| File name: | Synaptics.exe |
| Full analysis: | https://app.any.run/tasks/42185b43-516e-4cf0-bed5-749f763879c9 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | September 04, 2025, 23:27:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 85E3D4AC5A6EF32FB93764C090EF32B7 |
| SHA1: | ADEDB0AAB26D15CF96F66FDA8B4CFBBDCC15EF52 |
| SHA256: | 4E5CC8CB98584335400D00F0A0803C3E0202761F3FBE50BCAB3858A80DF255E1 |
| SSDEEP: | 12288:j3H6yScLnqOl0r5Zu0LMFbtizFJ6rAPvOxrcg0i7u48m+LXsSl:j3HzLnqOaNMCFJ6kPvOxrcg0i7uF/XsE |
MALICIOUS
XRED mutex has been found
- Synaptics.exe (PID: 6104)
- Synaptics.exe (PID: 4684)
- Synaptics.exe (PID: 2728)
XRED has been detected
- Synaptics.exe (PID: 6104)
Changes the autorun value in the registry
- Synaptics.exe (PID: 6104)
GENERIC has been found (auto)
- ._cache_Synaptics.exe (PID: 4540)
- ._cache_Synaptics.exe (PID: 4540)
AMADEY has been found (auto)
- ._cache_Synaptics.exe (PID: 4540)
STEALC has been detected
- 1.exe (PID: 4768)
XRED has been detected (YARA)
- Synaptics.exe (PID: 4684)
Create files in the Startup directory
- Cloudy.exe (PID: 1816)
HAUSBOMBER has been detected (YARA)
- ._cache_Synaptics.exe (PID: 4540)
Actions looks like stealing of personal data
- 1.exe (PID: 4768)
Steals credentials from Web Browsers
- 1.exe (PID: 4768)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 7340)
SUSPICIOUS
Executable content was dropped or overwritten
- Synaptics.exe (PID: 6104)
- Synaptics.exe (PID: 4684)
- ._cache_Synaptics.exe (PID: 4540)
- Cloudy.exe (PID: 1816)
- sthealthclient.exe (PID: 8036)
- svchost.exe (PID: 8072)
Reads security settings of Internet Explorer
- Synaptics.exe (PID: 6104)
- Synaptics.exe (PID: 4684)
- ._cache_Synaptics.exe (PID: 4540)
- 1.exe (PID: 4768)
- svchost.exe (PID: 8072)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 828)
Starts CMD.EXE for commands execution
- EmmetPROD.exe (PID: 4912)
- svchost.exe (PID: 8072)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 828)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 828)
Potential Corporate Privacy Violation
- ._cache_Synaptics.exe (PID: 4540)
- sthealthclient.exe (PID: 8036)
Connects to unusual port
- ._cache_Synaptics.exe (PID: 4540)
- EmmetPROD.exe (PID: 4912)
- Cloudy.exe (PID: 1816)
- sthealthclient.exe (PID: 8036)
Checks for external IP
- svchost.exe (PID: 2200)
- Cloudy.exe (PID: 1816)
- sthealthclient.exe (PID: 8036)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 828)
Application launched itself
- 1.exe (PID: 2504)
Searches for installed software
- 1.exe (PID: 4768)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 4684)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 4684)
There is functionality for taking screenshot (YARA)
- EmmetPROD.exe (PID: 4912)
- Synaptics.exe (PID: 4684)
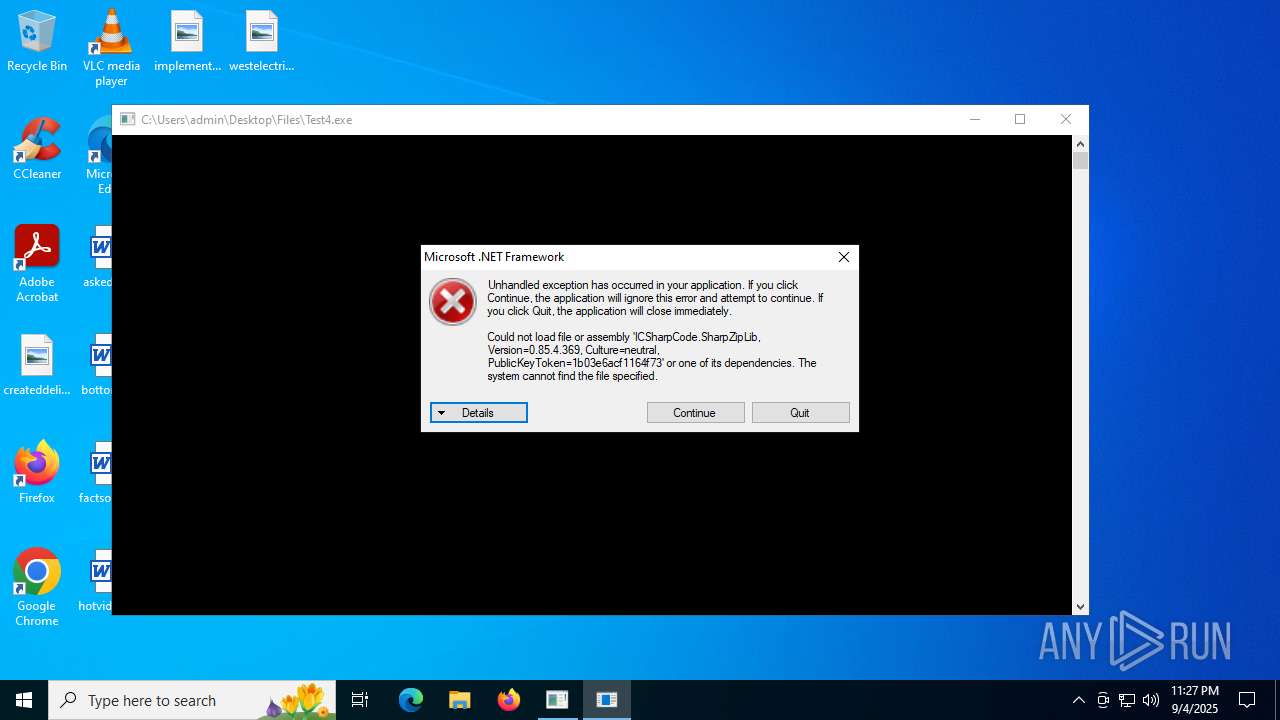
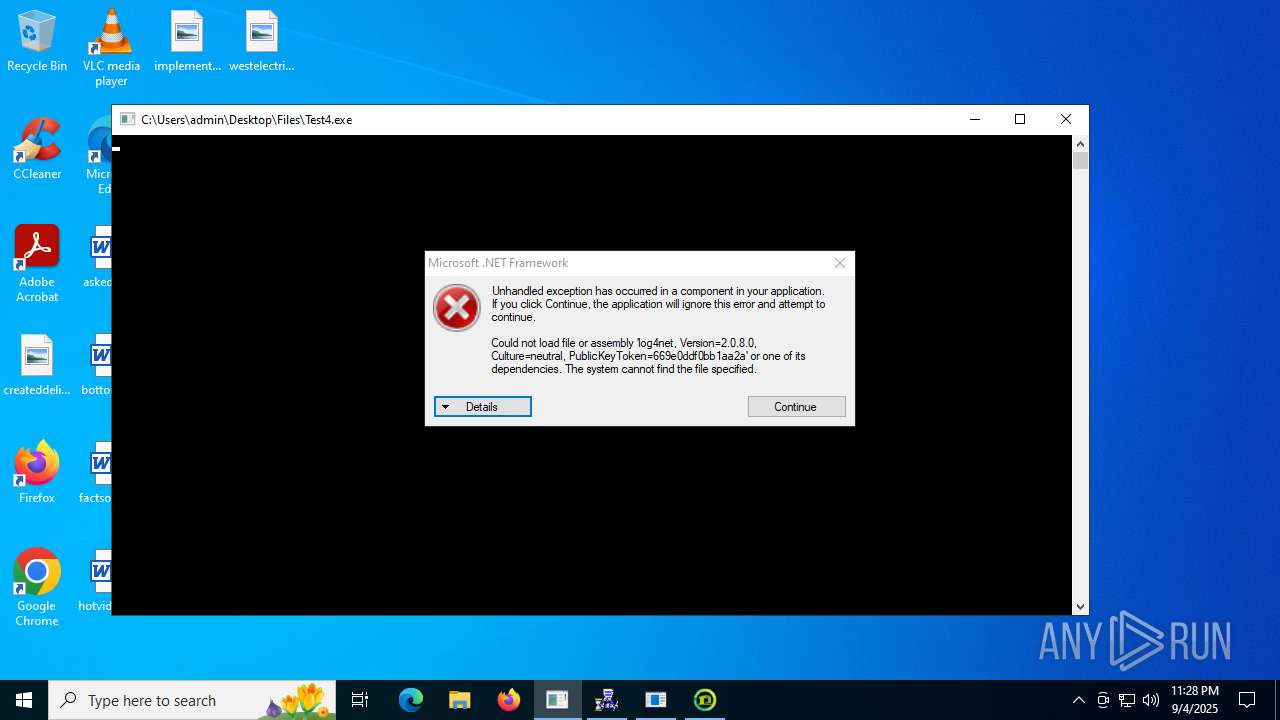
Executes application which crashes
- Acente2Service.exe (PID: 7748)
- AnaMakineProgrami.exe (PID: 7908)
- 1.exe (PID: 4768)
The process creates files with name similar to system file names
- ._cache_Synaptics.exe (PID: 4540)
- svchost.exe (PID: 8072)
Reads the date of Windows installation
- svchost.exe (PID: 8072)
Executing commands from a ".bat" file
- svchost.exe (PID: 8072)
The executable file from the user directory is run by the CMD process
- $77svchost.exe (PID: 7364)
Loads DLL from Mozilla Firefox
- 1.exe (PID: 4768)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7308)
INFO
Checks supported languages
- Synaptics.exe (PID: 6104)
- Synaptics.exe (PID: 4684)
- ._cache_Synaptics.exe (PID: 4540)
- EmmetPROD.exe (PID: 4912)
- 5d418a4b9682b.exe (PID: 6412)
- Cloudy.exe (PID: 1816)
- Update.exe (PID: 7084)
- Test4.exe (PID: 4380)
- 1.exe (PID: 2504)
- Synaptics.exe (PID: 2728)
- 1.exe (PID: 4768)
- Acente2Service.exe (PID: 7748)
- AnaMakineProgrami.exe (PID: 7908)
- hack1226.exe (PID: 8128)
- sthealthclient.exe (PID: 8036)
- svchost.exe (PID: 8072)
- $77svchost.exe (PID: 7364)
Reads the computer name
- Synaptics.exe (PID: 6104)
- ._cache_Synaptics.exe (PID: 4540)
- Synaptics.exe (PID: 4684)
- 5d418a4b9682b.exe (PID: 6412)
- Update.exe (PID: 7084)
- Cloudy.exe (PID: 1816)
- Test4.exe (PID: 4380)
- Synaptics.exe (PID: 2728)
- Acente2Service.exe (PID: 7748)
- AnaMakineProgrami.exe (PID: 7908)
- svchost.exe (PID: 8072)
- hack1226.exe (PID: 8128)
- sthealthclient.exe (PID: 8036)
- 1.exe (PID: 4768)
- $77svchost.exe (PID: 7364)
Process checks computer location settings
- Synaptics.exe (PID: 6104)
- ._cache_Synaptics.exe (PID: 4540)
- svchost.exe (PID: 8072)
Creates files in the program directory
- Synaptics.exe (PID: 6104)
- Synaptics.exe (PID: 4684)
- 1.exe (PID: 4768)
Launching a file from a Registry key
- Synaptics.exe (PID: 6104)
The sample compiled with turkish language support
- Synaptics.exe (PID: 6104)
- Synaptics.exe (PID: 4684)
Reads the machine GUID from the registry
- ._cache_Synaptics.exe (PID: 4540)
- Update.exe (PID: 7084)
- Cloudy.exe (PID: 1816)
- Acente2Service.exe (PID: 7748)
- AnaMakineProgrami.exe (PID: 7908)
- sthealthclient.exe (PID: 8036)
- svchost.exe (PID: 8072)
- $77svchost.exe (PID: 7364)
- Synaptics.exe (PID: 4684)
Reads the software policy settings
- ._cache_Synaptics.exe (PID: 4540)
- Update.exe (PID: 7084)
- WerFault.exe (PID: 7840)
- WerFault.exe (PID: 7964)
- $77svchost.exe (PID: 7364)
- WerFault.exe (PID: 7404)
- Synaptics.exe (PID: 4684)
Disables trace logs
- ._cache_Synaptics.exe (PID: 4540)
- Cloudy.exe (PID: 1816)
- Update.exe (PID: 7084)
- sthealthclient.exe (PID: 8036)
- $77svchost.exe (PID: 7364)
Checks proxy server information
- ._cache_Synaptics.exe (PID: 4540)
- Synaptics.exe (PID: 4684)
- Cloudy.exe (PID: 1816)
- Update.exe (PID: 7084)
- 1.exe (PID: 4768)
- WerFault.exe (PID: 7840)
- WerFault.exe (PID: 7964)
- sthealthclient.exe (PID: 8036)
- $77svchost.exe (PID: 7364)
- WerFault.exe (PID: 7404)
The sample compiled with polish language support
- ._cache_Synaptics.exe (PID: 4540)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4692)
- WMIC.exe (PID: 7016)
- WMIC.exe (PID: 4100)
The sample compiled with chinese language support
- ._cache_Synaptics.exe (PID: 4540)
Create files in a temporary directory
- Test4.exe (PID: 4380)
- Synaptics.exe (PID: 4684)
- svchost.exe (PID: 8072)
Reads Environment values
- Cloudy.exe (PID: 1816)
- Update.exe (PID: 7084)
- $77svchost.exe (PID: 7364)
Manual execution by a user
- Synaptics.exe (PID: 2728)
- Acente2Service.exe (PID: 7748)
- AnaMakineProgrami.exe (PID: 7908)
Creates files or folders in the user directory
- Cloudy.exe (PID: 1816)
- WerFault.exe (PID: 7964)
- WerFault.exe (PID: 7840)
- svchost.exe (PID: 8072)
- WerFault.exe (PID: 7404)
- Synaptics.exe (PID: 4684)
Launching a file from the Startup directory
- Cloudy.exe (PID: 1816)
Compiled with Borland Delphi (YARA)
- conhost.exe (PID: 5248)
- ._cache_Synaptics.exe (PID: 4540)
- Synaptics.exe (PID: 4684)
- EmmetPROD.exe (PID: 4912)
Reads CPU info
- 1.exe (PID: 4768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (96.4) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.3) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 151552 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Turkish |
| CharacterSet: | Windows, Turkish |
| CompanyName: | Synaptics |
| FileDescription: | Synaptics Pointing Device Driver |
| FileVersion: | 1.0.0.4 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Synaptics Pointing Device Driver |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
184
Monitored processes
43
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | C:\WINDOWS\system32\cmd.exe /c wmic computersystem get name, TotalPhysicalMemory /Value && wmic os get caption /Value && wmic path Win32_VideoController get CurrentHorizontalResolution,CurrentVerticalResolution /Value && ipconfig | find "IPv4" | find /N ":" | find "[1]" | C:\Windows\SysWOW64\cmd.exe | — | EmmetPROD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1816 | "C:\Users\admin\Desktop\Files\Cloudy.exe" | C:\Users\admin\Desktop\Files\Cloudy.exe | ._cache_Synaptics.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 1.0.0.0 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\Desktop\._cache_Synaptics.exe" | C:\Users\admin\Desktop\._cache_Synaptics.exe | — | Synaptics.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\Desktop\Files\1.exe" | C:\Users\admin\Desktop\Files\1.exe | — | ._cache_Synaptics.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2728 | C:\ProgramData\Synaptics\Synaptics.exe | C:\ProgramData\Synaptics\Synaptics.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 2848 | schtasks /create /f /sc onlogon /rl highest /tn "$77svchost" /tr '"C:\Users\admin\AppData\Roaming\$77svchost.exe"' | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Test4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3788 | find /N ":" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3932 | ipconfig | C:\Windows\SysWOW64\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 557
Read events
19 451
Write events
103
Delete events
3
Modification events
| (PID) Process: | (6104) Synaptics.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4540) ._cache_Synaptics.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
33
Suspicious files
24
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4684 | Synaptics.exe | C:\Users\admin\AppData\Local\Temp\jGBRBbwI.exe | executable | |
MD5:80421089B46D27AD31BBA48F8946AF3F | SHA256:11F931102F640EA8406D95C2EEBEADD1462FD205BC651DAC57AC1BCAC922E8F5 | |||
| 6104 | Synaptics.exe | C:\Users\admin\Desktop\._cache_Synaptics.exe | executable | |
MD5:2A94F3960C58C6E70826495F76D00B85 | SHA256:2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE | |||
| 4540 | ._cache_Synaptics.exe | C:\Users\admin\Desktop\Files\5d418a4b9682b.exe | executable | |
MD5:A50C917BF6B9E9F0B9E3049B83B69DFB | SHA256:FD3C2DAF5275B250B0A9F0EED230736A3B3255E12B10A1014CF51747CB2D51E0 | |||
| 4540 | ._cache_Synaptics.exe | C:\Users\admin\Desktop\Files\Cloudy.exe | executable | |
MD5:DF8B7081B4E73EC77C418C69F9B6E67B | SHA256:F7E2D59D77B6C034F80A08DCCA6C863C443F0D74B2073DD3925C4E959E5150B6 | |||
| 4540 | ._cache_Synaptics.exe | C:\Users\admin\Desktop\Files\Update.exe | executable | |
MD5:FFC2637ACDE7B6DB1823A2B3304A6C6C | SHA256:35EFC0520B78A1B413AFEE5DBE5D8B0674EEA2ACFC7D943DE70A99B5B2FD92EF | |||
| 4684 | Synaptics.exe | C:\Users\admin\AppData\Local\Temp\MqQ9O1h3.exe | executable | |
MD5:80421089B46D27AD31BBA48F8946AF3F | SHA256:11F931102F640EA8406D95C2EEBEADD1462FD205BC651DAC57AC1BCAC922E8F5 | |||
| 4684 | Synaptics.exe | C:\Users\admin\AppData\Local\Temp\RCXCFBE.tmp | executable | |
MD5:D2198345719D805D26F7EB0B4D1B392E | SHA256:DEC01229A800BBF9AB170FB4FE5320187F410D6AE99A73972CE685B71C7DE60A | |||
| 6104 | Synaptics.exe | C:\ProgramData\Synaptics\RCXCB88.tmp | executable | |
MD5:80421089B46D27AD31BBA48F8946AF3F | SHA256:11F931102F640EA8406D95C2EEBEADD1462FD205BC651DAC57AC1BCAC922E8F5 | |||
| 4380 | Test4.exe | C:\Users\admin\AppData\Local\Temp\game4.log | text | |
MD5:26695B173BBBE08DF418B7823CA617D8 | SHA256:5211BD8EE3AB123A75AEB775F196967820E086FB437AE13EE47656E850EE2E6C | |||
| 6104 | Synaptics.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:85E3D4AC5A6EF32FB93764C090EF32B7 | SHA256:4E5CC8CB98584335400D00F0A0803C3E0202761F3FBE50BCAB3858A80DF255E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
53
DNS requests
30
Threats
50
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4912 | EmmetPROD.exe | GET | 101 | 141.147.43.219:3000 | http://141.147.43.219:3000/socket.io/?EIO=4&transport=websocket&t=1757028447 | unknown | — | — | malicious |
4540 | ._cache_Synaptics.exe | GET | 200 | 141.147.43.219:3000 | http://141.147.43.219:3000/ftp/EmmetPROD.exe | unknown | — | — | malicious |
4540 | ._cache_Synaptics.exe | GET | 200 | 31.145.124.122:80 | http://www.teknoarge.com/update/ana/Update.exe | unknown | — | — | unknown |
1816 | Cloudy.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
4540 | ._cache_Synaptics.exe | GET | 200 | 122.188.44.51:80 | http://src1.minibai.com/uploads/thirdupload/5d418a4b9682b.exe | unknown | — | — | malicious |
4540 | ._cache_Synaptics.exe | GET | 301 | 140.82.121.3:80 | http://github.com/JustJZero/ahh/raw/refs/heads/main/Cloudy.exe | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.21:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4540 | ._cache_Synaptics.exe | GET | 200 | 176.46.152.47:80 | http://176.46.152.47/1.exe | unknown | — | — | malicious |
4540 | ._cache_Synaptics.exe | GET | 200 | 47.104.173.216:9876 | http://47.104.173.216:9876/sthealthclient.exe | unknown | — | — | unknown |
4684 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1964 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4540 | ._cache_Synaptics.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
4540 | ._cache_Synaptics.exe | 141.147.43.219:3000 | — | ORACLE-BMC-31898 | DE | malicious |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4912 | EmmetPROD.exe | 141.147.43.219:3000 | — | ORACLE-BMC-31898 | DE | malicious |
4684 | Synaptics.exe | 69.42.215.252:80 | freedns.afraid.org | AWKNET | US | whitelisted |
4540 | ._cache_Synaptics.exe | 122.188.44.51:80 | src1.minibai.com | CHINA UNICOM China169 Backbone | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
src1.minibai.com |
| malicious |
xred.mooo.com |
| malicious |
freedns.afraid.org |
| whitelisted |
www.teknoarge.com |
| unknown |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4540 | ._cache_Synaptics.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4540 | ._cache_Synaptics.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4540 | ._cache_Synaptics.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4540 | ._cache_Synaptics.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
4540 | ._cache_Synaptics.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
4540 | ._cache_Synaptics.exe | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
4540 | ._cache_Synaptics.exe | Not Suspicious Traffic | INFO [ANY.RUN] Socket.IO requests event-based bidirectional communication via HTTP |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to Abused Domain *.mooo.com |
4540 | ._cache_Synaptics.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4540 | ._cache_Synaptics.exe | Misc activity | ET INFO Packed Executable Download |
Process | Message |
|---|---|
._cache_Synaptics.exe | An exception occurred during a WebClient request.
|