| File name: | Pre-Activated-Setup.exe |
| Full analysis: | https://app.any.run/tasks/70368e8e-ed69-4c9c-ac59-09fc80c85988 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 03, 2023, 21:47:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | B117A957510E259E39D6043F18FD2AF5 |
| SHA1: | 831676B908A9399FF993016E84FBA6F22C666421 |
| SHA256: | 4F2A44EEC93AF69930962DA39816CBEAF4E88B00C517C6654E0AC02D2CB00865 |
| SSDEEP: | 98304:1ibTSHH3G8POqDJhB3bTee7vb/BI6LaQgxrebsiNe5xxUdA8Kbga3/Z+o8y+DPbK:lLGefF0 |
MALICIOUS
LUMMA has been detected (YARA)
- RegSvcs.exe (PID: 3816)
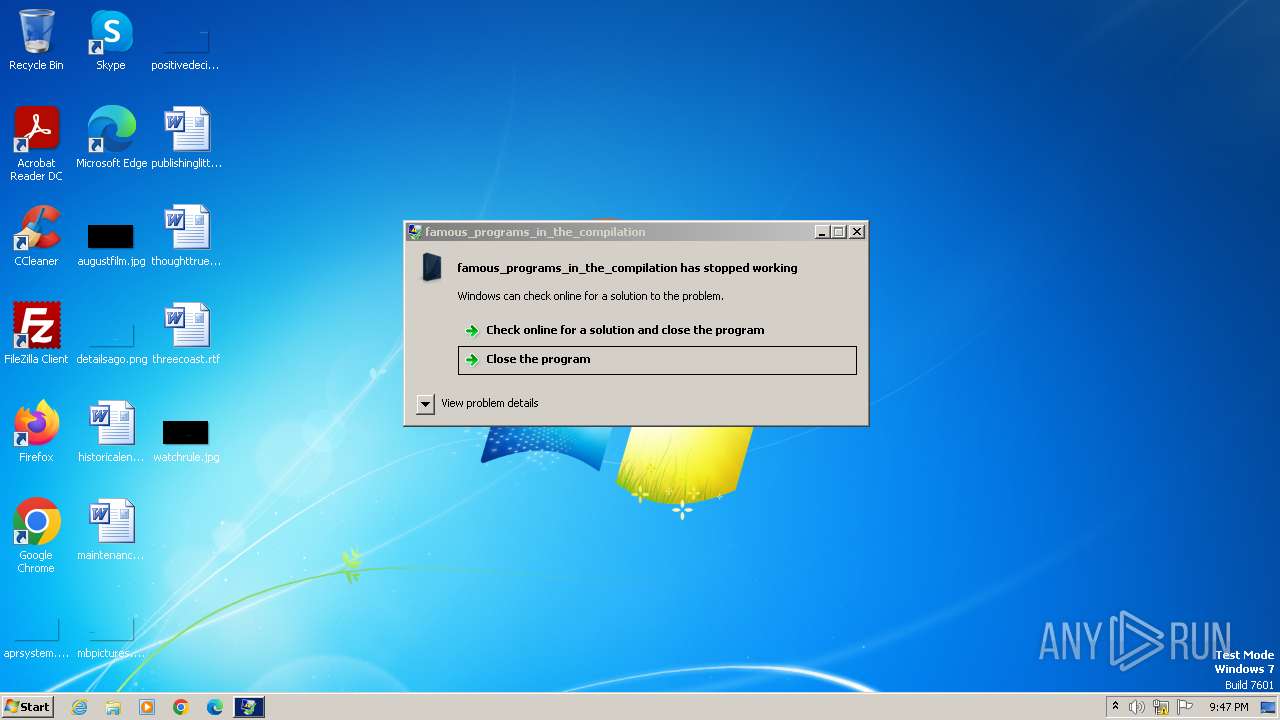
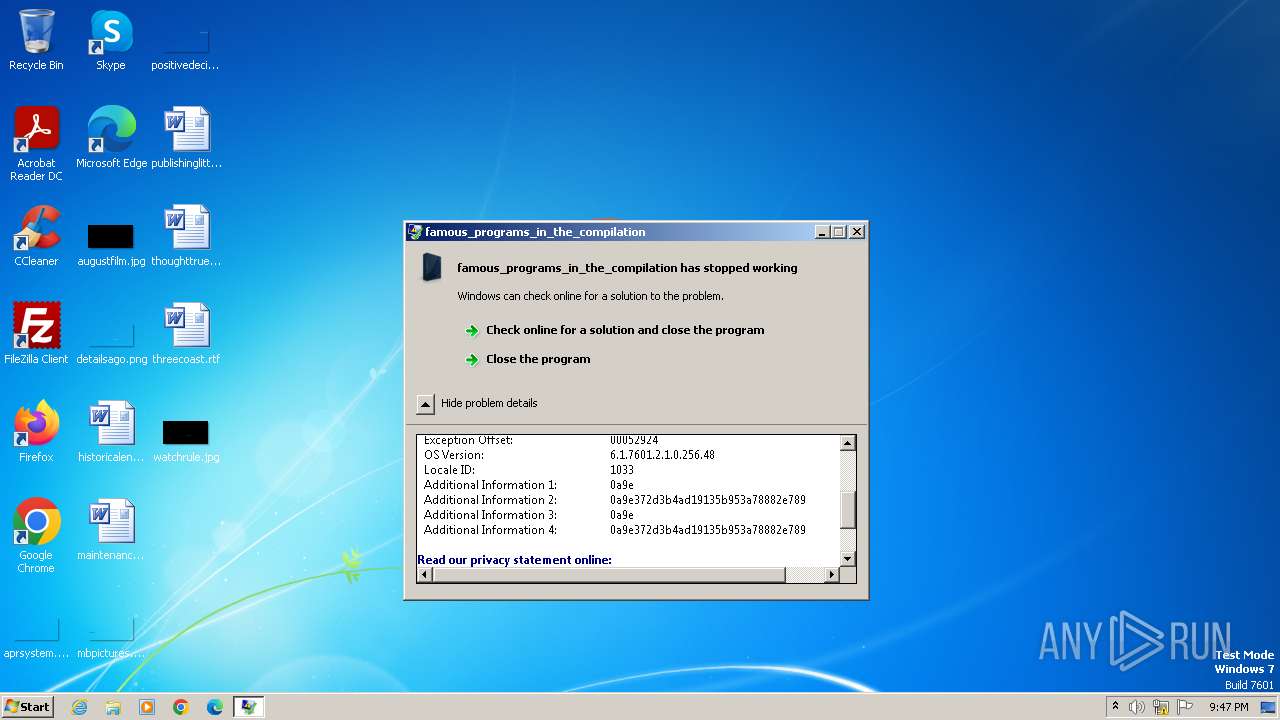
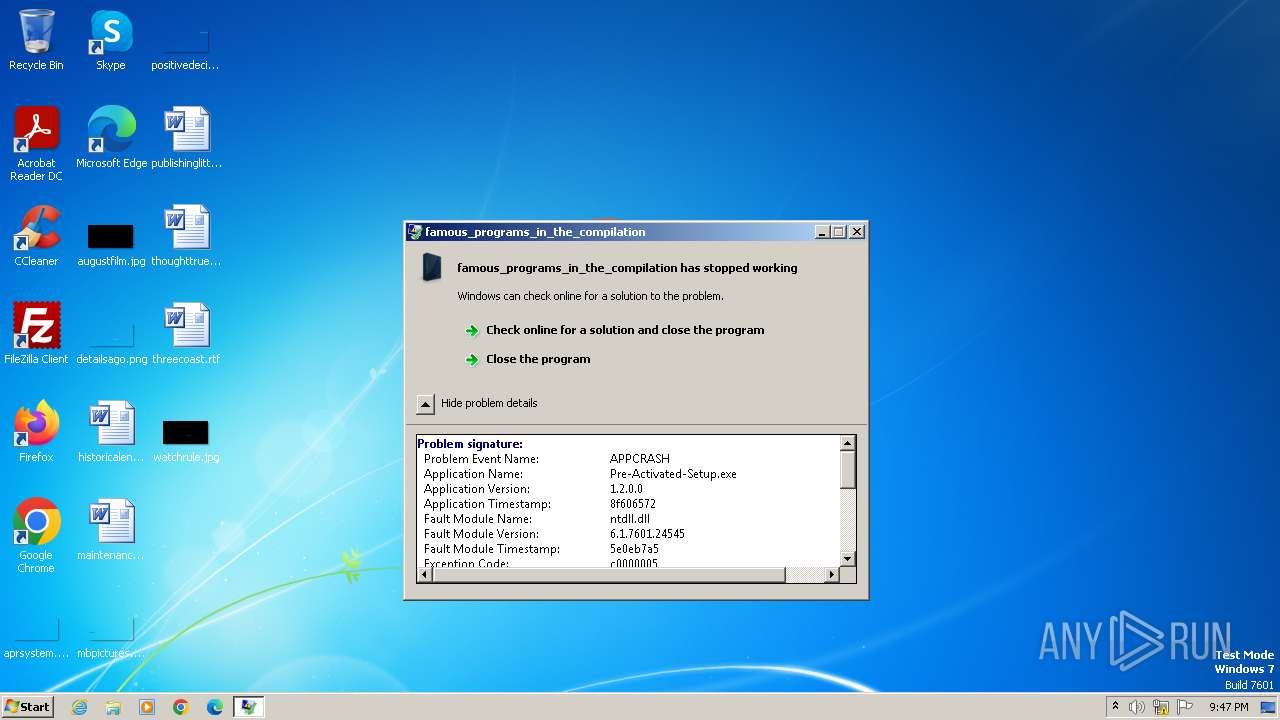
- Pre-Activated-Setup.exe (PID: 3060)
Drops the executable file immediately after the start
- Pre-Activated-Setup.exe (PID: 3060)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- Pre-Activated-Setup.exe (PID: 3060)
- RegSvcs.exe (PID: 3816)
- pwsh.exe (PID: 1352)
Reads the computer name
- Pre-Activated-Setup.exe (PID: 3060)
- RegSvcs.exe (PID: 3816)
- pwsh.exe (PID: 1352)
Reads the machine GUID from the registry
- Pre-Activated-Setup.exe (PID: 3060)
Create files in a temporary directory
- Pre-Activated-Setup.exe (PID: 3060)
Manual execution by a user
- WINWORD.EXE (PID: 2364)
- pwsh.exe (PID: 1352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31) |
| .scr | | | Windows screen saver (14.7) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.3) |
| .exe | | | Win32 Executable (generic) (5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2046:03:24 00:08:34+01:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 3834880 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3aa1fe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.0.0 |
| ProductVersionNumber: | 1.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
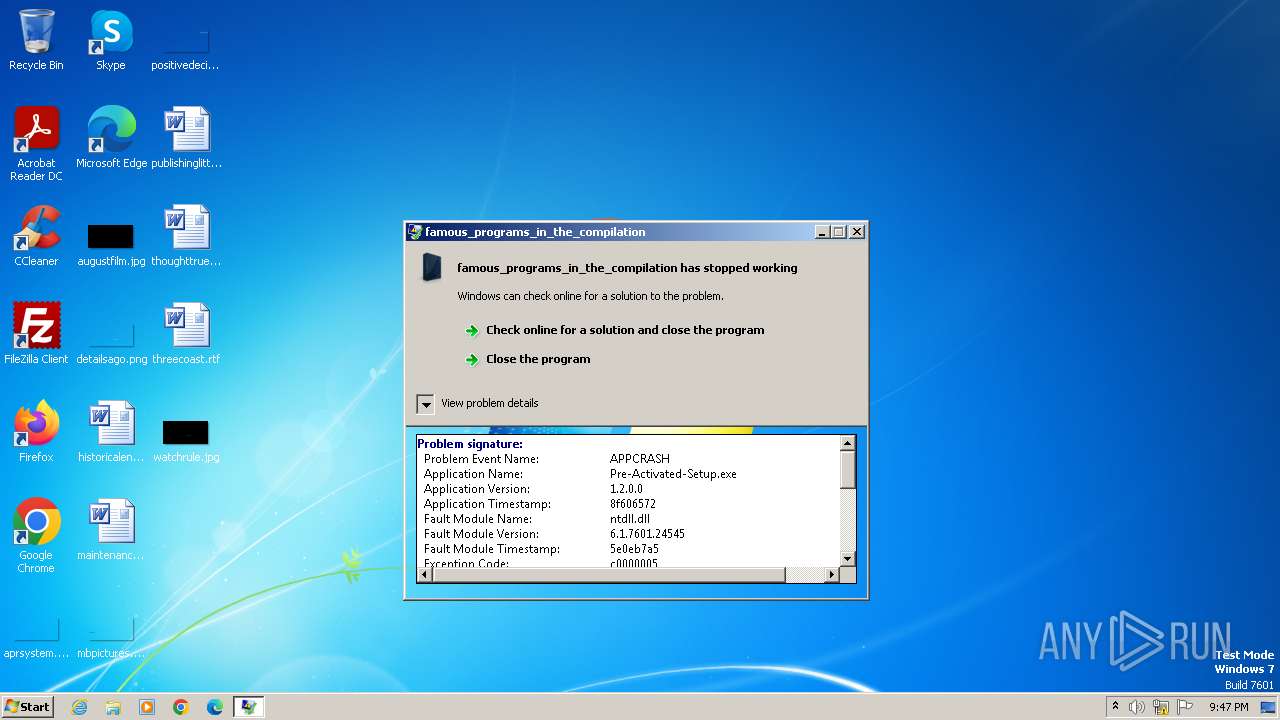
| FileDescription: | famous_programs_in_the_compilation |
| FileVersion: | 1.2.0.0 |
| InternalName: | famous_programs_in_the_compilation.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | famous_programs_in_the_compilation.exe |
| ProductName: | famous_programs_in_the_compilation |
| ProductVersion: | 1.2.0.0 |
| AssemblyVersion: | 1.2.0.0 |
Total processes
46
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1352 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 3221225786 Version: 7.2.11.500 Modules
| |||||||||||||||
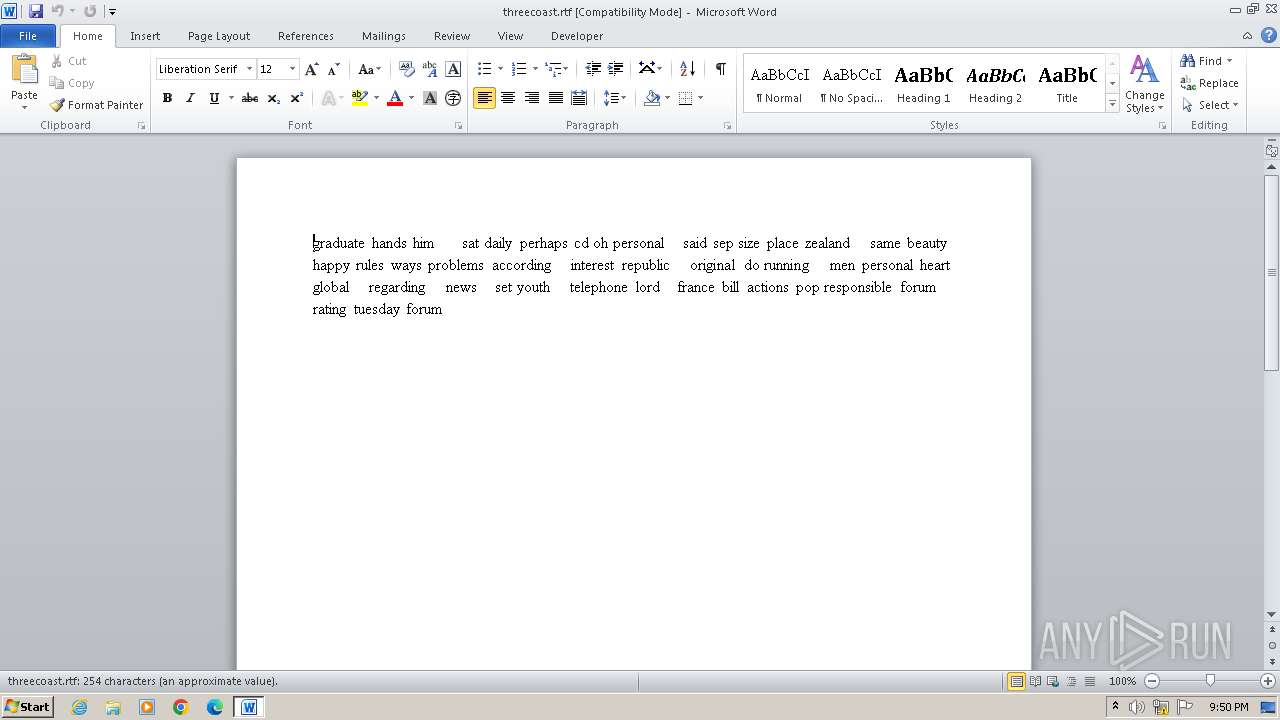
| 2364 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\threecoast.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3060 | "C:\Users\admin\AppData\Local\Temp\Pre-Activated-Setup.exe" | C:\Users\admin\AppData\Local\Temp\Pre-Activated-Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: famous_programs_in_the_compilation Exit code: 3221225477 Version: 1.2.0.0 Modules
| |||||||||||||||
| 3816 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Pre-Activated-Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
6 895
Read events
6 653
Write events
97
Delete events
145
Modification events
| (PID) Process: | (1352) pwsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2364) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
Executable files
2
Suspicious files
10
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC88A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:2AAAE3ACBB757876A909D5B6AD6C8BF8 | SHA256:109E564B8390E6F16FA68705F60A99992F42AEF6FC4E596C64142D8629C1260C | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:B7B7CA6FE0A321F05DAB35C1D18C21ED | SHA256:C8B8D14E782CBB0ABABEC23CAD30876279FA41F81AF8F88779D84567A0B5084D | |||
| 3060 | Pre-Activated-Setup.exe | C:\Users\admin\AppData\Local\Temp\Protect544cd51a.dll | executable | |
MD5:544CD51A596619B78E9B54B70088307D | SHA256:DFCE2D4D06DE6452998B3C5B2DC33EAA6DB2BD37810D04E3D02DC931887CFDDD | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{673A5A7C-6C95-4EA1-865F-D1E638ABCCE1}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 1352 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\B27IEVHJ4NFU12GJUXVP.temp | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 1352 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 2364 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{2071C4E0-282E-42A5-9C87-191C512F202F}.tmp | binary | |
MD5:93F1FB02EA4C7CBDBD608A034D0E8787 | SHA256:8F1D83D07368A2646C034D5DBCEBD2A82188427791F29F0E4856B3A73DE23CE3 | |||
| 1352 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_emcnavli.rgq.psm1 | text | |
MD5:F71085F591C9DA11E9CB0C1913569E46 | SHA256:E0223F32EFD4D2CE7E000D81E46D1979AA629B8281A0B7723123F74AEAC5BB7C | |||
| 2364 | WINWORD.EXE | C:\Users\admin\Desktop\~$reecoast.rtf | binary | |
MD5:5B18D0C8D548F7C4FF9C83012142D596 | SHA256:2D0B4095C0AAEA0C6759A9B1F81D337F3DDE531FB6BA75E268BE466F1BA20124 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
19
DNS requests
13
Threats
14
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3816 | RegSvcs.exe | 188.114.97.3:80 | conterso.pw | CLOUDFLARENET | NL | unknown |
3816 | RegSvcs.exe | 188.114.96.3:80 | conterso.pw | CLOUDFLARENET | NL | unknown |
3816 | RegSvcs.exe | 104.21.13.53:80 | tirechinecarpett.pw | CLOUDFLARENET | — | unknown |
3816 | RegSvcs.exe | 172.67.154.200:80 | tirechinecarpett.pw | CLOUDFLARENET | US | unknown |
1352 | pwsh.exe | 2.18.238.120:443 | aka.ms | AKAMAI-AS | CL | unknown |
3816 | RegSvcs.exe | 104.21.43.126:80 | musclefarelongea.pw | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
conterso.pw |
| unknown |
tirechinecarpett.pw |
| malicious |
dns.msftncsi.com |
| shared |
aka.ms |
| whitelisted |
musclefarelongea.pw |
| malicious |
fanlumpactiras.pw |
| malicious |
ownerbuffersuperw.pw |
| unknown |
freckletropsao.pw |
| malicious |
hemispheredonkkl.pw |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (tirechinecarpett .pw) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (musclefarelongea .pw) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (fanlumpactiras .pw) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (ownerbuffersuperw .pw) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 1352. Message ID: [0x2509].
|