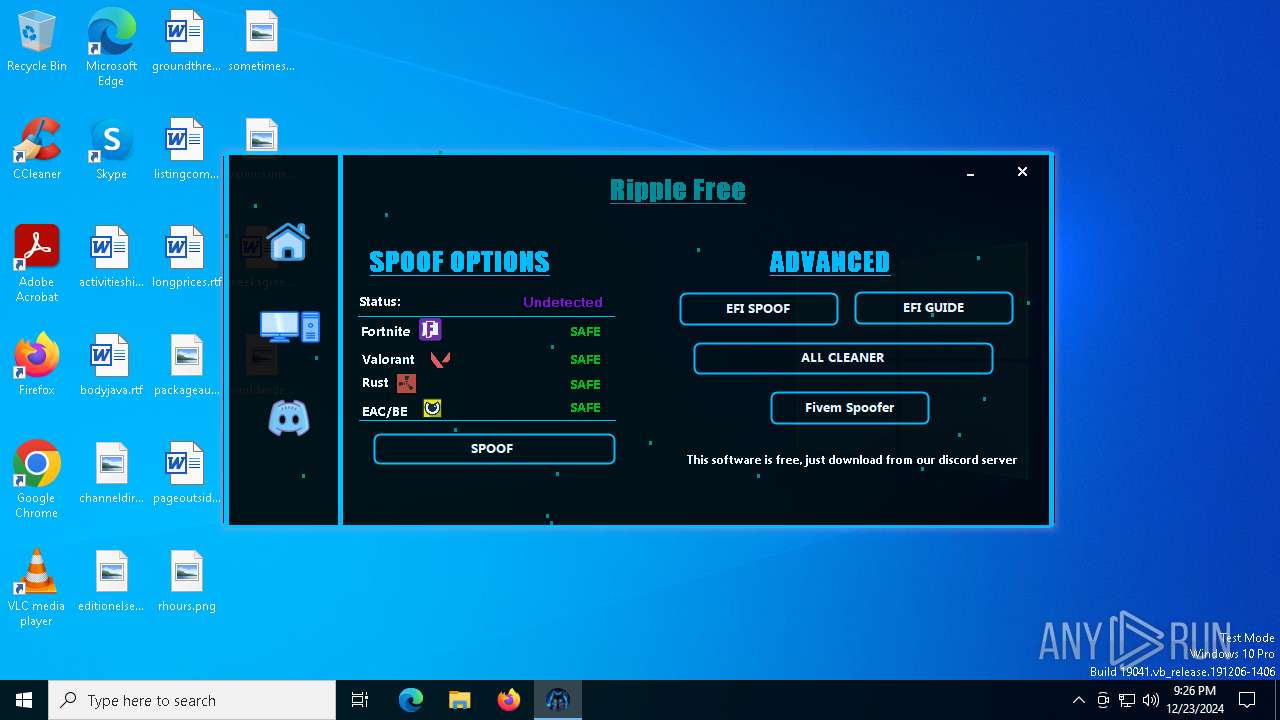
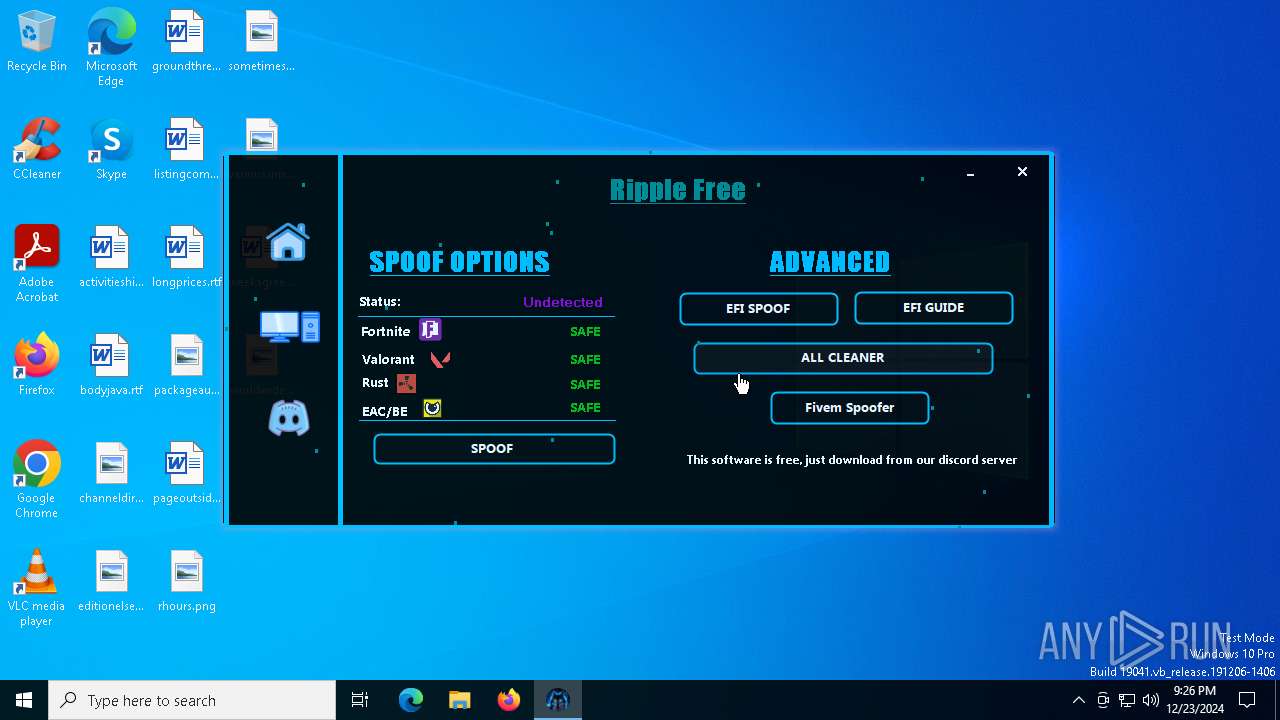
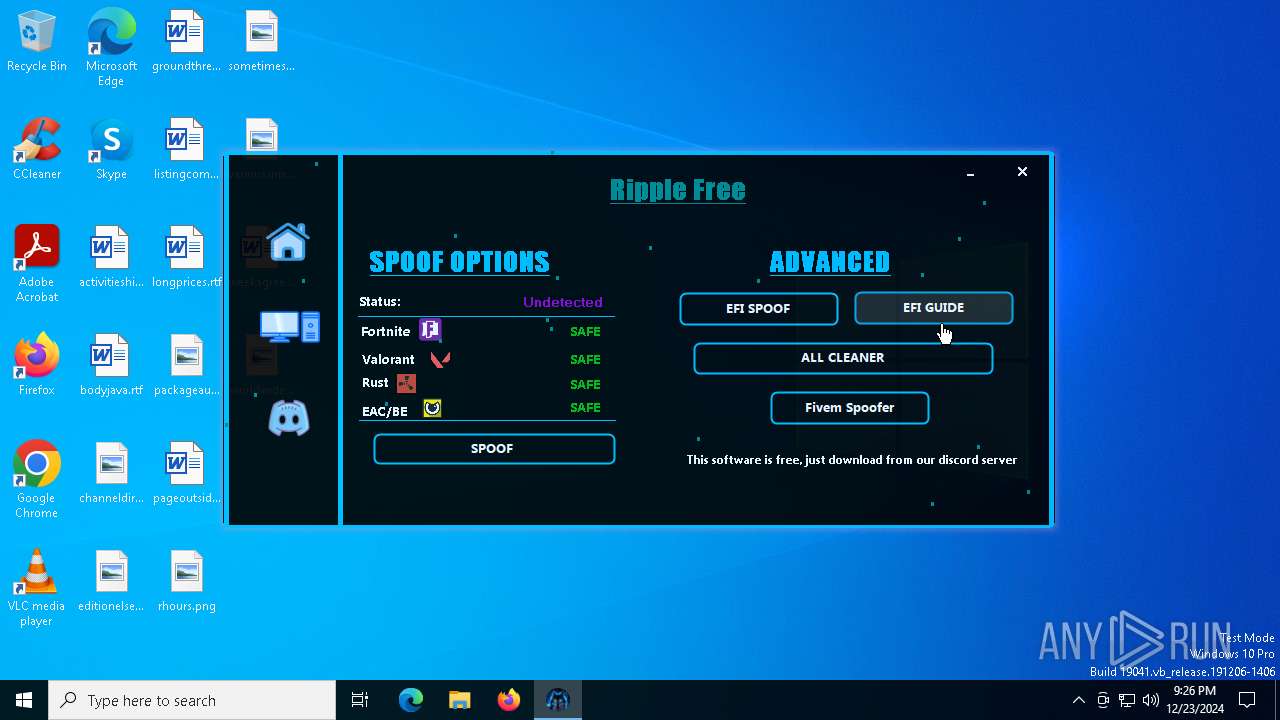
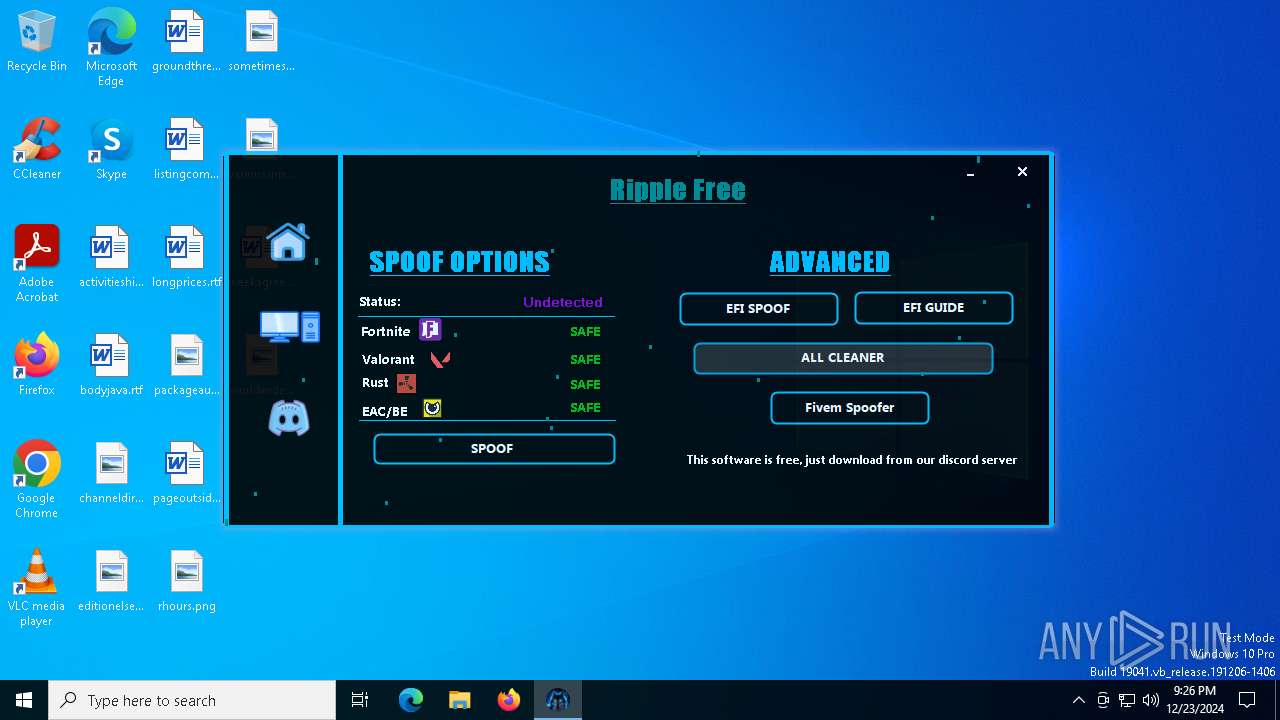
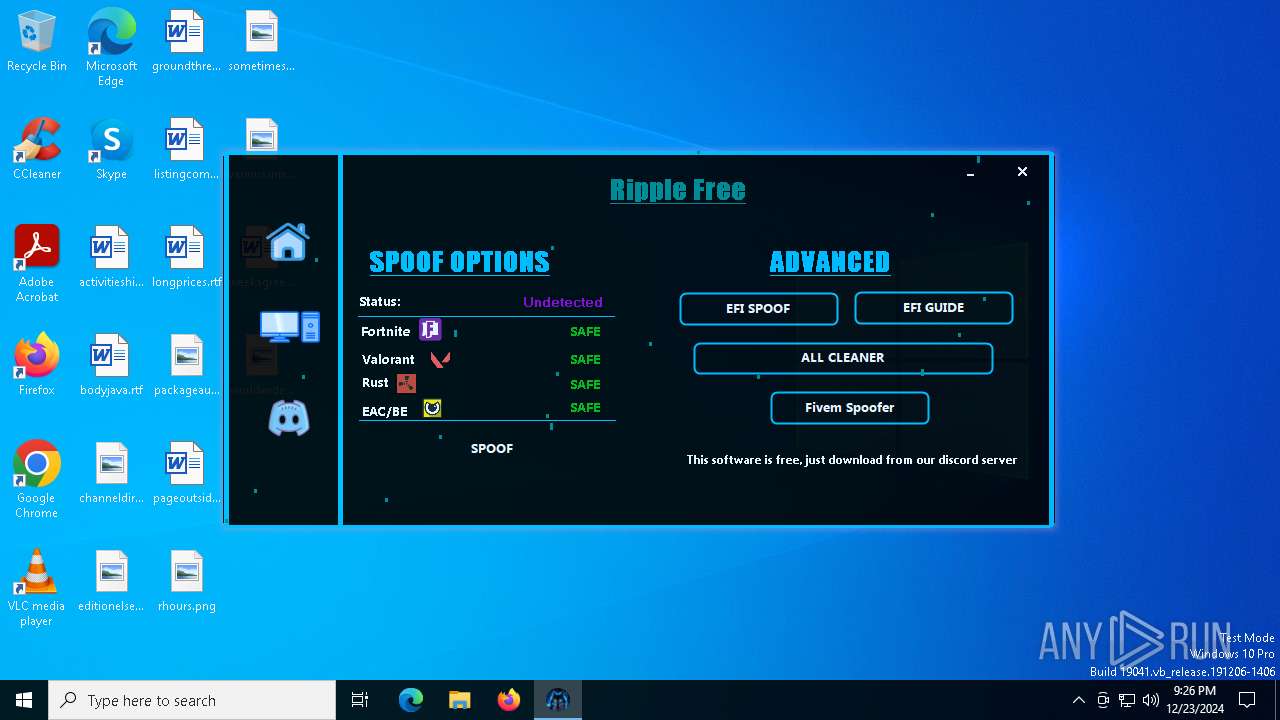
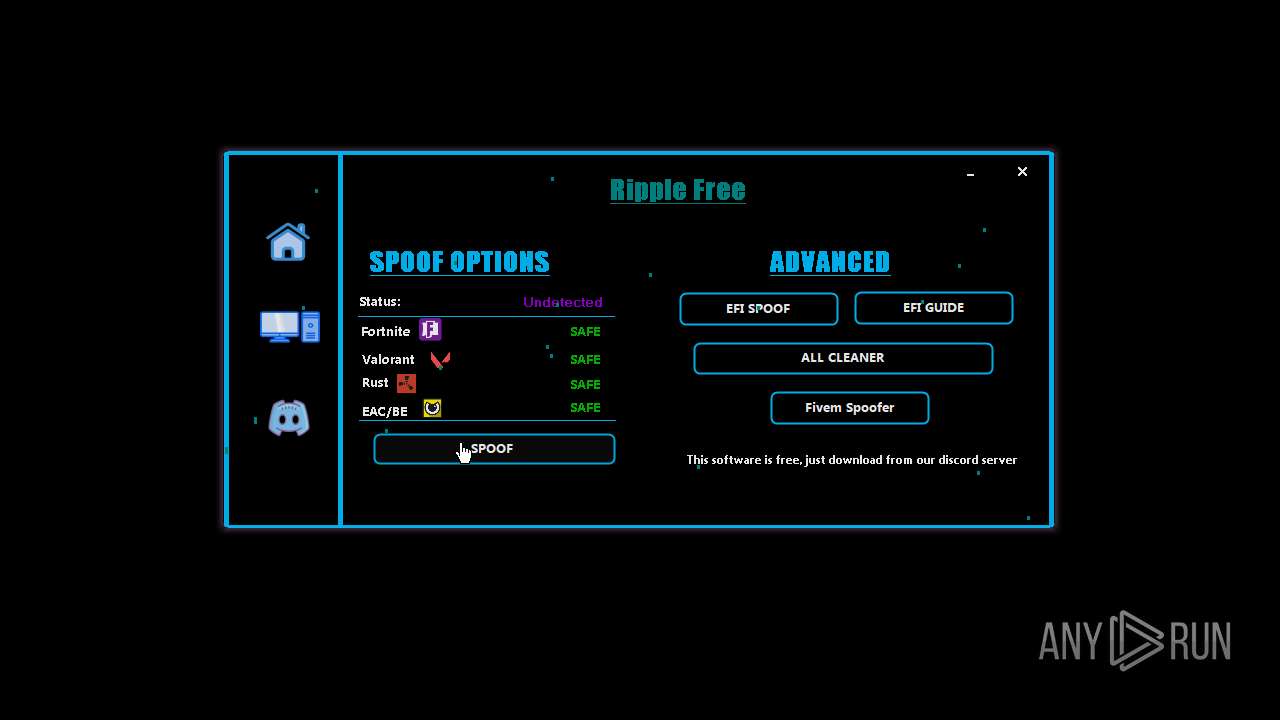
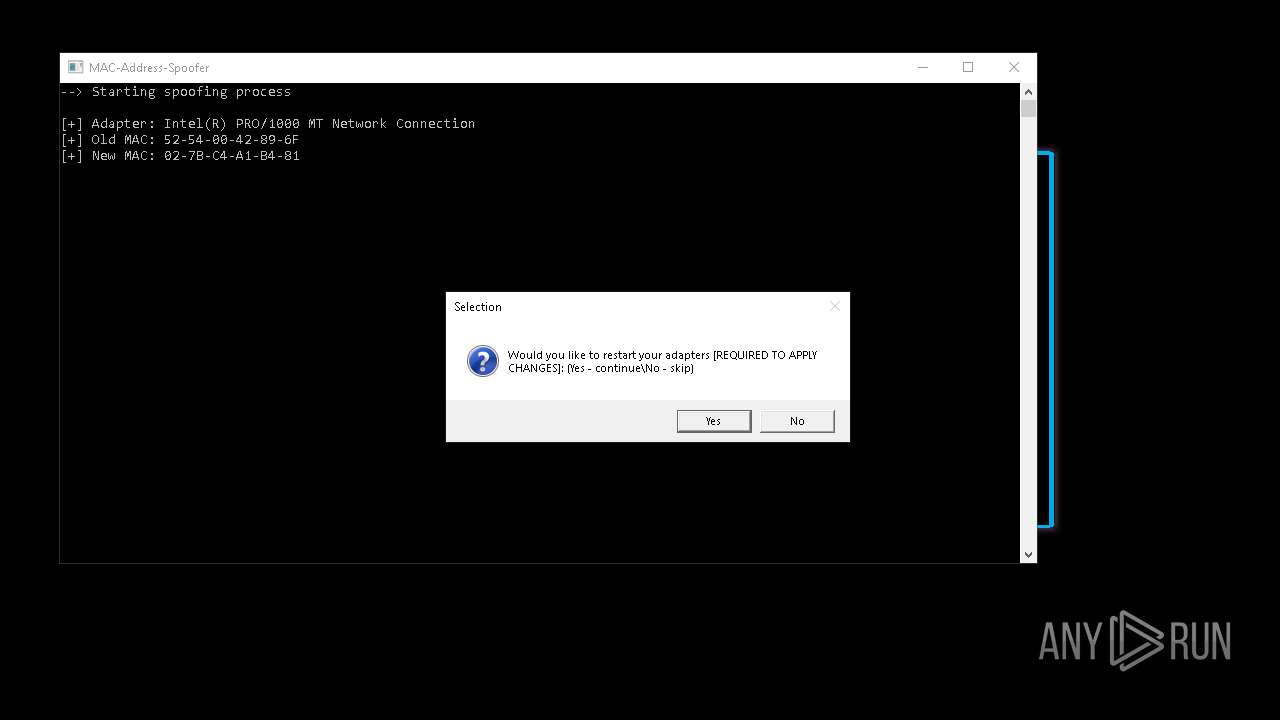
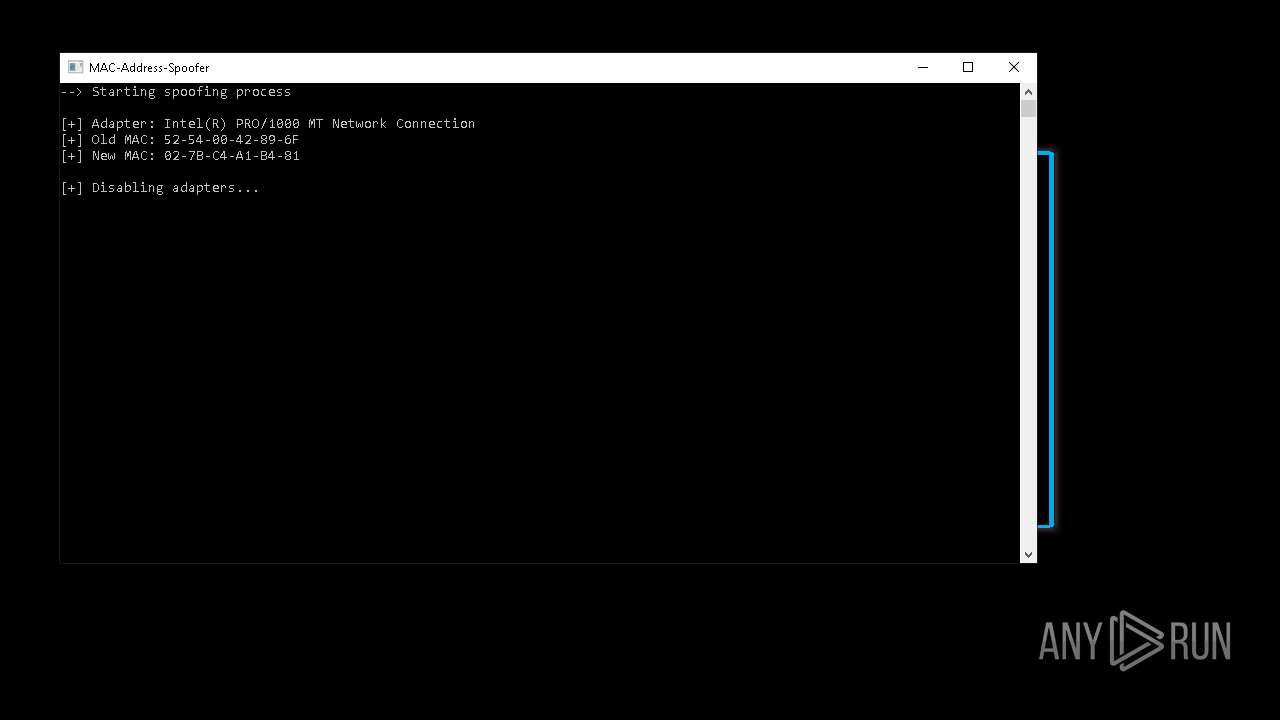
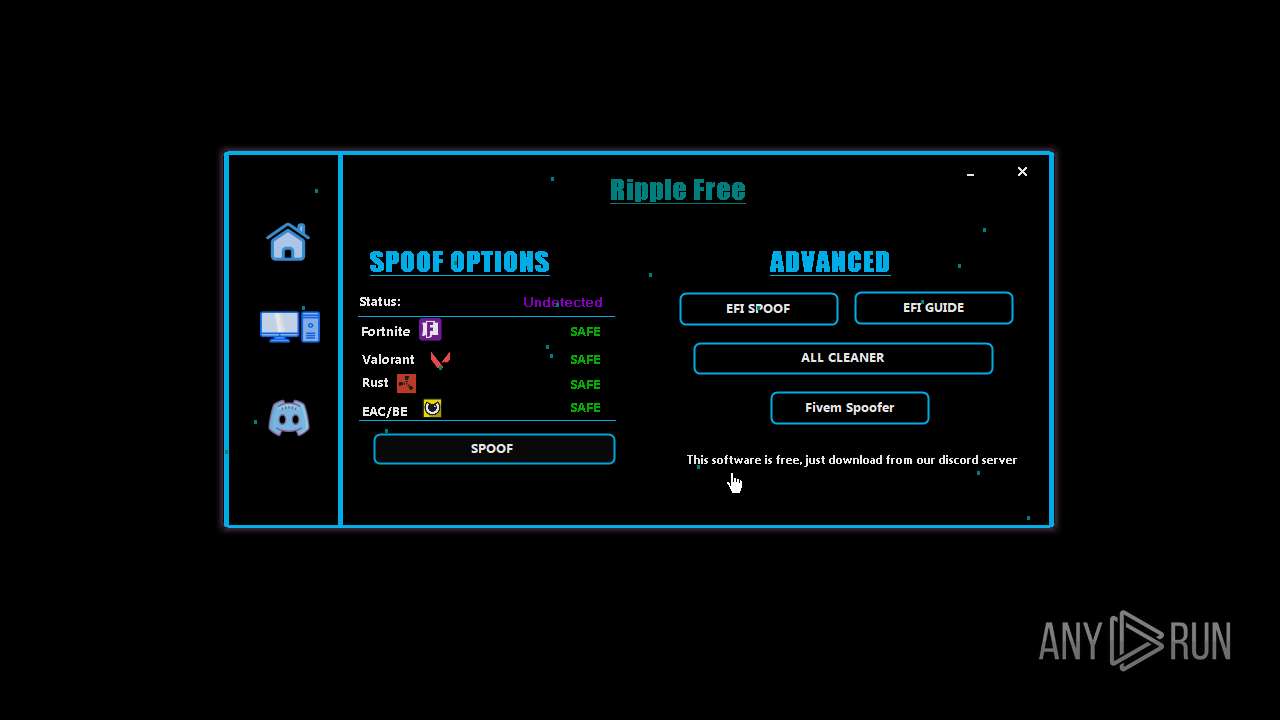
| File name: | RippleSpoofer.exe |
| Full analysis: | https://app.any.run/tasks/6ef1ffea-fd1a-4bbe-b62f-e2537e467782 |
| Verdict: | Malicious activity |
| Threats: | Exela Stealer is an infostealer malware written in Python. It is capable of collecting a wide range of sensitive information from compromised systems and exfiltrating it to attackers over Discord. It is frequently used to steal browser data, and obtain session files from various applications, including gaming platforms, social media platforms, and messaging apps. |
| Analysis date: | December 23, 2024, 21:26:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 76ED914A265F60FF93751AFE02CF35A4 |
| SHA1: | 4F8EA583E5999FAAEC38BE4C66FF4849FCF715C6 |
| SHA256: | 51BD245F8CB24C624674CD2BEBCAD4152D83273DAB4D1EE7D982E74A0548890B |
| SSDEEP: | 196608:nly0+XoaHUueZwDWjRByfuJ5CaHU3KUXQ6NAz:nIfooeZfvy6Ca03KUQz |
MALICIOUS
Steals credentials from Web Browsers
- mac.exe (PID: 2132)
Actions looks like stealing of personal data
- mac.exe (PID: 2132)
ExelaStealer has been detected
- mac.exe (PID: 2132)
Starts NET.EXE to view/add/change user profiles
- net.exe (PID: 6768)
- net.exe (PID: 6420)
- cmd.exe (PID: 6176)
- net.exe (PID: 2972)
Starts NET.EXE to view/change users localgroup
- net.exe (PID: 3832)
- net.exe (PID: 3640)
- cmd.exe (PID: 6176)
Bypass execution policy to execute commands
- powershell.exe (PID: 4832)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6956)
SUSPICIOUS
Executable content was dropped or overwritten
- RippleSpoofer.exe (PID: 6976)
- mac.exe (PID: 3700)
- mac.exe (PID: 2132)
- csc.exe (PID: 3140)
- randomizer.EXE (PID: 6824)
Drops a system driver (possible attempt to evade defenses)
- RippleSpoofer.exe (PID: 6976)
Process drops legitimate windows executable
- RippleSpoofer.exe (PID: 6976)
- mac.exe (PID: 3700)
- mac.exe (PID: 2132)
- randomizer.EXE (PID: 6824)
Uses TASKKILL.EXE to kill process
- RippleSpoofer.exe (PID: 6976)
Starts a Microsoft application from unusual location
- mac.exe (PID: 3700)
- mac.exe (PID: 2132)
Reads the BIOS version
- RippleSpoofer.exe (PID: 6976)
The process drops C-runtime libraries
- mac.exe (PID: 3700)
- randomizer.EXE (PID: 6824)
Process drops python dynamic module
- mac.exe (PID: 3700)
- randomizer.EXE (PID: 6824)
Application launched itself
- mac.exe (PID: 3700)
- cmd.exe (PID: 6368)
- cmd.exe (PID: 6464)
- randomizer.EXE (PID: 6824)
Starts CMD.EXE for commands execution
- mac.exe (PID: 2132)
- cmd.exe (PID: 6368)
- cmd.exe (PID: 6464)
- RippleSpoofer.exe (PID: 6976)
- 21902902190121290mc.exe (PID: 2996)
Get information on the list of running processes
- mac.exe (PID: 2132)
- cmd.exe (PID: 6804)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 6452)
- cmd.exe (PID: 6176)
There is functionality for taking screenshot (YARA)
- RippleSpoofer.exe (PID: 6976)
Loads Python modules
- mac.exe (PID: 2132)
- randomizer.EXE (PID: 6388)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 372)
- WMIC.exe (PID: 1668)
- WMIC.exe (PID: 6748)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6824)
- cmd.exe (PID: 4608)
- cmd.exe (PID: 6244)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3836)
Starts application with an unusual extension
- cmd.exe (PID: 396)
- cmd.exe (PID: 5000)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5096)
- cmd.exe (PID: 6956)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 6176)
Checks for external IP
- svchost.exe (PID: 2192)
- mac.exe (PID: 2132)
Uses WMIC.EXE to obtain local storage devices information
- cmd.exe (PID: 6176)
Uses QUSER.EXE to read information about current user sessions
- query.exe (PID: 1828)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 5352)
Uses WMIC.EXE to obtain commands that are run when users log in
- cmd.exe (PID: 6176)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 6176)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 6176)
Process uses ARP to discover network configuration
- cmd.exe (PID: 6176)
Starts SC.EXE for service management
- cmd.exe (PID: 6176)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6956)
Base64-obfuscated command line is found
- cmd.exe (PID: 6956)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3140)
Potential Corporate Privacy Violation
- RippleSpoofer.exe (PID: 6976)
Windows service management via SC.EXE
- sc.exe (PID: 5332)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 6176)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 6956)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 4832)
Hides command output
- cmd.exe (PID: 5544)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 6004)
Uses WMIC.EXE
- cmd.exe (PID: 5544)
- cmd.exe (PID: 5008)
The executable file from the user directory is run by the CMD process
- AMIDEWINx64.EXE (PID: 4624)
- AMIDEWINx64.EXE (PID: 4980)
- AMIDEWINx64.EXE (PID: 5892)
- AMIDEWINx64.EXE (PID: 5684)
- AMIDEWINx64.EXE (PID: 5872)
- AMIDEWINx64.EXE (PID: 6364)
- AMIDEWINx64.EXE (PID: 4852)
- AMIDEWINx64.EXE (PID: 4560)
- AMIDEWINx64.EXE (PID: 5836)
- AMIDEWINx64.EXE (PID: 5220)
- AMIDEWINx64.EXE (PID: 1228)
- AMIDEWINx64.EXE (PID: 2324)
- AMIDEWINx64.EXE (PID: 4776)
- AMIDEWINx64.EXE (PID: 6676)
- AMIDEWINx64.EXE (PID: 6736)
- AMIDEWINx64.EXE (PID: 2216)
- AMIDEWINx64.EXE (PID: 6168)
- AMIDEWINx64.EXE (PID: 1140)
- AMIDEWINx64.EXE (PID: 5964)
- AMIDEWINx64.EXE (PID: 6012)
- AMIDEWINx64.EXE (PID: 6828)
- AMIDEWINx64.EXE (PID: 6752)
- AMIDEWINx64.EXE (PID: 5240)
- AMIDEWINx64.EXE (PID: 5404)
- AMIDEWINx64.EXE (PID: 2548)
- AMIDEWINx64.EXE (PID: 1620)
- AMIDEWINx64.EXE (PID: 2828)
- AMIDEWINx64.EXE (PID: 4928)
- AMIDEWINx64.EXE (PID: 6756)
- AMIDEWINx64.EXE (PID: 5104)
- AMIDEWINx64.EXE (PID: 5152)
- AMIDEWINx64.EXE (PID: 5416)
- AMIDEWINx64.EXE (PID: 5596)
- AMIDEWINx64.EXE (PID: 5960)
- AMIDEWINx64.EXE (PID: 4668)
- AMIDEWINx64.EXE (PID: 4136)
- AMIDEWINx64.EXE (PID: 6808)
- AMIDEWINx64.EXE (PID: 3176)
- AMIDEWINx64.EXE (PID: 6312)
- AMIDEWINx64.EXE (PID: 4536)
- AMIDEWINx64.EXE (PID: 7116)
Executing commands from a ".bat" file
- RippleSpoofer.exe (PID: 6976)
Reads the date of Windows installation
- RippleSpoofer.exe (PID: 6976)
Reads security settings of Internet Explorer
- RippleSpoofer.exe (PID: 6976)
The system shut down or reboot
- RippleSpoofer.exe (PID: 6976)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2992)
INFO
Process checks whether UAC notifications are on
- RippleSpoofer.exe (PID: 6976)
Create files in a temporary directory
- RippleSpoofer.exe (PID: 6976)
- mac.exe (PID: 3700)
- mac.exe (PID: 2132)
- randomizer.EXE (PID: 6388)
- cvtres.exe (PID: 4756)
- csc.exe (PID: 3140)
- randomizer.EXE (PID: 6824)
The sample compiled with english language support
- RippleSpoofer.exe (PID: 6976)
- mac.exe (PID: 3700)
- mac.exe (PID: 2132)
- randomizer.EXE (PID: 6824)
Checks supported languages
- mac.exe (PID: 3700)
- RippleSpoofer.exe (PID: 6976)
- mac.exe (PID: 2132)
- chcp.com (PID: 4264)
- chcp.com (PID: 1448)
- csc.exe (PID: 3140)
- cvtres.exe (PID: 4756)
- randomizer.EXE (PID: 6388)
- randomizer.EXE (PID: 6824)
- AMIDEWINx64.EXE (PID: 5892)
- AMIDEWINx64.EXE (PID: 4980)
- AMIDEWINx64.EXE (PID: 4624)
- 21902902190121290mc.exe (PID: 2996)
- AMIDEWINx64.EXE (PID: 5872)
- AMIDEWINx64.EXE (PID: 4852)
- AMIDEWINx64.EXE (PID: 2324)
- AMIDEWINx64.EXE (PID: 5220)
- AMIDEWINx64.EXE (PID: 6364)
- AMIDEWINx64.EXE (PID: 1228)
- AMIDEWINx64.EXE (PID: 4776)
- AMIDEWINx64.EXE (PID: 2216)
- AMIDEWINx64.EXE (PID: 6168)
- AMIDEWINx64.EXE (PID: 1140)
- AMIDEWINx64.EXE (PID: 6676)
- AMIDEWINx64.EXE (PID: 6736)
- AMIDEWINx64.EXE (PID: 6828)
- AMIDEWINx64.EXE (PID: 6012)
- AMIDEWINx64.EXE (PID: 5404)
- AMIDEWINx64.EXE (PID: 6752)
- AMIDEWINx64.EXE (PID: 2828)
- AMIDEWINx64.EXE (PID: 4928)
- AMIDEWINx64.EXE (PID: 5152)
- AMIDEWINx64.EXE (PID: 5104)
- AMIDEWINx64.EXE (PID: 5596)
- AMIDEWINx64.EXE (PID: 1620)
- AMIDEWINx64.EXE (PID: 6756)
- AMIDEWINx64.EXE (PID: 4668)
- AMIDEWINx64.EXE (PID: 6312)
- AMIDEWINx64.EXE (PID: 4536)
- AMIDEWINx64.EXE (PID: 4136)
- AMIDEWINx64.EXE (PID: 6808)
- AMIDEWINx64.EXE (PID: 3176)
- AMIDEWINx64.EXE (PID: 7116)
- volumeid.EXE (PID: 4264)
- volumeid64.EXE (PID: 3488)
- PLUGScheduler.exe (PID: 2992)
- SearchApp.exe (PID: 4052)
- SearchApp.exe (PID: 5104)
Reads the computer name
- mac.exe (PID: 3700)
- RippleSpoofer.exe (PID: 6976)
- mac.exe (PID: 2132)
- randomizer.EXE (PID: 6824)
- 21902902190121290mc.exe (PID: 2996)
- AMIDEWINx64.EXE (PID: 4980)
- AMIDEWINx64.EXE (PID: 4624)
- AMIDEWINx64.EXE (PID: 5892)
- AMIDEWINx64.EXE (PID: 5872)
- AMIDEWINx64.EXE (PID: 2324)
- AMIDEWINx64.EXE (PID: 6364)
- AMIDEWINx64.EXE (PID: 5220)
- AMIDEWINx64.EXE (PID: 5684)
- AMIDEWINx64.EXE (PID: 1228)
- AMIDEWINx64.EXE (PID: 4776)
- AMIDEWINx64.EXE (PID: 2216)
- AMIDEWINx64.EXE (PID: 6676)
- AMIDEWINx64.EXE (PID: 6168)
- AMIDEWINx64.EXE (PID: 6012)
- AMIDEWINx64.EXE (PID: 6752)
- AMIDEWINx64.EXE (PID: 5404)
- AMIDEWINx64.EXE (PID: 2828)
- AMIDEWINx64.EXE (PID: 6736)
- AMIDEWINx64.EXE (PID: 6828)
- AMIDEWINx64.EXE (PID: 1620)
- AMIDEWINx64.EXE (PID: 4928)
- AMIDEWINx64.EXE (PID: 5152)
- AMIDEWINx64.EXE (PID: 6756)
- AMIDEWINx64.EXE (PID: 5416)
- AMIDEWINx64.EXE (PID: 4668)
- AMIDEWINx64.EXE (PID: 6312)
- AMIDEWINx64.EXE (PID: 4136)
- AMIDEWINx64.EXE (PID: 4536)
- AMIDEWINx64.EXE (PID: 6808)
- AMIDEWINx64.EXE (PID: 5960)
- AMIDEWINx64.EXE (PID: 3176)
- PLUGScheduler.exe (PID: 2992)
- AMIDEWINx64.EXE (PID: 7116)
- volumeid.EXE (PID: 4264)
Themida protector has been detected
- RippleSpoofer.exe (PID: 6976)
Checks operating system version
- mac.exe (PID: 2132)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 372)
- WMIC.exe (PID: 6736)
- WMIC.exe (PID: 1476)
- WMIC.exe (PID: 1668)
- WMIC.exe (PID: 6748)
- WMIC.exe (PID: 5988)
- WMIC.exe (PID: 4840)
Creates files or folders in the user directory
- mac.exe (PID: 2132)
Changes the display of characters in the console
- cmd.exe (PID: 396)
- cmd.exe (PID: 5000)
The Powershell gets current clipboard
- powershell.exe (PID: 5992)
Reads the time zone
- net1.exe (PID: 1144)
- net1.exe (PID: 5740)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 5256)
Reads the machine GUID from the registry
- RippleSpoofer.exe (PID: 6976)
- csc.exe (PID: 3140)
- randomizer.EXE (PID: 6388)
- SearchApp.exe (PID: 5104)
Reads the software policy settings
- RippleSpoofer.exe (PID: 6976)
- SearchApp.exe (PID: 5104)
Reads Environment values
- RippleSpoofer.exe (PID: 6976)
- SearchApp.exe (PID: 5104)
Checks proxy server information
- RippleSpoofer.exe (PID: 6976)
Disables trace logs
- RippleSpoofer.exe (PID: 6976)
Process checks computer location settings
- RippleSpoofer.exe (PID: 6976)
- SearchApp.exe (PID: 5104)
Application launched itself
- firefox.exe (PID: 3656)
- firefox.exe (PID: 3972)
Manual execution by a user
- RippleSpoofer.exe (PID: 7808)
- RippleSpoofer.exe (PID: 756)
- firefox.exe (PID: 3656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:03 21:34:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 6075904 |
| InitializedDataSize: | 9216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x187a058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Ripple Free Spoofer |
| CompanyName: | Ripple |
| FileDescription: | RippleFree |
| FileVersion: | 1.0.0.0 |
| InternalName: | RippleSpoofer.exe |
| LegalCopyright: | Ripple |
| LegalTrademarks: | Ripple |
| OriginalFileName: | RippleSpoofer.exe |
| ProductName: | Ripple |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
431
Monitored processes
151
Malicious processes
7
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | cmd.exe /c chcp | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 756 | "C:\Users\admin\AppData\Local\Temp\RippleSpoofer.exe" | C:\Users\admin\AppData\Local\Temp\RippleSpoofer.exe | explorer.exe | ||||||||||||
User: admin Company: Ripple Integrity Level: HIGH Description: RippleFree Version: 1.0.0.0 Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | tasklist /FO LIST | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 932 | "taskkill" /F /IM explorer.exe | C:\Windows\System32\taskkill.exe | — | RippleSpoofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | AMIDEWINx64.EXE /PSN qqylT23f8XxdkA2 | C:\Users\admin\AppData\Local\Temp\TempAppFiles\AMIDEWINx64.EXE | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 224 Modules
| |||||||||||||||
| 1144 | C:\WINDOWS\system32\net1 user administrator | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | AMIDEWINx64.EXE /CV dt7beU3EvjYB7be | C:\Users\admin\AppData\Local\Temp\TempAppFiles\AMIDEWINx64.EXE | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 224 Modules
| |||||||||||||||
| 1448 | chcp | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
59 433
Read events
59 220
Write events
206
Delete events
7
Modification events
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6976) RippleSpoofer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RippleSpoofer_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
56
Suspicious files
280
Text files
342
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\hardware_info.txt | text | |
MD5:3BC5174896118FF3C0DA6FABB75E2CB1 | SHA256:FEE9EEC5FDB69A27C1F57F5886E4A80070EE1AD234124DB4D21473B30FA1D311 | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\TempAppFiles\spoof.bat | text | |
MD5:596866DC4485091A5F124F2809E9BE67 | SHA256:AB3993B6D78B0DFAD3A288D7EDB6D04F7580AAC6702AF3BD6BD2CF9F4F91D8AA | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\TempAppFiles\randomizer.EXE | executable | |
MD5:6E4421D0C8E459B2B378EA968510182E | SHA256:63534BF58D0657AEE6DEF9711BD75310FC58724BDA6200F34A11DF0DE9F49F96 | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\TempAppFiles\amigendrv64.sys | executable | |
MD5:9ACCEBD928A8926FECF317F53CD1C44E | SHA256:811E5D65DF60DFB8C6E1713DA708BE16D9A13EF8DFCD1022D8D1DDA52ED057B2 | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\TempAppFiles\21902902190121290mc.exe | executable | |
MD5:FEA8C89F2D44E44834728203CF395267 | SHA256:2D70CFC13468820F22F5FDA01B0A74EA6BD904EFD6918899D6C9C7D4EF39C293 | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\tmp7B9C.tmp.mp3 | binary | |
MD5:244CC3A6C2FABF8A05CF40C3BEA324E0 | SHA256:7C61C3EF11AD80C2941EAD551179F02D6CBD472AD53DC613708313F0E7B9171A | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\TempAppFiles\volumeid64.EXE | executable | |
MD5:81A45F1A91448313B76D2E6D5308AA7A | SHA256:FB0D02EA26BB1E5DF5A07147931CAF1AE3D7D1D9B4D83F168B678E7F3A1C0ECD | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\TempAppFiles\amifldrv64.sys | executable | |
MD5:785045F8B25CD2E937DDC6B09DEBE01A | SHA256:37073E42FFA0322500F90CD7E3C8D02C4CDD695D31C77E81560ABEC20BFB68BA | |||
| 3700 | mac.exe | C:\Users\admin\AppData\Local\Temp\_MEI37002\_hashlib.pyd | executable | |
MD5:0629BDB5FF24CE5E88A2DDCEDE608AEE | SHA256:F404BB8371618BBD782201F092A3BCD7A96D3C143787EBEA1D8D86DED1F4B3B8 | |||
| 6976 | RippleSpoofer.exe | C:\Users\admin\AppData\Local\Temp\TempAppFiles\volumeid.EXE | executable | |
MD5:4D867033B27C8A603DE4885B449C4923 | SHA256:22A2484D7FA799E6E71E310141614884F3BC8DAD8AC749B6F1C475B5398A72F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
128
DNS requests
131
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6532 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2132 | mac.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | shared |
6644 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6644 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4988 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3972 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.dropbox.com |
| shared |
uc17fb25a19ebce81bee2da7a679.dl.dropboxusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6976 | RippleSpoofer.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2132 | mac.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2192 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2132 | mac.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2132 | mac.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |