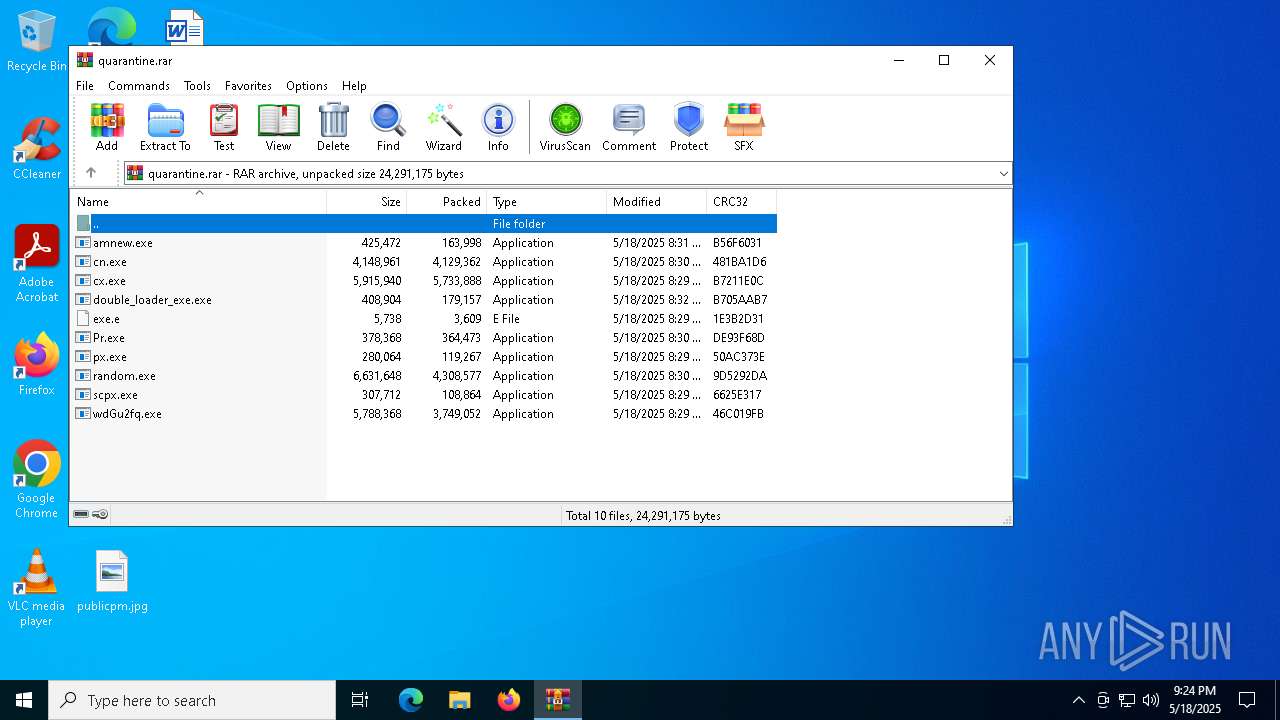
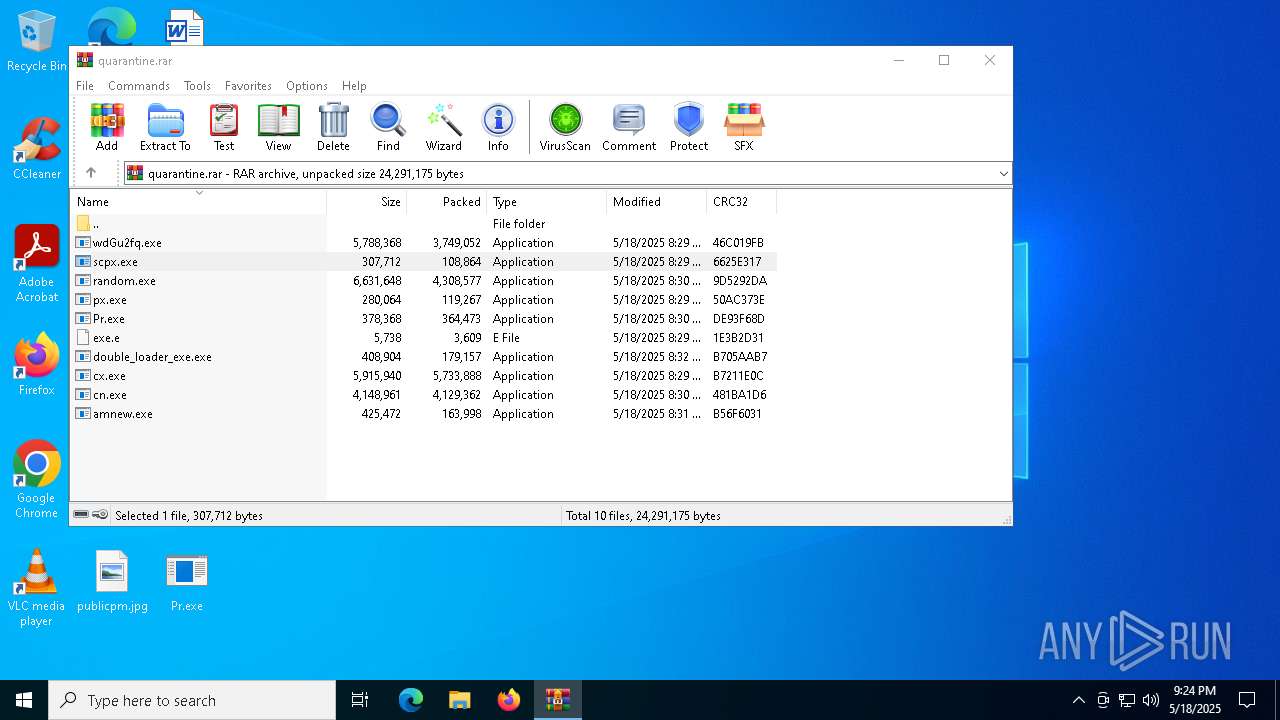
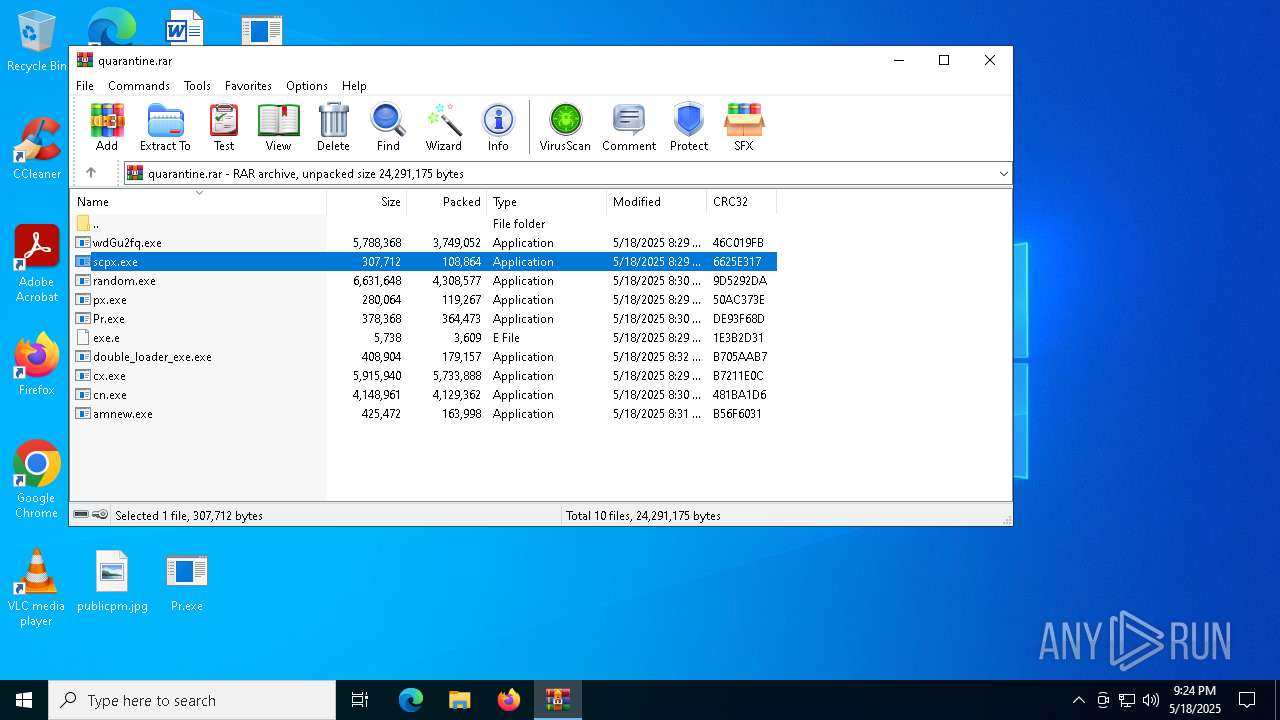
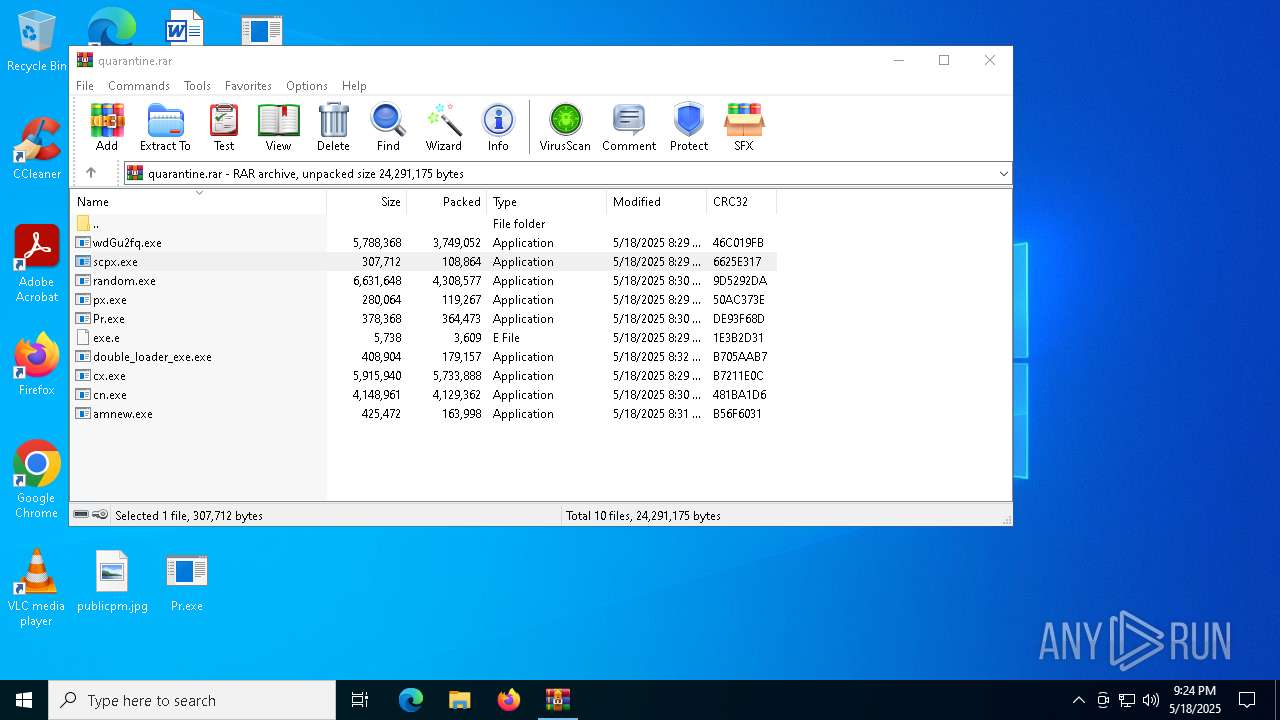
| File name: | quarantine.rar |
| Full analysis: | https://app.any.run/tasks/48371434-ec58-4abd-8f5b-2f079514fc42 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 18, 2025, 21:24:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C4D85821555DF62A9DDFBCCF35342DCF |
| SHA1: | 26EA9BE08575AB479E3EE0FDB7525B5FFAD6C218 |
| SHA256: | 536D9F49AA90C9E91F21E7928BF719774E3DC059C728699EDFF0C82C503F0CCC |
| SSDEEP: | 196608:wO0uu6bK44aeqhKaa+M3R/2UE5RH9D5+EQKvyvkQAY2ez:p0jQKqZKaaROUE559DoWvGkQTz |
MALICIOUS
Executing a file with an untrusted certificate
- double_loader_exe.exe (PID: 680)
- 3b8205767a.exe (PID: 2320)
Generic archive extractor
- WinRAR.exe (PID: 1228)
Changes the autorun value in the registry
- Pr.exe (PID: 5216)
- Pr.exe (PID: 3768)
AMADEY mutex has been found
- amnew.exe (PID: 2504)
- saren.exe (PID: 5024)
- saren.exe (PID: 2284)
- saren.exe (PID: 4560)
- saren.exe (PID: 3768)
AMADEY has been detected (SURICATA)
- saren.exe (PID: 5024)
Connects to the CnC server
- saren.exe (PID: 5024)
- svchost.exe (PID: 2196)
REDLINE has been detected (YARA)
- scpx.exe (PID: 6184)
AMADEY has been detected (YARA)
- saren.exe (PID: 5024)
GCLEANER has been detected (SURICATA)
- cvtres.exe (PID: 5936)
GENERIC has been found (auto)
- cvtres.exe (PID: 5936)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- RqwLx7ziok38X.exe (PID: 6560)
LUMMA mutex has been found
- RqwLx7ziok38X.exe (PID: 6560)
Steals credentials from Web Browsers
- RqwLx7ziok38X.exe (PID: 6560)
Actions looks like stealing of personal data
- RqwLx7ziok38X.exe (PID: 6560)
SUSPICIOUS
Connects to unusual port
- double_loader_exe.exe (PID: 680)
- scpx.exe (PID: 6184)
Executable content was dropped or overwritten
- amnew.exe (PID: 2504)
- cn.exe (PID: 6652)
- cn.tmp (PID: 4980)
- duplicatevideoremover.exe (PID: 6264)
- saren.exe (PID: 5024)
- cvtres.exe (PID: 5936)
- qKPCkRKg0.exe (PID: 2420)
- qKPCkRKg0.tmp (PID: 2192)
Starts itself from another location
- amnew.exe (PID: 2504)
Reads security settings of Internet Explorer
- amnew.exe (PID: 2504)
- duplicatevideoremover.exe (PID: 6264)
- saren.exe (PID: 5024)
- cvtres.exe (PID: 5936)
- duplicatevideoremover15.exe (PID: 2600)
- DuplicateVideoRemover.exe (PID: 6700)
The process drops C-runtime libraries
- cn.tmp (PID: 4980)
Reads the Windows owner or organization settings
- cn.tmp (PID: 4980)
- qKPCkRKg0.tmp (PID: 2192)
Process drops legitimate windows executable
- cn.tmp (PID: 4980)
- qKPCkRKg0.tmp (PID: 2192)
Contacting a server suspected of hosting an CnC
- saren.exe (PID: 5024)
- svchost.exe (PID: 2196)
- RqwLx7ziok38X.exe (PID: 6560)
Potential Corporate Privacy Violation
- saren.exe (PID: 5024)
- cvtres.exe (PID: 5936)
The process executes via Task Scheduler
- saren.exe (PID: 2284)
- saren.exe (PID: 4560)
- saren.exe (PID: 3768)
There is functionality for taking screenshot (YARA)
- scpx.exe (PID: 6184)
- saren.exe (PID: 5024)
Process requests binary or script from the Internet
- saren.exe (PID: 5024)
Starts POWERSHELL.EXE for commands execution
- duplicatevideoremover.exe (PID: 6264)
- duplicatevideoremover15.exe (PID: 2600)
Connects to the server without a host name
- saren.exe (PID: 5024)
- cvtres.exe (PID: 5936)
There is functionality for enable RDP (YARA)
- saren.exe (PID: 5024)
Searches for installed software
- qKPCkRKg0.tmp (PID: 2192)
- RqwLx7ziok38X.exe (PID: 6560)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RqwLx7ziok38X.exe (PID: 6560)
INFO
Checks supported languages
- double_loader_exe.exe (PID: 680)
- Pr.exe (PID: 5216)
- scpx.exe (PID: 6184)
- Pr.exe (PID: 3768)
- amnew.exe (PID: 2504)
- cn.exe (PID: 6652)
- cn.tmp (PID: 4980)
- saren.exe (PID: 5024)
- duplicatevideoremover.exe (PID: 6264)
- saren.exe (PID: 2284)
- 3b8205767a.exe (PID: 2320)
- cvtres.exe (PID: 5936)
- DuplicateVideoRemover.exe (PID: 6700)
- saren.exe (PID: 4560)
- qKPCkRKg0.exe (PID: 2420)
- qKPCkRKg0.tmp (PID: 2192)
- duplicatevideoremover15.exe (PID: 2600)
- RqwLx7ziok38X.exe (PID: 6560)
- SX9eZRUCpN.exe (PID: 736)
- saren.exe (PID: 3768)
Reads the computer name
- scpx.exe (PID: 6184)
- amnew.exe (PID: 2504)
- saren.exe (PID: 5024)
- cn.tmp (PID: 4980)
- duplicatevideoremover.exe (PID: 6264)
- 3b8205767a.exe (PID: 2320)
- DuplicateVideoRemover.exe (PID: 6700)
- cvtres.exe (PID: 5936)
- qKPCkRKg0.tmp (PID: 2192)
- duplicatevideoremover15.exe (PID: 2600)
- SX9eZRUCpN.exe (PID: 736)
- RqwLx7ziok38X.exe (PID: 6560)
Manual execution by a user
- scpx.exe (PID: 6184)
- double_loader_exe.exe (PID: 680)
- Pr.exe (PID: 5216)
- Pr.exe (PID: 3768)
- amnew.exe (PID: 2504)
- cn.exe (PID: 6652)
- OpenWith.exe (PID: 5596)
- cvtres.exe (PID: 5936)
- DuplicateVideoRemover.exe (PID: 6700)
Reads the machine GUID from the registry
- scpx.exe (PID: 6184)
- 3b8205767a.exe (PID: 2320)
- cvtres.exe (PID: 5936)
- duplicatevideoremover.exe (PID: 6264)
- DuplicateVideoRemover.exe (PID: 6700)
- RqwLx7ziok38X.exe (PID: 6560)
Auto-launch of the file from Registry key
- Pr.exe (PID: 5216)
- Pr.exe (PID: 3768)
Create files in a temporary directory
- amnew.exe (PID: 2504)
- cn.exe (PID: 6652)
- cn.tmp (PID: 4980)
- saren.exe (PID: 5024)
- qKPCkRKg0.exe (PID: 2420)
- qKPCkRKg0.tmp (PID: 2192)
- cvtres.exe (PID: 5936)
Process checks computer location settings
- amnew.exe (PID: 2504)
- duplicatevideoremover.exe (PID: 6264)
- saren.exe (PID: 5024)
- duplicatevideoremover15.exe (PID: 2600)
Creates files in the program directory
- duplicatevideoremover.exe (PID: 6264)
- duplicatevideoremover15.exe (PID: 2600)
Creates a software uninstall entry
- cn.tmp (PID: 4980)
- qKPCkRKg0.tmp (PID: 2192)
Checks proxy server information
- saren.exe (PID: 5024)
- cvtres.exe (PID: 5936)
- duplicatevideoremover.exe (PID: 6264)
- DuplicateVideoRemover.exe (PID: 6700)
- slui.exe (PID: 2344)
Creates files or folders in the user directory
- cn.tmp (PID: 4980)
- saren.exe (PID: 5024)
- cvtres.exe (PID: 5936)
- qKPCkRKg0.tmp (PID: 2192)
The sample compiled with english language support
- cn.tmp (PID: 4980)
- saren.exe (PID: 5024)
- qKPCkRKg0.tmp (PID: 2192)
- cvtres.exe (PID: 5936)
Changes the registry key values via Powershell
- duplicatevideoremover.exe (PID: 6264)
- duplicatevideoremover15.exe (PID: 2600)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5596)
Detects InnoSetup installer (YARA)
- cn.exe (PID: 6652)
- cn.tmp (PID: 4980)
Compiled with Borland Delphi (YARA)
- cn.tmp (PID: 4980)
Reads the software policy settings
- cvtres.exe (PID: 5936)
- slui.exe (PID: 2344)
- duplicatevideoremover.exe (PID: 6264)
- DuplicateVideoRemover.exe (PID: 6700)
- RqwLx7ziok38X.exe (PID: 6560)
Attempting to use instant messaging service
- RqwLx7ziok38X.exe (PID: 6560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(6184) scpx.exe
C2 (1)62.60.226.191:1912
Botnetppvv
Options
ErrorMessage
Keys
Xorsfsdolpmjfpsdoljflsdkpfjpsoldmf
Amadey
(PID) Process(5024) saren.exe
C277.83.207.69
URLhttp://77.83.207.69/rob75u9v/index.php
Version5.34
Options
Drop directory02106dbc20
Drop namesaren.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
02106dbc20
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
saren.exe
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
/rob75u9v/index.php
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
77.83.207.69
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 5733888 |
| UncompressedSize: | 5915940 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | cx.exe |
Total processes
152
Monitored processes
28
Malicious processes
12
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -c Set-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Run" -Name "dvRemover" -Value "C:\ProgramData\DuplicateVideoRemover\DuplicateVideoRemover.exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | duplicatevideoremover15.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\double_loader_exe.exe" | C:\Users\admin\Desktop\double_loader_exe.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 736 | "C:\Users\admin\AppData\Roaming\8pT1EfKZnv\SX9eZRUCpN.exe" | C:\Users\admin\AppData\Roaming\8pT1EfKZnv\SX9eZRUCpN.exe | — | cvtres.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Gcleanerapp Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\quarantine.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\AppData\Local\Temp\is-PR85R.tmp\qKPCkRKg0.tmp" /SL5="$A0162,3936557,54272,C:\Users\admin\AppData\Roaming\n6rpoQS9\qKPCkRKg0.exe" | C:\Users\admin\AppData\Local\Temp\is-PR85R.tmp\qKPCkRKg0.tmp | qKPCkRKg0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.52.0.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\AppData\Local\Temp\02106dbc20\saren.exe" | C:\Users\admin\AppData\Local\Temp\02106dbc20\saren.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\AppData\Local\Temp\10000360101\3b8205767a.exe" | C:\Users\admin\AppData\Local\Temp\10000360101\3b8205767a.exe | — | saren.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: WiFi Password Key Generator Software Exit code: 4294967295 Version: 10.0.0.0 Modules
| |||||||||||||||
| 2344 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Roaming\n6rpoQS9\qKPCkRKg0.exe" | C:\Users\admin\AppData\Roaming\n6rpoQS9\qKPCkRKg0.exe | cvtres.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Duplicate Video Remover Setup Version: Modules
| |||||||||||||||
Total events
30 669
Read events
30 611
Write events
57
Delete events
1
Modification events
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\quarantine.rar | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (5216) Pr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | pxUQdBQedu |
Value: C:\Users\admin\Desktop\Pr.exe | |||
Executable files
45
Suspicious files
11
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6652 | cn.exe | C:\Users\admin\AppData\Local\Temp\is-ORR70.tmp\cn.tmp | executable | |
MD5:3C832EC322A42E260A9CB745BF729890 | SHA256:6C1129D06B90FE73F0197B8E68D6F46A15C74D85CA1C23DBBB19D2B1F3472635 | |||
| 2504 | amnew.exe | C:\Users\admin\AppData\Local\Temp\02106dbc20\saren.exe | executable | |
MD5:14BCF4728388BDCD9C6AFDE0C9792B85 | SHA256:07CF56CD893705BC40A0F27C7575E4E78798098A681A1C88A7F67576101A6821 | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Duplicate Video Remover 2.4.1.168\uninstall\unins000.exe | executable | |
MD5:3EF08A4D4A7EEAC9CA719A0F782085EB | SHA256:0955953CFCB38E1810DA1E823B377E98A4FFA773B121B69C7E05D7A641C49E63 | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Duplicate Video Remover 2.4.1.168\is-0MM2H.tmp | executable | |
MD5:A7F201C0B9AC05E950ECC55D4403EC16 | SHA256:173092C4E256958B100683A6AB2CE0D1C9895EC63F222198F9DE485E61C728CA | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Duplicate Video Remover 2.4.1.168\is-2MH4R.tmp | executable | |
MD5:EAE56B896A718C3BC87A4253832A5650 | SHA256:EE1D7D8F396D627FEE7DCF2655FB5ACFE5A1EE2A5DEEDA764EF311E75B94CEA1 | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Duplicate Video Remover 2.4.1.168\is-3GISC.tmp | executable | |
MD5:DAE4100039A943128C34BA3E05F6CD02 | SHA256:2357806CA24C9D3152D54D34270810DA9D9CA943462EBF7291AE06A10E5CB8BA | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Temp\is-MCFED.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Duplicate Video Remover 2.4.1.168\icuuc51.dll | executable | |
MD5:DAE4100039A943128C34BA3E05F6CD02 | SHA256:2357806CA24C9D3152D54D34270810DA9D9CA943462EBF7291AE06A10E5CB8BA | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Duplicate Video Remover 2.4.1.168\libEGL.dll | executable | |
MD5:EAE56B896A718C3BC87A4253832A5650 | SHA256:EE1D7D8F396D627FEE7DCF2655FB5ACFE5A1EE2A5DEEDA764EF311E75B94CEA1 | |||
| 4980 | cn.tmp | C:\Users\admin\AppData\Local\Temp\is-MCFED.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
65
DNS requests
20
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5024 | saren.exe | POST | 200 | 77.83.207.69:80 | http://77.83.207.69/rob75u9v/index.php | unknown | — | — | malicious |
5024 | saren.exe | POST | 200 | 77.83.207.69:80 | http://77.83.207.69/rob75u9v/index.php | unknown | — | — | malicious |
5024 | saren.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/unique2/random.exe | unknown | — | — | unknown |
5740 | SIHClient.exe | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
5740 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
680 | double_loader_exe.exe | 5.252.153.15:7002 | — | — | PA | malicious |
6184 | scpx.exe | 62.60.226.191:1912 | — | Iranian Research Organization for Science & Technology | HK | unknown |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5024 | saren.exe | 77.83.207.69:80 | — | Internet Technologies LLC | UA | malicious |
5024 | saren.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | unknown |
5740 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5024 | saren.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
5024 | saren.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
5024 | saren.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5024 | saren.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
5024 | saren.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
5024 | saren.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5936 | cvtres.exe | A Network Trojan was detected | LOADER [ANY.RUN] GCleaner HTTP Header |
5936 | cvtres.exe | A Network Trojan was detected | LOADER [ANY.RUN] GCleaner HTTP Header |
5936 | cvtres.exe | A Network Trojan was detected | LOADER [ANY.RUN] GCleaner HTTP Header |
5936 | cvtres.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |