| File name: | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4 |
| Full analysis: | https://app.any.run/tasks/7019fdc5-c467-410e-afb2-2da15117eac1 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 15, 2025, 12:56:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | C4728320593F676C0CA9FF636FEE0E5B |
| SHA1: | C9712FC22F7292A279AE8580CCA573C6525AE98C |
| SHA256: | 527214F65D4C7AAAA21DB80291A9D37B9625583F5BA60B3DE2226C03713660B4 |
| SSDEEP: | 98304:lf/OQ8Ojcu3LklaM94p7quLI8QToLAGHiO3jTa+go1LUTQpgpsHL9YwE+I0pPcS2:5z |
MALICIOUS
Steals credentials from Web Browsers
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- MSBuild.exe (PID: 7640)
- MSBuild.exe (PID: 6228)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- MSBuild.exe (PID: 6228)
- svchost.exe (PID: 2140)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6504)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6956)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 2028)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6676)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 4044)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 7104)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 480)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6728)
LUMMA mutex has been found
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- MSBuild.exe (PID: 7640)
- MSBuild.exe (PID: 6228)
Connects to the CnC server
- svchost.exe (PID: 2196)
- ramez.exe (PID: 7920)
- svchost.exe (PID: 2140)
- ramez.exe (PID: 6332)
Actions looks like stealing of personal data
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- MSBuild.exe (PID: 7640)
- MSBuild.exe (PID: 6228)
LUMMA has been detected (YARA)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
AMADEY mutex has been found
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 7920)
- ramez.exe (PID: 4428)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 7920)
- ramez.exe (PID: 6332)
Runs injected code in another process
- e5jg7MM.exe (PID: 2236)
Application was injected by another process
- svchost.exe (PID: 4120)
- svchost.exe (PID: 4336)
AMADEY has been detected (YARA)
- ramez.exe (PID: 7920)
Executing a file with an untrusted certificate
- HGVm49v.exe (PID: 5868)
- ra02W4S.exe (PID: 7760)
SUSPICIOUS
Reads the BIOS version
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- ramez.exe (PID: 7920)
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 4428)
- e5jg7MM.exe (PID: 2236)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- ramez.exe (PID: 7920)
- MSBuild.exe (PID: 6228)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6504)
- svchost.exe (PID: 2140)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6956)
- ramez.exe (PID: 6332)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 2028)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 4044)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6676)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 7104)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 480)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6728)
Process requests binary or script from the Internet
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- ramez.exe (PID: 7920)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6504)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6956)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 2028)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 4044)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6676)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 480)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6728)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 7104)
Connects to the server without a host name
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- ramez.exe (PID: 7920)
- svchost.exe (PID: 4336)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6504)
- ramez.exe (PID: 6332)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6956)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 2028)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 4044)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6676)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 7104)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 480)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6728)
Potential Corporate Privacy Violation
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- ramez.exe (PID: 7920)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6504)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6956)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 2028)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 4044)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6676)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 7104)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 480)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6728)
Searches for installed software
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- MSBuild.exe (PID: 7640)
- MSBuild.exe (PID: 6228)
Executable content was dropped or overwritten
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 7920)
- 3d1e813836.exe (PID: 7860)
- 3d1e813836.tmp (PID: 7748)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6504)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6956)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 2028)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 4044)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6676)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 7104)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 480)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6728)
Starts itself from another location
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- 7WTY6YS5DNLYFYJLSUQ.exe (PID: 7124)
Reads security settings of Internet Explorer
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 7920)
Application launched itself
- svchost.exe (PID: 4120)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 7920)
The process executes via Task Scheduler
- ramez.exe (PID: 4428)
- PLUGScheduler.exe (PID: 3640)
- ramez.exe (PID: 2432)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 4336)
Checks for external IP
- svchost.exe (PID: 4336)
- svchost.exe (PID: 2196)
Executes application which crashes
- HGVm49v.exe (PID: 5868)
Reads the Windows owner or organization settings
- 3d1e813836.tmp (PID: 7748)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 7640)
INFO
Checks supported languages
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- ramez.exe (PID: 7920)
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 4428)
- e5jg7MM.exe (PID: 2236)
- d1oAX1c.exe (PID: 7228)
- MSBuild.exe (PID: 6228)
- HGVm49v.exe (PID: 5868)
- MSBuild.exe (PID: 7640)
- ra02W4S.exe (PID: 7760)
- 3d1e813836.exe (PID: 7860)
- 3d1e813836.tmp (PID: 7748)
Reads the software policy settings
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- MSBuild.exe (PID: 7640)
- MSBuild.exe (PID: 6228)
Reads the computer name
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 7920)
- MSBuild.exe (PID: 7640)
- MSBuild.exe (PID: 6228)
- 3d1e813836.tmp (PID: 7748)
Create files in a temporary directory
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 7920)
- 3d1e813836.exe (PID: 7860)
- 3d1e813836.tmp (PID: 7748)
Themida protector has been detected
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6132)
- ramez.exe (PID: 7920)
Process checks computer location settings
- 6DTM3GABA555NFMTNYONN20.exe (PID: 7744)
- ramez.exe (PID: 7920)
Checks proxy server information
- ramez.exe (PID: 7920)
Creates files or folders in the user directory
- ramez.exe (PID: 7920)
- WerFault.exe (PID: 4112)
- 3d1e813836.tmp (PID: 7748)
The sample compiled with english language support
- ramez.exe (PID: 7920)
Manual execution by a user
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6504)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6956)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 2028)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 4044)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6676)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 7104)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 480)
- Taskmgr.exe (PID: 3272)
- Taskmgr.exe (PID: 2512)
- Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe (PID: 6728)
Creates a software uninstall entry
- 3d1e813836.tmp (PID: 7748)
Attempting to use instant messaging service
- MSBuild.exe (PID: 7640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(6132) Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe
C2 (9)featurlyin.top/pdal
overcovtcg.top/juhd
meteorplyp.live/lekp
zmedtipp.live/mnvzx
flowerexju.bet/lanz
posseswsnc.top/akds
araucahkbm.live/baneb
blackswmxc.top/bgry
easterxeen.run/zavc
Amadey
(PID) Process(7920) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
d610cf342e
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
/te4h2nus/index.php
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
ramez.exe
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
185.156.72.96
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:08 12:17:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 314880 |
| InitializedDataSize: | 37376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4bb000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
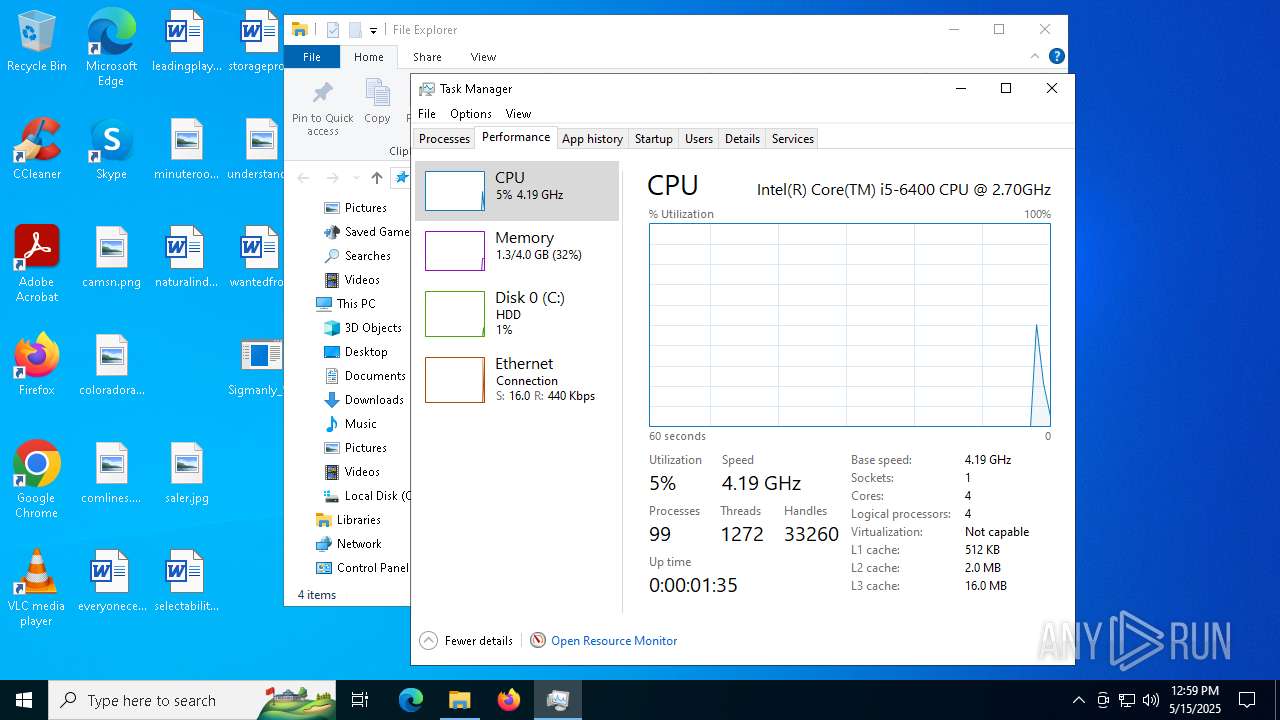
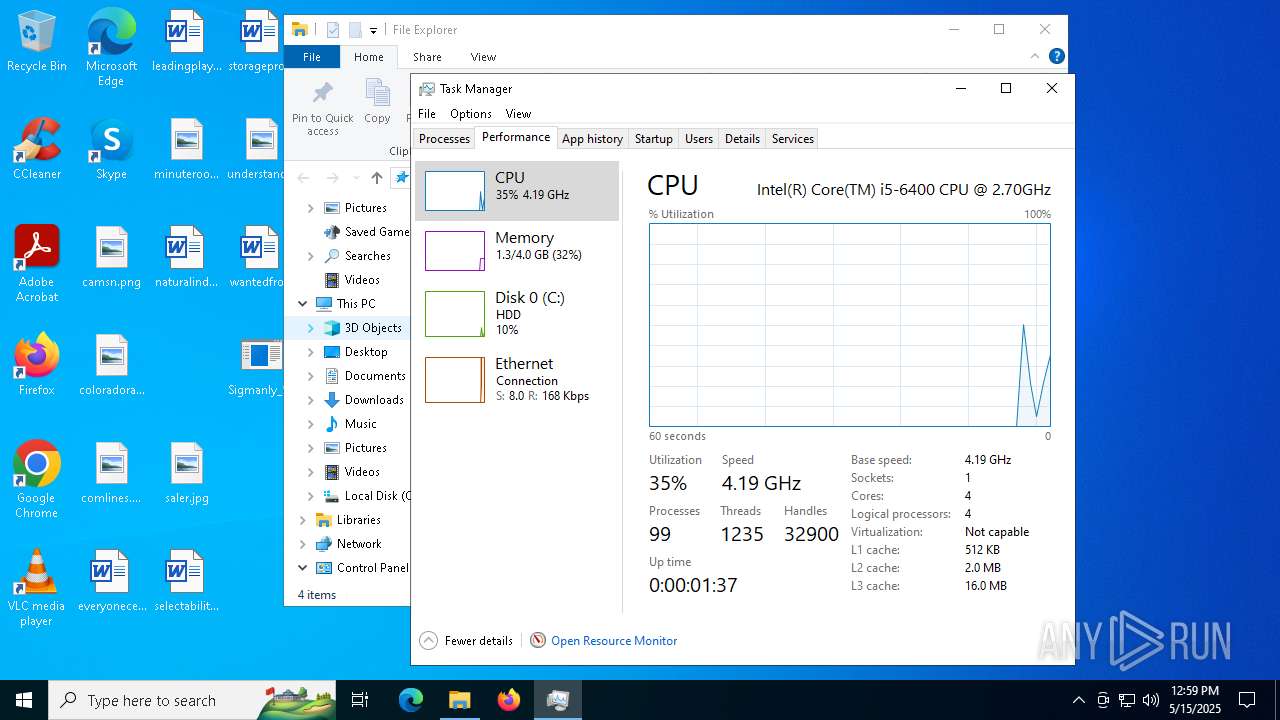
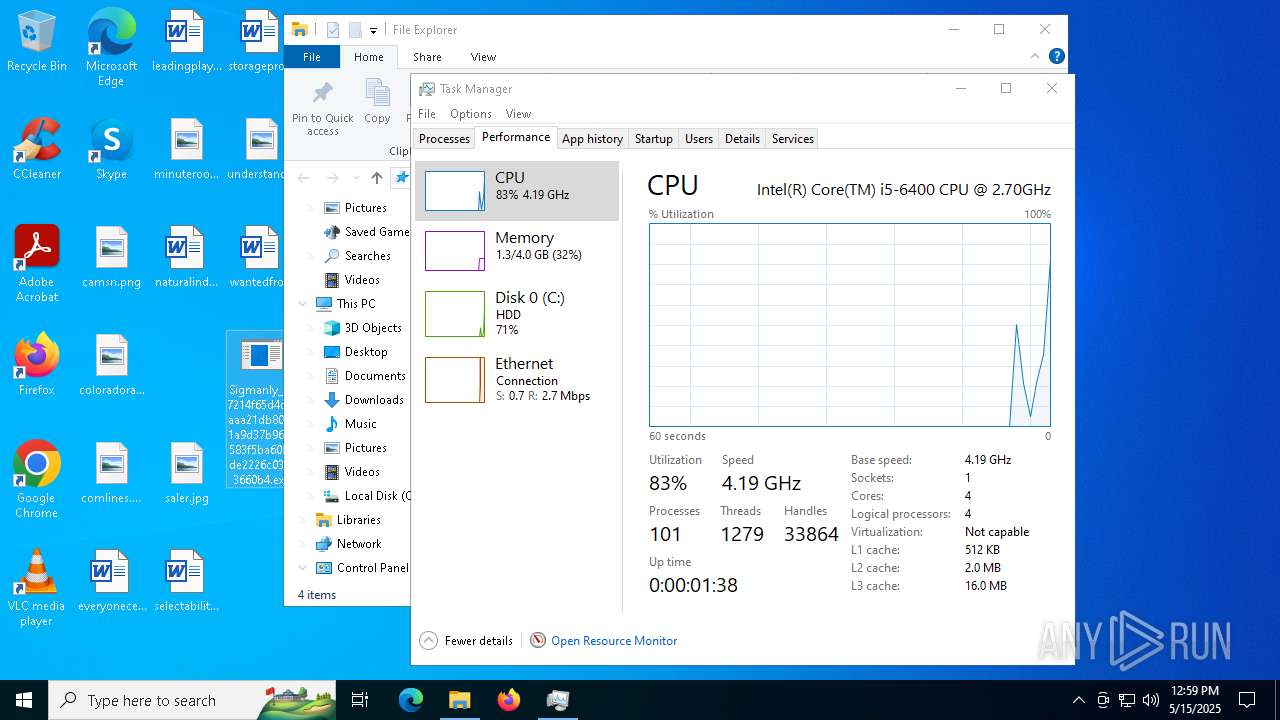
Total processes
317
Monitored processes
42
Malicious processes
22
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Users\admin\Desktop\Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe" | C:\Users\admin\Desktop\Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 716 | "C:\Users\admin\AppData\Local\Temp\US9U5E7QZGFXXAKBPJAGWQUVLVQRO.exe" | C:\Users\admin\AppData\Local\Temp\US9U5E7QZGFXXAKBPJAGWQUVLVQRO.exe | — | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\AppData\Local\Temp\S15PYHD5FQE7N0CREXESCQM0KHR3.exe" | C:\Users\admin\AppData\Local\Temp\S15PYHD5FQE7N0CREXESCQM0KHR3.exe | — | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1516 | "C:\Users\admin\AppData\Local\Temp\GQOBZ3F3GCSXL9K7.exe" | C:\Users\admin\AppData\Local\Temp\GQOBZ3F3GCSXL9K7.exe | — | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2028 | "C:\Users\admin\Desktop\Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe" | C:\Users\admin\Desktop\Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2140 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | "C:\Users\admin\AppData\Local\Temp\BJ2X7TNTO5GQOCTE.exe" | C:\Users\admin\AppData\Local\Temp\BJ2X7TNTO5GQOCTE.exe | — | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\AppData\Local\Temp\10117950101\e5jg7MM.exe" | C:\Users\admin\AppData\Local\Temp\10117950101\e5jg7MM.exe | — | ramez.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe" | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
15 051
Read events
15 023
Write events
27
Delete events
1
Modification events
| (PID) Process: | (7920) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7920) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7920) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
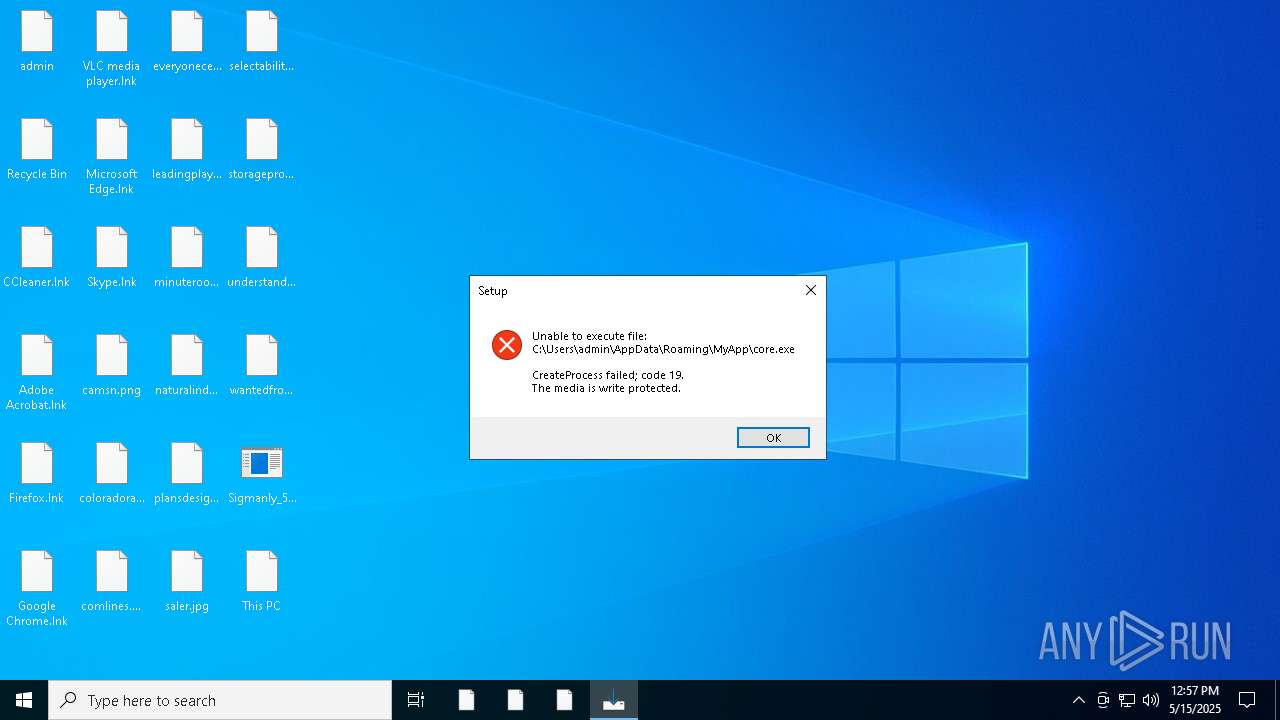
| (PID) Process: | (7748) 3d1e813836.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.4.0 | |||
| (PID) Process: | (7748) 3d1e813836.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Roaming\MyApp | |||
| (PID) Process: | (7748) 3d1e813836.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Roaming\MyApp\ | |||
| (PID) Process: | (7748) 3d1e813836.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: MyApp | |||
| (PID) Process: | (7748) 3d1e813836.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (7748) 3d1e813836.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: default | |||
| (PID) Process: | (7748) 3d1e813836.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | DisplayName |
Value: MyApp version 1.0 | |||
Executable files
28
Suspicious files
50
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4112 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_HGVm49v.exe_ebc2bfdeb02554ccbb4f874b72494cab36ea3d4_a3665544_fff0a520-5da7-4b4b-afb0-8f8706790dc7\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6132 | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | C:\Users\admin\AppData\Local\Temp\6DTM3GABA555NFMTNYONN20.exe | executable | |
MD5:C5BCF2D948DCC86EE7DC2602FE981ED9 | SHA256:240E881B07BA103AB66CE6D7D8E555B0ACB3F359E6CFD6563788A2B205C2442E | |||
| 4112 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\HGVm49v.exe.5868.dmp | binary | |
MD5:FDBD18E42FC7818F8B16610EF3F47E01 | SHA256:6FC3B9BE116E9201D0635E2066860B4F82D3D5F3F2FFBCB918784ADAF6219D48 | |||
| 7744 | 6DTM3GABA555NFMTNYONN20.exe | C:\Windows\Tasks\ramez.job | binary | |
MD5:015A037C3552C30EC829D8CCCD57458D | SHA256:6845447C8455E4C5CDEDA76842731A19D72E951A736792C197CC6E09853706AD | |||
| 7744 | 6DTM3GABA555NFMTNYONN20.exe | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | executable | |
MD5:C5BCF2D948DCC86EE7DC2602FE981ED9 | SHA256:240E881B07BA103AB66CE6D7D8E555B0ACB3F359E6CFD6563788A2B205C2442E | |||
| 7920 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10117950101\e5jg7MM.exe | executable | |
MD5:7B07898D527A455AE4669C253D8722D5 | SHA256:0D532157B751A2AFE492ED04131E1C05D12D425CE65F5FD9FE7E5F92B2F526E2 | |||
| 4112 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5012.tmp.WERInternalMetadata.xml | binary | |
MD5:5699B76DA937CA78967A5AB9BA9E46C5 | SHA256:F68783F42786DF6FFB90EEA6CF816B2FE77DFD12C79DDC75D8B047D4C5C474B0 | |||
| 7920 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10117960101\HGVm49v.exe | executable | |
MD5:A33FA5D4484673A634FB1DA94EB0A4B0 | SHA256:2229D49F74E72840F0A315372ECA8C099F1226AC1B63CAA3917EF39739BCAC26 | |||
| 4112 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER4F27.tmp.dmp | binary | |
MD5:82D6FF8D3E9253470477408BDB252676 | SHA256:06DA31CF8230CB02FD28C6B9309CDFA5B0247653CBB8D4B4D741CC51D99D6B0E | |||
| 4112 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5051.tmp.xml | xml | |
MD5:FF7CE1CFE1973D26B3653E3D90889B98 | SHA256:06645F71B169341BD8C1548D4C80A102CE2C0B80570E27EE1A89F2DD16B47420 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
142
TCP/UDP connections
172
DNS requests
78
Threats
162
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6132 | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/mine/random.exe | unknown | — | — | unknown |
7920 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
4336 | svchost.exe | HEAD | 206 | 23.95.245.178:80 | http://23.95.245.178/cvk90 | unknown | — | — | unknown |
7920 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/5561582465/e5jg7MM.exe | unknown | — | — | unknown |
4336 | svchost.exe | GET | 206 | 23.95.245.178:80 | http://23.95.245.178/cvk90 | unknown | — | — | unknown |
7920 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
4336 | svchost.exe | GET | 206 | 23.95.245.178:80 | http://23.95.245.178/cvk90 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4024 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6132 | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | 172.67.150.184:443 | overcovtcg.top | CLOUDFLARENET | US | malicious |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6132 | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
meteorplyp.live |
| malicious |
flowerexju.bet |
| malicious |
zmedtipp.live |
| malicious |
easterxeen.run |
| malicious |
araucahkbm.live |
| malicious |
overcovtcg.top |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (overcovtcg .top) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (easterxeen .run) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (araucahkbm .live) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (flowerexju .bet) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (zmedtipp .live) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (meteorplyp .live) |
6132 | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
6132 | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
6132 | Sigmanly_527214f65d4c7aaaa21db80291a9d37b9625583f5ba60b3de2226c03713660b4.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |