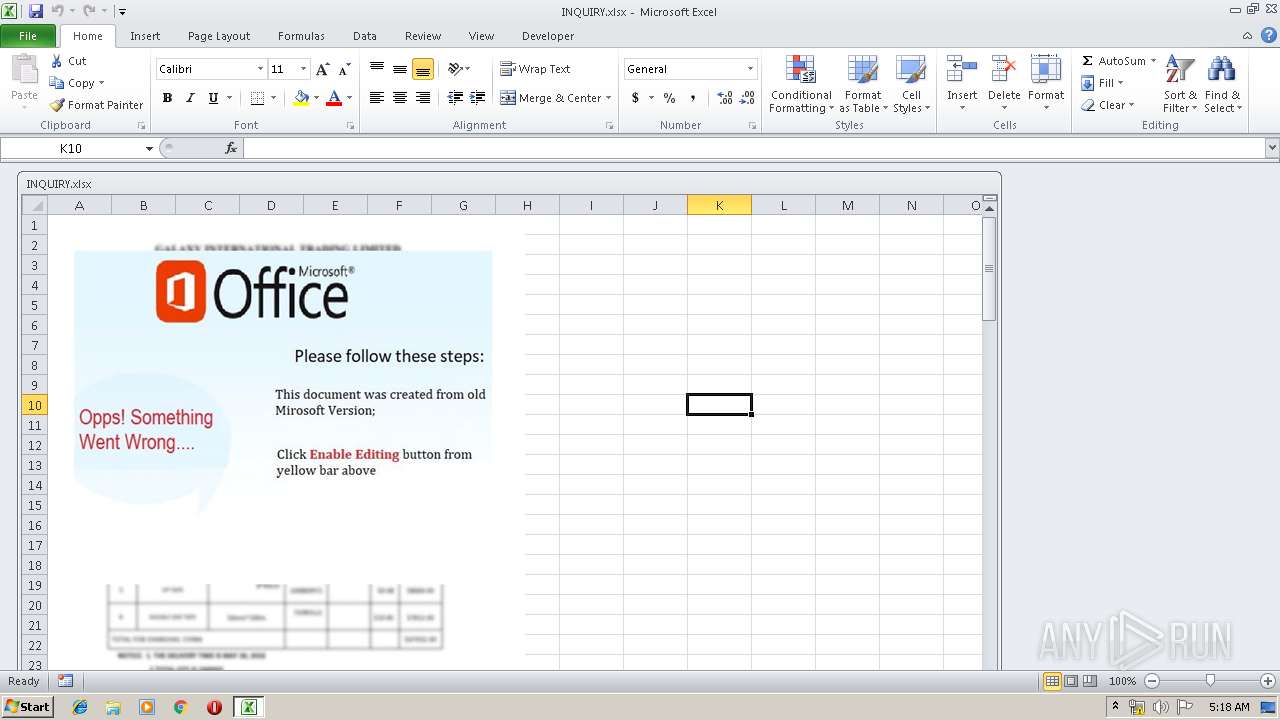
| File name: | INQUIRY.xlsx |
| Full analysis: | https://app.any.run/tasks/eeafd156-a9f2-40ad-b3a9-c5535eb34fd3 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | July 18, 2019, 04:18:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | 7560F795E299DF5979265612739C901E |
| SHA1: | 5AEBD69B131339FAE39A9FBC7AB30917D7F71672 |
| SHA256: | 4A980701F0FE7CCDF9F5B0E6BF33F969B0268DFAA4F2A36F24375D687264D9D6 |
| SSDEEP: | 1536:NnCAEGVU100V6gF/XoSAcp+M4UDS3leud:BCjGVw02F/YSoMIlX |
MALICIOUS
Application was dropped or rewritten from another process
- vbc.exe (PID: 1340)
- vbc.exe (PID: 2480)
- vbc.exe (PID: 3924)
- vbc.exe (PID: 3640)
- vbc.exe (PID: 2624)
- vbc.exe (PID: 952)
- vbc.exe (PID: 2500)
- vbc.exe (PID: 3596)
- vbc.exe (PID: 1264)
- vbc.exe (PID: 2224)
- vbc.exe (PID: 2304)
- vbc.exe (PID: 1636)
- vbc.exe (PID: 2280)
- vbc.exe (PID: 592)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 1456)
Downloads executable files from the Internet
- EQNEDT32.EXE (PID: 1456)
Connects to CnC server
- explorer.exe (PID: 292)
FORMBOOK was detected
- explorer.exe (PID: 292)
Changes the autorun value in the registry
- lsass.exe (PID: 2544)
Formbook was detected
- lsass.exe (PID: 2544)
- Firefox.exe (PID: 3856)
Actions looks like stealing of personal data
- lsass.exe (PID: 2544)
Stealing of credential data
- lsass.exe (PID: 2544)
SUSPICIOUS
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 1456)
Starts CMD.EXE for commands execution
- lsass.exe (PID: 2544)
Application launched itself
- vbc.exe (PID: 2480)
Executed via COM
- EQNEDT32.EXE (PID: 1456)
Loads DLL from Mozilla Firefox
- lsass.exe (PID: 2544)
Creates files in the user directory
- lsass.exe (PID: 2544)
INFO
Manual execution by user
- lsass.exe (PID: 2544)
- NAPSTAT.EXE (PID: 1196)
- autoconv.exe (PID: 2840)
- autoconv.exe (PID: 2536)
- wuapp.exe (PID: 2920)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3860)
Starts Microsoft Office Application
- explorer.exe (PID: 292)
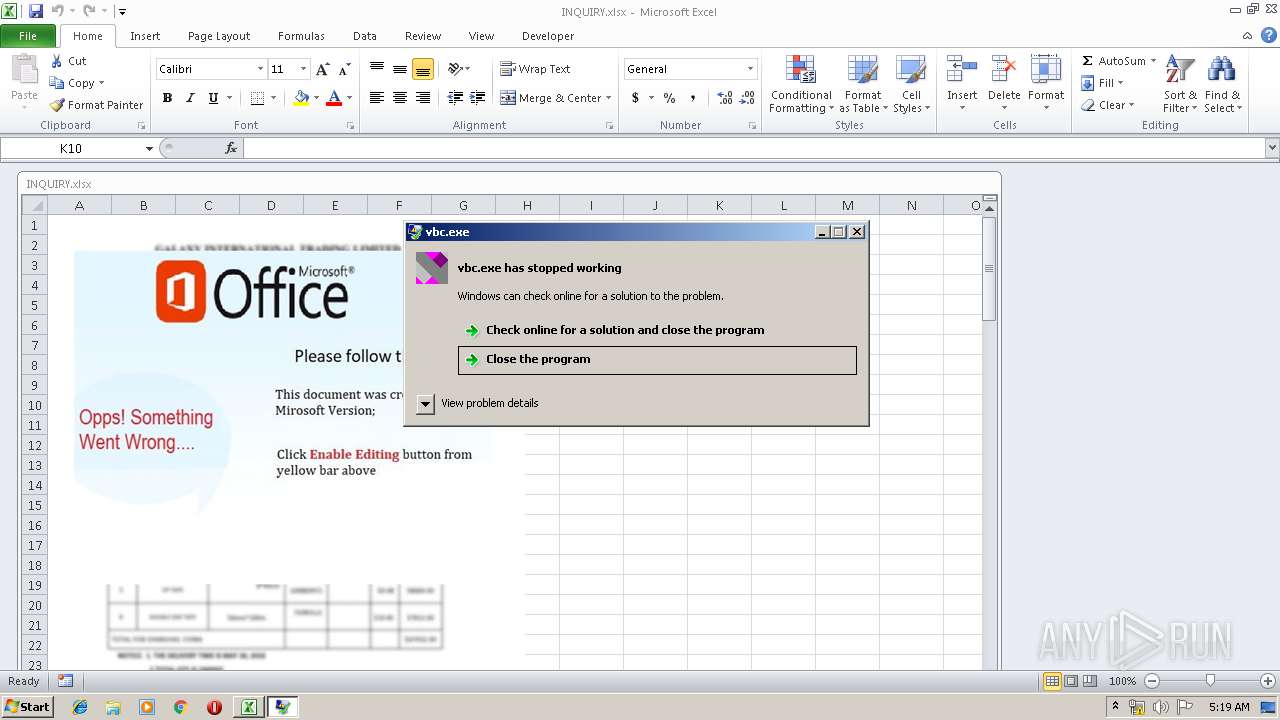
Application was crashed
- vbc.exe (PID: 2480)
Creates files in the user directory
- Firefox.exe (PID: 3856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
61
Monitored processes
24
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 952 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1196 | "C:\Windows\System32\NAPSTAT.EXE" | C:\Windows\System32\NAPSTAT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Access Protection Client UI Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1340 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 1636 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2224 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2280 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
633
Read events
582
Write events
44
Delete events
7
Modification events
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | r,= |
Value: 722C3D00140F0000010000000000000000000000 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 140F00008A0A8BD91F3DD50100000000 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | r,= |
Value: 722C3D00140F0000010000000000000000000000 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (1456) EQNEDT32.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109E60090400000000000F01FEC\Usage |
| Operation: | write | Name: | EquationEditorFilesIntl_1033 |
Value: 1324482563 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3860) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
73
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3860 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRF472.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1456 | EQNEDT32.EXE | C:\Users\Public\vbc.exe | executable | |
MD5:— | SHA256:— | |||
| 2544 | lsass.exe | C:\Users\admin\AppData\Roaming\77M3PD5E\77Mlogrc.ini | binary | |
MD5:— | SHA256:— | |||
| 3856 | Firefox.exe | C:\Users\admin\AppData\Roaming\77M3PD5E\77Mlogrf.ini | binary | |
MD5:— | SHA256:— | |||
| 1456 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\jhn[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2544 | lsass.exe | C:\Users\admin\AppData\Roaming\77M3PD5E\77Mlogim.jpeg | image | |
MD5:— | SHA256:— | |||
| 2544 | lsass.exe | C:\Users\admin\AppData\Roaming\77M3PD5E\77Mlogrv.ini | binary | |
MD5:BA3B6BC807D4F76794C4B81B09BB9BA5 | SHA256:6EEBF968962745B2E9DE2CA969AF7C424916D4E3FE3CC0BB9B3D414ABFCE9507 | |||
| 2544 | lsass.exe | C:\Users\admin\AppData\Roaming\77M3PD5E\77Mlogri.ini | binary | |
MD5:D63A82E5D81E02E399090AF26DB0B9CB | SHA256:EAECE2EBA6310253249603033C744DD5914089B0BB26BDE6685EC9813611BAAE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
43
DNS requests
15
Threats
93
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2024 | WerFault.exe | GET | — | 52.158.209.219:80 | http://watson.microsoft.com/StageOne/vbc_exe/0_0_0_0/5d2e31f6/StackHash_0a9e/0_0_0_0/00000000/c0000005/001100be.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063 | US | — | — | whitelisted |
292 | explorer.exe | GET | — | 50.63.202.40:80 | http://www.nitincreationsphotography.com/jo/?GzyLF=OEX4fKCCXmBLkssY7FHX9KNR5fIgU3FomDIGpaWwPqpCUif3LlnDOO6uF5tMQERiXaGVpQ==&Ann=oJIttXspZ | US | — | — | malicious |
292 | explorer.exe | GET | 404 | 195.201.179.80:80 | http://www.getstudynews.com/jo/?GzyLF=w7C3kWilSUfdx85OmTrKHiGMqQwst4j23ZEVXfnSdJ6+X+VczIYY94sxmTzsf6V8JjAwxw==&Ann=oJIttXspZ&sql=1 | RU | html | 287 b | malicious |
1456 | EQNEDT32.EXE | GET | 200 | 23.249.165.218:80 | http://zerodayv3startedexploitpcwithexcelgreat.duckdns.org/bartn/jhn.exe | US | executable | 1.29 Mb | malicious |
292 | explorer.exe | POST | — | 195.201.179.80:80 | http://www.getstudynews.com/jo/ | RU | — | — | malicious |
292 | explorer.exe | GET | 301 | 198.204.237.165:80 | http://www.emilymayphotography.com/jo/?GzyLF=AaaD6BhuQqf5SZIdIZVn+r94aw/haQZ8LDGnwi806KNRHVyZAHzTXiAMWh8ReDhB+HHzXQ==&Ann=oJIttXspZ&sql=1 | US | html | 354 b | malicious |
292 | explorer.exe | POST | — | 195.201.179.80:80 | http://www.getstudynews.com/jo/ | RU | — | — | malicious |
292 | explorer.exe | GET | 301 | 217.160.0.193:80 | http://www.getmetoibiza.com/jo/?GzyLF=z4w0ICBzWjMsJaStn3jibMQwS67rmVgdN8gw47X4F34PuTLlQTA/FBNBJaS3GbAywK5oug==&Ann=oJIttXspZ&sql=1 | DE | html | 346 b | malicious |
292 | explorer.exe | POST | — | 198.204.237.165:80 | http://www.emilymayphotography.com/jo/ | US | — | — | malicious |
292 | explorer.exe | POST | — | 217.160.0.193:80 | http://www.getmetoibiza.com/jo/ | DE | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1456 | EQNEDT32.EXE | 23.249.165.218:80 | zerodayv3startedexploitpcwithexcelgreat.duckdns.org | ColoCrossing | US | malicious |
2024 | WerFault.exe | 52.158.209.219:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
292 | explorer.exe | 50.63.202.40:80 | www.nitincreationsphotography.com | GoDaddy.com, LLC | US | malicious |
292 | explorer.exe | 195.201.179.80:80 | www.getstudynews.com | Awanti Ltd. | RU | malicious |
292 | explorer.exe | 198.204.237.165:80 | www.emilymayphotography.com | DataShack, LC | US | malicious |
292 | explorer.exe | 217.160.0.193:80 | www.getmetoibiza.com | 1&1 Internet SE | DE | malicious |
292 | explorer.exe | 198.187.30.241:80 | www.boxcay.com | Namecheap, Inc. | US | malicious |
292 | explorer.exe | 50.63.202.57:80 | www.untamedprovisions.us | GoDaddy.com, LLC | US | malicious |
292 | explorer.exe | 104.253.182.251:80 | www.w6526.com | EGIHosting | US | malicious |
292 | explorer.exe | 188.165.53.185:80 | www.carolinecolbach.com | OVH SAS | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zerodayv3startedexploitpcwithexcelgreat.duckdns.org |
| malicious |
www.salliorecentralle-amazon.com |
| unknown |
watson.microsoft.com |
| whitelisted |
www.nitincreationsphotography.com |
| malicious |
www.getstudynews.com |
| malicious |
www.emilymayphotography.com |
| malicious |
www.getmetoibiza.com |
| malicious |
www.xn--xhq44jgvd3c878f.net |
| unknown |
www.supplychainrisk-management.com |
| malicious |
www.qian73.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1456 | EQNEDT32.EXE | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
1456 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2024 | WerFault.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
2024 | WerFault.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
292 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
31 ETPRO signatures available at the full report