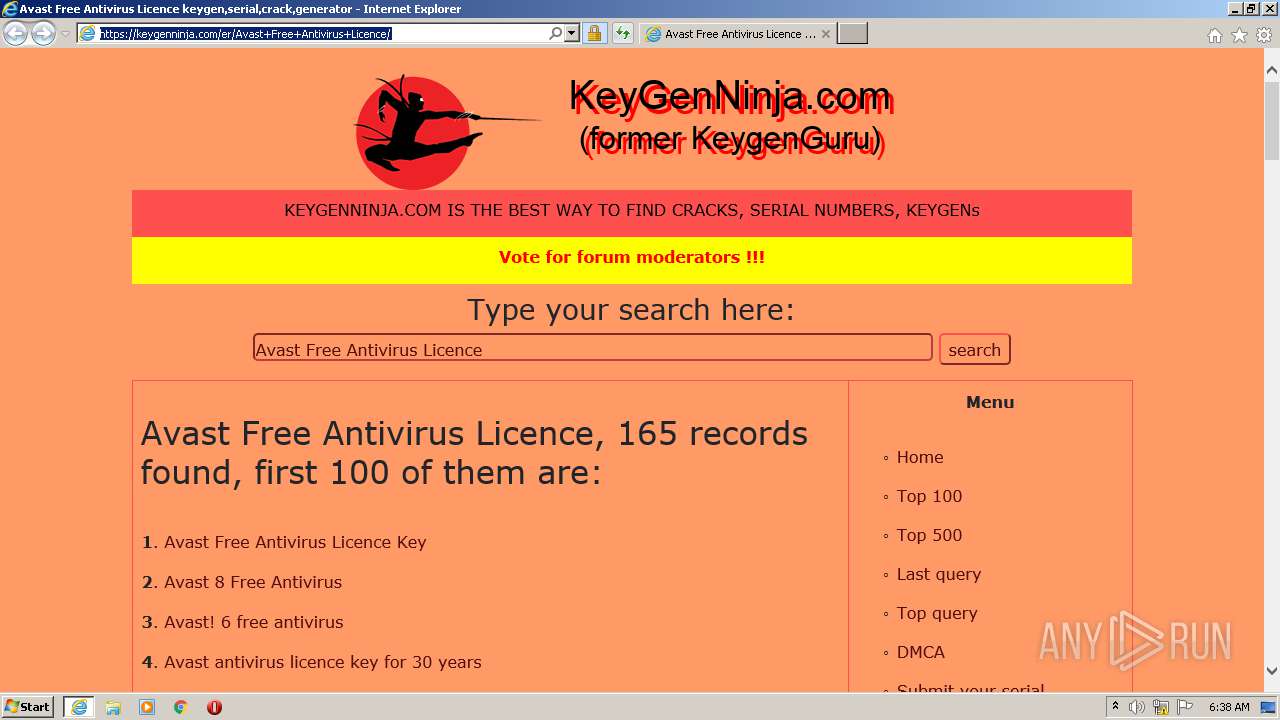
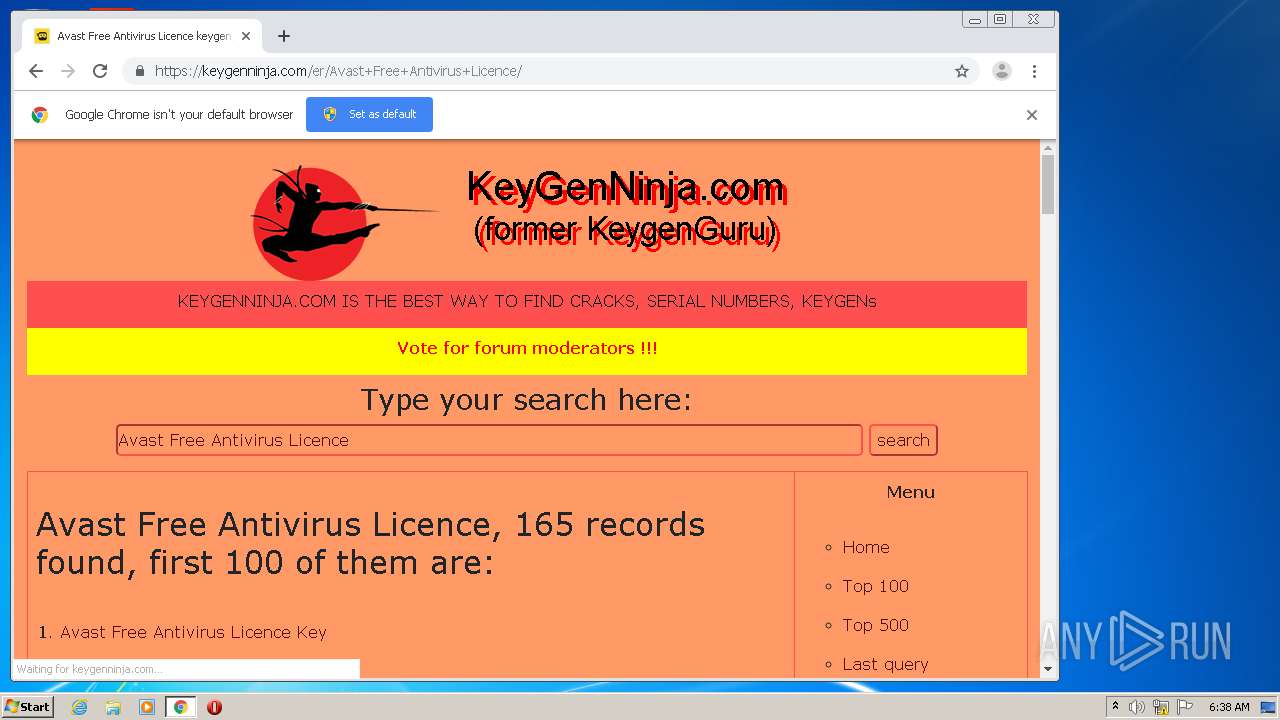
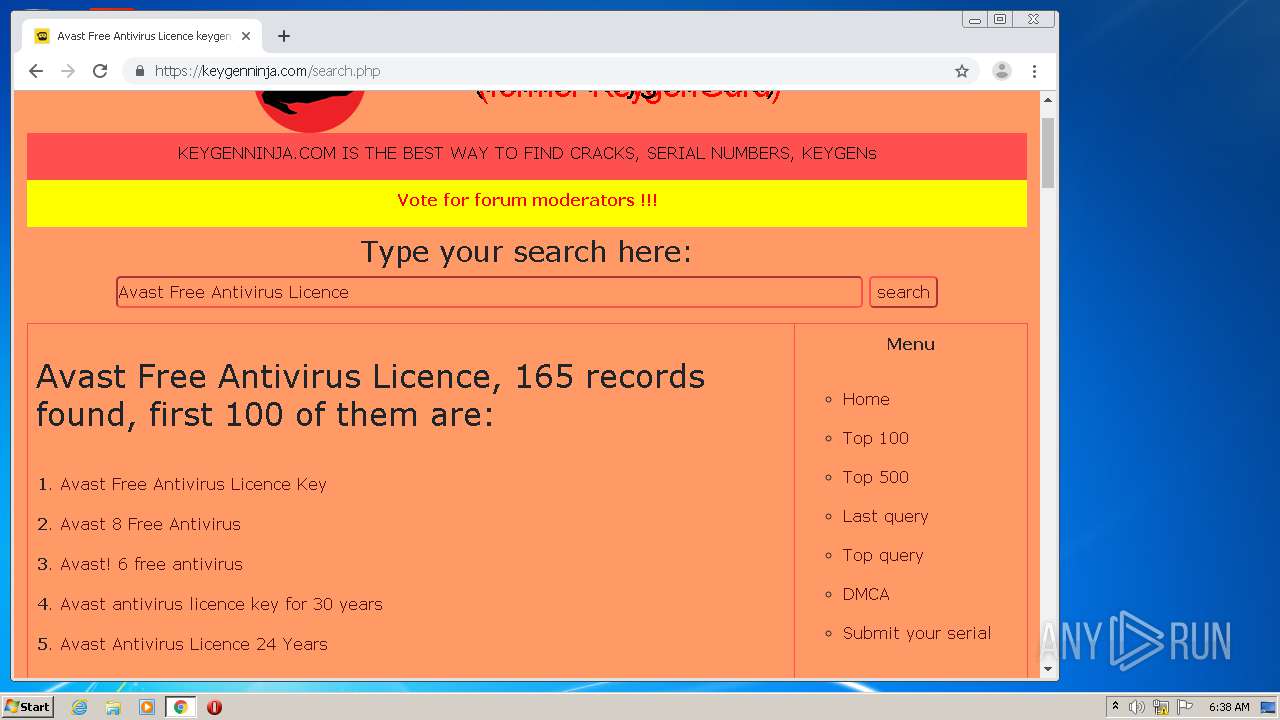
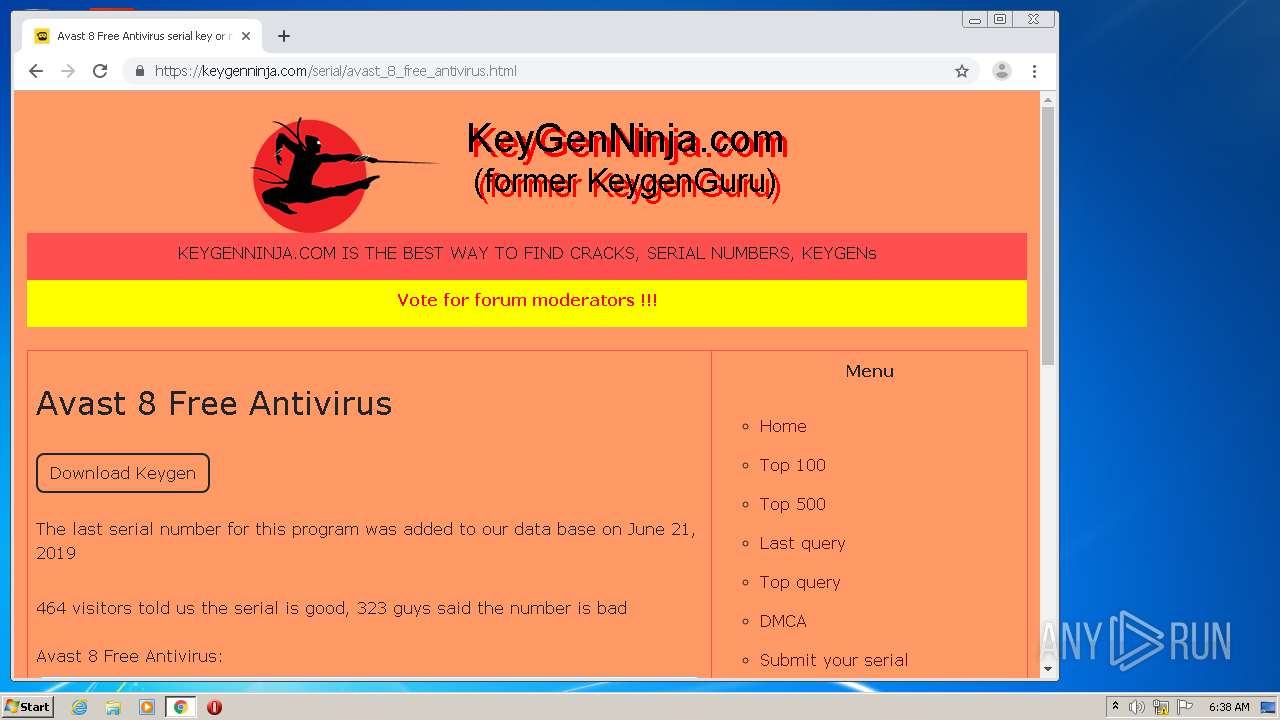
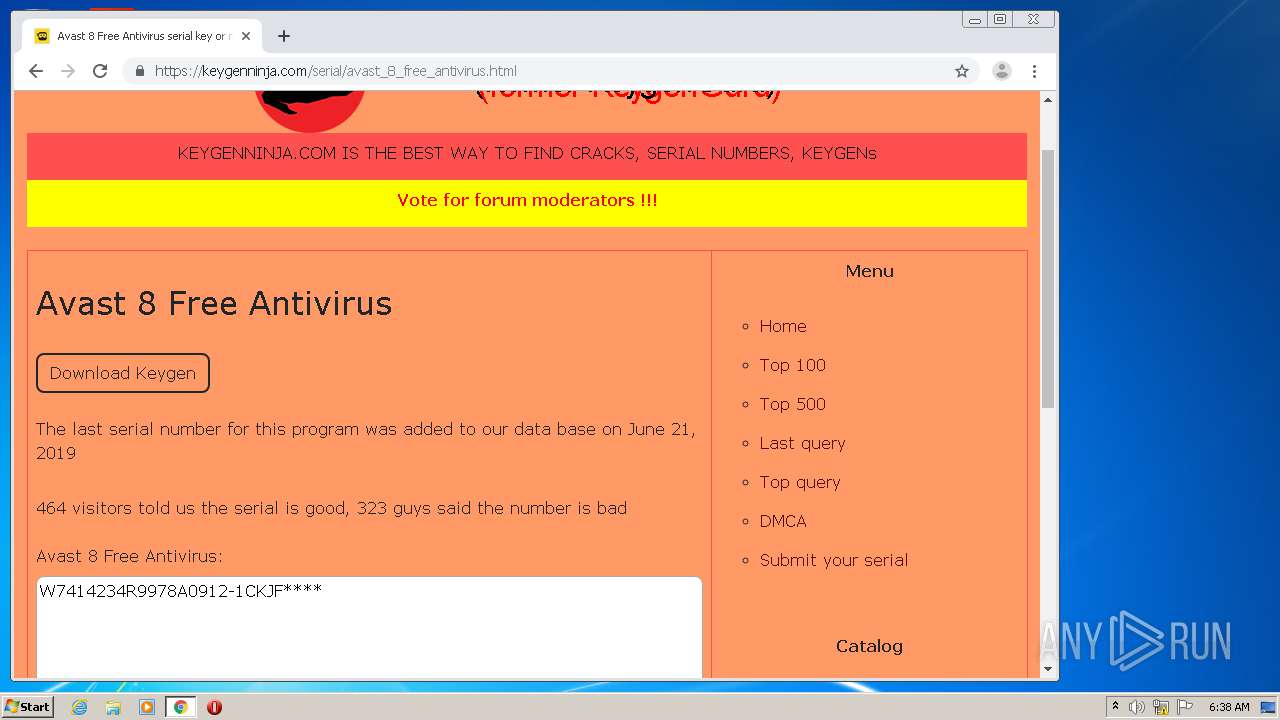
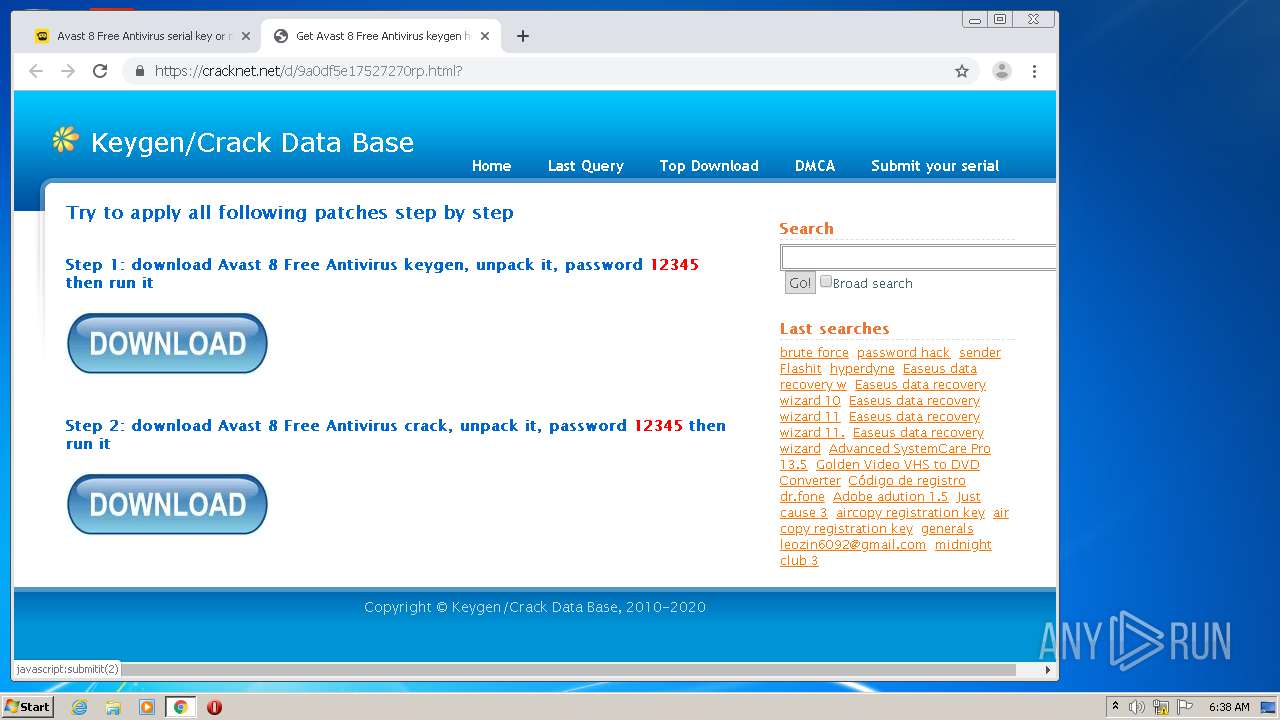
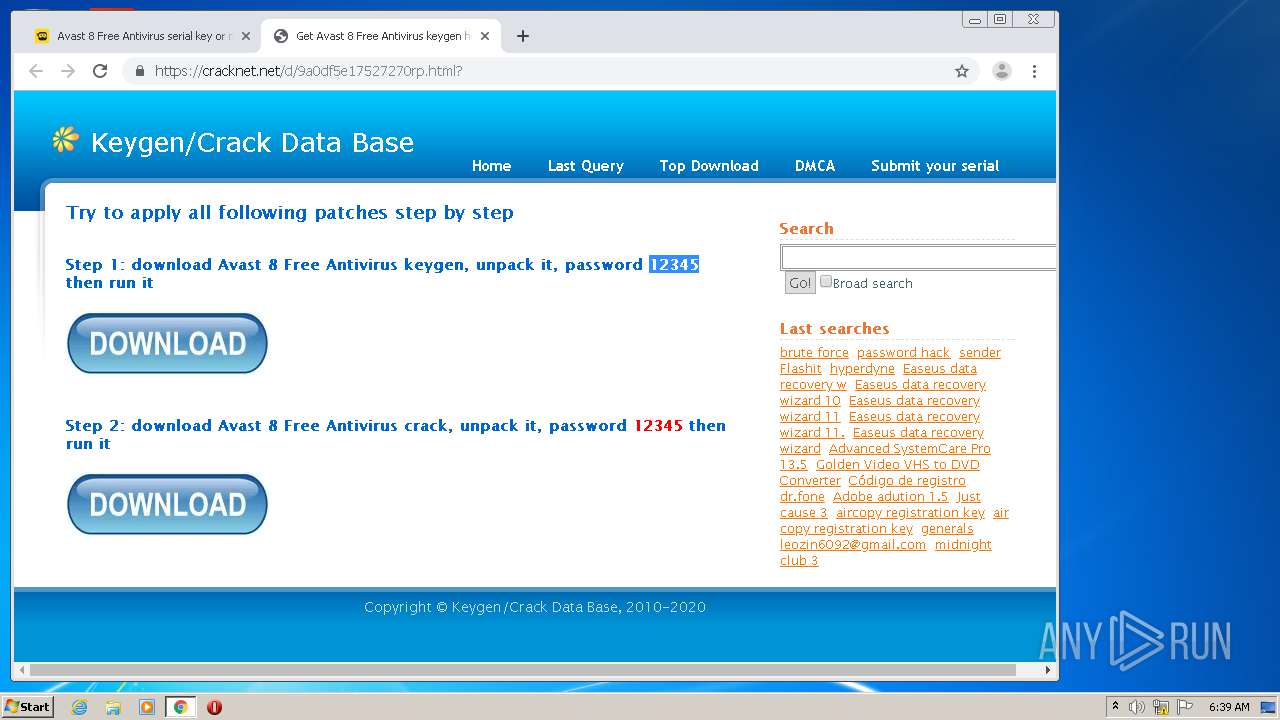
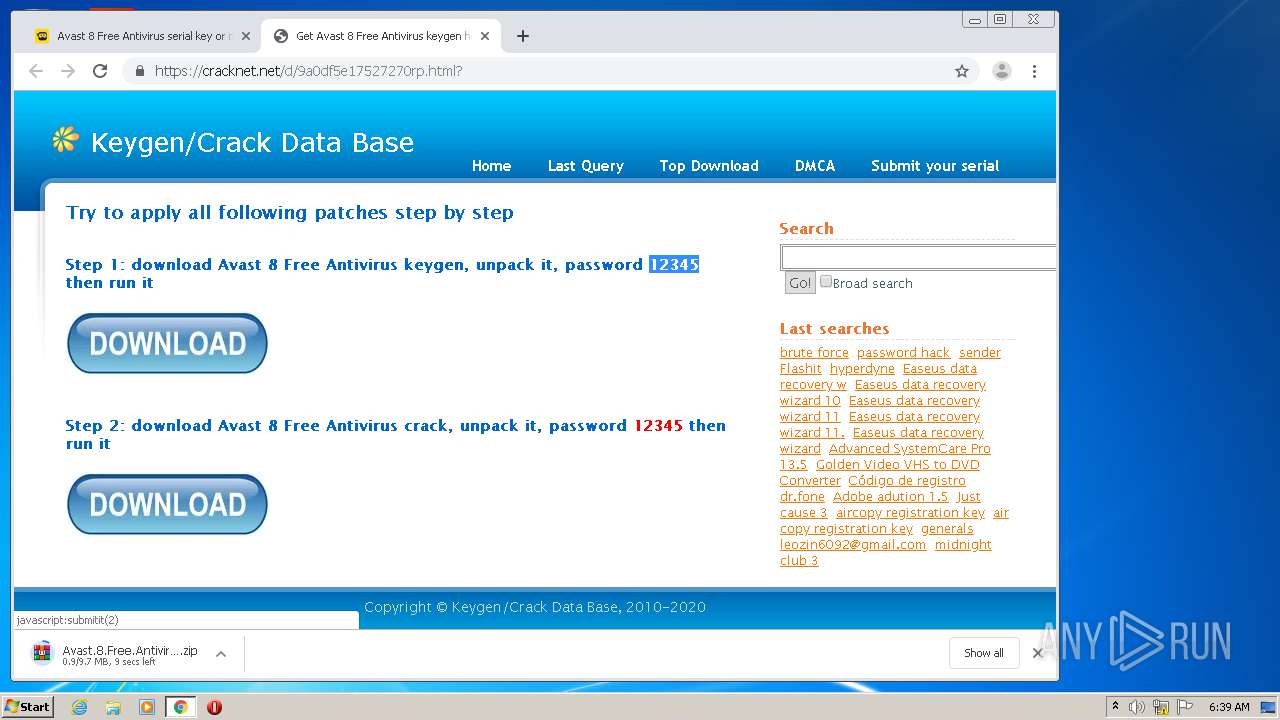
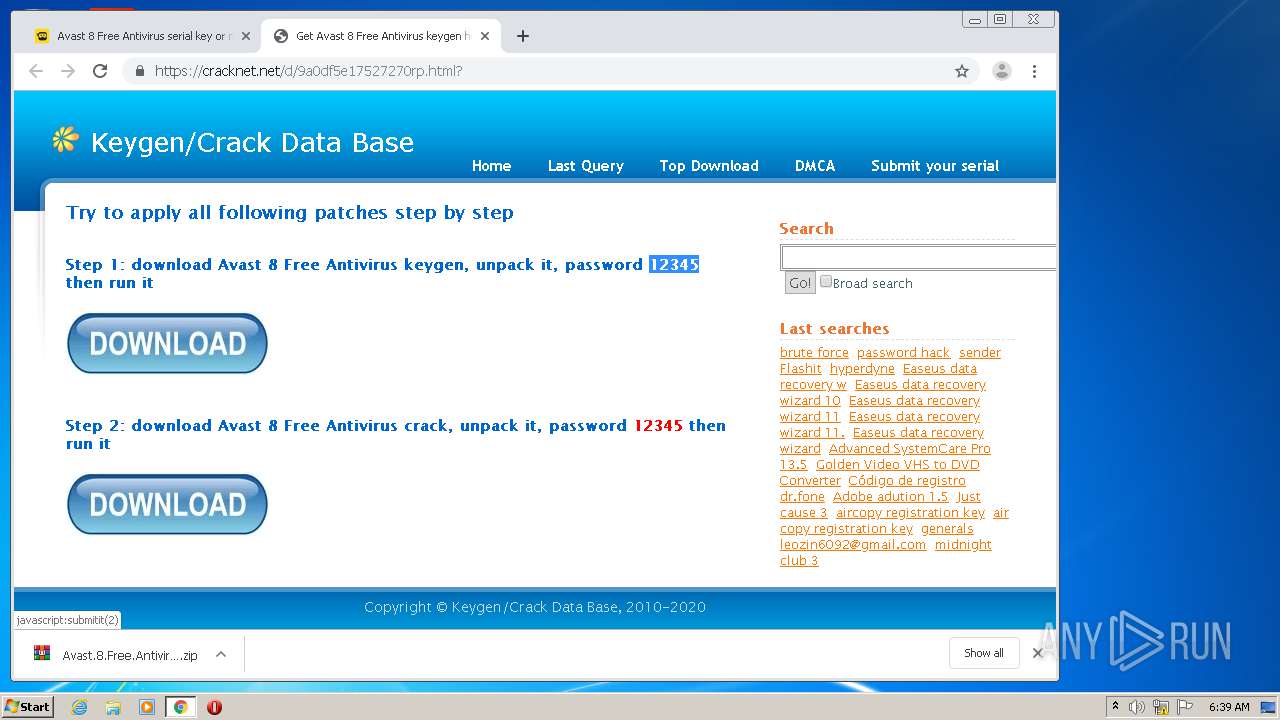
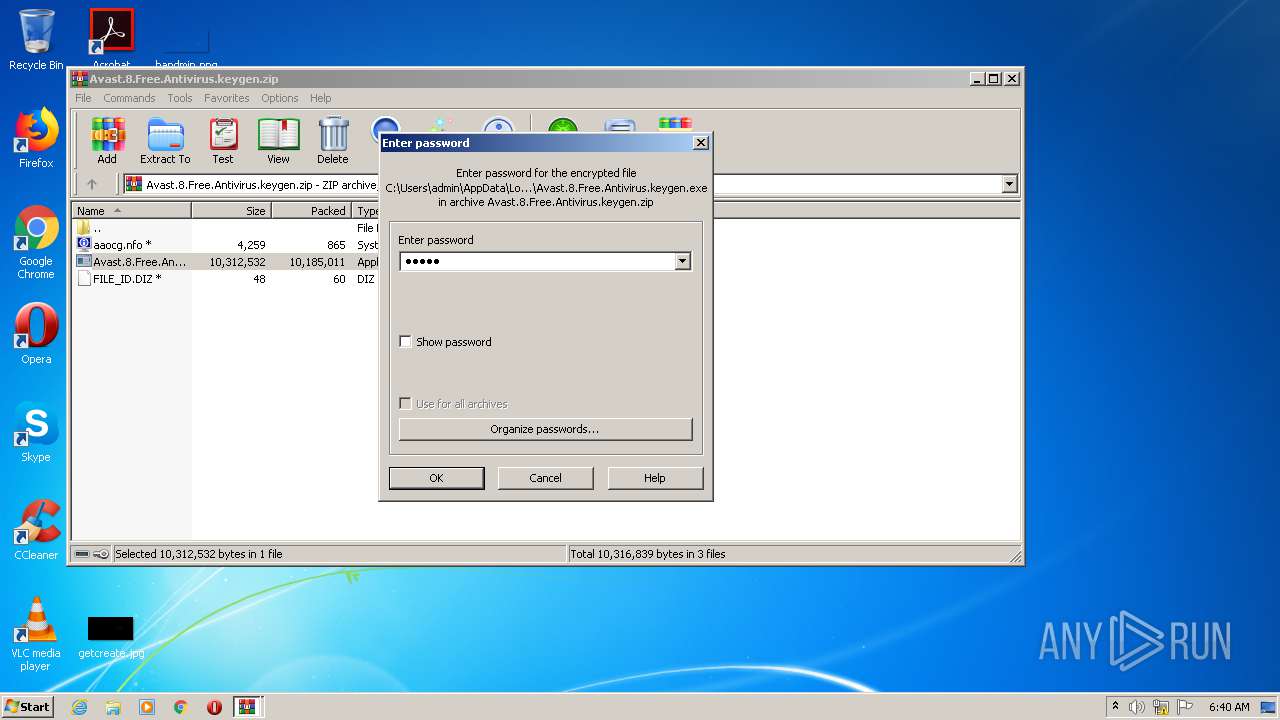
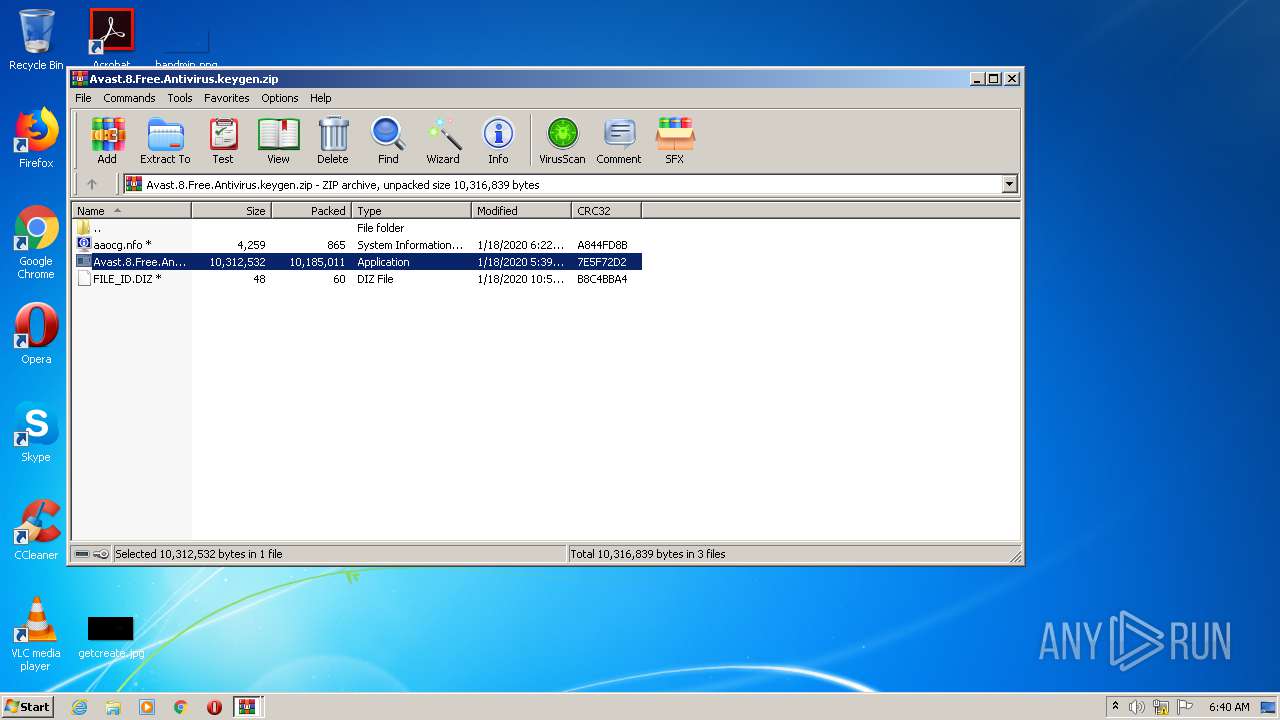
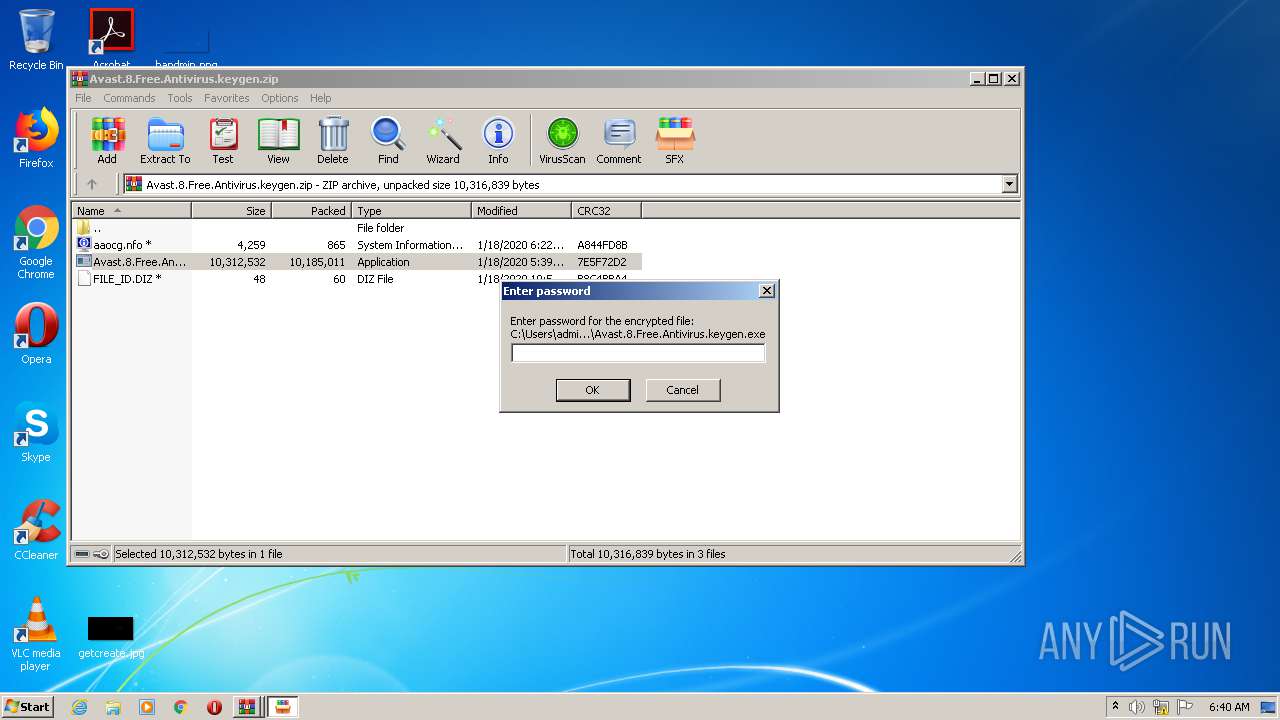
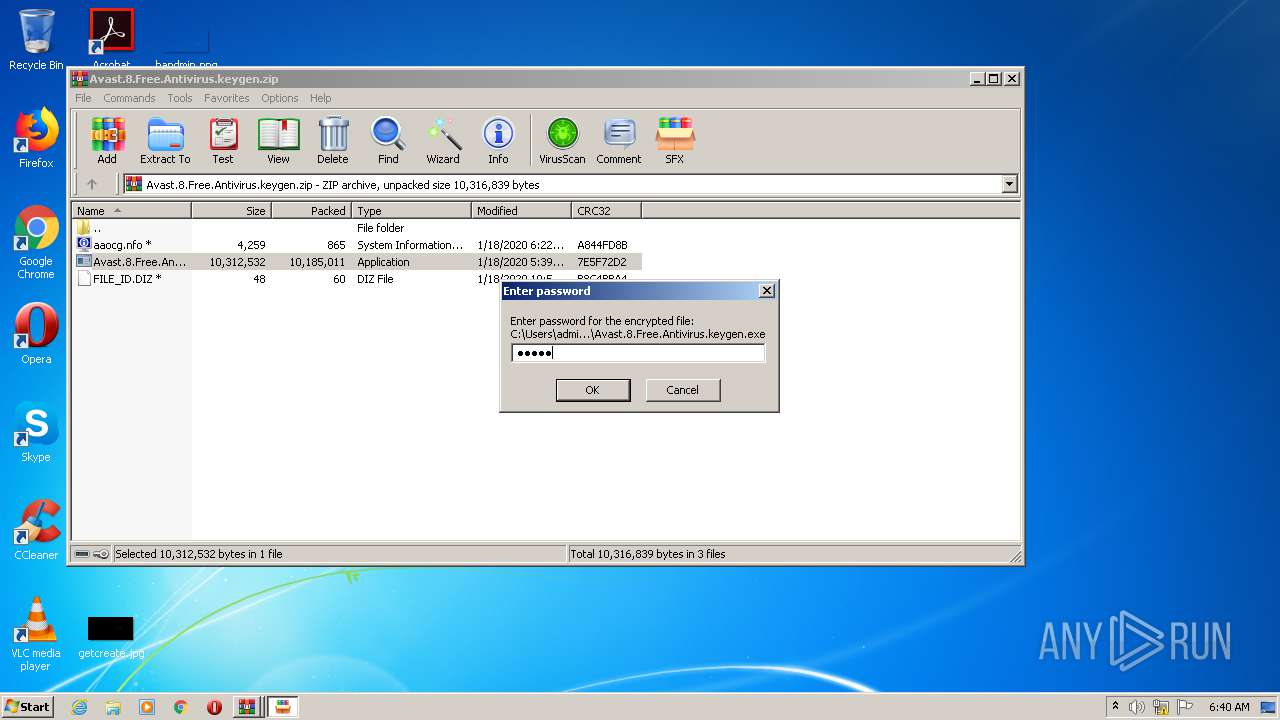
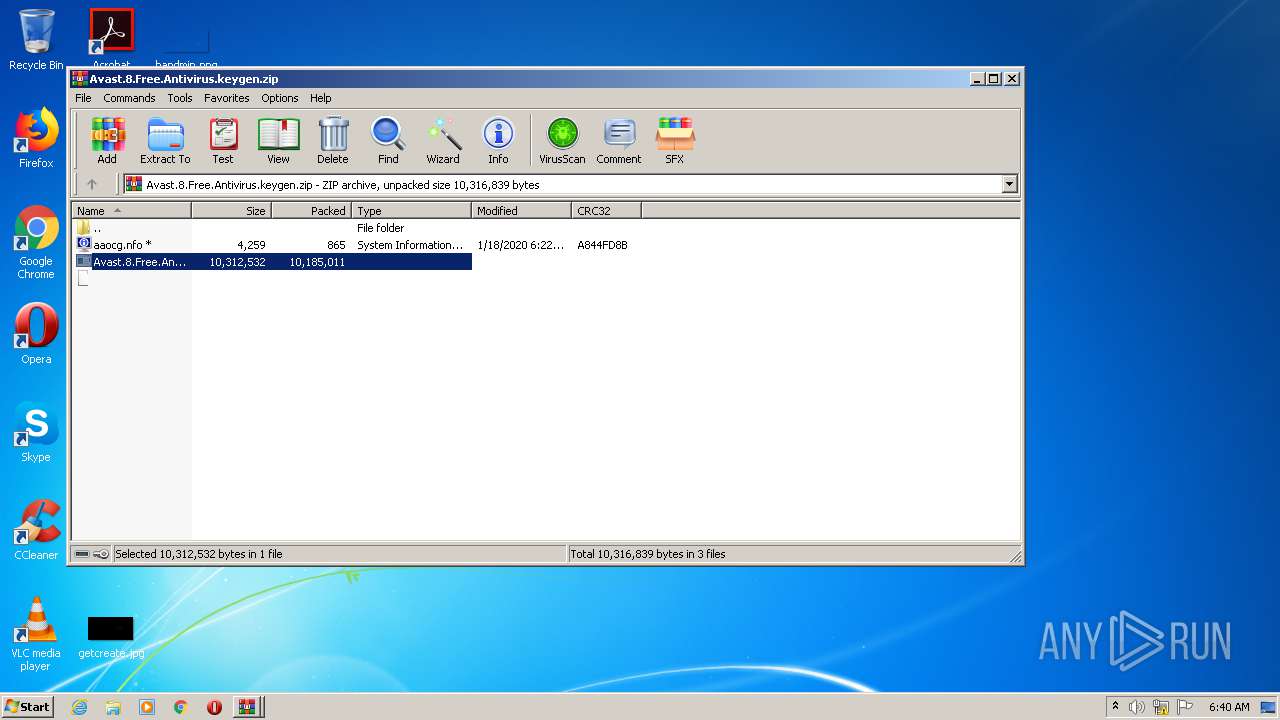
| URL: | https://keygenninja.com/er/Avast+Free+Antivirus+Licence/ |
| Full analysis: | https://app.any.run/tasks/eb1239d7-8b65-4f87-bff8-229c0f49a06e |
| Verdict: | Malicious activity |
| Threats: | Pony is a malware with two main functions — stealing information and dropping other viruses with different tasks on infected machines. It has been around since 2011, and it still actively attacks users in Europe and America. |
| Analysis date: | August 29, 2020, 05:37:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1DEF278D134BBCEABBDCF800B4E92E24 |
| SHA1: | 7D5BE1D47248DF696742289297A7E3DB1117BD1D |
| SHA256: | 4B103C75342FC33A09BCDB7B0C86E379A49CA2BABF7AD17A19A5CF7E29E39D5E |
| SSDEEP: | 3:N8FVYpPJwkVAHJv:24pPJwkyF |
MALICIOUS
Application was dropped or rewritten from another process
- Avast.8.Free.Antivirus.keygen.exe (PID: 2880)
- keygen-pr.exe (PID: 632)
- intro.exe (PID: 4072)
- key.exe (PID: 1748)
- setup.upx.exe (PID: 2212)
- keygen-step-3.exe (PID: 2572)
- key.exe (PID: 1096)
- id6.exe (PID: 1388)
- keygen-step-4.exe (PID: 2400)
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3400)
- hjjgaa.exe (PID: 1232)
- searzar.exe (PID: 2964)
- hjjgaa.exe (PID: 1512)
- jfiag_gg.exe (PID: 1772)
- mdmd_pytopm.exe (PID: 2072)
- Install.exe (PID: 3984)
- Install.exe (PID: 4080)
- jfiag_gg.exe (PID: 1796)
- Yandex.exe (PID: 1800)
- Yandex.exe (PID: 1684)
- privacytools2.exe (PID: 2296)
- privacytools2.exe (PID: 4052)
- BTRSetp.exe (PID: 560)
- wyfdggzz.exe (PID: 960)
- Yandex.exe (PID: 2636)
Stealing of credential data
- keygen-step-3.exe (PID: 2572)
- setup.upx.exe (PID: 2212)
- id6.exe (PID: 1388)
- Yandex.exe (PID: 2636)
- xcopy.exe (PID: 3084)
- WerFault.exe (PID: 3160)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 856)
- cmd.exe (PID: 1324)
- cmd.exe (PID: 1680)
- cmd.exe (PID: 2976)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 3900)
Connects to CnC server
- setup.upx.exe (PID: 2212)
- key.exe (PID: 1748)
- id6.exe (PID: 1388)
- searzar.exe (PID: 2964)
- hjjgaa.exe (PID: 1512)
- Yandex.exe (PID: 2636)
Loads the Task Scheduler COM API
- sppsvc.exe (PID: 4028)
Detected Pony/Fareit Trojan
- key.exe (PID: 1748)
PONY was detected
- key.exe (PID: 1748)
Actions looks like stealing of personal data
- id6.exe (PID: 1388)
- keygen-step-4.exe (PID: 2400)
- key.exe (PID: 1748)
- searzar.exe (PID: 2964)
- mdmd_pytopm.exe (PID: 2072)
- Yandex.exe (PID: 1684)
- Yandex.exe (PID: 2636)
- wyfdggzz.exe (PID: 960)
SOCELARS was detected
- searzar.exe (PID: 2964)
Changes settings of System certificates
- mdmd_pytopm.exe (PID: 2072)
- hjjgaa.exe (PID: 1512)
- Install.exe (PID: 3984)
Changes the autorun value in the registry
- hjjgaa.exe (PID: 1512)
Loads dropped or rewritten executable
- svchost.exe (PID: 3200)
- chrome.exe (PID: 3980)
- intro.exe (PID: 4072)
- chrome.exe (PID: 2780)
- jfiag_gg.exe (PID: 1796)
- hjjgaa.exe (PID: 1232)
- key.exe (PID: 1748)
- chrome.exe (PID: 1176)
- Install.exe (PID: 4080)
- chrome.exe (PID: 1668)
- Yandex.exe (PID: 1800)
- WinRAR.exe (PID: 2440)
- DllHost.exe (PID: 1460)
- chrome.exe (PID: 3124)
- privacytools2.exe (PID: 4052)
- Install.exe (PID: 3984)
- chrome.exe (PID: 3464)
- conhost.exe (PID: 2708)
- cmd.exe (PID: 856)
- wmiprvse.exe (PID: 2584)
- cmd.exe (PID: 1680)
- conhost.exe (PID: 324)
- host.exe (PID: 2596)
- iexplore.exe (PID: 2940)
- conhost.exe (PID: 2812)
- chrome.exe (PID: 2920)
- wmiprvse.exe (PID: 4076)
- PING.EXE (PID: 3168)
- chrome.exe (PID: 2164)
- AUDIODG.EXE (PID: 2540)
- SearchProtocolHost.exe (PID: 3136)
- wmiprvse.exe (PID: 4040)
- WerFault.exe (PID: 3160)
- key.exe (PID: 1096)
- wmiprvse.exe (PID: 1428)
- hjjgaa.exe (PID: 1512)
- cmd.exe (PID: 1324)
- Setup.exe (PID: 3400)
- chrome.exe (PID: 572)
- cmd.exe (PID: 2712)
- keygen-pr.exe (PID: 632)
- SearchProtocolHost.exe (PID: 3264)
- cmd.exe (PID: 1512)
- Avast.8.Free.Antivirus.keygen.exe (PID: 2880)
- PING.EXE (PID: 2456)
- chrome.exe (PID: 2764)
- privacytools2.exe (PID: 2296)
- consent.exe (PID: 3188)
- BTRSetp.exe (PID: 560)
- SearchProtocolHost.exe (PID: 2500)
- iexplore.exe (PID: 2904)
- iexplore.exe (PID: 2648)
- conhost.exe (PID: 4044)
- SearchFilterHost.exe (PID: 992)
- chrome.exe (PID: 2436)
- searzar.exe (PID: 2964)
- jfiag_gg.exe (PID: 1772)
- Setup.exe (PID: 3024)
- Yandex.exe (PID: 2636)
- chrome.exe (PID: 3480)
- mdmd_pytopm.exe (PID: 2072)
- keygen-step-4.exe (PID: 2400)
- DllHost.exe (PID: 1072)
- chrome.exe (PID: 2496)
- id6.exe (PID: 1388)
- Yandex.exe (PID: 1684)
- chrome.exe (PID: 3544)
- WinRAR.exe (PID: 2224)
- conhost.exe (PID: 2536)
- SearchFilterHost.exe (PID: 2624)
- PING.EXE (PID: 3984)
- IELowutil.exe (PID: 3572)
- DllHost.exe (PID: 3808)
- chrome.exe (PID: 2744)
- keygen-step-3.exe (PID: 2572)
- sppsvc.exe (PID: 4028)
- chrome.exe (PID: 3884)
- chrome.exe (PID: 2204)
- chrome.exe (PID: 3080)
- iexplore.exe (PID: 2944)
- consent.exe (PID: 376)
- SearchProtocolHost.exe (PID: 2916)
- conhost.exe (PID: 2640)
- conhost.exe (PID: 2520)
- setup.upx.exe (PID: 2212)
- chrome.exe (PID: 2188)
- consent.exe (PID: 1704)
- DllHost.exe (PID: 3696)
- taskkill.exe (PID: 4024)
- rundll32.exe (PID: 4012)
- cmd.exe (PID: 2976)
- firefox.exe (PID: 4052)
- conhost.exe (PID: 2108)
- cmd.exe (PID: 3780)
- conhost.exe (PID: 2952)
- taskkill.exe (PID: 3456)
- cmd.exe (PID: 3844)
- conhost.exe (PID: 2900)
- cmd.exe (PID: 3236)
- conhost.exe (PID: 792)
- PING.EXE (PID: 1856)
- xcopy.exe (PID: 3084)
- wyfdggzz.exe (PID: 960)
- cmd.exe (PID: 2064)
- conhost.exe (PID: 2796)
- PING.EXE (PID: 576)
- PING.EXE (PID: 3204)
- chrome.exe (PID: 3328)
- chrome.exe (PID: 1332)
- chrome.exe (PID: 3476)
- chrome.exe (PID: 2456)
- chrome.exe (PID: 2016)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 3276)
- chrome.exe (PID: 1536)
- chrome.exe (PID: 3552)
- chrome.exe (PID: 2512)
- chrome.exe (PID: 3736)
- chrome.exe (PID: 3948)
- chrome.exe (PID: 2040)
- cmd.exe (PID: 3900)
- conhost.exe (PID: 3004)
- PING.EXE (PID: 3520)
- chrome.exe (PID: 3088)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 3792)
Modifies files in Chrome extension folder
- Yandex.exe (PID: 1684)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2440)
- key.exe (PID: 1748)
- hjjgaa.exe (PID: 1232)
- privacytools2.exe (PID: 2296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2224)
- Avast.8.Free.Antivirus.keygen.exe (PID: 2880)
- keygen-pr.exe (PID: 632)
- keygen-step-4.exe (PID: 2400)
- Setup.exe (PID: 3400)
- Setup.tmp (PID: 3216)
- hjjgaa.exe (PID: 1512)
- Install.exe (PID: 3984)
- privacytools2.exe (PID: 4052)
- Setup.exe (PID: 3024)
- xcopy.exe (PID: 3084)
- Yandex.exe (PID: 2636)
Starts CMD.EXE for commands execution
- Avast.8.Free.Antivirus.keygen.exe (PID: 2880)
- setup.upx.exe (PID: 2212)
- keygen-step-3.exe (PID: 2572)
- keygen-step-4.exe (PID: 2400)
- Install.exe (PID: 3984)
- Yandex.exe (PID: 1684)
- Yandex.exe (PID: 1800)
- BTRSetp.exe (PID: 560)
- rundll32.exe (PID: 4012)
- Yandex.exe (PID: 2636)
Reads the cookies of Google Chrome
- setup.upx.exe (PID: 2212)
- keygen-step-3.exe (PID: 2572)
- id6.exe (PID: 1388)
- searzar.exe (PID: 2964)
- jfiag_gg.exe (PID: 1772)
- mdmd_pytopm.exe (PID: 2072)
- Yandex.exe (PID: 2636)
- xcopy.exe (PID: 3084)
- wyfdggzz.exe (PID: 960)
Reads Environment values
- key.exe (PID: 1096)
Reads the Windows organization settings
- key.exe (PID: 1096)
Reads Windows owner or organization settings
- key.exe (PID: 1096)
Reads Windows Product ID
- key.exe (PID: 1096)
Starts CMD.EXE for self-deleting
- keygen-step-3.exe (PID: 2572)
- setup.upx.exe (PID: 2212)
- Install.exe (PID: 3984)
- Yandex.exe (PID: 1800)
- BTRSetp.exe (PID: 560)
- Yandex.exe (PID: 1684)
- Yandex.exe (PID: 2636)
Creates files in the user directory
- key.exe (PID: 1748)
- id6.exe (PID: 1388)
- Yandex.exe (PID: 1684)
- Yandex.exe (PID: 2636)
Loads DLL from Mozilla Firefox
- key.exe (PID: 1748)
Reads Internet Cache Settings
- key.exe (PID: 1748)
- id6.exe (PID: 1388)
- searzar.exe (PID: 2964)
- mdmd_pytopm.exe (PID: 2072)
- IELowutil.exe (PID: 3572)
- BTRSetp.exe (PID: 560)
- wyfdggzz.exe (PID: 960)
- Yandex.exe (PID: 2636)
Searches for installed software
- key.exe (PID: 1748)
- key.exe (PID: 1096)
Reads the cookies of Mozilla Firefox
- id6.exe (PID: 1388)
- searzar.exe (PID: 2964)
- mdmd_pytopm.exe (PID: 2072)
- Yandex.exe (PID: 2636)
- wyfdggzz.exe (PID: 960)
Starts Internet Explorer
- cmd.exe (PID: 2712)
Creates a software uninstall entry
- searzar.exe (PID: 2964)
- Install.exe (PID: 3984)
Checks for external IP
- hjjgaa.exe (PID: 1512)
Adds / modifies Windows certificates
- mdmd_pytopm.exe (PID: 2072)
- hjjgaa.exe (PID: 1512)
Low-level read access rights to disk partition
- Install.exe (PID: 3984)
- Yandex.exe (PID: 1800)
- Yandex.exe (PID: 1684)
- Yandex.exe (PID: 2636)
Creates files in the Windows directory
- consent.exe (PID: 1704)
- Yandex.exe (PID: 2636)
Removes files from Windows directory
- consent.exe (PID: 1704)
Starts itself from another location
- Install.exe (PID: 3984)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 3780)
- cmd.exe (PID: 3236)
Uses RUNDLL32.EXE to load library
- Yandex.exe (PID: 1800)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2648)
- iexplore.exe (PID: 2944)
- chrome.exe (PID: 1176)
- iexplore.exe (PID: 2940)
- iexplore.exe (PID: 2904)
Application launched itself
- iexplore.exe (PID: 2648)
- chrome.exe (PID: 1176)
- iexplore.exe (PID: 2940)
- chrome.exe (PID: 2512)
Reads settings of System Certificates
- iexplore.exe (PID: 2944)
- iexplore.exe (PID: 2648)
- chrome.exe (PID: 1668)
- iexplore.exe (PID: 2940)
- iexplore.exe (PID: 2904)
- chrome.exe (PID: 2456)
Changes internet zones settings
- iexplore.exe (PID: 2648)
- iexplore.exe (PID: 2940)
Creates files in the user directory
- iexplore.exe (PID: 2944)
- iexplore.exe (PID: 2648)
- iexplore.exe (PID: 2940)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2648)
- iexplore.exe (PID: 2940)
- chrome.exe (PID: 2456)
Manual execution by user
- chrome.exe (PID: 1176)
Reads internet explorer settings
- iexplore.exe (PID: 2944)
- iexplore.exe (PID: 2904)
Changes settings of System certificates
- iexplore.exe (PID: 2648)
- iexplore.exe (PID: 2940)
- chrome.exe (PID: 2456)
Reads the hosts file
- chrome.exe (PID: 1176)
- chrome.exe (PID: 1668)
- chrome.exe (PID: 2512)
- chrome.exe (PID: 2456)
Reads Microsoft Office registry keys
- key.exe (PID: 1096)
Application was dropped or rewritten from another process
- Setup.tmp (PID: 3976)
- Setup.tmp (PID: 3216)
Creates a software uninstall entry
- Setup.tmp (PID: 3216)
Loads dropped or rewritten executable
- Setup.tmp (PID: 3976)
- Setup.tmp (PID: 3216)
Dropped object may contain Bitcoin addresses
- xcopy.exe (PID: 3084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
163
Monitored processes
129
Malicious processes
44
Suspicious processes
27
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | \??\C:\Windows\system32\conhost.exe "-1989872801555741158-369249440-8958998671057930393-2077447134-726827811-157760501" | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | consent.exe 868 454 04C4D008 | C:\Windows\system32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\BTRSetp.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\BTRSetp.exe | keygen-step-4.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=4028 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 576 | ping 127.0.0.1 -n 3 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 632 | keygen-pr.exe -p83fsase3Ge | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-pr.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 792 | \??\C:\Windows\system32\conhost.exe "15310543701886791492987932172-4438884082126704913-1603639800464645449-1638906695" | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | cmd.exe /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q "C:\Users\admin\AppData\Local\Temp\RarSFX2\setup.upx.exe" | C:\Windows\system32\cmd.exe | — | setup.upx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 960 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\wyfdggzz.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\wyfdggzz.exe | keygen-step-4.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 992 | "C:\Windows\system32\SearchFilterHost.exe" 0 516 520 528 65536 524 | C:\Windows\system32\SearchFilterHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Filter Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 251
Read events
8 632
Write events
594
Delete events
25
Modification events
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | APPSTARTING |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | ARROW |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | CROSS |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | HAND |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | HELP |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | IBEAM |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | NO |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | SIZEALL |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | SIZENESW |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (2596) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | SIZENS |
Value: %SystemRoot%\cursors\clearcur.cur | |||
Executable files
39
Suspicious files
265
Text files
623
Unknown types
90
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab34D1.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar34D2.tmp | — | |
MD5:— | SHA256:— | |||
| 2648 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\AAQR4IKK.txt | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\YXSY2UN2.txt | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_297403111CEDEF1869FC623007E30BE7 | der | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9FF67FB3141440EED32363089565AE60_297403111CEDEF1869FC623007E30BE7 | binary | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\Avast+Free+Antivirus+Licence[1].htm | html | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
65
TCP/UDP connections
132
DNS requests
76
Threats
73
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2944 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2944 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2944 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAQgdyntsK7JtJWcMhDXcC0%3D | US | der | 278 b | whitelisted |
2944 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAQgdyntsK7JtJWcMhDXcC0%3D | US | der | 278 b | whitelisted |
2648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2944 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2944 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDt8oJ55dD%2FpwgAAAAAUx1U | US | der | 472 b | whitelisted |
2648 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2944 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEArLKLpGXuU5CHZ0cPPNxhI%3D | US | der | 471 b | whitelisted |
2944 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDt878iBbv1RCAAAAABTHN4%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2944 | iexplore.exe | 172.67.168.77:443 | keygenninja.com | — | US | unknown |
2944 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2944 | iexplore.exe | 104.17.78.107:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
2944 | iexplore.exe | 172.217.22.8:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2944 | iexplore.exe | 172.217.21.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2648 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2944 | iexplore.exe | 216.58.208.46:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2944 | iexplore.exe | 74.125.206.155:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
2944 | iexplore.exe | 216.58.206.4:443 | www.google.com | Google Inc. | US | whitelisted |
2648 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
keygenninja.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4072 | intro.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
4072 | intro.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2572 | keygen-step-3.exe | A Network Trojan was detected | STEALER [PTsecurity] Powerkatz32_2 |
2572 | keygen-step-3.exe | A Network Trojan was detected | STEALER [PTsecurity] Powerkatz32_2 |
1748 | key.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Nebuler Checkin |
1748 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1748 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
1388 | id6.exe | A Network Trojan was detected | ET TROJAN Suspicious User-Agent (WindowsNT) With No Separating Space |
1388 | id6.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
25 ETPRO signatures available at the full report
Process | Message |
|---|---|
id6.exe | 006 |
id6.exe | http://freekzvideo.cloud/business/receive |
mdmd_pytopm.exe | OpenProcess |
mdmd_pytopm.exe | NtQueryInformationFile |
mdmd_pytopm.exe | |
mdmd_pytopm.exe | DuplicateHandle |
mdmd_pytopm.exe | |
mdmd_pytopm.exe | NtQuerySystemInformation |
mdmd_pytopm.exe | |
mdmd_pytopm.exe | |