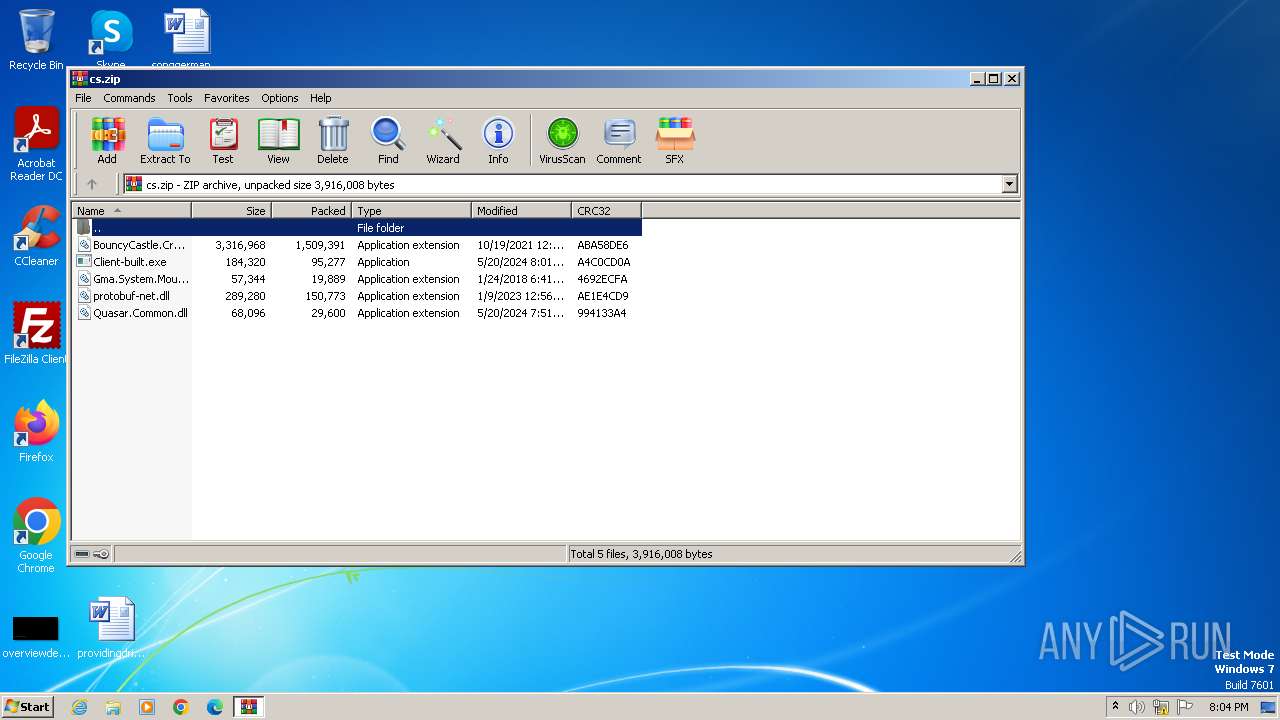
| File name: | cs.zip |
| Full analysis: | https://app.any.run/tasks/1460bd8d-6a58-4a03-b14f-0a506d75d876 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 20, 2024, 19:04:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5007265C9838ED4E956E40113E13F64C |
| SHA1: | 4D2619FC8B107EEA9D0445BDD407E421424EB76C |
| SHA256: | 4E3A4FC478406E74D5C1E7E2CAD0DDC7BBB6E0778D4C9D6412B25575F6CD5359 |
| SSDEEP: | 98304:StC2LhpY69QIadUG2E7PJeKHS12xsKjFwbbYEUcoMWLhkXGXg2v0HlIv8pBtyaz1:Uwb7a8FU |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3988)
Changes the autorun value in the registry
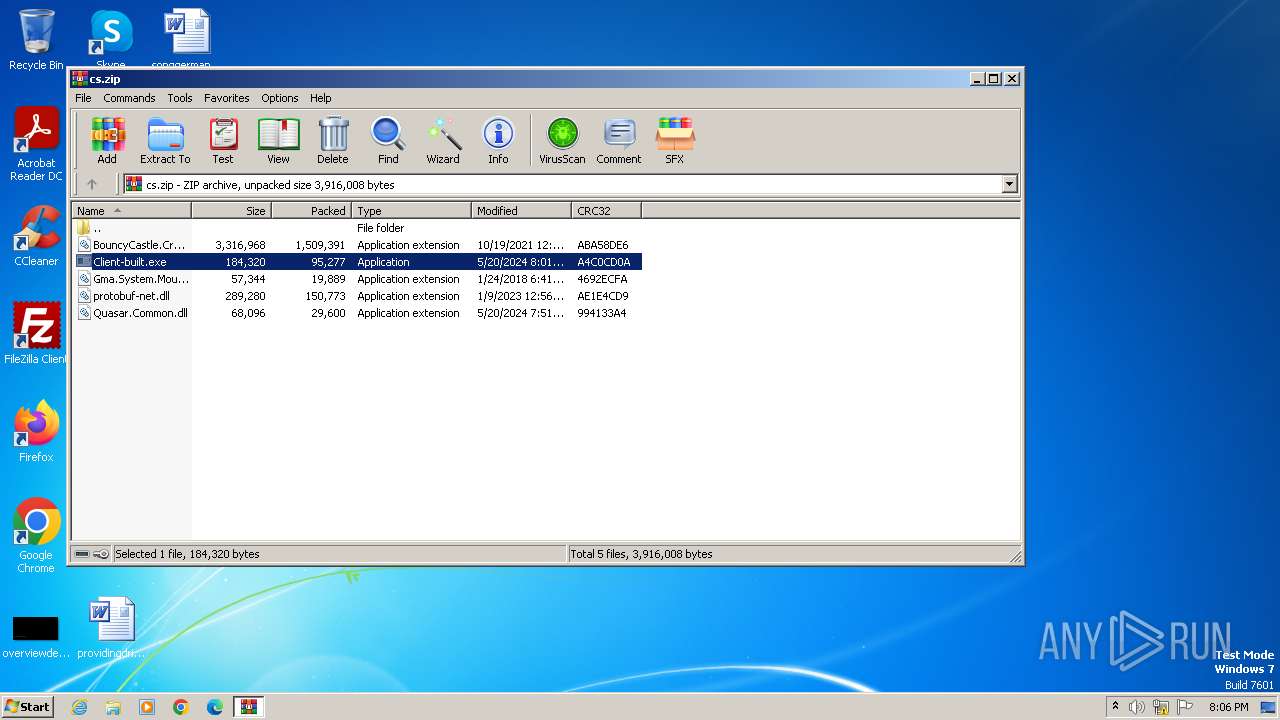
- Client-built.exe (PID: 4076)
QUASAR has been detected (YARA)
- Client-built.exe (PID: 4076)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3988)
Reads settings of System Certificates
- Client-built.exe (PID: 4076)
Connects to unusual port
- Client-built.exe (PID: 4076)
Reads the Internet Settings
- Client-built.exe (PID: 4076)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3988)
Checks supported languages
- Client-built.exe (PID: 4076)
- Client-built.exe (PID: 928)
- wmpnscfg.exe (PID: 1440)
Reads the computer name
- Client-built.exe (PID: 4076)
- Client-built.exe (PID: 928)
- wmpnscfg.exe (PID: 1440)
Reads the machine GUID from the registry
- Client-built.exe (PID: 4076)
- Client-built.exe (PID: 928)
Reads Environment values
- Client-built.exe (PID: 4076)
- Client-built.exe (PID: 928)
Reads the software policy settings
- Client-built.exe (PID: 4076)
Manual execution by a user
- wmpnscfg.exe (PID: 1440)
Create files in a temporary directory
- Client-built.exe (PID: 4076)
Disables trace logs
- Client-built.exe (PID: 4076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:21 03:01:48 |
| ZipCRC: | 0xa4c0cd0a |
| ZipCompressedSize: | 95277 |
| ZipUncompressedSize: | 184320 |
| ZipFileName: | Client-built.exe |
Total processes
36
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28913\Client-built.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28913\Client-built.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 2 Version: 1.4.1 Modules
| |||||||||||||||
| 1440 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3988 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\cs.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28854\Client-built.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28854\Client-built.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Version: 1.4.1 Modules
| |||||||||||||||
Total events
9 062
Read events
9 002
Write events
60
Delete events
0
Modification events
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\cs.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
10
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28854\Gma.System.MouseKeyHook.dll | executable | |
MD5:BFB3BD1CB571360435100BFA6ED2B997 | SHA256:A67A424013544C8270C12633E2E1E287CD5CF0B3F2E81E8D8204B37A03DA59EF | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28913\Gma.System.MouseKeyHook.dll | executable | |
MD5:BFB3BD1CB571360435100BFA6ED2B997 | SHA256:A67A424013544C8270C12633E2E1E287CD5CF0B3F2E81E8D8204B37A03DA59EF | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28854\protobuf-net.dll | executable | |
MD5:ABC82AE4F579A0BBFA2A93DB1486EB38 | SHA256:CA6608346291EC82EE4ACF8017C90E72DB2EE7598015F695120C328D25319EC6 | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28913\Client-built.exe | executable | |
MD5:888515F712E934E5A2E2CF02264C3EBB | SHA256:08D360BD263592D9A63A54CEF91AAD7FBC26D9BCD0B373FF96762E4215CFDBD0 | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28854\Quasar.Common.dll | executable | |
MD5:7696A6D8083ED64F35B978B1B22F7DE6 | SHA256:618F9E810DC1B7D30D933716804C821A79D14C197E3A713BBF02E8ABCD1BAB2B | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3988.28854\BouncyCastle.Crypto.dll | executable | |
MD5:0CF454B6ED4D9E46BC40306421E4B800 | SHA256:E51721DC0647F4838B1ABC592BD95FD8CB924716E8A64F83D4B947821FA1FA42 | |||
| 4076 | Client-built.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:427D429168B95EC45B652F69EF38A330 | SHA256:9E765994CCC43B1CF97A3A9E4829C57886FA8FD7AFE64055CF79F170544FDC19 | |||
| 4076 | Client-built.exe | C:\Users\admin\AppData\Local\Temp\TarC755.tmp | cat | |
MD5:435A9AC180383F9FA094131B173A2F7B | SHA256:67DC37ED50B8E63272B49A254A6039EE225974F1D767BB83EB1FD80E759A7C34 | |||
| 4076 | Client-built.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 4076 | Client-built.exe | C:\Users\admin\AppData\Local\Temp\CabC754.tmp | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4076 | Client-built.exe | GET | 200 | 213.155.157.155:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?848da376213f7aca | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4076 | Client-built.exe | 38.55.186.187:6000 | — | 24.hk global BGP | US | unknown |
4076 | Client-built.exe | 213.155.157.155:80 | ctldl.windowsupdate.com | Telia Company AB | SE | unknown |
4076 | Client-built.exe | 195.201.57.90:443 | ipwho.is | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ipwho.is |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
1088 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
— | — | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (GCM_SHA384) |