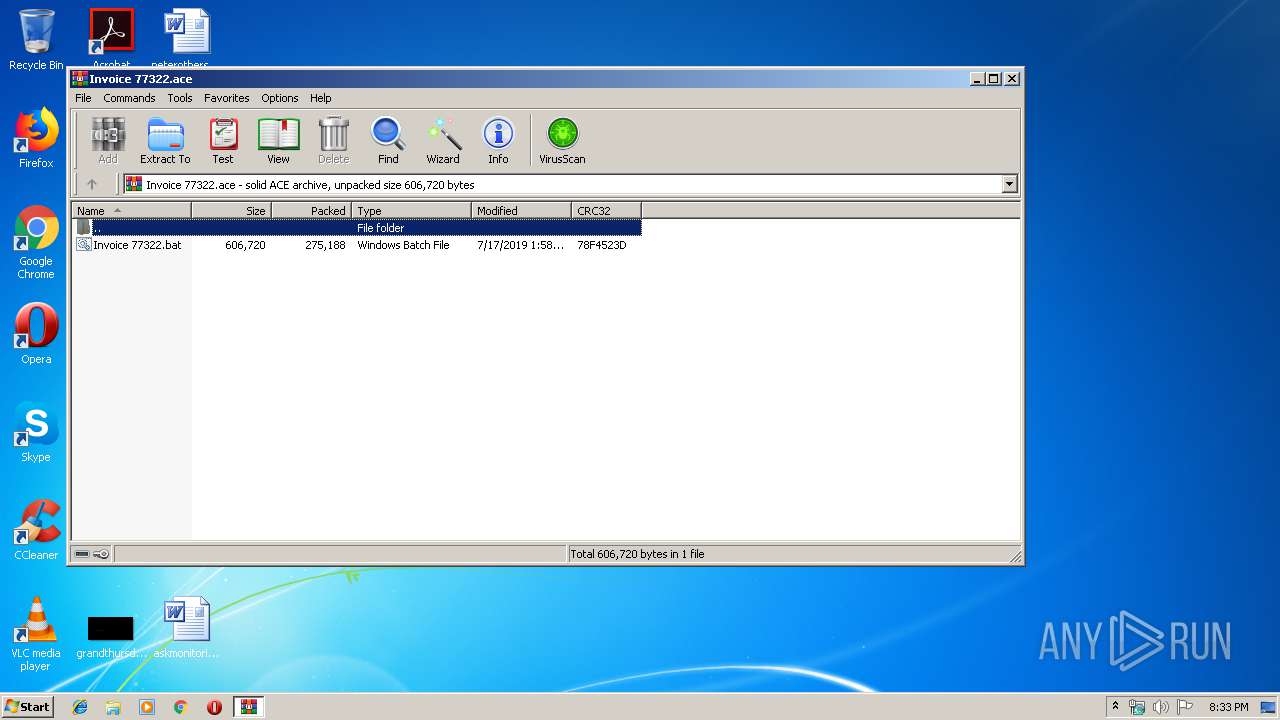
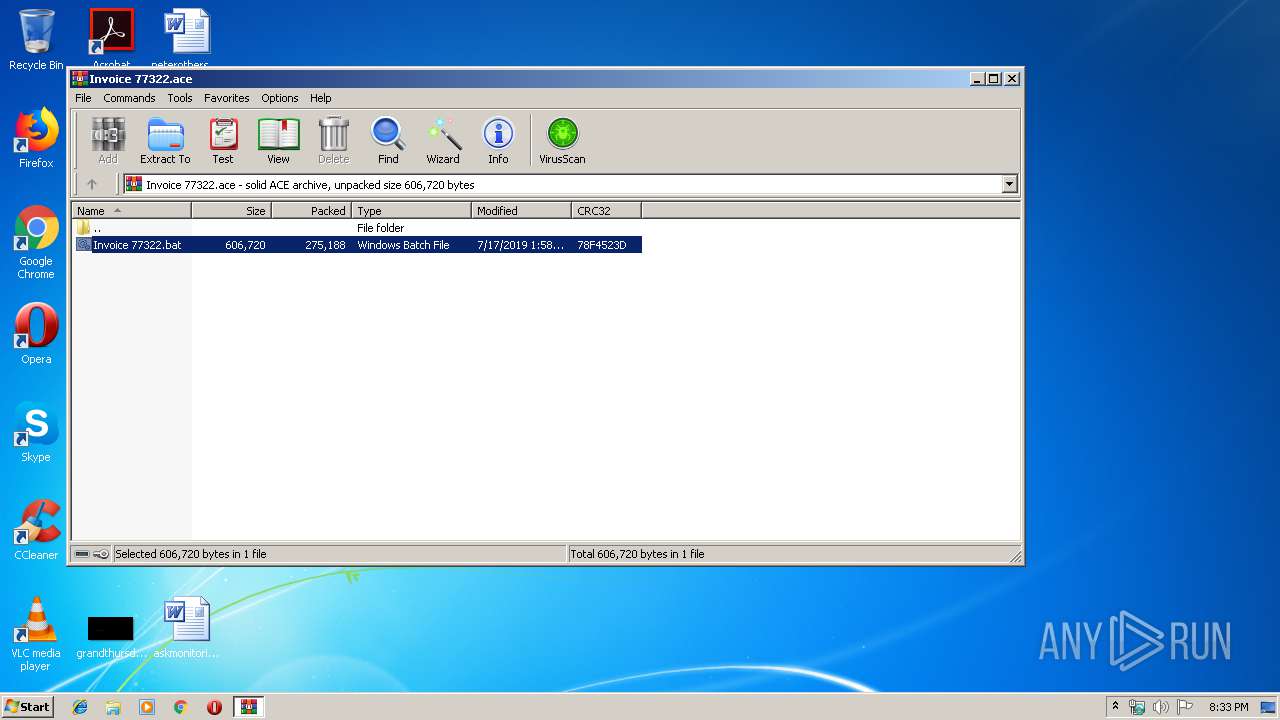
| File name: | Invoice 77322.ace |
| Full analysis: | https://app.any.run/tasks/031d4a3d-b951-4267-957f-05f8caa06b73 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | July 17, 2019, 19:32:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | ACE archive data version 20, from Win/32, version 20 to extract, contains AV-String (unregistered), solid |
| MD5: | 1207B8FE3B94441DFCE8FB4269243660 |
| SHA1: | 40F168BC0440D6B9CE2609D15EA7FCDD78A22433 |
| SHA256: | 4DD9BD00D2881946E1ED6715D19ED24912B3CC0711490FCDECAB12DDB1A034F6 |
| SSDEEP: | 6144:BikUncK2XHyU/K8+lGStpKnVPhL4YjWrHHx/Fd4XaU0gr+q:MRc73yuKQVJhhjeHHFeVhaq |
MALICIOUS
Application was dropped or rewritten from another process
- Invoice 77322.bat (PID: 2572)
- Invoice 77322.bat (PID: 3420)
LOKIBOT was detected
- Invoice 77322.bat (PID: 3420)
Connects to CnC server
- Invoice 77322.bat (PID: 3420)
Detected artifacts of LokiBot
- Invoice 77322.bat (PID: 3420)
Actions looks like stealing of personal data
- Invoice 77322.bat (PID: 3420)
SUSPICIOUS
Starts application with an unusual extension
- WinRAR.exe (PID: 2988)
- Invoice 77322.bat (PID: 2572)
Suspicious files were dropped or overwritten
- WinRAR.exe (PID: 2988)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2988)
- Invoice 77322.bat (PID: 3420)
Loads DLL from Mozilla Firefox
- Invoice 77322.bat (PID: 3420)
Creates files in the user directory
- Invoice 77322.bat (PID: 3420)
Application launched itself
- Invoice 77322.bat (PID: 2572)
INFO
Manual execution by user
- WINWORD.EXE (PID: 1900)
- WINWORD.EXE (PID: 2288)
- WINWORD.EXE (PID: 3548)
- WINWORD.EXE (PID: 2276)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2288)
- WINWORD.EXE (PID: 1900)
- WINWORD.EXE (PID: 2276)
- WINWORD.EXE (PID: 3548)
Creates files in the user directory
- WINWORD.EXE (PID: 1900)
- WINWORD.EXE (PID: 2276)
- WINWORD.EXE (PID: 2288)
- WINWORD.EXE (PID: 3548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ace | | | ACE compressed archive (100) |
|---|
Total processes
45
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1900 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\advancedgeneral.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\chicagofine.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2288 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\videoscommerce.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2988.932\Invoice 77322.bat" | C:\Users\admin\AppData\Local\Temp\Rar$DIa2988.932\Invoice 77322.bat | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2988 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Invoice 77322.ace" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2988.932\Invoice 77322.bat" | C:\Users\admin\AppData\Local\Temp\Rar$DIa2988.932\Invoice 77322.bat | Invoice 77322.bat | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3548 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\peterothers.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 295
Read events
3 198
Write events
1 059
Delete events
38
Modification events
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Invoice 77322.ace | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\ACE Compression Software\ActiveAce\2.0 |
| Operation: | write | Name: | Count |
Value: 0 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\ACE Compression Software\ActiveAce\2.0 |
| Operation: | write | Name: | Name |
Value: 542D4B42647265644B76737A7E794B566767537663764B5B7874767B4B43727A674B5E7961787E747237202024252539767472171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171700 | |||
Executable files
2
Suspicious files
2
Text files
11
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3548 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4A43.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2288 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4A44.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1900 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4A43.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4A71.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRC0000.tmp | — | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{9A4FD4E0-92DA-4F00-BD1C-0EC545E5DDCC}.tmp | — | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{030E591A-5CE7-452D-982A-9032AC094530}.tmp | — | |
MD5:— | SHA256:— | |||
| 1900 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D9F09573-34CB-49F2-8B82-AAE53483A6D5}.tmp | — | |
MD5:— | SHA256:— | |||
| 1900 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{F4C05463-045F-44DF-BC7D-D050CF2CF503}.tmp | — | |
MD5:— | SHA256:— | |||
| 3548 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRC0001.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
4
DNS requests
1
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3420 | Invoice 77322.bat | POST | 404 | 95.213.199.127:80 | http://vman22.com/ab18/fre.php | RU | text | 15 b | malicious |
3420 | Invoice 77322.bat | POST | 404 | 95.213.199.127:80 | http://vman22.com/ab18/fre.php | RU | binary | 23 b | malicious |
3420 | Invoice 77322.bat | POST | 404 | 95.213.199.127:80 | http://vman22.com/ab18/fre.php | RU | text | 15 b | malicious |
3420 | Invoice 77322.bat | POST | 404 | 95.213.199.127:80 | http://vman22.com/ab18/fre.php | RU | binary | 23 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3420 | Invoice 77322.bat | 95.213.199.127:80 | vman22.com | OOO Network of data-centers Selectel | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vman22.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3420 | Invoice 77322.bat | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3420 | Invoice 77322.bat | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3420 | Invoice 77322.bat | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
4 ETPRO signatures available at the full report