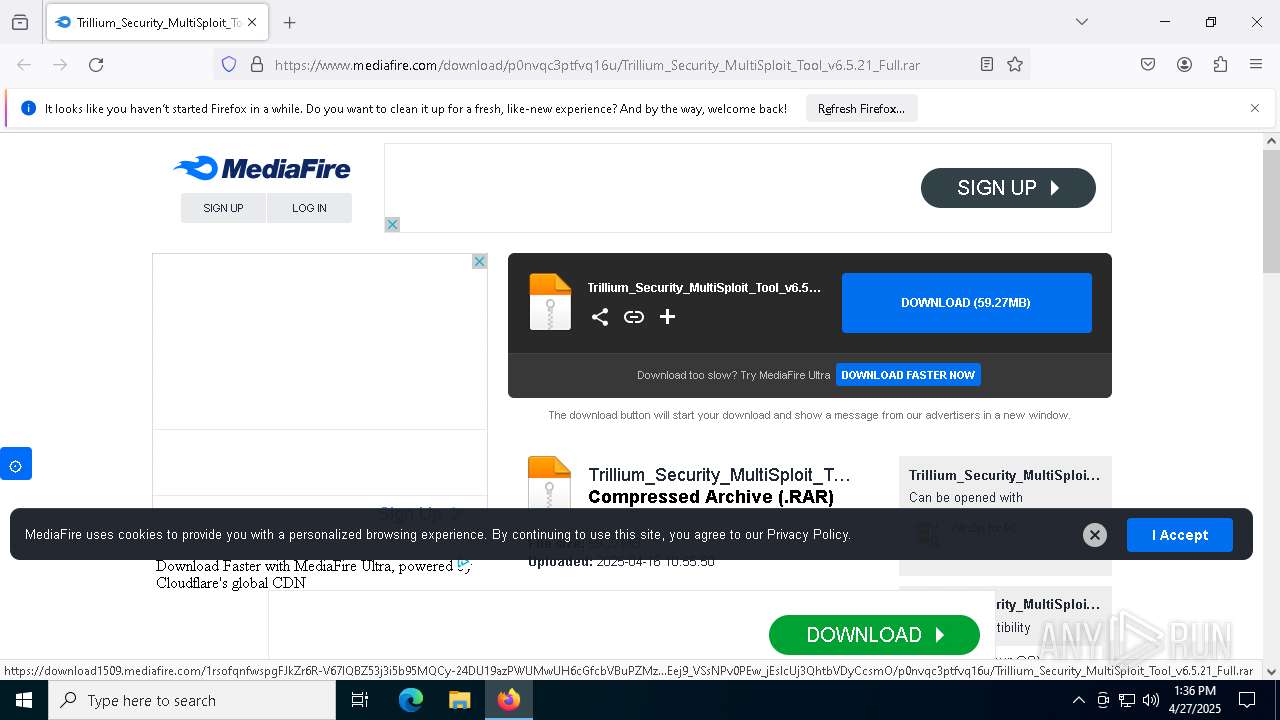
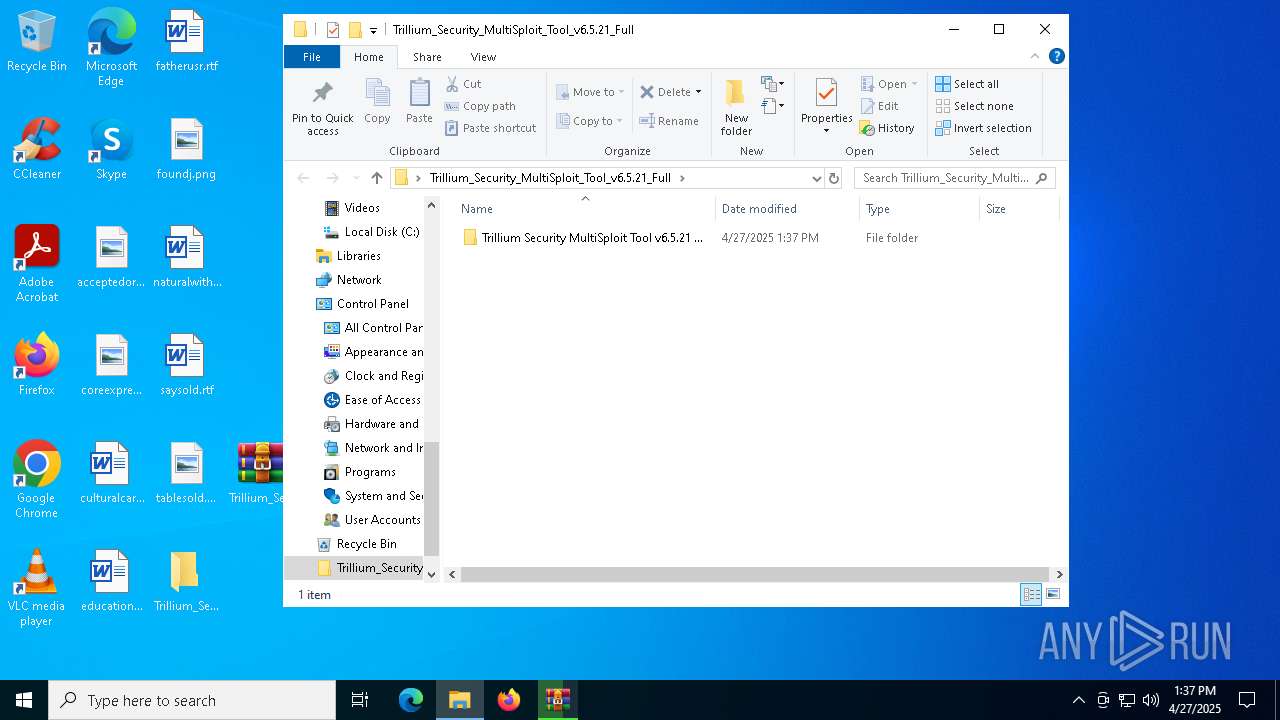
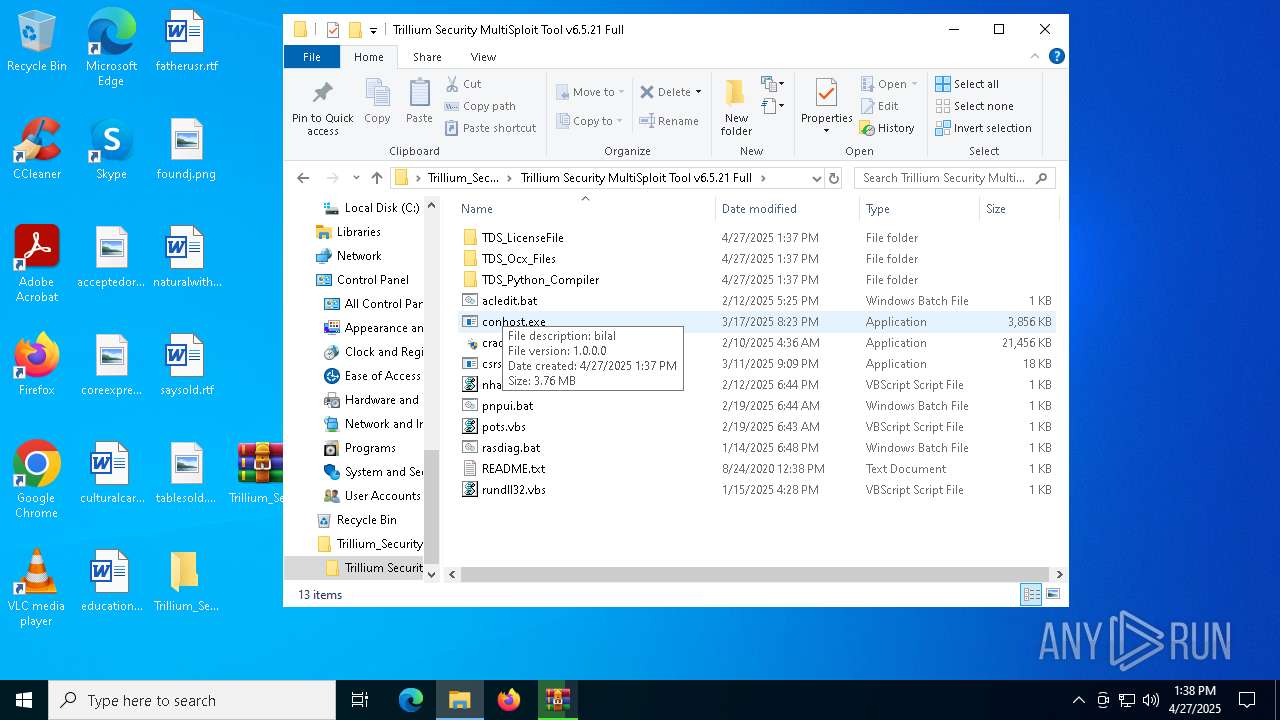
| URL: | https://www.mediafire.com/download/p0nvqc3ptfvq16u/Trillium_Security_MultiSploit_Tool_v6.5.21_Full.rar |
| Full analysis: | https://app.any.run/tasks/232dde81-d805-4f98-938d-8f06c8b26f0c |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | April 27, 2025, 13:36:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 80BF55C4D83EB3D4CA88244671E1F33D |
| SHA1: | CD5A4BE61AEF2713B331850C3319CA235140930F |
| SHA256: | 4C6BD12D36630DC7CD60E74B48A49BF9F558CEA7A490E53D3E0A75E1CF4A762E |
| SSDEEP: | 3:N8DSLw3eGWKLnSlY72A8RoQfTpkoNLX+n:2OLw3eGND2rTpkUan |
MALICIOUS
Vulnerable driver has been detected
- InstallUtil.exe (PID: 968)
XMRig has been detected
- OmegaEngine.exe (PID: 6768)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
- OmegaEngine.exe (PID: 6768)
XMRIG has been detected (YARA)
- InstallUtil.exe (PID: 968)
- OmegaEngine.exe (PID: 6768)
Connects to the CnC server
- OmegaEngine.exe (PID: 6768)
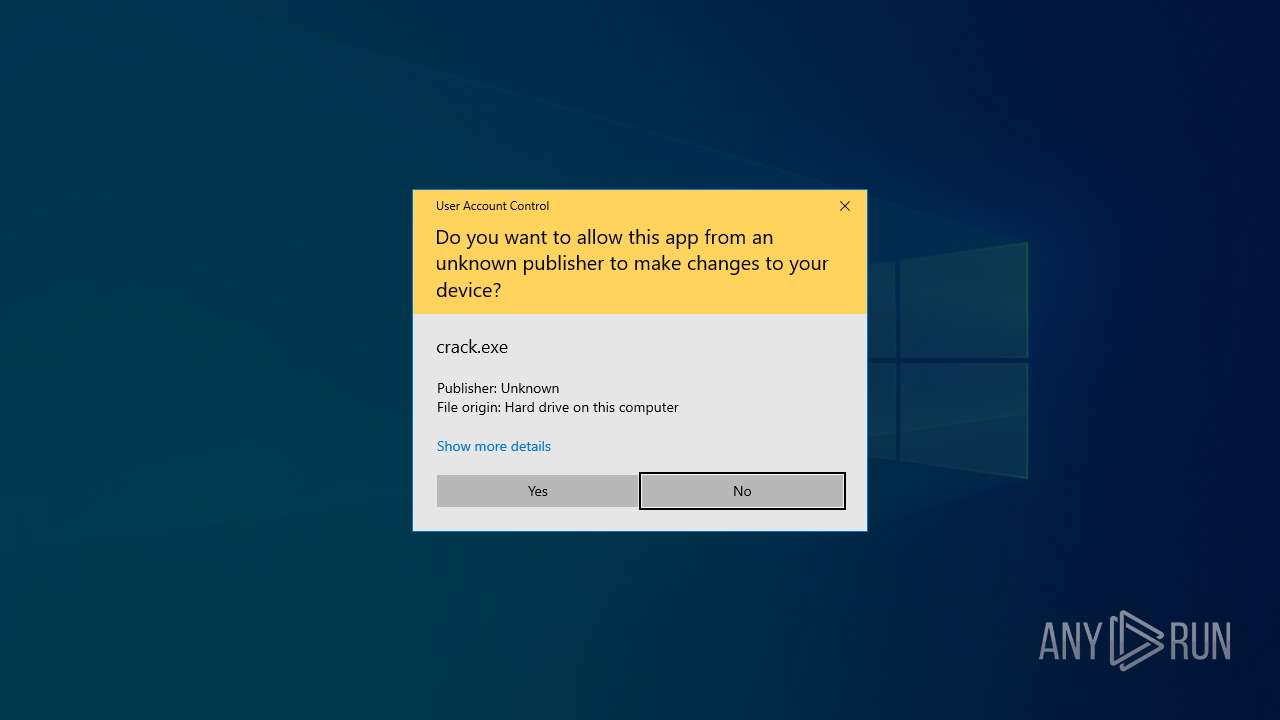
Executing a file with an untrusted certificate
- Built.exe (PID: 4996)
- Built.exe (PID: 7576)
Adds path to the Windows Defender exclusion list
- Built.exe (PID: 7576)
- cmd.exe (PID: 7464)
- cmd.exe (PID: 7868)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 2420)
Changes Controlled Folder Access settings
- powershell.exe (PID: 8632)
Changes Windows Defender settings
- cmd.exe (PID: 2420)
- cmd.exe (PID: 7464)
- cmd.exe (PID: 7868)
Changes settings for real-time protection
- powershell.exe (PID: 8632)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 8632)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 8632)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 8632)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 8632)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 8632)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 8564)
Bypass execution policy to execute commands
- powershell.exe (PID: 3332)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 5156)
BLANKGRABBER has been detected (SURICATA)
- Built.exe (PID: 7576)
SUSPICIOUS
Executable content was dropped or overwritten
- conhost.exe (PID: 900)
- InstallUtil.exe (PID: 968)
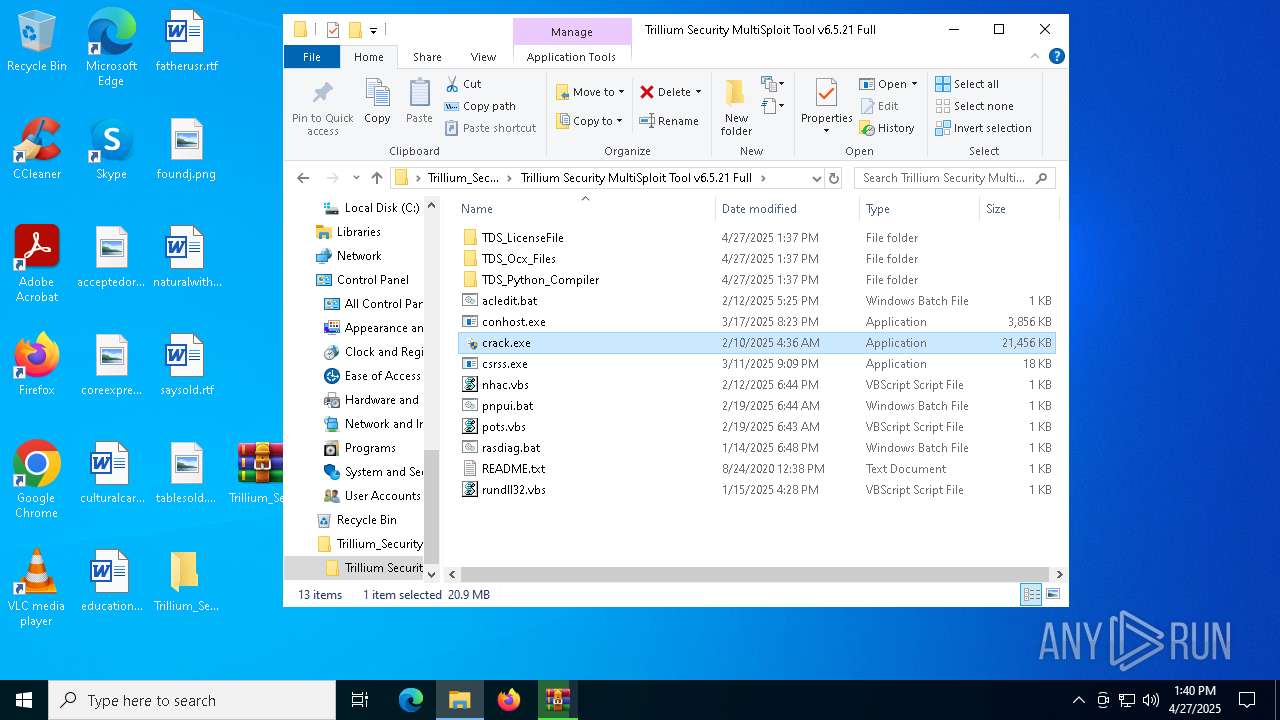
- crack.exe (PID: 456)
- Built.exe (PID: 4996)
- conhost.exe (PID: 2100)
- Built.exe (PID: 7576)
- csc.exe (PID: 8820)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6044)
- InstallUtil.exe (PID: 968)
- crack.exe (PID: 456)
- conhost.exe (PID: 2100)
- Built.exe (PID: 4996)
- Built.exe (PID: 7576)
Process drops python dynamic module
- WinRAR.exe (PID: 6044)
- Built.exe (PID: 4996)
- conhost.exe (PID: 2100)
Drops a system driver (possible attempt to evade defenses)
- InstallUtil.exe (PID: 968)
Potential Corporate Privacy Violation
- OmegaEngine.exe (PID: 6768)
Starts a Microsoft application from unusual location
- Built.exe (PID: 4996)
- Built.exe (PID: 7576)
The process drops C-runtime libraries
- Built.exe (PID: 4996)
- conhost.exe (PID: 2100)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Executes application which crashes
- svchost.exe (PID: 3888)
Application launched itself
- Built.exe (PID: 4996)
Script disables Windows Defender's IPS
- cmd.exe (PID: 2420)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 2420)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7464)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 8488)
- cmd.exe (PID: 8564)
- cmd.exe (PID: 8708)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 4976)
- cmd.exe (PID: 5360)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7464)
- cmd.exe (PID: 7868)
Found strings related to reading or modifying Windows Defender settings
- Built.exe (PID: 7576)
Starts CMD.EXE for commands execution
- Built.exe (PID: 7576)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 8064)
- cmd.exe (PID: 7448)
Get information on the list of running processes
- cmd.exe (PID: 8032)
- cmd.exe (PID: 1180)
- Built.exe (PID: 7576)
- cmd.exe (PID: 8440)
Starts application with an unusual extension
- cmd.exe (PID: 8476)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 8552)
- cmd.exe (PID: 8196)
- cmd.exe (PID: 5188)
- cmd.exe (PID: 4628)
Base64-obfuscated command line is found
- cmd.exe (PID: 8564)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 8564)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 8360)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 8564)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 8432)
CSC.EXE is used to compile C# code
- csc.exe (PID: 8820)
Checks for external IP
- Built.exe (PID: 7576)
- svchost.exe (PID: 2196)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Built.exe (PID: 7576)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 4324)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2476)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 9020)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 1164)
INFO
Application launched itself
- firefox.exe (PID: 5512)
- firefox.exe (PID: 1616)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6044)
The sample compiled with english language support
- WinRAR.exe (PID: 6044)
- InstallUtil.exe (PID: 968)
- conhost.exe (PID: 2100)
- Built.exe (PID: 4996)
The sample compiled with german language support
- WinRAR.exe (PID: 6044)
Reads the software policy settings
- slui.exe (PID: 1676)
Manual execution by a user
- WinRAR.exe (PID: 6044)
- conhost.exe (PID: 900)
- InstallUtil.exe (PID: 968)
- crack.exe (PID: 5592)
- crack.exe (PID: 8756)
- crack.exe (PID: 456)
The sample compiled with japanese language support
- InstallUtil.exe (PID: 968)
Checks the directory tree
- tree.com (PID: 7188)
- tree.com (PID: 8304)
- tree.com (PID: 540)
- tree.com (PID: 8300)
- tree.com (PID: 2568)
- tree.com (PID: 5176)
The Powershell gets current clipboard
- powershell.exe (PID: 7212)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 2392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
261
Monitored processes
123
Malicious processes
10
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
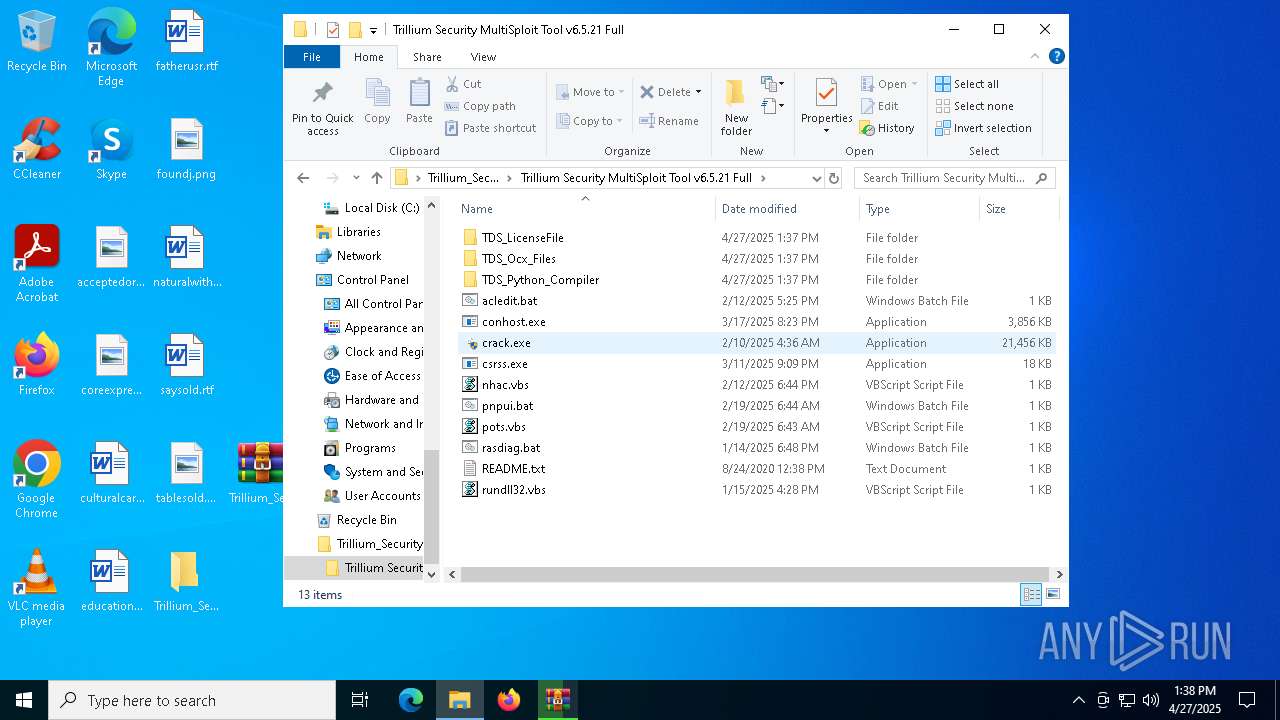
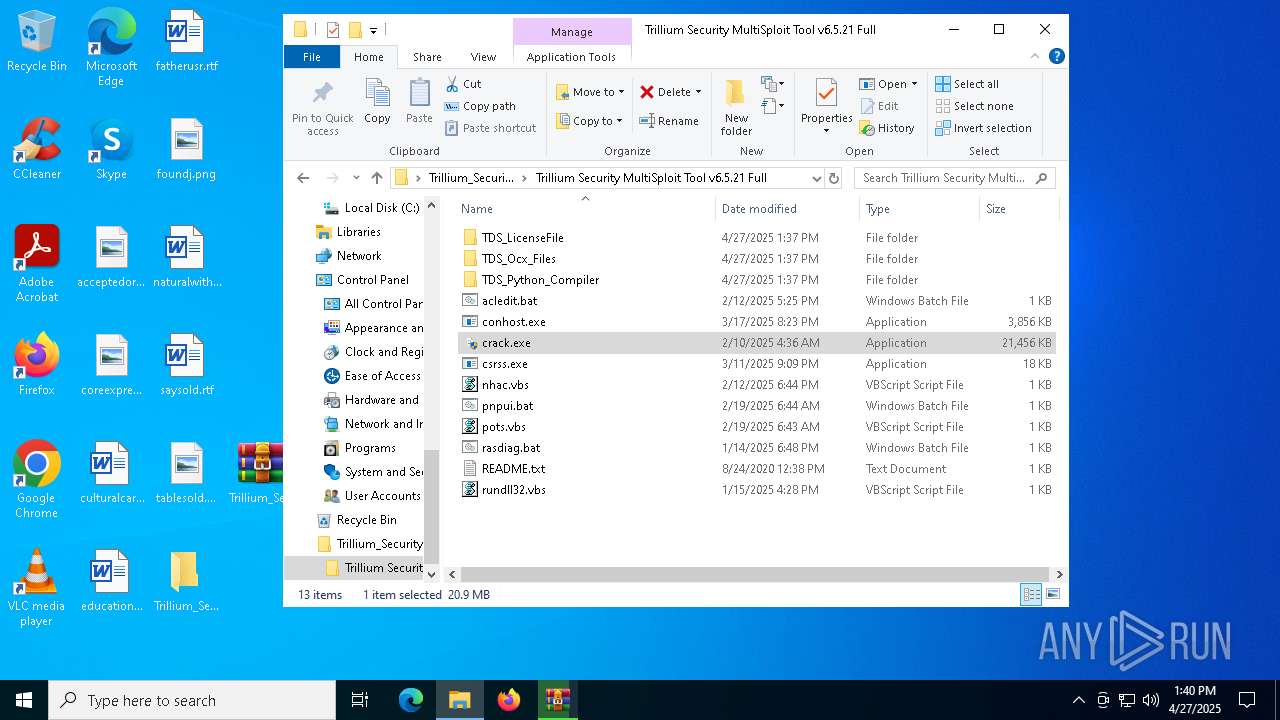
| 456 | "C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full\Trillium Security MultiSploit Tool v6.5.21 Full\crack.exe" | C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full\Trillium Security MultiSploit Tool v6.5.21 Full\crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 540 | tree /A /F | C:\Windows\System32\tree.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Tree Walk Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
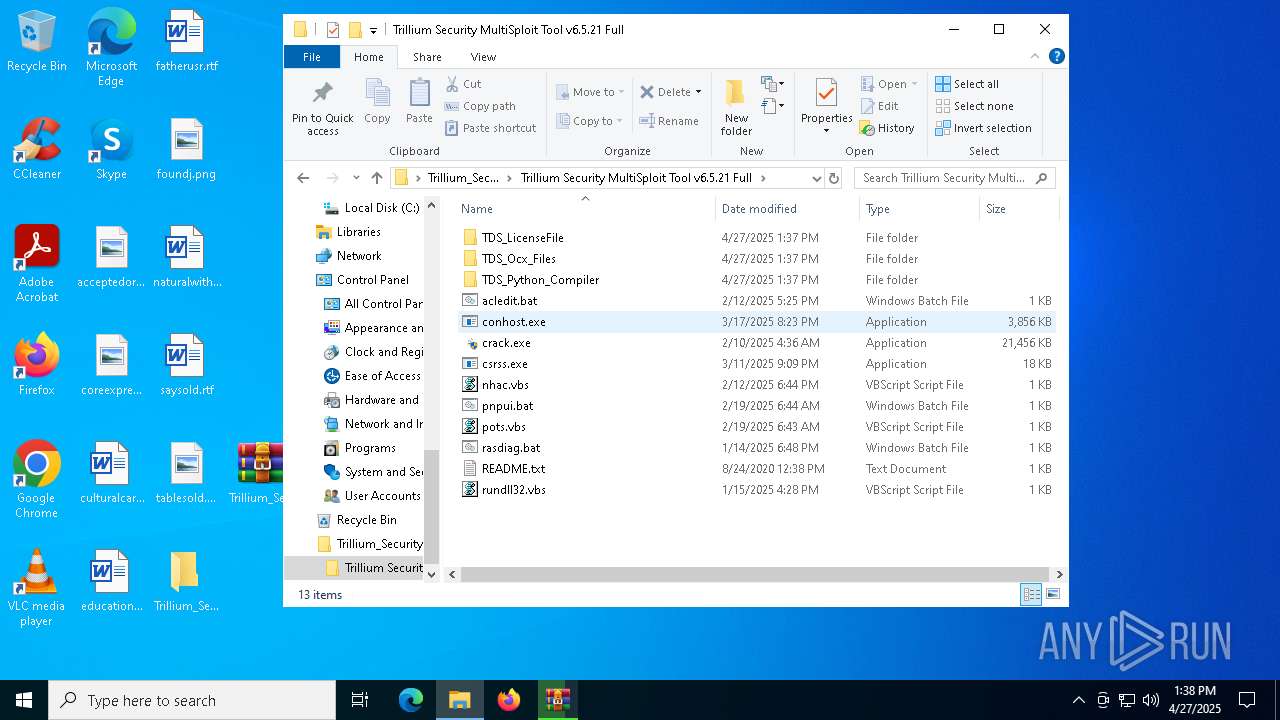
| 900 | "C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full\Trillium Security MultiSploit Tool v6.5.21 Full\conhost.exe" | C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full\Trillium Security MultiSploit Tool v6.5.21 Full\conhost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: bilal Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 968 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 980 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\_MEI49962\rar.exe a -r -hp"@adrik123@" "C:\Users\admin\AppData\Local\Temp\I7dLK.zip" *" | C:\Windows\System32\cmd.exe | — | Built.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | C:\WINDOWS\system32\cmd.exe /c "wmic path win32_VideoController get name" | C:\Windows\System32\cmd.exe | — | Built.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | Built.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1824 -parentBuildID 20240213221259 -prefsHandle 1760 -prefMapHandle 1744 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {7463322c-5b24-4ea7-a003-cf95c95a9617} 1616 "\\.\pipe\gecko-crash-server-pipe.1616" 21b967ee710 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
Total events
84 625
Read events
84 579
Write events
30
Delete events
16
Modification events
| (PID) Process: | (1616) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
Executable files
128
Suspicious files
848
Text files
3 255
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1616 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:3B156E12141F8CBCE9D60CDCE2077617 | SHA256:E6287E44B44ABEA20E1B2E3F415D22B9E5E5FBBC155AD9DADBABA63951B2AF6F | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:3B156E12141F8CBCE9D60CDCE2077617 | SHA256:E6287E44B44ABEA20E1B2E3F415D22B9E5E5FBBC155AD9DADBABA63951B2AF6F | |||
| 1616 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
75
TCP/UDP connections
312
DNS requests
330
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1616 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1616 | firefox.exe | POST | 200 | 142.250.185.67:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1616 | firefox.exe | POST | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1616 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
1616 | firefox.exe | POST | — | 142.250.185.67:80 | http://o.pki.goog/s/we1/sY8 | unknown | — | — | whitelisted |
1616 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1616 | firefox.exe | POST | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1616 | firefox.exe | POST | 200 | 142.250.185.67:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1616 | firefox.exe | 104.17.151.117:443 | www.mediafire.com | CLOUDFLARENET | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1616 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
1616 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
www.mediafire.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
prod.content-signature-chains.prod.webservices.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |