| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/9533206f-54e1-4fff-8d4c-62faeca63bf1 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 11, 2024, 16:24:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | AD2735F096925010A53450CB4178C89E |
| SHA1: | C6D65163C6315A642664F4EAEC0FAE9528549BFE |
| SHA256: | 4E775B5FAFB4E6D89A4694F8694D2B8B540534BD4A52FF42F70095F1C929160E |
| SSDEEP: | 98304:i1DIdhM4/FRL+lnkENnPRPrmImRTlsjR1+8O4hhySd/W83WD3wCyGgd0lprVpXXp:i1DPdJnho |
MALICIOUS
Stealers network behavior
- RelishKitchen.a3x (PID: 4080)
Connects to the CnC server
- svchost.exe (PID: 2256)
Actions looks like stealing of personal data
- RelishKitchen.a3x (PID: 4080)
LUMMA has been detected (SURICATA)
- RelishKitchen.a3x (PID: 4080)
- svchost.exe (PID: 2256)
LUMMA has been detected (YARA)
- RelishKitchen.a3x (PID: 4080)
Changes powershell execution policy (Bypass)
- RelishKitchen.a3x (PID: 4080)
Bypass execution policy to execute commands
- powershell.exe (PID: 2520)
Probably downloads file via BitsAdmin (POWERSHELL)
- powershell.exe (PID: 2520)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 5160)
Changes the autorun value in the registry
- reg.exe (PID: 1156)
SUSPICIOUS
Executable content was dropped or overwritten
- Setup.exe (PID: 5112)
- more.com (PID: 6140)
- RelishKitchen.a3x (PID: 4080)
- EX7PRD39SOBEO0NUL0A5.exe (PID: 4576)
Process drops legitimate windows executable
- Setup.exe (PID: 5112)
The process drops C-runtime libraries
- Setup.exe (PID: 5112)
Starts application with an unusual extension
- Setup.exe (PID: 5112)
- more.com (PID: 6140)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2256)
- RelishKitchen.a3x (PID: 4080)
Starts POWERSHELL.EXE for commands execution
- RelishKitchen.a3x (PID: 4080)
The process executes Powershell scripts
- RelishKitchen.a3x (PID: 4080)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2520)
Starts CMD.EXE for commands execution
- EX7PRD39SOBEO0NUL0A5.exe (PID: 4576)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2572)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 2520)
The process executes via Task Scheduler
- 514D3030303031.exe (PID: 6816)
Found regular expressions for crypto-addresses (YARA)
- 514D3030303031.exe (PID: 6816)
INFO
Reads the computer name
- Setup.exe (PID: 5112)
- more.com (PID: 6140)
- RelishKitchen.a3x (PID: 4080)
- OVM9HNUXBV8CF8Z2SQGJP78S2S.exe (PID: 6356)
- EX7PRD39SOBEO0NUL0A5.exe (PID: 4576)
- 514D3030303031.exe (PID: 6816)
Manual execution by a user
- Setup.exe (PID: 5112)
Creates files or folders in the user directory
- Setup.exe (PID: 5112)
Checks supported languages
- Setup.exe (PID: 5112)
- more.com (PID: 6140)
- RelishKitchen.a3x (PID: 4080)
- EX7PRD39SOBEO0NUL0A5.exe (PID: 4576)
- OVM9HNUXBV8CF8Z2SQGJP78S2S.exe (PID: 6356)
- 514D3030303031.exe (PID: 6816)
Create files in a temporary directory
- Setup.exe (PID: 5112)
- more.com (PID: 6140)
- OVM9HNUXBV8CF8Z2SQGJP78S2S.exe (PID: 6356)
- RelishKitchen.a3x (PID: 4080)
Reads the software policy settings
- RelishKitchen.a3x (PID: 4080)
- 514D3030303031.exe (PID: 6816)
The process uses the downloaded file
- powershell.exe (PID: 2520)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2520)
Creates files in the program directory
- EX7PRD39SOBEO0NUL0A5.exe (PID: 4576)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2520)
Reads the machine GUID from the registry
- 514D3030303031.exe (PID: 6816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:03:22 10:26:52+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.37 |
| CodeSize: | 3617792 |
| InitializedDataSize: | 2067968 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x240ca8 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 13.162.0.5675 |
| ProductVersionNumber: | 13.162.0.5675 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Static library |
| FileSubtype: | - |
| LanguageCode: | English (Canadian) |
| CharacterSet: | Unicode |
| CompanyName: | Electronic Arts |
| FileDescription: | EA |
| FileVersion: | 13, 162, 0, 5675 |
| InternalName: | EA |
| LegalCopyright: | Copyright (c) 2024 |
| LegalTrademarks: | (c) Electronic Arts 2024. All rights reserved. |
| OriginalFileName: | EASteamProxy.exe |
| ProductName: | EA |
| ProductVersion: | 13, 162, 0, 5675 |
Total processes
141
Monitored processes
18
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v 514D3030303031 /t REG_SZ /d C:\ProgramData\514D3030303031.exe /f | C:\Windows\SysWOW64\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2520 | powershell -exec bypass -f "C:\Users\admin\AppData\Local\Temp\L73YKL359GOETH2ZC.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | RelishKitchen.a3x | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | cmd /c "reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v 514D3030303031 /t REG_SZ /d C:\ProgramData\514D3030303031.exe /f" | C:\Windows\SysWOW64\cmd.exe | — | EX7PRD39SOBEO0NUL0A5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2588 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3296 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4080 | C:\Users\admin\AppData\Local\Temp\RelishKitchen.a3x | C:\Users\admin\AppData\Local\Temp\RelishKitchen.a3x | more.com | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
| 4576 | "C:\Users\admin\AppData\Local\Temp\EX7PRD39SOBEO0NUL0A5.exe" | C:\Users\admin\AppData\Local\Temp\EX7PRD39SOBEO0NUL0A5.exe | RelishKitchen.a3x | ||||||||||||
User: admin Company: Яндекс Integrity Level: MEDIUM Description: YandexDiskSetup Exit code: 0 Version: 3.2.41.5053 Modules
| |||||||||||||||
Total events
12 046
Read events
12 044
Write events
2
Delete events
0
Modification events
| (PID) Process: | (1156) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 514D3030303031 |
Value: C:\ProgramData\514D3030303031.exe | |||
| (PID) Process: | (2520) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | InternetFilesCache |
Value: C:\Users\admin\AppData\Roaming\InternetFilesCache\client32.exe | |||
Executable files
13
Suspicious files
4
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6140 | more.com | C:\Users\admin\AppData\Local\Temp\vfhsubgymo | — | |
MD5:— | SHA256:— | |||
| 5112 | Setup.exe | C:\Users\admin\AppData\Roaming\MonWri\qttiso | binary | |
MD5:DD43BEDDF15617D880B65976798B00F5 | SHA256:1D73A3A14562CB043253B568AB9B162584BE7920D18B24DD5B3240AAA9781AB8 | |||
| 5112 | Setup.exe | C:\Users\admin\AppData\Roaming\MonWri\vcruntime140.dll | executable | |
MD5:49C96CECDA5C6C660A107D378FDFC3D4 | SHA256:69320F278D90EFAAEB67E2A1B55E5B0543883125834C812C8D9C39676E0494FC | |||
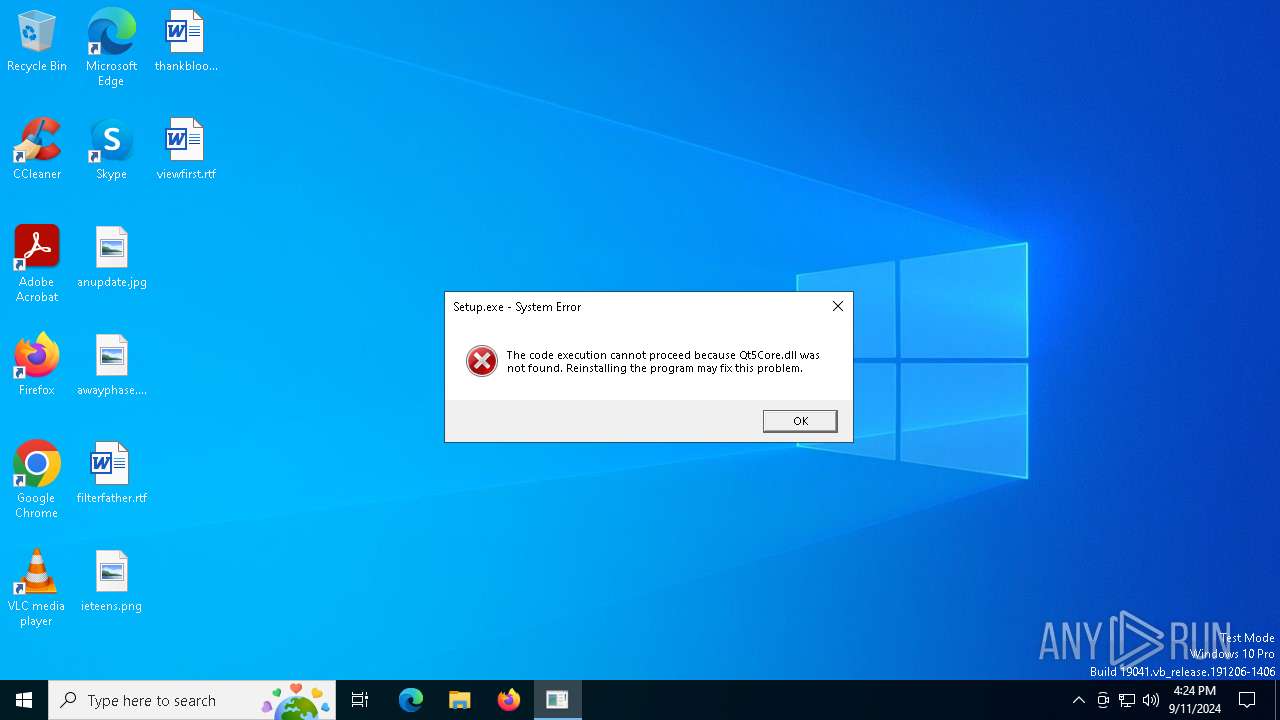
| 5112 | Setup.exe | C:\Users\admin\AppData\Roaming\MonWri\Qt5Network.dll | executable | |
MD5:4D38839EFD84026DEAC6874E686129BA | SHA256:D632D6DCF30C34240B388B0E341EFD8C4EC4EEFFF4160527803E96ECFDB98A3C | |||
| 5112 | Setup.exe | C:\Users\admin\AppData\Roaming\MonWri\msvcp140_1.dll | executable | |
MD5:69D96E09A54FBC5CF92A0E084AB33856 | SHA256:A3A1199DE32BBBC8318EC33E2E1CE556247D012851E4B367FE853A51E74CE4EE | |||
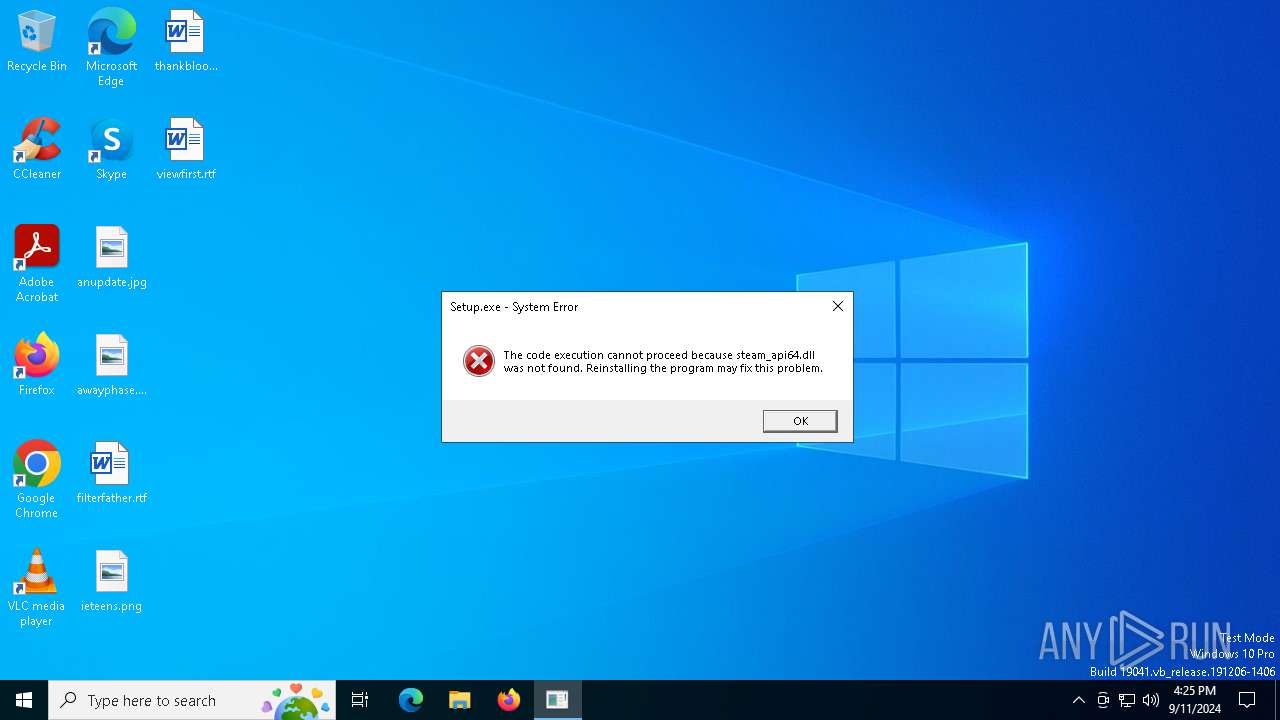
| 5112 | Setup.exe | C:\Users\admin\AppData\Roaming\MonWri\steam_api64.dll | executable | |
MD5:6B4AB6E60364C55F18A56A39021B74A6 | SHA256:1DB3FD414039D3E5815A5721925DD2E0A3A9F2549603C6CAB7C49B84966A1AF3 | |||
| 5112 | Setup.exe | C:\Users\admin\AppData\Roaming\MonWri\libcrypto-1_1-x64.dll | executable | |
MD5:28DEA3E780552EB5C53B3B9B1F556628 | SHA256:52415829D85C06DF8724A3D3D00C98F12BEABF5D6F3CBAD919EC8000841A86E8 | |||
| 4080 | RelishKitchen.a3x | C:\Users\admin\AppData\Local\Temp\OVM9HNUXBV8CF8Z2SQGJP78S2S.exe | executable | |
MD5:7F41FE3E70E6068B9C13C3C8738A8364 | SHA256:73AAC3C537761E667A5DE139F90D5D99CDDE0E153E5C6370DA81E385BC7D46D6 | |||
| 4080 | RelishKitchen.a3x | C:\Users\admin\AppData\Local\Temp\L73YKL359GOETH2ZC.ps1 | text | |
MD5:FD8EDC156E282155F7D2FBA4663530A3 | SHA256:F6D16DB3E818DC771911891F60A40C967676690F90F7EA03F7A2C6172966C881 | |||
| 4080 | RelishKitchen.a3x | C:\Users\admin\AppData\Local\Temp\EX7PRD39SOBEO0NUL0A5.exe | executable | |
MD5:0EA091352DC7A270BECA956BDDB2E3E7 | SHA256:D639E613F76EBE5B3AC06D637A0BD5FE92BE175C243B754F01C82C185CC282D0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
36
DNS requests
21
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1280 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
568 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6124 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1280 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
568 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
weakkysemwmns.shop |
| malicious |
preachstrwnwjw.shop |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (preachstrwnwjw .shop) |
4080 | RelishKitchen.a3x | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
4080 | RelishKitchen.a3x | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (preachstrwnwjw .shop in TLS SNI) |
4080 | RelishKitchen.a3x | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (preachstrwnwjw .shop in TLS SNI) |
4080 | RelishKitchen.a3x | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (preachstrwnwjw .shop in TLS SNI) |
4080 | RelishKitchen.a3x | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (preachstrwnwjw .shop in TLS SNI) |
4080 | RelishKitchen.a3x | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (preachstrwnwjw .shop in TLS SNI) |
4080 | RelishKitchen.a3x | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (preachstrwnwjw .shop in TLS SNI) |
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
4080 | RelishKitchen.a3x | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |