Command and Control Activity Detected | ET MALWARE STRRAT CnC Checkin |
3060 | java.exe | Malware Command and Control Activity Detected | ET MALWARE STRRAT CnC Checkin |
3060 | java.exe | Malware Command and Control Activity Detected | ET MALWARE STRRAT CnC Checkin |
1 ETPRO signatures available at the full report