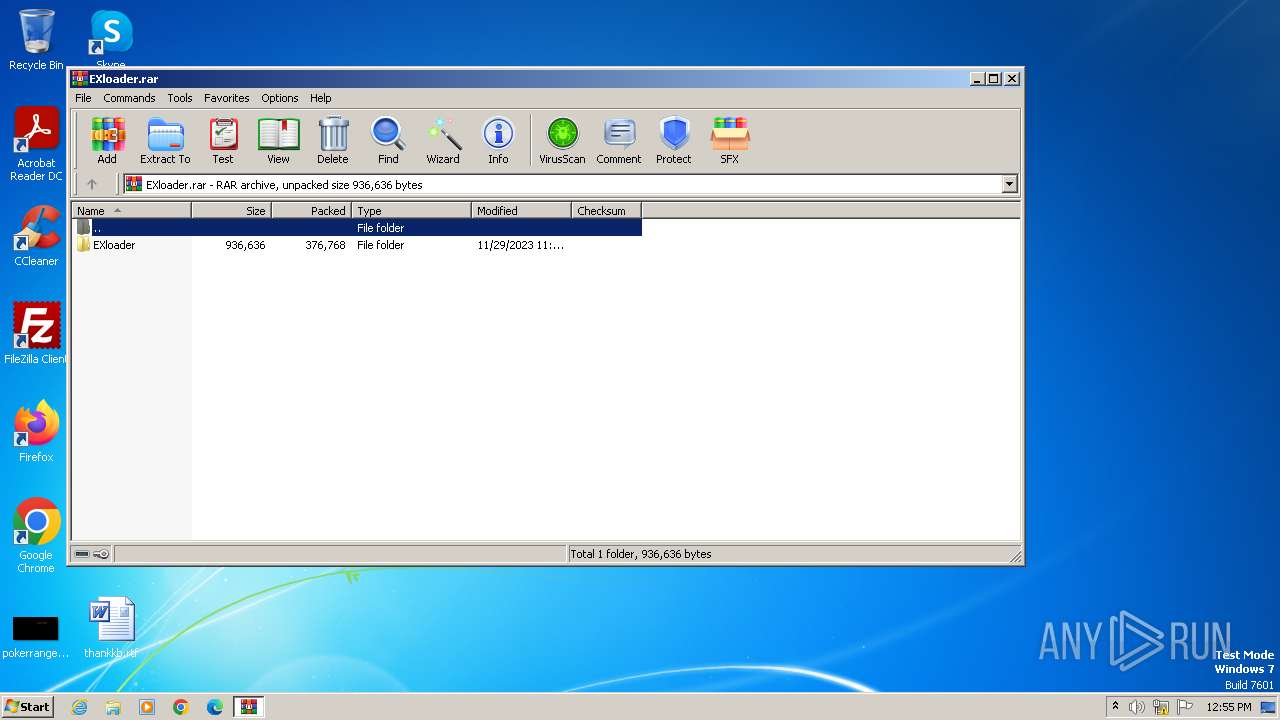
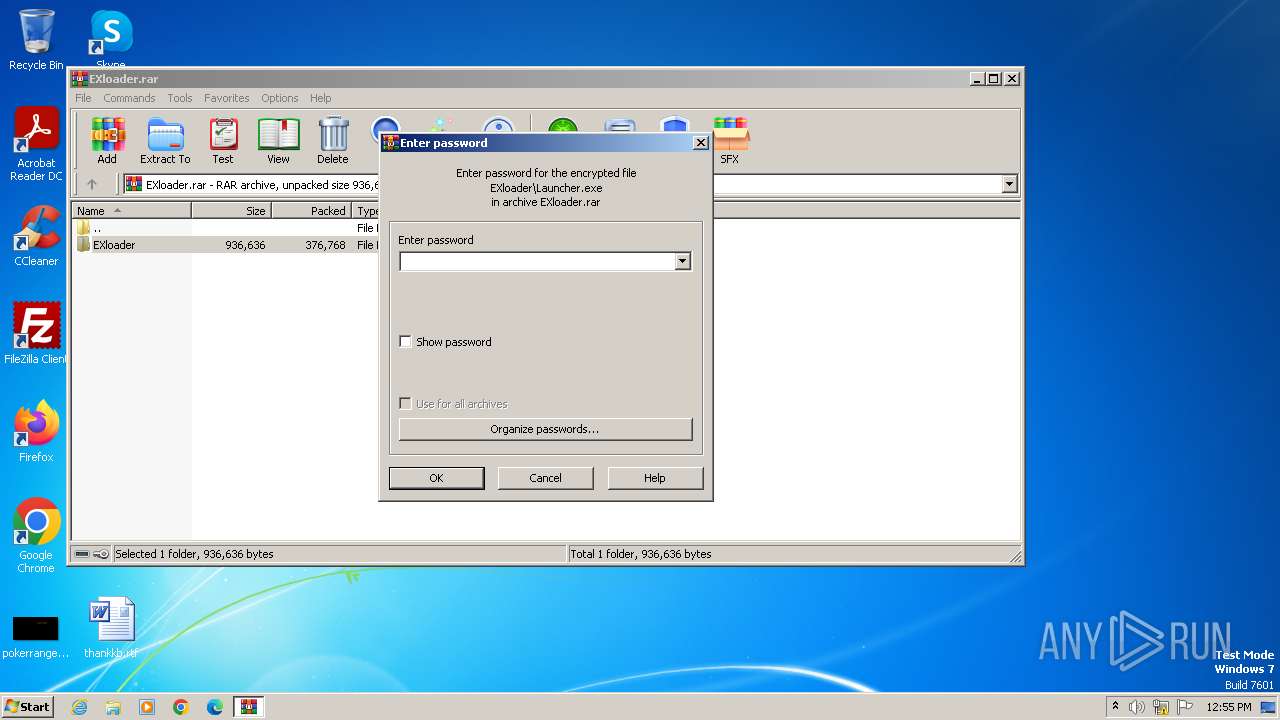
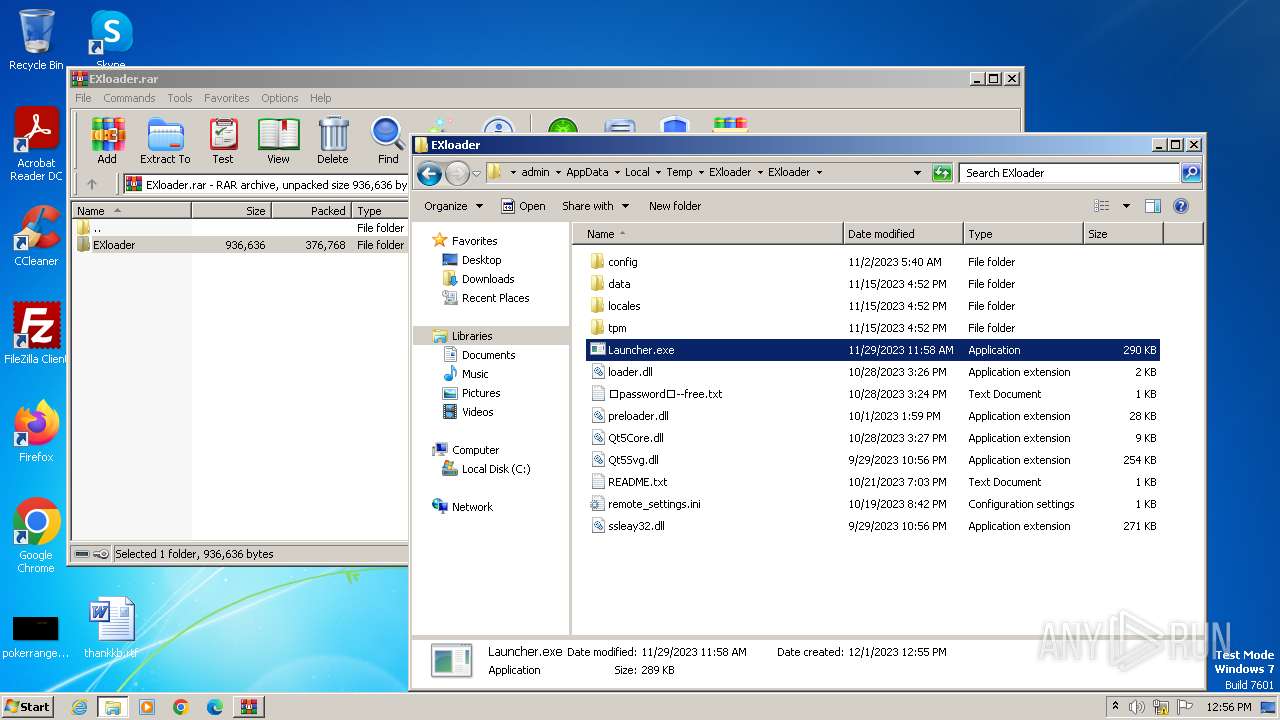
| File name: | EXloader.rar |
| Full analysis: | https://app.any.run/tasks/806c60f5-a8c5-4b40-8cb2-8178442130d7 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | December 01, 2023, 12:55:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EC23ADDBD39E1DF710CA7932D32CF4F7 |
| SHA1: | 31B494237F4C13CD529C3A5FDABE9145AE18A8A6 |
| SHA256: | 4FC0E939AA75E3DB5A329045C850F78E3777E8A8C8D6DA8D9C1B6538CC150C39 |
| SSDEEP: | 12288:YYjv1X88wopxMK/BKG49wuhYtd7KXDt6Rou7HdXsIQP:YYz1MAX+auStdwDt6Rf7HdXsIg |
MALICIOUS
Steals credentials from Web Browsers
- Launcher.exe (PID: 2764)
Connects to the CnC server
- Launcher.exe (PID: 2764)
REDLINE has been detected (SURICATA)
- Launcher.exe (PID: 2764)
Actions looks like stealing of personal data
- Launcher.exe (PID: 2764)
SUSPICIOUS
Connects to unusual port
- Launcher.exe (PID: 2764)
Searches for installed software
- Launcher.exe (PID: 2764)
Reads browser cookies
- Launcher.exe (PID: 2764)
INFO
Manual execution by a user
- explorer.exe (PID: 3796)
- Launcher.exe (PID: 2764)
- wmpnscfg.exe (PID: 3204)
- wmpnscfg.exe (PID: 3388)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2144)
Checks supported languages
- Launcher.exe (PID: 2764)
- wmpnscfg.exe (PID: 3388)
- wmpnscfg.exe (PID: 3204)
Reads the computer name
- Launcher.exe (PID: 2764)
- wmpnscfg.exe (PID: 3388)
- wmpnscfg.exe (PID: 3204)
Reads the machine GUID from the registry
- Launcher.exe (PID: 2764)
Reads product name
- Launcher.exe (PID: 2764)
Reads Environment values
- Launcher.exe (PID: 2764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
43
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2144 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\EXloader.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2764 | "C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\Launcher.exe" | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\Launcher.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3204 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3388 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3796 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 632
Read events
3 605
Write events
9
Delete events
18
Modification events
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2764) Launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: 0AFF97CD06EF0F6CC1F8FBE057227F769EA5D3968F1D8EB3F8CC3641FAEC8D90 | |||
| (PID) Process: | (2764) Launcher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Google\Chrome\User Data\lockfile | |||
Executable files
8
Suspicious files
8
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\preloader.dll | executable | |
MD5:218A905DDE00690C0DF0CF3FF51D7EDF | SHA256:8023AF161301E71E9A827D8EE567713286C3407F90899E745FEA1533B038A66C | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\loader.dll | executable | |
MD5:F188F5741CF4BAF89B994B2F114D9BB5 | SHA256:B361203044BB95332B51A36D2527F64BB72CF2B445B250804083A8403C0BA88F | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\locales\sys-2023-09-08-132824 (2).log | binary | |
MD5:1A05D73739609A30C6C9AF75EDFAF82A | SHA256:EDAD59107F8FCD876BEB00371CB6D4FE3ACA28B6B9C00FF80B24286300C12F3E | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\locales\sys-2023-09-08-132824.log | binary | |
MD5:1A05D73739609A30C6C9AF75EDFAF82A | SHA256:EDAD59107F8FCD876BEB00371CB6D4FE3ACA28B6B9C00FF80B24286300C12F3E | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\remote_settings.ini | text | |
MD5:6C8B0641D4D019DA8F99339DE19DA7CA | SHA256:78EFB7D5F66CCE1C0DE86A764BC48450B929DF61849280B861FB0DB2128B2A37 | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\Qt5Core.dll | executable | |
MD5:9D05666DCFA76EDD18194F62148AF50E | SHA256:8B4EBF3129DEE8D8CC613502004882111D318E6E6172807D4ABD63CD2A2AABF8 | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\README.txt | text | |
MD5:3E0DBD9D30D6566CFBAB7A02255A9567 | SHA256:EE42D138C5EAFA4FE94887F1C0C7D028A9C506C8752A3D12CD681CCD098ACC56 | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\tpm\preloader (2).dll | executable | |
MD5:218A905DDE00690C0DF0CF3FF51D7EDF | SHA256:8023AF161301E71E9A827D8EE567713286C3407F90899E745FEA1533B038A66C | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\Launcher.exe | executable | |
MD5:DC7FFF76A3F2121466077FF80857E5BB | SHA256:2F14682643560CC3F56C662BEA16F3A1034FDB4008E7F08726859EB5F61E25CB | |||
| 2144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EXloader\EXloader\locales\sys-2023-09-09-111726.log | binary | |
MD5:9559DF53EF9DAFF7276856DB2E2B405E | SHA256:5FF1D7E59CE0A02F6BFBD1947A5CC094D9110382C4D0EC9932790FEE6E6C1B38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
0
Threats
10
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2764 | Launcher.exe | 45.15.156.142:33597 | — | Galaxy LLC | RU | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
2764 | Launcher.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
2764 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
2764 | Launcher.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer Family Related (MC-NMF Authorization) |
2764 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC - Id1Response |
2764 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
2764 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer Family Activity (Response) |
2764 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
2764 | Launcher.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
2764 | Launcher.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
2764 | Launcher.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |