| File name: | Paysafecard_bekommen.exe |
| Full analysis: | https://app.any.run/tasks/b933733c-519e-446a-966f-e12cc23c7583 |
| Verdict: | Malicious activity |
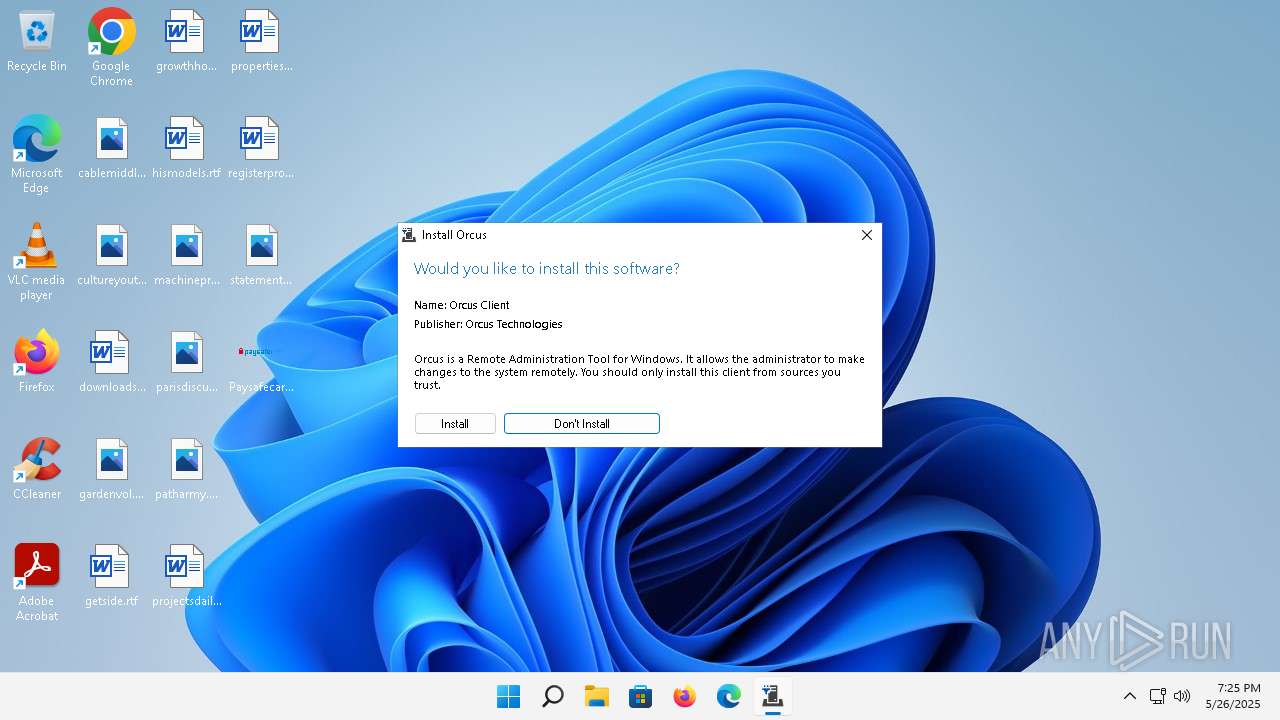
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | May 26, 2025, 19:24:51 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 796A2A42325218585C3376753AD59972 |
| SHA1: | 53DA2671FB13C1A9895C20A928172DF26D18F526 |
| SHA256: | 4D04D42CFE479FEED8D1B6DEABE90BC92C5B1DED049329093C821447DF16594B |
| SSDEEP: | 24576:5sQ3d3P51k22nQE7Wj6wogps/+LLjhvdUUgiWNVYdrZlI0AilFEvxHiW6s:5sKd3P51k22nQE7Wj6wogps/+L/hbWNC |
MALICIOUS
Orcus is detected
- Paysafecard_bekommen.exe (PID: 2692)
- Paysafecard_bekommen.exe (PID: 948)
- Orcus.exe (PID: 1084)
- Orcus.exe (PID: 3408)
Changes the autorun value in the registry
- Orcus.exe (PID: 1084)
ORCUS has been detected (YARA)
- Orcus.exe (PID: 1084)
SUSPICIOUS
Executable content was dropped or overwritten
- csc.exe (PID: 868)
- csc.exe (PID: 2188)
- Paysafecard_bekommen.exe (PID: 948)
Reads the Internet Settings
- Paysafecard_bekommen.exe (PID: 2692)
- Paysafecard_bekommen.exe (PID: 948)
Reads the date of Windows installation
- Paysafecard_bekommen.exe (PID: 2692)
- Paysafecard_bekommen.exe (PID: 948)
Reads security settings of Internet Explorer
- Paysafecard_bekommen.exe (PID: 2692)
- Paysafecard_bekommen.exe (PID: 948)
Application launched itself
- Paysafecard_bekommen.exe (PID: 2692)
Write to the desktop.ini file (may be used to cloak folders)
- Paysafecard_bekommen.exe (PID: 948)
Starts itself from another location
- Paysafecard_bekommen.exe (PID: 948)
Connects to unusual port
- Orcus.exe (PID: 1084)
There is functionality for taking screenshot (YARA)
- Orcus.exe (PID: 1084)
INFO
Checks supported languages
- Paysafecard_bekommen.exe (PID: 2692)
- csc.exe (PID: 868)
- cvtres.exe (PID: 2612)
- Paysafecard_bekommen.exe (PID: 948)
- csc.exe (PID: 2188)
- cvtres.exe (PID: 5952)
- Orcus.exe (PID: 1084)
- Orcus.exe (PID: 3408)
Reads the machine GUID from the registry
- Paysafecard_bekommen.exe (PID: 2692)
- csc.exe (PID: 868)
- cvtres.exe (PID: 2612)
- Paysafecard_bekommen.exe (PID: 948)
- csc.exe (PID: 2188)
- cvtres.exe (PID: 5952)
- Orcus.exe (PID: 1084)
- Orcus.exe (PID: 3408)
Create files in a temporary directory
- Paysafecard_bekommen.exe (PID: 2692)
- cvtres.exe (PID: 2612)
- csc.exe (PID: 868)
- csc.exe (PID: 2188)
- Paysafecard_bekommen.exe (PID: 948)
- cvtres.exe (PID: 5952)
Creates files or folders in the user directory
- Paysafecard_bekommen.exe (PID: 2692)
- Orcus.exe (PID: 3408)
Reads the computer name
- Paysafecard_bekommen.exe (PID: 2692)
- Paysafecard_bekommen.exe (PID: 948)
- Orcus.exe (PID: 1084)
- Orcus.exe (PID: 3408)
Creates files in the program directory
- Paysafecard_bekommen.exe (PID: 948)
Manual execution by a user
- Orcus.exe (PID: 3408)
Launch of the file from Registry key
- Orcus.exe (PID: 1084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Orcus
(PID) Process(1084) Orcus.exe
C2 (1)91.218.65.24:10134
Keys
AESfa9e1429db4b657edbcde9be2c1960aa74305077e2a592c01c9aaa2e98ad14db
Salt
Options
AutostartBuilderProperty
AutostartMethodRegistry
TaskSchedulerTaskNameOrcus
TaskHighestPrivilegestrue
RegistryHiddenStarttrue
RegistryKeyNameSystem
TryAllAutostartMethodsOnFailtrue
ChangeAssemblyInformationBuilderProperty
ChangeAssemblyInformationtrue
AssemblyTitlepaysafecard
AssemblyDescriptionnull
AssemblyCompanyNamenull
AssemblyProductNamenull
AssemblyCopyrightnull
AssemblyTrademarksnull
AssemblyProductVersion1.0.0.0
AssemblyFileVersion1.0.0.0
ChangeCreationDateBuilderProperty
IsEnabledfalse
NewCreationDate2019-06-09T21:34:41
ChangeIconBuilderProperty
ChangeIcontrue
IconPathC:\Users\Administrator\Downloads\paysafe-card.ico
ClientTagBuilderProperty
ClientTagnull
DataFolderBuilderProperty
Path%appdata%\Orcus
DefaultPrivilegesBuilderProperty
RequireAdministratorRightsfalse
DisableInstallationPromptBuilderProperty
IsDisabledfalse
FrameworkVersionBuilderProperty
FrameworkVersionNET35
HideFileBuilderProperty
HideFiletrue
InstallationLocationBuilderProperty
Path%programfiles%\Orcus\Orcus.exe
InstallBuilderProperty
Installtrue
KeyloggerBuilderProperty
IsEnabledtrue
MutexBuilderProperty
Mutexfd6ceba7b8b64b48a497798c7a31c837
ProxyBuilderProperty
ProxyOptionNone
ProxyAddressnull
ProxyPort1080
ProxyType2
ReconnectDelayProperty
Delay10000
RequireAdministratorPrivilegesInstallerBuilderProperty
RequireAdministratorPrivilegestrue
RespawnTaskBuilderProperty
IsEnabledfalse
TaskNameOrcus Respawner
ServiceBuilderProperty
Installfalse
SetRunProgramAsAdminFlagBuilderProperty
SetFlagfalse
WatchdogBuilderProperty
IsEnabledfalse
NameOrcusWatchdog.exe
WatchdogLocationAppData
PreventFileDeletionfalse
Plugins (0)
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:06:09 19:42:33+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 920064 |
| InitializedDataSize: | 11264 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe299e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | paysafecard |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | Orcus.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
111
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\Windows\Microsoft.NET\Framework64\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\p6ejog5m.cmdline" | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\csc.exe | Paysafecard_bekommen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.9157 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 948 | "C:\Users\admin\Desktop\Paysafecard_bekommen.exe" /wait | C:\Users\admin\Desktop\Paysafecard_bekommen.exe | Paysafecard_bekommen.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1084 | "C:\Program Files\Orcus\Orcus.exe" | C:\Program Files\Orcus\Orcus.exe | Paysafecard_bekommen.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.0.0.0 Modules
Orcus(PID) Process(1084) Orcus.exe C2 (1)91.218.65.24:10134 Keys AESfa9e1429db4b657edbcde9be2c1960aa74305077e2a592c01c9aaa2e98ad14db Salt Options AutostartBuilderProperty AutostartMethodRegistry TaskSchedulerTaskNameOrcus TaskHighestPrivilegestrue RegistryHiddenStarttrue RegistryKeyNameSystem TryAllAutostartMethodsOnFailtrue ChangeAssemblyInformationBuilderProperty ChangeAssemblyInformationtrue AssemblyTitlepaysafecard AssemblyDescriptionnull AssemblyCompanyNamenull AssemblyProductNamenull AssemblyCopyrightnull AssemblyTrademarksnull AssemblyProductVersion1.0.0.0 AssemblyFileVersion1.0.0.0 ChangeCreationDateBuilderProperty IsEnabledfalse NewCreationDate2019-06-09T21:34:41 ChangeIconBuilderProperty ChangeIcontrue IconPathC:\Users\Administrator\Downloads\paysafe-card.ico ClientTagBuilderProperty ClientTagnull DataFolderBuilderProperty Path%appdata%\Orcus DefaultPrivilegesBuilderProperty RequireAdministratorRightsfalse DisableInstallationPromptBuilderProperty IsDisabledfalse FrameworkVersionBuilderProperty FrameworkVersionNET35 HideFileBuilderProperty HideFiletrue InstallationLocationBuilderProperty Path%programfiles%\Orcus\Orcus.exe InstallBuilderProperty Installtrue KeyloggerBuilderProperty IsEnabledtrue MutexBuilderProperty Mutexfd6ceba7b8b64b48a497798c7a31c837 ProxyBuilderProperty ProxyOptionNone ProxyAddressnull ProxyPort1080 ProxyType2 ReconnectDelayProperty Delay10000 RequireAdministratorPrivilegesInstallerBuilderProperty RequireAdministratorPrivilegestrue RespawnTaskBuilderProperty IsEnabledfalse TaskNameOrcus Respawner ServiceBuilderProperty Installfalse SetRunProgramAsAdminFlagBuilderProperty SetFlagfalse WatchdogBuilderProperty IsEnabledfalse NameOrcusWatchdog.exe WatchdogLocationAppData PreventFileDeletionfalse Plugins (0) | |||||||||||||||
| 1160 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2188 | "C:\Windows\Microsoft.NET\Framework64\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\itfqwghx.cmdline" | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\csc.exe | Paysafecard_bekommen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.9157 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 2612 | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES5951.tmp" "c:\Users\admin\AppData\Local\Temp\CSC5950.tmp" | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.9680 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\Desktop\Paysafecard_bekommen.exe" | C:\Users\admin\Desktop\Paysafecard_bekommen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Orcus\Orcus.exe" | C:\Program Files\Orcus\Orcus.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5672 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5952 | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES7E2E.tmp" "c:\Users\admin\AppData\Local\Temp\CSC7E2D.tmp" | C:\Windows\Microsoft.NET\Framework64\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.9680 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
Total events
1 511
Read events
1 493
Write events
18
Delete events
0
Modification events
| (PID) Process: | (2692) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2692) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2692) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2692) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (948) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (948) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (948) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (948) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (948) Paysafecard_bekommen.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D28010000BD0E0C47735D584D9CEDE91E22E23282290100006078A409B011A54DAFA526D86198A7801302000060B81DB4E464D2119906E49FADC173CAD40100000114020000000000C000000000000046BF020000 | |||
| (PID) Process: | (1084) Orcus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | System |
Value: "C:\Program Files\Orcus\Orcus.exe" | |||
Executable files
3
Suspicious files
5
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2692 | Paysafecard_bekommen.exe | C:\Users\admin\AppData\Local\Temp\p6ejog5m.0.cs | text | |
MD5:A59BD4AB1E0DF53582D9F74CAD1EDBC0 | SHA256:4CC7C2C13D1534340F61412312B8E2E7BBEC52D4A8003BAD4AB27F766BE5DB64 | |||
| 868 | csc.exe | C:\Users\admin\AppData\Local\Temp\p6ejog5m.out | text | |
MD5:3777DE410A1105DF05C06DB0261424D8 | SHA256:90E8E9EC01C8C1A92CE0DBECB8FCDB42A138CF80CA2FD06CED6E71D27F1AC258 | |||
| 868 | csc.exe | C:\Users\admin\AppData\Local\Temp\p6ejog5m.dll | executable | |
MD5:7DE83072F6508B84418392BF5BB116F4 | SHA256:296F30915E75D61CD42DF9DB12EA3CDDD585A1C02317DA625A5C9924291EE234 | |||
| 2612 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES5951.tmp | binary | |
MD5:D49925A57D099AB834A896EB8DD7C1F4 | SHA256:4AE0A6BEDF6B209D8C8CD62D321D9676397EF9DB2E6B04B181B6D86D3CE75543 | |||
| 868 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC5950.tmp | binary | |
MD5:282E3A8EF3E0F428C53538034A5F14C0 | SHA256:5B3DC68011ABC968FF5351D8AEF0E956216F9898651B5A2C6564094061C6D3ED | |||
| 2692 | Paysafecard_bekommen.exe | C:\Users\admin\AppData\Local\Temp\p6ejog5m.cmdline | text | |
MD5:88D18CAADD123706826D626FD43C586C | SHA256:505AE84A5F6B210F946A8C1C272BD151E21B58F6DCC00B0CABFE30172A64E7EE | |||
| 2188 | csc.exe | C:\Users\admin\AppData\Local\Temp\itfqwghx.out | text | |
MD5:7FF64C815F94E125BCC9F15A576449E7 | SHA256:C1B5A196247925D21717E5719A418066889F96902E4FF41EF4483350193406D1 | |||
| 2692 | Paysafecard_bekommen.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v2.0\UsageLogs\Paysafecard_bekommen.exe.log | text | |
MD5:7055D791013082485EA6F118CB552462 | SHA256:4C8848096B86351CA097A6B94C33E5FC6CEAE75DFA85964A0F8C784F81785173 | |||
| 948 | Paysafecard_bekommen.exe | C:\Users\admin\AppData\Local\Temp\itfqwghx.0.cs | text | |
MD5:C36D190FBFD7F1720A8D9B1512829702 | SHA256:9E6910B31017F8230FB8AF32EDC7F0F6D837540D247BF3EDA620E6C2A1CBE126 | |||
| 948 | Paysafecard_bekommen.exe | C:\Users\admin\AppData\Local\Temp\itfqwghx.cmdline | text | |
MD5:B074F7945BB6176753DB886626AC984F | SHA256:E6F6479748AB0C76EC9F4ED7CD8A170FCF88B82424E7705D7B6AE645FBFF3670 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
29
DNS requests
9
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2576 | smartscreen.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?aa7b47d57d7a5f18 | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.191.45.158:443 | https://checkappexec.microsoft.com/windows/shell/actions | unknown | binary | 182 b | whitelisted |
1352 | svchost.exe | GET | 200 | 184.24.77.4:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.75:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.69:443 | https://login.live.com/RST2.srf | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 23.212.222.21:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
— | — | GET | 200 | 23.212.222.21:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | binary | 55 b | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6fdd1136c0f80710 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?364df18d80c9fc5b | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.189.173.6:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1352 | svchost.exe | 184.24.77.4:80 | — | Akamai International B.V. | DE | unknown |
2576 | smartscreen.exe | 20.56.187.20:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2576 | smartscreen.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
4632 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3640 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4132 | svchost.exe | 23.212.222.21:443 | fs.microsoft.com | AKAMAI-AS | AU | whitelisted |
2776 | svchost.exe | 51.104.15.252:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
1084 | Orcus.exe | 91.218.65.24:10134 | — | SYNLINQ | DE | unknown |
2768 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |