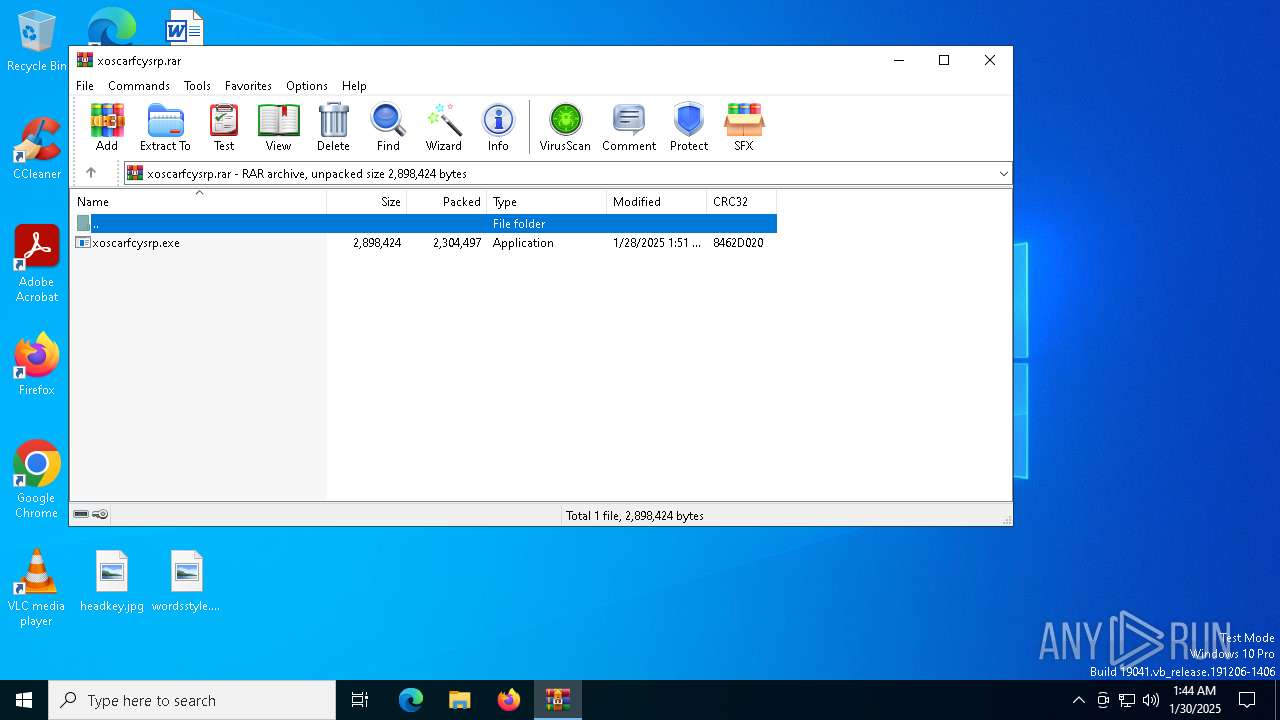
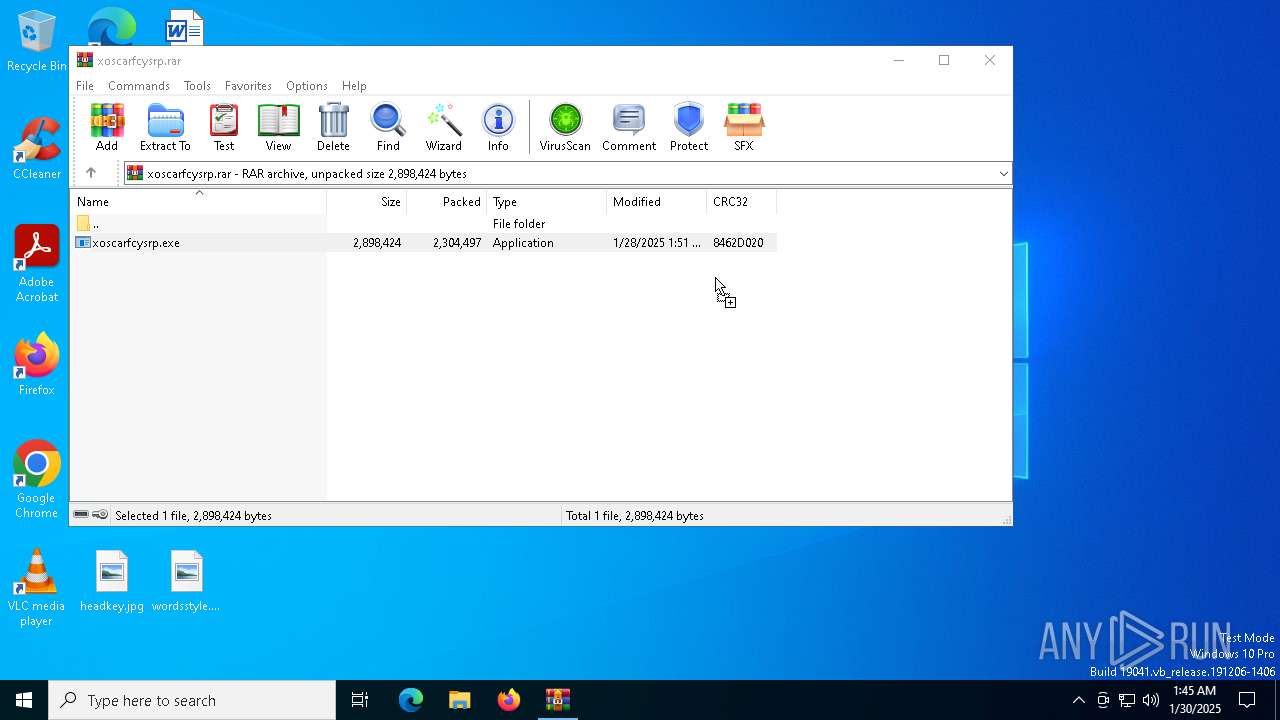
| File name: | xoscarfcysrp.rar |
| Full analysis: | https://app.any.run/tasks/4c9cf2fa-3ce5-4020-b3da-8f95c8eada3c |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | January 30, 2025, 01:44:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 9000D976BA8DDB57C7E754BBA2AB2759 |
| SHA1: | 85E5C6EBF65EC98C91F44AEB0DC5AC925CF63A06 |
| SHA256: | 5355C3F40686E48175807DA697CF6587ED3CED3257452DC46691A4E5C9C8E630 |
| SSDEEP: | 98304:C94wAzOQkop0S0PpC8ZP+IElVBjXtg8kylSNaM9hOdYB2FQomRMIPhuC21Q3FePV:I857 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6472)
Executing a file with an untrusted certificate
- xoscarfcysrp.exe (PID: 6268)
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Adds extension to the Windows Defender exclusion list
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 4164)
- cmd.exe (PID: 2440)
Application was injected by another process
- dwm.exe (PID: 912)
- svchost.exe (PID: 320)
- svchost.exe (PID: 1268)
- svchost.exe (PID: 1880)
- svchost.exe (PID: 1424)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 1452)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 1276)
- svchost.exe (PID: 1768)
- svchost.exe (PID: 1776)
- svchost.exe (PID: 1500)
- svchost.exe (PID: 1660)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 1068)
- svchost.exe (PID: 1076)
- lsass.exe (PID: 760)
- winlogon.exe (PID: 684)
- svchost.exe (PID: 2272)
- svchost.exe (PID: 2192)
- svchost.exe (PID: 1908)
- svchost.exe (PID: 2372)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 2064)
- svchost.exe (PID: 1972)
- svchost.exe (PID: 2340)
- svchost.exe (PID: 2500)
- svchost.exe (PID: 2748)
- svchost.exe (PID: 2364)
- spoolsv.exe (PID: 2652)
- svchost.exe (PID: 2816)
- svchost.exe (PID: 2892)
- svchost.exe (PID: 3016)
- svchost.exe (PID: 1564)
- svchost.exe (PID: 3592)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 3164)
- svchost.exe (PID: 3600)
- svchost.exe (PID: 2660)
- svchost.exe (PID: 3824)
- svchost.exe (PID: 2288)
- svchost.exe (PID: 3160)
- svchost.exe (PID: 4000)
- sihost.exe (PID: 1712)
- dasHost.exe (PID: 3896)
- svchost.exe (PID: 3704)
- svchost.exe (PID: 3668)
- svchost.exe (PID: 2952)
- svchost.exe (PID: 2852)
- svchost.exe (PID: 2944)
- svchost.exe (PID: 2920)
- OfficeClickToRun.exe (PID: 2884)
- svchost.exe (PID: 2360)
- svchost.exe (PID: 4696)
- explorer.exe (PID: 4488)
- svchost.exe (PID: 4436)
- svchost.exe (PID: 4168)
- RuntimeBroker.exe (PID: 4960)
- svchost.exe (PID: 4176)
- RuntimeBroker.exe (PID: 4676)
- RuntimeBroker.exe (PID: 5820)
- dllhost.exe (PID: 5164)
- ctfmon.exe (PID: 4268)
- svchost.exe (PID: 1176)
- svchost.exe (PID: 4200)
- dllhost.exe (PID: 1816)
- svchost.exe (PID: 1340)
- svchost.exe (PID: 4456)
- MoUsoCoreWorker.exe (PID: 4712)
- UserOOBEBroker.exe (PID: 3004)
- svchost.exe (PID: 3976)
- ApplicationFrameHost.exe (PID: 6108)
- svchost.exe (PID: 812)
- dllhost.exe (PID: 5904)
- svchost.exe (PID: 1888)
- uhssvc.exe (PID: 2908)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 376)
- svchost.exe (PID: 1764)
- svchost.exe (PID: 4980)
- svchost.exe (PID: 3032)
- svchost.exe (PID: 2224)
- taskhostw.exe (PID: 3992)
- WmiPrvSE.exe (PID: 5916)
- RuntimeBroker.exe (PID: 6892)
- WmiPrvSE.exe (PID: 5040)
Runs injected code in another process
- dialer.exe (PID: 6232)
- dialer.exe (PID: 2072)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2192)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- xoscarfcysrp.exe (PID: 6268)
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Starts process via Powershell
- powershell.exe (PID: 6292)
Script adds exclusion extension to Windows Defender
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Script adds exclusion path to Windows Defender
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Manipulates environment variables
- powershell.exe (PID: 3224)
- powershell.exe (PID: 6308)
Stops a currently running service
- sc.exe (PID: 7072)
- sc.exe (PID: 2160)
- sc.exe (PID: 7108)
- sc.exe (PID: 5316)
- sc.exe (PID: 6288)
- sc.exe (PID: 1476)
- sc.exe (PID: 3540)
- sc.exe (PID: 3680)
- sc.exe (PID: 2792)
- sc.exe (PID: 6348)
- sc.exe (PID: 2600)
Process uninstalls Windows update
- wusa.exe (PID: 6960)
- wusa.exe (PID: 4628)
Starts CMD.EXE for commands execution
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Creates a new Windows service
- sc.exe (PID: 3952)
Starts SC.EXE for service management
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Uses powercfg.exe to modify the power settings
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Windows service management via SC.EXE
- sc.exe (PID: 2972)
- sc.exe (PID: 5112)
Executable content was dropped or overwritten
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Executes as Windows Service
- xoscarfcysrp.exe (PID: 644)
Drops a system driver (possible attempt to evade defenses)
- xoscarfcysrp.exe (PID: 644)
Connects to unusual port
- dialer.exe (PID: 6392)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2192)
INFO
Reads the software policy settings
- lsass.exe (PID: 760)
Reads security settings of Internet Explorer
- RuntimeBroker.exe (PID: 6892)
- explorer.exe (PID: 4488)
The sample compiled with english language support
- explorer.exe (PID: 4488)
- WinRAR.exe (PID: 6472)
- xoscarfcysrp.exe (PID: 2084)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6472)
Manual execution by a user
- xoscarfcysrp.exe (PID: 6268)
Checks supported languages
- xoscarfcysrp.exe (PID: 6268)
- xoscarfcysrp.exe (PID: 2084)
- xoscarfcysrp.exe (PID: 644)
Reads the time zone
- WmiPrvSE.exe (PID: 5040)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3224)
- powershell.exe (PID: 6308)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3224)
- powershell.exe (PID: 6308)
Creates files in the program directory
- xoscarfcysrp.exe (PID: 2084)
- MoUsoCoreWorker.exe (PID: 4712)
- svchost.exe (PID: 1076)
The sample compiled with japanese language support
- xoscarfcysrp.exe (PID: 644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 2304497 |
| UncompressedSize: | 2898424 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | xoscarfcysrp.exe |
Total processes
192
Monitored processes
151
Malicious processes
93
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | C:\WINDOWS\system32\powercfg.exe /x -standby-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | xoscarfcysrp.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | C:\ProgramData\vgodrqhybann\xoscarfcysrp.exe | C:\ProgramData\vgodrqhybann\xoscarfcysrp.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft® Windows® Integrity Level: SYSTEM Description: Windows Media (Microsoft) Exit code: 0 Version: 12,0,22621,2506 Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 912 | "dwm.exe" | C:\Windows\System32\dwm.exe | winlogon.exe | ||||||||||||
User: DWM-1 Company: Microsoft Corporation Integrity Level: SYSTEM Description: Desktop Window Manager Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s gpsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
78 651
Read events
77 978
Write events
421
Delete events
252
Modification events
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000005035C |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (4268) ctfmon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Input\TypingInsights |
| Operation: | write | Name: | Insights |
Value: 02000000071DE8C131CC8360A3D6D9C1330A686B165ABA2E235F5A5C | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\xoscarfcysrp.rar | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
60
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1768 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-2E4E3AC7.pf | binary | |
MD5:7E3B036B14FFF6986A7AA74E56523E0E | SHA256:4BDBDD011BB124E017FC035535D00592886C5832F6E59ECA3F6ACB8EFDF54BE6 | |||
| 4488 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 5164 | dllhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\V01.chk | binary | |
MD5:9628937F1D0F7449C2BB18557D32ABBC | SHA256:B4F5910E457A3718E24C74BC67529F799CE881225673F938E9462A76F90C40C3 | |||
| 1176 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:D122E5212A2CDA5AEC566CC962F859B5 | SHA256:E3745DCDC4608147EEF31AEC87F02861C74D9EC02E3FA1FFE42E2F2A45F8E0FF | |||
| 1176 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:735889089A4E16BA45C92C32A4C246C1 | SHA256:C27873858E2F658F18D9800271C89047A70518D52FBFDEB8E7CDD7542CDD6BFD | |||
| 6472 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6472.31551\xoscarfcysrp.exe | executable | |
MD5:DF72985DC6FD669267F426F599423DF2 | SHA256:BD76C7AFD03D268F0E78A51EB0366CB2FD77BCC2067D74132BDAAE213557A8BF | |||
| 1340 | svchost.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:631AF249C762727E3F4A9EC164D7BA5D | SHA256:88AAD2297F6BB60C9408C2A3B77EF8D556E998E38EC143936CA1348613108E39 | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\RUNTIMEBROKER.EXE-660365C8.pf | binary | |
MD5:BBD9B32BBDDA07671B228228230C617A | SHA256:079ADC23A75EF9D8F06A7DF2EE28C51DAC84CBFA7DEB9DD698A3E39CFB5C0D04 | |||
| 4488 | explorer.exe | C:\Users\admin\Desktop\xoscarfcysrp.exe | executable | |
MD5:DF72985DC6FD669267F426F599423DF2 | SHA256:BD76C7AFD03D268F0E78A51EB0366CB2FD77BCC2067D74132BDAAE213557A8BF | |||
| 1768 | svchost.exe | C:\Windows\Prefetch\XOSCARFCYSRP.EXE-F4D5E537.pf | binary | |
MD5:4941EDB5A9664E559F0BD3B8356AD09C | SHA256:04598B355BBDAB1360BFE976833DC67B533823E73FBDEB63886D9B32899001AF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.78.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2600 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2600 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6644 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.78.32:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4536 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query to Coin Mining Domain (nanopool .org) |
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |