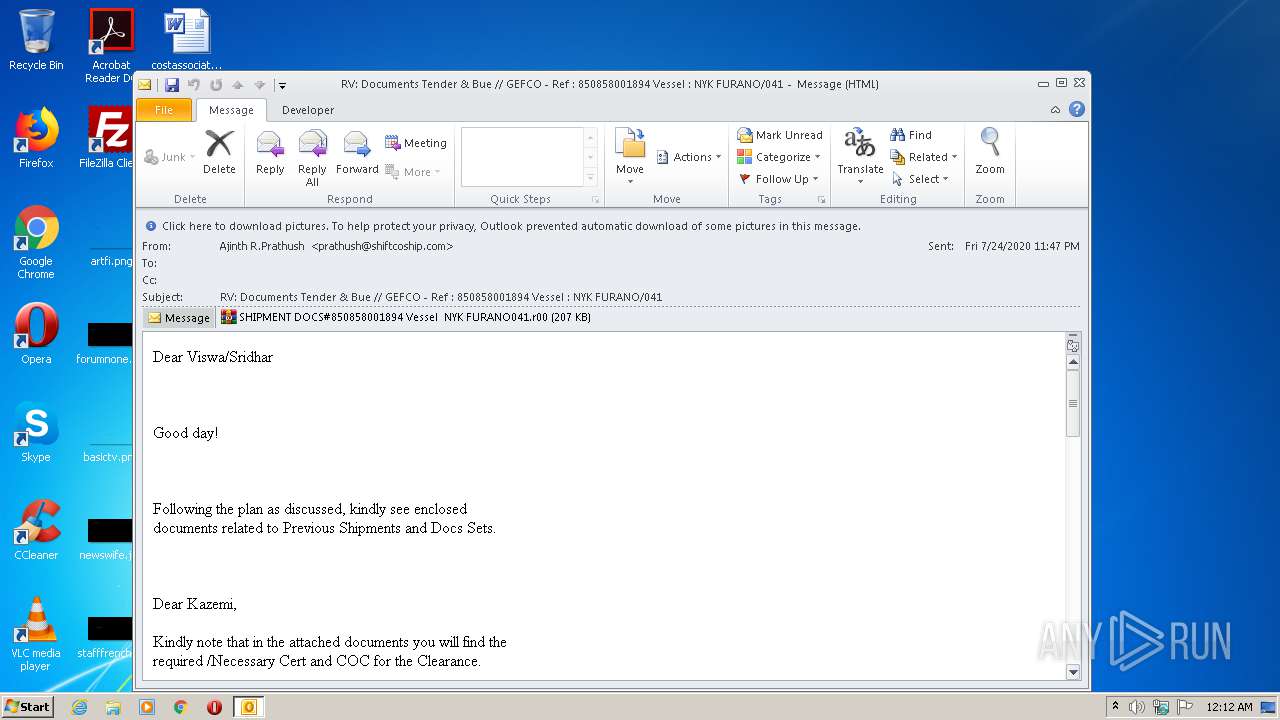
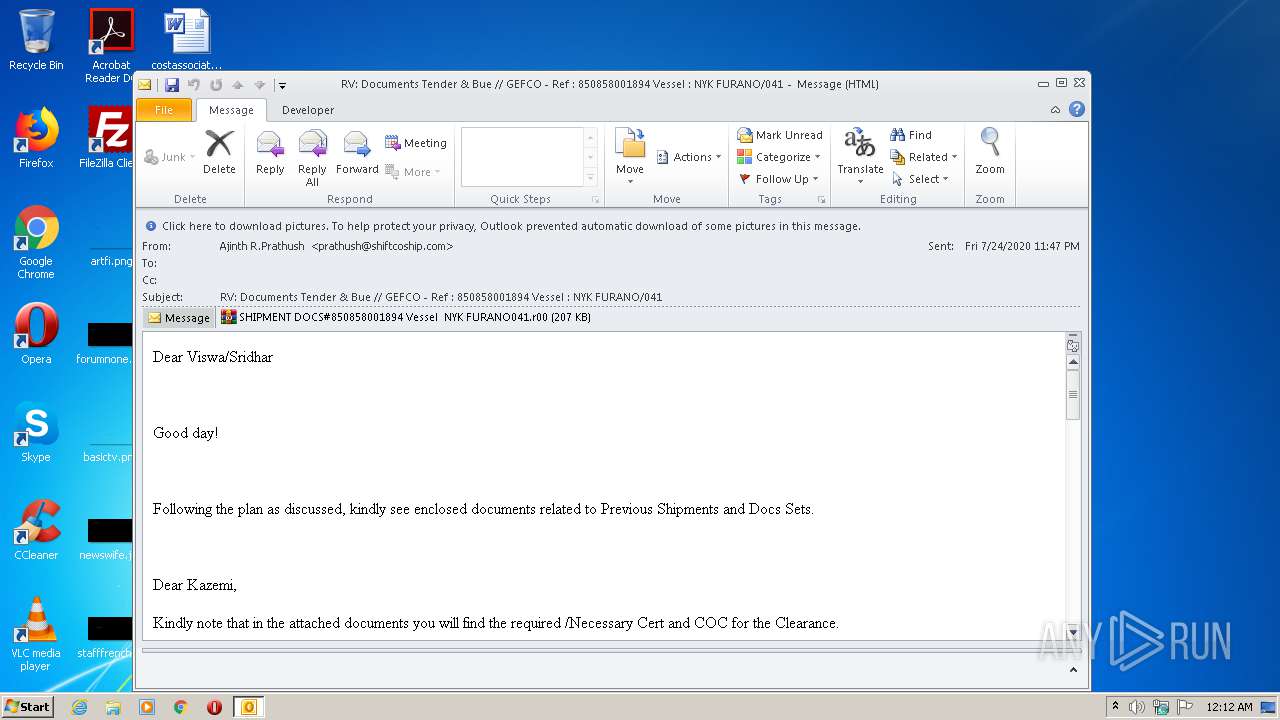
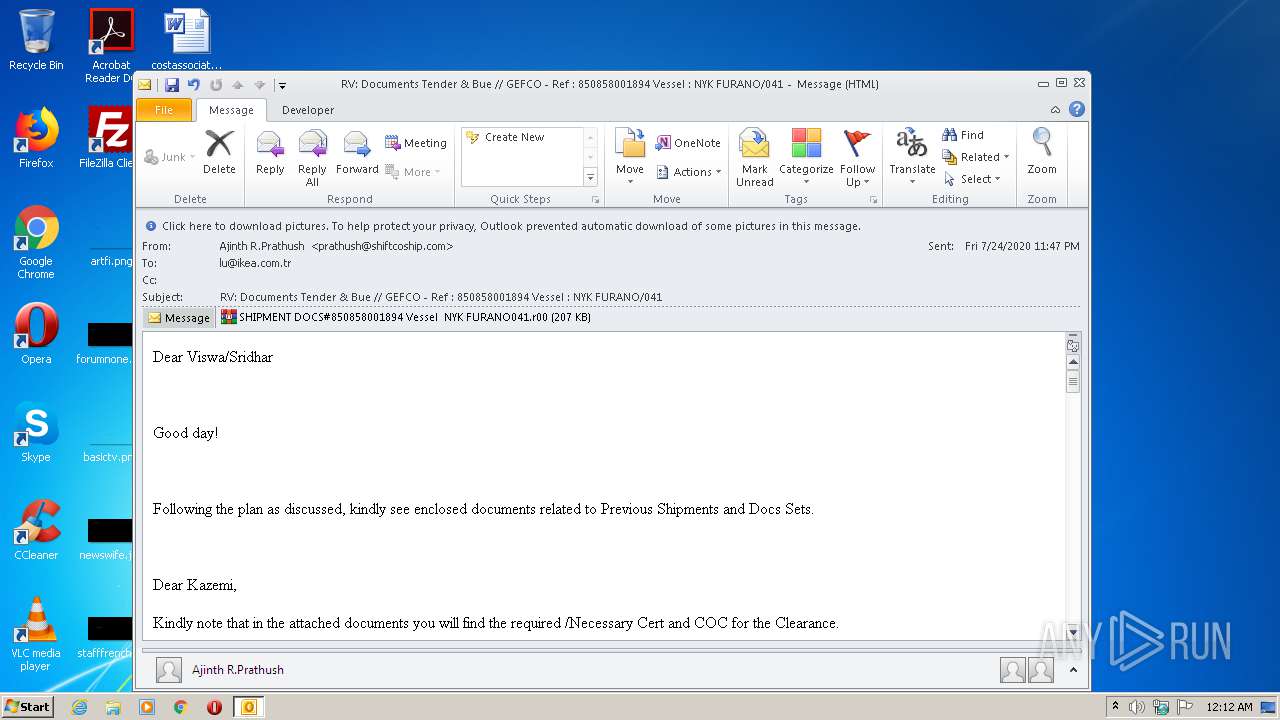
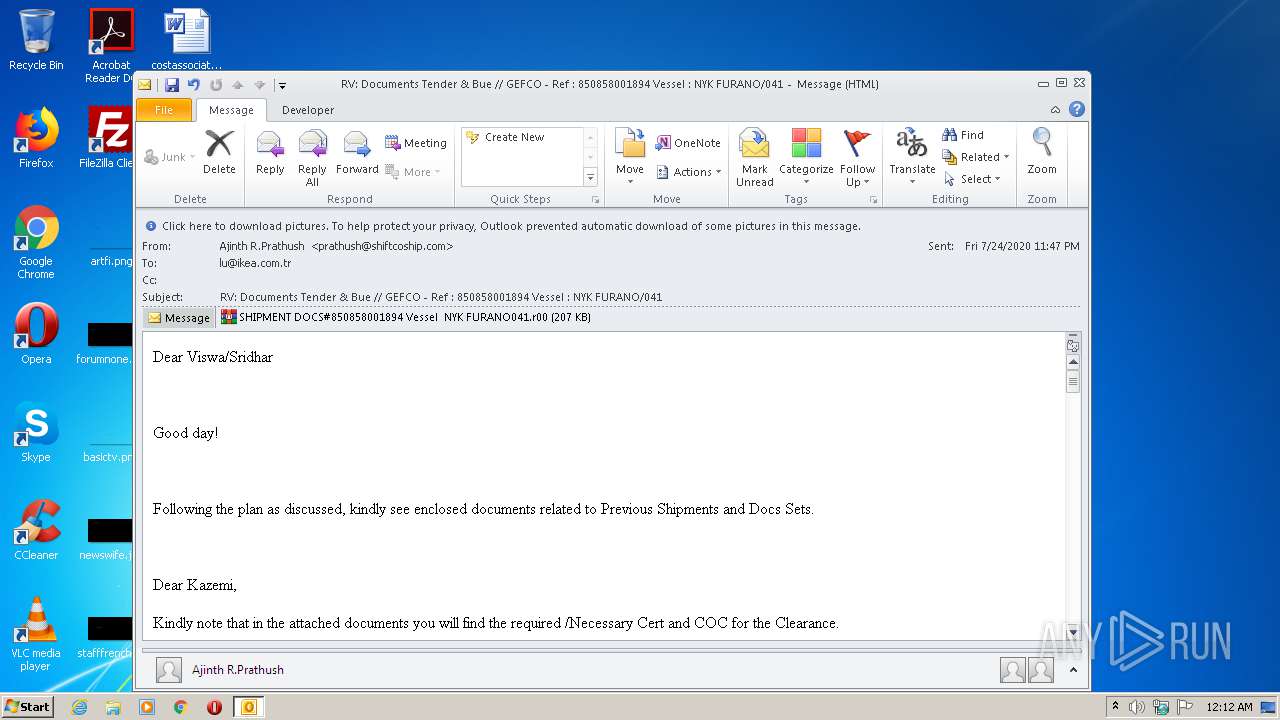
| File name: | RV%3a Documents Tender & Bue %2f%2f GEFCO - Ref %3a 850858001894 Vessel %3a NYK FURANO%2f041.eml |
| Full analysis: | https://app.any.run/tasks/db12c941-6e5e-434d-9757-931af78a0ae6 |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | July 24, 2020, 23:11:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | news or mail, ASCII text, with CRLF line terminators |
| MD5: | 626CC82942EB15533E0FFEA56E3A54E4 |
| SHA1: | 59658B55C388BDBA0C3CBD18AD267093074615B6 |
| SHA256: | 4ED892A944F45DE3B4BB5FB12A2FC70F8B6F21F596F407FD99354E9F8ACE5FC2 |
| SSDEEP: | 6144:07qZo7oHMHrzo+hTHeVNUfseG8KtILFHRuf1hwMIVzXuWQu0ufLaScuGcw9:8qZo7oHMHrzL9eTvcHRuh60u2ddcw9 |
MALICIOUS
Application was dropped or rewritten from another process
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Changes settings of System certificates
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Changes the autorun value in the registry
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2856)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3948)
Connects to CnC server
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
AVEMARIA was detected
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Actions looks like stealing of personal data
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 276)
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 276)
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Executed via COM
- OUTLOOK.EXE (PID: 700)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1328)
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Adds / modifies Windows certificates
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Starts CMD.EXE for commands execution
- Notepad.exe (PID: 572)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2856)
Reads the machine GUID from the registry
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Loads DLL from Mozilla Firefox
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 700)
- OUTLOOK.EXE (PID: 276)
Manual execution by user
- WinRAR.exe (PID: 1328)
- WinRAR.exe (PID: 2888)
- SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe (PID: 3680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 2) (100) |
|---|
Total processes
50
Monitored processes
11
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\692c7610-3282-4d26-877d-0e4e17ba61f5.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 572 | "C:\Windows\System32\Notepad.exe" | C:\Windows\System32\Notepad.exe | — | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 700 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.r00" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1744 | reg delete hkcu\Environment /v windir /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1828 | reg delete hkcu\Environment /v windir /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1912 | reg add hkcu\Environment /v windir /d "cmd /c start /min C:\Users\Public\x.bat reg delete hkcu\Environment /v windir /f && REM " | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2856 | cmd /c ""C:\Users\Public\Natso.bat" " | C:\Windows\System32\cmd.exe | — | Notepad.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2888 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.r00" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3680 | "C:\Users\admin\Desktop\SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe" | C:\Users\admin\Desktop\SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 725
Read events
1 707
Write events
994
Delete events
24
Modification events
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (276) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
2
Suspicious files
6
Text files
35
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE1A6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpE3BA.tmp | — | |
MD5:— | SHA256:— | |||
| 700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR178B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp1B17.tmp | — | |
MD5:— | SHA256:— | |||
| 276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\F7U3RPI8\SHIPMENT DOCS#850858001894 Vessel NYK FURANO041 (2).r00\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | C:\Users\admin\AppData\Local\Temp\Cab7064.tmp | — | |
MD5:— | SHA256:— | |||
| 3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | C:\Users\admin\AppData\Local\Temp\Tar7065.tmp | — | |
MD5:— | SHA256:— | |||
| 276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1328.22463\SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | executable | |
MD5:— | SHA256:— | |||
| 276 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
6
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 313 b | whitelisted |
276 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
276 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
— | — | 2.18.233.62:443 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | 84.38.135.151:3670 | story43.ddns.net | DataClub S.A. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cdn.discordapp.com |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |
story43.ddns.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | A Network Trojan was detected | AV TROJAN Ave Maria RAT CnC Response |
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
3680 | SHIPMENT DOCS#850858001894 Vessel NYK FURANO041.exe | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Connection |
2 ETPRO signatures available at the full report