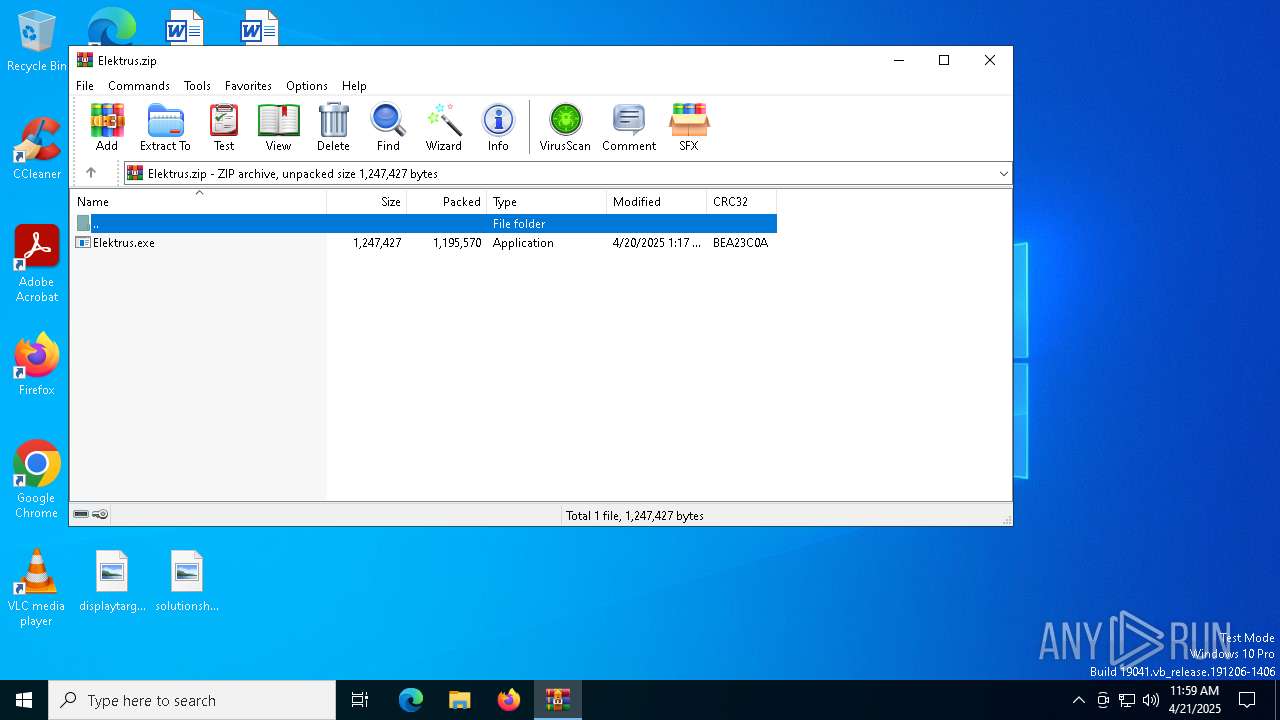
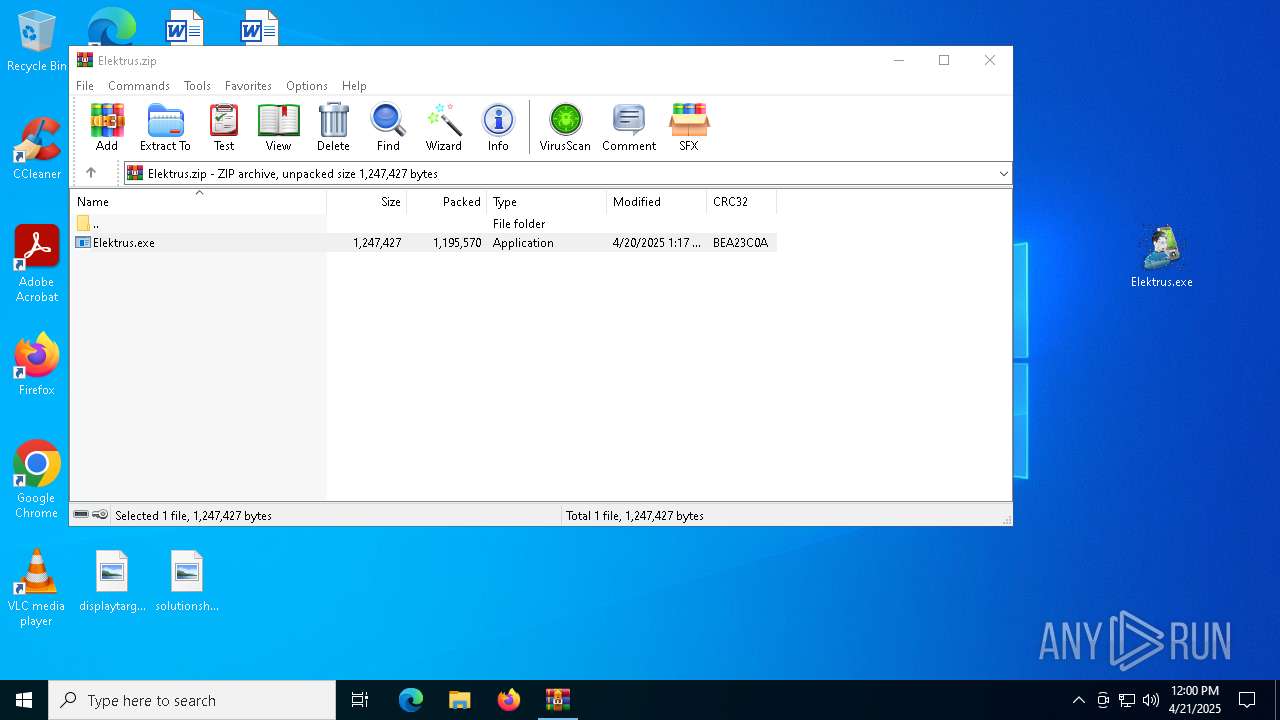
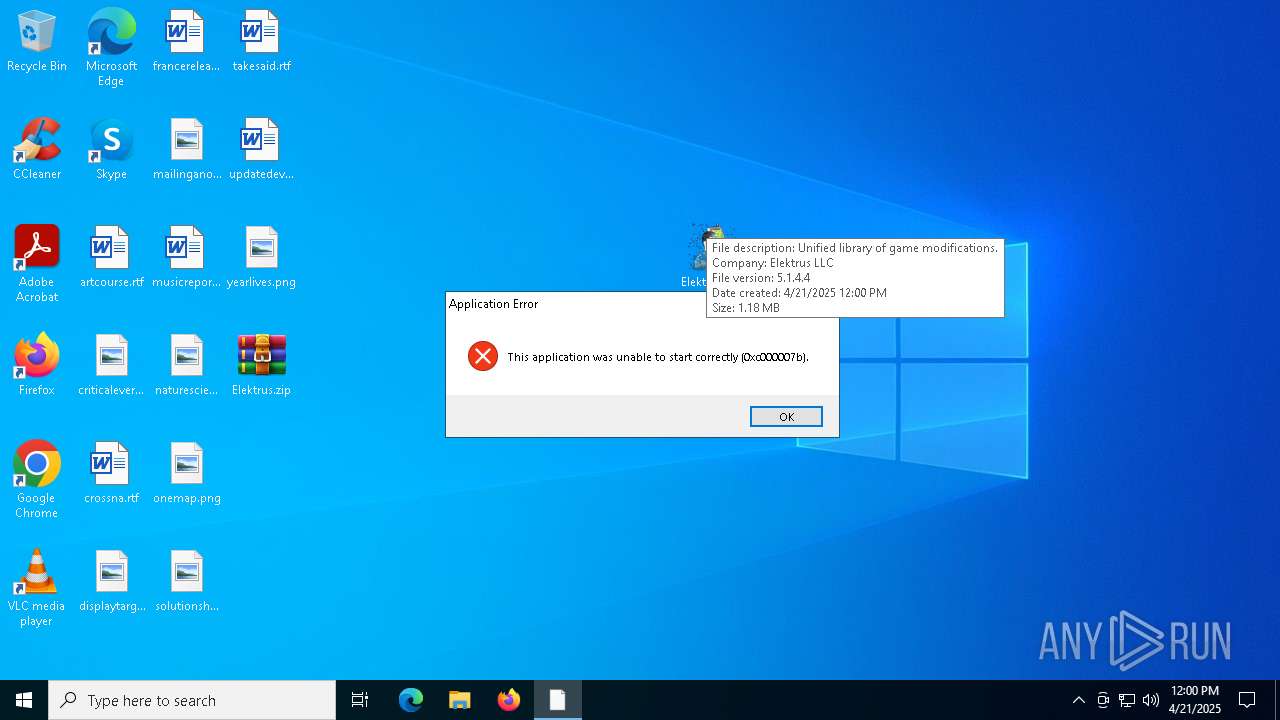
| File name: | Elektrus.zip |
| Full analysis: | https://app.any.run/tasks/becb4152-ee51-402e-a505-72084d116594 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 21, 2025, 11:58:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B3D6CECC7451F5A602598699E842989C |
| SHA1: | C138200CCA359A8731600B503498489AFF39AB57 |
| SHA256: | 524A7AEE21F0C3F3B2CBA3377DBBD519B8C9D91F99B6E27AD24A2E62EE991716 |
| SSDEEP: | 49152:2kvvIQjx8PzUYO2COz9L338n0EOFz/Hd8f9vJwCbvQLOqepDzDRy1yAiDt9qPyMX:JvvpgzUYjJ53kNY98f1WCDqedk1yfh9K |
MALICIOUS
Executing a file with an untrusted certificate
- Elektrus.exe (PID: 5548)
Generic archive extractor
- WinRAR.exe (PID: 4452)
AutoIt loader has been detected (YARA)
- Instantly.com (PID: 4740)
LUMMA mutex has been found
- Instantly.com (PID: 4740)
LUMMA has been detected (SURICATA)
- Instantly.com (PID: 4740)
- svchost.exe (PID: 2196)
Connects to the CnC server
- svchost.exe (PID: 2196)
Actions looks like stealing of personal data
- Instantly.com (PID: 4740)
- Instantly.com (PID: 4740)
Steals credentials from Web Browsers
- Instantly.com (PID: 4740)
SUSPICIOUS
Get information on the list of running processes
- cmd.exe (PID: 896)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 896)
- Elektrus.exe (PID: 5548)
Executing commands from a ".bat" file
- Elektrus.exe (PID: 5548)
Starts the AutoIt3 executable file
- cmd.exe (PID: 896)
Reads security settings of Internet Explorer
- Elektrus.exe (PID: 5548)
There is functionality for taking screenshot (YARA)
- Instantly.com (PID: 4740)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 896)
Application launched itself
- cmd.exe (PID: 896)
The executable file from the user directory is run by the CMD process
- Instantly.com (PID: 4740)
Starts application with an unusual extension
- cmd.exe (PID: 896)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- Instantly.com (PID: 4740)
Searches for installed software
- Instantly.com (PID: 4740)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4452)
Checks supported languages
- extrac32.exe (PID: 856)
- Elektrus.exe (PID: 5548)
- Instantly.com (PID: 4740)
Reads the computer name
- Elektrus.exe (PID: 5548)
- Instantly.com (PID: 4740)
- extrac32.exe (PID: 856)
Reads the software policy settings
- slui.exe (PID: 6044)
- Instantly.com (PID: 4740)
- slui.exe (PID: 4692)
Process checks computer location settings
- Elektrus.exe (PID: 5548)
Create files in a temporary directory
- Elektrus.exe (PID: 5548)
- extrac32.exe (PID: 856)
Reads mouse settings
- Instantly.com (PID: 4740)
Manual execution by a user
- Elektrus.exe (PID: 5548)
Creates a new folder
- cmd.exe (PID: 1568)
Checks proxy server information
- slui.exe (PID: 4692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:20 09:17:34 |
| ZipCRC: | 0xbea23c0a |
| ZipCompressedSize: | 1195570 |
| ZipUncompressedSize: | 1247427 |
| ZipFileName: | Elektrus.exe |
Total processes
147
Monitored processes
19
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | cmd /c copy /b 772673\Instantly.com + Tutorials + Extremely + Hawaii + Catering + Spot + Au + Females + Pat + Ideal 772673\Instantly.com | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | extrac32 /Y /E Toe.ppsx | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | "C:\WINDOWS\System32\cmd.exe" /c copy Webshots.ppsx Webshots.ppsx.bat & Webshots.ppsx.bat | C:\Windows\SysWOW64\cmd.exe | — | Elektrus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | findstr /I "opssvc wrsa" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | findstr /V "Elegant" Detailed | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | cmd /c md 772673 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | cmd /c copy /b ..\Infectious.ppsx + ..\Diving.ppsx + ..\Ends.ppsx + ..\Elections.ppsx + ..\Else.ppsx + ..\Clinic.ppsx + ..\Prepaid.ppsx + ..\Vice.ppsx z | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 4452 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Elektrus.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 140
Read events
3 122
Write events
18
Delete events
0
Modification events
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Elektrus.zip | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (4452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
1
Suspicious files
19
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5548 | Elektrus.exe | C:\Users\admin\AppData\Local\Temp\Else.ppsx | binary | |
MD5:5C0EC9ACDDFB1AFD2E8846736AD3C34E | SHA256:D99229DB0DE8AFA599BE8731B2C178679B2E82FC05F063899CD65FE5056FD235 | |||
| 5548 | Elektrus.exe | C:\Users\admin\AppData\Local\Temp\Ends.ppsx | binary | |
MD5:EB225AFCFC0697A14192351F7C30C14E | SHA256:CE01390CC12105FEF4958F26AAB0D4B4B07A5A70C890F8FD196415F530FDD9AE | |||
| 856 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Females | binary | |
MD5:2C6138AD8C005C492BF1D256D933E27C | SHA256:41FD5F65FA2EFE24F323DB7F0B307FEBEA2B5E650BC5C0C24D59EB2D8694DEF2 | |||
| 4452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4452.11396\Elektrus.exe | executable | |
MD5:41A6CD61D23CC6B868F649A6CC2D6F62 | SHA256:0B3A0738E27EDD5B654A28B610C6AB973A968255CD32E9D265F47B2E2F70E67F | |||
| 5548 | Elektrus.exe | C:\Users\admin\AppData\Local\Temp\Vice.ppsx | binary | |
MD5:068D311ACF1AC94F58CCE95B2516B9C8 | SHA256:2CFA98E5EB99C7DB7E6A896856F73E5AA2D65484422ADAABD2178EB2131030B4 | |||
| 5548 | Elektrus.exe | C:\Users\admin\AppData\Local\Temp\Elections.ppsx | binary | |
MD5:819A1AE350FCA23FD6BAAAE2090CA78E | SHA256:F90AC9466619A729A19642EF56F35023F99E8FBA65A02ADF7ED691712E36FD34 | |||
| 896 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Webshots.ppsx.bat | text | |
MD5:4BE2BC83969841071C0CCEE852A2FD6E | SHA256:CD2673270F49D550A644D085235B4C0C9E8F90EFC32233088E12650F8814592F | |||
| 856 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Catering | binary | |
MD5:6F614150C55AD39C850FBB4787D113D0 | SHA256:7589959320EBF3DD98A928A821BFFB85E948A22FE6217F143B60DB9316E973A2 | |||
| 5548 | Elektrus.exe | C:\Users\admin\AppData\Local\Temp\Clinic.ppsx | binary | |
MD5:1EE6C7CCB27D432A7072D43095C943B6 | SHA256:07C3468BED18909CDC8E2F4B56523DCB70D52DE747DC6F8AD786D242FAA3426A | |||
| 856 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Pat | binary | |
MD5:EEFD6AD07E3BDC4C895C1E8B43FF08C3 | SHA256:66F3B2B2E2E76AF1DA6C6A81A29F0791082006DB0B87814B9501FBFB5EEEE5DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
19
DNS requests
9
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 104.83.4.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 92.123.37.9:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.83.4.146:80 | crl.microsoft.com | Akamai International B.V. | AT | whitelisted |
— | — | 92.123.37.9:80 | www.microsoft.com | AKAMAI-AS | AT | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6044 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4740 | Instantly.com | 104.21.85.126:443 | clarmodq.top | CLOUDFLARENET | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
hCJfNGJjNAnmyVkXDJjNZ.hCJfNGJjNAnmyVkXDJjNZ |
| unknown |
clarmodq.top |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (clarmodq .top) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (clarmodq .top) |
4740 | Instantly.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
4740 | Instantly.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
4740 | Instantly.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
4740 | Instantly.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
4740 | Instantly.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
4740 | Instantly.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |