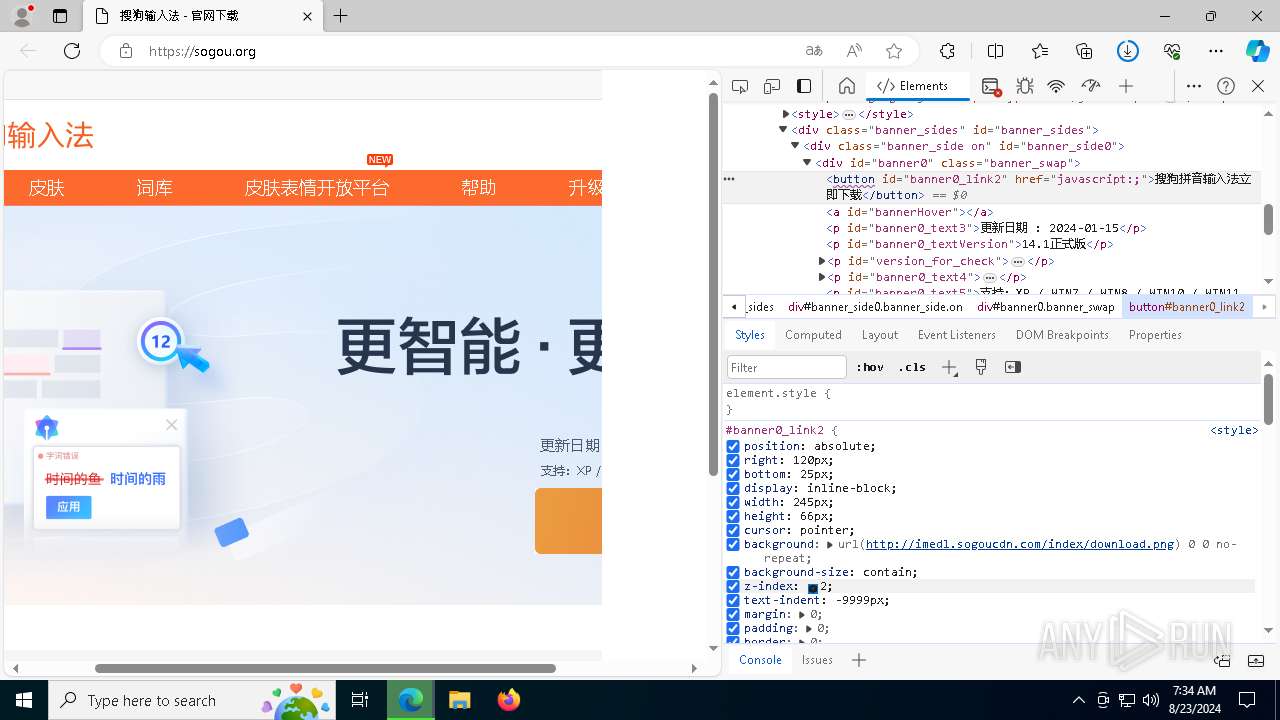
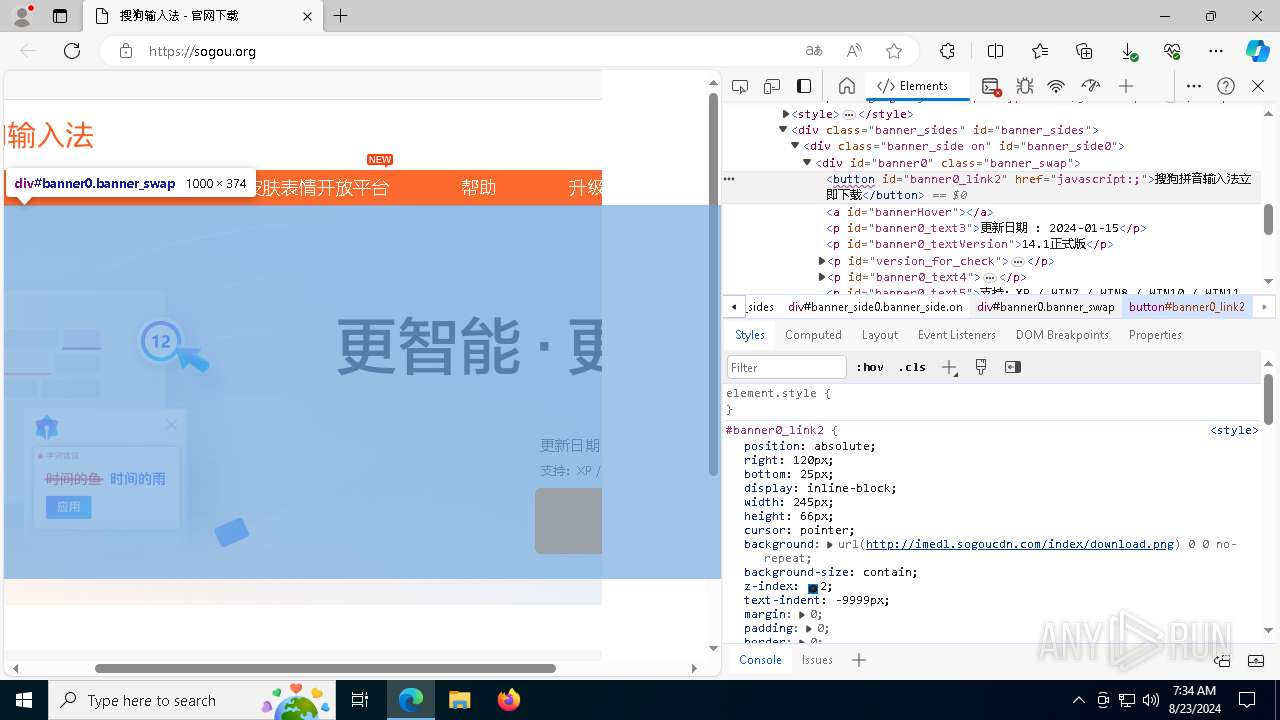
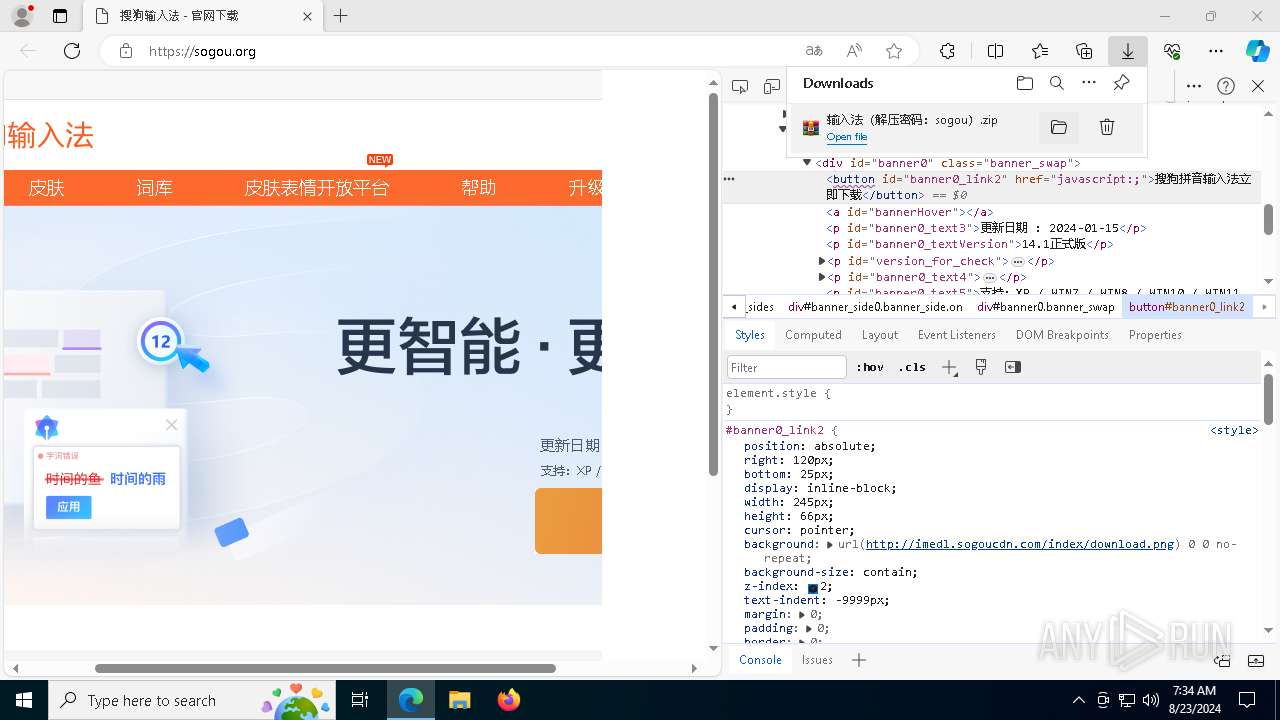
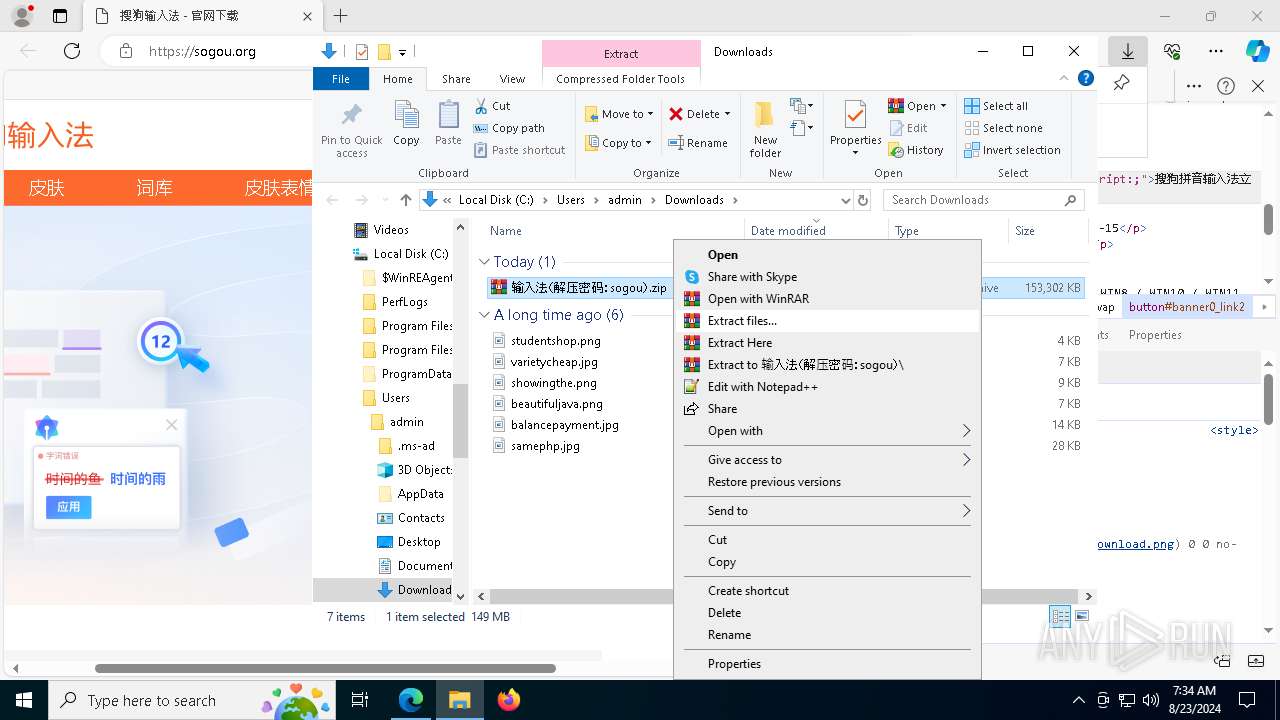
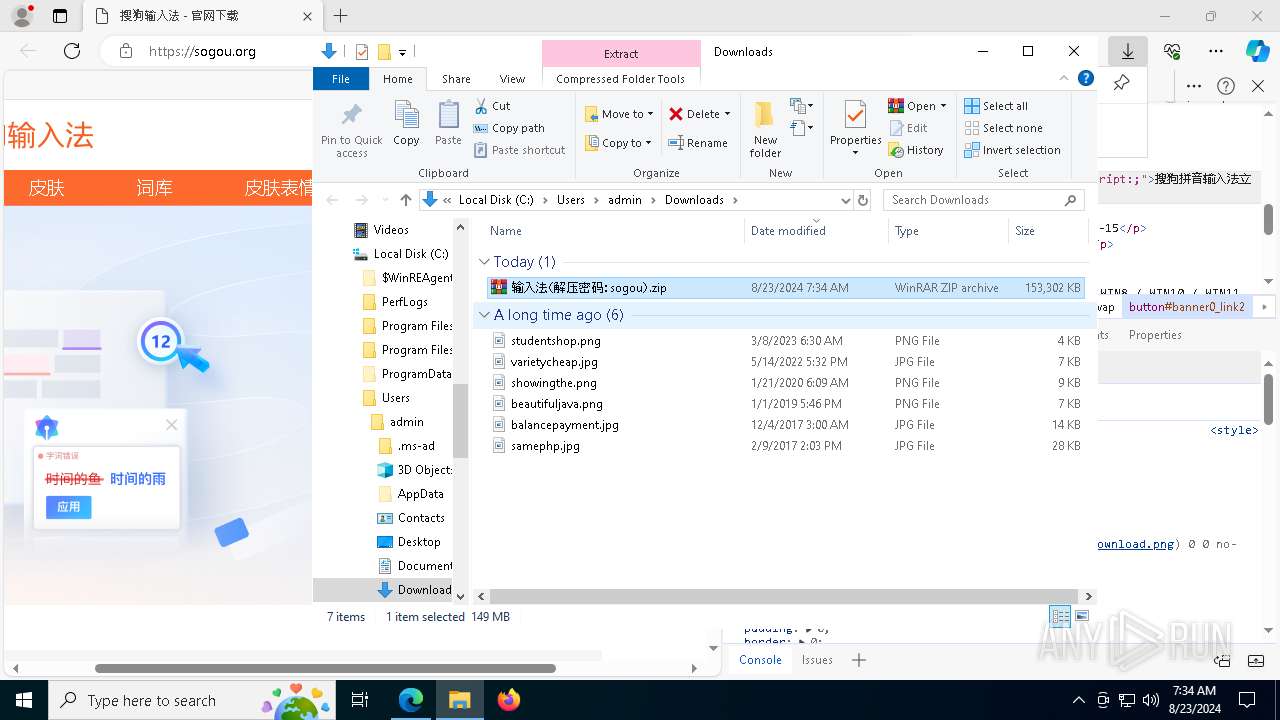
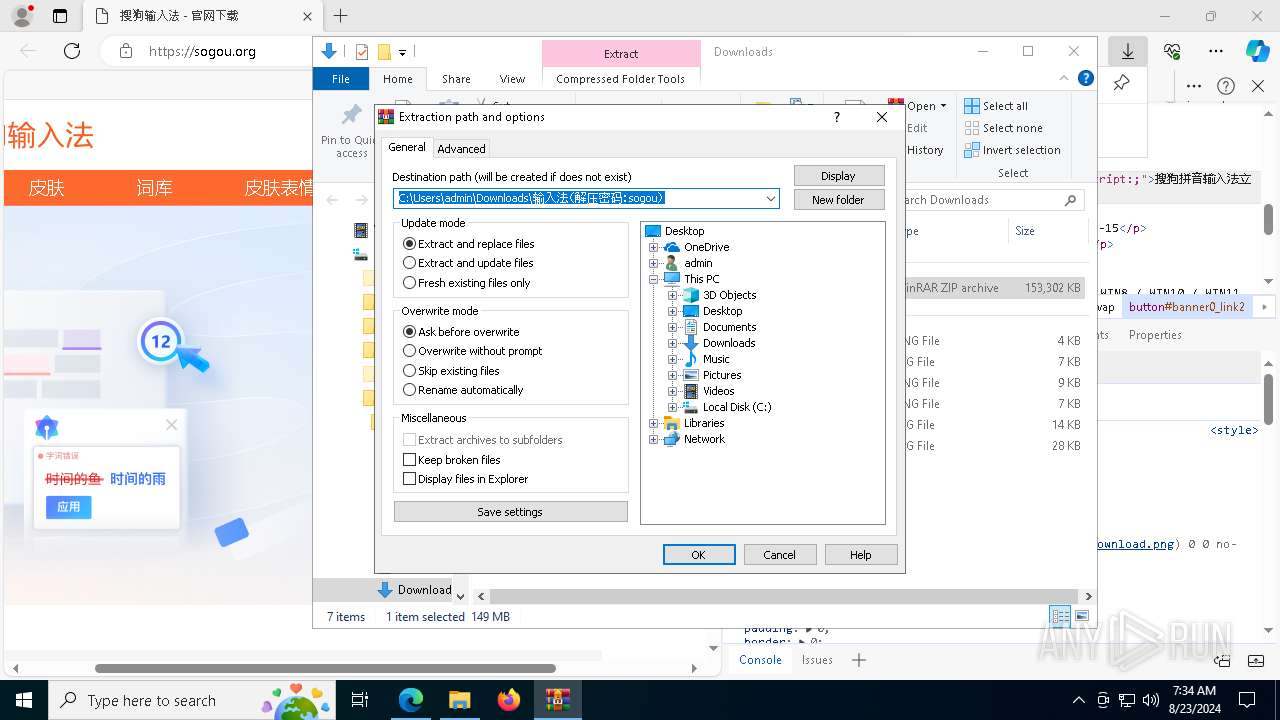
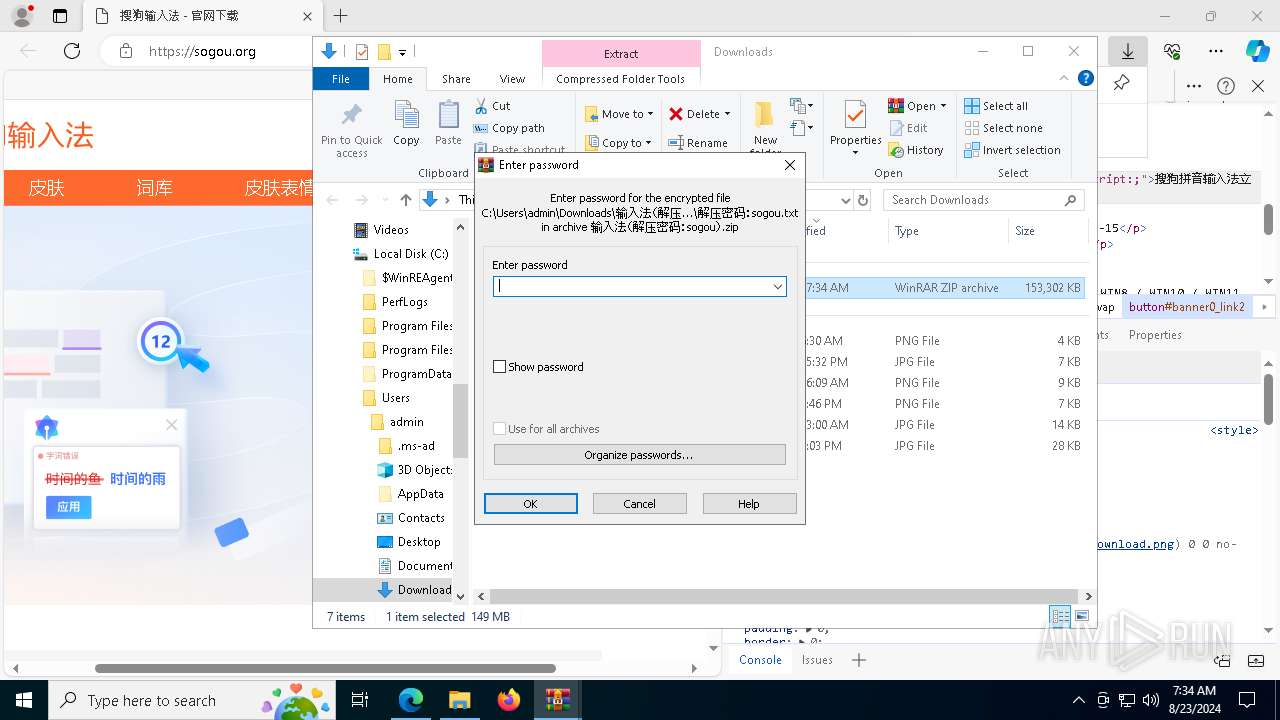
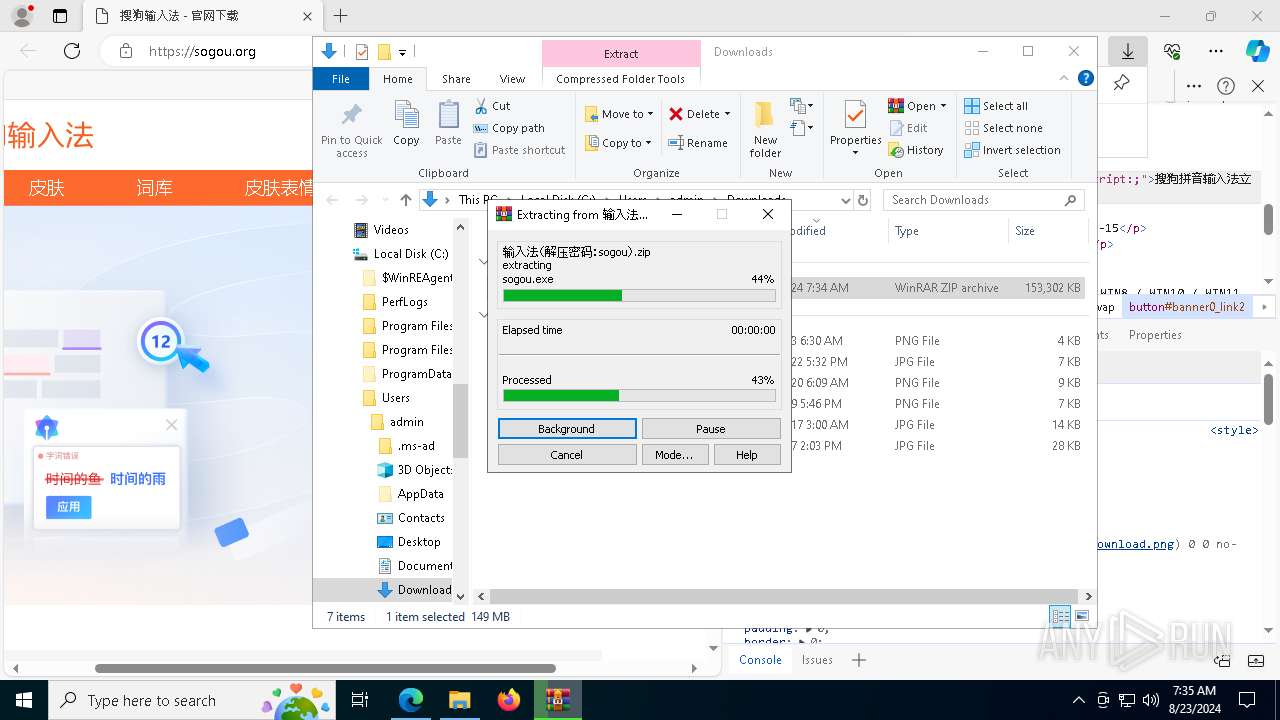
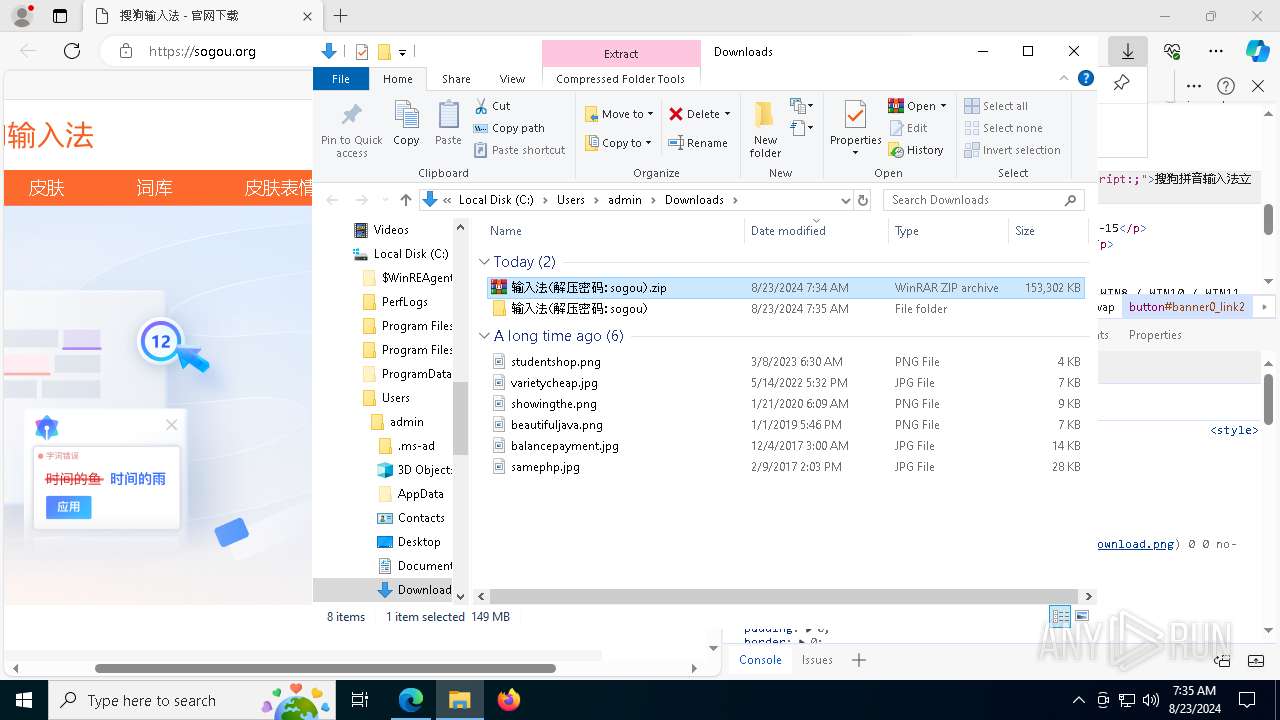
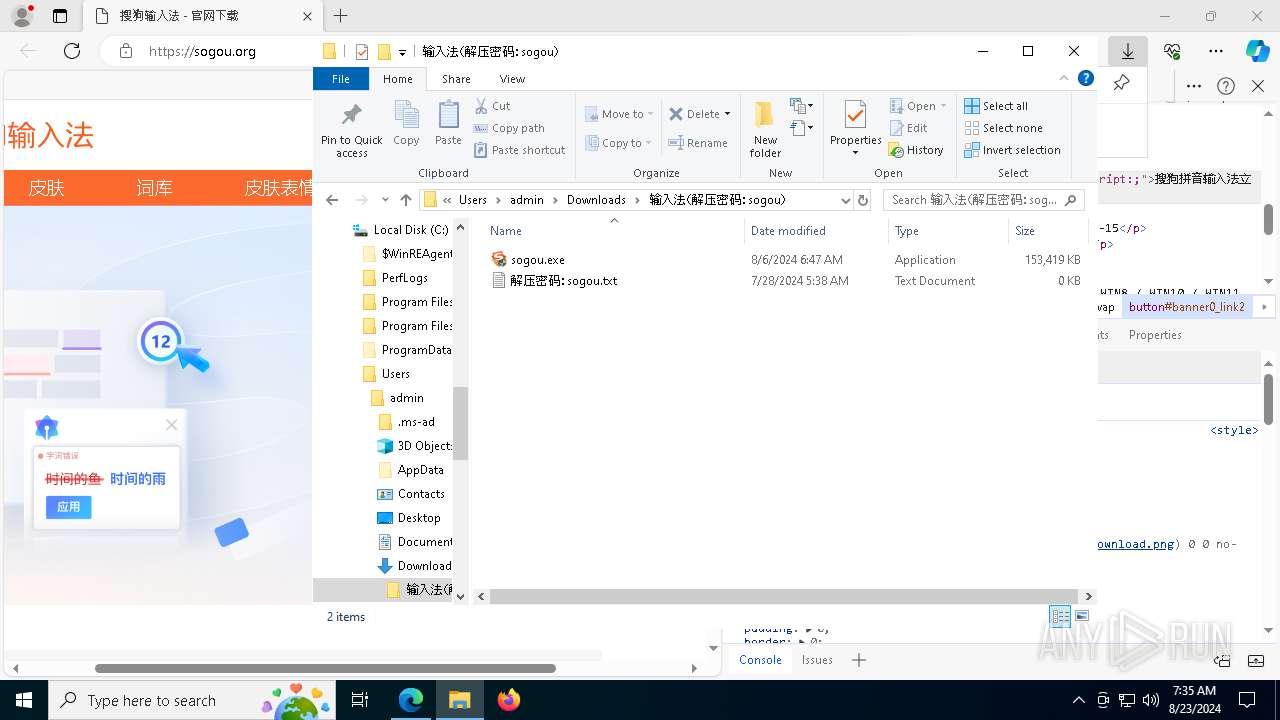
| URL: | sogou.org |
| Full analysis: | https://app.any.run/tasks/da28e3c7-d29a-4a9e-a051-99f1bf1d7646 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | August 23, 2024, 07:31:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 45411AC82CEAB1C44E98D5FA9BDF0A22 |
| SHA1: | 5DA11045E7632DB62812354E9E68DFF13D73BF67 |
| SHA256: | 4CA73FCECD476FBFDE659D80A565CF165369798A2792998B6C8946EF6E5489F0 |
| SSDEEP: | 3:GD:GD |
MALICIOUS
RHADAMANTHYS has been detected (SURICATA)
- OpenWith.exe (PID: 8172)
- OOBE-Maintenance.exe (PID: 7808)
Actions looks like stealing of personal data
- OOBE-Maintenance.exe (PID: 7808)
Registers / Runs the DLL via REGSVR32.EXE
- sogou_pinyin.exe (PID: 6472)
- Install64.exe (PID: 5772)
- biz_helper.exe (PID: 7512)
Signature: RAMNIT has been detected
- regsvr32.exe (PID: 7192)
- regsvr32.exe (PID: 6320)
EXPLOIT has been detected (SURICATA)
- SGBizLauncher.exe (PID: 7852)
SUSPICIOUS
Executable content was dropped or overwritten
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouExe.exe (PID: 7336)
- SogouExe.exe (PID: 4192)
- SogouExe.exe (PID: 7348)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- SogouComMgr.exe (PID: 7136)
Reads security settings of Internet Explorer
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- Install64.exe (PID: 5772)
- SGTool.exe (PID: 8080)
- SogouExe.exe (PID: 7336)
- SGTool.exe (PID: 7868)
- SGTool.exe (PID: 1292)
- SogouExe.exe (PID: 4192)
- SogouExe.exe (PID: 7348)
- SogouExe.exe (PID: 6916)
- SGTool.exe (PID: 7944)
- SGTool.exe (PID: 1048)
- SogouExe.exe (PID: 6388)
- SGTool.exe (PID: 7796)
- SogouExe.exe (PID: 7748)
- SogouComMgr.exe (PID: 7136)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- SogouComMgr.exe (PID: 7996)
- SGBizLauncher.exe (PID: 7852)
Checks Windows Trust Settings
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouExe.exe (PID: 7336)
- SogouExe.exe (PID: 4192)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 7748)
- SogouExe.exe (PID: 7348)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- SogouComMgr.exe (PID: 7136)
- SogouComMgr.exe (PID: 7996)
Drops the executable file immediately after the start
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouExe.exe (PID: 7336)
- SogouExe.exe (PID: 4192)
- SogouExe.exe (PID: 7348)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- SogouComMgr.exe (PID: 7136)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 8172)
- sogou_pinyin.exe (PID: 6472)
Malware-specific behavior (creating "System.dll" in Temp)
- sogou_pinyin.exe (PID: 6472)
The process creates files with name similar to system file names
- sogou_pinyin.exe (PID: 6472)
- SogouComMgr.exe (PID: 7136)
Starts POWERSHELL.EXE for commands execution
- SogouAnquan.exe (PID: 3876)
Contacting a server suspected of hosting an CnC
- OpenWith.exe (PID: 8172)
- OOBE-Maintenance.exe (PID: 7808)
Connects to unusual port
- OpenWith.exe (PID: 8172)
- SogouAnquan.exe (PID: 7948)
- OOBE-Maintenance.exe (PID: 7808)
The process executes via Task Scheduler
- SogouAnquan.exe (PID: 7948)
Searches for installed software
- OOBE-Maintenance.exe (PID: 7808)
Loads DLL from Mozilla Firefox
- OOBE-Maintenance.exe (PID: 7808)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 4344)
- regsvr32.exe (PID: 5468)
- regsvr32.exe (PID: 5908)
- regsvr32.exe (PID: 6788)
- regsvr32.exe (PID: 7192)
- regsvr32.exe (PID: 6320)
Reads the date of Windows installation
- Install64.exe (PID: 5772)
- SGTool.exe (PID: 8080)
- sogou_pinyin.exe (PID: 6472)
- SGTool.exe (PID: 1292)
- SGTool.exe (PID: 7868)
- SGTool.exe (PID: 7944)
- SGTool.exe (PID: 1048)
- SGTool.exe (PID: 7796)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 7748)
- SogouExe.exe (PID: 6388)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- SogouComMgr.exe (PID: 7136)
Creates a software uninstall entry
- sogou_pinyin.exe (PID: 6472)
Creates file in the systems drive root
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- sogou_pinyin.exe (PID: 6472)
Reads the BIOS version
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
Application launched itself
- biz_helper.exe (PID: 7188)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 8172)
INFO
Reads the computer name
- identity_helper.exe (PID: 7176)
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouAnquan.exe (PID: 3876)
- SogouAnquan.exe (PID: 7948)
- Install64.exe (PID: 5772)
- SGTool.exe (PID: 8080)
- SogouExe.exe (PID: 7336)
- SGTool.exe (PID: 7868)
- SGTool.exe (PID: 1292)
- SogouExe.exe (PID: 4192)
- SogouExe.exe (PID: 7348)
- SogouSvc.exe (PID: 7968)
- SogouExe.exe (PID: 6916)
- SGTool.exe (PID: 1048)
- SGTool.exe (PID: 7944)
- SogouExe.exe (PID: 6388)
- SGTool.exe (PID: 7796)
- SogouExe.exe (PID: 7748)
- SGTool.exe (PID: 5248)
- userNetSchedule.exe (PID: 7556)
- SGTool.exe (PID: 7152)
- SGTool.exe (PID: 5088)
- SGTool.exe (PID: 5548)
- SogouImeBroker.exe (PID: 6316)
- SogouComMgr.exe (PID: 7136)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- SGTool.exe (PID: 7752)
- SogouComMgr.exe (PID: 7996)
- SGBizLauncher.exe (PID: 7852)
Reads Environment values
- identity_helper.exe (PID: 7176)
- SogouAnquan.exe (PID: 7948)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 7748)
- SogouExe.exe (PID: 6388)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- sogou_pinyin.exe (PID: 6472)
Application launched itself
- msedge.exe (PID: 6588)
Manual execution by a user
- WinRAR.exe (PID: 3728)
- sogou.exe (PID: 8168)
- sogou.exe (PID: 7180)
Create files in a temporary directory
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouComMgr.exe (PID: 7996)
Checks proxy server information
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouAnquan.exe (PID: 7948)
- SogouExe.exe (PID: 7336)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouComMgr.exe (PID: 7136)
- SogouExe.exe (PID: 7748)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- SogouComMgr.exe (PID: 7996)
- SGBizLauncher.exe (PID: 7852)
Creates files or folders in the user directory
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SGTool.exe (PID: 8080)
- SogouExe.exe (PID: 7336)
- SGTool.exe (PID: 7868)
- SogouExe.exe (PID: 4192)
- SGTool.exe (PID: 1292)
- SogouExe.exe (PID: 7348)
- SGTool.exe (PID: 7944)
- SogouExe.exe (PID: 6916)
- SGTool.exe (PID: 1048)
- SogouExe.exe (PID: 6388)
- userNetSchedule.exe (PID: 7556)
- SGTool.exe (PID: 7152)
- SGTool.exe (PID: 7796)
- SogouExe.exe (PID: 7748)
- SGTool.exe (PID: 5248)
- SGTool.exe (PID: 5104)
- SGTool.exe (PID: 5088)
- SGTool.exe (PID: 5548)
- biz_helper.exe (PID: 7188)
- SogouComMgr.exe (PID: 7136)
- SGTool.exe (PID: 7752)
- SogouComMgr.exe (PID: 7996)
Checks supported languages
- identity_helper.exe (PID: 7176)
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouAnquan.exe (PID: 3696)
- SogouAnquan.exe (PID: 3876)
- SogouAnquan.exe (PID: 7948)
- wmpshare.exe (PID: 4092)
- SGTool.exe (PID: 4980)
- Install64.exe (PID: 5772)
- SGTool.exe (PID: 8080)
- SogouExe.exe (PID: 7336)
- SGTool.exe (PID: 7868)
- SogouExe.exe (PID: 4192)
- SGTool.exe (PID: 1292)
- SogouExe.exe (PID: 7348)
- SGIGuideHelper.exe (PID: 1280)
- SogouSvc.exe (PID: 7968)
- SGTool.exe (PID: 7944)
- SogouExe.exe (PID: 6916)
- SGTool.exe (PID: 1048)
- SGTool.exe (PID: 7796)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- userNetSchedule.exe (PID: 7556)
- SGTool.exe (PID: 7152)
- SGTool.exe (PID: 5248)
- SGTool.exe (PID: 5104)
- SGTool.exe (PID: 5088)
- SGTool.exe (PID: 5548)
- biz_helper.exe (PID: 7188)
- SogouImeBroker.exe (PID: 6316)
- SogouComMgr.exe (PID: 7136)
- biz_helper.exe (PID: 7512)
- biz_helper.exe (PID: 5712)
- biz_helper.exe (PID: 5092)
- biz_helper.exe (PID: 320)
- SGTool.exe (PID: 7752)
- SogouComMgr.exe (PID: 7996)
- SGBizLauncher.exe (PID: 7852)
- SGBizLauncher.exe (PID: 5244)
Reads the software policy settings
- sogou.exe (PID: 7180)
- sogou_pinyin.exe (PID: 6472)
- SogouAnquan.exe (PID: 7948)
- regsvr32.exe (PID: 5908)
- regsvr32.exe (PID: 5468)
- regsvr32.exe (PID: 6788)
- SogouExe.exe (PID: 7336)
- SogouExe.exe (PID: 4192)
- SogouExe.exe (PID: 7348)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- biz_helper.exe (PID: 5092)
- biz_helper.exe (PID: 7188)
- SogouComMgr.exe (PID: 7136)
- SogouComMgr.exe (PID: 7996)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6588)
Reads the machine GUID from the registry
- sogou.exe (PID: 7180)
- SogouAnquan.exe (PID: 3876)
- sogou_pinyin.exe (PID: 6472)
- SogouAnquan.exe (PID: 7948)
- SogouExe.exe (PID: 7336)
- SogouExe.exe (PID: 4192)
- SogouExe.exe (PID: 7348)
- wmpshare.exe (PID: 4092)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- SogouComMgr.exe (PID: 7136)
- SogouComMgr.exe (PID: 7996)
- SGBizLauncher.exe (PID: 7852)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7648)
Disables trace logs
- SogouAnquan.exe (PID: 7948)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7648)
Creates files in the program directory
- sogou_pinyin.exe (PID: 6472)
- SogouExe.exe (PID: 7336)
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouComMgr.exe (PID: 7136)
- biz_helper.exe (PID: 7512)
- biz_helper.exe (PID: 320)
- biz_helper.exe (PID: 5712)
- biz_helper.exe (PID: 5092)
- SGTool.exe (PID: 7752)
- SGBizLauncher.exe (PID: 7852)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7648)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- SogouAnquan.exe (PID: 7948)
Found Base64 encoded reference to WMI classes (YARA)
- SogouAnquan.exe (PID: 7948)
Process checks computer location settings
- Install64.exe (PID: 5772)
- SGTool.exe (PID: 8080)
- SGTool.exe (PID: 7868)
- SGTool.exe (PID: 1292)
- SGTool.exe (PID: 7944)
- SGTool.exe (PID: 1048)
- SGTool.exe (PID: 7796)
- SogouComMgr.exe (PID: 7136)
- sogou_pinyin.exe (PID: 6472)
Reads security settings of Internet Explorer
- regsvr32.exe (PID: 5908)
- regsvr32.exe (PID: 5468)
- regsvr32.exe (PID: 6788)
Dropped object may contain TOR URL's
- sogou_pinyin.exe (PID: 6472)
UPX packer has been detected
- sogou_pinyin.exe (PID: 6472)
Reads product name
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 6388)
- SogouExe.exe (PID: 7748)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
- sogou_pinyin.exe (PID: 6472)
Reads Windows Product ID
- SogouExe.exe (PID: 6916)
- SogouExe.exe (PID: 7748)
- SogouExe.exe (PID: 6388)
- biz_helper.exe (PID: 7188)
- biz_helper.exe (PID: 5092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
256
Monitored processes
116
Malicious processes
22
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files (x86)\SogouInput\Components\biz_center\1.0.0.2387\biz_helper.exe" --type=cp --subtype=reg | C:\Program Files (x86)\SogouInput\Components\biz_center\1.0.0.2387\biz_helper.exe | — | biz_helper.exe | |||||||||||
User: admin Company: Sogou.com Integrity Level: HIGH Description: 搜狗输入法 辅助程序 Exit code: 0 Version: 1.0.0.2387 Modules
| |||||||||||||||
| 420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7648 --field-trial-handle=2244,i,17068815275004683292,8658771200956583673,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1048 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7120 --field-trial-handle=2244,i,17068815275004683292,8658771200956583673,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1048 | "C:\Program Files (x86)\SogouInput\14.7.0.9739\SGTool.exe" --appid=scdreg -register "C:\Program Files (x86)\SogouInput\14.7.0.9739" | C:\Program Files (x86)\SogouInput\14.7.0.9739\SGTool.exe | — | sogou_pinyin.exe | |||||||||||
User: admin Company: Sogou.com Integrity Level: HIGH Description: 搜狗输入法 工具 Exit code: 0 Version: 14.7.0.9739 Modules
| |||||||||||||||
| 1280 | "C:\Program Files (x86)\SogouInput\14.7.0.9739\SGIGuideHelper.exe" --action=if --fp="C:\Program Files (x86)\SogouInput\14.7.0.9739\HYZhongHeiTi-197.ttf" --fn="汉仪中黑 197" | C:\Program Files (x86)\SogouInput\14.7.0.9739\SGIGuideHelper.exe | — | sogou_pinyin.exe | |||||||||||
User: admin Company: Sogou.com Integrity Level: HIGH Description: 搜狗输入法 生僻字安装工具 Exit code: 0 Version: 14.7.0.9739 Modules
| |||||||||||||||
| 1292 | "C:\Program Files (x86)\SogouInput\14.7.0.9739\SGTool.exe" --appid=pinyinrepair /k | C:\Program Files (x86)\SogouInput\14.7.0.9739\SGTool.exe | — | sogou_pinyin.exe | |||||||||||
User: admin Company: Sogou.com Integrity Level: HIGH Description: 搜狗输入法 工具 Exit code: 0 Version: 14.7.0.9739 Modules
| |||||||||||||||
| 1440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7500 --field-trial-handle=2244,i,17068815275004683292,8658771200956583673,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1656 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7056 --field-trial-handle=2244,i,17068815275004683292,8658771200956583673,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7012 --field-trial-handle=2244,i,17068815275004683292,8658771200956583673,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
98 309
Read events
97 660
Write events
588
Delete events
61
Modification events
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6588) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
114
Suspicious files
453
Text files
391
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11df32.TMP | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF11df32.TMP | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11df32.TMP | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF11df8f.TMP | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF11dfaf.TMP | — | |
MD5:— | SHA256:— | |||
| 6588 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
135
DNS requests
96
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6888 | msedge.exe | GET | 301 | 137.175.124.141:80 | http://sogou.org/ | unknown | — | — | unknown |
7292 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2628 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7868 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1616 | svchost.exe | HEAD | 200 | 23.48.23.43:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1724992716&P2=404&P3=2&P4=EDD01YajlK2BfGtcVA7DRQjzAUEf5%2brqk3zbPAL8cPRPeUGRJkZC1xzAxe0n%2beIKwOSYFesvtKBON1Vfsny7YA%3d%3d | unknown | — | — | whitelisted |
7568 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1616 | svchost.exe | GET | 206 | 23.48.23.43:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1724992716&P2=404&P3=2&P4=EDD01YajlK2BfGtcVA7DRQjzAUEf5%2brqk3zbPAL8cPRPeUGRJkZC1xzAxe0n%2beIKwOSYFesvtKBON1Vfsny7YA%3d%3d | unknown | — | — | whitelisted |
1616 | svchost.exe | GET | 206 | 23.48.23.43:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1724992716&P2=404&P3=2&P4=EDD01YajlK2BfGtcVA7DRQjzAUEf5%2brqk3zbPAL8cPRPeUGRJkZC1xzAxe0n%2beIKwOSYFesvtKBON1Vfsny7YA%3d%3d | unknown | — | — | whitelisted |
1616 | svchost.exe | GET | 206 | 23.48.23.43:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7b9cac0d-9ca2-42ef-9c46-ce975d51335a?P1=1724992716&P2=404&P3=2&P4=EDD01YajlK2BfGtcVA7DRQjzAUEf5%2brqk3zbPAL8cPRPeUGRJkZC1xzAxe0n%2beIKwOSYFesvtKBON1Vfsny7YA%3d%3d | unknown | — | — | whitelisted |
1616 | svchost.exe | GET | 206 | 23.48.23.43:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/062b65bc-b6a4-4f5a-8413-7218292237fe?P1=1724901204&P2=404&P3=2&P4=cLqeDPhzTf3i1eqY%2bkiVD9VhHdHtKyrZTnrW71EBw6HM279I6GwU%2bfjRuJaWwvMAnOsEpzTOW1NMunYO9y4iVw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2208 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3384 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6888 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6588 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6888 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6888 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6888 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6888 | msedge.exe | 137.175.124.141:80 | sogou.org | PEGTECHINC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
sogou.org |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6888 | msedge.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
6888 | msedge.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
6888 | msedge.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
6888 | msedge.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
6888 | msedge.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
6472 | sogou_pinyin.exe | Misc activity | ET INFO Win32/Sogou User-Agent (SOGOU_UPDATER) |
2256 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7852 | SGBizLauncher.exe | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |
8 ETPRO signatures available at the full report