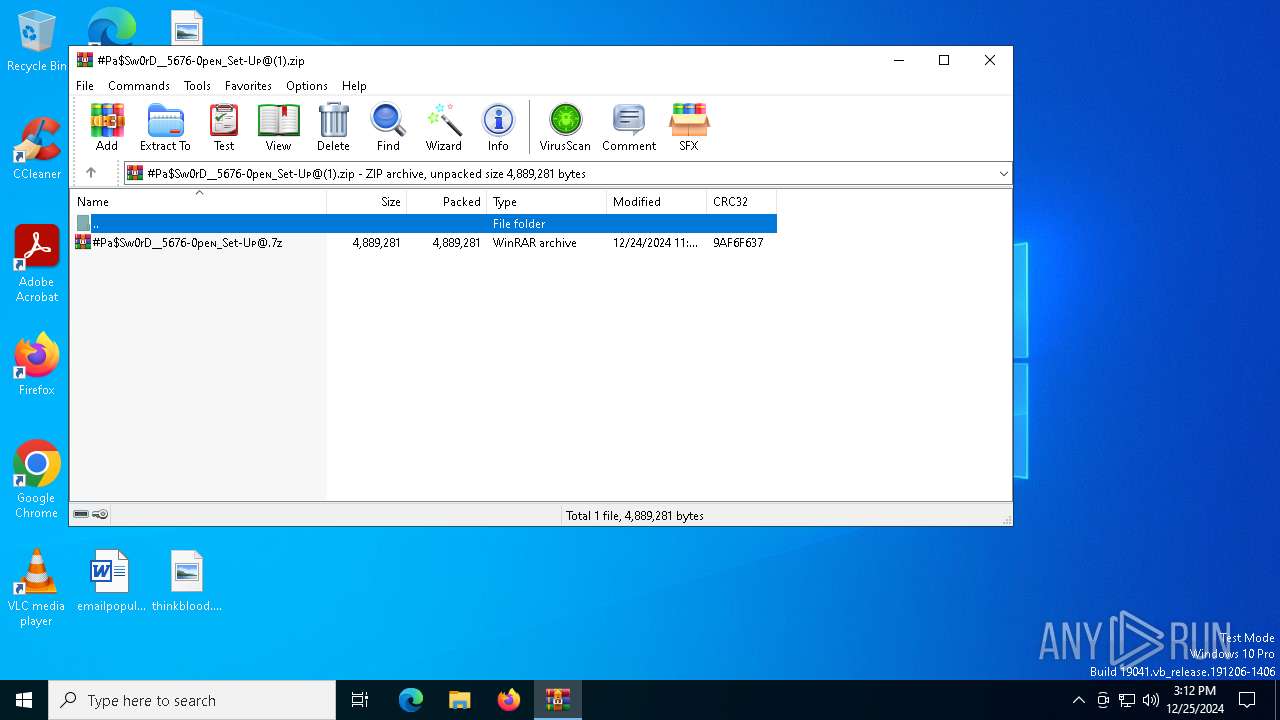
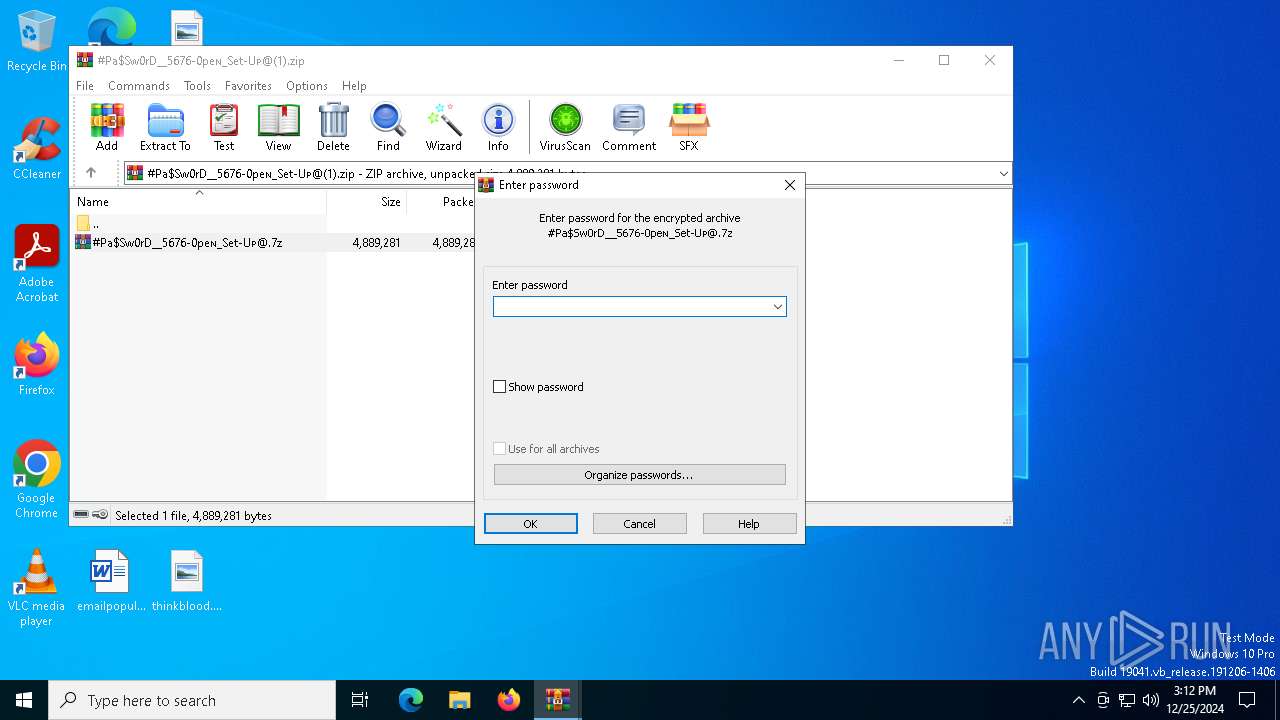
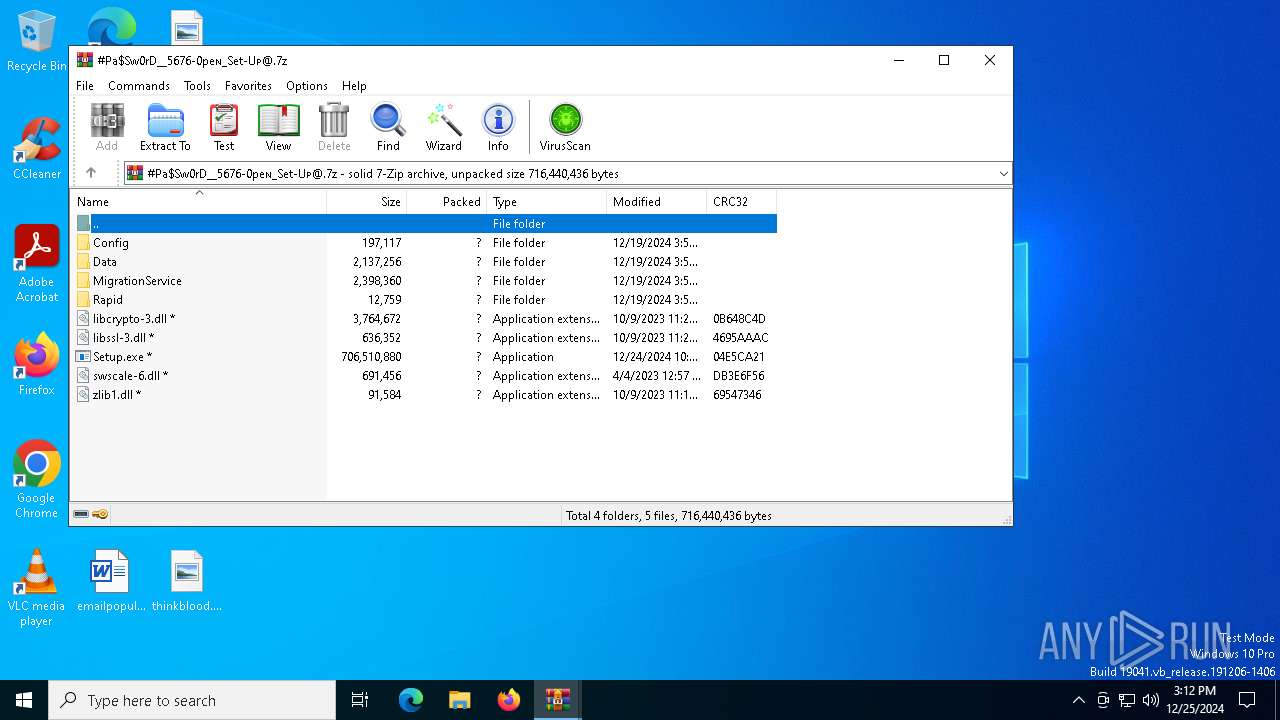
| File name: | #Pa$Sw0rD__5676-0peɴ_Set-Uᴘ@(1).zip |
| Full analysis: | https://app.any.run/tasks/9b2477b1-5cf4-4fc4-851a-12bc5ec430d1 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 25, 2024, 15:12:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | CFF148AB203C04841FDF074A9759C4C2 |
| SHA1: | 7890810E6CCFF3911852AA549F3BBAF7AC15236C |
| SHA256: | 5027593D821A39CBB5BBB22318DD7C5863068721B9F67BCB6A132304138C3FFC |
| SSDEEP: | 98304:jR018apx25zljdkSJ9vSQDe8T6oZWZ75TrhcMI/sTAx6Elx+ynS6H94kVlkidbM4:g4Wwl6cf |
MALICIOUS
Steals credentials from Web Browsers
- Setup.exe (PID: 6908)
Actions looks like stealing of personal data
- Setup.exe (PID: 6908)
Executing a file with an untrusted certificate
- Setup.exe (PID: 6908)
LUMMA mutex has been found
- Setup.exe (PID: 6908)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 5736)
Generic archive extractor
- WinRAR.exe (PID: 5736)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5736)
- WinRAR.exe (PID: 6468)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6468)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6468)
INFO
Checks supported languages
- Setup.exe (PID: 6908)
Reads the software policy settings
- Setup.exe (PID: 6908)
The process uses the downloaded file
- WinRAR.exe (PID: 5736)
- WinRAR.exe (PID: 6468)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6468)
The sample compiled with english language support
- WinRAR.exe (PID: 6468)
Reads the computer name
- Setup.exe (PID: 6908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:24 16:36:00 |
| ZipCRC: | 0x9af6f637 |
| ZipCompressedSize: | 4889281 |
| ZipUncompressedSize: | 4889281 |
| ZipFileName: | #Pa$Sw0rD__5676-0peɴ_Set-Uᴘ@.7z |
Total processes
130
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5736 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\#Pa$Sw0rD__5676-0peɴ_Set-Uᴘ@(1).zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6468 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa5736.37216\#Pa$Sw0rD__5676-0peɴ_Set-Uᴘ@.7z | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6908 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Bitvise Limited Integrity Level: MEDIUM Description: Bitvise SSH Client scriptable command line remote program execution client Version: 9.42.0.0 Modules
| |||||||||||||||
Total events
4 086
Read events
4 069
Write events
17
Delete events
0
Modification events
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\#Pa$Sw0rD__5676-0peɴ_Set-Uᴘ@(1).zip | |||
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
12
Suspicious files
2
Text files
43
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5736 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5736.37216\#Pa$Sw0rD__5676-0peɴ_Set-Uᴘ@.7z | — | |
MD5:— | SHA256:— | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\build_no_go.txt | text | |
MD5:4423738EA11C32298E0DF0E160DFCB6F | SHA256:99C037FEA2E972065B6ADD7BAE526491B91F41A765257876A09D0FA3F075D1CA | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\fold.txt | text | |
MD5:EC70D9AC95E4D0C8ECFC859D46E2EB3C | SHA256:16F84C45C630CE3071A164AA46FD2DC09B2F9CCD992072C8660FC2F737F8780F | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\DisplayLanguageNames.fa.txt | text | |
MD5:59A00623B4B640EFCFBB205563B2A27A | SHA256:977CE09D594A79582B30B71DCF558E1CF3C5CE28C8813E3D2A1B524D6F76B7DF | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\DisplayLanguageNames.ja_JP.txt | text | |
MD5:468293226B9E51736BE5FD18A7A428E5 | SHA256:A3E756356ACA1A07A49B90B6B546D6C56AB8D7B1D1595C70F00A0DA2AA5CBC01 | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\mod_list.txt | text | |
MD5:A651545EBAC407934B9C4CC1EE5D62D8 | SHA256:D3FDE0FC938D802398B694F84F6AE5EA340C37D6889C14B5BBDBC84C79419020 | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\mod_test_files.txt | text | |
MD5:85E210F2A362F270D46EB0D9A83BC9C9 | SHA256:2ADC1A5401A6156C34F92D0BA5899400253DBDBF81CC32925A647A60255A673B | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\mod_replace_import.txt | text | |
MD5:75167CD6A35994124A0E4F1CB24F02E4 | SHA256:C9458651F018744E56046D1EB053CFA2A22F223AB9764B163DBF247A934387BD | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\cy.txt | text | |
MD5:0F5662A68805D859F871EDC07E766A57 | SHA256:931DE741A6C8F1348A946623776FE36C55DD2FC384C7B1478225F7467853199E | |||
| 6468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6468.37765\Config\ga.txt | text | |
MD5:B4295E254B9DFC90E0093188257C007C | SHA256:406669ECBDF562E773B9CDF831CF5F63C3DD1A012C3521A41227C9141511D959 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
37
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6312 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4308 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4308 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4804 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4804 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4308 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4308 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.158:443 | www.bing.com | Akamai International B.V. | GB | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| unknown |