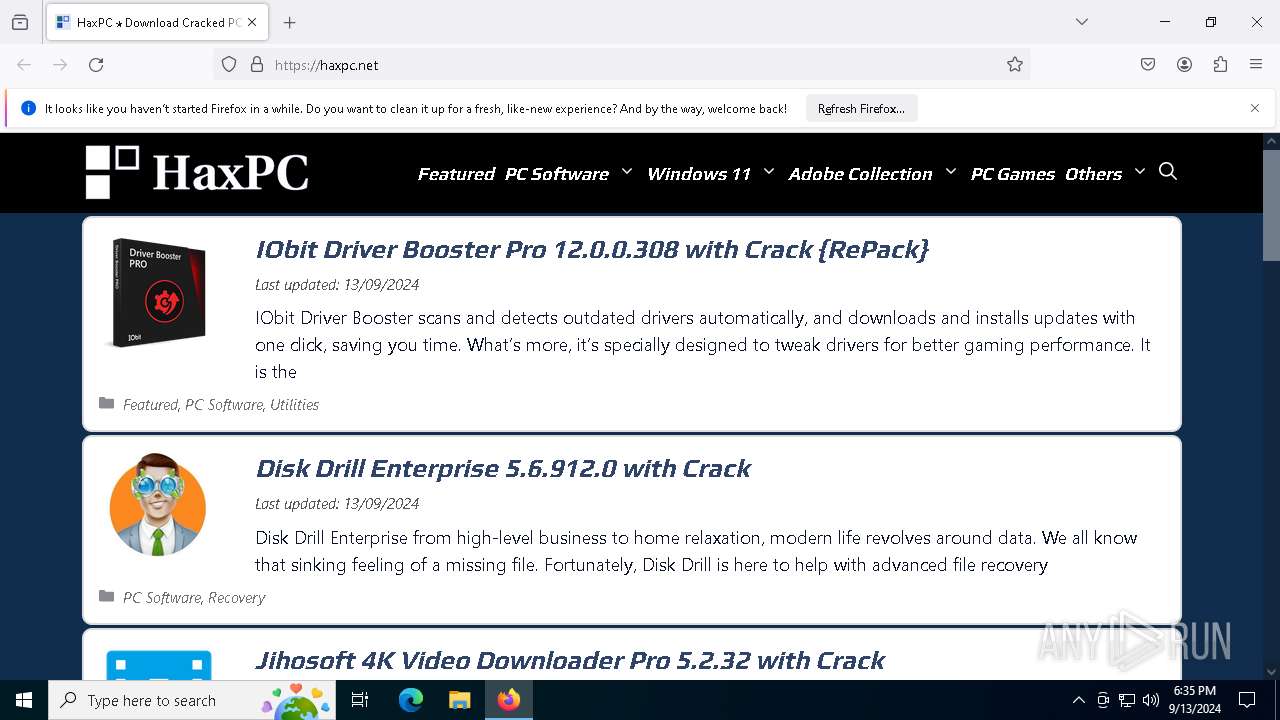
| URL: | haxpc.net |
| Full analysis: | https://app.any.run/tasks/09f5678f-8511-4fcd-87b8-af4c4e622cfc |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 13, 2024, 18:35:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 949ED561C52DFA8A18A9DB7FE8C9BF85 |
| SHA1: | EBA5405E30E663A51548318E0D859C1CCF05F6E5 |
| SHA256: | 4DEF8755A0C2341BC320E33E407BD65465BB615C8E265E70ADADFB956B43A430 |
| SSDEEP: | 3:B0n:B0n |
MALICIOUS
LUMMA has been detected (YARA)
- SearchIndexer.exe (PID: 3568)
Stealers network behavior
- SearchIndexer.exe (PID: 3568)
LUMMA has been detected (SURICATA)
- SearchIndexer.exe (PID: 3568)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1452)
Executable content was dropped or overwritten
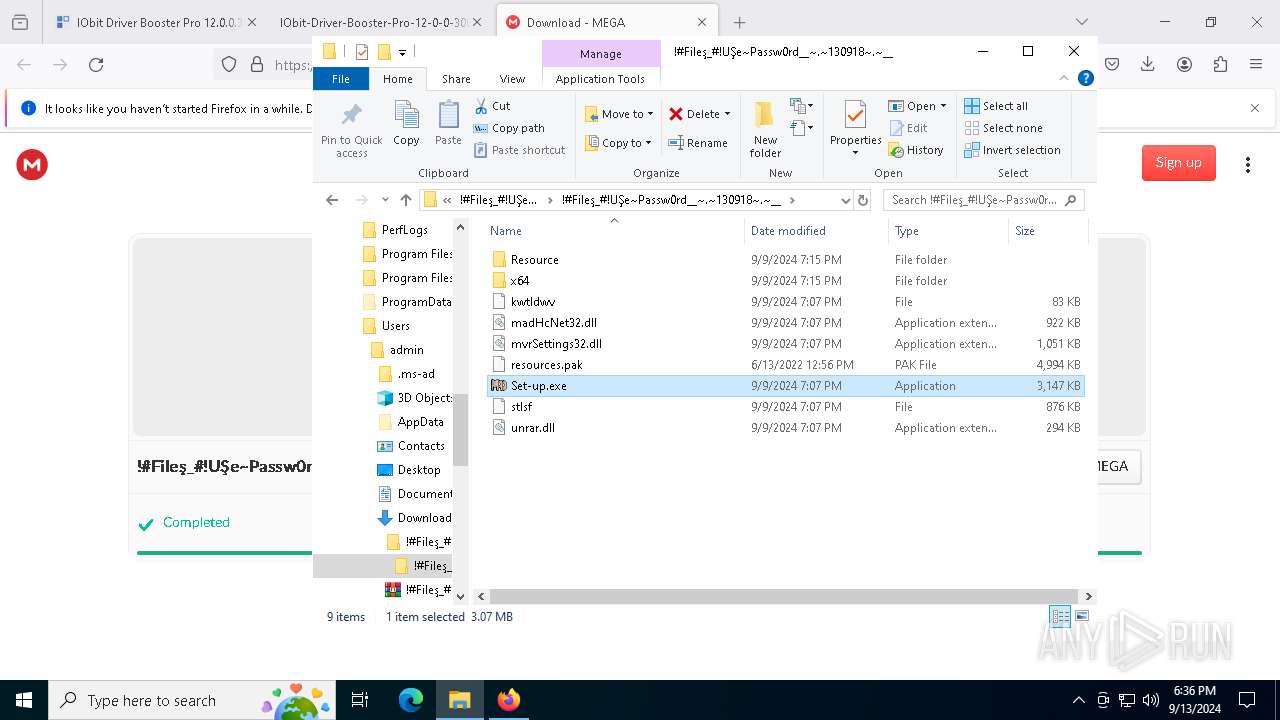
- Set-up.exe (PID: 2524)
Starts application with an unusual extension
- Set-up.exe (PID: 2524)
INFO
Application launched itself
- firefox.exe (PID: 5164)
- firefox.exe (PID: 2232)
The process uses the downloaded file
- WinRAR.exe (PID: 2112)
- firefox.exe (PID: 5164)
- WinRAR.exe (PID: 1452)
Manual execution by a user
- WinRAR.exe (PID: 2112)
- WinRAR.exe (PID: 1452)
- Set-up.exe (PID: 2524)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1452)
- firefox.exe (PID: 5164)
Checks supported languages
- Set-up.exe (PID: 2524)
- more.com (PID: 6256)
Reads the computer name
- Set-up.exe (PID: 2524)
- more.com (PID: 6256)
Creates files or folders in the user directory
- Set-up.exe (PID: 2524)
Create files in a temporary directory
- Set-up.exe (PID: 2524)
- more.com (PID: 6256)
Reads the software policy settings
- SearchIndexer.exe (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(3568) SearchIndexer.exe
C2 (9)stryyridomwn.shop
charistmatwio.shop
grassemenwji.shop
complainnykso.shop
ignoracndwko.shop
basedsymsotp.shop
stitchmiscpaew.shop
preachstrwnwjw.shop
commisionipwn.shop
Total processes
145
Monitored processes
20
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
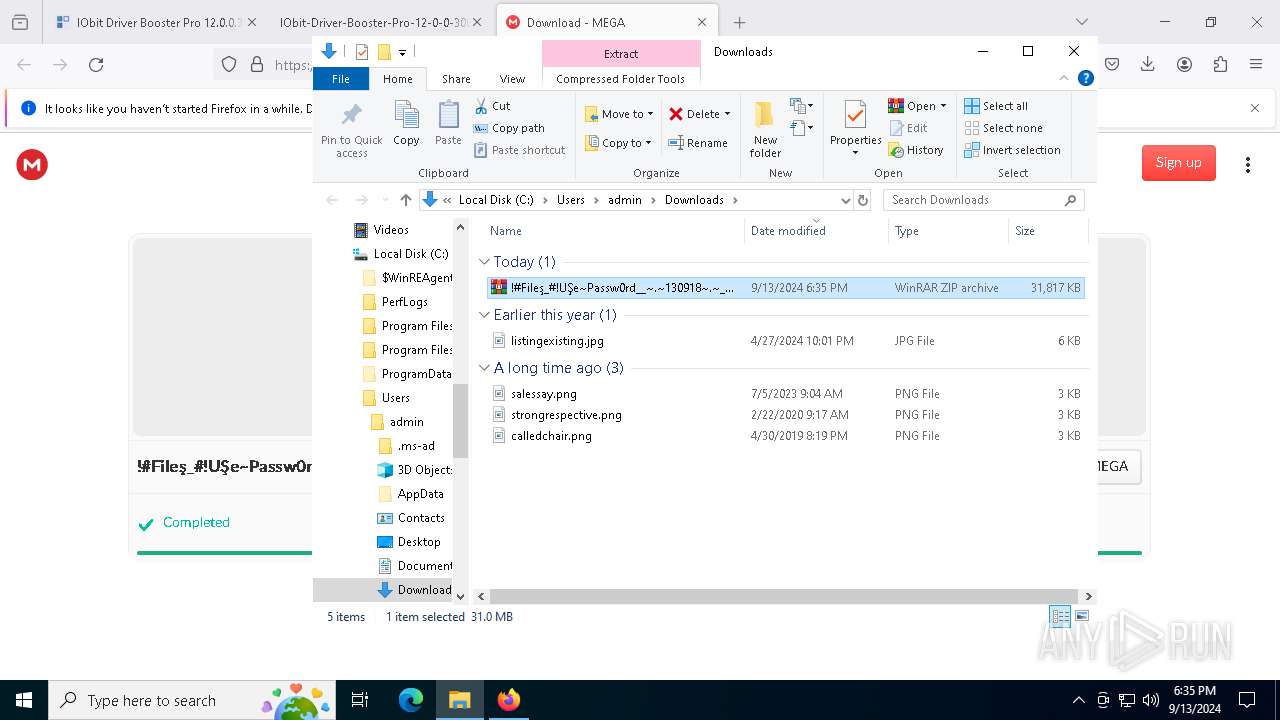
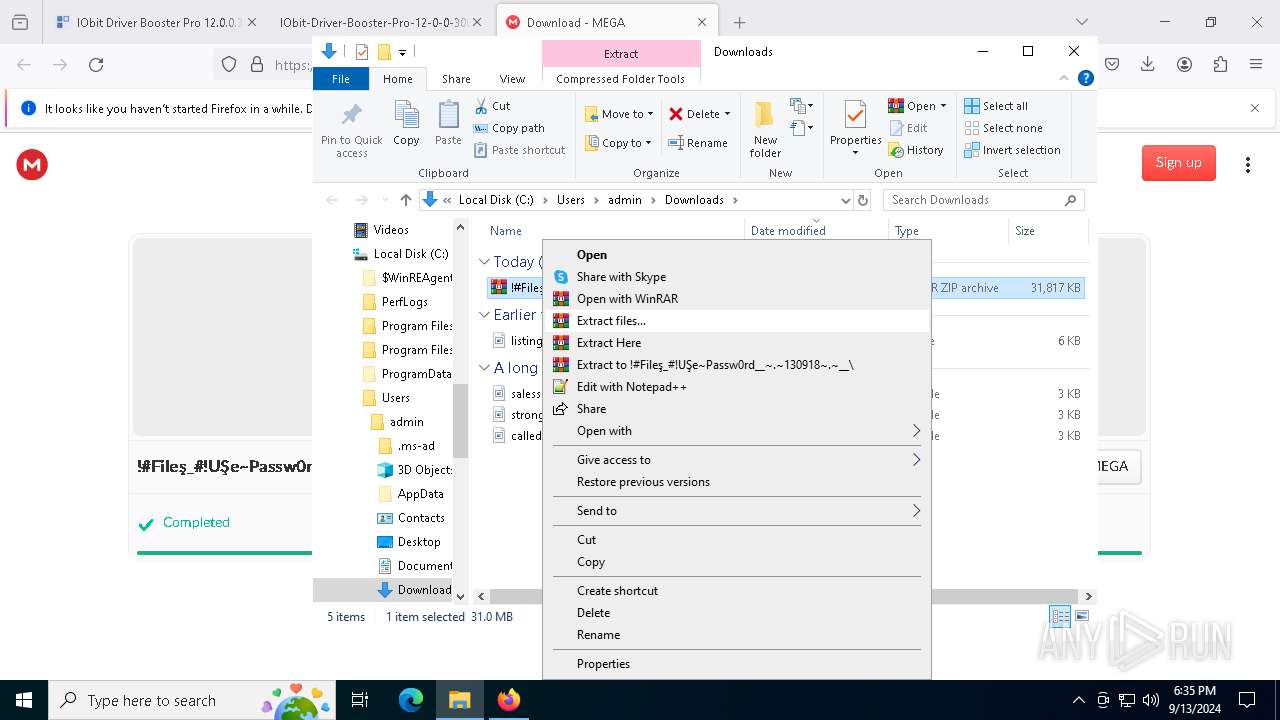
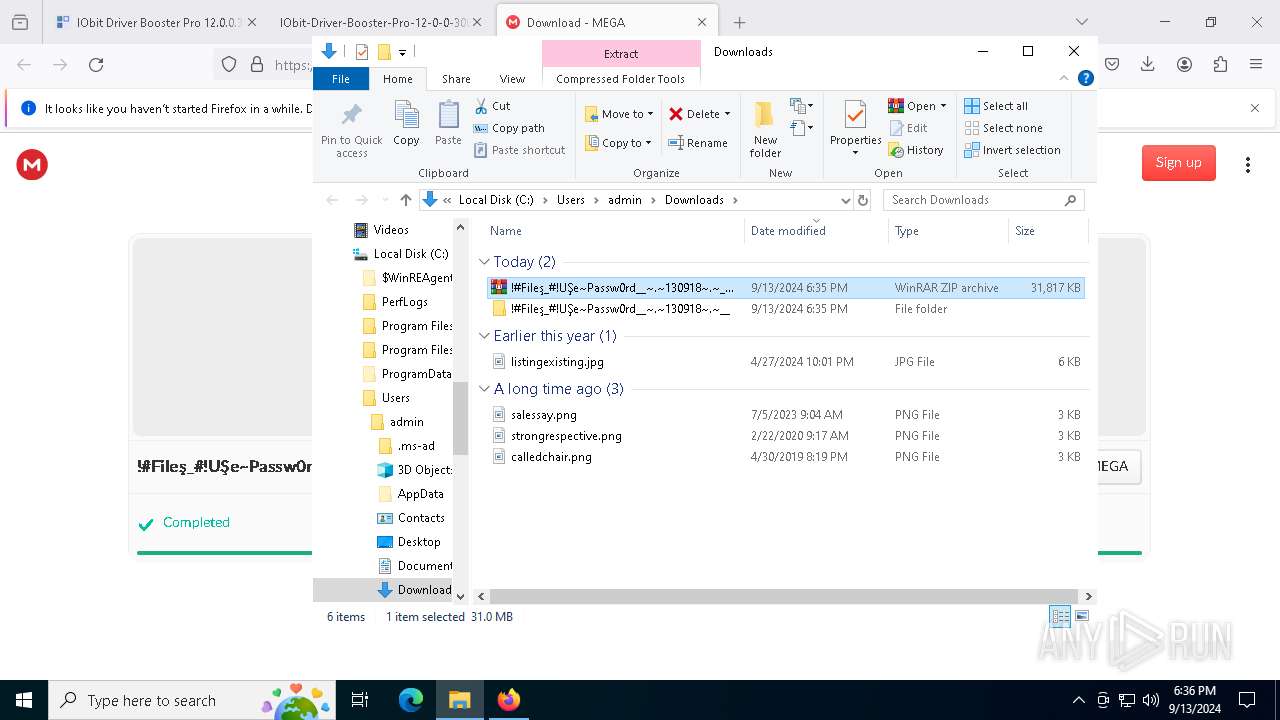
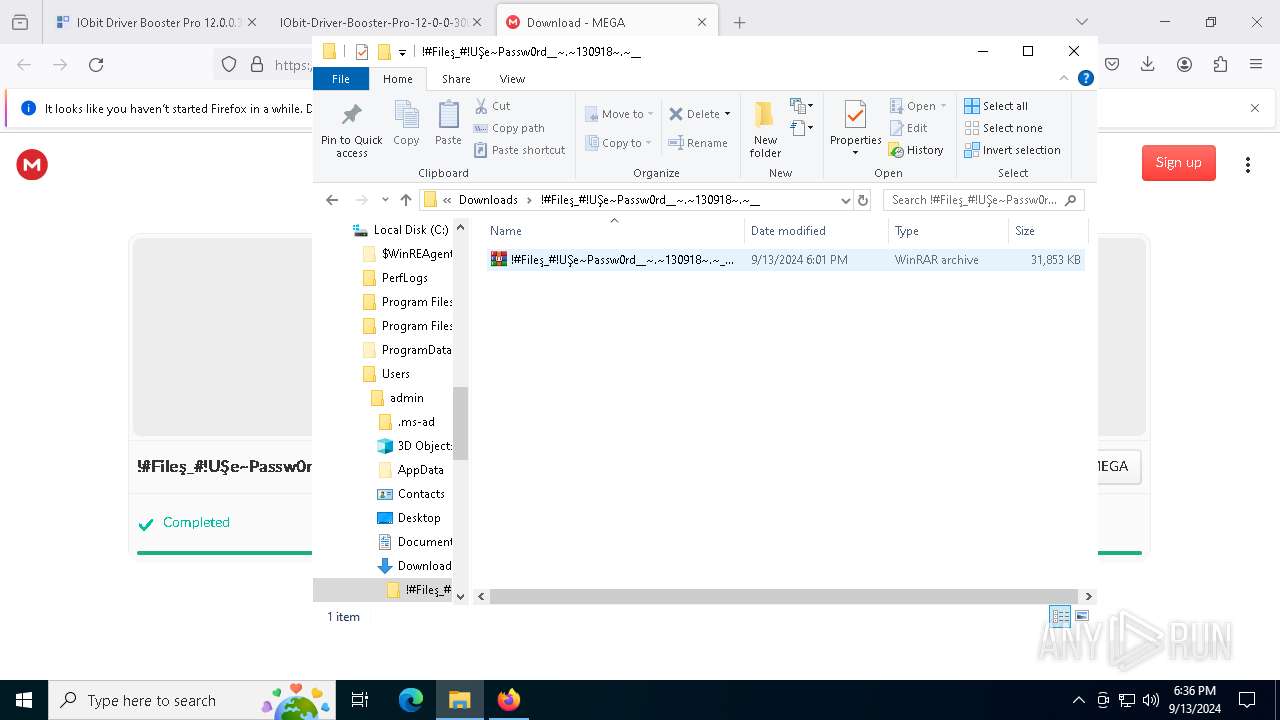
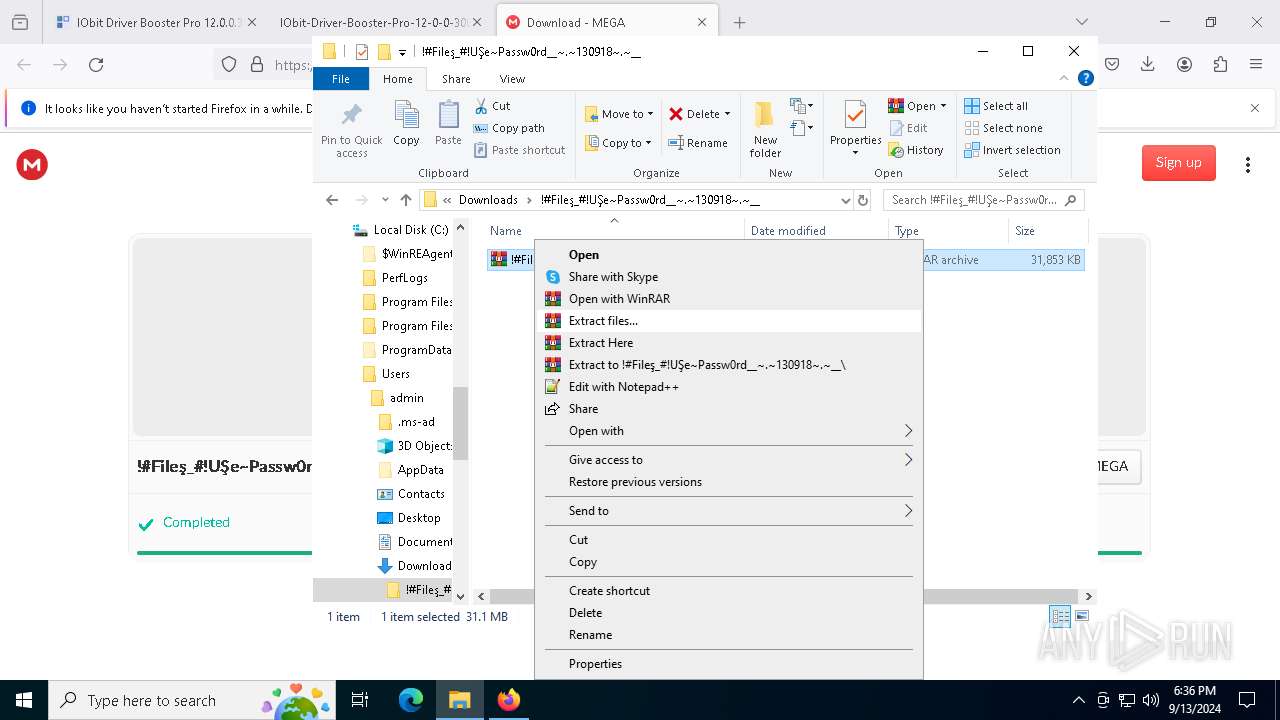
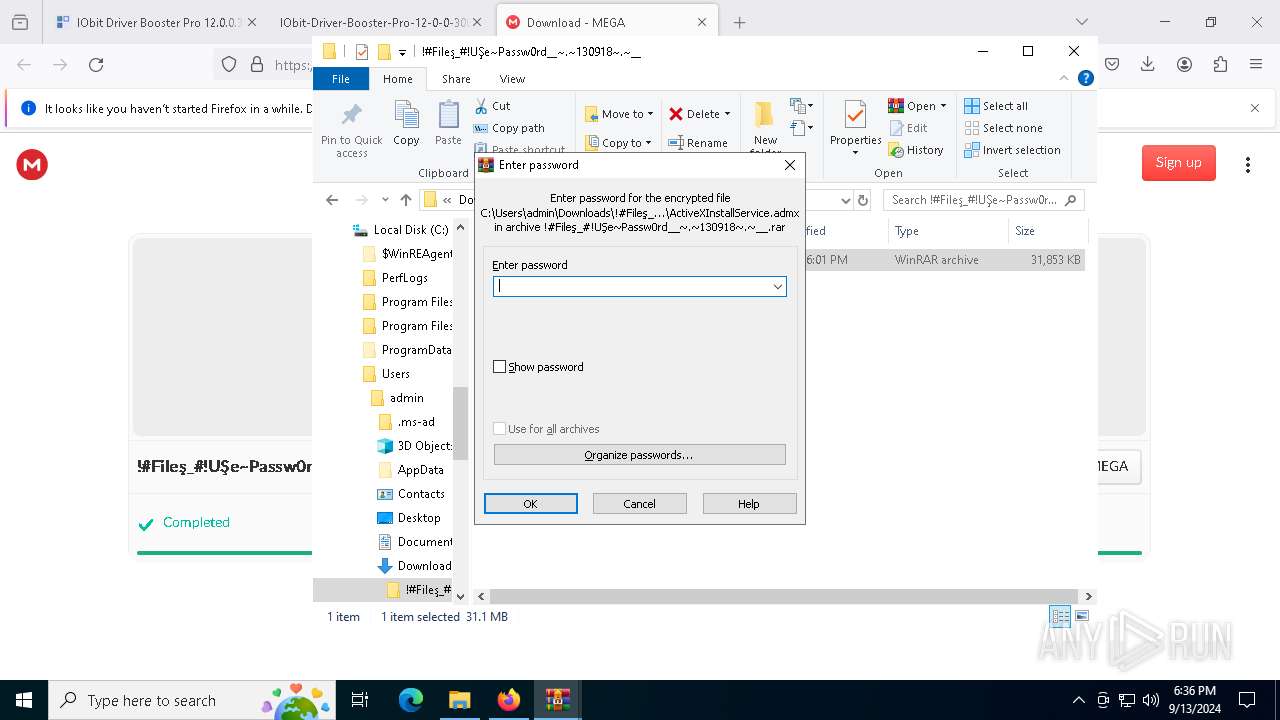
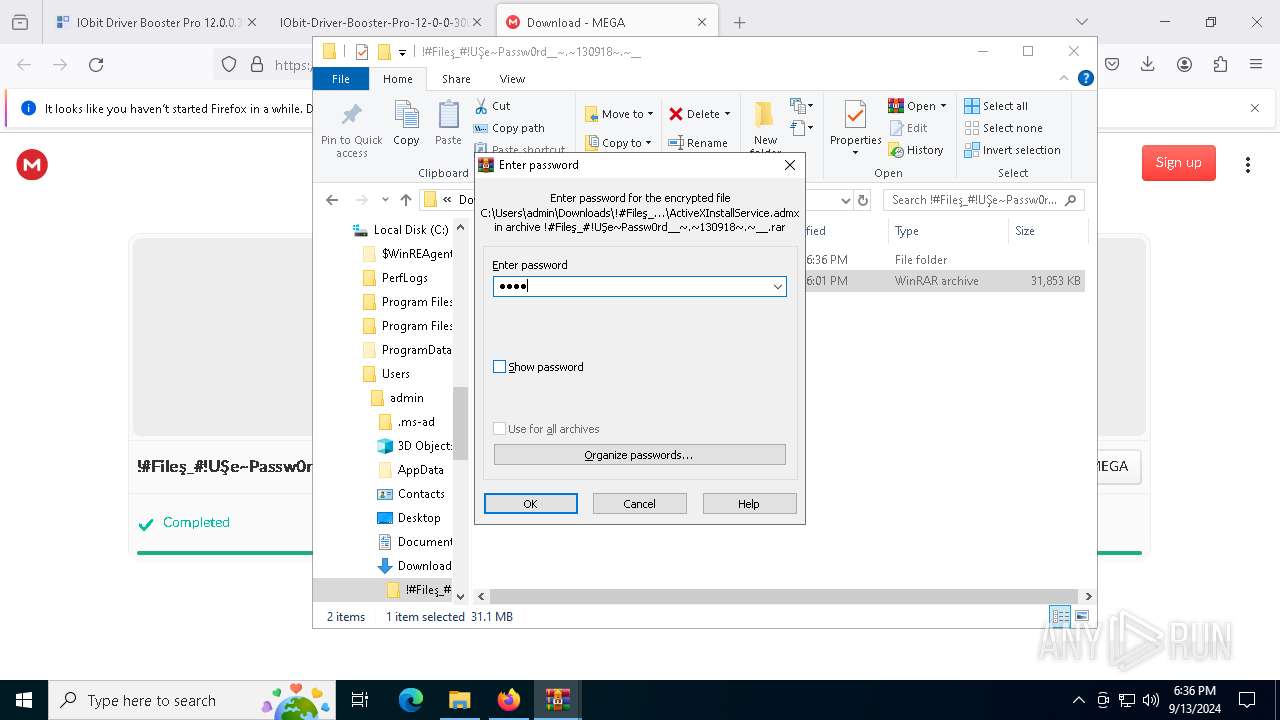
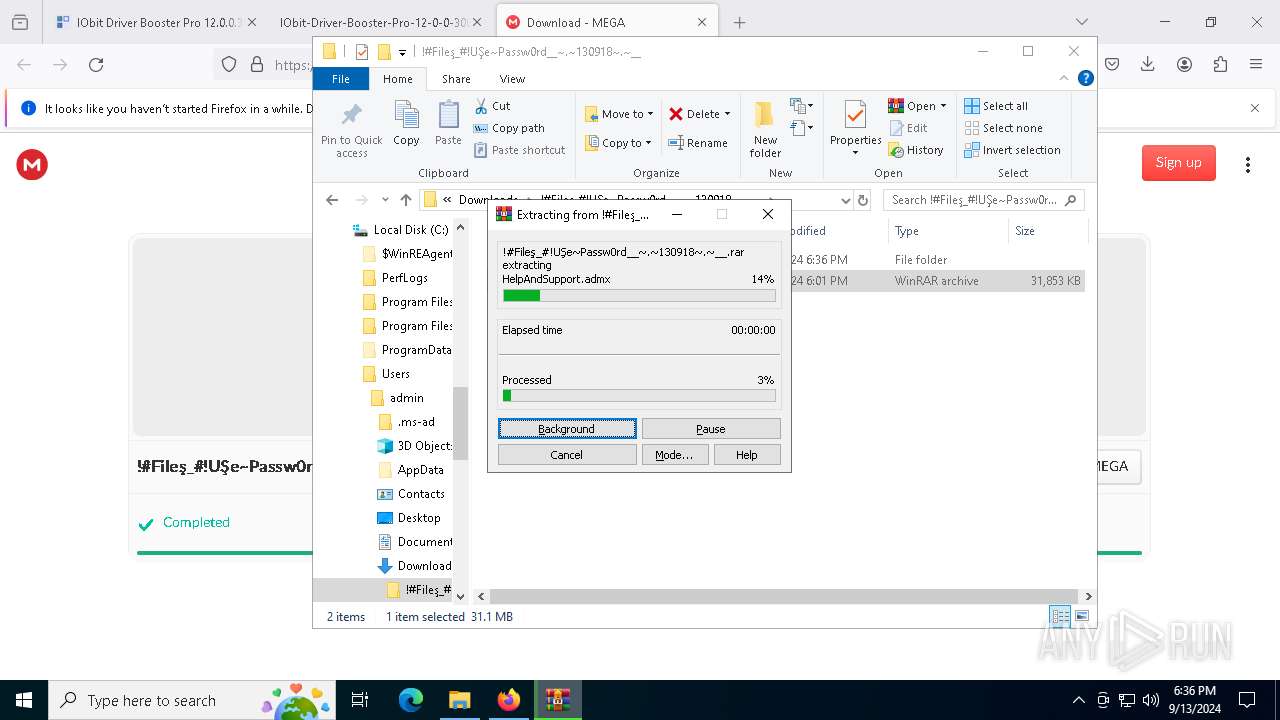
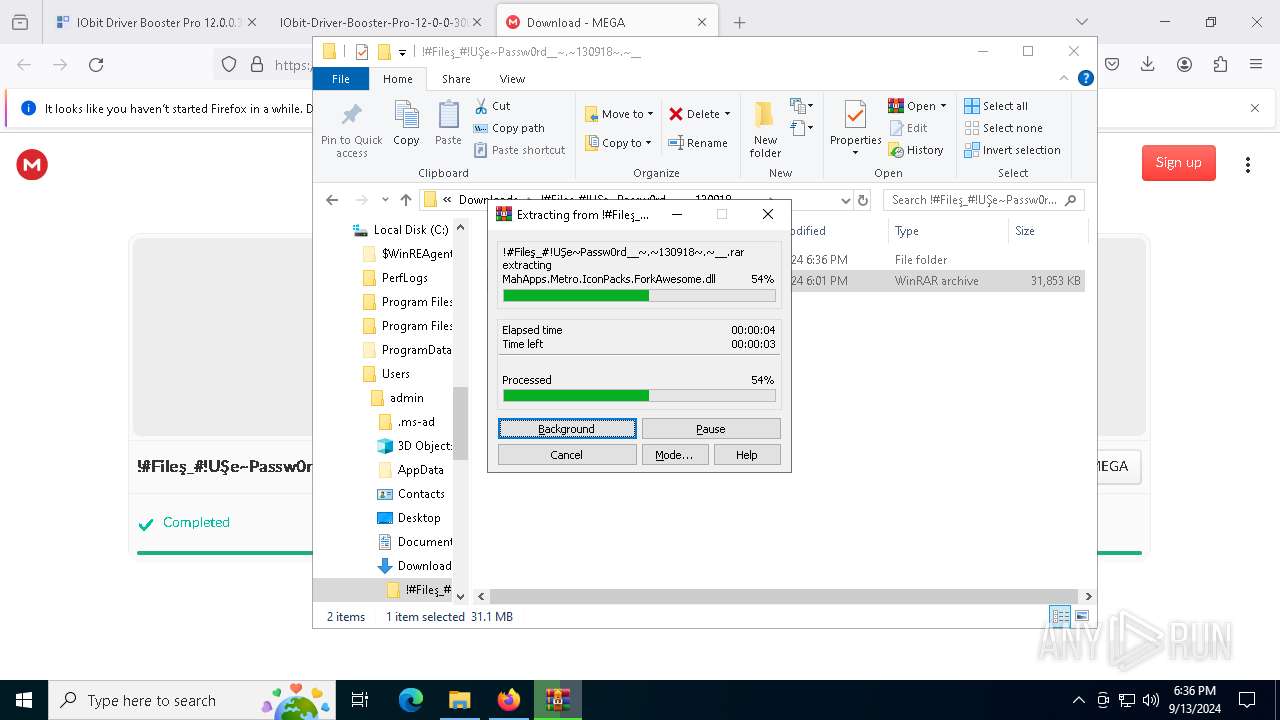
| 1452 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__.rar" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2112 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
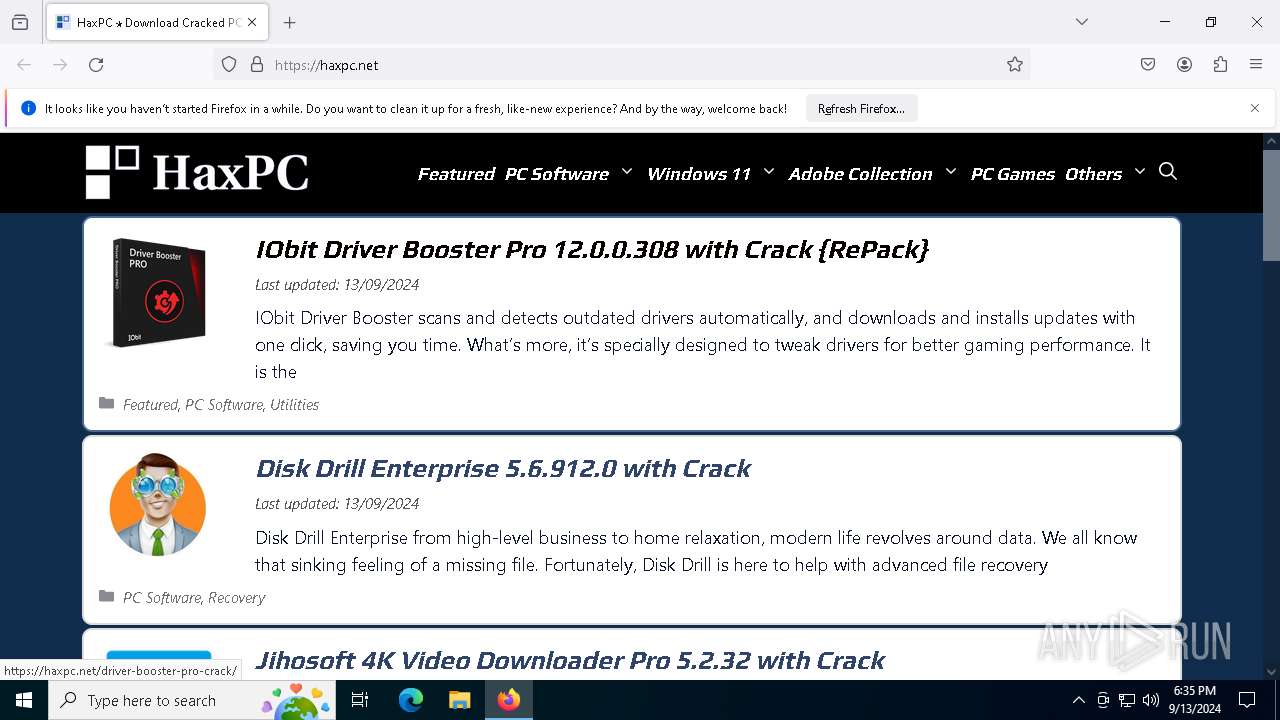
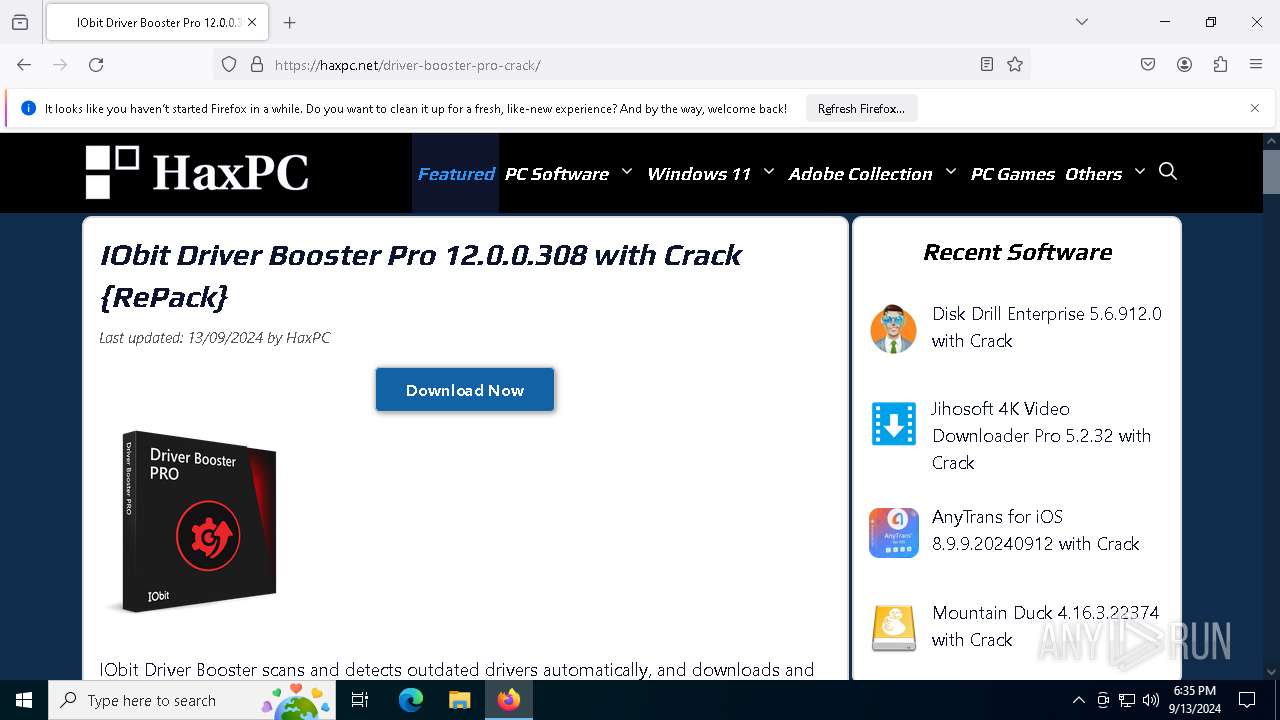
| 2232 | "C:\Program Files\Mozilla Firefox\firefox.exe" "haxpc.net" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2508 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\Downloads\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__\Set-up.exe" | C:\Users\admin\Downloads\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__\Set-up.exe | explorer.exe | ||||||||||||
User: admin Company: madshi.net Integrity Level: HIGH Description: mad* home cinema control Exit code: 1 Version: 1.1.21.0 Modules
| |||||||||||||||
| 3412 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1796 -parentBuildID 20240213221259 -prefsHandle 1736 -prefMapHandle 1728 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {29704ff3-4155-42a0-a7c4-11bb91115856} 5164 "\\.\pipe\gecko-crash-server-pipe.5164" 216d72c4c10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 | |||||||||||||||
| 3568 | C:\WINDOWS\SysWOW64\SearchIndexer.exe | C:\Windows\SysWOW64\SearchIndexer.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.0.19041.3758 (WinBuild.160101.0800) Modules
Lumma(PID) Process(3568) SearchIndexer.exe C2 (9)stryyridomwn.shop charistmatwio.shop grassemenwji.shop complainnykso.shop ignoracndwko.shop basedsymsotp.shop stitchmiscpaew.shop preachstrwnwjw.shop commisionipwn.shop | |||||||||||||||
| 5164 | "C:\Program Files\Mozilla Firefox\firefox.exe" haxpc.net | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6168 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4384 -childID 10 -isForBrowser -prefsHandle 7072 -prefMapHandle 7100 -prefsLen 31242 -prefMapSize 244343 -jsInitHandle 1232 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {241428d0-b2e2-4a65-9c61-3f58af1ab27d} 5164 "\\.\pipe\gecko-crash-server-pipe.5164" 216deefe4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
8 078
Read events
8 051
Write events
13
Delete events
14
Modification events
| (PID) Process: | (5164) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\!#Fileş_#!UŞe~Passw0rd__~.~130918~.~__ | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
57
Suspicious files
221
Text files
434
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:7A97B8DBC4F98D175F958C00F463A52A | SHA256:92074D2ED1AA1FD621287E35DB9EF1AE3DC04777EFAE5F09E7A3B4534C201548 | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:C4E7C74E3DAA7543372F8CAD6B3AED61 | SHA256:A96AFEE211D625736CAE842A2A4FD085293A98ECF21E7D806EAC5A2EEE464AE9 | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:7A97B8DBC4F98D175F958C00F463A52A | SHA256:92074D2ED1AA1FD621287E35DB9EF1AE3DC04777EFAE5F09E7A3B4534C201548 | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5164 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\AlternateServices.bin | binary | |
MD5:E2CFB96279CEEC078207E0BBD643318A | SHA256:E29696C3638492459AA4E769C3E1426F9BFBA70B05852020CDFBE348B5AE1868 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
116
DNS requests
161
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/XjA | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.61:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.61:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
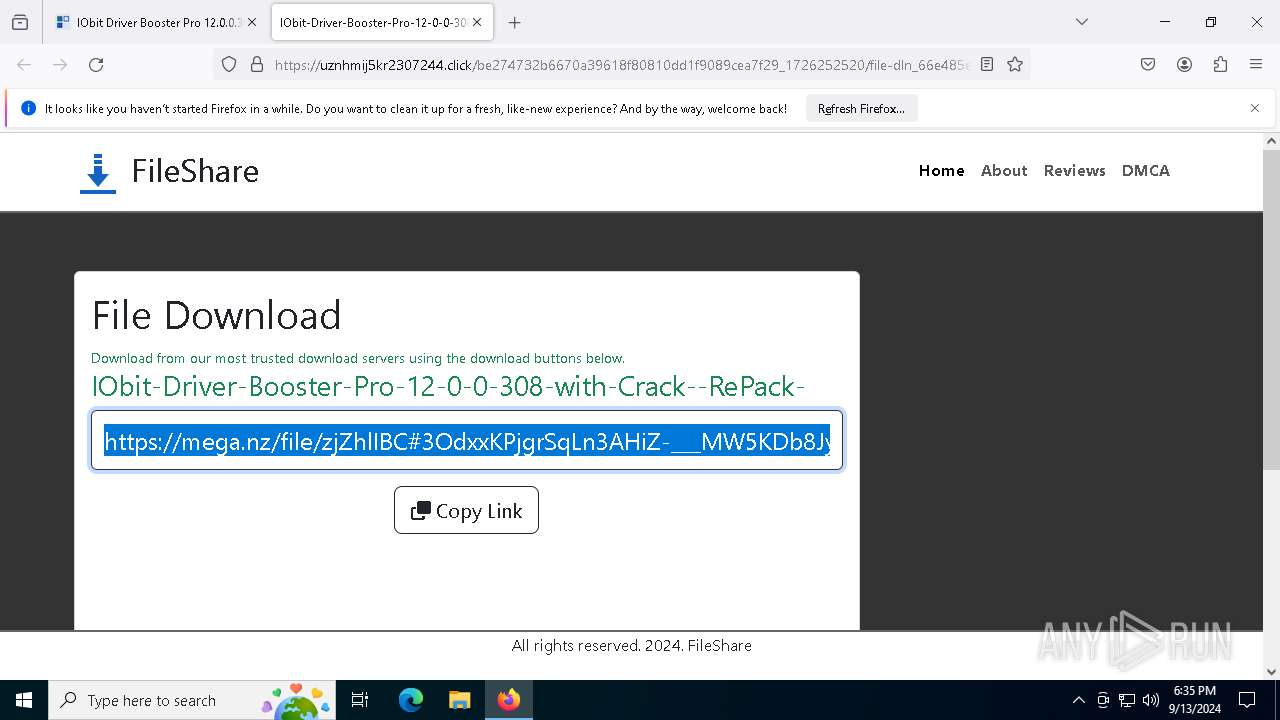
— | — | GET | 301 | 104.17.15.101:80 | http://haxpc.net/ | unknown | — | — | malicious |
— | — | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.61:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.32.97.216:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.32.97.216:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.17.15.101:80 | haxpc.net | CLOUDFLARENET | — | malicious |
— | — | 104.17.15.101:443 | haxpc.net | — | — | malicious |
— | — | 142.250.186.170:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
haxpc.net |
| malicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
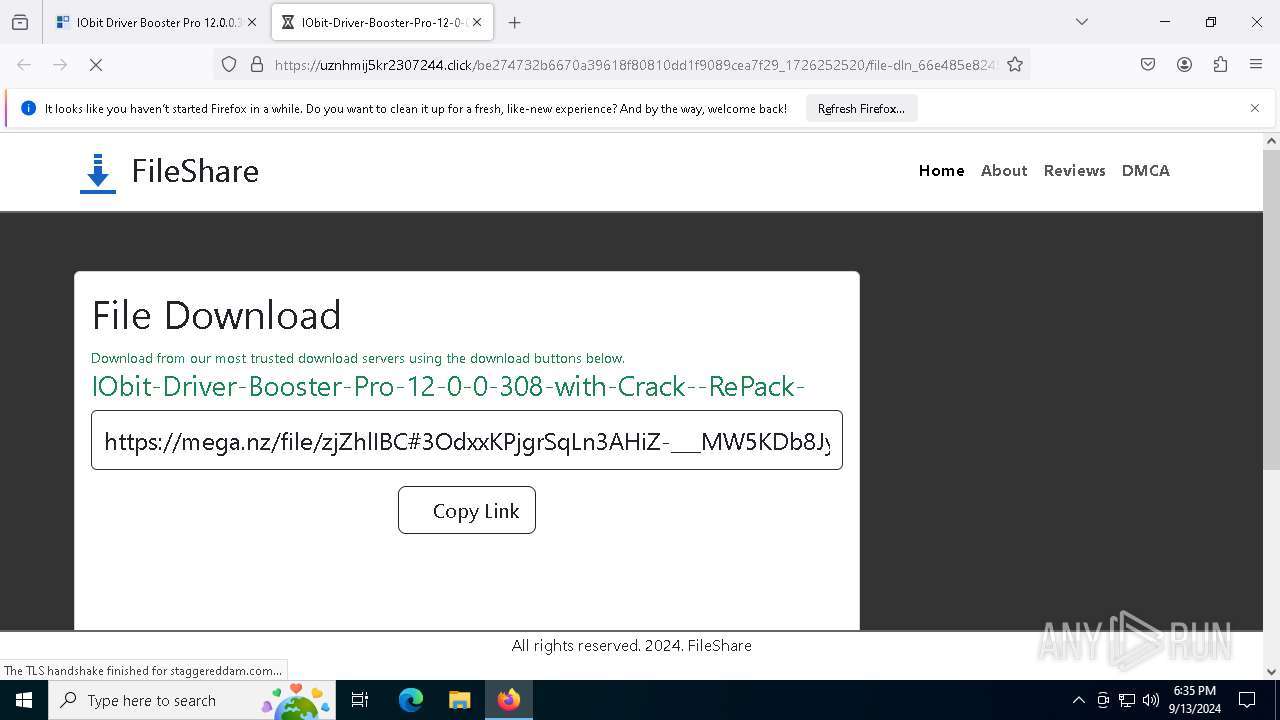
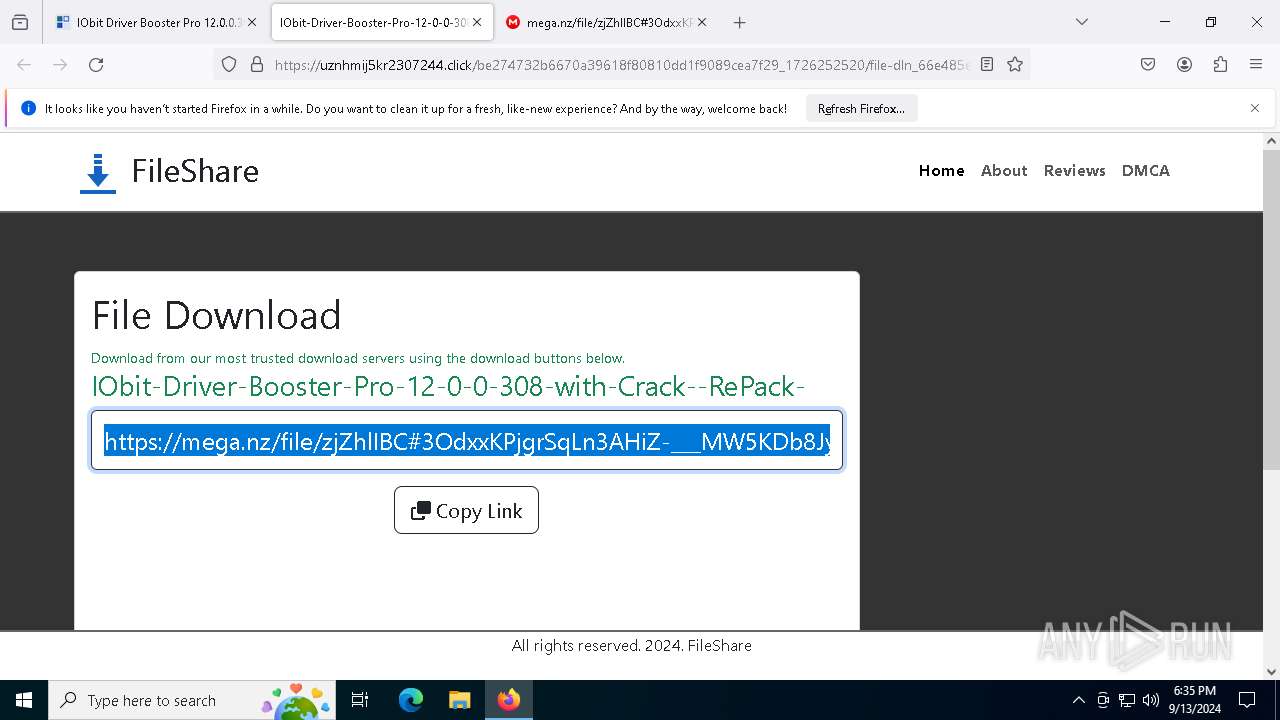
2256 | svchost.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
2256 | svchost.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
2256 | svchost.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
5164 | firefox.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
2256 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
2256 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |