| File name: | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe |
| Full analysis: | https://app.any.run/tasks/2cd68d52-65ea-4b18-859e-3b2be60a6d52 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 25, 2025, 00:40:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 54DBE54846A05D5A1677A5AB2970BD6A |
| SHA1: | 4EA5792F72F540C58A54F5CFCE9DE19EB05FFAAA |
| SHA256: | 53965F472183C0E8EC94202B3BA0716FAF8E095E073A688F3396C4B8DCCA6F30 |
| SSDEEP: | 24576:BPfvfwP83PK9OP2aGc0YI38Y0MUXnhhApL9h+FzgC/9L0p96WmPk9xoPpjvwnM1v:BPfvfwP83PK9OP2aGc0YI38Y0MUXnhhN |
MALICIOUS
RAT has been found (auto)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
Uses Task Scheduler to run other applications
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
Actions looks like stealing of personal data
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
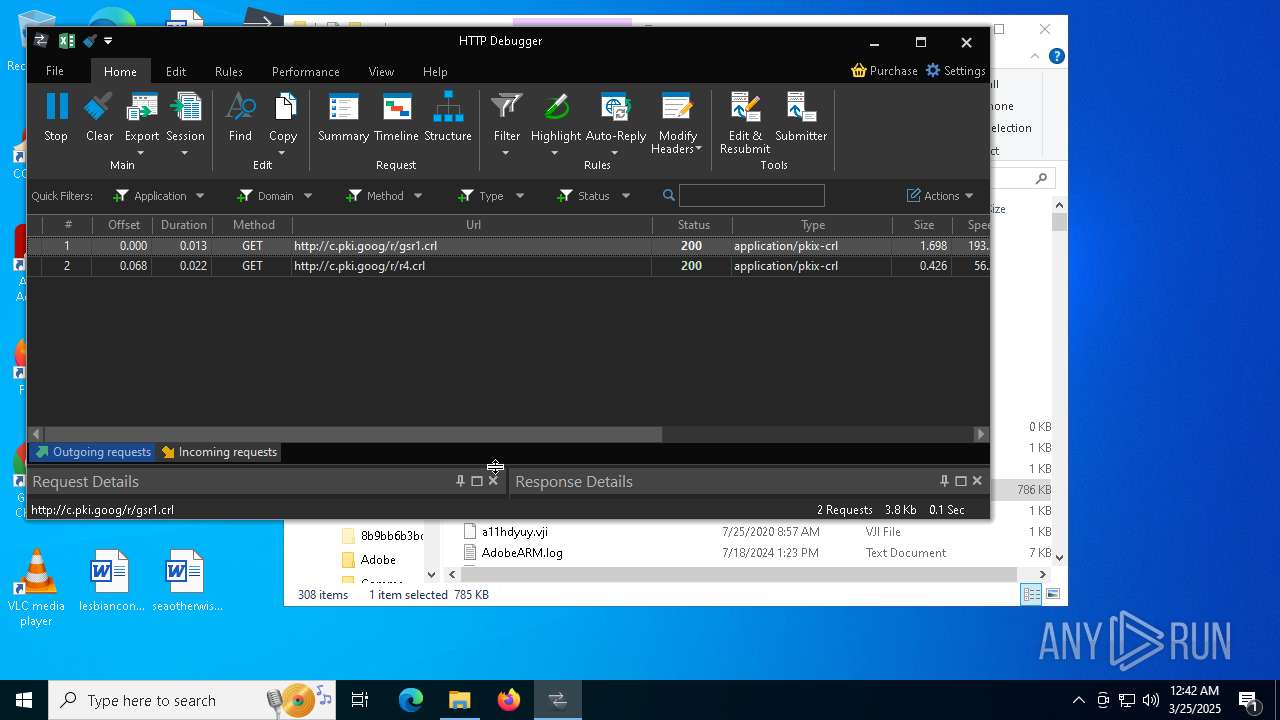
- HTTPDebuggerSvc.exe (PID: 1532)
- certutil.exe (PID: 5728)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
Steals credentials from Web Browsers
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
STORMKITTY has been detected (YARA)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
SUSPICIOUS
Executable content was dropped or overwritten
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- HTTPDebuggerSvc.exe (PID: 1532)
Reads security settings of Internet Explorer
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- ShellExperienceHost.exe (PID: 6192)
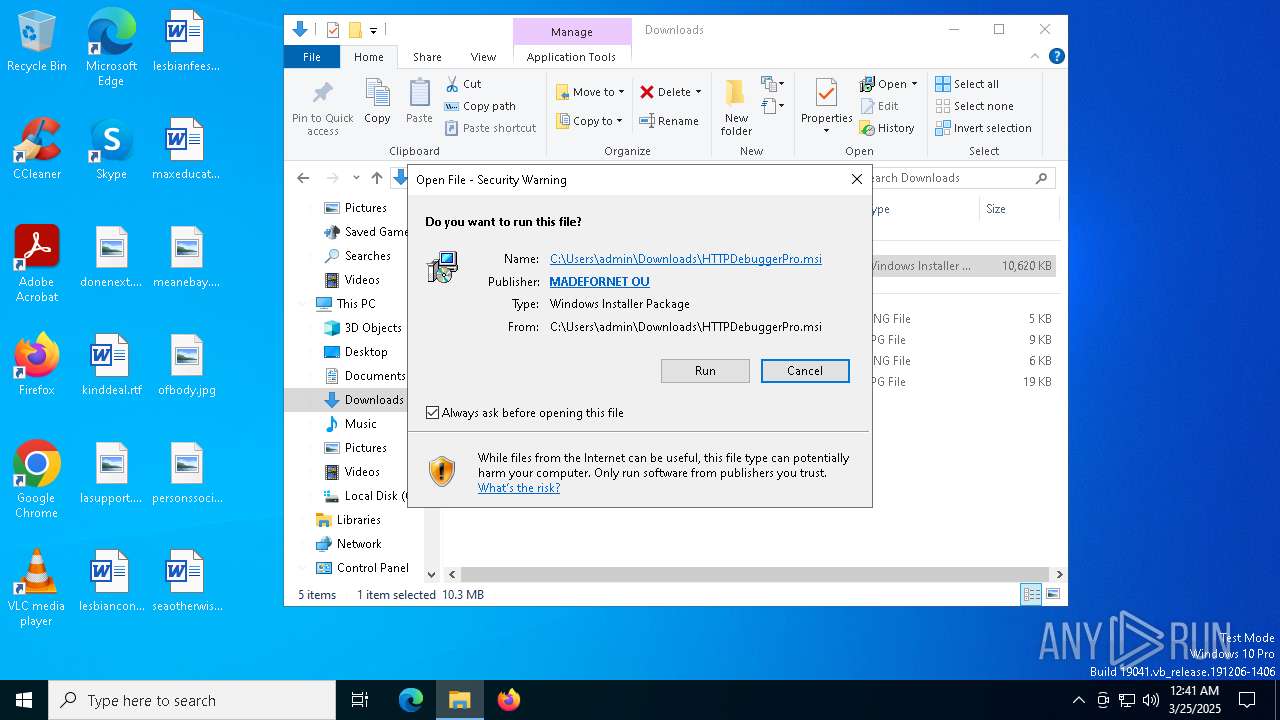
- msiexec.exe (PID: 8788)
- HTTPDebuggerUI.exe (PID: 7152)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
Application launched itself
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
Write to the desktop.ini file (may be used to cloak folders)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Starts application with an unusual extension
- cmd.exe (PID: 7680)
- cmd.exe (PID: 8220)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 7740)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 1052)
Starts CMD.EXE for commands execution
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Checks for external IP
- svchost.exe (PID: 2196)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
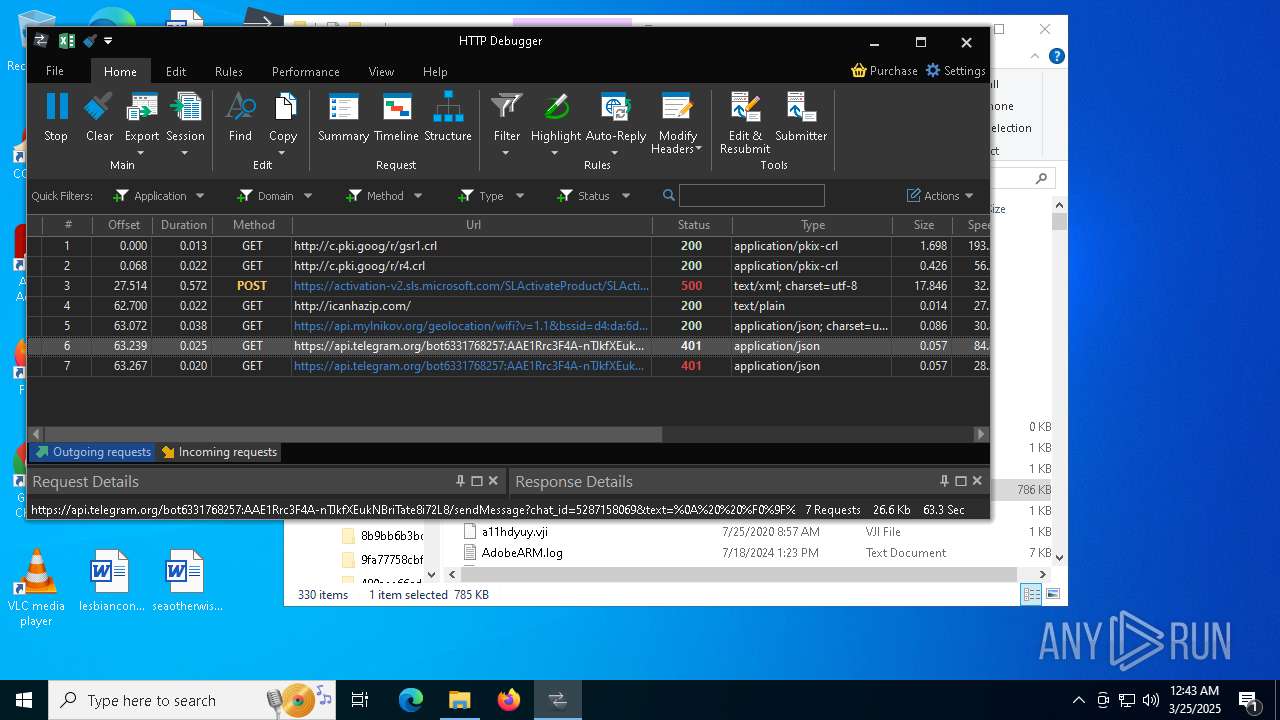
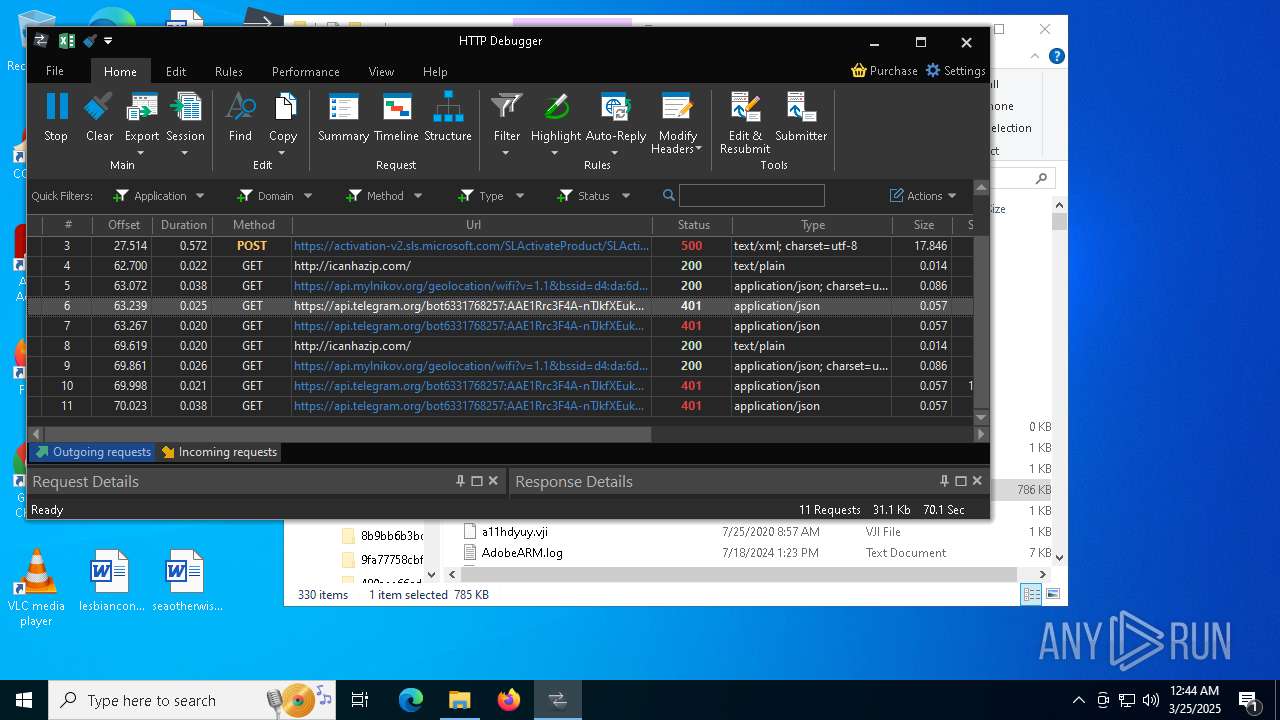
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 8220)
- cmd.exe (PID: 7680)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 7740)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 1052)
Potential Corporate Privacy Violation
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7680)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 7988)
Possible usage of Discord/Telegram API has been detected (YARA)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
Executes as Windows Service
- VSSVC.exe (PID: 8916)
- HTTPDebuggerSvc.exe (PID: 1532)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 8700)
- msiexec.exe (PID: 8748)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 8748)
- HTTPDebuggerSvc.exe (PID: 1532)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 4652)
The process creates files with name similar to system file names
- msiexec.exe (PID: 8748)
Creates files in the driver directory
- HTTPDebuggerSvc.exe (PID: 1532)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 8748)
Adds/modifies Windows certificates
- HTTPDebuggerSvc.exe (PID: 1532)
Reads Microsoft Outlook installation path
- HTTPDebuggerUI.exe (PID: 7152)
Reads Internet Explorer settings
- HTTPDebuggerUI.exe (PID: 7152)
INFO
Checks supported languages
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- chcp.com (PID: 2288)
- chcp.com (PID: 8268)
- msiexec.exe (PID: 8788)
- msiexec.exe (PID: 8748)
- ShellExperienceHost.exe (PID: 6192)
- HTTPDebuggerSvc.exe (PID: 1532)
- HTTPDebuggerSvc.exe (PID: 8348)
- msiexec.exe (PID: 1812)
- HTTPDebuggerUI.exe (PID: 7152)
- certutil.exe (PID: 5728)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
- chcp.com (PID: 5952)
- chcp.com (PID: 7852)
- chcp.com (PID: 8000)
- chcp.com (PID: 1180)
Reads the machine GUID from the registry
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- msiexec.exe (PID: 8748)
- HTTPDebuggerSvc.exe (PID: 1532)
- HTTPDebuggerSvc.exe (PID: 8348)
- HTTPDebuggerUI.exe (PID: 7152)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Reads the computer name
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- msiexec.exe (PID: 8748)
- msiexec.exe (PID: 8788)
- ShellExperienceHost.exe (PID: 6192)
- msiexec.exe (PID: 1812)
- HTTPDebuggerSvc.exe (PID: 1532)
- HTTPDebuggerUI.exe (PID: 7152)
- HTTPDebuggerSvc.exe (PID: 8348)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
- certutil.exe (PID: 5728)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- BackgroundTransferHost.exe (PID: 8060)
- BackgroundTransferHost.exe (PID: 5868)
- BackgroundTransferHost.exe (PID: 4652)
- BackgroundTransferHost.exe (PID: 1328)
- BackgroundTransferHost.exe (PID: 5260)
- msiexec.exe (PID: 8700)
Manual execution by a user
- firefox.exe (PID: 7768)
Application launched itself
- firefox.exe (PID: 7768)
- firefox.exe (PID: 7824)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 5868)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- explorer.exe (PID: 5492)
- HTTPDebuggerUI.exe (PID: 7152)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 5868)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- explorer.exe (PID: 5492)
- HTTPDebuggerUI.exe (PID: 7152)
- slui.exe (PID: 9092)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 5868)
- explorer.exe (PID: 5492)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- msiexec.exe (PID: 8700)
- slui.exe (PID: 7416)
- msiexec.exe (PID: 8748)
- slui.exe (PID: 9092)
- HTTPDebuggerUI.exe (PID: 7152)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
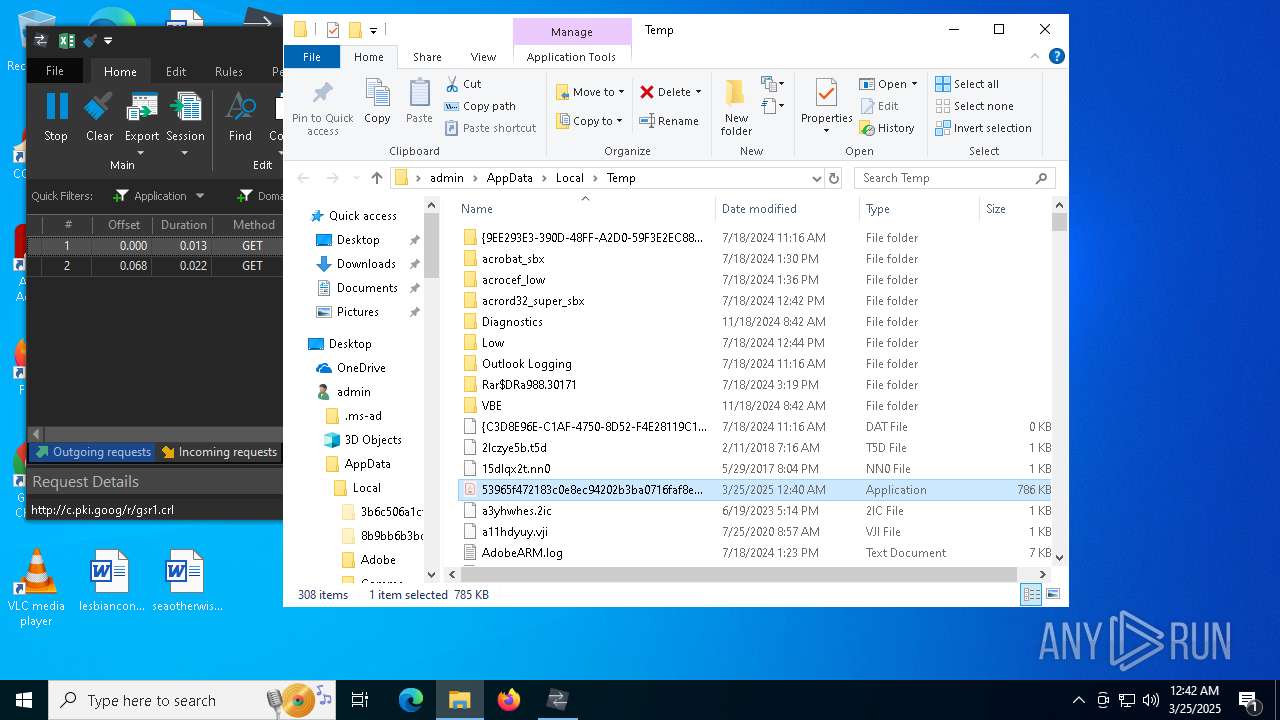
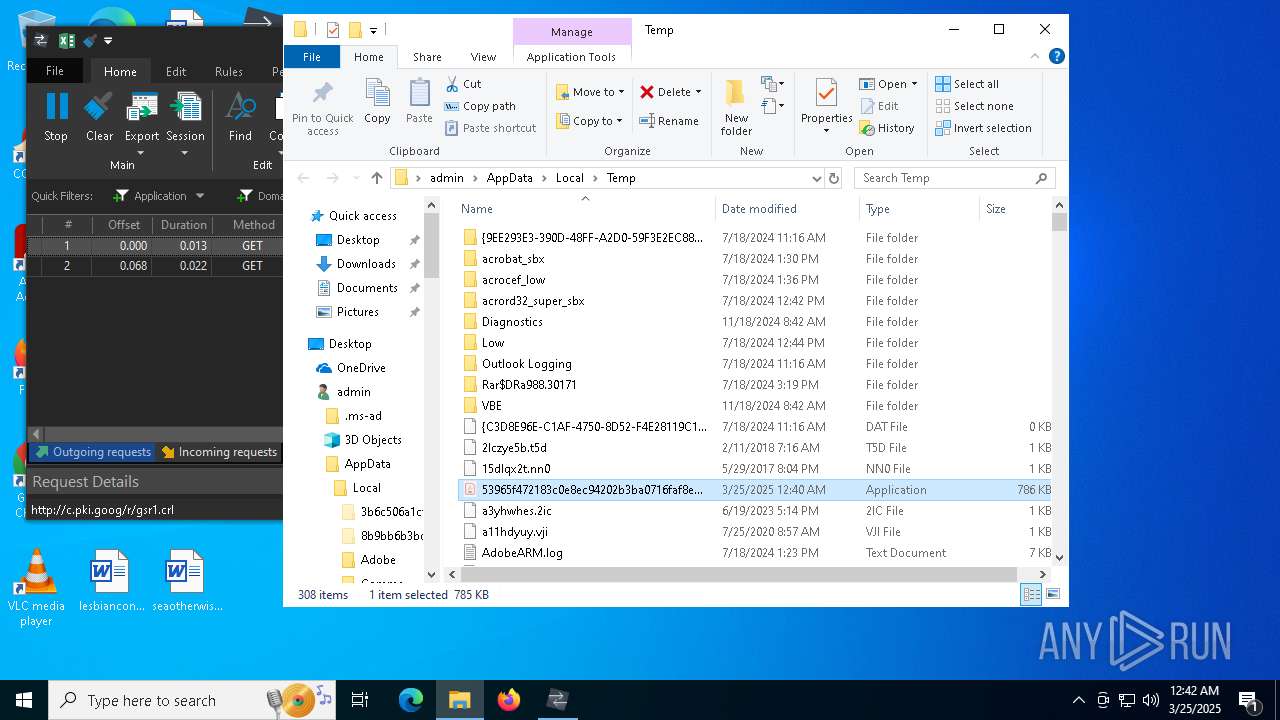
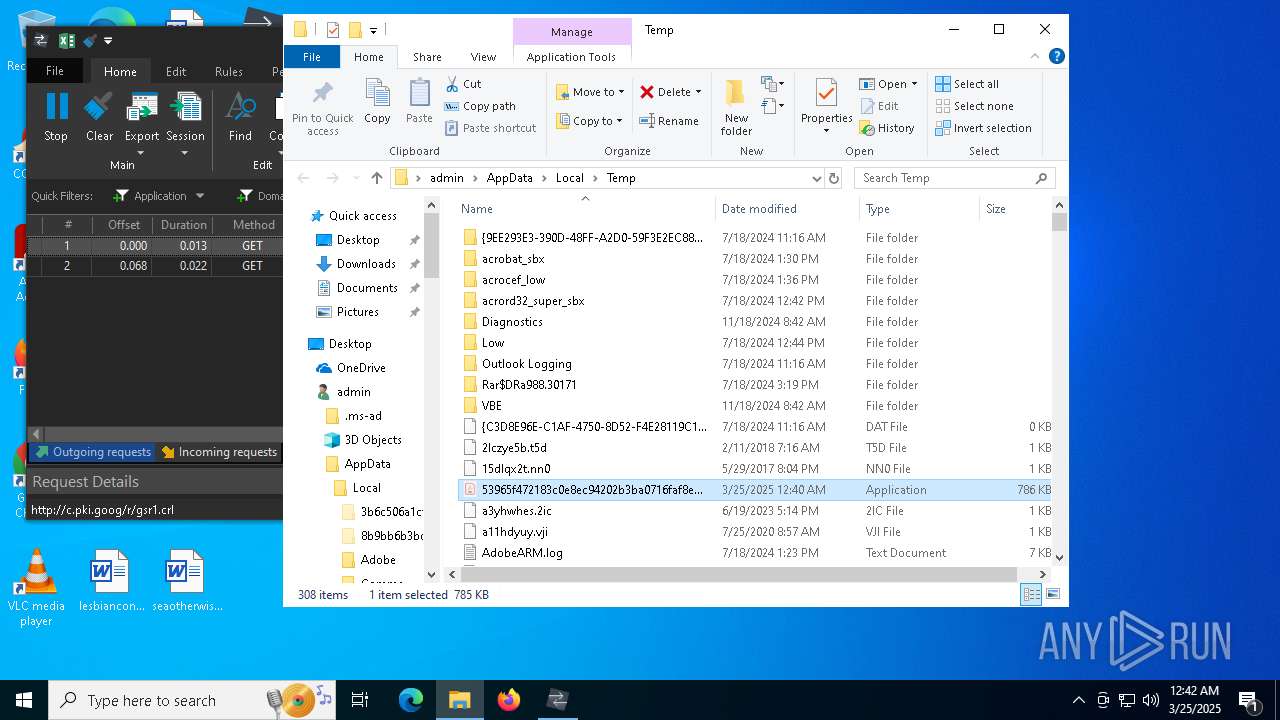
Create files in a temporary directory
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Process checks computer location settings
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 7324)
- msiexec.exe (PID: 8788)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 8600)
Changes the display of characters in the console
- cmd.exe (PID: 7680)
- cmd.exe (PID: 8220)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 7740)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 1052)
Reads CPU info
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Disables trace logs
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 2244)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 4068)
- 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe (PID: 9188)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Autorun file from Downloads
- firefox.exe (PID: 7824)
The sample compiled with english language support
- msiexec.exe (PID: 8700)
- msiexec.exe (PID: 8748)
- HTTPDebuggerSvc.exe (PID: 1532)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8700)
- msiexec.exe (PID: 8748)
Manages system restore points
- SrTasks.exe (PID: 1168)
Creates files in the program directory
- HTTPDebuggerSvc.exe (PID: 1532)
Creates a software uninstall entry
- msiexec.exe (PID: 8748)
Local mutex for internet shortcut management
- explorer.exe (PID: 5492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
StormKitty
(PID) Process(2244) 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
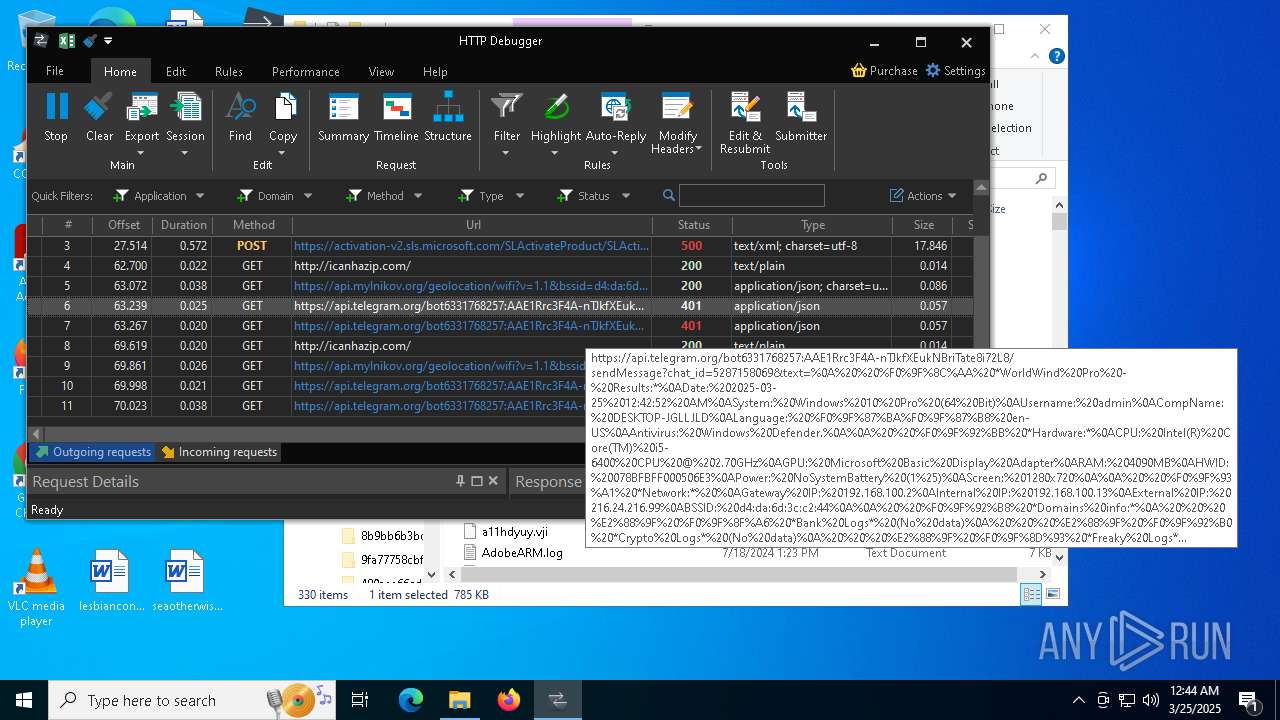
Protocoltelegram
URLnull
Token6331768257:AAE1Rrc3F4A-nTJkfXEukNBriTate8i72L8
ChatId5287158069
Version
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignatureJ7XpD4w+JaFzTixc0nCmiRA4ZP4bPCIpEYYGofNxvC1+0OsFQr56oTWwQMosnOTB64TZRGSdXVHKzjVchQf7X5Uwu/KQU61NPArjxWVScwKZXOGS4ZNzsWbrxgztkmlyRlQgvEq4rdFsqy1bfvHEoQ/s9aDXBNoLPPjJOexTRQSGuZYMpGSUD+ZUiVwPqqFWTb8KcjEMyABMeXGKfia2e9u8ePKpWv4HSiOfl6N47tTtIfN2FW/2mCX7BOnIZwCl3UxaQnITN812tHD1enX9TK86R91F02c0wabnf4oC07S3...
Keys
AESe5e3972eba013063607e705973dfdf80a8555bcfd8fe09651da2ab43b5773d9b
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (72.2) |
|---|---|---|
| .scr | | | Windows screen saver (12.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.4) |
| .exe | | | Win32 Executable (generic) (4.4) |
| .exe | | | Generic Win/DOS Executable (1.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:12:11 05:35:28+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 770048 |
| InitializedDataSize: | 33792 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbdf7e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft |
| FileDescription: | UdpSocket |
| FileVersion: | 3.0.0.0 |
| InternalName: | hQcr.exe |
| LegalCopyright: | |
| LegalTrademarks: | UdpSocket |
| OriginalFileName: | hQcr.exe |
| ProductVersion: | 3.0.0.0 |
| AssemblyVersion: | 19.2.0.0 |
Total processes
223
Monitored processes
79
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | findstr All | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | findstr All | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "cmd.exe" /C chcp 65001 && netsh wlan show networks mode=bssid | C:\Windows\SysWOW64\cmd.exe | — | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | chcp 65001 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\SFHAWxtoIpgL" /XML "C:\Users\admin\AppData\Local\Temp\tmp2E70.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | netsh wlan show networks mode=bssid | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
99 736
Read events
99 202
Write events
505
Delete events
29
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppLaunch |
| Operation: | write | Name: | 308046B0AF4A39CB |
Value: 15 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000402E6 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (7824) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | 308046B0AF4A39CB |
Value: 21 | |||
| (PID) Process: | (8060) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8060) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8060) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5868) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5868) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5868) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
29
Suspicious files
290
Text files
143
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7824 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:C216A4F2E4F533C14AC8C4A1B432705D | SHA256:AA07E227121171B851F7202696A0C00ACB3390A7B8FC222EC81D44FAAD5B9F2C | |||
| 7824 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
171
DNS requests
187
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7824 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7824 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7824 | firefox.exe | POST | — | 216.58.206.35:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
7824 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7824 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
7824 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7824 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7540 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7824 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7824 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
7824 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2244 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Potential Corporate Privacy Violation | ET INFO Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |
2244 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Attempted Information Leak | ET INFO IP Check Domain (icanhazip. com in HTTP Host) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
2244 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
2244 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
2244 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
4068 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Attempted Information Leak | ET INFO IP Check Domain (icanhazip. com in HTTP Host) |
4068 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
4068 | 53965f472183c0e8ec94202b3ba0716faf8e095e073a688f3396c4b8dcca6f30.exe | Potential Corporate Privacy Violation | ET INFO Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |