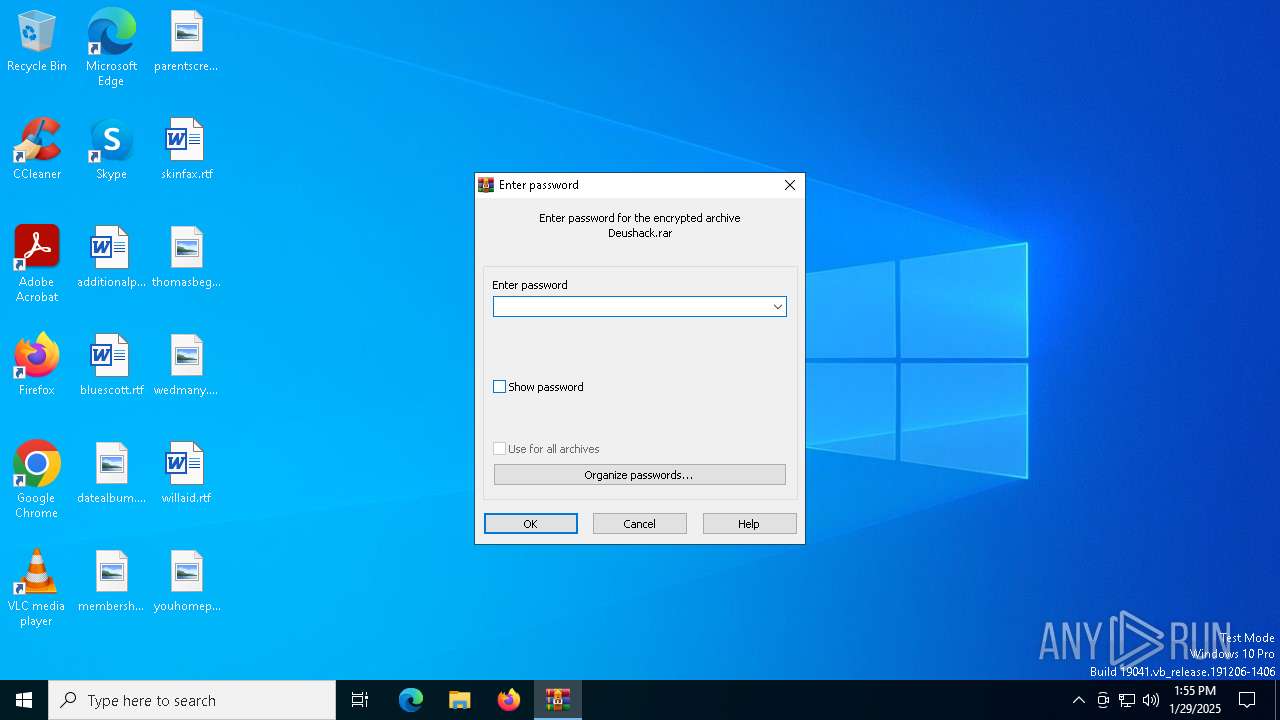
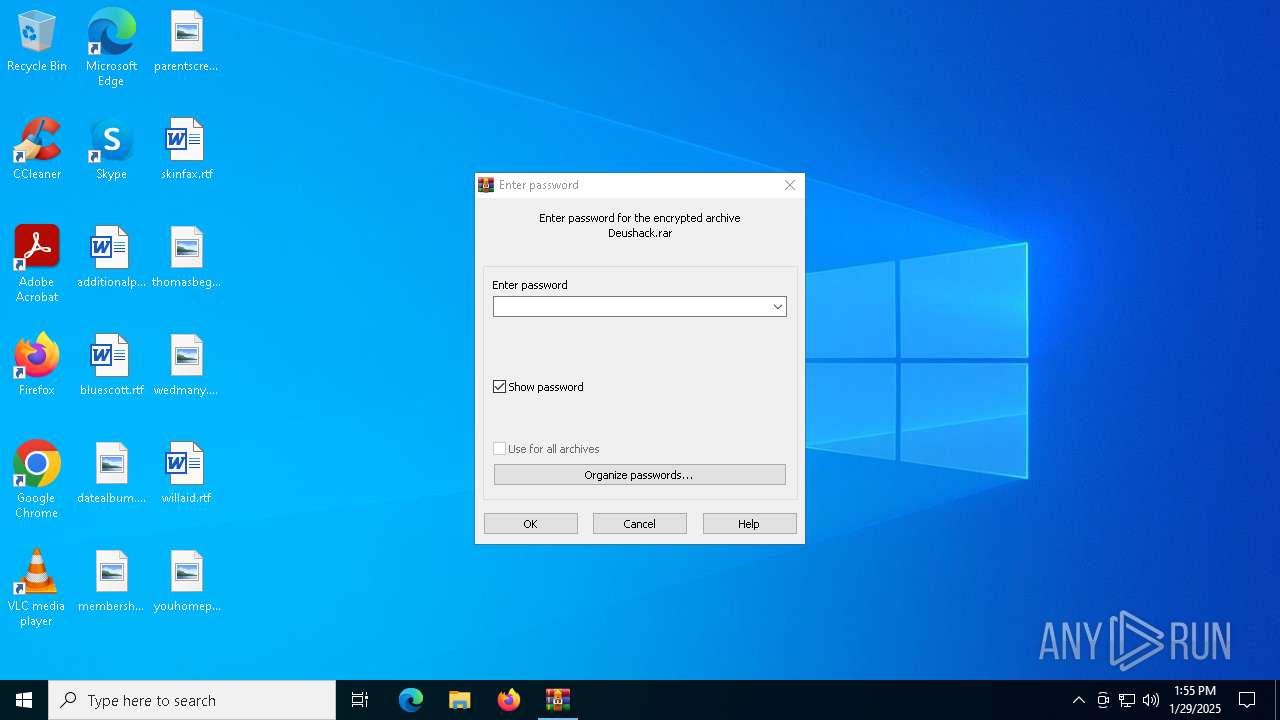
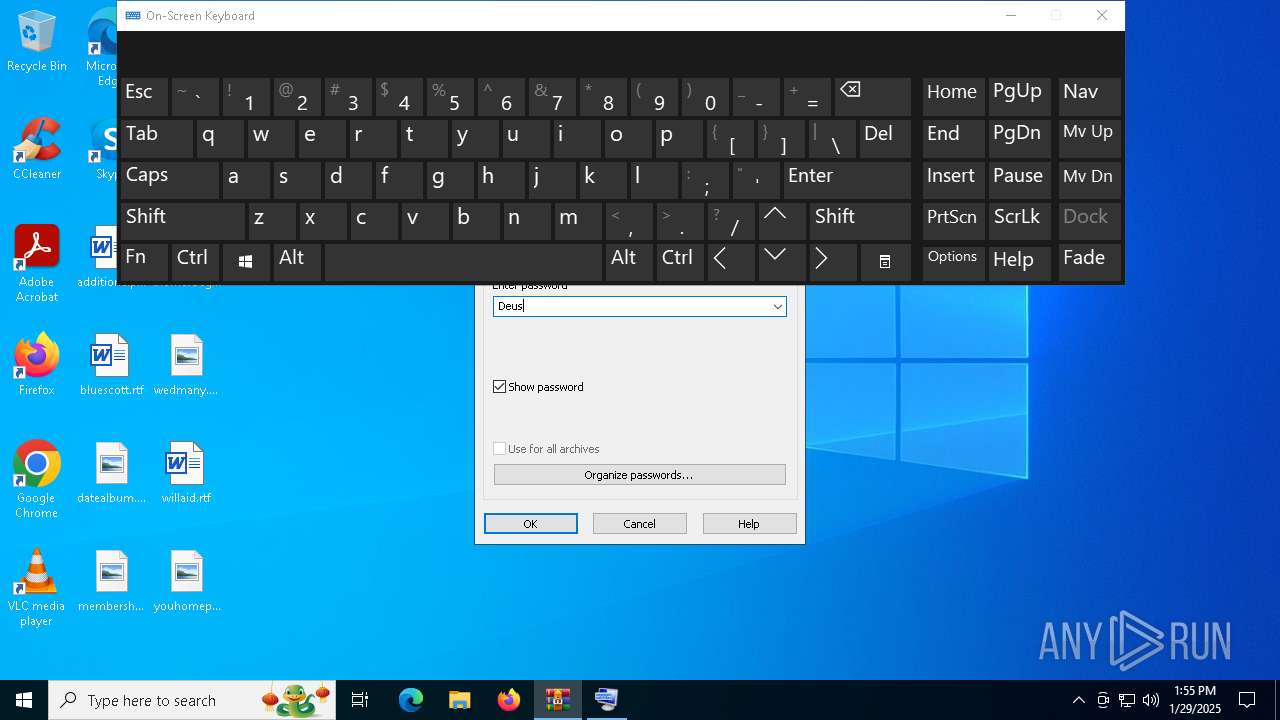
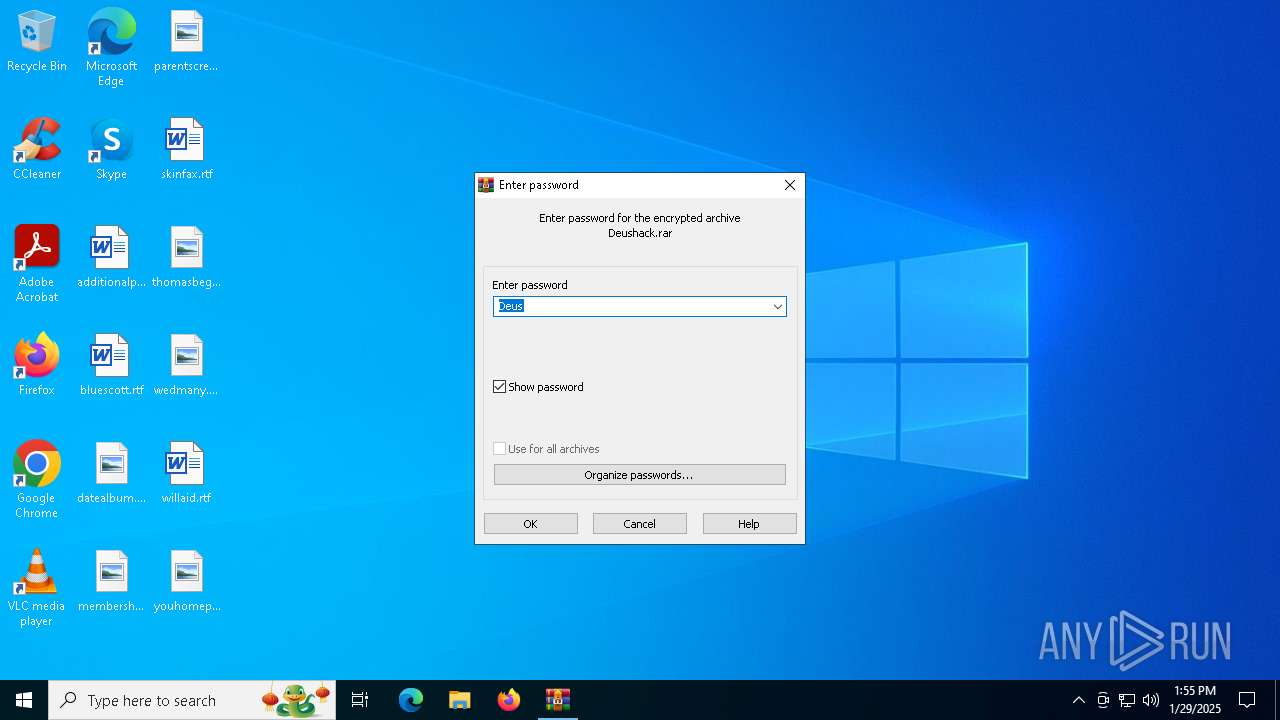
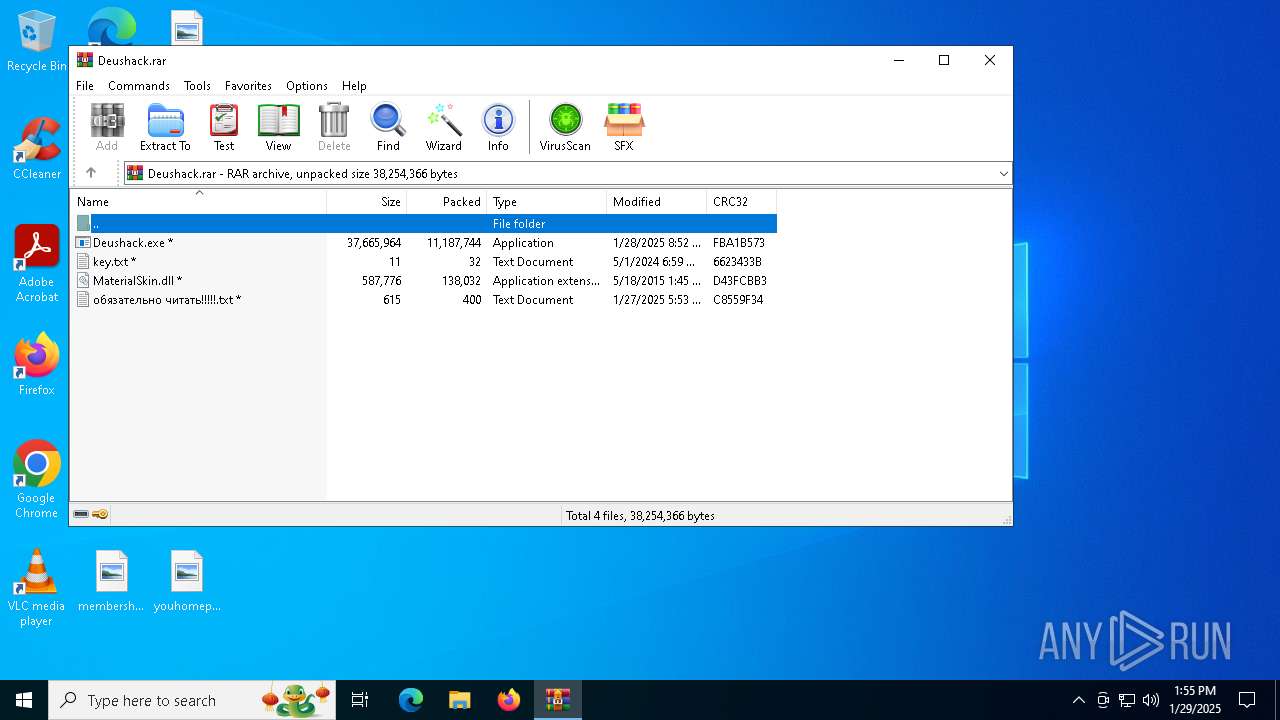
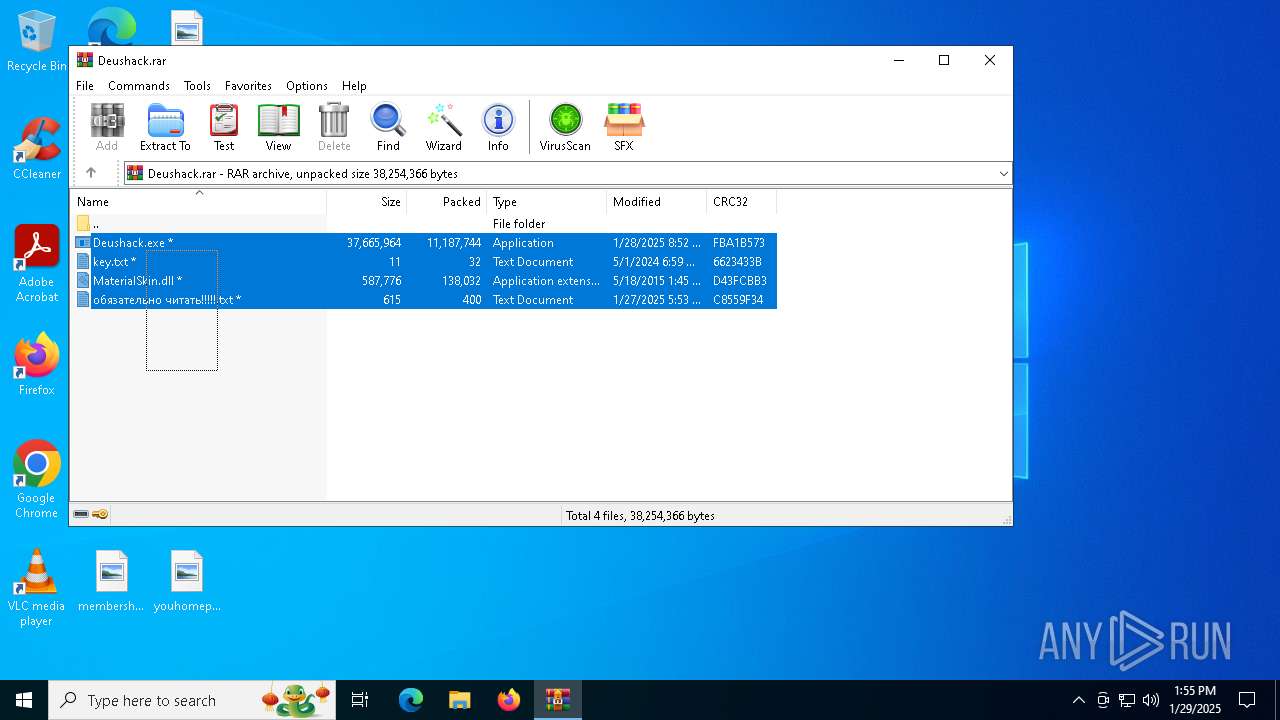
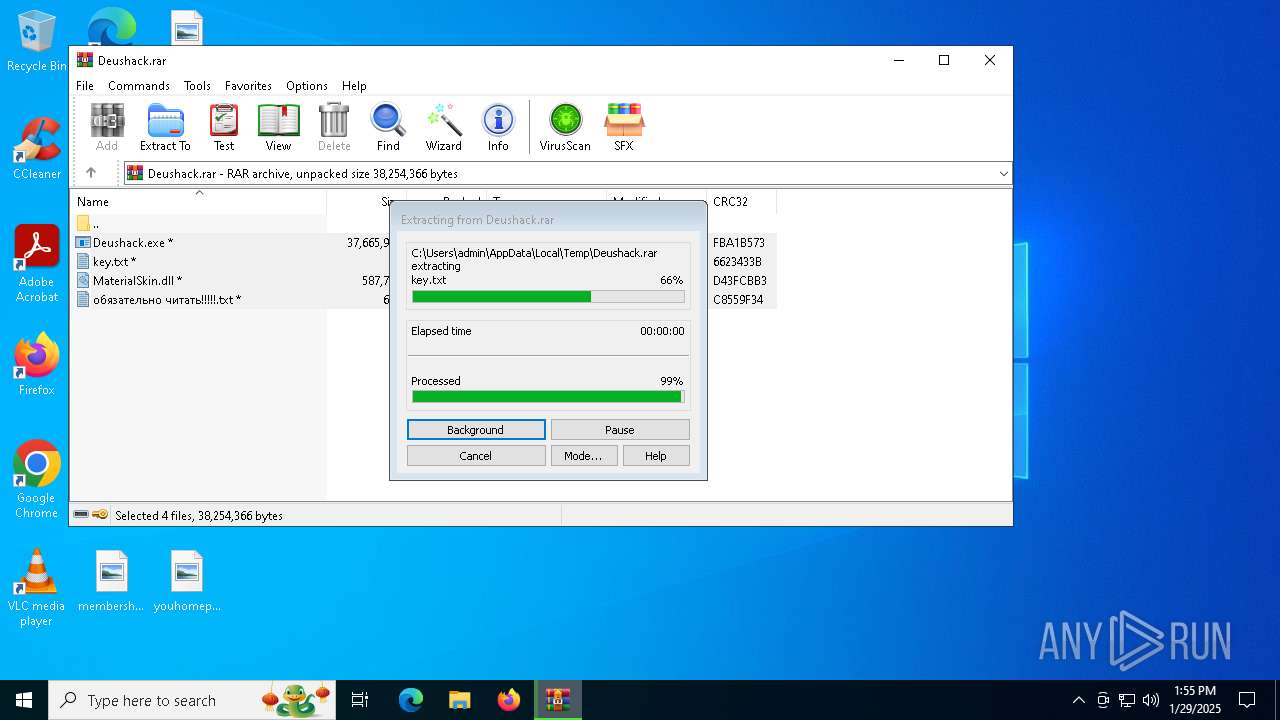
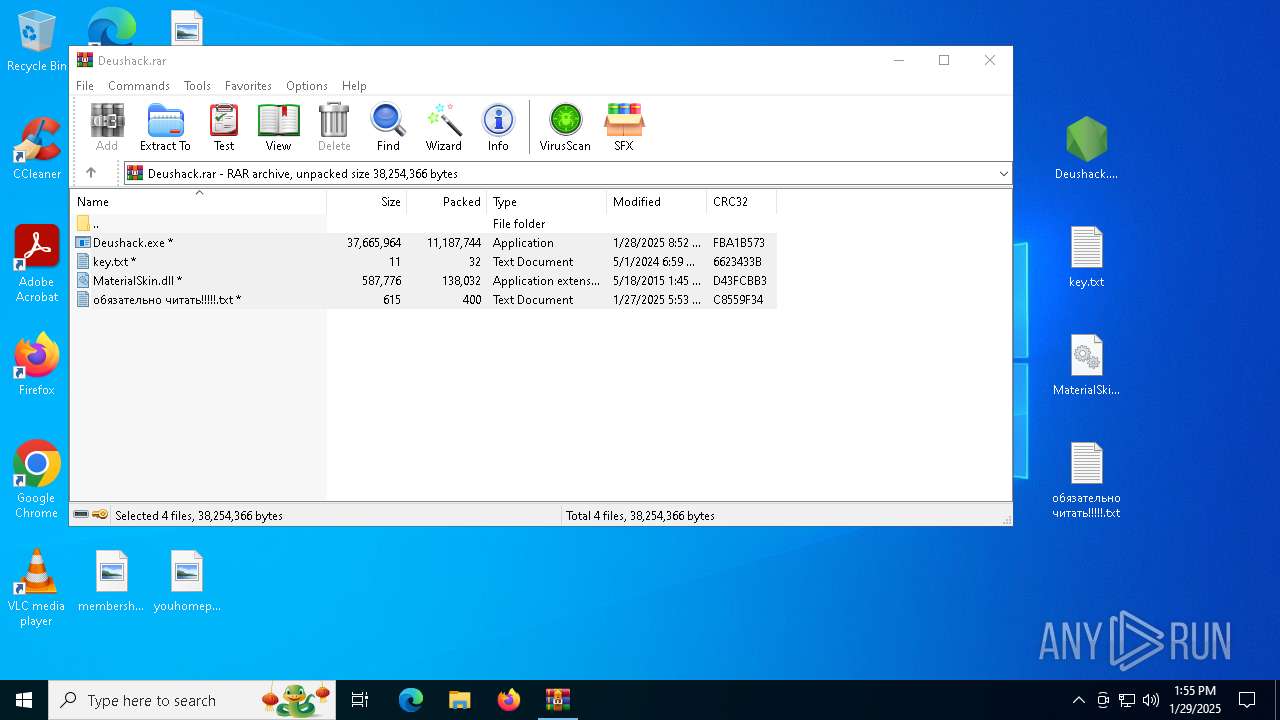
| File name: | Deushack.rar |
| Full analysis: | https://app.any.run/tasks/ea4b512a-a5f4-4622-9cda-9878006f03dd |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | January 29, 2025, 13:55:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 07982122CFFDD3B1BA41B5B5D014A8DD |
| SHA1: | C7D9B2834A77AED5A90A08A47C96AD460C0744D4 |
| SHA256: | 4D14119CC95F50A4E4EC0149D463F29E22B058B4D05B9ED5657FCF232B03164D |
| SSDEEP: | 98304:CFgfi8c2z2Dv38Nj51YSEN9StY2Mm5/KHkYRpIZniif8+dKtlmRsM4DbQdOSYs2w:+TX5Jf/1aP5uOp+Cm5Qk2uI/ |
MALICIOUS
Steals credentials from Web Browsers
- BUILD0~1.EXE (PID: 7084)
- msedge.exe (PID: 6224)
Known privilege escalation attack
- dllhost.exe (PID: 3060)
Actions looks like stealing of personal data
- BUILD0~1.EXE (PID: 7084)
- chrome.exe (PID: 6812)
- msedge.exe (PID: 6224)
RHADAMANTHYS mutex has been found
- svchost.exe (PID: 7128)
- c214.exe (PID: 6976)
Scans artifacts that could help determine the target
- msedge.exe (PID: 6224)
RHADAMANTHYS has been detected (SURICATA)
- svchost.exe (PID: 5000)
RHADAMANTHYS has been detected (YARA)
- svchost.exe (PID: 5000)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 3040)
- msedge.exe (PID: 6224)
Starts CMD.EXE for commands execution
- Deushack.exe (PID: 2436)
- Deushack.exe (PID: 1488)
Executable content was dropped or overwritten
- Deushack.exe (PID: 2436)
- joy.exe (PID: 6224)
Process drops legitimate windows executable
- Deushack.exe (PID: 2436)
Checks for external IP
- Deushack.exe (PID: 2436)
- Deushack.exe (PID: 1488)
- BUILD0~1.EXE (PID: 7084)
- svchost.exe (PID: 2192)
Executes application which crashes
- c214.exe (PID: 6976)
Connects to unusual port
- BUILD0~1.EXE (PID: 7084)
- svchost.exe (PID: 7128)
- svchost.exe (PID: 5000)
The process checks if it is being run in the virtual environment
- svchost.exe (PID: 7128)
Application launched itself
- chrome.exe (PID: 6812)
- c214.exe (PID: 3780)
- msedge.exe (PID: 6224)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 6224)
Searches for installed software
- svchost.exe (PID: 5000)
Loads DLL from Mozilla Firefox
- svchost.exe (PID: 5000)
INFO
Manual execution by a user
- osk.exe (PID: 5548)
- osk.exe (PID: 4320)
- Deushack.exe (PID: 2436)
- Deushack.exe (PID: 1488)
- svchost.exe (PID: 7128)
- svchost.exe (PID: 5000)
Checks supported languages
- ShellExperienceHost.exe (PID: 3040)
- Deushack.exe (PID: 2436)
- joy.exe (PID: 6224)
- BUILD0~1.EXE (PID: 3052)
- Deushack.exe (PID: 1488)
- c214.exe (PID: 3780)
- c214.exe (PID: 6976)
- BUILD0~1.EXE (PID: 7084)
- chrome.exe (PID: 6812)
- msedge.exe (PID: 6224)
- wmprph.exe (PID: 7412)
Reads the computer name
- ShellExperienceHost.exe (PID: 3040)
- Deushack.exe (PID: 2436)
- Deushack.exe (PID: 1488)
- c214.exe (PID: 3780)
- BUILD0~1.EXE (PID: 3052)
- BUILD0~1.EXE (PID: 7084)
- chrome.exe (PID: 6812)
- msedge.exe (PID: 6224)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6668)
Reads product name
- Deushack.exe (PID: 2436)
- Deushack.exe (PID: 1488)
Reads Environment values
- Deushack.exe (PID: 2436)
- Deushack.exe (PID: 1488)
- BUILD0~1.EXE (PID: 7084)
- chrome.exe (PID: 6812)
- msedge.exe (PID: 6224)
Reads CPU info
- Deushack.exe (PID: 2436)
- Deushack.exe (PID: 1488)
- BUILD0~1.EXE (PID: 7084)
The sample compiled with english language support
- Deushack.exe (PID: 2436)
Create files in a temporary directory
- joy.exe (PID: 6224)
- svchost.exe (PID: 5000)
- chrome.exe (PID: 6812)
- msedge.exe (PID: 6224)
Reads the machine GUID from the registry
- BUILD0~1.EXE (PID: 7084)
- BUILD0~1.EXE (PID: 3052)
- msedge.exe (PID: 6224)
- chrome.exe (PID: 6812)
- wmprph.exe (PID: 7412)
Disables trace logs
- BUILD0~1.EXE (PID: 7084)
Checks proxy server information
- BUILD0~1.EXE (PID: 7084)
- chrome.exe (PID: 6812)
- msedge.exe (PID: 6224)
Checks transactions between databases Windows and Oracle
- BUILD0~1.EXE (PID: 3052)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 3060)
Node.js compiler has been detected
- Deushack.exe (PID: 1488)
Process checks computer location settings
- chrome.exe (PID: 6812)
- msedge.exe (PID: 6224)
Process checks whether UAC notifications are on
- msedge.exe (PID: 6224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
184
Monitored processes
45
Malicious processes
7
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=5324 --field-trial-handle=2408,i,10416706172922100664,17615922124948419030,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\Desktop\Deushack.exe" | C:\Users\admin\Desktop\Deushack.exe | explorer.exe | ||||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Node.js JavaScript Runtime Version: 18.5.0 Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3116 --field-trial-handle=1908,i,14445459779075300340,17995187134394163047,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1580 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=4428 --field-trial-handle=2408,i,10416706172922100664,17615922124948419030,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1904 --field-trial-handle=1908,i,14445459779075300340,17995187134394163047,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2064 --field-trial-handle=1908,i,14445459779075300340,17995187134394163047,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3596 --field-trial-handle=1908,i,14445459779075300340,17995187134394163047,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2436 | "C:\Users\admin\Desktop\Deushack.exe" | C:\Users\admin\Desktop\Deushack.exe | explorer.exe | ||||||||||||
User: admin Company: Node.js Integrity Level: HIGH Description: Node.js JavaScript Runtime Exit code: 0 Version: 18.5.0 Modules
| |||||||||||||||
| 2572 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=4648 --field-trial-handle=2408,i,10416706172922100664,17615922124948419030,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
14 476
Read events
14 241
Write events
233
Delete events
2
Modification events
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AccessibilityTemp |
| Operation: | write | Name: | osk |
Value: 3 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Osk |
| Operation: | write | Name: | RunningState |
Value: 1 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Osk |
| Operation: | write | Name: | WindowLeft |
Value: 100 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Accessibility\ATConfig\osk |
| Operation: | write | Name: | WindowLeft |
Value: 100 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Osk |
| Operation: | write | Name: | WindowTop |
Value: 100 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Accessibility\ATConfig\osk |
| Operation: | write | Name: | WindowTop |
Value: 100 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Osk |
| Operation: | write | Name: | WindowWidth |
Value: 1024 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Accessibility\ATConfig\osk |
| Operation: | write | Name: | WindowWidth |
Value: 1024 | |||
| (PID) Process: | (4320) osk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Osk |
| Operation: | write | Name: | WindowHeight |
Value: 293 | |||
Executable files
5
Suspicious files
170
Text files
64
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6668.25828\Deushack.exe | — | |
MD5:— | SHA256:— | |||
| 2436 | Deushack.exe | C:\GoogleUpdater\joy.exe | executable | |
MD5:11AD0F71CAABBADBA8CA08663690CA39 | SHA256:861F2C5F07C9E1C7D24C2E34EB47FF3129CD39A2227A2549809B9D5C92267883 | |||
| 6224 | joy.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\BUILD0~1.EXE | executable | |
MD5:B15C2D0072DF0E7C756C4338F34643DC | SHA256:56D449AE82F8985ED268A7CE88D51729F96E22AE023AC7C8B57F32E565670C0D | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr82DA.tmp\Default\History-journal | — | |
MD5:— | SHA256:— | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr82DA.tmp\7a91ab4e-d60b-4ca3-99ad-b9715e75dee6.tmp | binary | |
MD5:44DD71765C6D0D0AC0ADF1122B8DA6FA | SHA256:C7835DD48618EE5F7491FD3519F260B7D91C5CF3E9190FF59E279EBB8FC15DB9 | |||
| 6224 | joy.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\c214.exe | executable | |
MD5:DC89D3DF253D2A99C687FDC1175525B0 | SHA256:1838AF37F774045256981101F05C22CC796088AE6643F7DE07B3D6AC19A9B9F3 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6668.25828\MaterialSkin.dll | executable | |
MD5:DAE45E51F8763BD0369A221480DB0EE1 | SHA256:B9879DF15E82C52E9166C71F7B177C57BD4C8289821A65A9D3F5228B3F606B4E | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr82DA.tmp\Default\Code Cache\js\index | binary | |
MD5:54CB446F628B2EA4A5BCE5769910512E | SHA256:FBCFE23A2ECB82B7100C50811691DDE0A33AA3DA8D176BE9882A9DB485DC0F2D | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr82DA.tmp\Crashpad\settings.dat | binary | |
MD5:5E9A06A186A12B66746F74ED71987F91 | SHA256:6093ADA4BDC6B937FB3A3FB08A6D24D8622494A527AC792DC7F32C91AAA52B5A | |||
| 6812 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chr82DA.tmp\Default\Code Cache\wasm\index | binary | |
MD5:54CB446F628B2EA4A5BCE5769910512E | SHA256:FBCFE23A2ECB82B7100C50811691DDE0A33AA3DA8D176BE9882A9DB485DC0F2D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
60
DNS requests
47
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6384 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7084 | BUILD0~1.EXE | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | shared |
6948 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6948 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2972 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2220 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.194:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5064 | SearchApp.exe | 2.23.227.221:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2436 | Deushack.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1488 | Deushack.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7084 | BUILD0~1.EXE | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7128 | svchost.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 4 |
5000 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
5000 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr82DA.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chr900A.tmp directory exists )
|