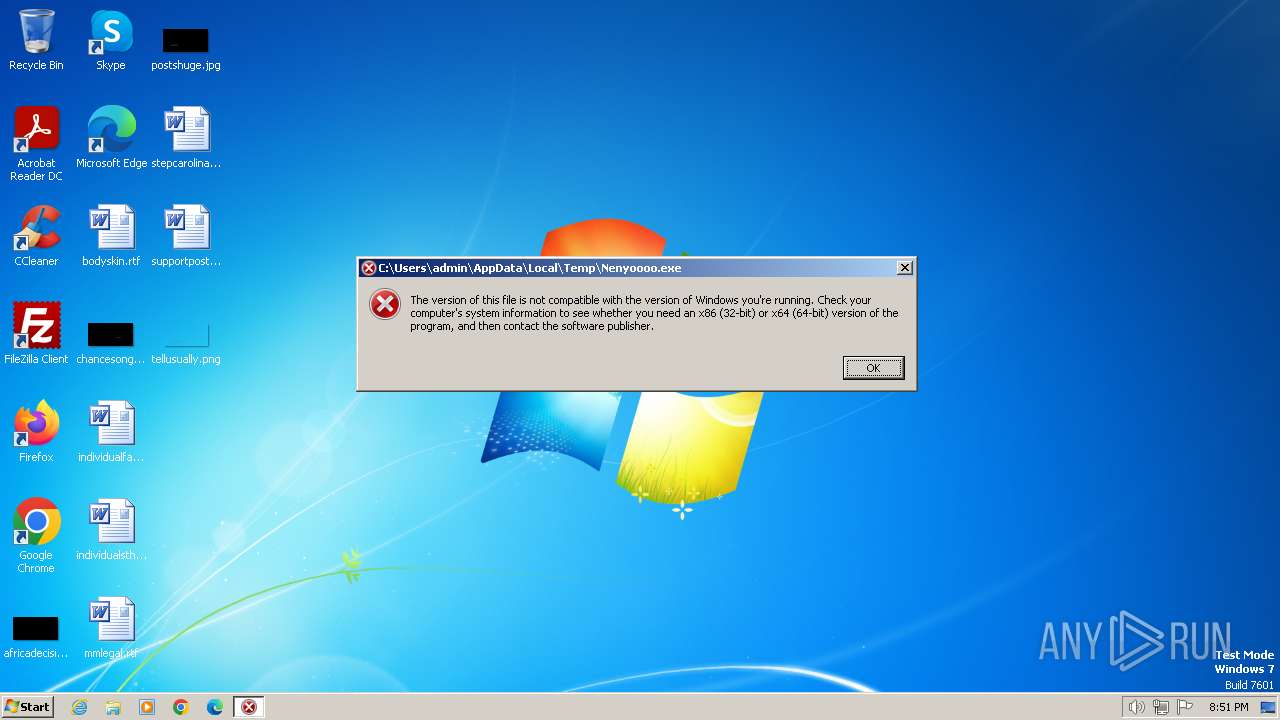
| File name: | Nenyooo v1.0.3028.0.7.exe |
| Full analysis: | https://app.any.run/tasks/614345d5-4981-45f8-aaa8-24b51a625c8f |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | December 23, 2023, 20:51:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B5FA4B00D245D0DFF8C680CC04A71695 |
| SHA1: | 6A95A30CE75E67CCE5E96EBD1D6AF67D5C8888C9 |
| SHA256: | 516719608B05FA6F962E398A14171299E93044ECCFB9B8A5B27B8F9C22DECB62 |
| SSDEEP: | 98304:GV9UupqC82lAMbeqJIDECRDbVY1yDojT9MY+BhtUR72ezmhEYarOvNuDSZnh8j/2:xCOhboHCV0L+1RkgbBLSghIDjTU+ng |
MALICIOUS
Changes the autorun value in the registry
- Nenyooo.exe (PID: 2076)
QUASAR has been detected (YARA)
- Nenyooo.exe (PID: 2076)
SUSPICIOUS
Reads the Internet Settings
- Nenyooo v1.0.3028.0.7.exe (PID: 2040)
INFO
Drops the executable file immediately after the start
- Nenyooo v1.0.3028.0.7.exe (PID: 2040)
- Nenyooo.exe (PID: 1056)
Reads the computer name
- Nenyooo v1.0.3028.0.7.exe (PID: 2040)
- Nenyooo.exe (PID: 1056)
- Nenyooo.exe (PID: 2076)
Reads the machine GUID from the registry
- Nenyooo.exe (PID: 1056)
- Nenyooo.exe (PID: 2076)
Checks supported languages
- Nenyooo v1.0.3028.0.7.exe (PID: 2040)
- Nenyooo.exe (PID: 1056)
- Nenyooo.exe (PID: 2076)
Create files in a temporary directory
- Nenyooo v1.0.3028.0.7.exe (PID: 2040)
Starts itself from another location
- Nenyooo.exe (PID: 1056)
Reads Environment values
- Nenyooo.exe (PID: 1056)
- Nenyooo.exe (PID: 2076)
Creates files or folders in the user directory
- Nenyooo.exe (PID: 1056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(2076) Nenyooo.exe
Version1.4.1
C2 (2)192.168.0.9:5780
Sub_DirSubDir
Install_NameNenyooo.exe
Mutexcc34d9ab-4056-4e30-a27b-b51b22332f28
StartupNenyooo
TagSneaky
LogDirLogs
SignatureMZ/ZPP0WBL32b9L41ybjUiTdhjObOQuCSMyWcSjXNBDm3nQicgJorBvefsExn0ZG/qqxfb62DQxephnHZ5j2KLrygCvI58slAMCYFiDJ9FJCPMgPWxOY1nXx+wsbEESzixC/CJYMIeqLMwbfFet9EBs7X6VtxqrsO3eFLocppt+bsluEcUygY0bNDc+CZ9sdTn+uK9Bi5U1cMdKBa31zV+9Nki6bB3HdqLrHW8VFZthAzSneZWohu9XnU6youPCGQEhVHhoeIqMySoC1GakaVZDodwfDeKL7VsSazOTnqZ2p...
CertificateMIIE9DCCAtygAwIBAgIQAMf3tQSo5UTYOEXiezkpTTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMTIyMTIwMjI1MloYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAnwy+9hSav4OxsbqwjP3xsrTk1JxJSUIxySu91GLGRKvX9viXam5lCJr1EXcw8wRGikyadkSB...
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:01 11:26:10+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 208384 |
| InitializedDataSize: | 189440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20790 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
35
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | "C:\Users\admin\AppData\Local\Temp\Nenyooo.exe" | C:\Users\admin\AppData\Local\Temp\Nenyooo.exe | — | Nenyooo v1.0.3028.0.7.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 3 Version: 1.4.1 Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\Nenyooo v1.0.3028.0.7.exe" | C:\Users\admin\AppData\Local\Temp\Nenyooo v1.0.3028.0.7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\AppData\Roaming\SubDir\Nenyooo.exe" | C:\Users\admin\AppData\Roaming\SubDir\Nenyooo.exe | Nenyooo.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 0 Version: 1.4.1 Modules
Quasar(PID) Process(2076) Nenyooo.exe Version1.4.1 C2 (2)192.168.0.9:5780 Sub_DirSubDir Install_NameNenyooo.exe Mutexcc34d9ab-4056-4e30-a27b-b51b22332f28 StartupNenyooo TagSneaky LogDirLogs SignatureMZ/ZPP0WBL32b9L41ybjUiTdhjObOQuCSMyWcSjXNBDm3nQicgJorBvefsExn0ZG/qqxfb62DQxephnHZ5j2KLrygCvI58slAMCYFiDJ9FJCPMgPWxOY1nXx+wsbEESzixC/CJYMIeqLMwbfFet9EBs7X6VtxqrsO3eFLocppt+bsluEcUygY0bNDc+CZ9sdTn+uK9Bi5U1cMdKBa31zV+9Nki6bB3HdqLrHW8VFZthAzSneZWohu9XnU6youPCGQEhVHhoeIqMySoC1GakaVZDodwfDeKL7VsSazOTnqZ2p... CertificateMIIE9DCCAtygAwIBAgIQAMf3tQSo5UTYOEXiezkpTTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMTIyMTIwMjI1MloYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAnwy+9hSav4OxsbqwjP3xsrTk1JxJSUIxySu91GLGRKvX9viXam5lCJr1EXcw8wRGikyadkSB... | |||||||||||||||
Total events
1 293
Read events
1 256
Write events
37
Delete events
0
Modification events
| (PID) Process: | (2040) Nenyooo v1.0.3028.0.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) Nenyooo v1.0.3028.0.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) Nenyooo v1.0.3028.0.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) Nenyooo v1.0.3028.0.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1056) Nenyooo.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2076) Nenyooo.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2076) Nenyooo.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Nenyooo |
Value: "C:\Users\admin\AppData\Roaming\SubDir\Nenyooo.exe" | |||
Executable files
3
Suspicious files
3
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\Extra\Vehicle\XML\Spinethetic-HamburgersRevenge.xml | xml | |
MD5:2C47A42E9F72D0FB34DD900C7262A9CE | SHA256:7FBBBF30A4F5B2FF143A3D463C82D913A7BBAD31EA5B030E22F122E927E416FA | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\Extra\Vehicle\XML\Spinethetic-XmasSleighBoat.xml | xml | |
MD5:3253820C216399F27C99D87EDB7F570E | SHA256:E0F3FBD6066BD16DE849DB6A510DEBAAFA4791B2A994810F99914D9C5CE1A141 | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\Extra\Vehicle\XML\Spinethetic-ZombieSabreGT.xml | xml | |
MD5:338B29F194B2C45F867BBB15AD5F8ADE | SHA256:60E5297772148DB56F9E9260227988CA90452145D5D88CEBFE7EB81B1FC849EC | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\Extra\Vehicle\All_Vehicle.ini | text | |
MD5:CCAB2A5C67F52F2762CF9F38045AA185 | SHA256:B18E18245DE7B9CA4F234B9E48492FB116FAF19C2EB65365047C8DFFA2E47BFA | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\Extra\Maps\Upside_Down_World.xml | xml | |
MD5:9F80B6869101D36970385C105F7B972B | SHA256:0E33381722A907DD166511F11BC46209D5B23FC881B4E96F82F664E6183CDFA0 | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\User Interface\Textures\Header.gif | image | |
MD5:319241870A5CD9B3702681F240A3AD50 | SHA256:ADDC49E4C0DAB10182A74175CF68CBAEE9337C6F2D800A07C4EC24358FF94D9F | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\Extra\Maps\Aerial_Islands.xml | xml | |
MD5:0BF237E9D12C53F63296A553048CBF07 | SHA256:54005C1F5B8F94C52A335D5335AE0ADCAE532DFD30083566ADF34EB1A5F36348 | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\Extra\Appearance\Barbie Barb.xml | xml | |
MD5:BF5B3C75607A0218010A97798EDB8714 | SHA256:DA95769EEA117588A95888FD7E189BCD000C050D843CD13611DBBCC5030ED809 | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\User Interface\Audio\Xmas.wav | binary | |
MD5:1E2BD472C41FF2590C9346826285162F | SHA256:379BF9206E8F3A50969F5290F5472EA87747B067B410C29AC6B5D137F3F7B808 | |||
| 2040 | Nenyooo v1.0.3028.0.7.exe | C:\Users\admin\AppData\Local\Temp\Nenyooo\User Interface\Fonts\Options.ttf | ttf | |
MD5:E671580DAC468CBC7E4AE3B5A5720842 | SHA256:3348F57B874451E5AFA158ECEF7F1376887A4218C9A0CBE545A1DDAD7EDA4FC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 192.168.100.40:49165 | — | — | — | unknown |
— | — | 192.168.100.40:49166 | — | — | — | unknown |