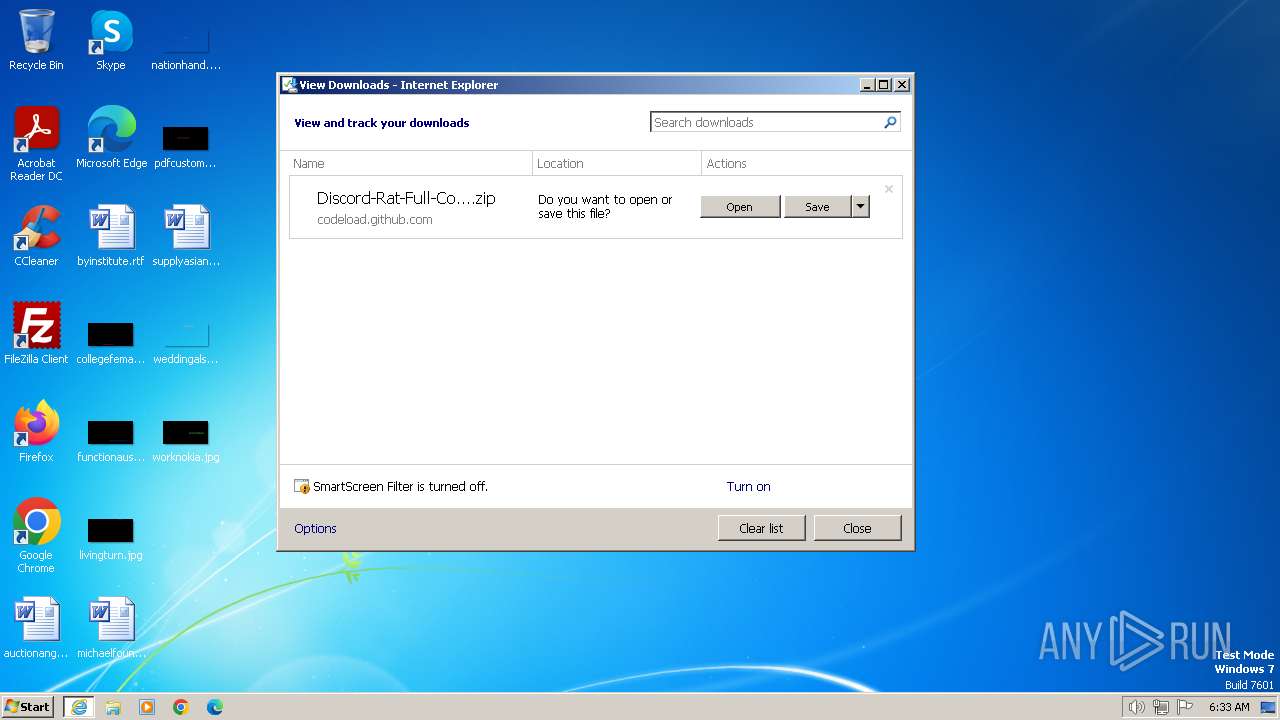
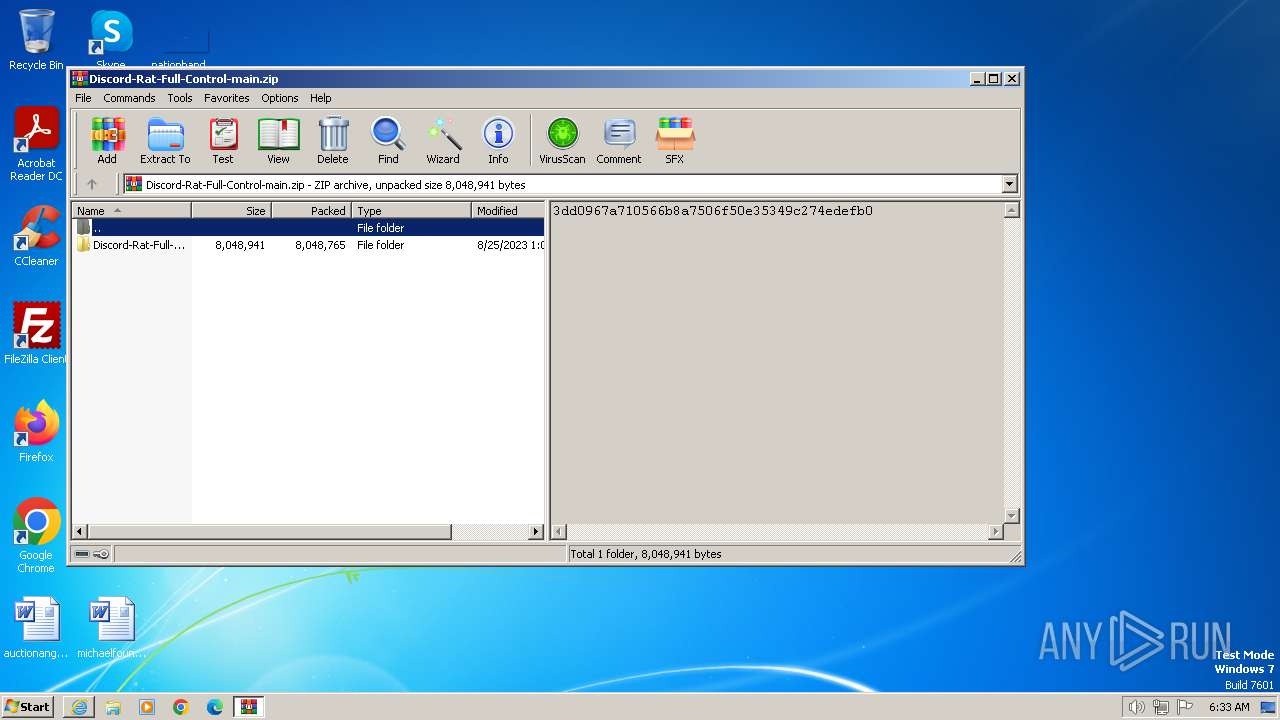
| URL: | https://github.com/ASTR0C0/Discord-Rat-Full-Control/archive/refs/heads/main.zip |
| Full analysis: | https://app.any.run/tasks/62eebfbd-c396-4c4f-8acc-1a7935044ac1 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 13, 2024, 06:33:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 381FF74928537E02C34FF341A91D6E18 |
| SHA1: | FF364F808677C22D14EB8F2C90016AD0488C1919 |
| SHA256: | 4BA672318920DD7CC2CBCA194E1F0525AEDF4136905B2700B344B5D7658D5198 |
| SSDEEP: | 3:N8tEdyFWde4bKlKXT4RSLNLc:2uaR7lKD4ULN4 |
MALICIOUS
Actions looks like stealing of personal data
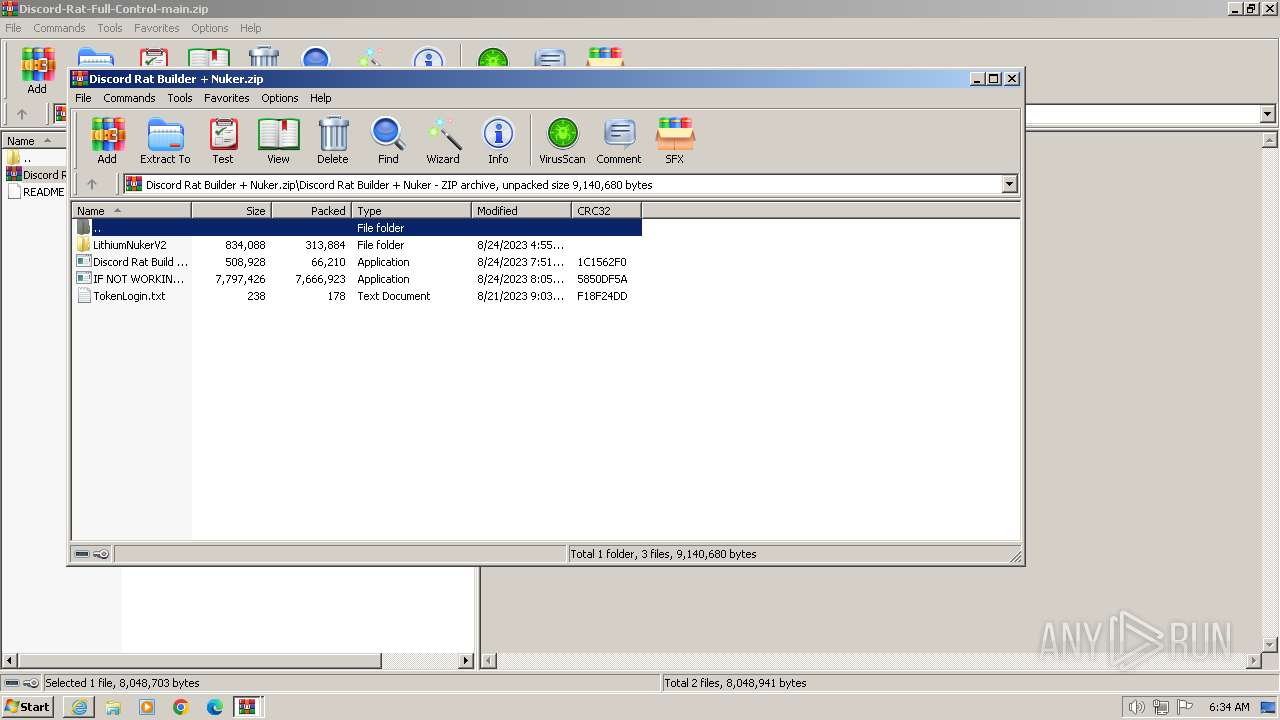
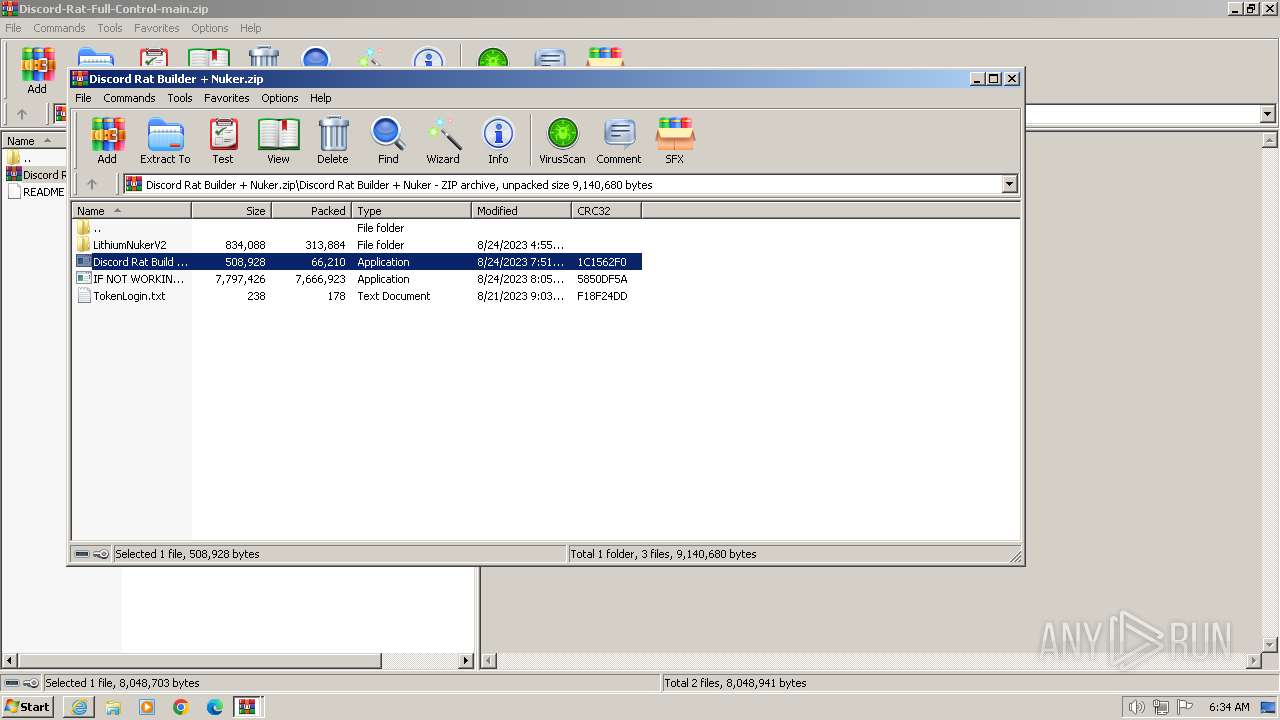
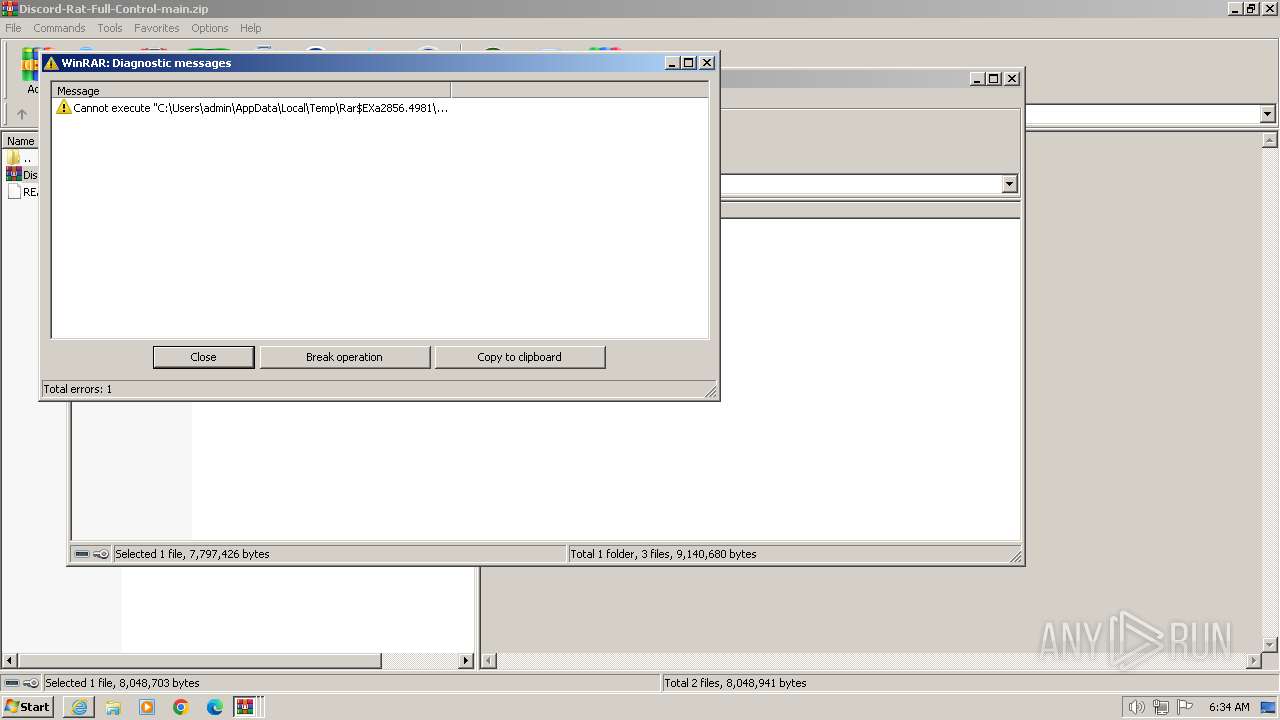
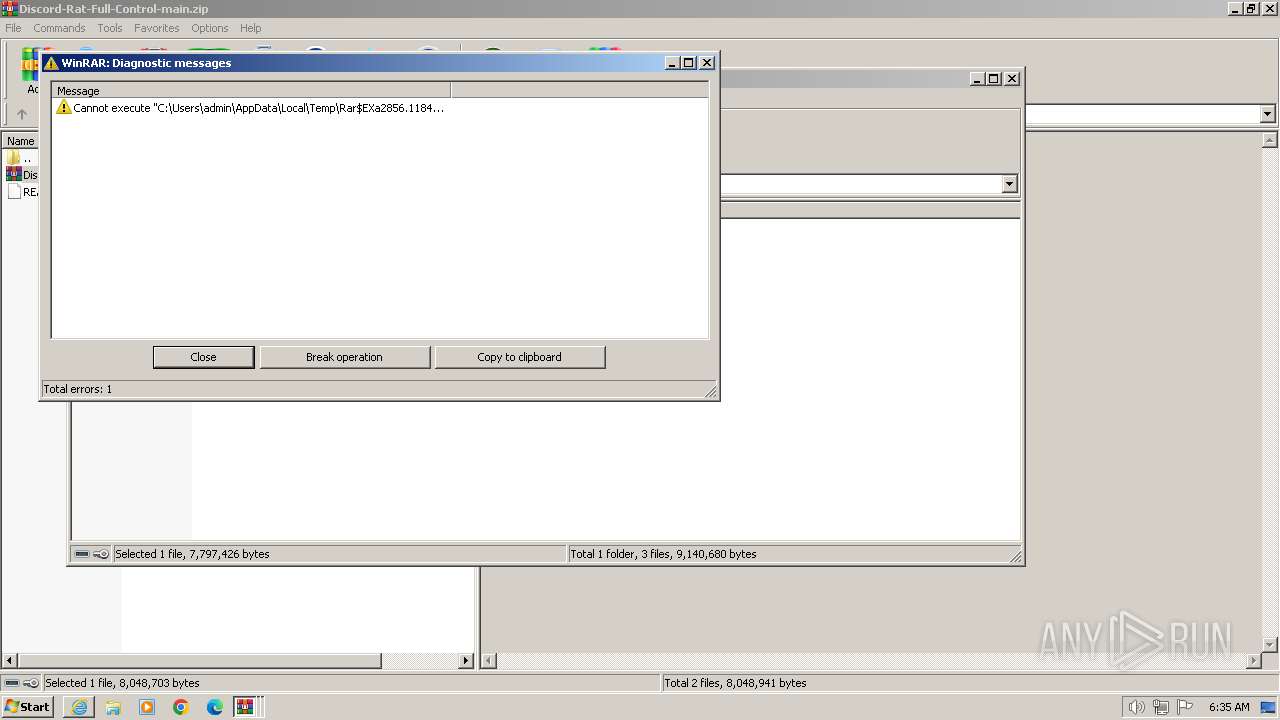
- WinRAR.exe (PID: 1836)
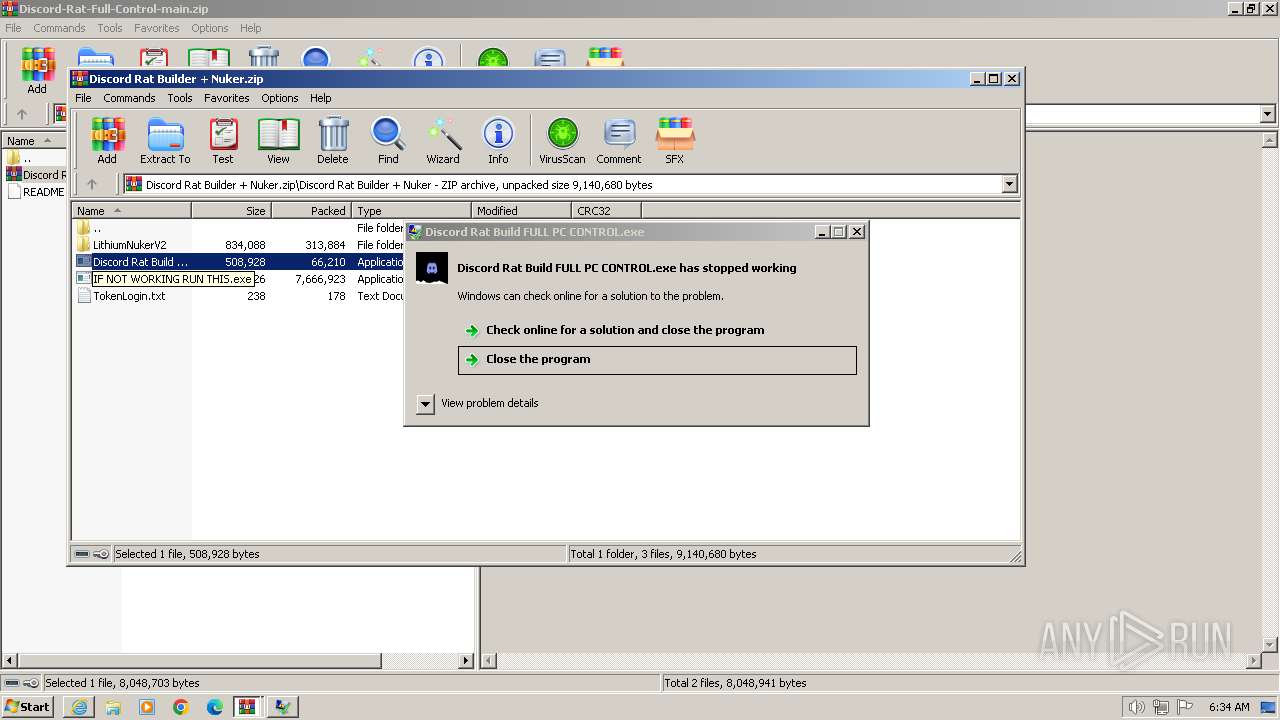
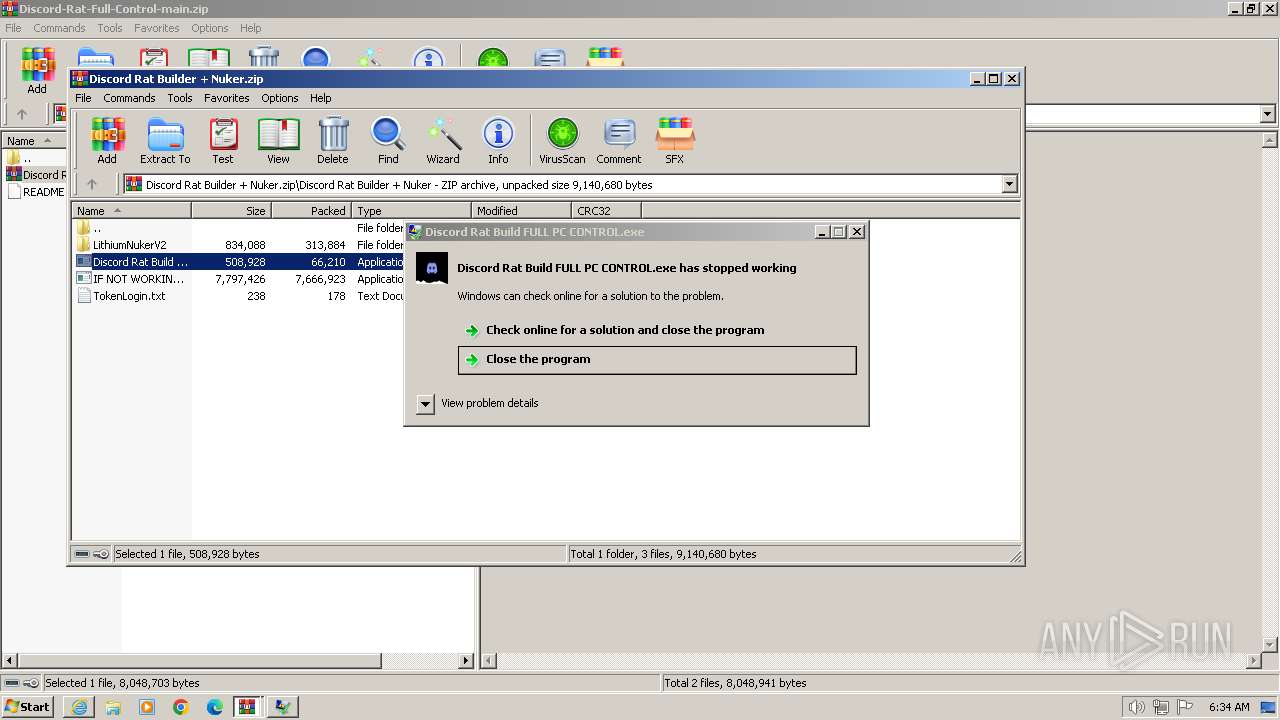
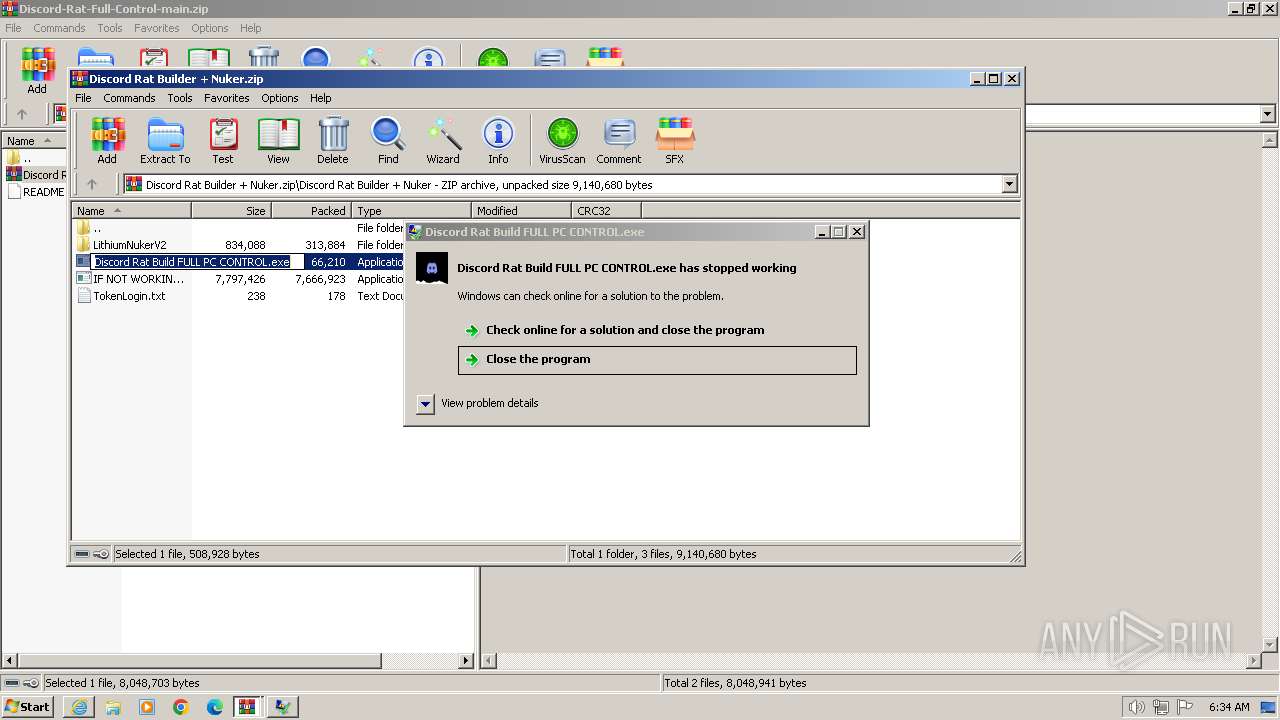
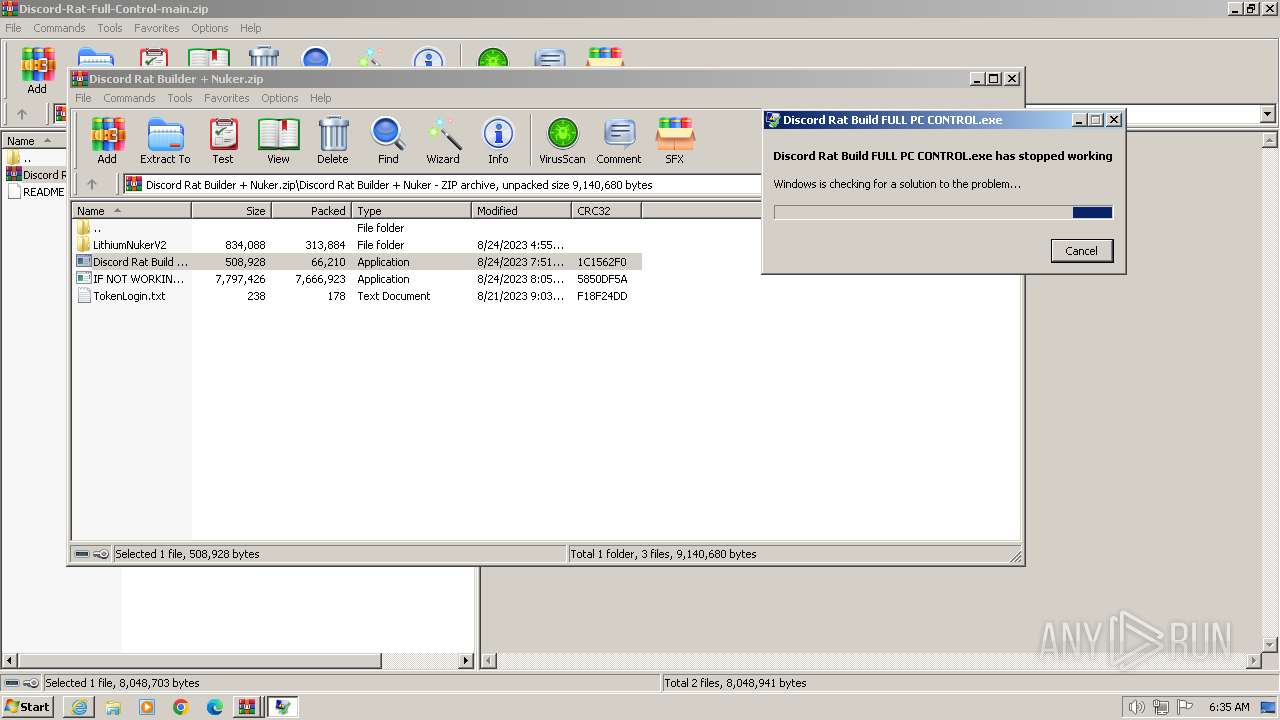
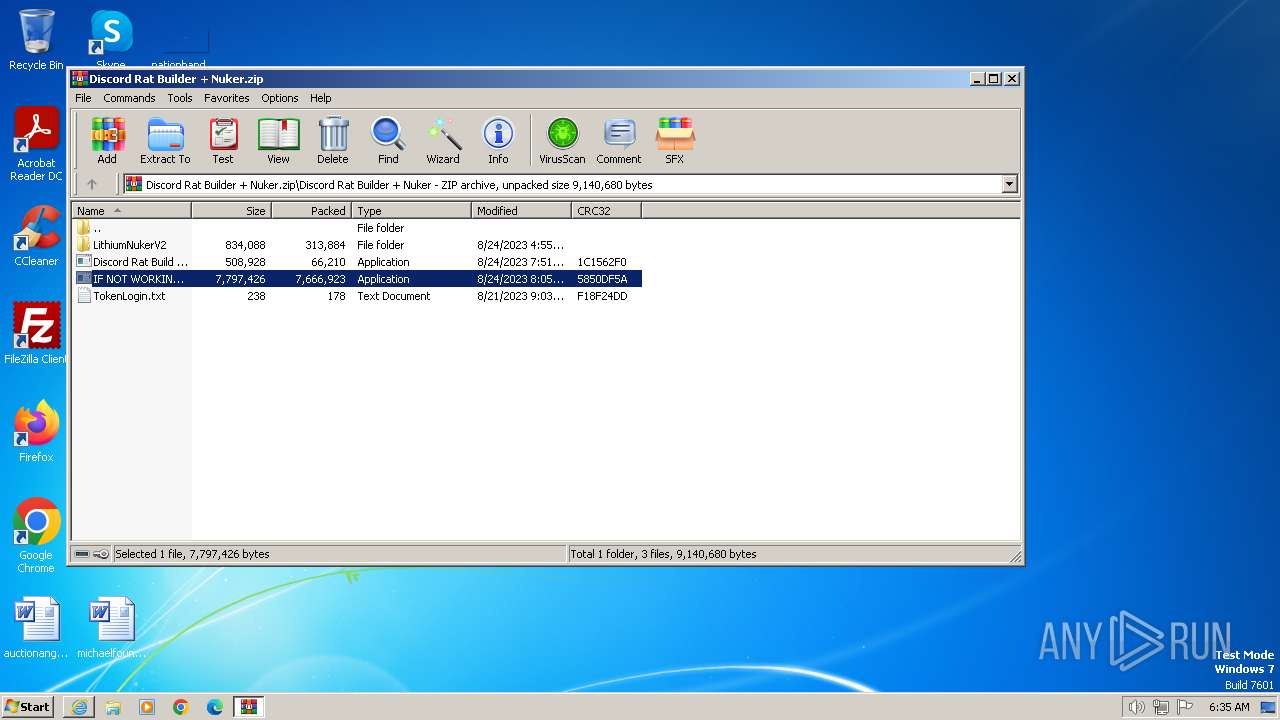
- Discord Rat Build FULL PC CONTROL.exe (PID: 116)
- Discord Rat Build FULL PC CONTROL.exe (PID: 2904)
- WinRAR.exe (PID: 2856)
ASYNCRAT has been detected (YARA)
- Discord Rat Build FULL PC CONTROL.exe (PID: 2904)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1836)
- WinRAR.exe (PID: 2856)
Application launched itself
- WinRAR.exe (PID: 1836)
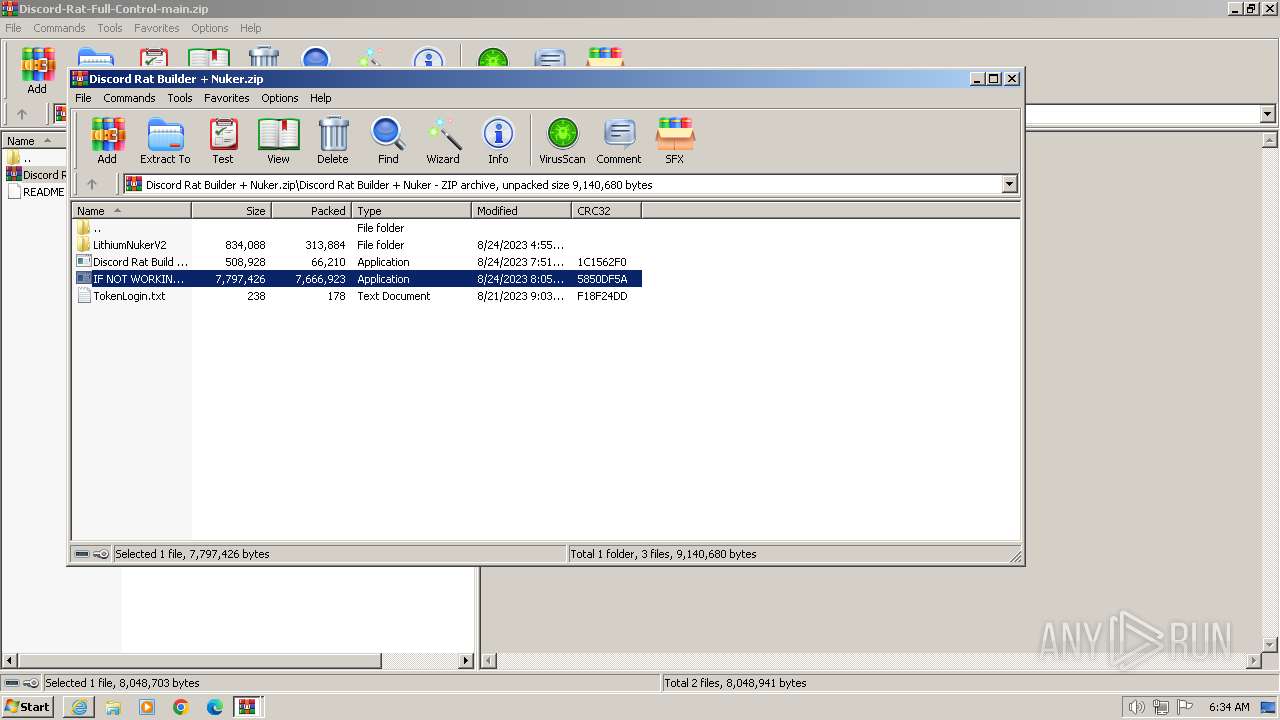
Process drops legitimate windows executable
- WinRAR.exe (PID: 2856)
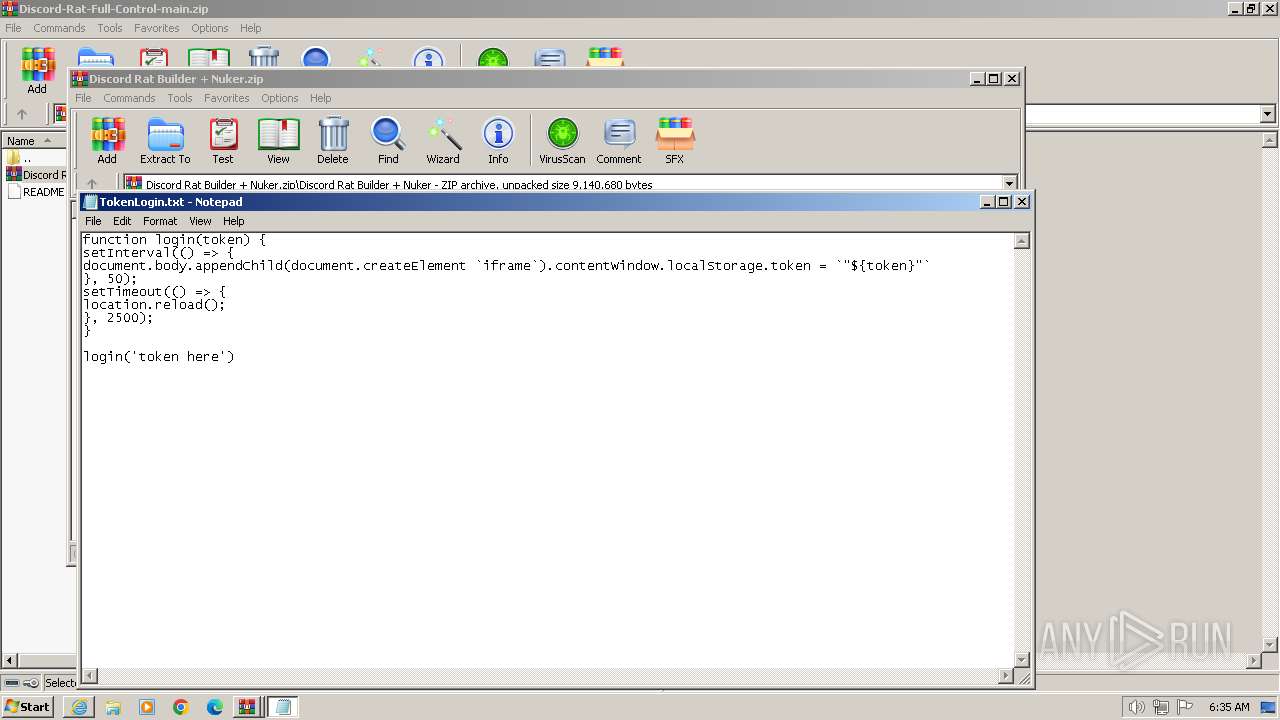
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2856)
INFO
Application launched itself
- iexplore.exe (PID: 3240)
The process uses the downloaded file
- iexplore.exe (PID: 3240)
- WinRAR.exe (PID: 1836)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3240)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2856)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2856)
Checks supported languages
- Discord Rat Build FULL PC CONTROL.exe (PID: 116)
- wmpnscfg.exe (PID: 1976)
- Discord Rat Build FULL PC CONTROL.exe (PID: 2904)
Creates files or folders in the user directory
- Discord Rat Build FULL PC CONTROL.exe (PID: 116)
Reads the machine GUID from the registry
- Discord Rat Build FULL PC CONTROL.exe (PID: 116)
- Discord Rat Build FULL PC CONTROL.exe (PID: 2904)
Reads the computer name
- Discord Rat Build FULL PC CONTROL.exe (PID: 116)
- wmpnscfg.exe (PID: 1976)
- Discord Rat Build FULL PC CONTROL.exe (PID: 2904)
Reads Environment values
- Discord Rat Build FULL PC CONTROL.exe (PID: 116)
- Discord Rat Build FULL PC CONTROL.exe (PID: 2904)
Manual execution by a user
- wmpnscfg.exe (PID: 1976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(2904) Discord Rat Build FULL PC CONTROL.exe
BotnetC_0
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRuntrue
Mutexzcolcgnbpquzsrmecm
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureTwyCKw9tCPwM+BAr2OpaOqs5I04CJwuvJHQH7voJ5djizTTwAJBUp+ZjXZYSTjJi1NSB6Yp3K16wCFjLPgA+nruY8Bg5bBI8NP/yDM+mhikZ0ug+O/GfYnG28r1ACPUnf4qnXh6GoZoJfWMzxJQ3E0nM4nSXR9S+NxKdfVfDhg8=
Keys
AES8f3d23d9610cd93016d3031f49c53fe8a2e1947bd4ef7ada35a23f5f1bef7900
SaltVenomRATByVenom
Credentials
Protocolpastebin
URLhttps://pastebin.com/raw/LwwcrLg4
Total processes
48
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2856.3797\Discord Rat Builder + Nuker\Discord Rat Build FULL PC CONTROL.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2856.3797\Discord Rat Builder + Nuker\Discord Rat Build FULL PC CONTROL.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2148734499 Version: 6.0.1 Modules
| |||||||||||||||
| 1836 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Discord-Rat-Full-Control-main.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1864 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2856.10758\TokenLogin.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1976 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2856 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa1836.3155\Discord Rat Builder + Nuker.zip" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2904 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2856.5942\Discord Rat Builder + Nuker\Discord Rat Build FULL PC CONTROL.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2856.5942\Discord Rat Builder + Nuker\Discord Rat Build FULL PC CONTROL.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2148734499 Version: 6.0.1 Modules
AsyncRat(PID) Process(2904) Discord Rat Build FULL PC CONTROL.exe BotnetC_0 VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3 Options AutoRuntrue Mutexzcolcgnbpquzsrmecm InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN... Server_SignatureTwyCKw9tCPwM+BAr2OpaOqs5I04CJwuvJHQH7voJ5djizTTwAJBUp+ZjXZYSTjJi1NSB6Yp3K16wCFjLPgA+nruY8Bg5bBI8NP/yDM+mhikZ0ug+O/GfYnG28r1ACPUnf4qnXh6GoZoJfWMzxJQ3E0nM4nSXR9S+NxKdfVfDhg8= Keys AES8f3d23d9610cd93016d3031f49c53fe8a2e1947bd4ef7ada35a23f5f1bef7900 SaltVenomRATByVenom Credentials Protocolpastebin URLhttps://pastebin.com/raw/LwwcrLg4 | |||||||||||||||
| 3240 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/ASTR0C0/Discord-Rat-Full-Control/archive/refs/heads/main.zip" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3916 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3240 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
29 400
Read events
29 207
Write events
165
Delete events
28
Modification events
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31088198 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31088198 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3240) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
25
Suspicious files
16
Text files
19
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_02835C6072261A584AE38D197B622594 | der | |
MD5:8AE3562C62B54283F046D117889F6EF6 | SHA256:A7AFA22513C8A24102E6FD4F089EC971A1EC54D8F45445EE2F01792896D3DEE3 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_02835C6072261A584AE38D197B622594 | binary | |
MD5:BDFDB7195245674B5B01C320EF7ED126 | SHA256:6F2D45DDEC6BE20CEAD4810871293B415E615A0F088C75B02D01F639225EBFA2 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\Discord-Rat-Full-Control-main[1].zip | compressed | |
MD5:B156BF846ACCA0E05528BAC432EA6874 | SHA256:7A5EA453DD4F7FAC58D34876F9CDDA03AA580B2EE1C6779B92BBF60EFFDEDFEF | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | der | |
MD5:DCF073E986A7BECF4569195EC2946D16 | SHA256:F4354895A86DE99B49444AA19C77D327262C72884C160FFEB644C786F8B95B5B | |||
| 2856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2856.3797\Discord Rat Builder + Nuker\LithiumNukerV2\Veylib.dll | executable | |
MD5:3552D418CE6394CDD9FC0FB06B883013 | SHA256:0A87FEDE388EA48D2F21452058A40982A46D1601F9F7C6B1080B983078A59742 | |||
| 1836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1836.3155\Discord Rat Builder + Nuker.zip | compressed | |
MD5:1A097B3E12AE3F71F55EBB6B7F167995 | SHA256:64B63AA62AFCDB340E729E74514289242121DF77A08658C5A40F02FCA693BC9F | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Discord-Rat-Full-Control-main.zip | compressed | |
MD5:B727337590BD0496FC13A6E8A2B63059 | SHA256:6EEED07B61CBD3EB467869E5A3A619A132D180BFC6FD40FB345E75389098A4E7 | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:E7937FCA03067554BF8FB7A4C4439E49 | SHA256:1B4D2CBB2509D283014B1F7351E84F0EE39002FC641EFE15A398B9FAEB43CCFF | |||
| 2856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2856.3797\Discord Rat Builder + Nuker\Discord Rat Build FULL PC CONTROL.exe | executable | |
MD5:741A587EBA74FFA242FB0BE890324B8E | SHA256:F9949948026C5DC70CF997D2CCD0D0CCD63043D41F78A41247A56F7C4A74E11F | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF8C1BC09AD30D9245.TMP | binary | |
MD5:5FD788DAE7D807C0D871ED7C0D2B6940 | SHA256:30900C5FFA73CB66D11F0949BCDCAA424A189F9E379D949BB078ACDB501C6349 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
23
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3916 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5b0325f31ae0f9b6 | unknown | — | — | unknown |
3916 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 312 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?89bca2e7018c82c0 | unknown | compressed | 65.2 Kb | unknown |
3240 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
3240 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3240 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3916 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c503292d7802e201 | unknown | compressed | 65.2 Kb | unknown |
3916 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAuJBTcSX0UQ1jcqECipKaU%3D | unknown | binary | 313 b | unknown |
3240 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3916 | iexplore.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
3916 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3916 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3916 | iexplore.exe | 140.82.121.10:443 | codeload.github.com | GITHUB | US | unknown |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3240 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3240 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
codeload.github.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
watson.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Discord Rat Build FULL PC CONTROL.exe | CLR: Managed code called FailFast without specifying a reason.
|
Discord Rat Build FULL PC CONTROL.exe | CLR: Managed code called FailFast without specifying a reason.
|