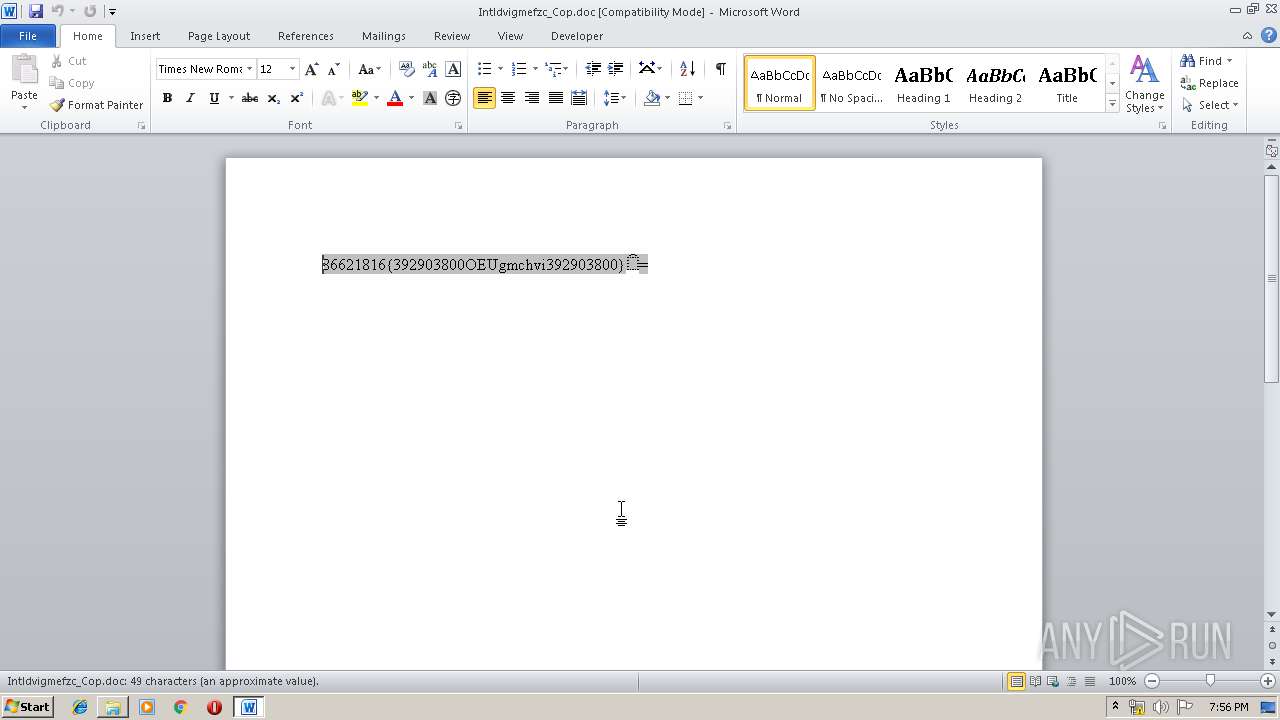
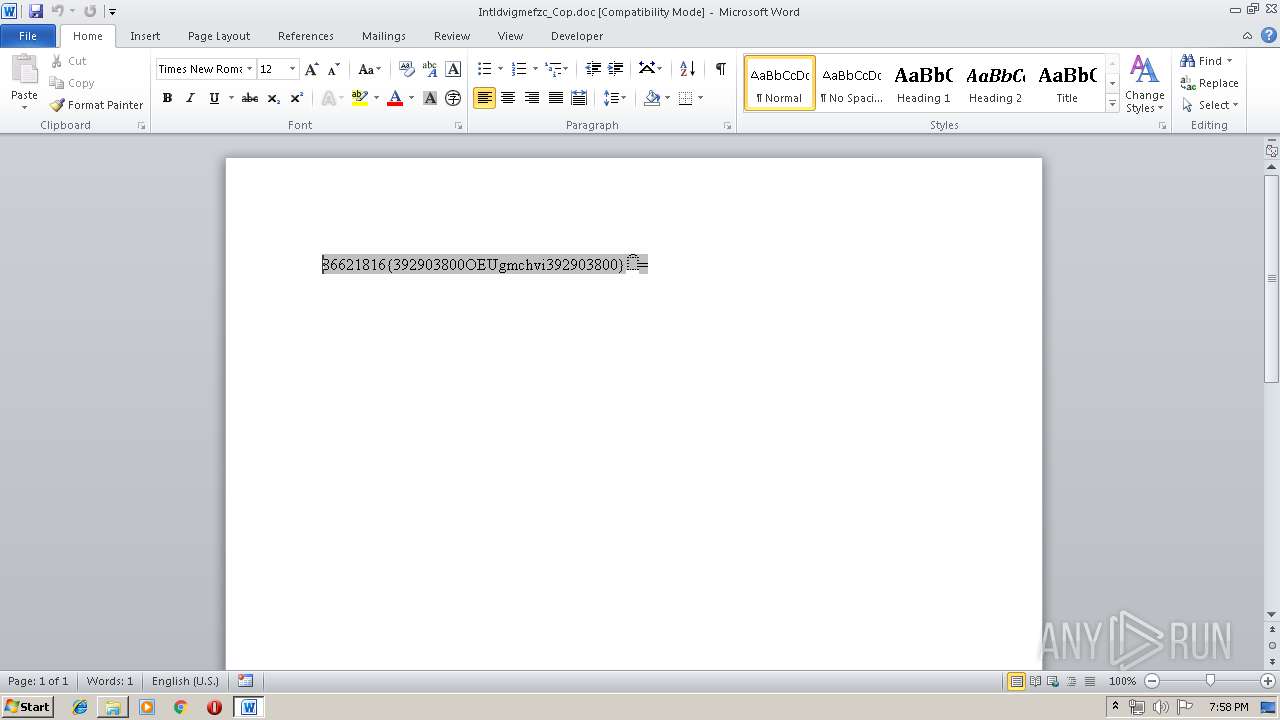
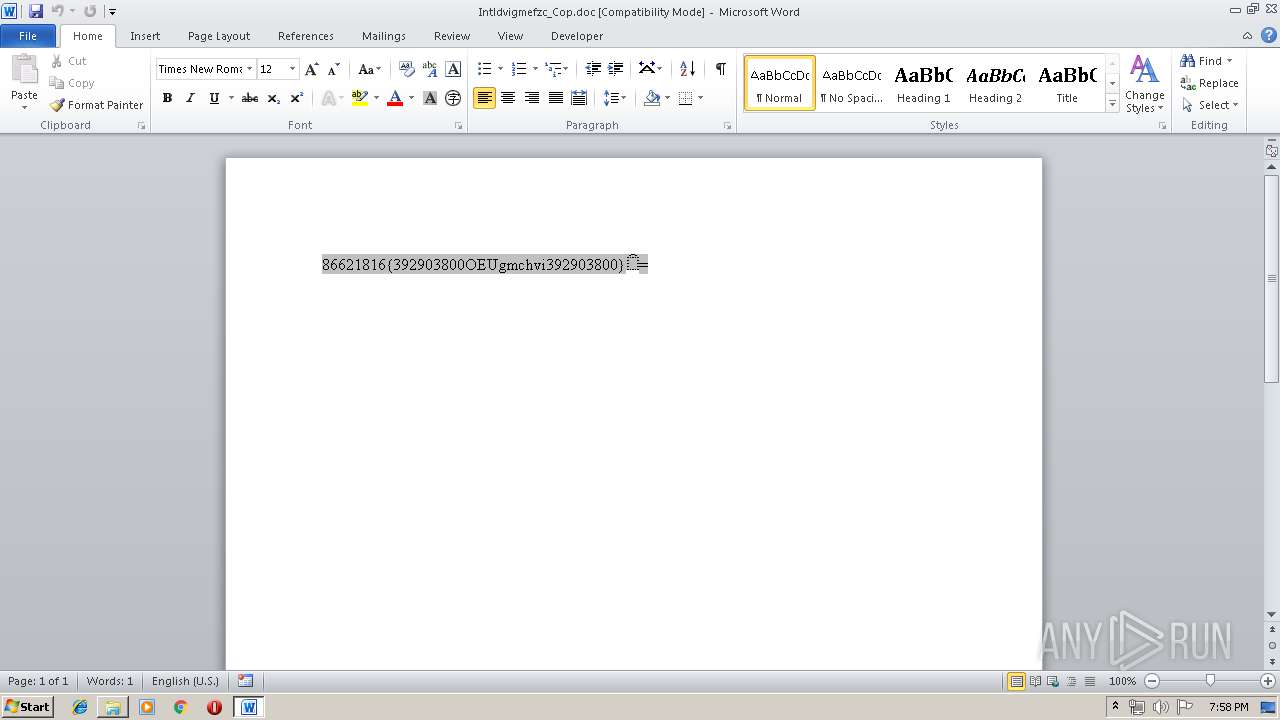
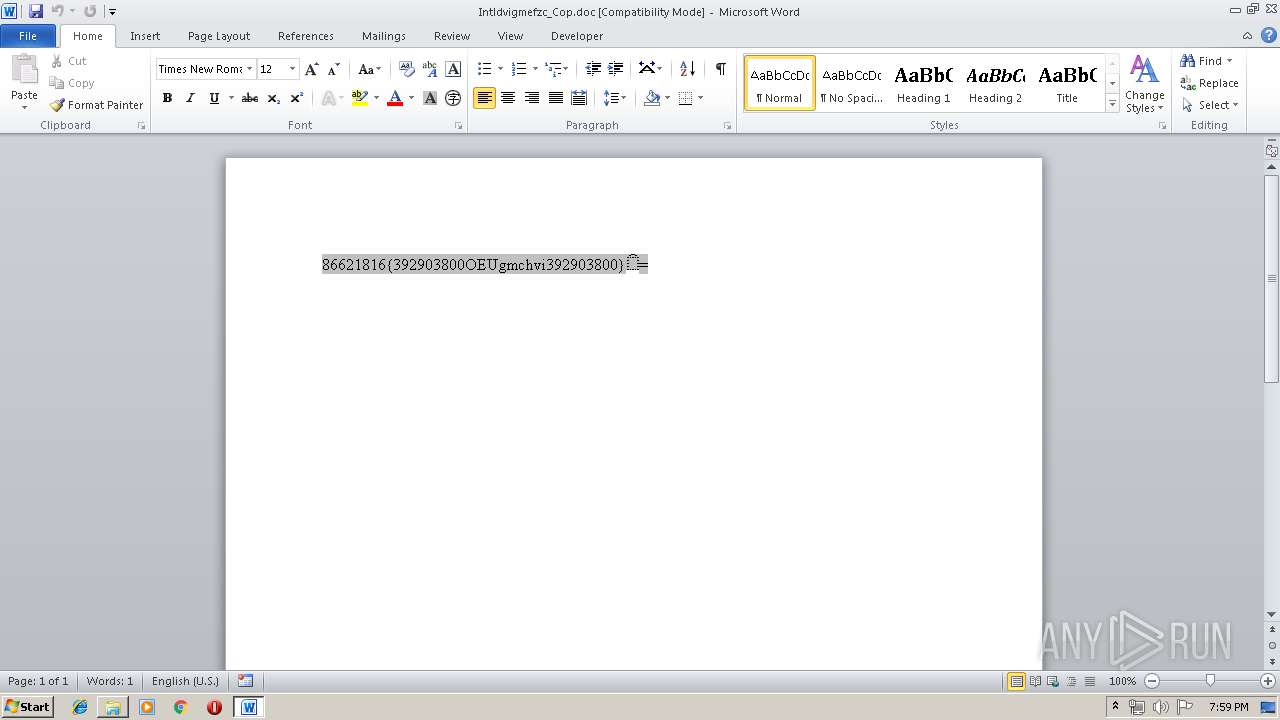
| File name: | Intldvigmefzc_Cop.doc |
| Full analysis: | https://app.any.run/tasks/c81c460b-847c-487a-94cd-f60a4f0df8b9 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | December 02, 2019, 19:54:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, unknown version |
| MD5: | 2D38C831449AD31D3A58592FA4142F0B |
| SHA1: | 7C6FC38004AA455B2B3E7B5D6A58154E3283833F |
| SHA256: | 51F9B61A7735FE1551FFFBED05E8D6A969C6D5E072849AAA5522C8EB06030BEF |
| SSDEEP: | 12288:ZiEUeRxtMFuzqgU1lR89w9Ki3fLMjrLZ9yt6hzIkJ1Be04mFRep77V6Z2xt8l:ZFUAMF63qD8yU0fLMu8JIkJ+iF4V6UfK |
MALICIOUS
Application was dropped or rewritten from another process
- mroutputroj4737.com (PID: 788)
- mroutputroj4737.com (PID: 1268)
- MR.FESTUS ORIGIN RAWFILE.exe (PID: 2212)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3624)
Downloads executable files from the Internet
- EQNEDT32.EXE (PID: 3624)
AGENTTESLA detected
- MR.FESTUS ORIGIN RAWFILE.exe (PID: 2212)
FORMBOOK was detected
- explorer.exe (PID: 352)
- Firefox.exe (PID: 2392)
- NAPSTAT.EXE (PID: 3784)
Actions looks like stealing of personal data
- MR.FESTUS ORIGIN RAWFILE.exe (PID: 2212)
- NAPSTAT.EXE (PID: 3784)
Connects to CnC server
- explorer.exe (PID: 352)
Changes the autorun value in the registry
- NAPSTAT.EXE (PID: 3784)
Stealing of credential data
- NAPSTAT.EXE (PID: 3784)
SUSPICIOUS
Starts application with an unusual extension
- EQNEDT32.EXE (PID: 3624)
- mroutputroj4737.com (PID: 1268)
Creates files in the user directory
- EQNEDT32.EXE (PID: 3624)
- NAPSTAT.EXE (PID: 3784)
Executed via COM
- EQNEDT32.EXE (PID: 3624)
- EQNEDT32.EXE (PID: 3932)
Application launched itself
- mroutputroj4737.com (PID: 1268)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 3624)
- mroutputroj4737.com (PID: 788)
Starts CMD.EXE for commands execution
- NAPSTAT.EXE (PID: 3784)
Loads DLL from Mozilla Firefox
- NAPSTAT.EXE (PID: 3784)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 4060)
- WINWORD.EXE (PID: 2172)
Manual execution by user
- verclsid.exe (PID: 2892)
- WINWORD.EXE (PID: 4060)
- autoconv.exe (PID: 2660)
- autoconv.exe (PID: 2772)
- NAPSTAT.EXE (PID: 3784)
Creates files in the user directory
- WINWORD.EXE (PID: 2172)
- Firefox.exe (PID: 2392)
Starts Microsoft Office Application
- explorer.exe (PID: 352)
Reads settings of System Certificates
- MR.FESTUS ORIGIN RAWFILE.exe (PID: 2212)
Reads the hosts file
- NAPSTAT.EXE (PID: 3784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
52
Monitored processes
14
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 788 | "C:\Users\admin\AppData\Roaming\mroutputroj4737.com" | C:\Users\admin\AppData\Roaming\mroutputroj4737.com | mroutputroj4737.com | ||||||||||||
User: admin Company: prj4___Supe4 Integrity Level: MEDIUM Description: prj4___Supe4 Exit code: 0 Version: 6.06.0008 Modules
| |||||||||||||||
| 1268 | "C:\Users\admin\AppData\Roaming\mroutputroj4737.com" | C:\Users\admin\AppData\Roaming\mroutputroj4737.com | — | EQNEDT32.EXE | |||||||||||
User: admin Company: prj4___Supe4 Integrity Level: MEDIUM Description: prj4___Supe4 Exit code: 0 Version: 6.06.0008 Modules
| |||||||||||||||
| 2104 | /c del "C:\Users\admin\AppData\Roaming\mroutputroj4737.com" | C:\Windows\System32\cmd.exe | — | NAPSTAT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Intldvigmefzc_Cop.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2212 | "C:\Users\admin\MR.FESTUS ORIGIN RAWFILE.exe" | C:\Users\admin\MR.FESTUS ORIGIN RAWFILE.exe | mroutputroj4737.com | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2392 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | NAPSTAT.EXE | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2660 | "C:\Windows\System32\autoconv.exe" | C:\Windows\System32\autoconv.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Conversion Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2772 | "C:\Windows\System32\autoconv.exe" | C:\Windows\System32\autoconv.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Conversion Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2892 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 219
Read events
2 452
Write events
1 501
Delete events
266
Modification events
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | w}a |
Value: 777D61007C080000010000000000000000000000 | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2172) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1333919806 | |||
Executable files
3
Suspicious files
78
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2172 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA9A8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2172 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{CF735F48-CB65-4BB1-89F3-B64CC4972684}.tmp | — | |
MD5:— | SHA256:— | |||
| 2172 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{C39DCD18-3F71-4C41-BC7C-8C57C01A2BCE}.tmp | — | |
MD5:— | SHA256:— | |||
| 4060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD4F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2172 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$tldvigmefzc_Cop.doc | pgc | |
MD5:— | SHA256:— | |||
| 2172 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2172 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{8E7C4E4A-3096-4CBD-AAE0-E084289DABF5}.tmp | binary | |
MD5:— | SHA256:— | |||
| 3784 | NAPSTAT.EXE | C:\Users\admin\AppData\Roaming\1NP-10-A\1NPlogrc.ini | binary | |
MD5:— | SHA256:— | |||
| 788 | mroutputroj4737.com | C:\Users\admin\MR.FESTUS ORIGIN RAWFILE.exe | executable | |
MD5:— | SHA256:— | |||
| 2212 | MR.FESTUS ORIGIN RAWFILE.exe | C:\Users\admin\AppData\Local\Temp\06abc01b-dc19-4b74-9fae-ff4a2d07f58b | sqlite | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
16
DNS requests
14
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
352 | explorer.exe | GET | — | 50.63.202.54:80 | http://www.miamilakesholistictherapy.com/s0s/?ARrx=7dCGkfN753CqEzFOj0FfDmX1N0/cMErS+a4+kHTx2hMdMxVVJ39bszixn68ZZR7XP6KD9A==&kDql=uXTpgPWx5&sql=1 | US | — | — | malicious |
352 | explorer.exe | POST | — | 211.149.138.87:80 | http://www.scjiaoyuwang.com/s0s/ | CN | — | — | malicious |
352 | explorer.exe | GET | 302 | 217.160.0.78:80 | http://www.artecesped.com/s0s/?ARrx=eMsIqkcj+RKUgUnvoIUPYGpNeVFApfZ5mSk9YbkoCIJ/6D4s81Ls5gug0K7pMZCbTywDpQ==&kDql=uXTpgPWx5&sql=1 | DE | html | 204 b | malicious |
352 | explorer.exe | POST | — | 217.160.0.78:80 | http://www.artecesped.com/s0s/ | DE | — | — | malicious |
352 | explorer.exe | POST | — | 217.160.0.78:80 | http://www.artecesped.com/s0s/ | DE | — | — | malicious |
352 | explorer.exe | POST | — | 211.149.138.87:80 | http://www.scjiaoyuwang.com/s0s/ | CN | — | — | malicious |
352 | explorer.exe | POST | — | 211.149.138.87:80 | http://www.scjiaoyuwang.com/s0s/ | CN | — | — | malicious |
352 | explorer.exe | POST | — | 217.160.0.78:80 | http://www.artecesped.com/s0s/ | DE | — | — | malicious |
352 | explorer.exe | POST | — | 50.63.202.54:80 | http://www.miamilakesholistictherapy.com/s0s/ | US | — | — | malicious |
352 | explorer.exe | GET | 404 | 211.149.138.87:80 | http://www.scjiaoyuwang.com/s0s/?ARrx=oNLLEs6gns8/nYjFA2pfOarYeivZROzH5GNw9vN0cZ/upd8UgUyaMrBeFye05D3AS0SlQQ==&kDql=uXTpgPWx5&sql=1 | CN | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3932 | EQNEDT32.EXE | 162.144.128.116:80 | dubem.top | Unified Layer | US | malicious |
3624 | EQNEDT32.EXE | 162.144.128.116:80 | dubem.top | Unified Layer | US | malicious |
2212 | MR.FESTUS ORIGIN RAWFILE.exe | 208.91.198.143:587 | us2.smtp.mailhostbox.com | PDR | US | shared |
352 | explorer.exe | 198.54.112.75:80 | www.veroxin.com | Namecheap, Inc. | US | malicious |
352 | explorer.exe | 211.149.138.87:80 | www.scjiaoyuwang.com | CHINANET SiChuan Telecom Internet Data Center | CN | malicious |
— | — | 217.160.0.78:80 | www.artecesped.com | 1&1 Internet SE | DE | malicious |
352 | explorer.exe | 217.160.0.78:80 | www.artecesped.com | 1&1 Internet SE | DE | malicious |
352 | explorer.exe | 50.63.202.54:80 | www.miamilakesholistictherapy.com | GoDaddy.com, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dubem.top |
| unknown |
us2.smtp.mailhostbox.com |
| malicious |
www.wlgj66.com |
| unknown |
www.ibericoargentino.com |
| unknown |
www.www997789.com |
| unknown |
www.borespanda.com |
| unknown |
www.veroxin.com |
| malicious |
www.scjiaoyuwang.com |
| malicious |
www.simbascfans.com |
| unknown |
www.artecesped.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3624 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
3624 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3624 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3624 | EQNEDT32.EXE | Misc activity | ET INFO Possible EXE Download From Suspicious TLD |
2212 | MR.FESTUS ORIGIN RAWFILE.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
352 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
352 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
352 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
352 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
11 ETPRO signatures available at the full report