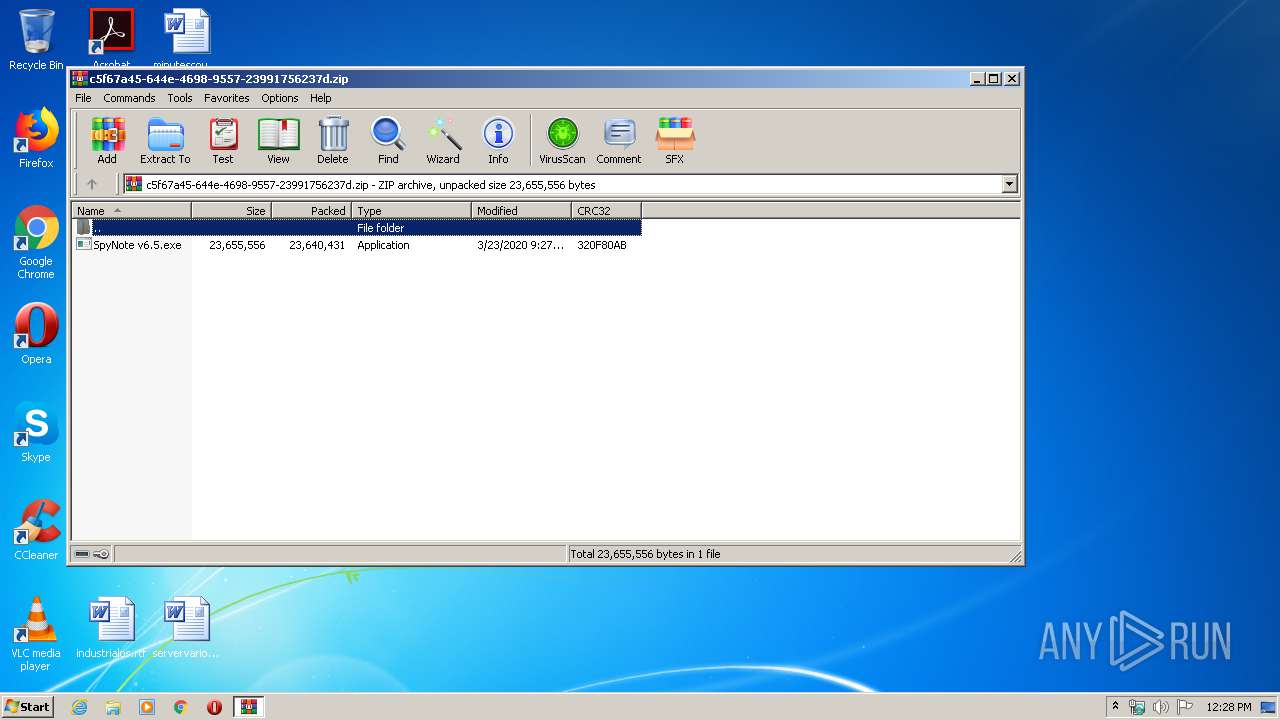
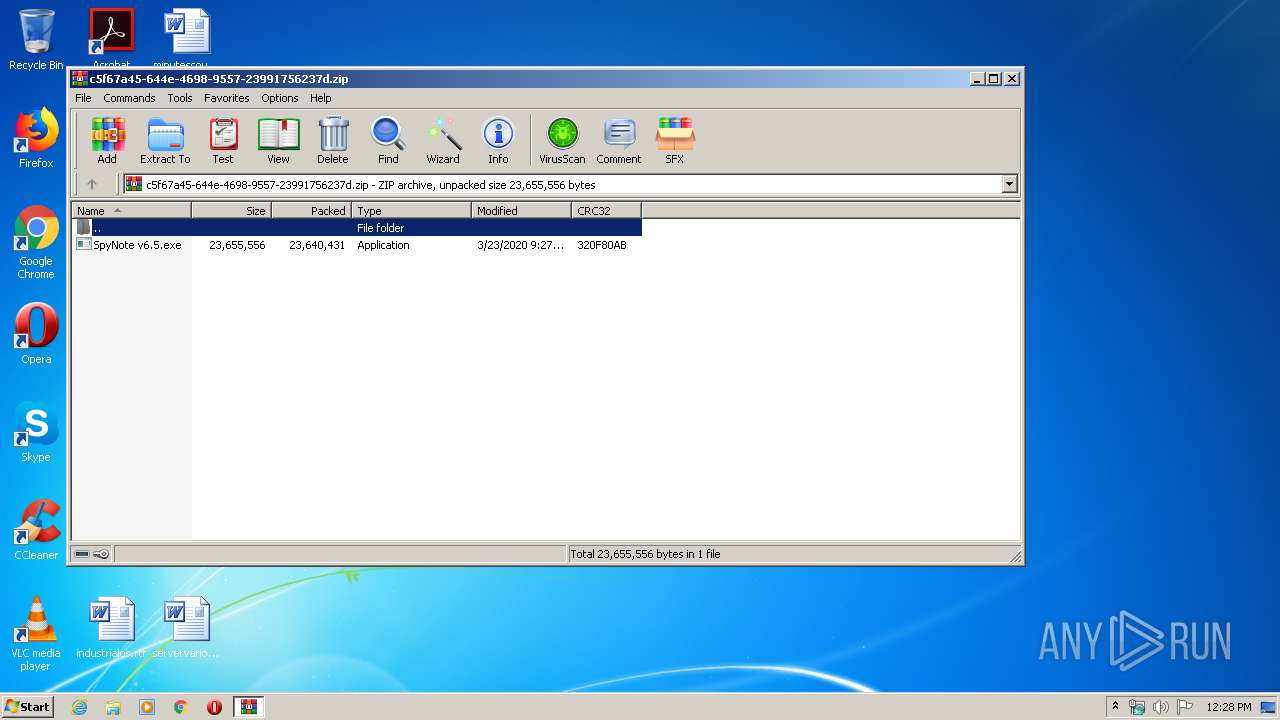
| download: | SpyNote%20v6.5.zip |
| Full analysis: | https://app.any.run/tasks/f8035371-0618-49a7-a224-880a4eeba5cd |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | March 23, 2020, 12:27:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F39B6C8391D7E0E0198E6B49DEF25748 |
| SHA1: | 2038399D096C430470385365613F3A3A41CF8425 |
| SHA256: | 4B1CBDFEFE6F51790D29D25A3E5E2C459D5751FF83CE6B58CFCBE2F733AC7F57 |
| SSDEEP: | 393216:bdQwlFJwfojvfBe/QyqLSbn9JkSl53WNWeCJl1tCBrjamDZ+2G0MzPU46:bSyJFjvfB61lt7ecTA++E8 |
MALICIOUS
Application was dropped or rewritten from another process
- SpyNote v6.5.exe (PID: 1008)
- SpyNote v6.5.exe (PID: 2744)
- WSReset.exe (PID: 2876)
- AndroidTester_v6.4.6.exe (PID: 3828)
- WSReset.exe (PID: 2184)
- WSReset.exe (PID: 1156)
- WSReset.exe (PID: 3952)
- Android Tester.exe (PID: 2780)
- Android Tester.exe (PID: 1392)
- Android Tester.exe (PID: 256)
- Android Tester.exe (PID: 3368)
Uses Task Scheduler to run other applications
- WSReset.exe (PID: 3952)
Changes the autorun value in the registry
- WSReset.exe (PID: 3952)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 392)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3548)
Writes to a start menu file
- WSReset.exe (PID: 3952)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1692)
- SpyNote v6.5.exe (PID: 1008)
- WSReset.exe (PID: 2876)
- WSReset.exe (PID: 3952)
- AndroidTester_v6.4.6.exe (PID: 3828)
Reads internet explorer settings
- AndroidTester_v6.4.6.exe (PID: 3828)
Application launched itself
- WSReset.exe (PID: 2184)
- WSReset.exe (PID: 1156)
Starts itself from another location
- WSReset.exe (PID: 2876)
Creates files in the user directory
- WSReset.exe (PID: 2876)
- WSReset.exe (PID: 3952)
Reads Internet Cache Settings
- AndroidTester_v6.4.6.exe (PID: 3828)
INFO
Manual execution by user
- SpyNote v6.5.exe (PID: 1008)
- SpyNote v6.5.exe (PID: 2744)
- Android Tester.exe (PID: 2780)
- Android Tester.exe (PID: 3368)
- Android Tester.exe (PID: 256)
- Android Tester.exe (PID: 1392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:03:23 17:27:28 |
| ZipCRC: | 0x320f80ab |
| ZipCompressedSize: | 23640431 |
| ZipUncompressedSize: | 23655556 |
| ZipFileName: | SpyNote v6.5.exe |
Total processes
62
Monitored processes
14
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
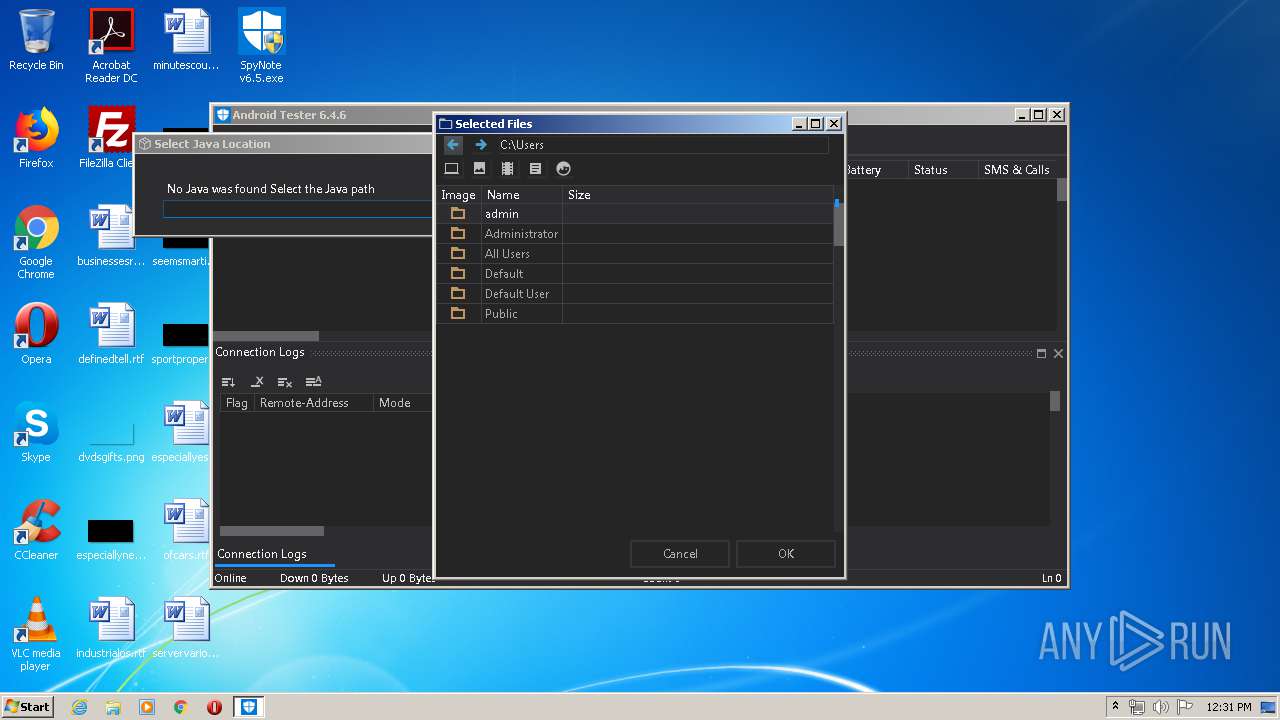
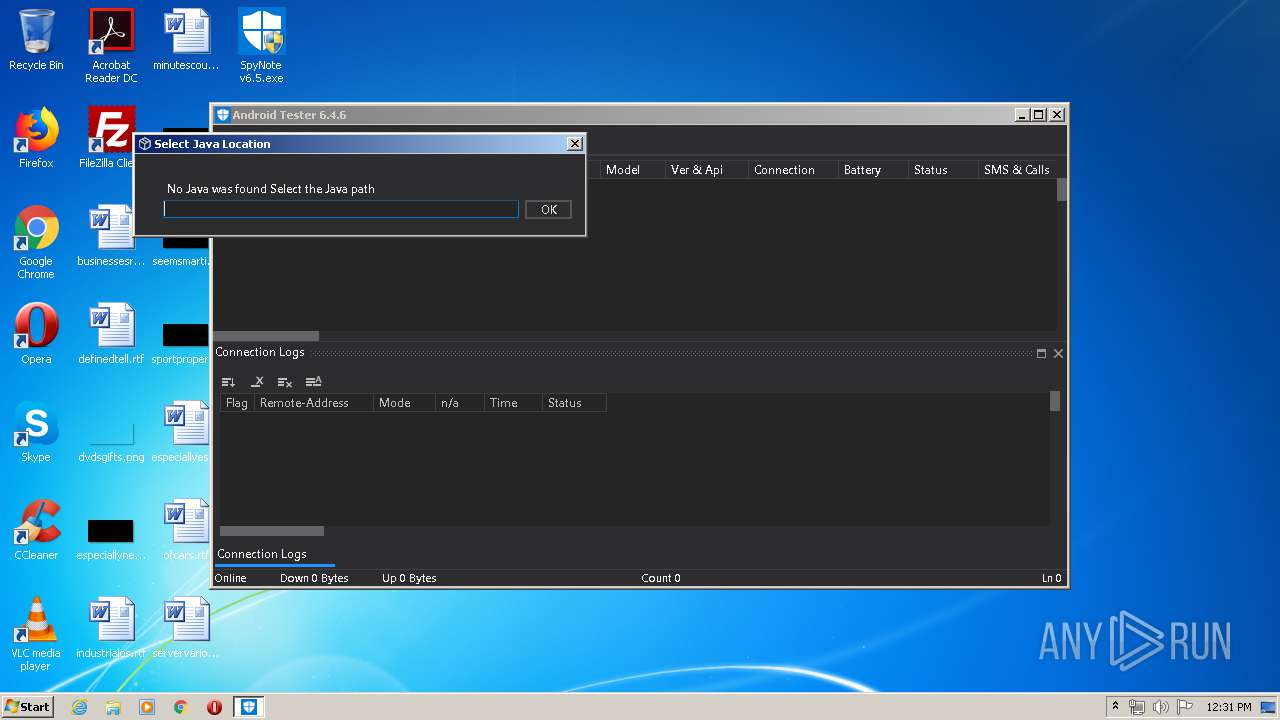
| 256 | "C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe" | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe | explorer.exe | ||||||||||||
User: admin Company: kkkk Inc. Integrity Level: HIGH Description: Android Tester Exit code: 0 Version: 6.4.6.0 Modules
| |||||||||||||||
| 392 | schtasks /create /sc minute /mo 60 /tn "WSReset" /tr "C:\Users\admin\AppData\Roaming\WSReset.exe" | C:\Windows\system32\schtasks.exe | — | WSReset.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | "C:\Users\admin\Desktop\SpyNote v6.5.exe" | C:\Users\admin\Desktop\SpyNote v6.5.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1156 | "C:\Users\admin\AppData\Roaming\WSReset.exe" | C:\Users\admin\AppData\Roaming\WSReset.exe | — | WSReset.exe | |||||||||||
User: admin Integrity Level: HIGH Description: WSReset Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1392 | "C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe" | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe | — | explorer.exe | |||||||||||
User: admin Company: kkkk Inc. Integrity Level: MEDIUM Description: Android Tester Exit code: 3221226540 Version: 6.4.6.0 Modules
| |||||||||||||||
| 1692 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\c5f67a45-644e-4698-9557-23991756237d.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\AppData\Local\Temp\WSReset.exe" | C:\Users\admin\AppData\Local\Temp\WSReset.exe | — | SpyNote v6.5.exe | |||||||||||
User: admin Integrity Level: HIGH Description: WSReset Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2744 | "C:\Users\admin\Desktop\SpyNote v6.5.exe" | C:\Users\admin\Desktop\SpyNote v6.5.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2780 | "C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe" | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe | — | explorer.exe | |||||||||||
User: admin Company: kkkk Inc. Integrity Level: MEDIUM Description: Android Tester Exit code: 3221226540 Version: 6.4.6.0 Modules
| |||||||||||||||
| 2876 | "C:\Users\admin\AppData\Local\Temp\WSReset.exe" | C:\Users\admin\AppData\Local\Temp\WSReset.exe | WSReset.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: WSReset Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 973
Read events
1 928
Write events
45
Delete events
0
Modification events
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\c5f67a45-644e-4698-9557-23991756237d.zip | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
13
Suspicious files
4
Text files
551
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1008 | SpyNote v6.5.exe | C:\Users\admin\AppData\Local\Temp\WSReset.exe | executable | |
MD5:— | SHA256:— | |||
| 2876 | WSReset.exe | C:\Users\admin\AppData\Roaming\WSReset.exe | executable | |
MD5:— | SHA256:— | |||
| 3828 | AndroidTester_v6.4.6.exe | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.xml | xml | |
MD5:— | SHA256:— | |||
| 1008 | SpyNote v6.5.exe | C:\Users\admin\AppData\Local\Temp\AndroidTester_v6.4.6.exe | executable | |
MD5:— | SHA256:— | |||
| 3828 | AndroidTester_v6.4.6.exe | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe | executable | |
MD5:— | SHA256:— | |||
| 1692 | WinRAR.exe | C:\Users\admin\Desktop\SpyNote v6.5.exe | executable | |
MD5:— | SHA256:— | |||
| 3828 | AndroidTester_v6.4.6.exe | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.pdb | pdb | |
MD5:— | SHA256:— | |||
| 3952 | WSReset.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\WSReset.exe | executable | |
MD5:— | SHA256:— | |||
| 3828 | AndroidTester_v6.4.6.exe | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Android Tester.exe.config | xml | |
MD5:2C9C466EBDA44588DF645D3E745218F5 | SHA256:E40FB7B72E64FC194DEBEB83D9905CA3EF1826626669DC7CF90CC0ACA82D3EEC | |||
| 3828 | AndroidTester_v6.4.6.exe | C:\Users\admin\Desktop\AndroidTester_v6.4.6\Resources\Icons\AccountManager\com.android.email.png | image | |
MD5:1FC4ABE2F26276C04B55591BD0A584C3 | SHA256:6E68465A4C4E86F84517A3B230510E4D5D2F163744CD592C55DA8A89B0C866F5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
22
DNS requests
12
Threats
12
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2876 | WSReset.exe | 79.151.109.211:3333 | nibiru3.duckdns.org | Telefonica De Espana | ES | unknown |
3952 | WSReset.exe | 79.151.109.211:3333 | nibiru3.duckdns.org | Telefonica De Espana | ES | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nibiru3.duckdns.org |
| malicious |
nibiru4.duckdns.org |
| malicious |
nibiru5.duckdns.org |
| malicious |
karmina113.sytes.net |
| malicious |
karmina117.sytes.net |
| malicious |
karmina118.sytes.net |
| malicious |
karmina119.sytes.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
7 ETPRO signatures available at the full report