| File name: | e0efd04993bb3f169b71cc88474aac95.xls |
| Full analysis: | https://app.any.run/tasks/f9c9fae1-e8c1-4d01-99b8-a62426cc85f3 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | March 21, 2019, 03:16:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Windows User, Last Saved By: Windows User, Name of Creating Application: Microsoft Excel, Create Time/Date: Wed Mar 20 10:23:25 2019, Last Saved Time/Date: Wed Mar 20 10:31:38 2019, Security: 0 |
| MD5: | E0EFD04993BB3F169B71CC88474AAC95 |
| SHA1: | 1B9472407658503F1E92D11E7656AF9C3DF65CE2 |
| SHA256: | 525E268FD0F4E402A46538E8ABD4E26FB6CD8961164AC372DEDAE7FE2960C814 |
| SSDEEP: | 3072:GaxEtjPOtioVjDGUU1qfDlaGGx+cL2QnAb8fblW66CQt+RmaiIT54rLyBm87wNSN:NxEtjPOtioVjDGUU1qfDlavx+W2QnAok |
MALICIOUS
Application was dropped or rewritten from another process
- ZFSJSLN.exe (PID: 1544)
- WerFault.exe (PID: 2996)
Detected artifacts of LokiBot
- WerFault.exe (PID: 2996)
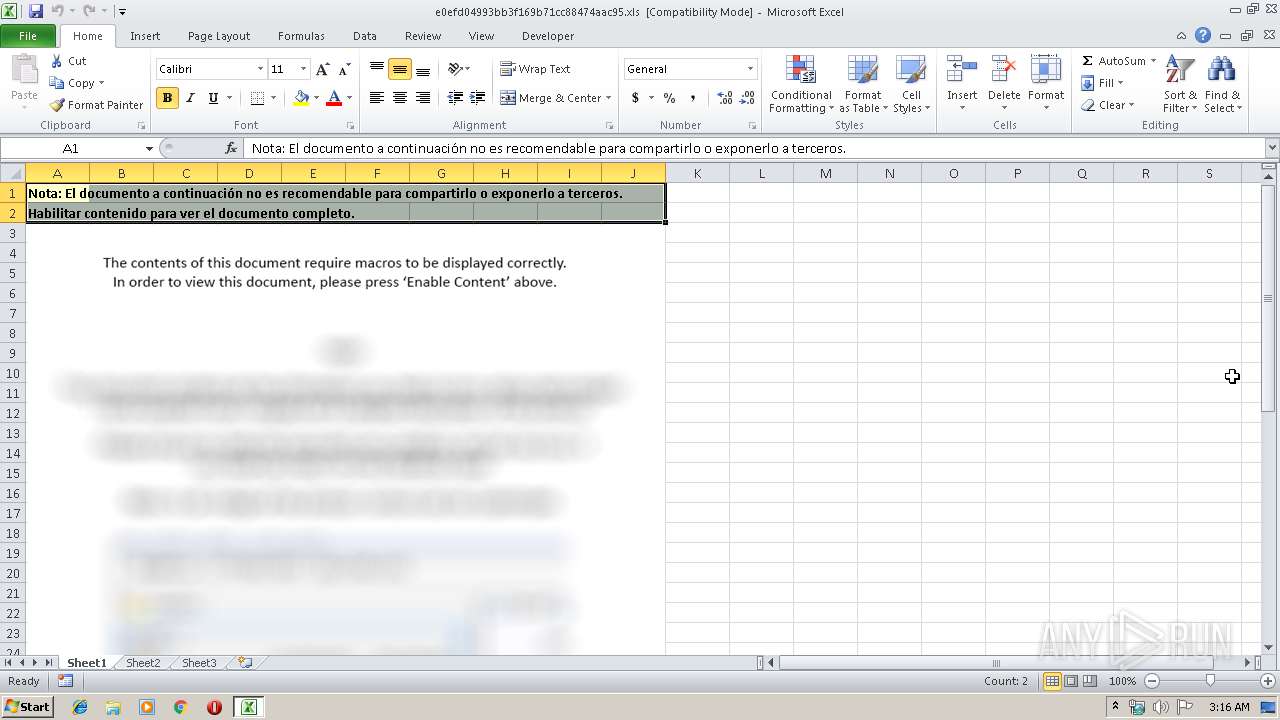
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 128)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 128)
Connects to CnC server
- WerFault.exe (PID: 2996)
Actions looks like stealing of personal data
- WerFault.exe (PID: 2996)
SUSPICIOUS
Loads DLL from Mozilla Firefox
- WerFault.exe (PID: 2996)
Executable content was dropped or overwritten
- WerFault.exe (PID: 2996)
Creates files in the user directory
- WerFault.exe (PID: 2996)
Connects to server without host name
- WerFault.exe (PID: 2996)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 128)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | Windows User |
|---|---|
| LastModifiedBy: | Windows User |
| Software: | Microsoft Excel |
| CreateDate: | 2019:03:20 10:23:25 |
| ModifyDate: | 2019:03:20 10:31:38 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
33
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1544 | "C:\Users\admin\AppData\Local\Temp\ZFSJSLN.exe" | C:\Users\admin\AppData\Local\Temp\ZFSJSLN.exe | — | EXCEL.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2996 | "C:\Windows\system32\WerFault.exe" | C:\Windows\system32\WerFault.exe | ZFSJSLN.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
612
Read events
572
Write events
33
Delete events
7
Modification events
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ;i8 |
Value: 3B69380080000000010000000000000000000000 | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 800000003406497894DFD40100000000 | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | ;i8 |
Value: 3B69380080000000010000000000000000000000 | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (128) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\F8FE4 |
| Operation: | write | Name: | F8FE4 |
Value: 04000000800000004600000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00650030006500660064003000340039003900330062006200330066003100360039006200370031006300630038003800340037003400610061006300390035002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0001000000000000000099A27994DFD401E48F0F00E48F0F0000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
3
Suspicious files
1
Text files
1
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 128 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR893B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1544 | ZFSJSLN.exe | C:\Users\admin\AppData\Local\Temp\aut97D2.tmp | — | |
MD5:— | SHA256:— | |||
| 2996 | WerFault.exe | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.lck | — | |
MD5:— | SHA256:— | |||
| 1544 | ZFSJSLN.exe | C:\Users\admin\AppData\Local\Temp\1.resource | binary | |
MD5:— | SHA256:— | |||
| 2996 | WerFault.exe | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.hdb | text | |
MD5:— | SHA256:— | |||
| 128 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\DSFJSDJGBSRE[1].exe | executable | |
MD5:— | SHA256:— | |||
| 128 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\ZFSJSLN.exe | executable | |
MD5:— | SHA256:— | |||
| 2996 | WerFault.exe | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.exe | executable | |
MD5:5FEAB868CAEDBBD1B7A145CA8261E4AA | SHA256:08BACE187A0225E10677DE9AA6738A7118BE3E5CAD6DC45FB8D3366A61BB343C | |||
| 2996 | WerFault.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\0f5007522459c86e95ffcc62f32308f1_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:18B8CFC0185C50383AAC0A4F30A9DAC8 | SHA256:913E8CED6A447FE791954D382ABA52D490513C5D2F689B391866C7E561F89A03 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
1
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2996 | WerFault.exe | POST | — | 155.94.211.199:80 | http://155.94.211.199/freshmint/Panel/five/fre.php | US | — | — | malicious |
2996 | WerFault.exe | POST | — | 155.94.211.199:80 | http://155.94.211.199/freshmint/Panel/five/fre.php | US | — | — | malicious |
2996 | WerFault.exe | POST | — | 155.94.211.199:80 | http://155.94.211.199/freshmint/Panel/five/fre.php | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2996 | WerFault.exe | 155.94.211.199:80 | — | QuadraNet, Inc | US | malicious |
128 | EXCEL.EXE | 185.103.97.212:443 | www.nilemixitupd.biz.pl | UK Dedicated Servers Limited | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.nilemixitupd.biz.pl |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
128 | EXCEL.EXE | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
2996 | WerFault.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
2996 | WerFault.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3 ETPRO signatures available at the full report