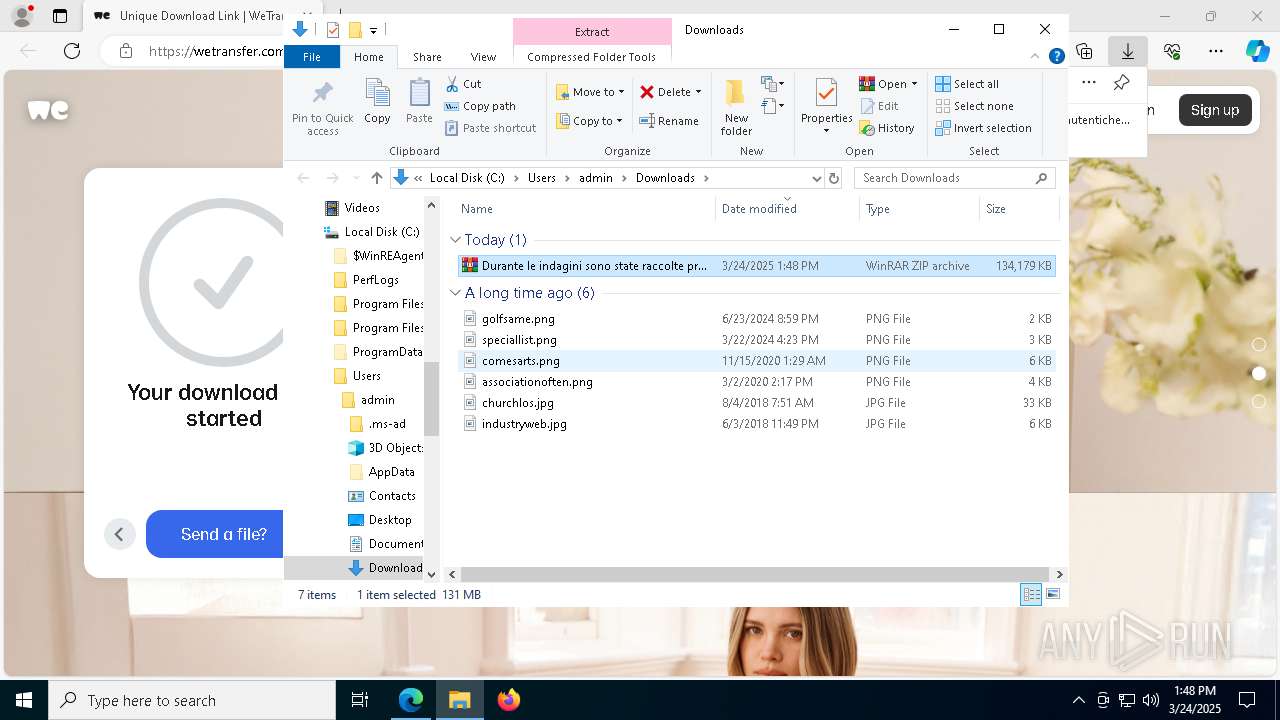
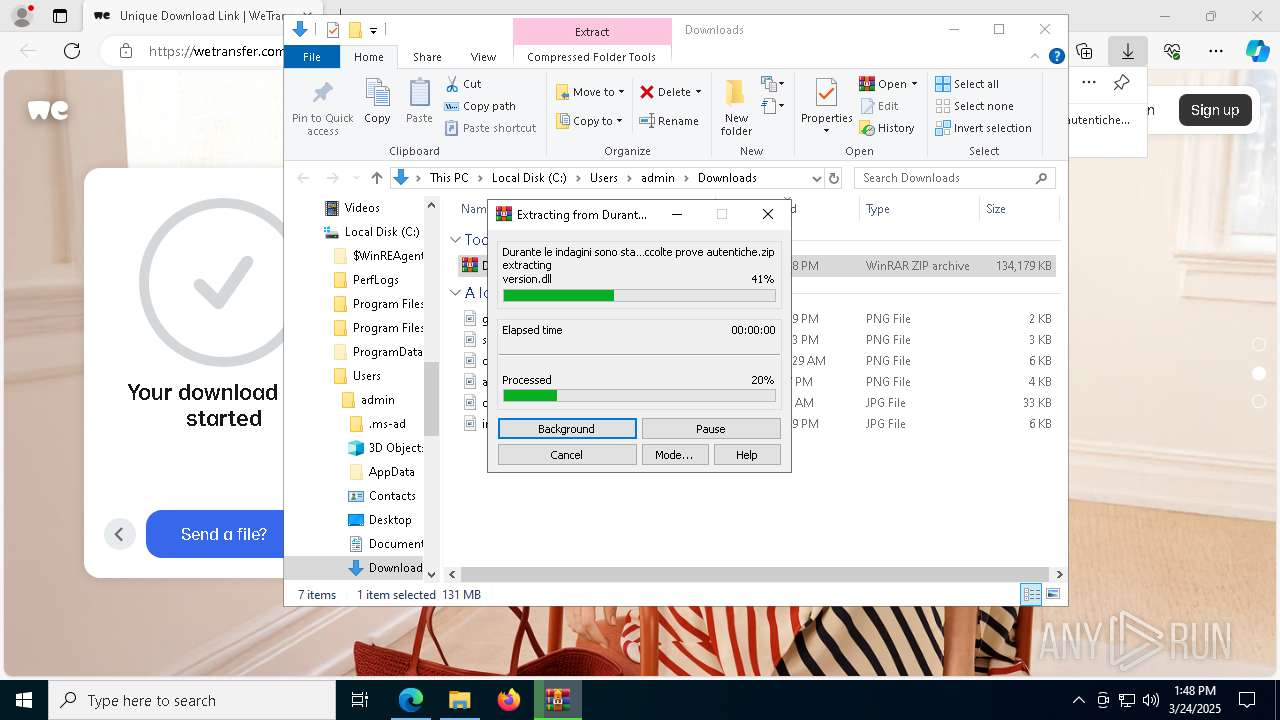
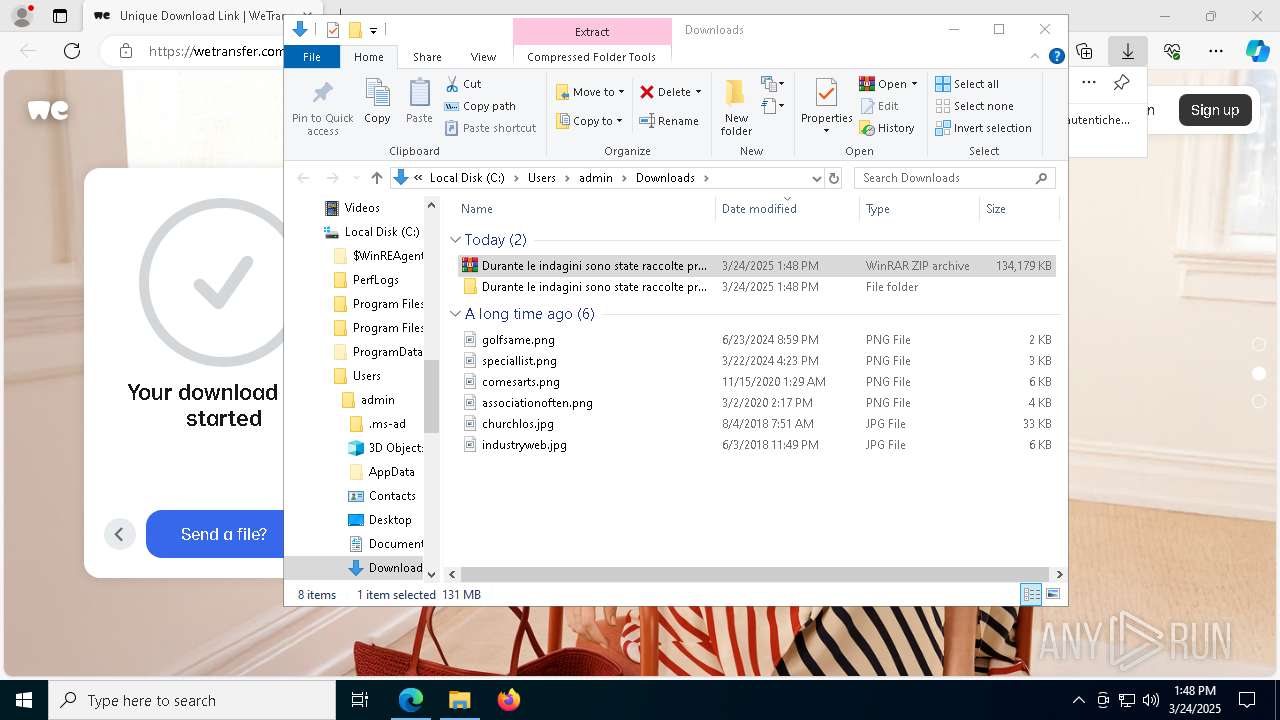
| URL: | https://we.tl/t-weT5qaseBB |
| Full analysis: | https://app.any.run/tasks/6aa39304-15a4-45bf-ad49-b8ab7800a1eb |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 24, 2025, 13:47:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0A2586CA5C294C1DEC0ECF2064E88E62 |
| SHA1: | 9C282313D22881806A9D6D733A92F3851062EFBB |
| SHA256: | 4D92D070B973C303A26D9201F3C7FC53CF01B3708B6D4CCB622EEBB32DF497CA |
| SSDEEP: | 3:N8RlJKCT/k:2+ |
MALICIOUS
Actions looks like stealing of personal data
- svchost.exe (PID: 5044)
Suspicious browser debugging (Possible cookie theft)
- svchost.exe (PID: 5044)
ASYNCRAT has been detected (SURICATA)
- InstallUtil.exe (PID: 5404)
SUSPICIOUS
Process drops legitimate windows executable
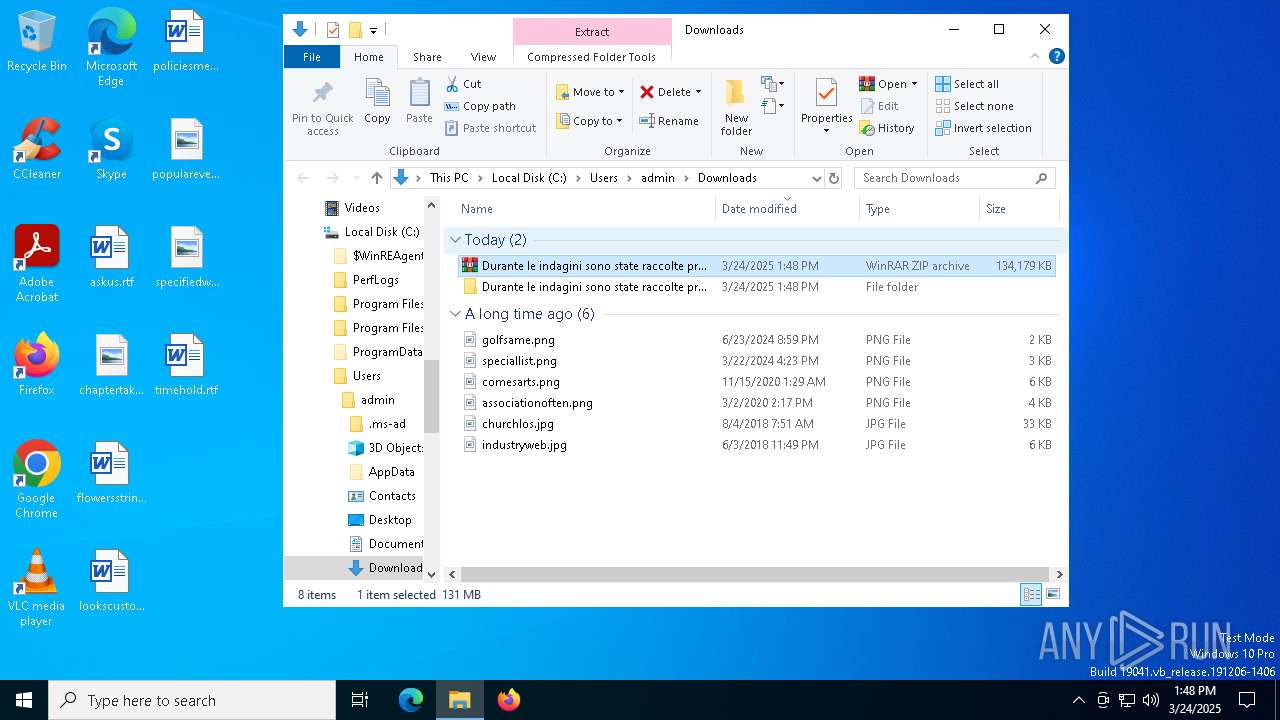
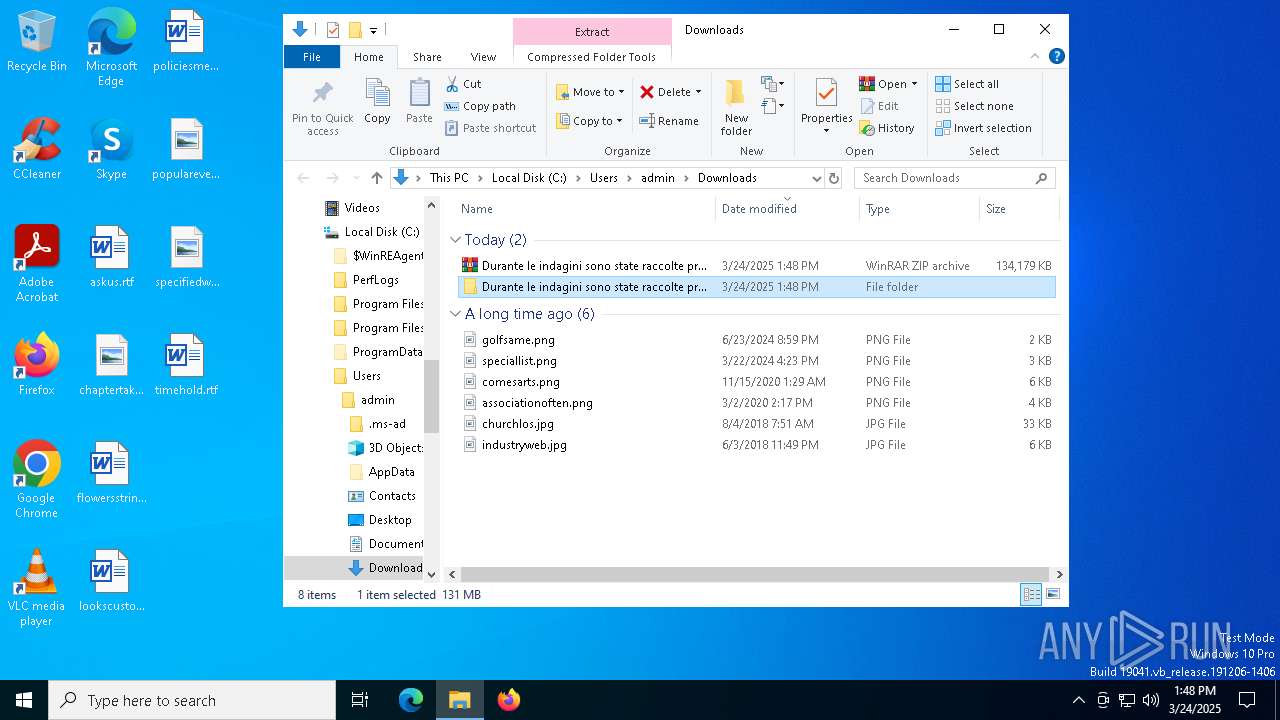
- WinRAR.exe (PID: 8788)
- Images.png (PID: 7980)
The executable file from the user directory is run by the CMD process
- Images.png (PID: 7980)
Likely accesses (executes) a file from the Public directory
- Images.png (PID: 7980)
- svchost.exe (PID: 5044)
- reg.exe (PID: 5172)
Starts application with an unusual extension
- cmd.exe (PID: 8888)
Executable content was dropped or overwritten
- Images.png (PID: 7980)
Process drops python dynamic module
- Images.png (PID: 7980)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 8656)
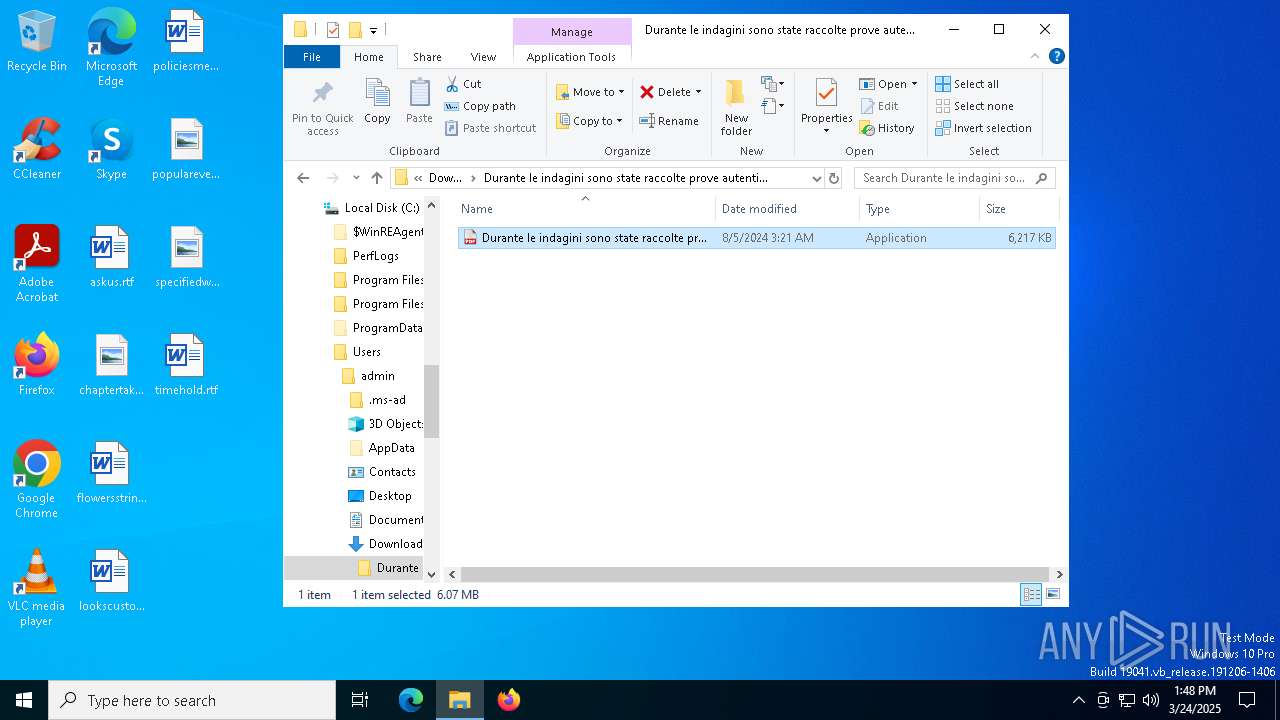
There is functionality for taking screenshot (YARA)
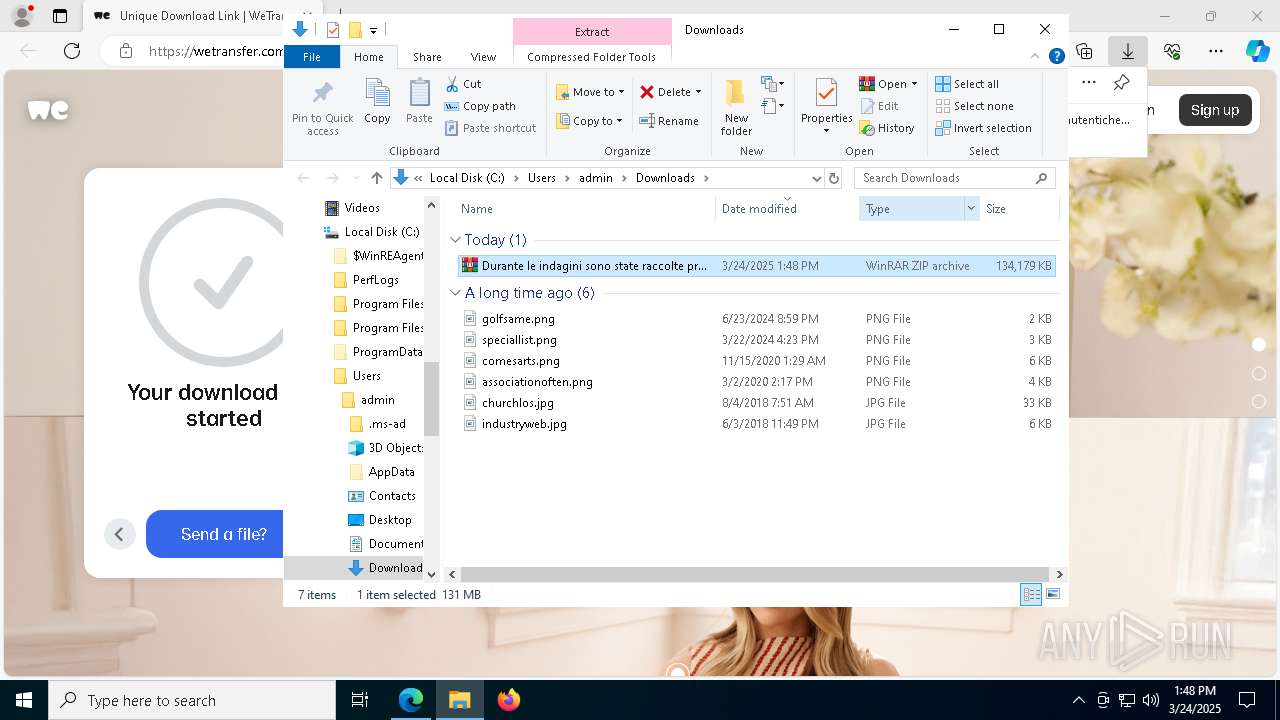
- Durante le indagini sono state raccolte prove autentiche.exe (PID: 8036)
Starts CMD.EXE for commands execution
- Durante le indagini sono state raccolte prove autentiche.exe (PID: 8036)
Executing commands from ".cmd" file
- Durante le indagini sono state raccolte prove autentiche.exe (PID: 8036)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 8888)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8888)
Loads Python modules
- svchost.exe (PID: 5044)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- svchost.exe (PID: 5044)
MS Edge headless start
- msedge.exe (PID: 7820)
- msedge.exe (PID: 8788)
The process creates files with name similar to system file names
- Images.png (PID: 7980)
The process drops C-runtime libraries
- Images.png (PID: 7980)
Probably fake Windows Update
- reg.exe (PID: 5172)
Get information on the list of running processes
- svchost.exe (PID: 5044)
Checks for external IP
- svchost.exe (PID: 2196)
Connects to unusual port
- InstallUtil.exe (PID: 5404)
Contacting a server suspected of hosting an CnC
- InstallUtil.exe (PID: 5404)
INFO
Reads Environment values
- identity_helper.exe (PID: 8380)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 8204)
Reads the computer name
- identity_helper.exe (PID: 8380)
Autorun file from Downloads
- msedge.exe (PID: 8364)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8580)
- BackgroundTransferHost.exe (PID: 9040)
- BackgroundTransferHost.exe (PID: 6040)
- BackgroundTransferHost.exe (PID: 1300)
- BackgroundTransferHost.exe (PID: 8204)
Checks supported languages
- identity_helper.exe (PID: 8380)
- identity_helper.exe (PID: 8916)
- ShellExperienceHost.exe (PID: 8656)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 8204)
- slui.exe (PID: 616)
- InstallUtil.exe (PID: 5404)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 8204)
- svchost.exe (PID: 5044)
The sample compiled with english language support
- WinRAR.exe (PID: 8788)
- Images.png (PID: 7980)
- msedge.exe (PID: 8400)
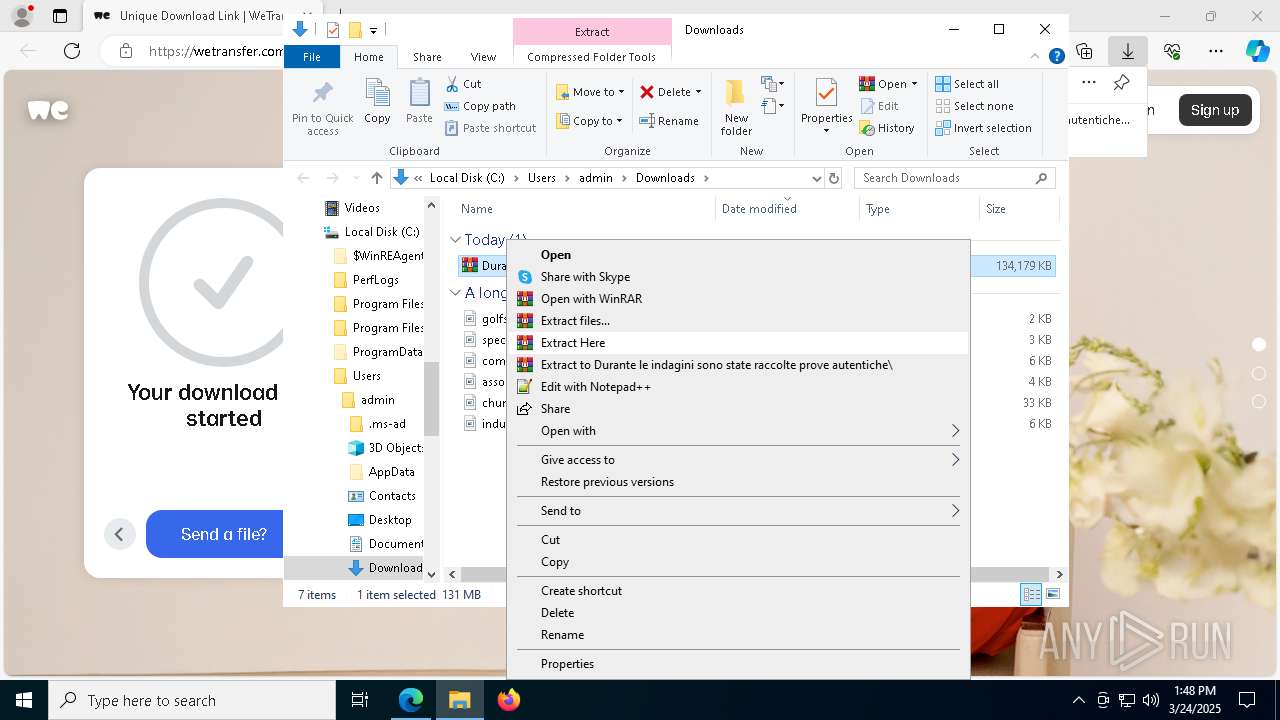
Manual execution by a user
- WinRAR.exe (PID: 8788)
- Durante le indagini sono state raccolte prove autentiche.exe (PID: 8036)
Application launched itself
- msedge.exe (PID: 7212)
- Acrobat.exe (PID: 2236)
- msedge.exe (PID: 8396)
- AcroCEF.exe (PID: 5392)
- chrome.exe (PID: 7816)
- msedge.exe (PID: 7820)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8788)
- msedge.exe (PID: 8400)
Python executable
- svchost.exe (PID: 5044)
Create files in a temporary directory
- svchost.exe (PID: 5044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
270
Monitored processes
127
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=7228 --field-trial-handle=2372,i,2370780693562543809,5229753922697292,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1072 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Temp\GsX2EcuXIQl6iSJ0" --extension-process --no-appcompat-clear --no-sandbox --remote-debugging-port=9678 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=3136 --field-trial-handle=1888,i,15529064200040196604,5756278441284118281,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6004 --field-trial-handle=2372,i,2370780693562543809,5229753922697292,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3492 --field-trial-handle=2372,i,2370780693562543809,5229753922697292,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1300 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=6156 --field-trial-handle=2372,i,2370780693562543809,5229753922697292,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Temp\orkZStDxo2MCNBpo" --no-appcompat-clear --no-sandbox --remote-debugging-port=9383 --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=4928 --field-trial-handle=2272,i,12106529000545699249,5382886657380296066,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
34 530
Read events
34 273
Write events
240
Delete events
17
Modification events
| (PID) Process: | (7212) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7212) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7212) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7212) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7212) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 334CE520AD8F2F00 | |||
| (PID) Process: | (2616) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2616) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2616) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2616) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2616) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
Executable files
157
Suspicious files
1 426
Text files
1 538
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10c20a.TMP | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10c219.TMP | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10c229.TMP | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10c258.TMP | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10c296.TMP | — | |
MD5:— | SHA256:— | |||
| 7212 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
213
DNS requests
253
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7908 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6392 | svchost.exe | HEAD | 200 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1743117876&P2=404&P3=2&P4=IS4IVUrcFqbLi9jRU7zKJ1sg3EW2Gb46R1IjLsDXDDoIciiHWuMSENBNt03psl4LCvnhdlEWygtY1HDrW2tNQw%3d%3d | unknown | — | — | whitelisted |
8204 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6392 | svchost.exe | GET | 206 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1743117876&P2=404&P3=2&P4=IS4IVUrcFqbLi9jRU7zKJ1sg3EW2Gb46R1IjLsDXDDoIciiHWuMSENBNt03psl4LCvnhdlEWygtY1HDrW2tNQw%3d%3d | unknown | — | — | whitelisted |
3888 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6392 | svchost.exe | GET | 206 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1743117876&P2=404&P3=2&P4=IS4IVUrcFqbLi9jRU7zKJ1sg3EW2Gb46R1IjLsDXDDoIciiHWuMSENBNt03psl4LCvnhdlEWygtY1HDrW2tNQw%3d%3d | unknown | — | — | whitelisted |
6392 | svchost.exe | GET | 206 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1743117876&P2=404&P3=2&P4=IS4IVUrcFqbLi9jRU7zKJ1sg3EW2Gb46R1IjLsDXDDoIciiHWuMSENBNt03psl4LCvnhdlEWygtY1HDrW2tNQw%3d%3d | unknown | — | — | whitelisted |
6392 | svchost.exe | GET | 206 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1743117876&P2=404&P3=2&P4=IS4IVUrcFqbLi9jRU7zKJ1sg3EW2Gb46R1IjLsDXDDoIciiHWuMSENBNt03psl4LCvnhdlEWygtY1HDrW2tNQw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7212 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7448 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7448 | msedge.exe | 18.155.153.121:443 | we.tl | AMAZON-02 | US | whitelisted |
7448 | msedge.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
7448 | msedge.exe | 52.85.92.128:443 | wetransfer.com | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7448 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
we.tl |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
wetransfer.com |
| whitelisted |
cdn.wetransfer.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7448 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wetransfer .com) |
7448 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (wetransfer .com) |
7448 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wetransfer .com) |
7448 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7448 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7448 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7448 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wetransfer .com) |
7448 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7448 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wetransfer .com) |
7448 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (wetransfer .com) |