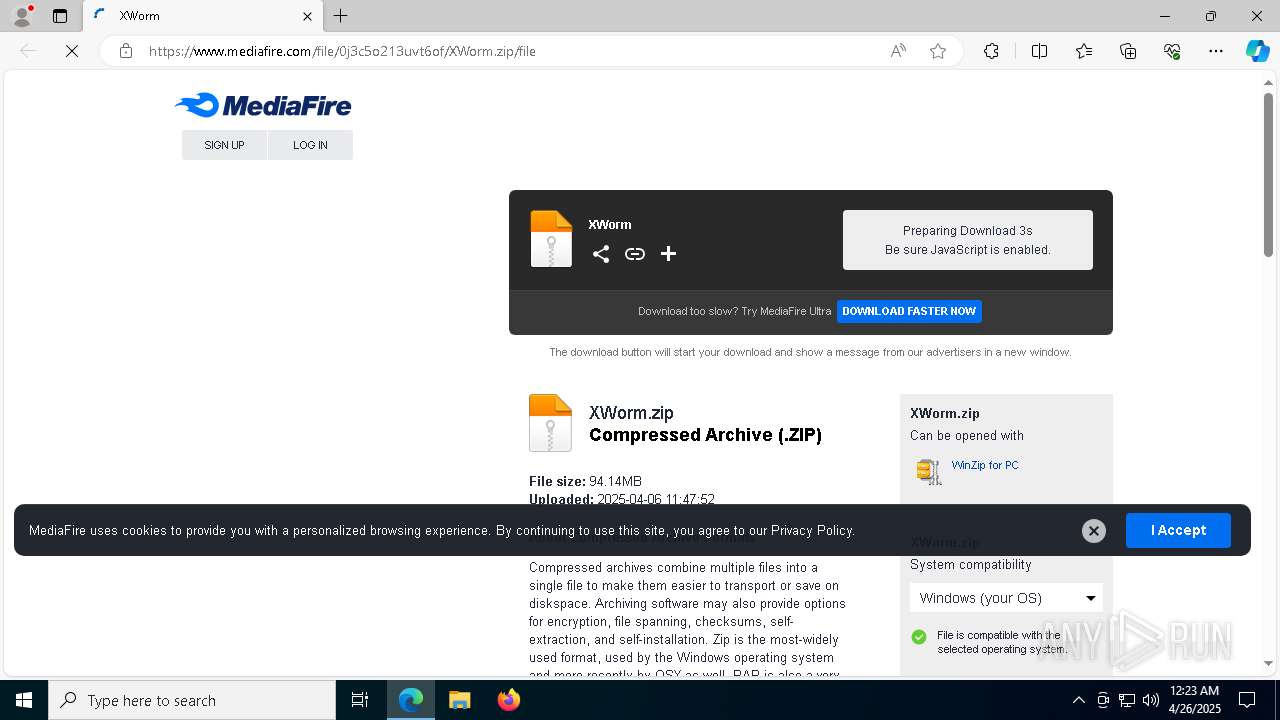
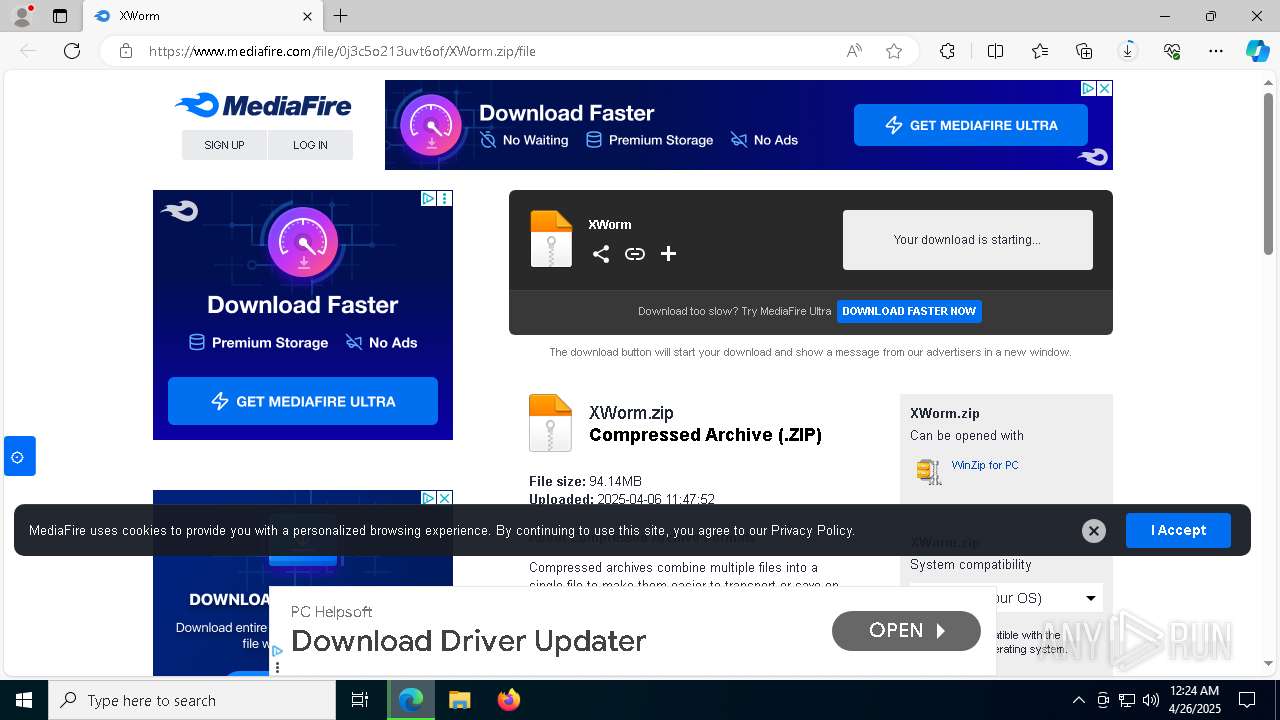
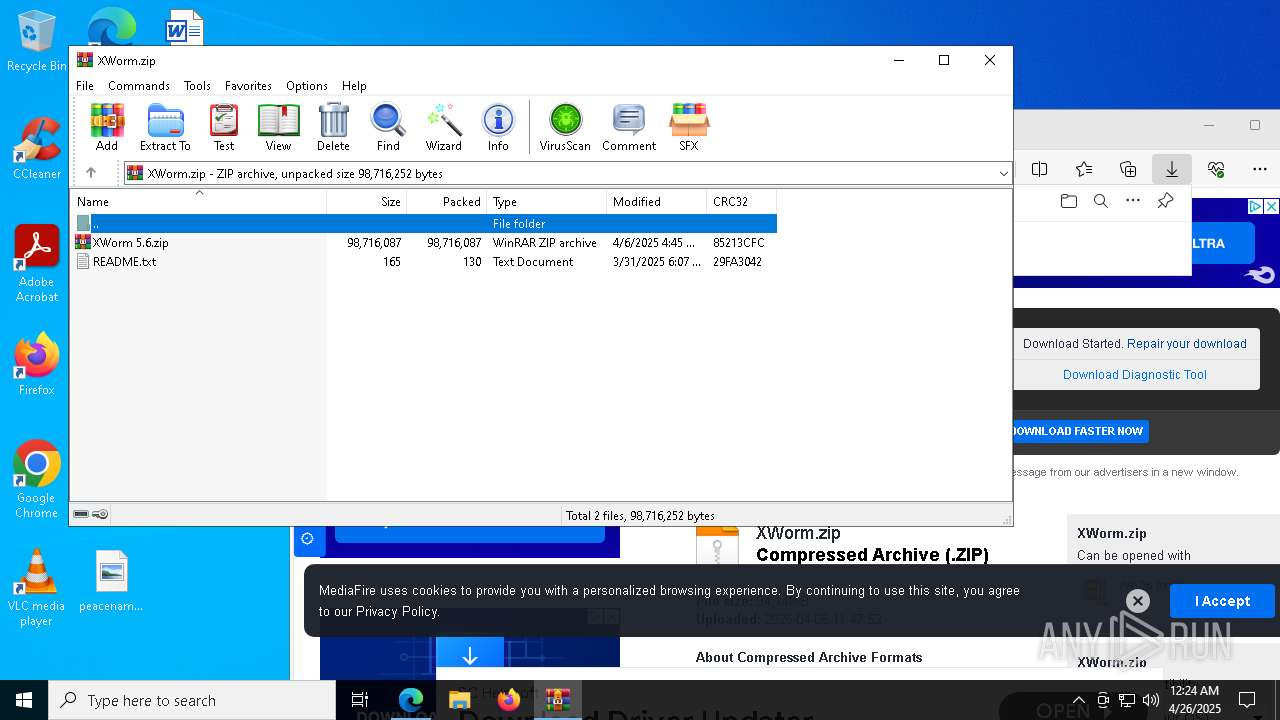
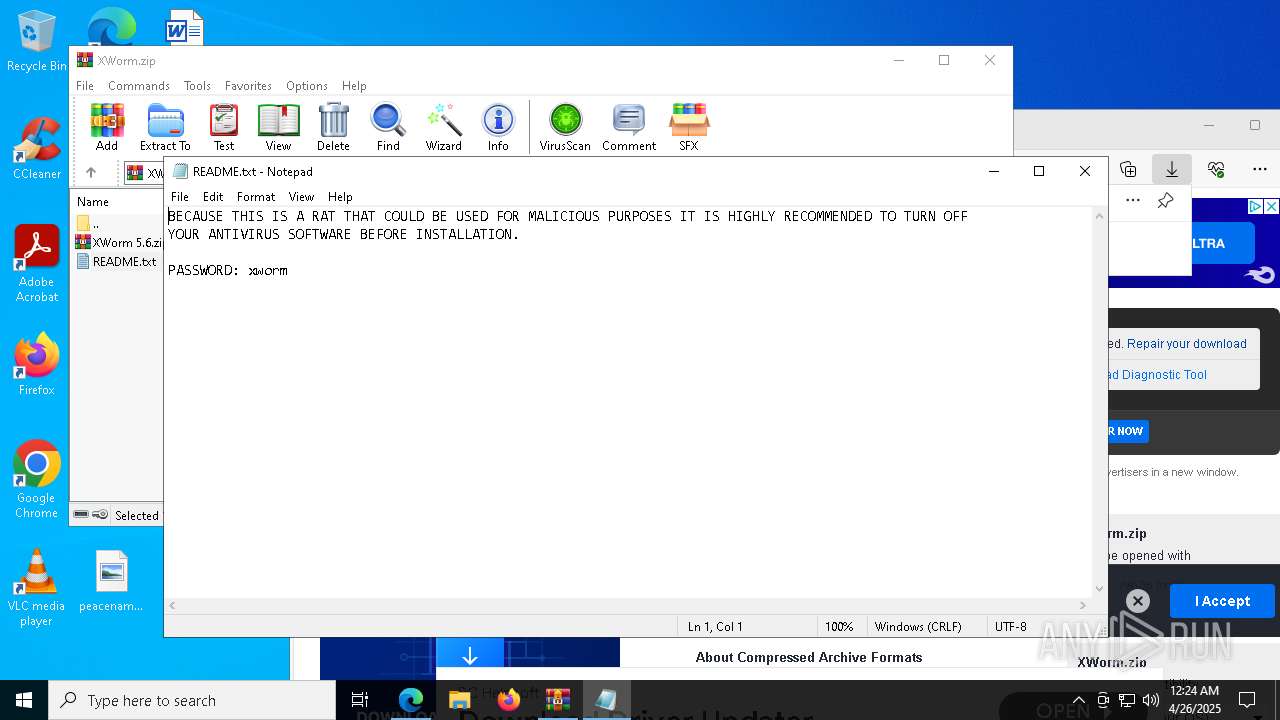
| URL: | www.mediafire.com/file/0j3c5o213uvt6of/XWorm.zip/file |
| Full analysis: | https://app.any.run/tasks/7d33e230-e9d0-4e4b-852b-f9816d4bf82f |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 26, 2025, 00:23:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9F358711F7CDF06593F45B5B7CA91825 |
| SHA1: | C7378F3EDC7386490B5EBB56243C647757C846CC |
| SHA256: | 512162BC91020AF79B46CBEE553728FF74D50E4469A0B945A0A1EE595BC9E190 |
| SSDEEP: | 3:ER63eGUoVuFBc:h3eGxUG |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2196)
- msedge.exe (PID: 7324)
- svchost.exe (PID: 2240)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- msedge.exe (PID: 7324)
Vulnerable driver has been detected
- updater.exe (PID: 8172)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2240)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 4268)
Application launched itself
- WinRAR.exe (PID: 8360)
Executes application which crashes
- Xworm V5.6.exe (PID: 5136)
- Xworm V5.6.exe (PID: 4284)
- svc.exe (PID: 7376)
- svc.exe (PID: 3992)
- Xworm V5.6.exe (PID: 8280)
- Xworm V5.6.exe (PID: 8140)
- svc.exe (PID: 7392)
- Xworm V5.6.exe (PID: 8460)
- svc.exe (PID: 6660)
- Xworm V5.6.exe (PID: 6068)
- Xworm V5.6.exe (PID: 536)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 3096)
- cmd.exe (PID: 8000)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- msedge.exe (PID: 7324)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 8792)
- powershell.exe (PID: 6436)
Executable content was dropped or overwritten
- svc.exe (PID: 8096)
- updater.exe (PID: 8172)
The process checks if current user has admin rights
- updater.exe (PID: 8172)
Starts POWERSHELL.EXE for commands execution
- updater.exe (PID: 8172)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 8172)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6960)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 8360)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8360)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2240)
Connects to unusual port
- svchost.exe (PID: 2240)
INFO
Reads the computer name
- identity_helper.exe (PID: 9172)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4268)
Manual execution by a user
- WinRAR.exe (PID: 4268)
- Xworm V5.6.exe (PID: 5136)
- XwormLoader.exe (PID: 8364)
- powershell.exe (PID: 8792)
- powershell.exe (PID: 8040)
- cmd.exe (PID: 3096)
- Xworm V5.6.exe (PID: 4284)
- XwormLoader.exe (PID: 1660)
- Xworm V5.6.exe (PID: 8280)
- XwormLoader.exe (PID: 8620)
- Xworm V5.6.exe (PID: 8140)
- cmd.exe (PID: 8000)
- XwormLoader.exe (PID: 8460)
- conhost.exe (PID: 8792)
- cmd.exe (PID: 6960)
- cmd.exe (PID: 4012)
- XwormLoader.exe (PID: 5084)
- XwormLoader.exe (PID: 7592)
- XwormLoader.exe (PID: 4268)
- XwormLoader.exe (PID: 8568)
- XwormLoader.exe (PID: 8288)
- XwormLoader.exe (PID: 2776)
- XwormLoader.exe (PID: 9004)
- XwormLoader.exe (PID: 8892)
- XwormLoader.exe (PID: 3796)
- XwormLoader.exe (PID: 7736)
- XwormLoader.exe (PID: 8728)
- WinRAR.exe (PID: 7896)
- Xworm V5.6.exe (PID: 536)
- Xworm V5.6.exe (PID: 6068)
- Xworm V5.6.exe (PID: 8460)
- XwormLoader.exe (PID: 2340)
- svchost.exe (PID: 2240)
Checks supported languages
- identity_helper.exe (PID: 9172)
Application launched itself
- msedge.exe (PID: 6620)
Reads Environment values
- identity_helper.exe (PID: 9172)
Reads the software policy settings
- slui.exe (PID: 3140)
The sample compiled with japanese language support
- updater.exe (PID: 8172)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6620)
- WinRAR.exe (PID: 8360)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
301
Monitored processes
155
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Users\admin\Desktop\XWorm 5.6\Xworm V5.6.exe" | C:\Users\admin\Desktop\XWorm 5.6\Xworm V5.6.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 720 | C:\WINDOWS\system32\WerFault.exe -u -p 8460 -s 1540 | C:\Windows\System32\WerFault.exe | — | Xworm V5.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\WINDOWS\system32\reg.exe" add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v GoogleUpdateTaskMachineQC /t REG_SZ /f /d C:\Users\admin\AppData\Roaming\Google\Chrome\updater.exe | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1576 --field-trial-handle=2376,i,9347849691955947164,14397997739992110932,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\XWorm 5.6\XwormLoader.exe" | C:\Users\admin\Desktop\XWorm 5.6\XwormLoader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1676 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=5828 --field-trial-handle=2376,i,9347849691955947164,14397997739992110932,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | XwormLoader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\System32\svchost.exe rdivktoinsbrqenp 6E3sjfZq2rJQaxvLPmXgsFbIFjbxmk9QBL7MU6NBupT4bFjOM5ljkjva9Wuwf0mKrI0a+E9AE4BrmmhamSqTGuFa4LTaCOVDVXMuFOwqXoCUKfP0M8Y6F7ry6LjlwpABqWFUXMzKNovRG6R0WU637t4oLVi7FzpX9g6uTKPr7FY1pFteKvpv26DBzJE5n4ElFy2SlYXulLSXhuopVWKuAkYp6c4e79CIqF2IeTTCFjsq/LVqKudM064ZUYJvS1hJ78o2RHoMPfbjyQFCM+O5Xkzab/C+dW5F5FlUkrqynnPQnmXczTXGCgnyMFbhO8Ll1ls0wUgDsXB4Iiy8ixddCvcxu3Hd4J12th6ZFFxBJcihDR/s7PJcBR/Nfo70v4eqKbvCdM19m9/vR1xTvoYZ0IUG0FiqPvAlTVZUWobcPm4jRFqfW0ea+c4Z1KEkkx6g1YA8LXN0PlRxlpfR3yUvL2CHLQYitGQl2UMZZw04MET0qduwX2YwKSTzJ1Qmy1vEMvWqvzSlzX3kjR9c9DB8KQ== | C:\Windows\System32\svchost.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
58 418
Read events
58 332
Write events
86
Delete events
0
Modification events
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 85A0FEBF39922F00 | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656106 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {66FC88ED-34FF-4C81-9C1D-5426E7306997} | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: F983F1BF39922F00 | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656106 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C01CDFA9-4C52-44D2-B2DB-C231ACDAE478} | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656106 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E360943E-4C2C-4938-ADDA-808B84696D7C} | |||
| (PID) Process: | (6620) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656106 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C189D8BD-B440-45A3-B41A-0D6DBDC2388B} | |||
Executable files
65
Suspicious files
483
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b519.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b529.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b538.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b538.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b538.TMP | — | |
MD5:— | SHA256:— | |||
| 6620 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
246
DNS requests
347
Threats
56
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8512 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8512 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8668 | svchost.exe | HEAD | 200 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/23e5dd61-e224-4d56-858f-6ee086574ada?P1=1746054429&P2=404&P3=2&P4=I7L7c3QUw9LxiAwnBDwbaNML7D6BTG7aY%2fPvZWzvnbOWaXRkyEYYNcE2mtyMAEn%2frHaigCWkew1dKW650iIQWg%3d%3d | unknown | — | — | whitelisted |
8668 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/23e5dd61-e224-4d56-858f-6ee086574ada?P1=1746054429&P2=404&P3=2&P4=I7L7c3QUw9LxiAwnBDwbaNML7D6BTG7aY%2fPvZWzvnbOWaXRkyEYYNcE2mtyMAEn%2frHaigCWkew1dKW650iIQWg%3d%3d | unknown | — | — | whitelisted |
8668 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/23e5dd61-e224-4d56-858f-6ee086574ada?P1=1746054429&P2=404&P3=2&P4=I7L7c3QUw9LxiAwnBDwbaNML7D6BTG7aY%2fPvZWzvnbOWaXRkyEYYNcE2mtyMAEn%2frHaigCWkew1dKW650iIQWg%3d%3d | unknown | — | — | whitelisted |
8668 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/23e5dd61-e224-4d56-858f-6ee086574ada?P1=1746054429&P2=404&P3=2&P4=I7L7c3QUw9LxiAwnBDwbaNML7D6BTG7aY%2fPvZWzvnbOWaXRkyEYYNcE2mtyMAEn%2frHaigCWkew1dKW650iIQWg%3d%3d | unknown | — | — | whitelisted |
8668 | svchost.exe | GET | 206 | 2.22.242.227:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/23e5dd61-e224-4d56-858f-6ee086574ada?P1=1746054429&P2=404&P3=2&P4=I7L7c3QUw9LxiAwnBDwbaNML7D6BTG7aY%2fPvZWzvnbOWaXRkyEYYNcE2mtyMAEn%2frHaigCWkew1dKW650iIQWg%3d%3d | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6620 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7324 | msedge.exe | 104.21.42.32:443 | the.gatekeeperconsent.com | — | — | unknown |
7324 | msedge.exe | 104.17.151.117:443 | www.mediafire.com | — | — | whitelisted |
7324 | msedge.exe | 172.67.199.186:443 | the.gatekeeperconsent.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.mediafire.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7324 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7324 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7324 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7324 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7324 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7324 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7324 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7324 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7324 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
7324 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |